BUSN20016: Cybercrime Evaluation for Insecurity in Digital World
VerifiedAdded on 2023/06/11
|20
|4511
|317
Report
AI Summary
This report evaluates the growing problem of cybercrime and its impact on the insecurity of people in the digital world. It begins by outlining the problem statement, research aims, and objectives, followed by a conceptual framework that explores the relationship between cybercrime and digital insecurity. The literature review covers various aspects of cybercrime, including its types, impacts, and protection measures. The report also details the research methodology, including the research approach, data collection procedure, and data analysis techniques. It further includes the study's organization, research schedule, and project budget. The report highlights the importance of securing online data, the risks of sharing personal information, and possible steps to prevent cyber threats, contributing to the academic understanding of cybercrime and its consequences.

Running head: ASSESSMENT 3
Assessment 3
An Evaluation of Cybercrime for Insecurity of People in Digital World
Student’s name:
Name of the university:
Author’s note:
Assessment 3
An Evaluation of Cybercrime for Insecurity of People in Digital World
Student’s name:
Name of the university:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ASSESSMENT 3
Table of Contents
1. Introduction..................................................................................................................................2
1.1 Problem statement.................................................................................................................3
1.2 Research aim and Objectives.................................................................................................4
1.3 Research questions.................................................................................................................4
1.4 Justification and potential output of the research project......................................................4
2. Literature review and conceptual framework..............................................................................5
2.1 Cybercrime and insecurity of people in digital life...............................................................5
2.2 Types of cybercrime in digital world.....................................................................................6
2.3 Impact of cybercrime on people across the world.................................................................7
2.4 Protection against cybercrime and security...........................................................................8
2.5 Conceptual framework...........................................................................................................9
3. Methodology..............................................................................................................................10
3.1 Research approach...............................................................................................................10
3.2 Literature review..................................................................................................................10
3.2 Data collection procedure....................................................................................................10
3.3 Data analysis technique.......................................................................................................11
4. Organisation of the study...........................................................................................................11
5. Research schedule......................................................................................................................12
Table of Contents
1. Introduction..................................................................................................................................2
1.1 Problem statement.................................................................................................................3
1.2 Research aim and Objectives.................................................................................................4
1.3 Research questions.................................................................................................................4
1.4 Justification and potential output of the research project......................................................4
2. Literature review and conceptual framework..............................................................................5
2.1 Cybercrime and insecurity of people in digital life...............................................................5
2.2 Types of cybercrime in digital world.....................................................................................6
2.3 Impact of cybercrime on people across the world.................................................................7
2.4 Protection against cybercrime and security...........................................................................8
2.5 Conceptual framework...........................................................................................................9
3. Methodology..............................................................................................................................10
3.1 Research approach...............................................................................................................10
3.2 Literature review..................................................................................................................10
3.2 Data collection procedure....................................................................................................10
3.3 Data analysis technique.......................................................................................................11
4. Organisation of the study...........................................................................................................11
5. Research schedule......................................................................................................................12

2ASSESSMENT 3
6. Project budget and justification.................................................................................................14
Reference List................................................................................................................................16
6. Project budget and justification.................................................................................................14
Reference List................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ASSESSMENT 3
1. Introduction
Prevalence of cybercrimes is increasing day by day in the digital world and it lacks the
clarification about particular ‘cyber' into these incidents. There is a contrast between numbers of
cybercrimes incidents supposedly occur across the globe and relatively small numbers of
incidents known as the prosecutions. Therefore, this contrast exposes a sharp gap in making out
of the cybercrime and the knowledge of criminology. Today, technology now covers the life of
the people and people cannot think their life without the internet and online media. The spectacle
of technology now permeates the day-to-day life of the people and combines with the fear of
dystopia (Liu, Musen & Chou, 2015). People now store their personal information and data on
their mobile app, online account and computers. Therefore, hackers and criminals are targeting
the computers and online media as the object of the crime through hacking, spamming and
phishing. Crimes spread rapidly and the security of the personal data and information are at stake
for the people. Cybercriminals are using the computer technology in order to access the data and
personal information, banking information, business secret and they are using the internet for the
malicious and exploitative purposes.
The main focus of the project is to evaluate the problem of the cybercrime that leads to
the insecurity of people in digital life. In the first part of the study, the main focus is on the
problem statement, aim and objects of the study. In the second section, the conceptual
framework of the cybercrime and the insecurity of the people is explained through theoretical
framework and hypothesis of the study is developed. In the later section, research methodology
is given to collect the data for the future.
1. Introduction
Prevalence of cybercrimes is increasing day by day in the digital world and it lacks the
clarification about particular ‘cyber' into these incidents. There is a contrast between numbers of
cybercrimes incidents supposedly occur across the globe and relatively small numbers of
incidents known as the prosecutions. Therefore, this contrast exposes a sharp gap in making out
of the cybercrime and the knowledge of criminology. Today, technology now covers the life of
the people and people cannot think their life without the internet and online media. The spectacle
of technology now permeates the day-to-day life of the people and combines with the fear of
dystopia (Liu, Musen & Chou, 2015). People now store their personal information and data on
their mobile app, online account and computers. Therefore, hackers and criminals are targeting
the computers and online media as the object of the crime through hacking, spamming and
phishing. Crimes spread rapidly and the security of the personal data and information are at stake
for the people. Cybercriminals are using the computer technology in order to access the data and
personal information, banking information, business secret and they are using the internet for the
malicious and exploitative purposes.
The main focus of the project is to evaluate the problem of the cybercrime that leads to
the insecurity of people in digital life. In the first part of the study, the main focus is on the
problem statement, aim and objects of the study. In the second section, the conceptual
framework of the cybercrime and the insecurity of the people is explained through theoretical
framework and hypothesis of the study is developed. In the later section, research methodology
is given to collect the data for the future.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ASSESSMENT 3
1.1 Problem statement
People nowadays cannot think their lives without stepping into the digital world. The
virtual world always attracts the young and inquisitive minds. People have multiple accounts on
social networking sites and individuals use multiple wallets to paying the bills. Today, there are
almost 200 billion internet-connected devices and people cannot imagine spending their lives
without the possibilities and opportunities that the digital life brings to them (Lee, Kim & Kim,
2015). Organisations and global citizens are becoming vulnerable towards the cyber threats.
Cyber attacks are common in today's life as destructive cyber attacks steal the personal
information and the cybercriminals peep into the common people's internet activities (Sen &
Borle, 2017). Media’s interest towards the cyber attacks has increased in recent years and
volume of cyber attacks and complexity has been increased in recent time. The impact of
digitalisation is clear on the wrong move when the personal data of the users are leaked and
government agencies have defiantly discovered the value of the internet for espionage and
internet of cyber warfare (Martin, Borah & Palmatier, 2017). Cybercrime damages the costs of
that hit the figure of $4 trillion in 2017 and this figure represented that transfer of money and the
information is not secured through online.
This paper will centre on the insecurity of the internet and data in this digital age due to
the increasing popularity of the money sharing wallet and social networking sites. Internet users
share a large amount of personal information online. A recent example of Facebook and
Cambridge Analytica is real life case study where it is clear Facebook holds millions of people's
personal information. Corporations and the software builders are trying to spend to exceed $1
trillion to make protect the information. Therefore, this study will evaluate the cybercrime and
insecurity of people in digital life due to increased misusing and steal of the personal data.
1.1 Problem statement
People nowadays cannot think their lives without stepping into the digital world. The
virtual world always attracts the young and inquisitive minds. People have multiple accounts on
social networking sites and individuals use multiple wallets to paying the bills. Today, there are
almost 200 billion internet-connected devices and people cannot imagine spending their lives
without the possibilities and opportunities that the digital life brings to them (Lee, Kim & Kim,
2015). Organisations and global citizens are becoming vulnerable towards the cyber threats.
Cyber attacks are common in today's life as destructive cyber attacks steal the personal
information and the cybercriminals peep into the common people's internet activities (Sen &
Borle, 2017). Media’s interest towards the cyber attacks has increased in recent years and
volume of cyber attacks and complexity has been increased in recent time. The impact of
digitalisation is clear on the wrong move when the personal data of the users are leaked and
government agencies have defiantly discovered the value of the internet for espionage and
internet of cyber warfare (Martin, Borah & Palmatier, 2017). Cybercrime damages the costs of
that hit the figure of $4 trillion in 2017 and this figure represented that transfer of money and the
information is not secured through online.
This paper will centre on the insecurity of the internet and data in this digital age due to
the increasing popularity of the money sharing wallet and social networking sites. Internet users
share a large amount of personal information online. A recent example of Facebook and
Cambridge Analytica is real life case study where it is clear Facebook holds millions of people's
personal information. Corporations and the software builders are trying to spend to exceed $1
trillion to make protect the information. Therefore, this study will evaluate the cybercrime and
insecurity of people in digital life due to increased misusing and steal of the personal data.

5ASSESSMENT 3
1.2 Research aim and Objectives
The aim of the research is to find the importance of personal data on the internet and the
ways through which the data theft can be avoided by the users. The purpose of the research is to
explore the extent to which personal data is secured on the internet platform.
The objectives of the research are:
To find out the importance of securing online data
To explore the extent to which personal data can be shared on an internet platform
To point out the impact of cybercrimes on the insecurity of the people in digital life
To recommend some possible steps to prevent cyber threats and ensure security
1.3 Research questions
RQ1: What is the importance of securing online data?
RQ2: How far it is secured to share personal data on internet platform?
RQ3: What is the impact of cybercrimes on the insecurity of the people in digital life?
RQ4: What could be some possible steps to prevent cyber threats and ensure security?
1.4 Justification and potential output of the research project
In this research project, diverse articles have been reviewed in order to get the idea of
cybercrime and its impact on the digital life of the people. It is observed that most of the authors
focused on the effective progress of cyberspace and the crimes associated with this. Most of the
articles discussed increasing numbers of cybercrimes and the authors shared the concerned when
maximum incidents did not have any records. This particular research is going to fill the vacuum
as a maximum of the existing literature did not discuss the threat of cybercrime in digital life of
1.2 Research aim and Objectives
The aim of the research is to find the importance of personal data on the internet and the
ways through which the data theft can be avoided by the users. The purpose of the research is to
explore the extent to which personal data is secured on the internet platform.
The objectives of the research are:
To find out the importance of securing online data
To explore the extent to which personal data can be shared on an internet platform
To point out the impact of cybercrimes on the insecurity of the people in digital life
To recommend some possible steps to prevent cyber threats and ensure security
1.3 Research questions
RQ1: What is the importance of securing online data?
RQ2: How far it is secured to share personal data on internet platform?
RQ3: What is the impact of cybercrimes on the insecurity of the people in digital life?
RQ4: What could be some possible steps to prevent cyber threats and ensure security?
1.4 Justification and potential output of the research project
In this research project, diverse articles have been reviewed in order to get the idea of
cybercrime and its impact on the digital life of the people. It is observed that most of the authors
focused on the effective progress of cyberspace and the crimes associated with this. Most of the
articles discussed increasing numbers of cybercrimes and the authors shared the concerned when
maximum incidents did not have any records. This particular research is going to fill the vacuum
as a maximum of the existing literature did not discuss the threat of cybercrime in digital life of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ASSESSMENT 3
the common people. This particular research will highlight the diverse threats for the people in
the digital world regarding social networking sites and pay wallets.
This research will bring the output through the discussions of the challenges regarding
various types of cybercrimes. The future researchers and the readers of this research will get to
know about the diverse steps through which the people can prevent themselves from
cybercrimes. The research outputs will be considered as the academic work for the issues of
cybercrime and insecurity of the common people.
2. Literature review and conceptual framework
2.1 Cybercrime and insecurity of people in digital life
Cybercrime activity is done through Information and Communication Technology as the
criminals or hackers use ICT tools to target the businesses or the victims. The activities related to
cybercrimes focus on the ICT tools to gain the personal and financial data of the targeted
victims. The main target of the cybercrime is the ICT tool rather than the person or the
corporation (Morey, Forbath & Schoop, 2015). Cybercriminals are at home with the
technological tools and the cybercriminals make them potential with further research and find the
loopholes into the system of the ICT tool. As stated by Stieglitz & Dang-Xuan (2013), most
common types of cybercrimes are the identity theft, online scams, hacking, computer system
attack, fraud, illegal online content and prohibited online content. Some of the online scammers
use the digital piracy of the music and videos to make the business. These types of cybercrimes
make the lives of common people vulnerable as the personal data of the people are in danger.
People make online money transaction and people use online banking also; if the hackers get the
secured information; the money and data all will be lost within no time. As opined by
the common people. This particular research will highlight the diverse threats for the people in
the digital world regarding social networking sites and pay wallets.
This research will bring the output through the discussions of the challenges regarding
various types of cybercrimes. The future researchers and the readers of this research will get to
know about the diverse steps through which the people can prevent themselves from
cybercrimes. The research outputs will be considered as the academic work for the issues of
cybercrime and insecurity of the common people.
2. Literature review and conceptual framework
2.1 Cybercrime and insecurity of people in digital life
Cybercrime activity is done through Information and Communication Technology as the
criminals or hackers use ICT tools to target the businesses or the victims. The activities related to
cybercrimes focus on the ICT tools to gain the personal and financial data of the targeted
victims. The main target of the cybercrime is the ICT tool rather than the person or the
corporation (Morey, Forbath & Schoop, 2015). Cybercriminals are at home with the
technological tools and the cybercriminals make them potential with further research and find the
loopholes into the system of the ICT tool. As stated by Stieglitz & Dang-Xuan (2013), most
common types of cybercrimes are the identity theft, online scams, hacking, computer system
attack, fraud, illegal online content and prohibited online content. Some of the online scammers
use the digital piracy of the music and videos to make the business. These types of cybercrimes
make the lives of common people vulnerable as the personal data of the people are in danger.
People make online money transaction and people use online banking also; if the hackers get the
secured information; the money and data all will be lost within no time. As opined by
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ASSESSMENT 3
Vijayakumar (2016), governmental works and the corporations use the digital data and the
common people suffer collateral damage to the secured data. Data breach can cause intense
criminal activity in cyber media that will damage the credibility of the online platform.
In theoretical perspective, Choice Theory is gathered the ideas from the assumption that
people are rational human that pursue their own considerations and interests. Someone’s
interests in works can harm another’s happiness. Individuals do the crime because the people
choose to commit this. People sometimes attempt to maximise the pleasure and minimise the
sadness and pain. Punishment of the criminals must be swift, severe and certain which will create
difference. According to Sunde et al., (2017), data transmission across pay wallet or the mobile
networks is the least secure method as the data and information are jeopardizing with financial
and personal information. If the cybercriminals get the data and information about any victim;
the victim will be danger in terms of data and financial loss. Right IT security is very important
as the perception gap between practitioners and legislators are narrowed by stepping the concrete
advice and levels of awareness.
2.2 Types of cybercrime in digital world
Internet is risky place as some of the tech savvy criminals abuse the internet network and
steal the data of the users. Phishing is the attack of the suspecting users of doing something what
they originally do not do. Sometimes, the users click on the URL or e-mail attachment when this
particular link takes the users to some other sites. Actors of the phishing attacks try to steal the
users’ login identity and other credentials (Moore, 2014). As stated by Taylor, Fritsch &
Liederbach (2014), ransomware is the particular crimeware where the victims' computers can
infect through phishing. Ransomware is the type of exploit kit and successful infection can draw
encryption. The cybercriminals want money in return for the data. Identity theft is another type
Vijayakumar (2016), governmental works and the corporations use the digital data and the
common people suffer collateral damage to the secured data. Data breach can cause intense
criminal activity in cyber media that will damage the credibility of the online platform.
In theoretical perspective, Choice Theory is gathered the ideas from the assumption that
people are rational human that pursue their own considerations and interests. Someone’s
interests in works can harm another’s happiness. Individuals do the crime because the people
choose to commit this. People sometimes attempt to maximise the pleasure and minimise the
sadness and pain. Punishment of the criminals must be swift, severe and certain which will create
difference. According to Sunde et al., (2017), data transmission across pay wallet or the mobile
networks is the least secure method as the data and information are jeopardizing with financial
and personal information. If the cybercriminals get the data and information about any victim;
the victim will be danger in terms of data and financial loss. Right IT security is very important
as the perception gap between practitioners and legislators are narrowed by stepping the concrete
advice and levels of awareness.
2.2 Types of cybercrime in digital world
Internet is risky place as some of the tech savvy criminals abuse the internet network and
steal the data of the users. Phishing is the attack of the suspecting users of doing something what
they originally do not do. Sometimes, the users click on the URL or e-mail attachment when this
particular link takes the users to some other sites. Actors of the phishing attacks try to steal the
users’ login identity and other credentials (Moore, 2014). As stated by Taylor, Fritsch &
Liederbach (2014), ransomware is the particular crimeware where the victims' computers can
infect through phishing. Ransomware is the type of exploit kit and successful infection can draw
encryption. The cybercriminals want money in return for the data. Identity theft is another type

8ASSESSMENT 3
of cybercrime activity where the attackers can do the activities like seizing or controlling of the
personal identity. The users can apply for the personal bank account and the cybercriminals
desire to steal the data from the account of the users. The cybercriminals want to take some key
information to steal the data (Brown, 2015). In addition, scams are not just one type; however;
scams always offer some enticing things to trick the users to send them money in return of
something. However; the offers are baseless and people lose their money in this process.
It can be concluded that people need to be more cautious when they share the information
in online platform and the users should follow the best practices of internet security to protect
against any kind of trick and cybercrime. As pointed out by Mazurczyk, Holt & Szczypiorski,
(2016), cybercrime is continue to evolve and corporations train the employees to build the IT
awareness so that they must not lose the secured and encrypted data.
2.3 Impact of cybercrime on people across the world
In digital world, emerging and new security threats are developing. Technology in recent
time is involved around individuals almost in each step (McMahon et al., 2015). Cybersecurity is
very grave matter for now as the incidents of cybercrimes have been increasing day by day. All
the incidents are not reported in the legal papers as 49% of the Millennials accept that the fact of
having experienced cybercrime in the past 2 years. The survey done by The Norton Cyber
Security stated that three out of ten people cannot detect phishing attack on the internet page
(Leukfeldt & Yar, 2016). 86% of the common people stated that they have observed or
experienced the phishing attack on email and on the internet page through desktop and laptop.
Cybercrime is prevalent in today's life and social networking sites play one such important role
to spread the cybercrime. When people click on any unknown link; this page leads the users to
another unknown web source. In this process, the information in the computer or in mobile can
of cybercrime activity where the attackers can do the activities like seizing or controlling of the
personal identity. The users can apply for the personal bank account and the cybercriminals
desire to steal the data from the account of the users. The cybercriminals want to take some key
information to steal the data (Brown, 2015). In addition, scams are not just one type; however;
scams always offer some enticing things to trick the users to send them money in return of
something. However; the offers are baseless and people lose their money in this process.
It can be concluded that people need to be more cautious when they share the information
in online platform and the users should follow the best practices of internet security to protect
against any kind of trick and cybercrime. As pointed out by Mazurczyk, Holt & Szczypiorski,
(2016), cybercrime is continue to evolve and corporations train the employees to build the IT
awareness so that they must not lose the secured and encrypted data.
2.3 Impact of cybercrime on people across the world
In digital world, emerging and new security threats are developing. Technology in recent
time is involved around individuals almost in each step (McMahon et al., 2015). Cybersecurity is
very grave matter for now as the incidents of cybercrimes have been increasing day by day. All
the incidents are not reported in the legal papers as 49% of the Millennials accept that the fact of
having experienced cybercrime in the past 2 years. The survey done by The Norton Cyber
Security stated that three out of ten people cannot detect phishing attack on the internet page
(Leukfeldt & Yar, 2016). 86% of the common people stated that they have observed or
experienced the phishing attack on email and on the internet page through desktop and laptop.
Cybercrime is prevalent in today's life and social networking sites play one such important role
to spread the cybercrime. When people click on any unknown link; this page leads the users to
another unknown web source. In this process, the information in the computer or in mobile can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ASSESSMENT 3
be leaked to unknown host. As stated by (Hui, Kim & Wang, 2017), worm virus-like SQL
Slammer and Sasser made their way into cyberspace and these viruses spread via internet
targeting the unpatched vulnerabilities. Through cybercrimes, cybercriminals share obscene or
offensive content; the people easily fall into the trap of the cybercrime. The issue of cybercrime
leads to the online harassment of the common people. For example, one hacking group named
MOD allegedly stole the technical data and passwords of Nynex and Pencil Bell and other
telecommunication companies. The damage was extensive and the companies lost more than
$370,000. (Jhaveri et al., 2017) commented that there is now self-sufficient and sophisticated
digital underground economy where the data is illicit commodity. The cybercrime group steal the
personal data to fraudulently use these for profit. This decade is the advancement of the
communication technology and this information revolution of society has converged to bring the
industrialisation. Cybercrime rate has increased with internet adoption, deployment of broadband
and the mobile internet access.
2.4 Protection against cybercrime and security
Cybercrime is criminal phenomenon that blurs the traditional distinction of threats as the
threats are of two types; internal threat (terrorist activity and criminality) and external threat
(military) (Zhang et al., 2017). The users need to use strong password so that it would be difficult
to break the code. Cyber-stalking and hacking can be prevented by using a strong password
(Wright, 2017). The individuals who have internet connection at home; the users need to use
trusted anti-virus as anti-virus can provide online security. Anti-virus can help the people from
stealing the personal data and hacking of the cybercriminals. The users of the internet media
must not send the credit and debit card details to any of the un-trusted site (Buczak & Guven,
2016). In addition, it is very important to keep the password of Wi-Fi so that other people are no
be leaked to unknown host. As stated by (Hui, Kim & Wang, 2017), worm virus-like SQL
Slammer and Sasser made their way into cyberspace and these viruses spread via internet
targeting the unpatched vulnerabilities. Through cybercrimes, cybercriminals share obscene or
offensive content; the people easily fall into the trap of the cybercrime. The issue of cybercrime
leads to the online harassment of the common people. For example, one hacking group named
MOD allegedly stole the technical data and passwords of Nynex and Pencil Bell and other
telecommunication companies. The damage was extensive and the companies lost more than
$370,000. (Jhaveri et al., 2017) commented that there is now self-sufficient and sophisticated
digital underground economy where the data is illicit commodity. The cybercrime group steal the
personal data to fraudulently use these for profit. This decade is the advancement of the
communication technology and this information revolution of society has converged to bring the
industrialisation. Cybercrime rate has increased with internet adoption, deployment of broadband
and the mobile internet access.
2.4 Protection against cybercrime and security
Cybercrime is criminal phenomenon that blurs the traditional distinction of threats as the
threats are of two types; internal threat (terrorist activity and criminality) and external threat
(military) (Zhang et al., 2017). The users need to use strong password so that it would be difficult
to break the code. Cyber-stalking and hacking can be prevented by using a strong password
(Wright, 2017). The individuals who have internet connection at home; the users need to use
trusted anti-virus as anti-virus can provide online security. Anti-virus can help the people from
stealing the personal data and hacking of the cybercriminals. The users of the internet media
must not send the credit and debit card details to any of the un-trusted site (Buczak & Guven,
2016). In addition, it is very important to keep the password of Wi-Fi so that other people are no
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10ASSESSMENT 3
able to use the Wi-Fi easily. In order to secure the computers from the eyes of the
cybercriminals; it is very important to install firewalls and upgrade the operating system
including the sensitive and private information.
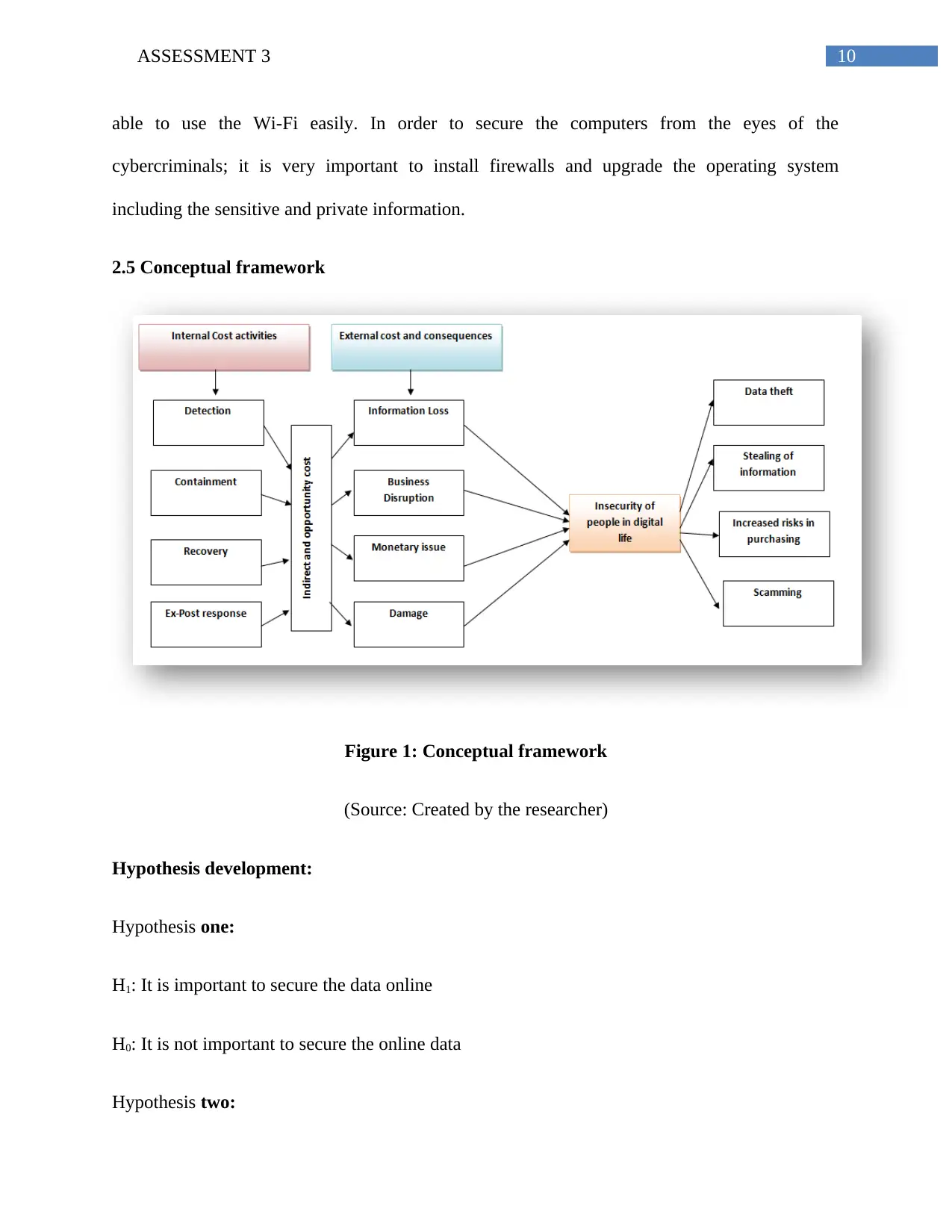
2.5 Conceptual framework
Figure 1: Conceptual framework
(Source: Created by the researcher)
Hypothesis development:
Hypothesis one:
H1: It is important to secure the data online
H0: It is not important to secure the online data
Hypothesis two:
able to use the Wi-Fi easily. In order to secure the computers from the eyes of the
cybercriminals; it is very important to install firewalls and upgrade the operating system
including the sensitive and private information.
2.5 Conceptual framework
Figure 1: Conceptual framework
(Source: Created by the researcher)
Hypothesis development:
Hypothesis one:
H1: It is important to secure the data online
H0: It is not important to secure the online data
Hypothesis two:

11ASSESSMENT 3
H1: Personal data can be shared through online media
H0: Personal data cannot be shared through online media
3. Methodology
3.1 Research approach
This research will be followed Quantitative research approach. Quantitative data are
numerical data (Kaplan, 2017). Numerical method emphasises objective measurement and it will
be easy to do statistical and numerical analysis of the collected data. In order to conduct the
research, it is very important to find out the primary data from where the data can be collected.
Quantitative research data is the systematic empirical investigation of phenomena that is
observable and this data must have computational technique.
3.2 Literature review
Literature review will be done based on the research topic cybercrime and the insecurity
of the people in digital life. Literature review helps to provide the current knowledge along with
substantial findings of the research area (Mackey & Gass, 2015). In this research, secondary data
sources of the topic will be identified through article, journals, paper and websites. Literature
review will be theoretical contribution of the research topic and literature review is the secondary
data sources; not just the original work.
3.2 Data collection procedure
In this research, both primary and secondary data will be collected. Primary data are the
raw data that would be collected through survey. Survey will be appropriate in order to collect
the respondents’ opinion regarding cybercrime and the people’s insecurity in digital life. The
H1: Personal data can be shared through online media
H0: Personal data cannot be shared through online media
3. Methodology
3.1 Research approach
This research will be followed Quantitative research approach. Quantitative data are
numerical data (Kaplan, 2017). Numerical method emphasises objective measurement and it will
be easy to do statistical and numerical analysis of the collected data. In order to conduct the
research, it is very important to find out the primary data from where the data can be collected.
Quantitative research data is the systematic empirical investigation of phenomena that is
observable and this data must have computational technique.
3.2 Literature review
Literature review will be done based on the research topic cybercrime and the insecurity
of the people in digital life. Literature review helps to provide the current knowledge along with
substantial findings of the research area (Mackey & Gass, 2015). In this research, secondary data
sources of the topic will be identified through article, journals, paper and websites. Literature
review will be theoretical contribution of the research topic and literature review is the secondary
data sources; not just the original work.
3.2 Data collection procedure
In this research, both primary and secondary data will be collected. Primary data are the
raw data that would be collected through survey. Survey will be appropriate in order to collect
the respondents’ opinion regarding cybercrime and the people’s insecurity in digital life. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




