Cybercrime and Countermeasures: International Perspective Report
VerifiedAdded on 2023/06/05
|9
|1545
|244
Report
AI Summary
This research proposal focuses on cybercrime and its countermeasures from an international perspective, specifically examining the UK, USA, Europe, and Asia (India, Pakistan, and China). It highlights the increasing importance of cybersecurity in an interconnected world, emphasizing the threats to organizational infrastructure and the need for proactive measures. The study aims to enable the prosecution of cybercrime through the establishment of effective rules and regulations. It investigates current cyber threats, potential countermeasures, and ways to handle security attacks on computer networks. The methodology includes a deductive research approach, primary data collection through surveys and interviews with online entrepreneurs, and hypothesis testing using regression analysis. The proposal also includes a literature review that explores existing research on cybercrime trends, countermeasures, and the role of cryptography in information security. The research concludes that factors like law enforcement, IT technology, and ethical awareness significantly impact cybercrime prevention. The study aims to equip business entrepreneurs with complex information technologies and restructured security systems to prevent cybercrime.

Running head: CYBER-CRIME AND ITS COUNTERMEASURE
Cyber-crime and its Countermeasure -An International perspective
Name of the Student:
Name of the University:
Cyber-crime and its Countermeasure -An International perspective
Name of the Student:
Name of the University:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER-CRIME AND ITS COUNTERMEASURE
Table of Contents
1.0 Title............................................................................................................................................2
2.0 Introduction................................................................................................................................2
3.0 Aim............................................................................................................................................2
4.0 Background................................................................................................................................2
5.0 Purpose research questions........................................................................................................3
6.0 Literature review........................................................................................................................4
7.0 Methodology..............................................................................................................................5
8.0 Plan of work and time schedule.................................................................................................6
9.0 Conclusion.................................................................................................................................7
References........................................................................................................................................8
Table of Contents
1.0 Title............................................................................................................................................2
2.0 Introduction................................................................................................................................2
3.0 Aim............................................................................................................................................2
4.0 Background................................................................................................................................2
5.0 Purpose research questions........................................................................................................3
6.0 Literature review........................................................................................................................4
7.0 Methodology..............................................................................................................................5
8.0 Plan of work and time schedule.................................................................................................6
9.0 Conclusion.................................................................................................................................7
References........................................................................................................................................8

2CYBER-CRIME AND ITS COUNTERMEASURE
1.0 Title
Cyber-crime and its Countermeasure -An International perspective
2.0 Introduction
The research proposal is based on cybercrime and its countermeasures for the
international perspective which is required to be focus on UK, USA, Europe and Asia (India,
Pakistan and China). Security of infrastructure of USA is identified as nation’s complex
challenges. This paper is based on growth importance of cybercrime with US as advanced of
internet is lead to non-traditional security concerns (Broadhurst et al. 2014). The information age
is presented society with unlimited possibilities in future and threats against it. The paper is
aimed to raise awareness of cybercrime issues and choices into the cyberspace.
3.0 Aim
The aim of this proposal is to enable prosecution of the cybercrime by establishment of
rules and regulations against the crime measures. There is analyzing of cybercrime for the
international perspective such as UK, USA, Europe and Asia (India, Pakistan and China).
4.0 Background
In the world, the organization is dependent on cyberspace is becoming an aspect of the
organizational security. The infrastructure of various organizations are being interconnected into
the cyberspace, therefore there is high level of risk to security has being increased. The threat to
1.0 Title
Cyber-crime and its Countermeasure -An International perspective
2.0 Introduction
The research proposal is based on cybercrime and its countermeasures for the
international perspective which is required to be focus on UK, USA, Europe and Asia (India,
Pakistan and China). Security of infrastructure of USA is identified as nation’s complex
challenges. This paper is based on growth importance of cybercrime with US as advanced of
internet is lead to non-traditional security concerns (Broadhurst et al. 2014). The information age
is presented society with unlimited possibilities in future and threats against it. The paper is
aimed to raise awareness of cybercrime issues and choices into the cyberspace.
3.0 Aim
The aim of this proposal is to enable prosecution of the cybercrime by establishment of
rules and regulations against the crime measures. There is analyzing of cybercrime for the
international perspective such as UK, USA, Europe and Asia (India, Pakistan and China).
4.0 Background
In the world, the organization is dependent on cyberspace is becoming an aspect of the
organizational security. The infrastructure of various organizations are being interconnected into
the cyberspace, therefore there is high level of risk to security has being increased. The threat to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER-CRIME AND ITS COUNTERMEASURE
cybercrime is growing at faster rate (Dawson 2015). This type of crime is included of computer
as well as person behind as victims. The cybercrime is included such as downloading.
5.0 Purpose research questions
The purpose of this study is to analyze of cyber security as well as security practices into
the network system, threats to prevent of cyber attacks into the countries. The research questions
are based on studying awareness of the cyber security management (Kamat and Gautam 2018).
In order to get information related to the research study, the researcher is formed of qualitative
questions to get suggestions from the respondents about alertness as well as existing law safety
of the cyber crime into USA, UK, Europe and Asia (India, Pakistan and China).
Following are the research questions such as:
1. What are current cyber threats to computer network security in UK, USA, Europe
and Asia?
2. What are possible countermeasures against the cyber threat caused?
3. What are the ways to handle of security attacks into the computer networks?
Hypothesis of the study such as:
Based on the research questions, following are hypothesis which are formed by the
researcher such as:
H1: The cyber crime rules and regulations affected the business operations of an
organization.
cybercrime is growing at faster rate (Dawson 2015). This type of crime is included of computer
as well as person behind as victims. The cybercrime is included such as downloading.
5.0 Purpose research questions
The purpose of this study is to analyze of cyber security as well as security practices into
the network system, threats to prevent of cyber attacks into the countries. The research questions
are based on studying awareness of the cyber security management (Kamat and Gautam 2018).
In order to get information related to the research study, the researcher is formed of qualitative
questions to get suggestions from the respondents about alertness as well as existing law safety
of the cyber crime into USA, UK, Europe and Asia (India, Pakistan and China).
Following are the research questions such as:
1. What are current cyber threats to computer network security in UK, USA, Europe
and Asia?
2. What are possible countermeasures against the cyber threat caused?
3. What are the ways to handle of security attacks into the computer networks?
Hypothesis of the study such as:
Based on the research questions, following are hypothesis which are formed by the
researcher such as:
H1: The cyber crime rules and regulations affected the business operations of an
organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER-CRIME AND ITS COUNTERMEASURE
This hypothesis is tested by use of primary data collection. In order to study rules as well
as regulations of the cyber crime, the parameters used are maintenance of the log registers,
electronic maintained records, and verification of documents (Li 2017). Regression analysis is
used to test this hypothesis at 5% level of significance is being used. The parameters used to test
the hypothesis are based on questionnaire prepared to take feedback. Those parameters are based
on current law protection of the cyber crimes into USA, UK, Europe and Asia.
H2: Cryptography techniques are used to encrypt information as best countermeasure of
cyber crime.
This hypothesis is tested by use of primary data collection. In order to analyze the
cryptography techniques for encryption of information, the parameters used to test the hypothesis
are based on questionnaire prepared to take feedback. Regression analysis is used to test this
hypothesis at 5% level of significance is being used. Reliability test is to be done for evaluation
of reliability of data which are obtained throughout questionnaires that are distributed to the
respondents.
6.0 Literature review
Bendovschi (2015) stated that expansion of internet participation results into rise of
cybercrime as well as information security problems which are occurred in UK, USA, Europe
and Asia. Into the online scams, internet is used to attain the victims through transferring of
unwanted messages pretending to initiate from the organizations to misinform individuals into
reveal the financial in addition to personal identity information. Kebande et al. (2017) argued
that information which is obtained from the phishing facilities crimes like financial fraud as well
as identify thread. The cybercrimes which are caused are e-mail spoofing, phishing, cyber
This hypothesis is tested by use of primary data collection. In order to study rules as well
as regulations of the cyber crime, the parameters used are maintenance of the log registers,
electronic maintained records, and verification of documents (Li 2017). Regression analysis is
used to test this hypothesis at 5% level of significance is being used. The parameters used to test
the hypothesis are based on questionnaire prepared to take feedback. Those parameters are based
on current law protection of the cyber crimes into USA, UK, Europe and Asia.
H2: Cryptography techniques are used to encrypt information as best countermeasure of
cyber crime.
This hypothesis is tested by use of primary data collection. In order to analyze the
cryptography techniques for encryption of information, the parameters used to test the hypothesis
are based on questionnaire prepared to take feedback. Regression analysis is used to test this
hypothesis at 5% level of significance is being used. Reliability test is to be done for evaluation
of reliability of data which are obtained throughout questionnaires that are distributed to the
respondents.
6.0 Literature review
Bendovschi (2015) stated that expansion of internet participation results into rise of
cybercrime as well as information security problems which are occurred in UK, USA, Europe
and Asia. Into the online scams, internet is used to attain the victims through transferring of
unwanted messages pretending to initiate from the organizations to misinform individuals into
reveal the financial in addition to personal identity information. Kebande et al. (2017) argued
that information which is obtained from the phishing facilities crimes like financial fraud as well
as identify thread. The cybercrimes which are caused are e-mail spoofing, phishing, cyber

5CYBER-CRIME AND ITS COUNTERMEASURE
stalking and computer sabotage. A countermeasure of cybercrime is implemented to combat with
the cybercrime as well as increase into security. Cryptography technique is the best method
which is used by most of the organizations to encrypt of information for keeping the information
secured.
7.0 Methodology
In this study, deductive research approach is used which is based on development of
hypothesis based on theory and research strategy is considered to analysis the research
hypothesis. This hypothesis testing is done against the researcher’s observations. In this
proposal, selected data method is primary data collection method where the data are collected
from survey and interview methods (Ilyas 2015). The target population into this research is
comprised of business online entrepreneurs in USA, UK, Europe and Asia. The theoretical
resources are drawn from the feedback of participants those are involved into the study. The
primary data collection is described when the business is conducted own research along with
control its own data. The advantages of primary data are that the research is being oriented from
the goals and purpose (Johnson 2016). The researchers can change of course of study when
required, and choose of platforms for observations. The limitations of primary method are that
this practice is very time consuming along with costs a lot of resources. The result from these
research audiences is not always realistic.
stalking and computer sabotage. A countermeasure of cybercrime is implemented to combat with
the cybercrime as well as increase into security. Cryptography technique is the best method
which is used by most of the organizations to encrypt of information for keeping the information
secured.
7.0 Methodology
In this study, deductive research approach is used which is based on development of
hypothesis based on theory and research strategy is considered to analysis the research
hypothesis. This hypothesis testing is done against the researcher’s observations. In this
proposal, selected data method is primary data collection method where the data are collected
from survey and interview methods (Ilyas 2015). The target population into this research is
comprised of business online entrepreneurs in USA, UK, Europe and Asia. The theoretical
resources are drawn from the feedback of participants those are involved into the study. The
primary data collection is described when the business is conducted own research along with
control its own data. The advantages of primary data are that the research is being oriented from
the goals and purpose (Johnson 2016). The researchers can change of course of study when
required, and choose of platforms for observations. The limitations of primary method are that
this practice is very time consuming along with costs a lot of resources. The result from these
research audiences is not always realistic.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6CYBER-CRIME AND ITS COUNTERMEASURE
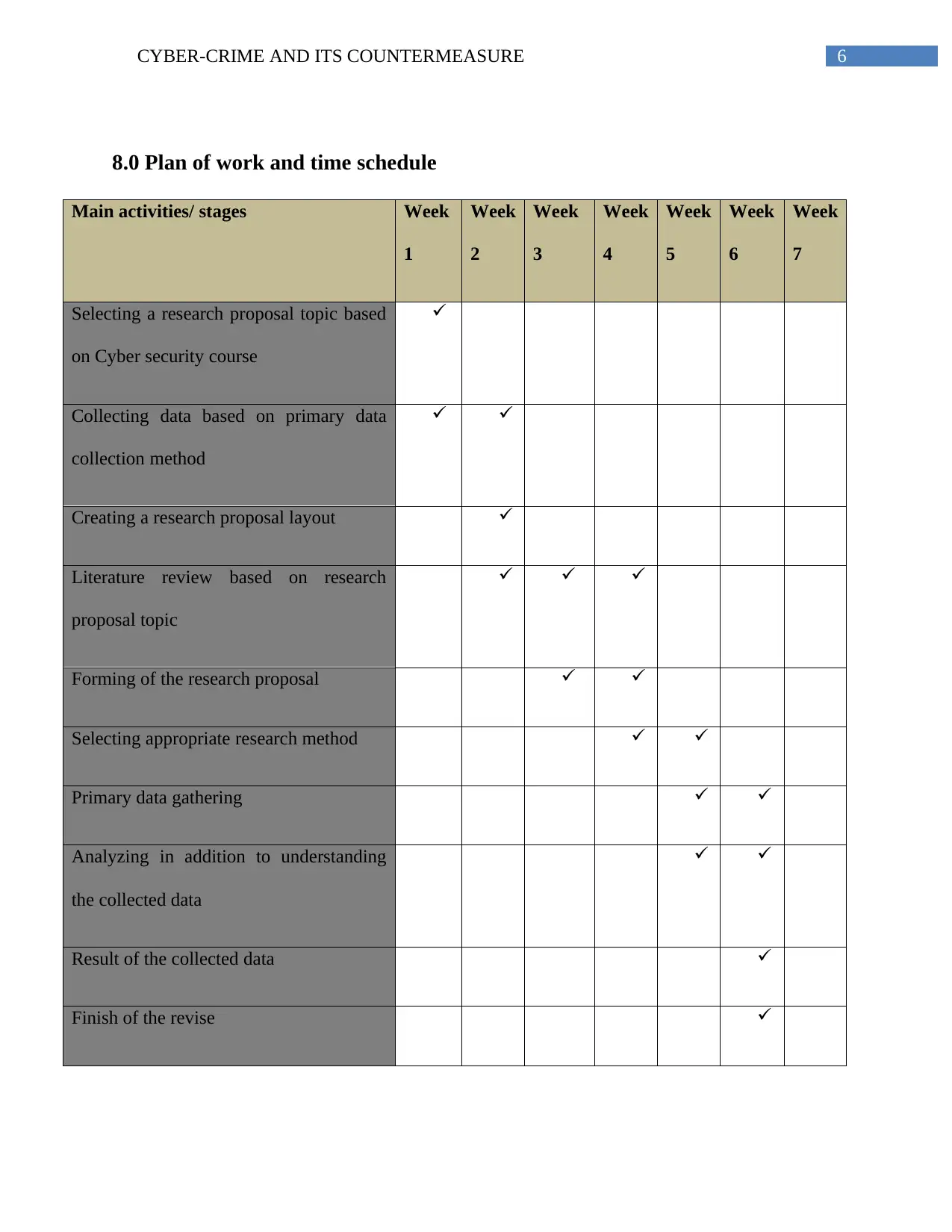
8.0 Plan of work and time schedule
Main activities/ stages Week
1
Week
2
Week
3
Week
4
Week
5
Week
6
Week
7
Selecting a research proposal topic based
on Cyber security course
Collecting data based on primary data
collection method
Creating a research proposal layout
Literature review based on research
proposal topic
Forming of the research proposal
Selecting appropriate research method
Primary data gathering
Analyzing in addition to understanding
the collected data
Result of the collected data
Finish of the revise
8.0 Plan of work and time schedule
Main activities/ stages Week
1
Week
2
Week
3
Week
4
Week
5
Week
6
Week
7
Selecting a research proposal topic based
on Cyber security course
Collecting data based on primary data
collection method
Creating a research proposal layout
Literature review based on research
proposal topic
Forming of the research proposal
Selecting appropriate research method
Primary data gathering
Analyzing in addition to understanding
the collected data
Result of the collected data
Finish of the revise
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CYBER-CRIME AND ITS COUNTERMEASURE
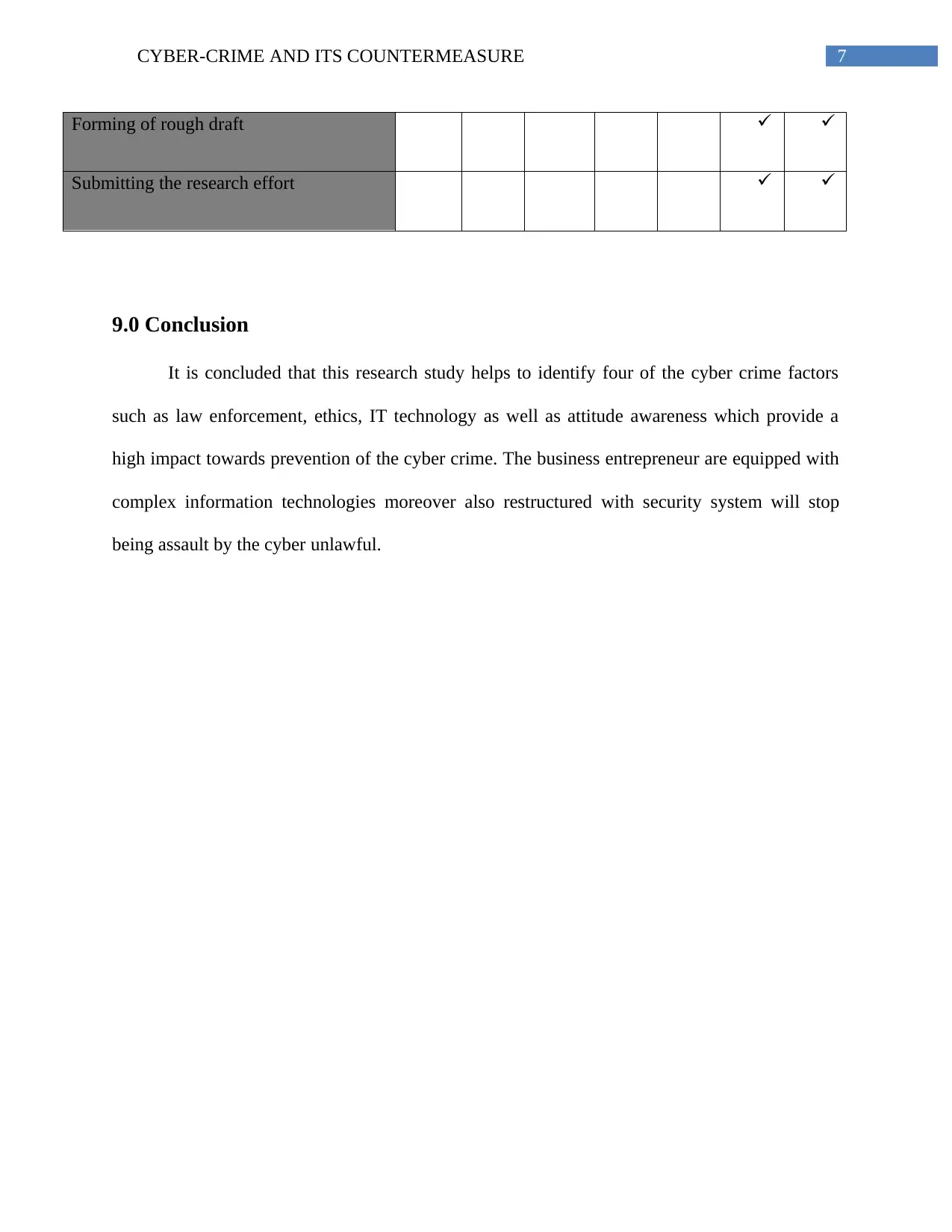
Forming of rough draft
Submitting the research effort
9.0 Conclusion
It is concluded that this research study helps to identify four of the cyber crime factors
such as law enforcement, ethics, IT technology as well as attitude awareness which provide a
high impact towards prevention of the cyber crime. The business entrepreneur are equipped with
complex information technologies moreover also restructured with security system will stop
being assault by the cyber unlawful.
Forming of rough draft
Submitting the research effort
9.0 Conclusion
It is concluded that this research study helps to identify four of the cyber crime factors
such as law enforcement, ethics, IT technology as well as attitude awareness which provide a
high impact towards prevention of the cyber crime. The business entrepreneur are equipped with
complex information technologies moreover also restructured with security system will stop
being assault by the cyber unlawful.

8CYBER-CRIME AND ITS COUNTERMEASURE
References
Bendovschi, A., 2015. Cyber-attacks–trends, patterns and security countermeasures. Procedia
Economics and Finance, 28, pp.24-31.
Broadhurst, R., Grabosky, P., Alazab, M., Bouhours, B. and Chon, S., 2014. An analysis of the
nature of groups engaged in cyber crime.
Dawson, M. ed., 2015. New Threats and Countermeasures in Digital Crime and Cyber
Terrorism. IGI Global.
Ilyas, M.M., 2015. Cyber security.
Johnson, M., 2016. Cyber crime, security and digital intelligence. Routledge.
Kamat, P. and Gautam, A.S., 2018. Recent Trends in the Era of Cybercrime and the Measures to
Control Them. In Handbook of e-Business Security (pp. 243-258). Auerbach Publications.
Kebande, V.R., Karie, N.M., Michael, A., Malapane, S.M. and Venter, H.S., 2017, May. How an
IoT-enabled “smart refrigerator” can play a clandestine role in perpetuating cyber-crime. In IST-
Africa Week Conference (IST-Africa), 2017 (pp. 1-10). IEEE.
Li, J.X., 2017. Cyber Crime and Legal Countermeasures: A Historical Analysis. International
Journal of Criminal Justice Sciences, 12(2), pp.196-207.
References
Bendovschi, A., 2015. Cyber-attacks–trends, patterns and security countermeasures. Procedia
Economics and Finance, 28, pp.24-31.
Broadhurst, R., Grabosky, P., Alazab, M., Bouhours, B. and Chon, S., 2014. An analysis of the
nature of groups engaged in cyber crime.
Dawson, M. ed., 2015. New Threats and Countermeasures in Digital Crime and Cyber
Terrorism. IGI Global.
Ilyas, M.M., 2015. Cyber security.
Johnson, M., 2016. Cyber crime, security and digital intelligence. Routledge.
Kamat, P. and Gautam, A.S., 2018. Recent Trends in the Era of Cybercrime and the Measures to
Control Them. In Handbook of e-Business Security (pp. 243-258). Auerbach Publications.
Kebande, V.R., Karie, N.M., Michael, A., Malapane, S.M. and Venter, H.S., 2017, May. How an
IoT-enabled “smart refrigerator” can play a clandestine role in perpetuating cyber-crime. In IST-
Africa Week Conference (IST-Africa), 2017 (pp. 1-10). IEEE.
Li, J.X., 2017. Cyber Crime and Legal Countermeasures: A Historical Analysis. International
Journal of Criminal Justice Sciences, 12(2), pp.196-207.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
