Quantitative Analysis of Cybercrime Impact on Delta Insurance Security
VerifiedAdded on 2020/03/16
|13
|3159
|32
Report
AI Summary
This report presents a quantitative analysis of cybercrime's impact on Delta Insurance, focusing on the company's security measures, the risks associated with cyber-attacks, and the effectiveness of their IT security infrastructure. The research methodology includes questionnaires administered to the IT department to gather primary data. Key findings reveal that the majority of respondents are confident in the strength of their security systems, though BYOD use poses a significant security threat. The report highlights Delta Insurance's commitment to IT security, its investment in security measures, and its proactive approach to addressing cyber threats through internal strategies and external partnerships. The discussion section emphasizes the importance of robust security systems, employee training, and strict BYOD policies to mitigate risks and protect customer data. The report concludes by underscoring the need for continuous adaptation to evolving cyber threats and the importance of a comprehensive security strategy.

1
Course:
Professor:
Institution:
Date:
Course:
Professor:
Institution:
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Research design and Methodology
In this section, the research procedure will be outlined which specifies the research
methods to be used in the study. In this research, most of the data will be quantitative. It implies
that the quantitative data will help in ascertaining exact impact of cybercrimes on businesses in
Bangladesh. The main focus in this research is Delta Insurance Company. The data obtained
from the research will help in assessing the level of risk associated with cyber-attacks and their
impact on business operations (Panneerselvam, 2014). The study will employ a number of
statistical analysis to give a better understanding of the cybercrimes committed and their effects
on the performance of businesses.
Design
In this research, the main data collection method is through questionnaire to gather
primary data. The data will be mainly focused on our company, Delta Insurance Company. The
question will have various sections with questions which require the respondent to key in their
responses as instructed (Silverman, 2016). It is through the questionnaire that we will understand
the setup of the business and how it is dealing with major cybercrimes threats which have cost
companies in the financial sector millions of money (Gast and Ledford, 2014). In this study, a
total of 30 questionnaires will be supplied to the staff of the firm. The reason for using the
sample of 30 respondents is due to the fact that the targeted group in the research come from the
IT department who are less in number. Most of the questionnaires will be given to the IT
department for the firm (Wang and Park, 2017). All the data captured in the questionnaires will
be entered into an excel sheet. Also, al the responses in the excel sheet will be checked to
ascertain their accuracy (Papajorgji, 2015). The data will then be exported to spss software for
detailed analysis.
Research findings
Security of Delta systems
The data was analyzed and the results obtained from the software. When the clients were asked
about their security systems, whether they were strong enough to protect the firm’s data all year
round, their responses were positive (Barrett and Nunn-Price, 2016). An average of 93% of the
respondents were confident that the systems they had were in a position to protect all the data for
the firm and secure it from hacking and such criminal acts.
Research design and Methodology
In this section, the research procedure will be outlined which specifies the research
methods to be used in the study. In this research, most of the data will be quantitative. It implies
that the quantitative data will help in ascertaining exact impact of cybercrimes on businesses in
Bangladesh. The main focus in this research is Delta Insurance Company. The data obtained
from the research will help in assessing the level of risk associated with cyber-attacks and their
impact on business operations (Panneerselvam, 2014). The study will employ a number of
statistical analysis to give a better understanding of the cybercrimes committed and their effects
on the performance of businesses.
Design
In this research, the main data collection method is through questionnaire to gather
primary data. The data will be mainly focused on our company, Delta Insurance Company. The
question will have various sections with questions which require the respondent to key in their
responses as instructed (Silverman, 2016). It is through the questionnaire that we will understand
the setup of the business and how it is dealing with major cybercrimes threats which have cost
companies in the financial sector millions of money (Gast and Ledford, 2014). In this study, a
total of 30 questionnaires will be supplied to the staff of the firm. The reason for using the
sample of 30 respondents is due to the fact that the targeted group in the research come from the
IT department who are less in number. Most of the questionnaires will be given to the IT
department for the firm (Wang and Park, 2017). All the data captured in the questionnaires will
be entered into an excel sheet. Also, al the responses in the excel sheet will be checked to
ascertain their accuracy (Papajorgji, 2015). The data will then be exported to spss software for
detailed analysis.
Research findings
Security of Delta systems
The data was analyzed and the results obtained from the software. When the clients were asked
about their security systems, whether they were strong enough to protect the firm’s data all year
round, their responses were positive (Barrett and Nunn-Price, 2016). An average of 93% of the
respondents were confident that the systems they had were in a position to protect all the data for
the firm and secure it from hacking and such criminal acts.
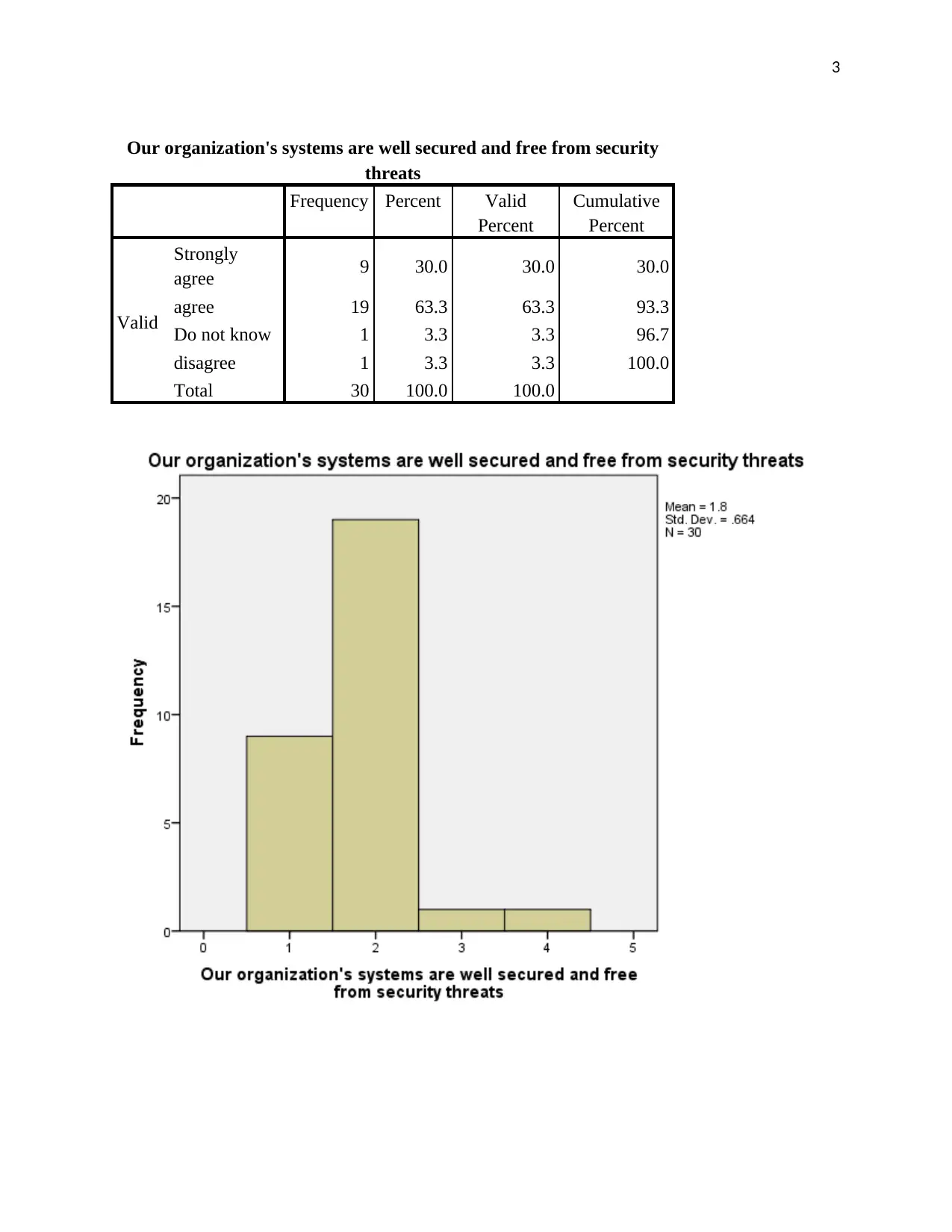
3
Our organization's systems are well secured and free from security
threats
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 9 30.0 30.0 30.0
agree 19 63.3 63.3 93.3
Do not know 1 3.3 3.3 96.7
disagree 1 3.3 3.3 100.0
Total 30 100.0 100.0
Our organization's systems are well secured and free from security
threats
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 9 30.0 30.0 30.0
agree 19 63.3 63.3 93.3
Do not know 1 3.3 3.3 96.7
disagree 1 3.3 3.3 100.0
Total 30 100.0 100.0
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
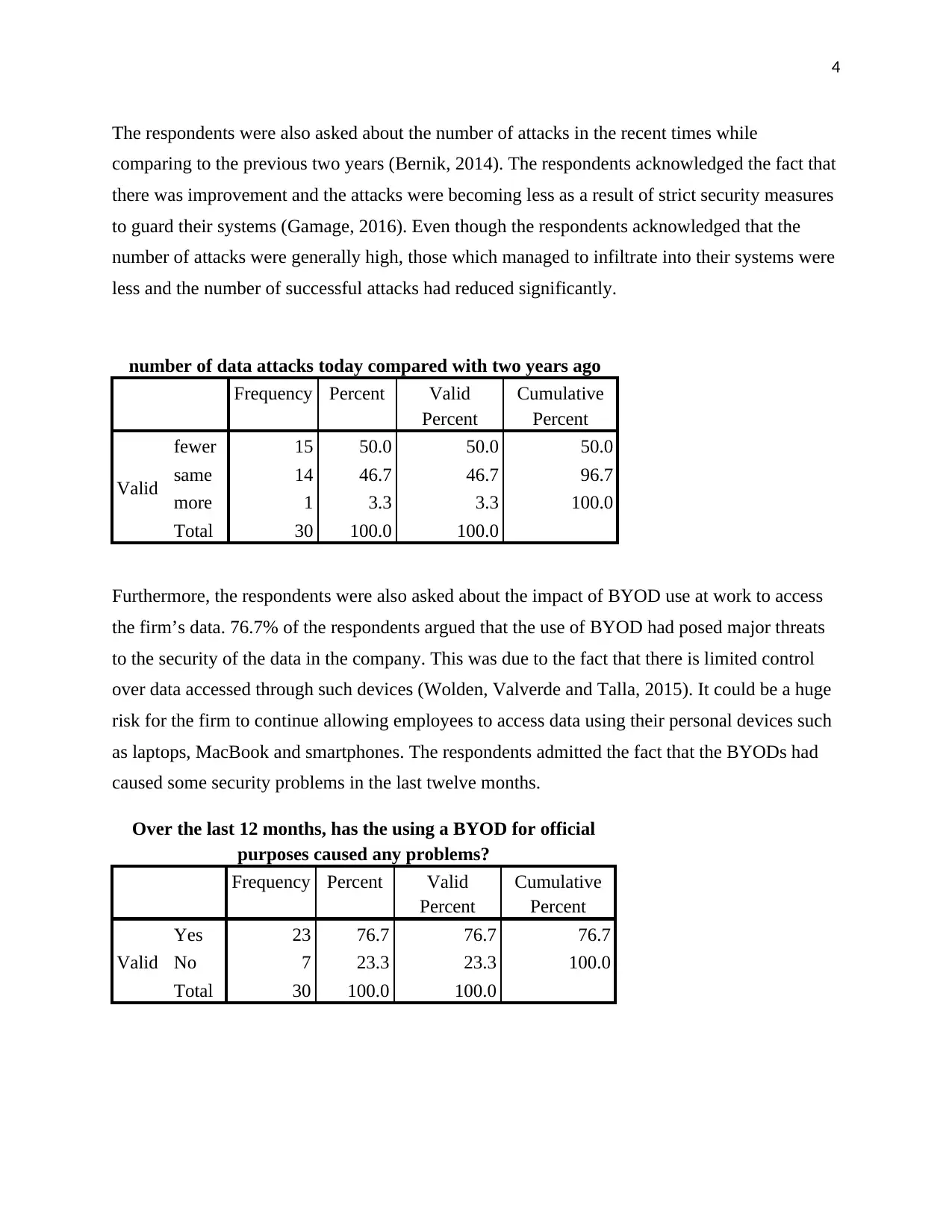
The respondents were also asked about the number of attacks in the recent times while
comparing to the previous two years (Bernik, 2014). The respondents acknowledged the fact that
there was improvement and the attacks were becoming less as a result of strict security measures
to guard their systems (Gamage, 2016). Even though the respondents acknowledged that the
number of attacks were generally high, those which managed to infiltrate into their systems were
less and the number of successful attacks had reduced significantly.
number of data attacks today compared with two years ago
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
fewer 15 50.0 50.0 50.0
same 14 46.7 46.7 96.7
more 1 3.3 3.3 100.0
Total 30 100.0 100.0
Furthermore, the respondents were also asked about the impact of BYOD use at work to access
the firm’s data. 76.7% of the respondents argued that the use of BYOD had posed major threats
to the security of the data in the company. This was due to the fact that there is limited control
over data accessed through such devices (Wolden, Valverde and Talla, 2015). It could be a huge
risk for the firm to continue allowing employees to access data using their personal devices such
as laptops, MacBook and smartphones. The respondents admitted the fact that the BYODs had
caused some security problems in the last twelve months.
Over the last 12 months, has the using a BYOD for official
purposes caused any problems?
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Yes 23 76.7 76.7 76.7
No 7 23.3 23.3 100.0
Total 30 100.0 100.0
The respondents were also asked about the number of attacks in the recent times while
comparing to the previous two years (Bernik, 2014). The respondents acknowledged the fact that
there was improvement and the attacks were becoming less as a result of strict security measures
to guard their systems (Gamage, 2016). Even though the respondents acknowledged that the
number of attacks were generally high, those which managed to infiltrate into their systems were
less and the number of successful attacks had reduced significantly.
number of data attacks today compared with two years ago
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
fewer 15 50.0 50.0 50.0
same 14 46.7 46.7 96.7
more 1 3.3 3.3 100.0
Total 30 100.0 100.0
Furthermore, the respondents were also asked about the impact of BYOD use at work to access
the firm’s data. 76.7% of the respondents argued that the use of BYOD had posed major threats
to the security of the data in the company. This was due to the fact that there is limited control
over data accessed through such devices (Wolden, Valverde and Talla, 2015). It could be a huge
risk for the firm to continue allowing employees to access data using their personal devices such
as laptops, MacBook and smartphones. The respondents admitted the fact that the BYODs had
caused some security problems in the last twelve months.
Over the last 12 months, has the using a BYOD for official
purposes caused any problems?
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Yes 23 76.7 76.7 76.7
No 7 23.3 23.3 100.0
Total 30 100.0 100.0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
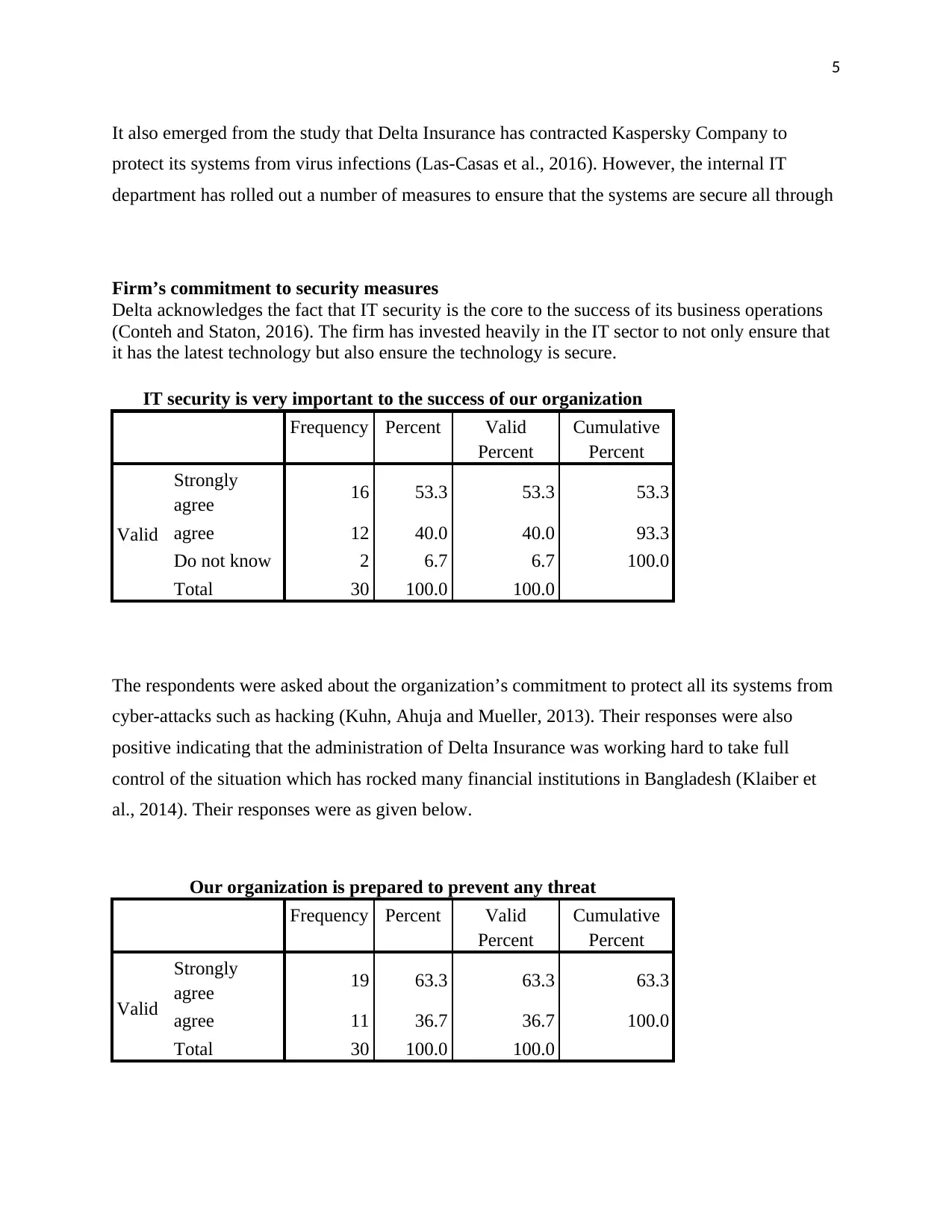
It also emerged from the study that Delta Insurance has contracted Kaspersky Company to
protect its systems from virus infections (Las-Casas et al., 2016). However, the internal IT
department has rolled out a number of measures to ensure that the systems are secure all through
Firm’s commitment to security measures
Delta acknowledges the fact that IT security is the core to the success of its business operations
(Conteh and Staton, 2016). The firm has invested heavily in the IT sector to not only ensure that
it has the latest technology but also ensure the technology is secure.
IT security is very important to the success of our organization
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 16 53.3 53.3 53.3
agree 12 40.0 40.0 93.3
Do not know 2 6.7 6.7 100.0
Total 30 100.0 100.0
The respondents were asked about the organization’s commitment to protect all its systems from
cyber-attacks such as hacking (Kuhn, Ahuja and Mueller, 2013). Their responses were also
positive indicating that the administration of Delta Insurance was working hard to take full
control of the situation which has rocked many financial institutions in Bangladesh (Klaiber et
al., 2014). Their responses were as given below.
Our organization is prepared to prevent any threat
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 19 63.3 63.3 63.3
agree 11 36.7 36.7 100.0
Total 30 100.0 100.0
It also emerged from the study that Delta Insurance has contracted Kaspersky Company to
protect its systems from virus infections (Las-Casas et al., 2016). However, the internal IT
department has rolled out a number of measures to ensure that the systems are secure all through
Firm’s commitment to security measures
Delta acknowledges the fact that IT security is the core to the success of its business operations
(Conteh and Staton, 2016). The firm has invested heavily in the IT sector to not only ensure that
it has the latest technology but also ensure the technology is secure.
IT security is very important to the success of our organization
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 16 53.3 53.3 53.3
agree 12 40.0 40.0 93.3
Do not know 2 6.7 6.7 100.0
Total 30 100.0 100.0
The respondents were asked about the organization’s commitment to protect all its systems from
cyber-attacks such as hacking (Kuhn, Ahuja and Mueller, 2013). Their responses were also
positive indicating that the administration of Delta Insurance was working hard to take full
control of the situation which has rocked many financial institutions in Bangladesh (Klaiber et
al., 2014). Their responses were as given below.
Our organization is prepared to prevent any threat
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 19 63.3 63.3 63.3
agree 11 36.7 36.7 100.0
Total 30 100.0 100.0
6
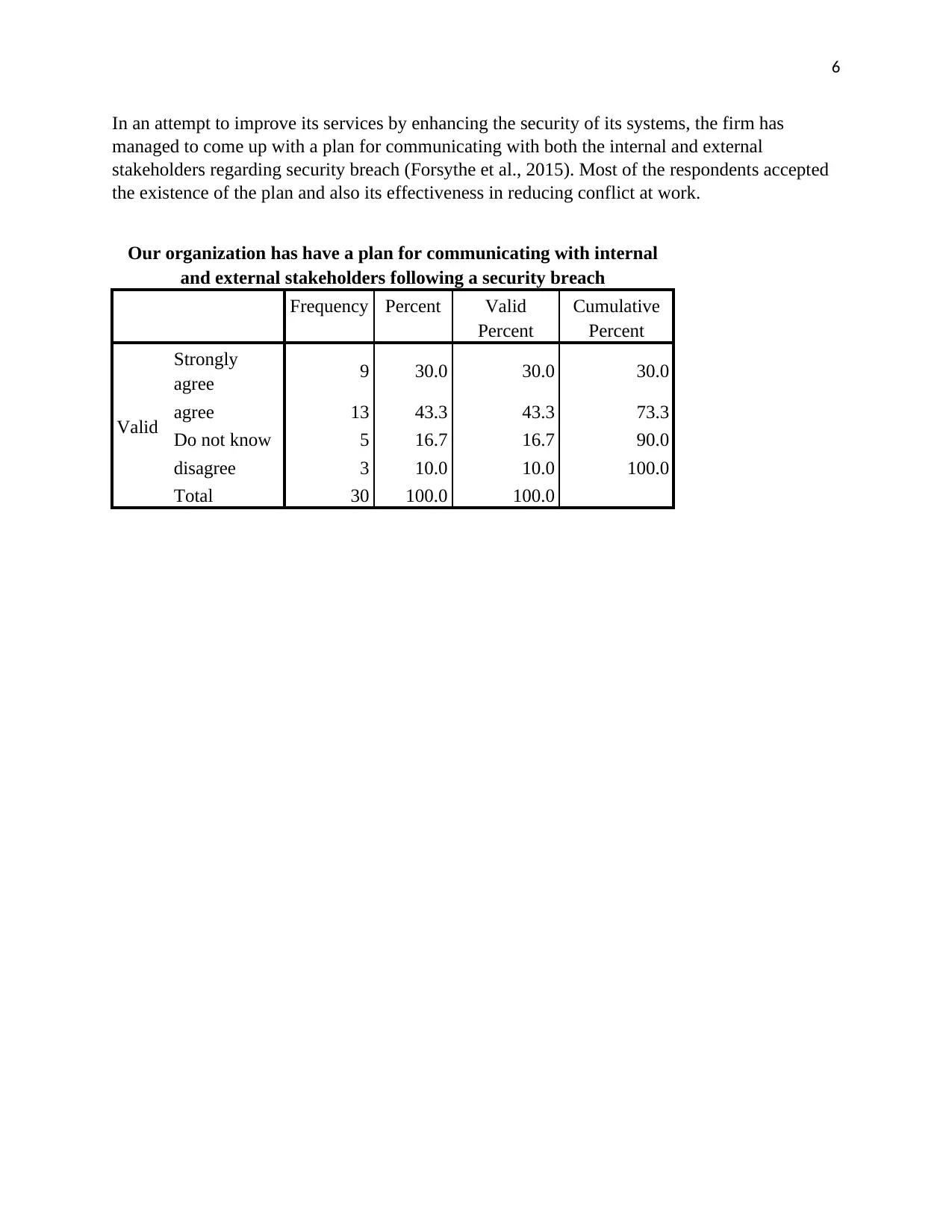
In an attempt to improve its services by enhancing the security of its systems, the firm has
managed to come up with a plan for communicating with both the internal and external
stakeholders regarding security breach (Forsythe et al., 2015). Most of the respondents accepted
the existence of the plan and also its effectiveness in reducing conflict at work.
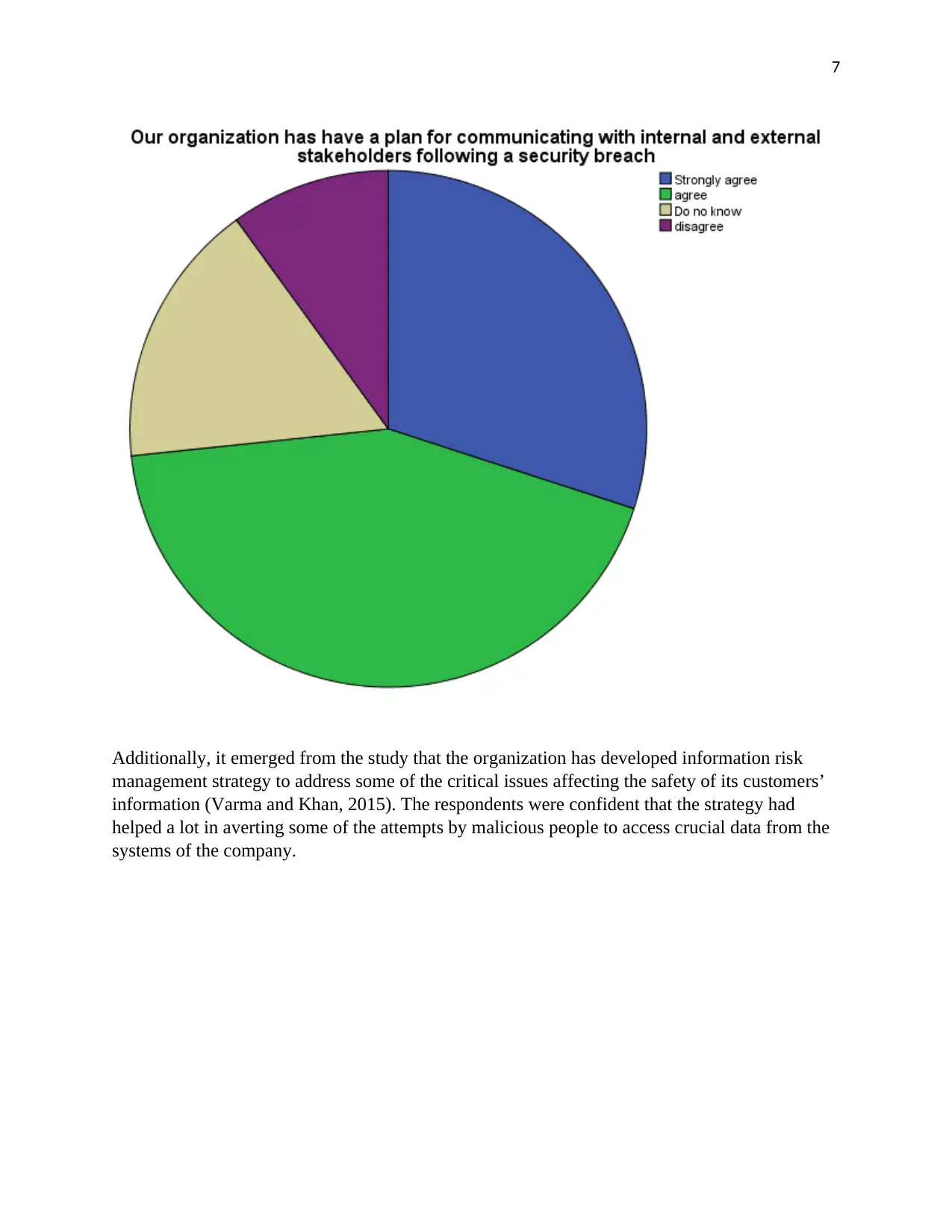
Our organization has have a plan for communicating with internal
and external stakeholders following a security breach
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 9 30.0 30.0 30.0
agree 13 43.3 43.3 73.3
Do not know 5 16.7 16.7 90.0
disagree 3 10.0 10.0 100.0
Total 30 100.0 100.0
In an attempt to improve its services by enhancing the security of its systems, the firm has
managed to come up with a plan for communicating with both the internal and external
stakeholders regarding security breach (Forsythe et al., 2015). Most of the respondents accepted
the existence of the plan and also its effectiveness in reducing conflict at work.
Our organization has have a plan for communicating with internal
and external stakeholders following a security breach
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 9 30.0 30.0 30.0
agree 13 43.3 43.3 73.3
Do not know 5 16.7 16.7 90.0
disagree 3 10.0 10.0 100.0
Total 30 100.0 100.0
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
Additionally, it emerged from the study that the organization has developed information risk
management strategy to address some of the critical issues affecting the safety of its customers’
information (Varma and Khan, 2015). The respondents were confident that the strategy had
helped a lot in averting some of the attempts by malicious people to access crucial data from the
systems of the company.
Additionally, it emerged from the study that the organization has developed information risk
management strategy to address some of the critical issues affecting the safety of its customers’
information (Varma and Khan, 2015). The respondents were confident that the strategy had
helped a lot in averting some of the attempts by malicious people to access crucial data from the
systems of the company.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8
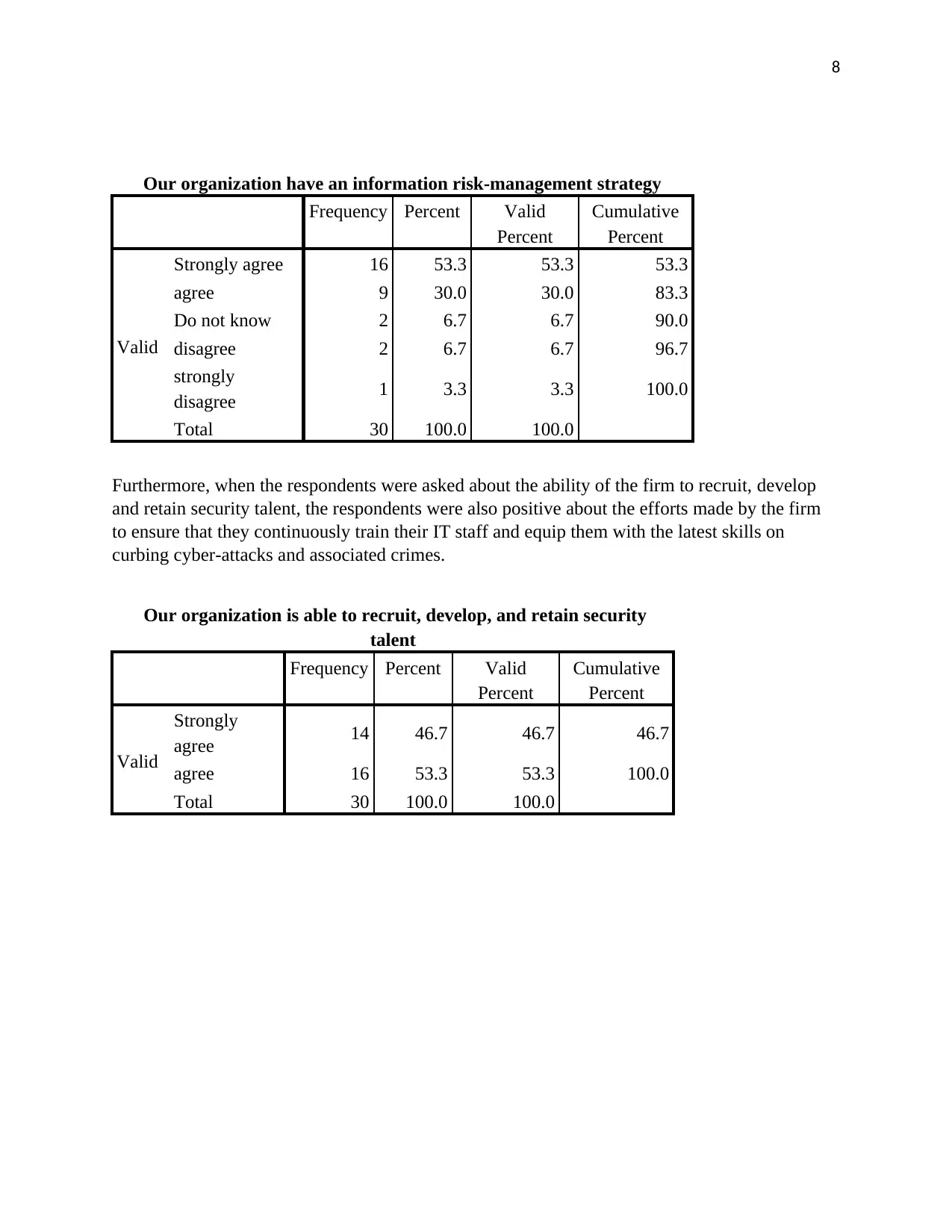
Our organization have an information risk-management strategy
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly agree 16 53.3 53.3 53.3
agree 9 30.0 30.0 83.3
Do not know 2 6.7 6.7 90.0
disagree 2 6.7 6.7 96.7
strongly
disagree 1 3.3 3.3 100.0
Total 30 100.0 100.0
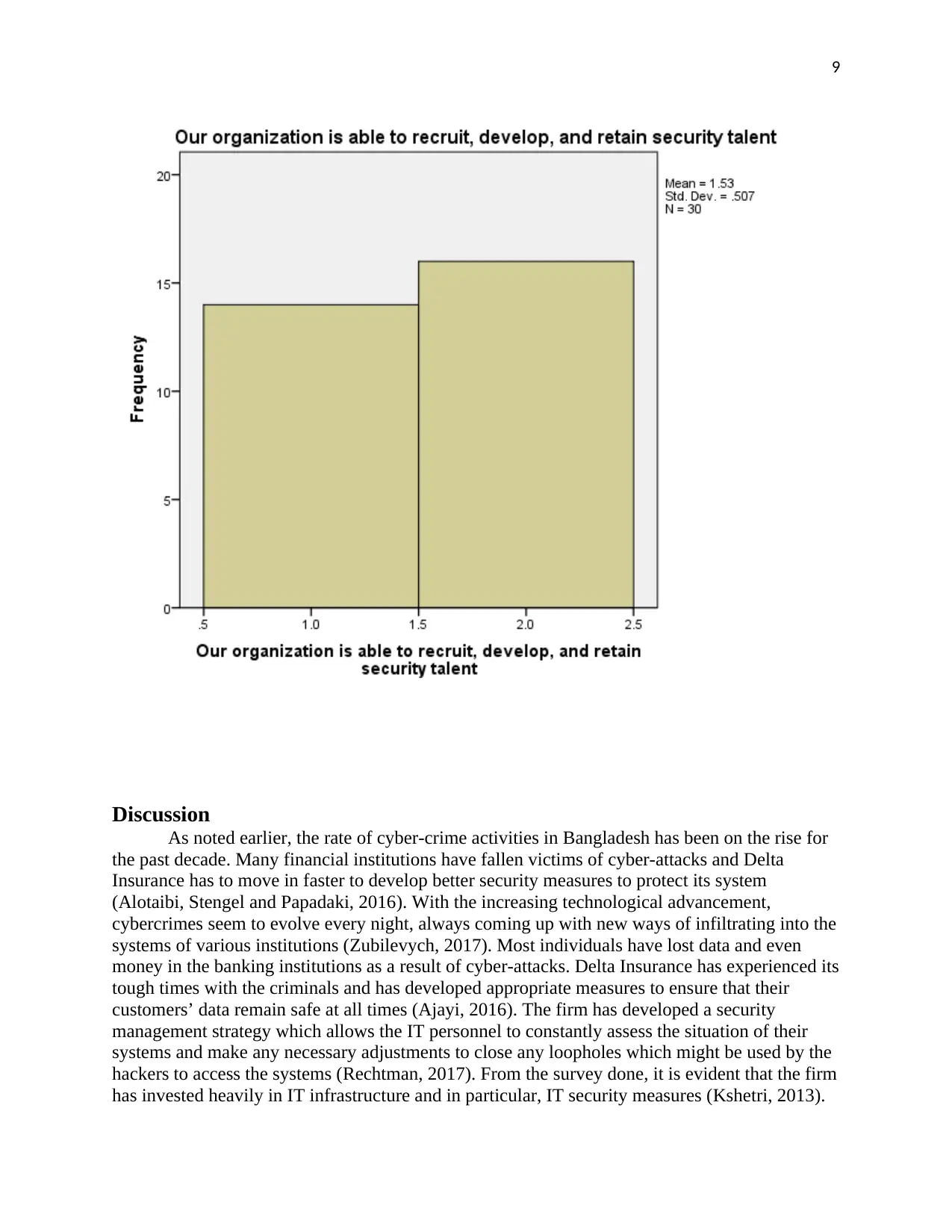
Furthermore, when the respondents were asked about the ability of the firm to recruit, develop
and retain security talent, the respondents were also positive about the efforts made by the firm
to ensure that they continuously train their IT staff and equip them with the latest skills on
curbing cyber-attacks and associated crimes.
Our organization is able to recruit, develop, and retain security
talent
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 14 46.7 46.7 46.7
agree 16 53.3 53.3 100.0
Total 30 100.0 100.0
Our organization have an information risk-management strategy
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly agree 16 53.3 53.3 53.3
agree 9 30.0 30.0 83.3
Do not know 2 6.7 6.7 90.0
disagree 2 6.7 6.7 96.7
strongly
disagree 1 3.3 3.3 100.0
Total 30 100.0 100.0
Furthermore, when the respondents were asked about the ability of the firm to recruit, develop
and retain security talent, the respondents were also positive about the efforts made by the firm
to ensure that they continuously train their IT staff and equip them with the latest skills on
curbing cyber-attacks and associated crimes.
Our organization is able to recruit, develop, and retain security
talent
Frequency Percent Valid
Percent
Cumulative
Percent
Valid
Strongly
agree 14 46.7 46.7 46.7
agree 16 53.3 53.3 100.0
Total 30 100.0 100.0
9
Discussion
As noted earlier, the rate of cyber-crime activities in Bangladesh has been on the rise for
the past decade. Many financial institutions have fallen victims of cyber-attacks and Delta
Insurance has to move in faster to develop better security measures to protect its system
(Alotaibi, Stengel and Papadaki, 2016). With the increasing technological advancement,
cybercrimes seem to evolve every night, always coming up with new ways of infiltrating into the
systems of various institutions (Zubilevych, 2017). Most individuals have lost data and even
money in the banking institutions as a result of cyber-attacks. Delta Insurance has experienced its
tough times with the criminals and has developed appropriate measures to ensure that their
customers’ data remain safe at all times (Ajayi, 2016). The firm has developed a security
management strategy which allows the IT personnel to constantly assess the situation of their
systems and make any necessary adjustments to close any loopholes which might be used by the
hackers to access the systems (Rechtman, 2017). From the survey done, it is evident that the firm
has invested heavily in IT infrastructure and in particular, IT security measures (Kshetri, 2013).
Discussion
As noted earlier, the rate of cyber-crime activities in Bangladesh has been on the rise for
the past decade. Many financial institutions have fallen victims of cyber-attacks and Delta
Insurance has to move in faster to develop better security measures to protect its system
(Alotaibi, Stengel and Papadaki, 2016). With the increasing technological advancement,
cybercrimes seem to evolve every night, always coming up with new ways of infiltrating into the
systems of various institutions (Zubilevych, 2017). Most individuals have lost data and even
money in the banking institutions as a result of cyber-attacks. Delta Insurance has experienced its
tough times with the criminals and has developed appropriate measures to ensure that their
customers’ data remain safe at all times (Ajayi, 2016). The firm has developed a security
management strategy which allows the IT personnel to constantly assess the situation of their
systems and make any necessary adjustments to close any loopholes which might be used by the
hackers to access the systems (Rechtman, 2017). From the survey done, it is evident that the firm
has invested heavily in IT infrastructure and in particular, IT security measures (Kshetri, 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
The firm has employed highly skilled IT staff to deal with all the issues associated with security
concerns (Alkhateeb, 2016). The firm does not take chances in any way, leaving no stone
unturned, it has managed to install one of the strongest IT security to protect the data of its many
customers.
It is also evident that the firm is fully committed to secure its systems completely. With
all the security measures put forth, it becomes very difficult for the hackers to gain access to their
systems (Cheah, 2015). For a strong security system, any firm must be willing to spend more
funds to secure such systems which come with a high price. The more expensive the security
system is, the more it can handle various security concerns (Antonescu and Birău, 2015). With
very powerful systems, the firm can rest assured that none of the hackers can access their data.
Poor security systems will damage the image of the company and it may lose customers (Okanga
and Drotski, 2016). Additionally, a firm can be sued by a client in the event that their data is lost
and the firm can neither explain the situation nor retrieve the data (Broadhurst, 2016). As a result
of these, firms might fight numerous court battles with their clients thus damaging the image of
the company.
One feature emerging from the survey is that most of the employees are confident and
happy about the measures the company has put to reduce and eliminate cyber-attacks (Jackson,
2015). When the members of staff are positive about the efforts made by the company to reduce
cyber-attacks, it boost the image of the firm and customers will be willing to invest in the
company (De Bruyn, 2017). The support from staff is very important in securing the security of
the systems. The company has replicated back by training and retaining the IT staff. The move
ensures that all the systems are managed by a few skilled people (Sharma and Tandekar, 2016).
Changing staff more often leads to possible exposure of the systems to major cybercrime risks.
Retaining the staff and subjecting them to regular security trainings enhances their skills and
expertise thus offering maximum protection to the firm’s systems (Kshetri, 2013). The firm must
also roll out strict measures on the use of BYOD as they pose a major threat to the security of the
systems (Taylor, Bogdan and DeVault, 2015). Anything can happen to the devices which
obviously have low security measures. In the event of an occurrence of risk, all data can be lost
(Kraemer-Mbula et al., 2013). There must be strict guidelines to the use of BYOD to ensure that
all the data and the interests of customers are safeguarded.
References
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons.
Silverman, D. ed., 2016. Qualitative research. Sage.
Gast, D.L. and Ledford, J.R. eds., 2014. Single case research methodology: Applications in
special education and behavioral sciences. Routledge.
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Barrett, M. and Nunn-Price, J., 2016. Cyber crimes on the up. Australia's Paydirt, 1(237), p.10.
The firm has employed highly skilled IT staff to deal with all the issues associated with security
concerns (Alkhateeb, 2016). The firm does not take chances in any way, leaving no stone
unturned, it has managed to install one of the strongest IT security to protect the data of its many
customers.
It is also evident that the firm is fully committed to secure its systems completely. With
all the security measures put forth, it becomes very difficult for the hackers to gain access to their
systems (Cheah, 2015). For a strong security system, any firm must be willing to spend more
funds to secure such systems which come with a high price. The more expensive the security
system is, the more it can handle various security concerns (Antonescu and Birău, 2015). With
very powerful systems, the firm can rest assured that none of the hackers can access their data.
Poor security systems will damage the image of the company and it may lose customers (Okanga
and Drotski, 2016). Additionally, a firm can be sued by a client in the event that their data is lost
and the firm can neither explain the situation nor retrieve the data (Broadhurst, 2016). As a result
of these, firms might fight numerous court battles with their clients thus damaging the image of
the company.
One feature emerging from the survey is that most of the employees are confident and
happy about the measures the company has put to reduce and eliminate cyber-attacks (Jackson,
2015). When the members of staff are positive about the efforts made by the company to reduce
cyber-attacks, it boost the image of the firm and customers will be willing to invest in the
company (De Bruyn, 2017). The support from staff is very important in securing the security of
the systems. The company has replicated back by training and retaining the IT staff. The move
ensures that all the systems are managed by a few skilled people (Sharma and Tandekar, 2016).
Changing staff more often leads to possible exposure of the systems to major cybercrime risks.
Retaining the staff and subjecting them to regular security trainings enhances their skills and
expertise thus offering maximum protection to the firm’s systems (Kshetri, 2013). The firm must
also roll out strict measures on the use of BYOD as they pose a major threat to the security of the
systems (Taylor, Bogdan and DeVault, 2015). Anything can happen to the devices which
obviously have low security measures. In the event of an occurrence of risk, all data can be lost
(Kraemer-Mbula et al., 2013). There must be strict guidelines to the use of BYOD to ensure that
all the data and the interests of customers are safeguarded.
References
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons.
Silverman, D. ed., 2016. Qualitative research. Sage.
Gast, D.L. and Ledford, J.R. eds., 2014. Single case research methodology: Applications in
special education and behavioral sciences. Routledge.
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Barrett, M. and Nunn-Price, J., 2016. Cyber crimes on the up. Australia's Paydirt, 1(237), p.10.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
Olayemi, O.J., 2014. A socio-technological analysis of cybercrime and cyber security in Nigeria.
International Journal of Sociology and Anthropology, 6(3), p.116.
Cheah, K.B., 2015. Effects Of Cyber Supply Chain Risk Management On Supply Chain
Performance (Doctoral dissertation, Universiti Sains Malaysia).
Wang, P. and Park, S.A., 2017. COMMUNICATION IN CYBERSECURITY: A PUBLIC
COMMUNICATION MODEL FOR BUSINESS DATA BREACH INCIDENT HANDLING.
Issues in Information Systems, 18(2).
Antonescu, M. and Birău, R., 2015. Financial and Non-financial Implications of Cybercrimes in
Emerging Countries. Procedia Economics and Finance, 32, pp.618-621.
Ajayi, E.F.G., 2016. The impact of cybercrimes on global trade and commerce. Available at
SSRN.
Papajorgji, P. ed., 2015. Automated Enterprise Systems for Maximizing Business Performance.
IGI Global.
Rechtman, Y., 2017. SHIFTING THE RISK OF CYBERCRIME. CPA Journal.
Forsythe, J.C., Hopkins, S., Silva, A.R. and Wilson, A., 2015. Factors Contributing to
Performance for Cyber Security Forensic Analysis (No. SAND2015-0744C). Sandia National
Laboratories (SNL-NM), Albuquerque, NM (United States).
Sharma, A. and Tandekar, P., 2016. Cyber Security and Business Growth. Business Analytics
and Cyber Security Management in Organizations, p.14.
De Bruyn, A.J., 2017. Exploring high performance work processes in effective virtual teams.
African Journal of Economic and Management Studies, (just-accepted), pp.00-00.
Klaiber, U., Hermanus, T. and Mason, R.B., 2014. E-business Developments and Skills
Requirements in the Retail Sector. Wholesale and Retail Leadership Chair, Cape Peninsula
University of Technology.
Zubilevych, A.V., 2017. CYBER SECURITY IN BUSINESS.
Kshetri, N., 2013. Cybercrimes in the Former Soviet Union and Central and Eastern Europe:
current status and key drivers. Crime, law and social change, 60(1), pp.39-65.
Olayemi, O.J., 2014. A socio-technological analysis of cybercrime and cyber security in Nigeria.
International Journal of Sociology and Anthropology, 6(3), p.116.
Cheah, K.B., 2015. Effects Of Cyber Supply Chain Risk Management On Supply Chain
Performance (Doctoral dissertation, Universiti Sains Malaysia).
Wang, P. and Park, S.A., 2017. COMMUNICATION IN CYBERSECURITY: A PUBLIC
COMMUNICATION MODEL FOR BUSINESS DATA BREACH INCIDENT HANDLING.
Issues in Information Systems, 18(2).
Antonescu, M. and Birău, R., 2015. Financial and Non-financial Implications of Cybercrimes in
Emerging Countries. Procedia Economics and Finance, 32, pp.618-621.
Ajayi, E.F.G., 2016. The impact of cybercrimes on global trade and commerce. Available at
SSRN.
Papajorgji, P. ed., 2015. Automated Enterprise Systems for Maximizing Business Performance.
IGI Global.
Rechtman, Y., 2017. SHIFTING THE RISK OF CYBERCRIME. CPA Journal.
Forsythe, J.C., Hopkins, S., Silva, A.R. and Wilson, A., 2015. Factors Contributing to
Performance for Cyber Security Forensic Analysis (No. SAND2015-0744C). Sandia National
Laboratories (SNL-NM), Albuquerque, NM (United States).
Sharma, A. and Tandekar, P., 2016. Cyber Security and Business Growth. Business Analytics
and Cyber Security Management in Organizations, p.14.
De Bruyn, A.J., 2017. Exploring high performance work processes in effective virtual teams.
African Journal of Economic and Management Studies, (just-accepted), pp.00-00.
Klaiber, U., Hermanus, T. and Mason, R.B., 2014. E-business Developments and Skills
Requirements in the Retail Sector. Wholesale and Retail Leadership Chair, Cape Peninsula
University of Technology.
Zubilevych, A.V., 2017. CYBER SECURITY IN BUSINESS.
Kshetri, N., 2013. Cybercrimes in the Former Soviet Union and Central and Eastern Europe:
current status and key drivers. Crime, law and social change, 60(1), pp.39-65.

12
Islam, M. and Stafford, T., 2017. Information Technology (IT) Integration and
Cybersecurity/Security: The Security Savviness of Board of Directors.
Kraemer-Mbula, E., Tang, P. and Rush, H., 2013. The cybercrime ecosystem: Online innovation
in the shadows?. Technological Forecasting and Social Change, 80(3), pp.541-555.
Kuhn Jr, J.R., Ahuja, M. and Mueller, J., 2013. An examination of the relationship of IT control
weakness to company financial performance and health. International Journal of Accounting &
Information Management, 21(3), pp.227-240.
Gamage, P., 2016. Big Data: are accounting educators ready?. Journal of Accounting and
Management Information Systems, 15(3), pp.588-604.
Conteh, N.Y. and Staton, Q., 2016. The Socio-Economic Impact of Identity Thefts and
Cybercrime: Preventive Measures and Solutions. International Journal of Computer Science and
Business Informatics, 15(6).
Okanga, B. and Drotski, A., 2016. Integrated business model for mitigating e-retail information
security risks. Journal of Contemporary Management, 13(1), pp.1364-1393.
Efg, A., 2016. The Impact of Cybercrimes on Global Trade and Commerce. Int'l J. Info. Sec. &
Cybercrime, 5, p.31.
Jackson, D., 2015. Financial crime-driven by opportunity, technology and greed...: business.
Professional Accountant, 2015(23), pp.8-10.
Wolden, M., Valverde, R. and Talla, M., 2015. The effectiveness of COBIT 5 Information
Security Framework for reducing Cyber Attacks on Supply Chain Management System. IFAC-
PapersOnLine, 48(3), pp.1846-1852.
Kshetri, N.B., 2013, January. Cybercrime Firms’ Internationalization Strategy and Processes: A
SAAPS Framework. In Academy of Management Proceedings (Vol. 2013, No. 1, p. 15055).
Academy of Management.
Kshetri, N., 2013. Cybercrime and cybersecurity in the global south. Springer.
Alotaibi, F., Furnell, S., Stengel, I. and Papadaki, M., 2016. A Review of Using Gaming
Technology for Cyber-Security Awareness.
Islam, M. and Stafford, T., 2017. Information Technology (IT) Integration and
Cybersecurity/Security: The Security Savviness of Board of Directors.
Kraemer-Mbula, E., Tang, P. and Rush, H., 2013. The cybercrime ecosystem: Online innovation
in the shadows?. Technological Forecasting and Social Change, 80(3), pp.541-555.
Kuhn Jr, J.R., Ahuja, M. and Mueller, J., 2013. An examination of the relationship of IT control
weakness to company financial performance and health. International Journal of Accounting &
Information Management, 21(3), pp.227-240.
Gamage, P., 2016. Big Data: are accounting educators ready?. Journal of Accounting and
Management Information Systems, 15(3), pp.588-604.
Conteh, N.Y. and Staton, Q., 2016. The Socio-Economic Impact of Identity Thefts and
Cybercrime: Preventive Measures and Solutions. International Journal of Computer Science and
Business Informatics, 15(6).
Okanga, B. and Drotski, A., 2016. Integrated business model for mitigating e-retail information
security risks. Journal of Contemporary Management, 13(1), pp.1364-1393.
Efg, A., 2016. The Impact of Cybercrimes on Global Trade and Commerce. Int'l J. Info. Sec. &
Cybercrime, 5, p.31.
Jackson, D., 2015. Financial crime-driven by opportunity, technology and greed...: business.
Professional Accountant, 2015(23), pp.8-10.
Wolden, M., Valverde, R. and Talla, M., 2015. The effectiveness of COBIT 5 Information
Security Framework for reducing Cyber Attacks on Supply Chain Management System. IFAC-
PapersOnLine, 48(3), pp.1846-1852.
Kshetri, N.B., 2013, January. Cybercrime Firms’ Internationalization Strategy and Processes: A
SAAPS Framework. In Academy of Management Proceedings (Vol. 2013, No. 1, p. 15055).
Academy of Management.
Kshetri, N., 2013. Cybercrime and cybersecurity in the global south. Springer.
Alotaibi, F., Furnell, S., Stengel, I. and Papadaki, M., 2016. A Review of Using Gaming
Technology for Cyber-Security Awareness.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



