Management Report: Creative Action in International Organizations
VerifiedAdded on 2023/04/21
|18
|3895
|63
Report
AI Summary
This report explores creative action in international organizations to combat cybersecurity and online crime, focusing on the feasibility of K7 Total Security in small international enterprises. It emphasizes the importance of strategic management, opportunity mapping, and innovation in averting cybercrimes that lead to data loss and financial instability. The report advocates for a leader-like approach, participative leadership, and communication with research and development teams to enhance product differentiation and security. It also introduces the Diamond model process for problem-solving and value delivery, along with a problem/opportunity map for assessing the benefits of K7 Total Security. The analysis includes a proposed product lifecycle and value chain analysis, ultimately offering recommendations for strengthening cybersecurity measures and improving the competitive advantage of international enterprises through proactive and innovative strategies.

Running head: MANAGEMENT
Creative action in international organizations: Cybersecurity & online crime
Name of the student:
Name of the university:
Author note:
Creative action in international organizations: Cybersecurity & online crime
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
MANAGEMENT
Executive summary
Value proposition is effective for assessing the feasibility of the plans in terms of the
identified requirements. This can be conducted through the means of product life cycle.
Opportunity mapping is also helpful in terms of scaling the sources, through which the
product would be acquired. Diamond model process is the most relevant in the case of
cybercrimes in the International enterprises. This is in terms of the loss of confidential data
and financial statement, which the report attempts to project. Communications with the
research and development team is fruitful in terms of conducting product differentiation
through the advent of innovation within the design of the software. Strategic approach is
beneficial in increasing the trafficking of the audience, expanding the scope and arena of the
entrepreneur business.
MANAGEMENT
Executive summary
Value proposition is effective for assessing the feasibility of the plans in terms of the
identified requirements. This can be conducted through the means of product life cycle.
Opportunity mapping is also helpful in terms of scaling the sources, through which the
product would be acquired. Diamond model process is the most relevant in the case of
cybercrimes in the International enterprises. This is in terms of the loss of confidential data
and financial statement, which the report attempts to project. Communications with the
research and development team is fruitful in terms of conducting product differentiation
through the advent of innovation within the design of the software. Strategic approach is
beneficial in increasing the trafficking of the audience, expanding the scope and arena of the
entrepreneur business.

2
MANAGEMENT
Table of contents
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
Overview of the situation.......................................................................................................3
Needful action........................................................................................................................4
Ideas for acquiring the security software...............................................................................5
Market focus...........................................................................................................................6
Thought process behind innovation.......................................................................................8
Plan for transforming the ideas into actions...........................................................................8
Diamond process model.....................................................................................................9
Problem/Opportunity Map.................................................................................................9
Value chain analysis.............................................................................................................11
Recommendations....................................................................................................................12
Conclusion................................................................................................................................14
References................................................................................................................................15
Bibliography.............................................................................................................................16
MANAGEMENT
Table of contents
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
Overview of the situation.......................................................................................................3
Needful action........................................................................................................................4
Ideas for acquiring the security software...............................................................................5
Market focus...........................................................................................................................6
Thought process behind innovation.......................................................................................8
Plan for transforming the ideas into actions...........................................................................8
Diamond process model.....................................................................................................9
Problem/Opportunity Map.................................................................................................9
Value chain analysis.............................................................................................................11
Recommendations....................................................................................................................12
Conclusion................................................................................................................................14
References................................................................................................................................15
Bibliography.............................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
MANAGEMENT
Introduction
Management of the business activities is crucial in terms of ensuring its smooth
functioning. Managerial activities are also necessary for averting the criminal activities,
which results in the loss of properties and the systems. In the present competitive era of the
market, the business operations are dependent on the systems. This is in terms of adding
automation into the processes, reducing the manual labour. Advancements have entered in the
information technology in the form of cloud computing, software and various apps, easing
the convenience of the businesspersons in enhancing the efficiency in the business (Shalley
and Gilson 2017). However, cybercrimes have compelled the personnel to encounter loss of
data, stalling the productivity. This alarming situation necessitates the need of security
software, which would be flexible and helps in maintaining the confidentiality and privacy of
the data and financial statements. This report attempts to shed light on the feasibility of K7
Total Security in the small International enterprises in terms of cyber security.
Discussion
Overview of the situation
Small International enterprises are on their developing stage, when the business
strategies need to be strong and flexible. Tactful approach is beneficial in terms of averting
wrong decisions. However, Cropley (2016), points out that most of the International
enterprises end up experiencing tough competition from the established brands. This is in
terms of improper approach towards conducting the marketing activities, which compels
them to experience a downmarket scenario. This situation adds an interrogative parameter
into their establishment in the market.
MANAGEMENT
Introduction
Management of the business activities is crucial in terms of ensuring its smooth
functioning. Managerial activities are also necessary for averting the criminal activities,
which results in the loss of properties and the systems. In the present competitive era of the
market, the business operations are dependent on the systems. This is in terms of adding
automation into the processes, reducing the manual labour. Advancements have entered in the
information technology in the form of cloud computing, software and various apps, easing
the convenience of the businesspersons in enhancing the efficiency in the business (Shalley
and Gilson 2017). However, cybercrimes have compelled the personnel to encounter loss of
data, stalling the productivity. This alarming situation necessitates the need of security
software, which would be flexible and helps in maintaining the confidentiality and privacy of
the data and financial statements. This report attempts to shed light on the feasibility of K7
Total Security in the small International enterprises in terms of cyber security.
Discussion
Overview of the situation
Small International enterprises are on their developing stage, when the business
strategies need to be strong and flexible. Tactful approach is beneficial in terms of averting
wrong decisions. However, Cropley (2016), points out that most of the International
enterprises end up experiencing tough competition from the established brands. This is in
terms of improper approach towards conducting the marketing activities, which compels
them to experience a downmarket scenario. This situation adds an interrogative parameter
into their establishment in the market.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
MANAGEMENT
Needful action
In terms of setting their business, the International enterprises need to come up with
something innovative. Herein lays the appropriateness of strategic management. Within this,
mention can be made of segmenting the approach into Opportunity, Creation and
Innovation. For this, the actions need to be leader like. As a matter of specification, Serrat
(2017) is of the view that the International enterprises need to think of security software,
which would be something unique.
Fig 1: Opportunity, creativity and innovation
(Source: Cohendet, Parmentier and Simon 2017)
If the managers practice participative leadership style, the members would get a
chance to share their ideas about the new security software, K7 Total Security. Combination
MANAGEMENT
Needful action
In terms of setting their business, the International enterprises need to come up with
something innovative. Herein lays the appropriateness of strategic management. Within this,
mention can be made of segmenting the approach into Opportunity, Creation and
Innovation. For this, the actions need to be leader like. As a matter of specification, Serrat
(2017) is of the view that the International enterprises need to think of security software,
which would be something unique.
Fig 1: Opportunity, creativity and innovation
(Source: Cohendet, Parmentier and Simon 2017)
If the managers practice participative leadership style, the members would get a
chance to share their ideas about the new security software, K7 Total Security. Combination

5
MANAGEMENT
of several ideas would act assistance in reaching to the appropriate. Indulging in discussions
with the engineers would help in adding innovative design to the software. Once the
responses start flooding in, the managers would be able to assess the prospective sources,
through which value can be generated.
Ideas for acquiring the security software
The ideas for acquiring change pops out from a problem, negative results from a
product or service, media stories, projects, events, charity purpose or just for the sake of
altering the business scenario. All of these aspects seem true for an enterprise. According to
the opinions of Henriksen, Mishra and Fisser (2016), as their business is on a raw stage,
negative results from the products and services can be one of the reasons behind the plans to
acquire new products. However, innovation in the existing products can also be beneficial in
terms of luring more customers. In this, the schemes of charity might be an innovative
opportunity in terms of strengthening the financial resources. In this context, problems in
security the data gains more weightage for the International enterprises in terms of adopting
k7 Total Security Software.
Sorting the ideas would be beneficial in terms of ensuring whether it aligns with the
identified needs and requirements. This can be done through an integrated process:
MANAGEMENT
of several ideas would act assistance in reaching to the appropriate. Indulging in discussions
with the engineers would help in adding innovative design to the software. Once the
responses start flooding in, the managers would be able to assess the prospective sources,
through which value can be generated.
Ideas for acquiring the security software
The ideas for acquiring change pops out from a problem, negative results from a
product or service, media stories, projects, events, charity purpose or just for the sake of
altering the business scenario. All of these aspects seem true for an enterprise. According to
the opinions of Henriksen, Mishra and Fisser (2016), as their business is on a raw stage,
negative results from the products and services can be one of the reasons behind the plans to
acquire new products. However, innovation in the existing products can also be beneficial in
terms of luring more customers. In this, the schemes of charity might be an innovative
opportunity in terms of strengthening the financial resources. In this context, problems in
security the data gains more weightage for the International enterprises in terms of adopting
k7 Total Security Software.
Sorting the ideas would be beneficial in terms of ensuring whether it aligns with the
identified needs and requirements. This can be done through an integrated process:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
MANAGEMENT
Fig 2: The idea process
(Source: Cruickshank 2016)
At the initial stage, need analysis would be crucial in terms of gaining an insight into
the need and urgency of security. This results in the generation of ideas regarding the
adoption of security software like k7 Total Security. As a sequential step, screening and
development of the software would be fruitful in terms of checking its proper functioning.
Offshore marketing would be helpful in enriching the scope and arena of the business.
Finally, after consistent lab tests and quality controls, the software can be purchased.
Market focus
Assessing the potential markets would be important for the technology brands. In this,
the typical components are value proposition, growth and development along with
accessibility. Adams and Makramalla (2015) states that the next step is segmenting the target
audience, that is, the entrepreneurs, as they are the easy targets of hackers due to lack of
antivirus. This is because they are in need of the security software for storing the data in a
secured manner. However, the brands would be able to enjoy higher competitive advantage
as the entrepreneurs would not have high decision making factors. They just need a solution,
which would help in securing the data. On the contrary, convergent thinking would turn the
ideas into opportunities for the International enterprises. Market research enrich their
knowledge regarding adopting the strategies of product differentiation for altering the
business dynamics.
In terms of value proposition, Cui (2016) points that DIFA model can be adopted by
the entrepreneurs. The components of this model are demand, innovation, feasibility and
attraction. Researching about k7 Total Security Software would help the entrepreneurs in
realizing the customers’ need and their actual potential to fulfil those needs. For bringing
MANAGEMENT
Fig 2: The idea process
(Source: Cruickshank 2016)
At the initial stage, need analysis would be crucial in terms of gaining an insight into
the need and urgency of security. This results in the generation of ideas regarding the
adoption of security software like k7 Total Security. As a sequential step, screening and
development of the software would be fruitful in terms of checking its proper functioning.
Offshore marketing would be helpful in enriching the scope and arena of the business.
Finally, after consistent lab tests and quality controls, the software can be purchased.
Market focus
Assessing the potential markets would be important for the technology brands. In this,
the typical components are value proposition, growth and development along with
accessibility. Adams and Makramalla (2015) states that the next step is segmenting the target
audience, that is, the entrepreneurs, as they are the easy targets of hackers due to lack of
antivirus. This is because they are in need of the security software for storing the data in a
secured manner. However, the brands would be able to enjoy higher competitive advantage
as the entrepreneurs would not have high decision making factors. They just need a solution,
which would help in securing the data. On the contrary, convergent thinking would turn the
ideas into opportunities for the International enterprises. Market research enrich their
knowledge regarding adopting the strategies of product differentiation for altering the
business dynamics.
In terms of value proposition, Cui (2016) points that DIFA model can be adopted by
the entrepreneurs. The components of this model are demand, innovation, feasibility and
attraction. Researching about k7 Total Security Software would help the entrepreneurs in
realizing the customers’ need and their actual potential to fulfil those needs. For bringing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
MANAGEMENT
innovation into the products and services, the entrepreneurs can conduct Product Life Cycle
of k7 Total Security SOFTWARE.
Fig 4: Propose product life cycle for k7 Total Security Software in the International
enterprises
(Source: Prepared by the researcher)
Discussion on the product life cycle would enhance the awareness of the
entrepreneurs about the innovation needed in the software. Involving the stakeholders and
shareholders in these discussions would be beneficial in assessing the feasibility of the
software in terms of securing their data as well as the confidential business codes and
financial statements. Maturation of the ideas into the positive response of the customers
would reflect the attraction levels. Considering the demand supply curve would be beneficial
in terms of mapping the needs, demands and requirements of the clients and the customers.
Surveys and feedbacks would expand the thought processes behind transforming the ideas
into practice (Zhuhadar et al. 2017).
MANAGEMENT
innovation into the products and services, the entrepreneurs can conduct Product Life Cycle
of k7 Total Security SOFTWARE.
Fig 4: Propose product life cycle for k7 Total Security Software in the International
enterprises
(Source: Prepared by the researcher)
Discussion on the product life cycle would enhance the awareness of the
entrepreneurs about the innovation needed in the software. Involving the stakeholders and
shareholders in these discussions would be beneficial in assessing the feasibility of the
software in terms of securing their data as well as the confidential business codes and
financial statements. Maturation of the ideas into the positive response of the customers
would reflect the attraction levels. Considering the demand supply curve would be beneficial
in terms of mapping the needs, demands and requirements of the clients and the customers.
Surveys and feedbacks would expand the thought processes behind transforming the ideas
into practice (Zhuhadar et al. 2017).

8
MANAGEMENT
For creating value, the entrepreneurs need to categorise the idea. Radical and
convergent thinking would be appropriate in terms of achieving positive outcomes. Software
would belong to the category of technology. In this, indication of the non-financial indicators,
like physical and human resources would help in preparation of the budget behind purchasing
the software. Opportunity map would be assistance in terms of generating value on the basis
of both the financial and non-financial resources.
Thought process behind innovation
At the initial stages, the business of the entrepreneurs lacks stability due to proper
approach, design and strategy. However, in order to maintain the competitive pace, they
envision quick success, which is not always the case. The immediate result is customer
turnover, resulting in loss. As per the arguments of Gretter and Yadav (2016), in order to
avert these situations, creativity and innovation is needed. Reference can be cited of
divergent and convergent thinking, which unleashes the imaginative power of the
entrepreneurs. Divergent thinking helps in expanding the scope and arena of the thought
processes. This is due to the collection of different and wide ranging ideas regarding
upgrading the cyber security through software. Market research on k7 Total Security
Software would help the managers to explore the opportunities for enhancing the security of
the confidential data.
On the other hand, convergent thinking eases the process of selecting the appropriate
solution from the available alternatives. Indulging in meeting with the members of the
research and development team would be beneficial in generating plans for preparing the
budget, resource allocation and monitoring (Janssen et al. 2017).
MANAGEMENT
For creating value, the entrepreneurs need to categorise the idea. Radical and
convergent thinking would be appropriate in terms of achieving positive outcomes. Software
would belong to the category of technology. In this, indication of the non-financial indicators,
like physical and human resources would help in preparation of the budget behind purchasing
the software. Opportunity map would be assistance in terms of generating value on the basis
of both the financial and non-financial resources.
Thought process behind innovation
At the initial stages, the business of the entrepreneurs lacks stability due to proper
approach, design and strategy. However, in order to maintain the competitive pace, they
envision quick success, which is not always the case. The immediate result is customer
turnover, resulting in loss. As per the arguments of Gretter and Yadav (2016), in order to
avert these situations, creativity and innovation is needed. Reference can be cited of
divergent and convergent thinking, which unleashes the imaginative power of the
entrepreneurs. Divergent thinking helps in expanding the scope and arena of the thought
processes. This is due to the collection of different and wide ranging ideas regarding
upgrading the cyber security through software. Market research on k7 Total Security
Software would help the managers to explore the opportunities for enhancing the security of
the confidential data.
On the other hand, convergent thinking eases the process of selecting the appropriate
solution from the available alternatives. Indulging in meeting with the members of the
research and development team would be beneficial in generating plans for preparing the
budget, resource allocation and monitoring (Janssen et al. 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
MANAGEMENT
Plan for transforming the ideas into actions
Action plans would be effective for the entrepreneurs in terms of strengthening the
business strategies. Preparing rough drafts and sharing it with the clients and the customers
would be beneficial in assessing its effectiveness in terms of the identified and specified
requirements. Analytical tools would act assistance for the entrepreneurs to assess whether
value is generated through the actions.
Diamond process model
Typical mention can be made of Diamond model process, which would help in
delving deeper into the roots of the problem and delivering value through the means of
effective solutions. The issue of cybercrime is at the centre of the businesses of International
enterprises, stalling the productivity. Adherence to the structure of Discover, Define, Develop
and Deliver would act as an agent in terms of valuing the purchasing power of the customers.
Fig 5: Double diamond model process for k7 Total Security Software
(Source: Created by the researcher)
Cybercrim
e
Discover
(research on k7
Total Security
Software
Define (Idea
generation on
acquiring the
security)
Develop
(communicatio
n with R&D
team and
Deliver (Product
life cycle of k7
Total Security
Software for
generating value
on the investments
of the clients and
the custromers
MANAGEMENT
Plan for transforming the ideas into actions
Action plans would be effective for the entrepreneurs in terms of strengthening the
business strategies. Preparing rough drafts and sharing it with the clients and the customers
would be beneficial in assessing its effectiveness in terms of the identified and specified
requirements. Analytical tools would act assistance for the entrepreneurs to assess whether
value is generated through the actions.
Diamond process model
Typical mention can be made of Diamond model process, which would help in
delving deeper into the roots of the problem and delivering value through the means of
effective solutions. The issue of cybercrime is at the centre of the businesses of International
enterprises, stalling the productivity. Adherence to the structure of Discover, Define, Develop
and Deliver would act as an agent in terms of valuing the purchasing power of the customers.
Fig 5: Double diamond model process for k7 Total Security Software
(Source: Created by the researcher)
Cybercrim
e
Discover
(research on k7
Total Security
Software
Define (Idea
generation on
acquiring the
security)
Develop
(communicatio
n with R&D
team and
Deliver (Product
life cycle of k7
Total Security
Software for
generating value
on the investments
of the clients and
the custromers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
MANAGEMENT
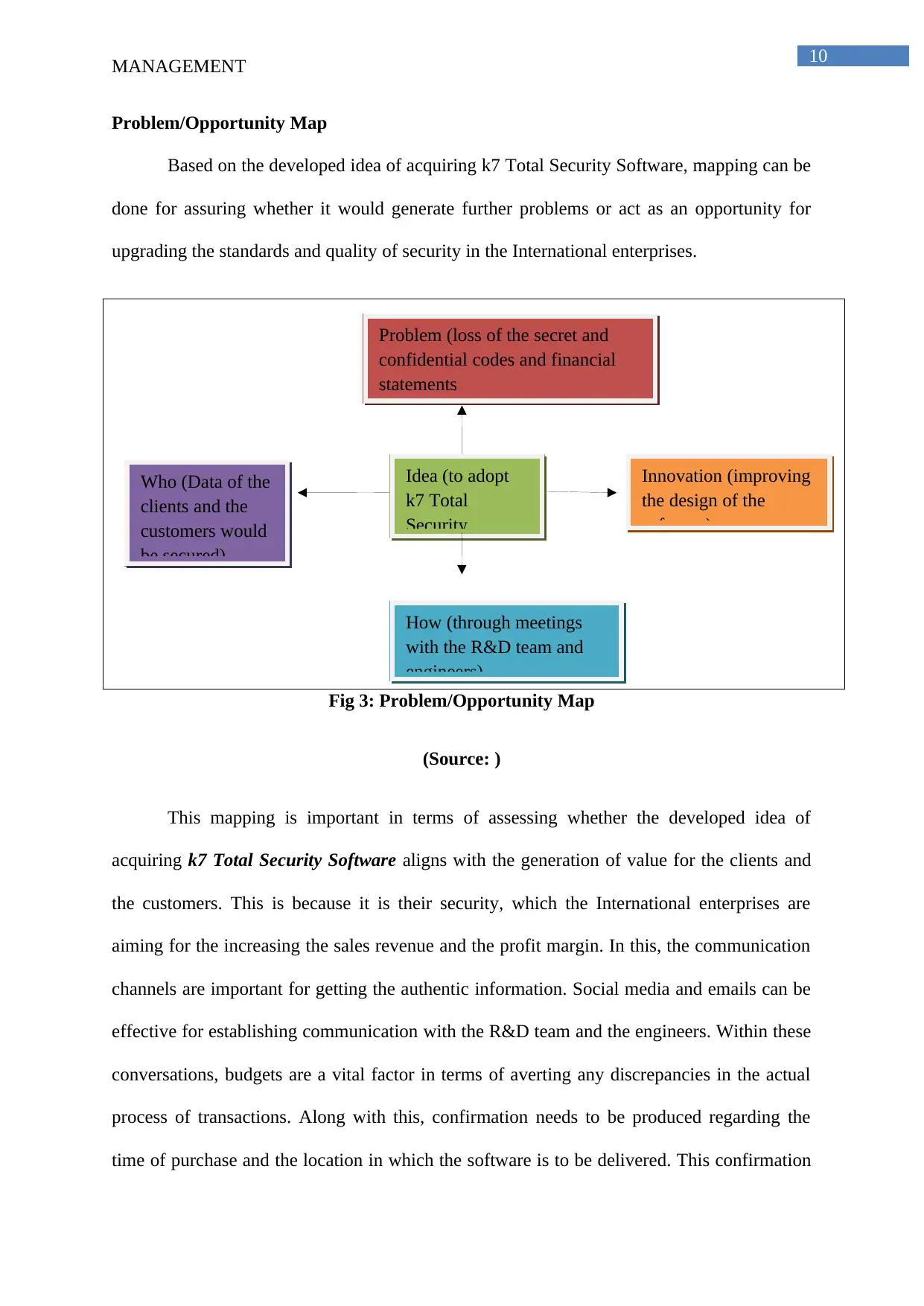
Problem/Opportunity Map
Based on the developed idea of acquiring k7 Total Security Software, mapping can be
done for assuring whether it would generate further problems or act as an opportunity for
upgrading the standards and quality of security in the International enterprises.
Fig 3: Problem/Opportunity Map
(Source: )
This mapping is important in terms of assessing whether the developed idea of
acquiring k7 Total Security Software aligns with the generation of value for the clients and
the customers. This is because it is their security, which the International enterprises are
aiming for the increasing the sales revenue and the profit margin. In this, the communication
channels are important for getting the authentic information. Social media and emails can be
effective for establishing communication with the R&D team and the engineers. Within these
conversations, budgets are a vital factor in terms of averting any discrepancies in the actual
process of transactions. Along with this, confirmation needs to be produced regarding the
time of purchase and the location in which the software is to be delivered. This confirmation
Idea (to adopt
k7 Total
Security
Problem (loss of the secret and
confidential codes and financial
statements
Innovation (improving
the design of the
software)
How (through meetings
with the R&D team and
engineers)
Who (Data of the
clients and the
customers would
be secured)
MANAGEMENT
Problem/Opportunity Map
Based on the developed idea of acquiring k7 Total Security Software, mapping can be
done for assuring whether it would generate further problems or act as an opportunity for
upgrading the standards and quality of security in the International enterprises.
Fig 3: Problem/Opportunity Map
(Source: )
This mapping is important in terms of assessing whether the developed idea of
acquiring k7 Total Security Software aligns with the generation of value for the clients and
the customers. This is because it is their security, which the International enterprises are
aiming for the increasing the sales revenue and the profit margin. In this, the communication
channels are important for getting the authentic information. Social media and emails can be
effective for establishing communication with the R&D team and the engineers. Within these
conversations, budgets are a vital factor in terms of averting any discrepancies in the actual
process of transactions. Along with this, confirmation needs to be produced regarding the
time of purchase and the location in which the software is to be delivered. This confirmation
Idea (to adopt
k7 Total
Security
Problem (loss of the secret and
confidential codes and financial
statements
Innovation (improving
the design of the
software)
How (through meetings
with the R&D team and
engineers)
Who (Data of the
clients and the
customers would
be secured)

11
MANAGEMENT
would act assistance for the suppliers to assess whether the order is ready and there is
adequate transport logistics for delivering the order. Intimating the International enterprises
about the delivery is important in terms of averting communication gaps.
Value chain analysis
Through value chain analysis, the International enterprises would be able to identify
the primary and supportive activities, which would attach value to the final product, k7 Total
Security Software. Reduction of the operational costs and increasing product differentiation
would be an agent in terms of attracting more customers.
Primary activities
Inbound logistics- assessing the resources and capabilities for acquiring the software
Operations- researching about the security software, which would generate greater
value
Outbound logistics- Offshore marketing for establishing contact with the technology
suppliers
Marketing & sales- Communicating with the marketing and sales team for
developing budget
Service- Survey and feedbacks on the levied strategies
Supporting activities
Firm infrastructure- Proper facilities for conducting meetings and discussions
Human resource management- skilled and qualified workers, quality raw materials
Procurement- contacting the suppliers for acquiring additional spare parts for the
software
MANAGEMENT
would act assistance for the suppliers to assess whether the order is ready and there is
adequate transport logistics for delivering the order. Intimating the International enterprises
about the delivery is important in terms of averting communication gaps.
Value chain analysis
Through value chain analysis, the International enterprises would be able to identify
the primary and supportive activities, which would attach value to the final product, k7 Total
Security Software. Reduction of the operational costs and increasing product differentiation
would be an agent in terms of attracting more customers.
Primary activities
Inbound logistics- assessing the resources and capabilities for acquiring the software
Operations- researching about the security software, which would generate greater
value
Outbound logistics- Offshore marketing for establishing contact with the technology
suppliers
Marketing & sales- Communicating with the marketing and sales team for
developing budget
Service- Survey and feedbacks on the levied strategies
Supporting activities
Firm infrastructure- Proper facilities for conducting meetings and discussions
Human resource management- skilled and qualified workers, quality raw materials
Procurement- contacting the suppliers for acquiring additional spare parts for the
software
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




