Criminology Research Proposal: Cybercrime, Governance, and Responses
VerifiedAdded on 2023/01/11
|8
|2107
|59
Report
AI Summary
This report presents a research proposal focusing on international cybercrime. It begins with an introduction to the topic, emphasizing the illegal activities conducted through digital platforms and their impact on international law and governance. The main body of the report examines the problems associated with cybercrime, such as data breaches and online fraud, along with an analysis of existing governance arrangements and responses, including the Cybercrime Act, 2001. The report also explores preliminary ideas for improving governance and responses, such as enhanced security measures and international cooperation. The research plan outlines the activities and timeline for the project, and the conclusion summarizes the key findings and recommendations, highlighting the need for robust security measures and international collaboration to combat cybercrime effectively. The references section includes various books, journals, and policy papers.

CRIMINOLOGY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION.................................................................................................................................3
MAIN BODY........................................................................................................................................3
Examination of problems...................................................................................................................3
Examination of the governance arrangement.....................................................................................4
Examination of the responses............................................................................................................4
Preliminary ideas to improve governance and responses...................................................................5
Research plan....................................................................................................................................6
CONCLUSION.....................................................................................................................................7
REFERENCES......................................................................................................................................7
INTRODUCTION.................................................................................................................................3
MAIN BODY........................................................................................................................................3
Examination of problems...................................................................................................................3
Examination of the governance arrangement.....................................................................................4
Examination of the responses............................................................................................................4
Preliminary ideas to improve governance and responses...................................................................5
Research plan....................................................................................................................................6
CONCLUSION.....................................................................................................................................7
REFERENCES......................................................................................................................................7

INTRODUCTION
Cybercrime refers to the illegal crime which is mainly committed through the
computer or any digital platform and which is against the policies of the government. If such
crime is committed internationally, than it results in challenges the rules and regulation of the
domestic and international law and government norms. If any person committed any offences
which is illegal, than he is liable to be punished under the Criminal code act 1995. In respect
of any activity committed through the mode of computers and are considered to be illegal,
than it is liable to be punished under the Cybercrime Act, 2001 (Broadhurst, 2017). It is
recorded that top 5 cybercrime are mainly considered to be serious offences as Phishing
scans, online harassment of people, cyber stalking, infringing the privacy information and
also theft scanning. Thus, the main reason of choosing this topic is to be identify the impact
of cybercrime which is occurring internationally instead of imposing strict government
regulation regarding securing the right of the person.
MAIN BODY
Examination of problems
In recent times, most of the people are totally depend on the electronic mode
regarding storing their information or also sharing their details regarding carrying any online
transaction through banks or other shopping sites. Thus, the issues raised regarding sharing
the personal information to the online sites or also attending the fraud calls which is made
through the name of banks. In such manner the major problems which is faced in the country
is relating to lack of security about the clients information or also not recruiting the
experiences person for developing the high security codes in the business. The impact which
is faced through this perspective is related to not building the trust of the people and also not
increasing the economy of the country (Slocombe, 2017). This situation is faced by the
Facebook Company during the period of election of Donald trump. As Cambridge Analytica
fraudulent hack the information of the users of the Facebook without their prior consent and
resulting in facing negative image of Facebook.
This resulting in one type of cybercrime in which the data is not highly secured and
also not protected by the experts after getting negative response from person whose data are
infringed. Another problem which is raised through Cybercrime is relating to the fraud calls
to person regarding sharing their bank detail for high security (Sarre, Lau and Chang, 2018).
Cybercrime refers to the illegal crime which is mainly committed through the
computer or any digital platform and which is against the policies of the government. If such
crime is committed internationally, than it results in challenges the rules and regulation of the
domestic and international law and government norms. If any person committed any offences
which is illegal, than he is liable to be punished under the Criminal code act 1995. In respect
of any activity committed through the mode of computers and are considered to be illegal,
than it is liable to be punished under the Cybercrime Act, 2001 (Broadhurst, 2017). It is
recorded that top 5 cybercrime are mainly considered to be serious offences as Phishing
scans, online harassment of people, cyber stalking, infringing the privacy information and
also theft scanning. Thus, the main reason of choosing this topic is to be identify the impact
of cybercrime which is occurring internationally instead of imposing strict government
regulation regarding securing the right of the person.
MAIN BODY
Examination of problems
In recent times, most of the people are totally depend on the electronic mode
regarding storing their information or also sharing their details regarding carrying any online
transaction through banks or other shopping sites. Thus, the issues raised regarding sharing
the personal information to the online sites or also attending the fraud calls which is made
through the name of banks. In such manner the major problems which is faced in the country
is relating to lack of security about the clients information or also not recruiting the
experiences person for developing the high security codes in the business. The impact which
is faced through this perspective is related to not building the trust of the people and also not
increasing the economy of the country (Slocombe, 2017). This situation is faced by the
Facebook Company during the period of election of Donald trump. As Cambridge Analytica
fraudulent hack the information of the users of the Facebook without their prior consent and
resulting in facing negative image of Facebook.
This resulting in one type of cybercrime in which the data is not highly secured and
also not protected by the experts after getting negative response from person whose data are
infringed. Another problem which is raised through Cybercrime is relating to the fraud calls
to person regarding sharing their bank detail for high security (Sarre, Lau and Chang, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The impact is raised in respect of getting less trust among the person to invest money in
banks. Thus, results in less usages of banks and also in turn results in closure of the existing
branches.
Examination of the governance arrangement
As government norms are strict in the cases of cybercrime as it results in affecting the
economy of the country regarding providing less security to the persons. Government had
taken the strict action, if any person committed any illegal act through the mode of computers
and thus imposed strict regulation in the form of regulating the Cybercrime Act, 2001. In this
the government regulation are imposed regarding controlling the usage of computer through
providing the high coded security of the person information. If the cases arises regarding
infringing any information without the consent of the person, then such accused are liable to
be punished under the Cybercrime act, 2001 for the time period of 3 years imprisonment with
fine.
Another issues which is raised through Cybercrime is relating to the violation of the
privacy of the clients information. As this is mainly undertaken by the competitors’ regarding
attracting the customer interest towards their own business. By this aspects, they violated the
government norms in respect of hacking the company strategies and also their client’s
information and then adapts the same strategies by imposing less pricing with better quality
products. In such manner, the issue of cyber hacking is undertaken in respect of infringing the
company detail and clients information without their permission. Thus, results in punishable
under the Privacy act, 1988 and also the criminal are liable to penalized under the Computer
misuse Act, 1990 under which the punishment is imposed for the period of two years in
prison and fine of 5000 (Maras, 2019.).
In such aspects, legislation are passed for the companies and organization to work and
maintain the security through protecting the data and also upgrading their software and
internal team in respect of reducing the offences in the country. It is necessary for the
companies to recruit the trained and experiences person who can bring innovative ideas to
protect the crime in respect of securing the nation from such illegal offences.
Examination of the responses
There are much different type of policies which has been made at international level
which used to has shown a good response to the global issue of cybercrime at global level.
banks. Thus, results in less usages of banks and also in turn results in closure of the existing
branches.
Examination of the governance arrangement
As government norms are strict in the cases of cybercrime as it results in affecting the
economy of the country regarding providing less security to the persons. Government had
taken the strict action, if any person committed any illegal act through the mode of computers
and thus imposed strict regulation in the form of regulating the Cybercrime Act, 2001. In this
the government regulation are imposed regarding controlling the usage of computer through
providing the high coded security of the person information. If the cases arises regarding
infringing any information without the consent of the person, then such accused are liable to
be punished under the Cybercrime act, 2001 for the time period of 3 years imprisonment with
fine.
Another issues which is raised through Cybercrime is relating to the violation of the
privacy of the clients information. As this is mainly undertaken by the competitors’ regarding
attracting the customer interest towards their own business. By this aspects, they violated the
government norms in respect of hacking the company strategies and also their client’s
information and then adapts the same strategies by imposing less pricing with better quality
products. In such manner, the issue of cyber hacking is undertaken in respect of infringing the
company detail and clients information without their permission. Thus, results in punishable
under the Privacy act, 1988 and also the criminal are liable to penalized under the Computer
misuse Act, 1990 under which the punishment is imposed for the period of two years in
prison and fine of 5000 (Maras, 2019.).
In such aspects, legislation are passed for the companies and organization to work and
maintain the security through protecting the data and also upgrading their software and
internal team in respect of reducing the offences in the country. It is necessary for the
companies to recruit the trained and experiences person who can bring innovative ideas to
protect the crime in respect of securing the nation from such illegal offences.
Examination of the responses
There are much different type of policies which has been made at international level
which used to has shown a good response to the global issue of cybercrime at global level.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This policy used to define the different government response to the global issue. These
policies are not limited to legislation. Some of the policy are as follows:
ICB4PAC896 Draft Model Policy for Cybercrime and HIPCAR Model Policy on Cybercrime
Are two main policies at the global level that used to govern the policy of cybercrime at
global level, these policies of cybercrime used to explain the importance of harmonization
toward cybercrime at global (Smith and Ingram, 2017). As it has been identified that. These
policies also used to define crucial responsibility of different stakeholder are clearly defined.
There are certain guidelines of using same also in the nation. Some of the guidelines are as
follows:
All the Countries should aim to bring or establish necessary interpretations in context
of key terms of cybercrime.
All the nation at global level shall develop substantive criminal law so that
cybercrime can be effectively manage in the nation.
Different Countries should look developing effective but balanced procedural
instruments which generally help the company in managing different authorities to
investigate cybercrime but protect the rights of the suspect.
There are many different authority and mechanism in the nation which are develop by
different treaties which generally used to help them in understand and monitor different
activity which used to come under mechanism of Surveillance against International
cybercrime in the nation. This surveillance used to play a very crucial role in understanding
different institute the real reason and location from which the issue like cybercrime is taking
place in the nation. This surveillance is formed by the contribution of different treaties and
university. In the year 2015 it was indentified by the international commission that their are
many loop pole in the surveillance of cybercrime. As a result company has decided to make
variety of the changes in the surveillance. So that commission with the help of the same can
understand the impact of different cybercrime very easily. Also, institute is able to track the
different cybercrime issue very easily in the market.
Preliminary ideas to improve governance and responses
After going through the different policy, law which used to govern the responses toward
cybercrime in the market, it has been analysed that these policy are helping the different
nation in reducing the amount of cyber security at global level. At the same time it has been
policies are not limited to legislation. Some of the policy are as follows:
ICB4PAC896 Draft Model Policy for Cybercrime and HIPCAR Model Policy on Cybercrime
Are two main policies at the global level that used to govern the policy of cybercrime at
global level, these policies of cybercrime used to explain the importance of harmonization
toward cybercrime at global (Smith and Ingram, 2017). As it has been identified that. These
policies also used to define crucial responsibility of different stakeholder are clearly defined.
There are certain guidelines of using same also in the nation. Some of the guidelines are as
follows:
All the Countries should aim to bring or establish necessary interpretations in context
of key terms of cybercrime.
All the nation at global level shall develop substantive criminal law so that
cybercrime can be effectively manage in the nation.
Different Countries should look developing effective but balanced procedural
instruments which generally help the company in managing different authorities to
investigate cybercrime but protect the rights of the suspect.
There are many different authority and mechanism in the nation which are develop by
different treaties which generally used to help them in understand and monitor different
activity which used to come under mechanism of Surveillance against International
cybercrime in the nation. This surveillance used to play a very crucial role in understanding
different institute the real reason and location from which the issue like cybercrime is taking
place in the nation. This surveillance is formed by the contribution of different treaties and
university. In the year 2015 it was indentified by the international commission that their are
many loop pole in the surveillance of cybercrime. As a result company has decided to make
variety of the changes in the surveillance. So that commission with the help of the same can
understand the impact of different cybercrime very easily. Also, institute is able to track the
different cybercrime issue very easily in the market.
Preliminary ideas to improve governance and responses
After going through the different policy, law which used to govern the responses toward
cybercrime in the market, it has been analysed that these policy are helping the different
nation in reducing the amount of cyber security at global level. At the same time it has been
also analysed that it is very easy for different institute in grapping the different cybercrime
which is occurring at the waste or wider level but cybercrime which is taking place at small
level it get difficult to examine. This eventually used t impact the performance of the
organization in long run. So it has been recommended to all the organization that they have to
make different policy in all the different nation to catch the cyber security which is taking
place at the small level in all the nation. This will eventually help the all the nation to provide
different support to cyber security, as it has been identified that this small cyber security in
the nation only used to provide the crucial support to the hacker who used to plan the cyber
security at wider level at global level (Warren and Leitch, 2018).
Another recommendation is that all the organization at domestic level should be taught about
different cyber security and also need to explain the different measure through which it can
be reduced (Harkin,Whelan and Chang, 2018)
.
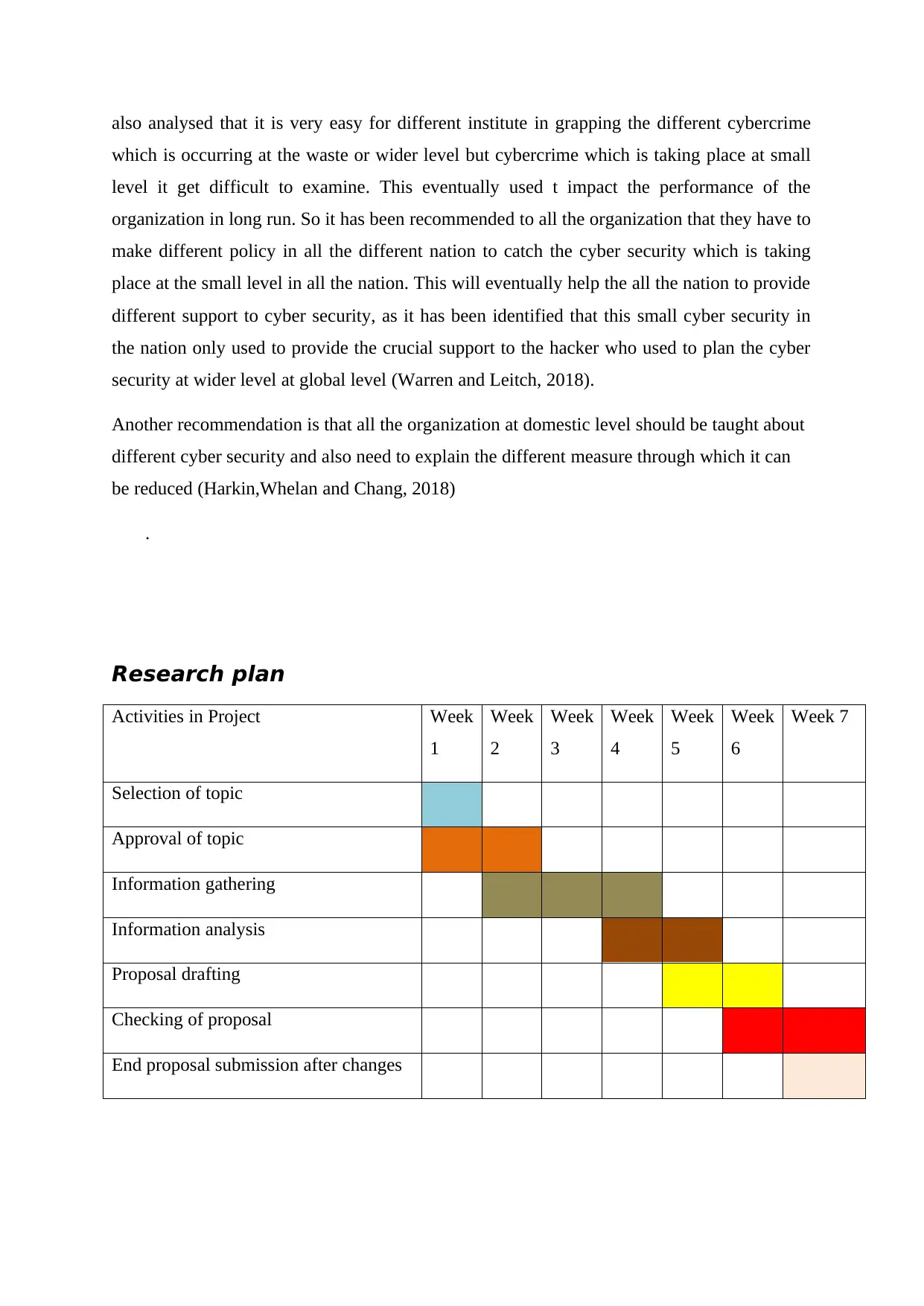
Research plan
Activities in Project Week
1
Week
2
Week
3
Week
4
Week
5
Week
6
Week 7
Selection of topic
Approval of topic
Information gathering
Information analysis
Proposal drafting
Checking of proposal
End proposal submission after changes
which is occurring at the waste or wider level but cybercrime which is taking place at small
level it get difficult to examine. This eventually used t impact the performance of the
organization in long run. So it has been recommended to all the organization that they have to
make different policy in all the different nation to catch the cyber security which is taking
place at the small level in all the nation. This will eventually help the all the nation to provide
different support to cyber security, as it has been identified that this small cyber security in
the nation only used to provide the crucial support to the hacker who used to plan the cyber
security at wider level at global level (Warren and Leitch, 2018).
Another recommendation is that all the organization at domestic level should be taught about
different cyber security and also need to explain the different measure through which it can
be reduced (Harkin,Whelan and Chang, 2018)
.
Research plan
Activities in Project Week
1
Week
2
Week
3
Week
4
Week
5
Week
6
Week 7
Selection of topic
Approval of topic
Information gathering
Information analysis
Proposal drafting
Checking of proposal
End proposal submission after changes
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CONCLUSION
From the above study, the report concludes the matters relating to examining the
impact of cybercrime in the country and also it’s crucially impact globally. The main problem
which is designed under this research is relating to the types of cybercrime such as theft,
fraud, misrepresenting any information and many more. The government laws are also
designed regarding Cybercrime act, 2001, Privacy act, 1988 and Computer misuse Act, 1990
which secures the right of the person regarding sharing any important information with
anyone. It is also examined regarding adapting various polices and surveillances in respect of
managing the crime and providing justice to affected parties. It is also studied that different
ideas are adapted such as high coded security, personal interaction, appointing expertise
person to resolve the illegal matters easily.
REFERENCES
Books and Journals
Broadhurst, R., 2017. Cybercrime in Australia. In The Palgrave Handbook of Australian and
New Zealand Criminology, Crime and Justice. (pp. 221-235). Palgrave Macmillan,
Cham.
Cross, C., 2019. Reflections on the reporting of fraud in Australia. Policing: An International
Journal.
Dupont, B., 2018. Mapping the International Governance of Cybercrime. Governing Cyber
Security in Canada, Australia and the United States. 38. p.23.
Farrell, G. and Birks, D., 2018. Did cybercrime cause the crime drop?. Crime science. 7(1).
pp.1-4.
From the above study, the report concludes the matters relating to examining the
impact of cybercrime in the country and also it’s crucially impact globally. The main problem
which is designed under this research is relating to the types of cybercrime such as theft,
fraud, misrepresenting any information and many more. The government laws are also
designed regarding Cybercrime act, 2001, Privacy act, 1988 and Computer misuse Act, 1990
which secures the right of the person regarding sharing any important information with
anyone. It is also examined regarding adapting various polices and surveillances in respect of
managing the crime and providing justice to affected parties. It is also studied that different
ideas are adapted such as high coded security, personal interaction, appointing expertise
person to resolve the illegal matters easily.
REFERENCES
Books and Journals
Broadhurst, R., 2017. Cybercrime in Australia. In The Palgrave Handbook of Australian and
New Zealand Criminology, Crime and Justice. (pp. 221-235). Palgrave Macmillan,
Cham.
Cross, C., 2019. Reflections on the reporting of fraud in Australia. Policing: An International
Journal.
Dupont, B., 2018. Mapping the International Governance of Cybercrime. Governing Cyber
Security in Canada, Australia and the United States. 38. p.23.
Farrell, G. and Birks, D., 2018. Did cybercrime cause the crime drop?. Crime science. 7(1).
pp.1-4.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Feakin, T., Nevill, L. and Hawkins, Z., 2017. The Australia-US Cyber Security Dialogue.
Australian Strategic Policy Institute.
Fukushima, T., 2020. Common Enemies: Crime, Policy, and Politics in Australia–Indonesia
Relations.
Hanson, F., 2018. Preventing another Australia Card fail.
Harkin, D., Whelan, C. and Chang, L., 2018. The challenges facing specialist police cyber-
crime units: an empirical analysis. Police Practice and Research. 19(6). pp.519-536.
Maras, M. H., 2019. 47 Cybercrime Laws and Investigations. International and
Transnational Crime and Justice. p.281.
Ng, J., 2016. International cybercrime, transnational evidence gathering and the challenges in
Australia: finding the delicate balance. International Journal of Information and
Communication Technology. 9(2). pp.177-198.
Sarre, R., Lau, L. Y. C. and Chang, L. Y., 2018. Responding to cybercrime: current trends.
Slocombe, G., 2017. Australian government-initiated cyber security projects. Asia-Pacific
Defence Reporter (2002). 43(9). p.40.
Smith, F. and Ingram, G., 2017. Organising cyber security in Australia and
beyond. Australian Journal of International Affairs. 71(6). pp.642-660.
Warren, M. and Leitch, S., 2018, June. Australian Cyber Security Policy Through a European
Lens. In European Conference on Cyber Warfare and Security. (pp. 489-XVI).
Academic Conferences International Limited.
)
Australian Strategic Policy Institute.
Fukushima, T., 2020. Common Enemies: Crime, Policy, and Politics in Australia–Indonesia
Relations.
Hanson, F., 2018. Preventing another Australia Card fail.
Harkin, D., Whelan, C. and Chang, L., 2018. The challenges facing specialist police cyber-
crime units: an empirical analysis. Police Practice and Research. 19(6). pp.519-536.
Maras, M. H., 2019. 47 Cybercrime Laws and Investigations. International and
Transnational Crime and Justice. p.281.
Ng, J., 2016. International cybercrime, transnational evidence gathering and the challenges in
Australia: finding the delicate balance. International Journal of Information and
Communication Technology. 9(2). pp.177-198.
Sarre, R., Lau, L. Y. C. and Chang, L. Y., 2018. Responding to cybercrime: current trends.
Slocombe, G., 2017. Australian government-initiated cyber security projects. Asia-Pacific
Defence Reporter (2002). 43(9). p.40.
Smith, F. and Ingram, G., 2017. Organising cyber security in Australia and
beyond. Australian Journal of International Affairs. 71(6). pp.642-660.
Warren, M. and Leitch, S., 2018, June. Australian Cyber Security Policy Through a European
Lens. In European Conference on Cyber Warfare and Security. (pp. 489-XVI).
Academic Conferences International Limited.
)
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





