CO4515 Cybercrime Trends: Research Paper on Detecting Spam Web Pages
VerifiedAdded on 2023/04/20
|10
|2680
|446
Report
AI Summary
This research paper delves into the trends in cybercrime, specifically focusing on the detection and mitigation of spam web pages and email spam. It includes an annotated bibliography of relevant works, a literature review discussing various cyber-attack types and security measures, and an analysis of the impact of cybercrime on individuals, businesses, and governments. The paper also provides recommendations for improving cybersecurity practices, such as using authentic networks, implementing firewalls and encryption, and adopting strong password policies. The research utilizes both quantitative and qualitative methods, drawing data from surveys, previous studies, and expert opinions to provide a comprehensive overview of the challenges and potential solutions in combating cybercrime. Desklib provides access to this and other solved assignments.
TRENDS IN CYBERCRIME
1
Trends in Cybercrime
1
Trends in Cybercrime
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TRENDS IN CYBERCRIME
2
Stage 1- research question
How to detect spam web pages?
How to effectively mitigate email spam?
Stage 2- an Annotated bibliography
Dashora, K., (2011) Cybercrime in the society: Problems and preventions. Journal
of Alternative Perspectives in the Social Sciences, 3(1), pp.240-259.
The title of this journal article is Cyber Crime in the Society: Problems and Preventions
which was written Kamini dashora in the year 2011. The main aim of this research
paper is to analysis the issue of cybercrime in the society and key factors that increase
the problem of cybercrime. According to author use of the internet is growing rapidly
and many consumers are using this approach for communication purpose that also
increases the problem of cyber-crime. In this paper, the author involves various reports
from news media and news portal and relevant information are gathered from the
previous research, online websites and books. Term cyber-crime is defined as the
security threat that occurs due to lack of security and the author described how hackers
attack the consumer personal networks and devices.
Ramdinmawii, E., Ghisingh, S. and Sharma, U.M., (2014) A Study on the Cyber-
Crime and Cyber Criminals: A Global Problem. International Journal of Web
Technology, 3(2), pp.172-179.
The title of this journal paper is A Study on the Cyber-Crime and Cyber Criminals: A
Global Problem which was written by Esther Ramdinmawii, Seema Ghisingh, and Usha
Mary Sharma. This paper is completely based on the cybercrimes and aim of this
investigation is to evaluate the common areas where cybercrime occurs and various
kinds of cyber-crimes that are faced by the consumers. According to the author, most
hackers transfer spam and fraud mails to consumers and users click on that mails due to
which hackers can easily enter into their networks. In this paper, the researcher uses
both qualitative and quantitative data approach to collect the data or information about
2
Stage 1- research question
How to detect spam web pages?
How to effectively mitigate email spam?
Stage 2- an Annotated bibliography
Dashora, K., (2011) Cybercrime in the society: Problems and preventions. Journal
of Alternative Perspectives in the Social Sciences, 3(1), pp.240-259.
The title of this journal article is Cyber Crime in the Society: Problems and Preventions
which was written Kamini dashora in the year 2011. The main aim of this research
paper is to analysis the issue of cybercrime in the society and key factors that increase
the problem of cybercrime. According to author use of the internet is growing rapidly
and many consumers are using this approach for communication purpose that also
increases the problem of cyber-crime. In this paper, the author involves various reports
from news media and news portal and relevant information are gathered from the
previous research, online websites and books. Term cyber-crime is defined as the
security threat that occurs due to lack of security and the author described how hackers
attack the consumer personal networks and devices.
Ramdinmawii, E., Ghisingh, S. and Sharma, U.M., (2014) A Study on the Cyber-
Crime and Cyber Criminals: A Global Problem. International Journal of Web
Technology, 3(2), pp.172-179.
The title of this journal paper is A Study on the Cyber-Crime and Cyber Criminals: A
Global Problem which was written by Esther Ramdinmawii, Seema Ghisingh, and Usha
Mary Sharma. This paper is completely based on the cybercrimes and aim of this
investigation is to evaluate the common areas where cybercrime occurs and various
kinds of cyber-crimes that are faced by the consumers. According to the author, most
hackers transfer spam and fraud mails to consumers and users click on that mails due to
which hackers can easily enter into their networks. In this paper, the researcher uses
both qualitative and quantitative data approach to collect the data or information about

TRENDS IN CYBERCRIME
3
cyber-crime. A survey is conducted by the investigator to gather the data or statics
about the research topic and they also collected the views of other experts.
Saini, H., Rao, Y.S. and Panda, T.C., (2012) Cyber-crimes and their impacts: A
review. International Journal of Engineering Research and Applications, 2(2),
pp.202-209.
This paper was written by hemraj saini in the year 2012 and the purpose of this journal
article is to review the cyber-crimes and their impacts on the consumer personal
networks or information. In which the author also identifies the key factors that
increase the problem of cyber-crime and process to improve the security of the
consumer data. The researcher used secondary research method to improve the
effectiveness of the investigation and observed that many consumers use unauthentic
networks or servers that are produced by hackers to collect their private details.
Stage 2 Research paper
Introduction
In the field of computer science, spam is defined as a threat which is used for the
unsolicited and bulk electronic message. Mainly, hackers use this term in cyber-crimes
and they transfer spam mails or messages to their personal account due to which they
can easily enter into their computer system (Dunn Cavelty, 2013). A recent study
observed that the rate of cybercrime has increase by 48% and many companies,
business industries, and government authorities are facing the issue of cyber-attack or
hacking. The aim of this research paper is to analysis the problem of cyber-crimes and
discusses how hackers encrypt consumer personal data and technique to solve such
kind of problem. In this research paper, the researcher will use both quantitative and
qualitative methods to collect and gather the relevant data from different sources.
Literature review
Cyber-crime is one of the biggest problems faced by many organizations and
communities and it occurs due to lack of security. A recent study identified that most
hackers use malware software to design a large amount of traffic and they send the
spam mails to consumers. With the help of spam, hackers can easily enter into their
3
cyber-crime. A survey is conducted by the investigator to gather the data or statics
about the research topic and they also collected the views of other experts.
Saini, H., Rao, Y.S. and Panda, T.C., (2012) Cyber-crimes and their impacts: A
review. International Journal of Engineering Research and Applications, 2(2),
pp.202-209.
This paper was written by hemraj saini in the year 2012 and the purpose of this journal
article is to review the cyber-crimes and their impacts on the consumer personal
networks or information. In which the author also identifies the key factors that
increase the problem of cyber-crime and process to improve the security of the
consumer data. The researcher used secondary research method to improve the
effectiveness of the investigation and observed that many consumers use unauthentic
networks or servers that are produced by hackers to collect their private details.
Stage 2 Research paper
Introduction
In the field of computer science, spam is defined as a threat which is used for the
unsolicited and bulk electronic message. Mainly, hackers use this term in cyber-crimes
and they transfer spam mails or messages to their personal account due to which they
can easily enter into their computer system (Dunn Cavelty, 2013). A recent study
observed that the rate of cybercrime has increase by 48% and many companies,
business industries, and government authorities are facing the issue of cyber-attack or
hacking. The aim of this research paper is to analysis the problem of cyber-crimes and
discusses how hackers encrypt consumer personal data and technique to solve such
kind of problem. In this research paper, the researcher will use both quantitative and
qualitative methods to collect and gather the relevant data from different sources.
Literature review
Cyber-crime is one of the biggest problems faced by many organizations and
communities and it occurs due to lack of security. A recent study identified that most
hackers use malware software to design a large amount of traffic and they send the
spam mails to consumers. With the help of spam, hackers can easily enter into their
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TRENDS IN CYBERCRIME
4
computer devices and they have the potential to block their networks. There are
numerous researchers provided their views on this problem and they identified that
many consumers use third party applications and unauthentic networks which are
developed by the criminals to obtain their private details. According to Holt, and
Bossler, (2008), the use of the internet is growing rapidly and many consumers use
internet connectivity to transfer data or information from one person to another. It also
increases the rate of cyber-crimes because the internet provides a way to enter into
consumer personal devices. In which author use both qualitative and qualitative
research method to improve the effectiveness of the research and relevant information
gathered from the various resources, for example, journal paper, previous investigation
and many more. The author observed that cyber-crime include some degree of
infringement on the security of another and it also damage the computer networks.
Katos and Bednar, (2008) identified that the use of computer and internet is increasing
very fast that also associated with the cyber-crimes and in the year 2015 the rate of
hacking or data breaching has increased by 46%. The main problem of consumers is
that they do not use the advanced security level due to which they can lose their
personal information like financial documents, bank details and many more. According
to Lagazio, Sherif, and Cushman, (2014) term cybercrime is defined as a crime that
includes the unauthentic networks or servers, malware software to break the security
of consumers by using internet connectivity.
In which the author describes the fundamental concept of the cybercrime and they
observed that many hackers attack the consumer Gmail account and transfer the spam
links to users. The author did not reduce the drawbacks of the previous investigation
and provided only theoretical information about cybercrime. There are various kinds of
cyber-attacks and threats occur into the computer networks, for example, denial of
service attack, phishing, cyber stalking, e-mail spamming, malware and many more.
These entire cans are discussed by Liang, and Lu, (2010) in their research paper and
they also investigated that if users adopt the advanced security tools like encryption
and firewall then they can resolve the issue of cyber-crime. Many consumers use the
low level password system which can be easily hacked by the attacker and if consumers
use the high level password then they can secure their personal data files. McGuire, and
Dowling, (2013) analysed that the between 2014 and 2016 the rate of cyber-crimes or
4
computer devices and they have the potential to block their networks. There are
numerous researchers provided their views on this problem and they identified that
many consumers use third party applications and unauthentic networks which are
developed by the criminals to obtain their private details. According to Holt, and
Bossler, (2008), the use of the internet is growing rapidly and many consumers use
internet connectivity to transfer data or information from one person to another. It also
increases the rate of cyber-crimes because the internet provides a way to enter into
consumer personal devices. In which author use both qualitative and qualitative
research method to improve the effectiveness of the research and relevant information
gathered from the various resources, for example, journal paper, previous investigation
and many more. The author observed that cyber-crime include some degree of
infringement on the security of another and it also damage the computer networks.
Katos and Bednar, (2008) identified that the use of computer and internet is increasing
very fast that also associated with the cyber-crimes and in the year 2015 the rate of
hacking or data breaching has increased by 46%. The main problem of consumers is
that they do not use the advanced security level due to which they can lose their
personal information like financial documents, bank details and many more. According
to Lagazio, Sherif, and Cushman, (2014) term cybercrime is defined as a crime that
includes the unauthentic networks or servers, malware software to break the security
of consumers by using internet connectivity.
In which the author describes the fundamental concept of the cybercrime and they
observed that many hackers attack the consumer Gmail account and transfer the spam
links to users. The author did not reduce the drawbacks of the previous investigation
and provided only theoretical information about cybercrime. There are various kinds of
cyber-attacks and threats occur into the computer networks, for example, denial of
service attack, phishing, cyber stalking, e-mail spamming, malware and many more.
These entire cans are discussed by Liang, and Lu, (2010) in their research paper and
they also investigated that if users adopt the advanced security tools like encryption
and firewall then they can resolve the issue of cyber-crime. Many consumers use the
low level password system which can be easily hacked by the attacker and if consumers
use the high level password then they can secure their personal data files. McGuire, and
Dowling, (2013) analysed that the between 2014 and 2016 the rate of cyber-crimes or
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TRENDS IN CYBERCRIME
5
hacking has increased by the 20% and users use third party application which are
produced by the attackers to collect the personal information of account through Google
access. Recently information technology developed many advanced techniques which
can be used to handle the issue of cyber-crime such as firewall, cryptography, limited
login attempts and antiviruses. In which investigator evaluated various security threats
and issues and provided the recommendation for improving the security of personal
information. According to Saini, Rao, and Panda, (2012) cyber-crime has caused many
damages on user personal devices, companies, government and business industries and
people can suffer from the financial problem. To reduce the rate of cyber-crimes and
hacking several strategies and polices are devolved by information and communication
technology and encryption is one of the advanced technique that can be used to
improve privacy. Recent survey observed that in 2013 saw the monetary damage of
nearly 781.85 million U.S. dollars due to the lack of security and use of unauthentic
servers. This paper also indicates that e-mail is one of the common platforms which is
used by the hackers during the cyber-crime process and there are different kinds of
attacks occur into IT, for example, DOS, malicious attack, data breach, and many more.
Salifu, (2008) identified that there are many examples of cyber-crimes such as cyber
stalking, intellectual property crimes, bot network, transmitting the virus, hacking,
cracking, internet time thefts, hacking, data breaching, phishing, voice phishing, carding,
child pornography and cyber-threats. Many hackers attack the large business industries
and banking sectors because they want to earn more money by encrypting consumers
and employees personal data files. the use the botnet technique to damage the
computer networks and passwords of individual computer devices after that they
produce the private key on their private data files that cannot be decrypted by the users
without paying ransom or money. The recent survey evaluated that in the year 2015
more than 1000 computer systems of users were hacked by the attackers in which they
transfer the spam mails or messages to consumers and use malicious approach to
collect their personal data. Wall, (2008) provided the overview of cybercrime and spam
in their investigation and also discussed the prevention techniques to resolve the issue
of cyber-crimes. The author also analysed the problem of hacking and found that lack of
security and use of unauthorized server both are main two key factors that increase the
rate of cyber-crimes. To address the issue of spam and the cyber-crimes consumer can
5
hacking has increased by the 20% and users use third party application which are
produced by the attackers to collect the personal information of account through Google
access. Recently information technology developed many advanced techniques which
can be used to handle the issue of cyber-crime such as firewall, cryptography, limited
login attempts and antiviruses. In which investigator evaluated various security threats
and issues and provided the recommendation for improving the security of personal
information. According to Saini, Rao, and Panda, (2012) cyber-crime has caused many
damages on user personal devices, companies, government and business industries and
people can suffer from the financial problem. To reduce the rate of cyber-crimes and
hacking several strategies and polices are devolved by information and communication
technology and encryption is one of the advanced technique that can be used to
improve privacy. Recent survey observed that in 2013 saw the monetary damage of
nearly 781.85 million U.S. dollars due to the lack of security and use of unauthentic
servers. This paper also indicates that e-mail is one of the common platforms which is
used by the hackers during the cyber-crime process and there are different kinds of
attacks occur into IT, for example, DOS, malicious attack, data breach, and many more.
Salifu, (2008) identified that there are many examples of cyber-crimes such as cyber
stalking, intellectual property crimes, bot network, transmitting the virus, hacking,
cracking, internet time thefts, hacking, data breaching, phishing, voice phishing, carding,
child pornography and cyber-threats. Many hackers attack the large business industries
and banking sectors because they want to earn more money by encrypting consumers
and employees personal data files. the use the botnet technique to damage the
computer networks and passwords of individual computer devices after that they
produce the private key on their private data files that cannot be decrypted by the users
without paying ransom or money. The recent survey evaluated that in the year 2015
more than 1000 computer systems of users were hacked by the attackers in which they
transfer the spam mails or messages to consumers and use malicious approach to
collect their personal data. Wall, (2008) provided the overview of cybercrime and spam
in their investigation and also discussed the prevention techniques to resolve the issue
of cyber-crimes. The author also analysed the problem of hacking and found that lack of
security and use of unauthorized server both are main two key factors that increase the
rate of cyber-crimes. To address the issue of spam and the cyber-crimes consumer can

TRENDS IN CYBERCRIME
6
adopt the following mitigation tools and steps:
Use only authentic networks and servers
Adopt the antivirus and firewall software to detect the spam and unauthentic
links
Keep secure data from hackers by Appling the strong passwords
Ensure that all security tools are working properly
Use encryption and cryptography technology during the communication process
If any spam mail occurs in Gmail then use robust technique to handle and block
them
Use backup plans to improve the security of personal data files
Always use only authentic websites or application to avoid the problem of
hacking
With the help of all these steps and methods, consumers can enhance the privacy of
their data or information and they can analysis their security level by using
cryptography approach. If they found any fraud or spam mail in their accounts they can
ignore or delete them because these are produced by hackers or criminals to obtain
personal data.
Discussion
It is discussed that in the year 2014 the rate of cyber-crimes has increased by the 36%
that time consumers used unauthentic servers which are developed by the attackers.
The main problem occurs in cyber-crime is that consumers can lose their personal
information and recent study observed that hackers have the potential to enter into
user computer devices (Kshetri, 2010). Recently, information technology developed
various technologies and approaches to improve the security of the data like firewall,
encryption, and cryptography. It is estimated that these security tools reduced the issue
of cyber-crime and spam mails by 48% in the year 2017 and they are more effective as
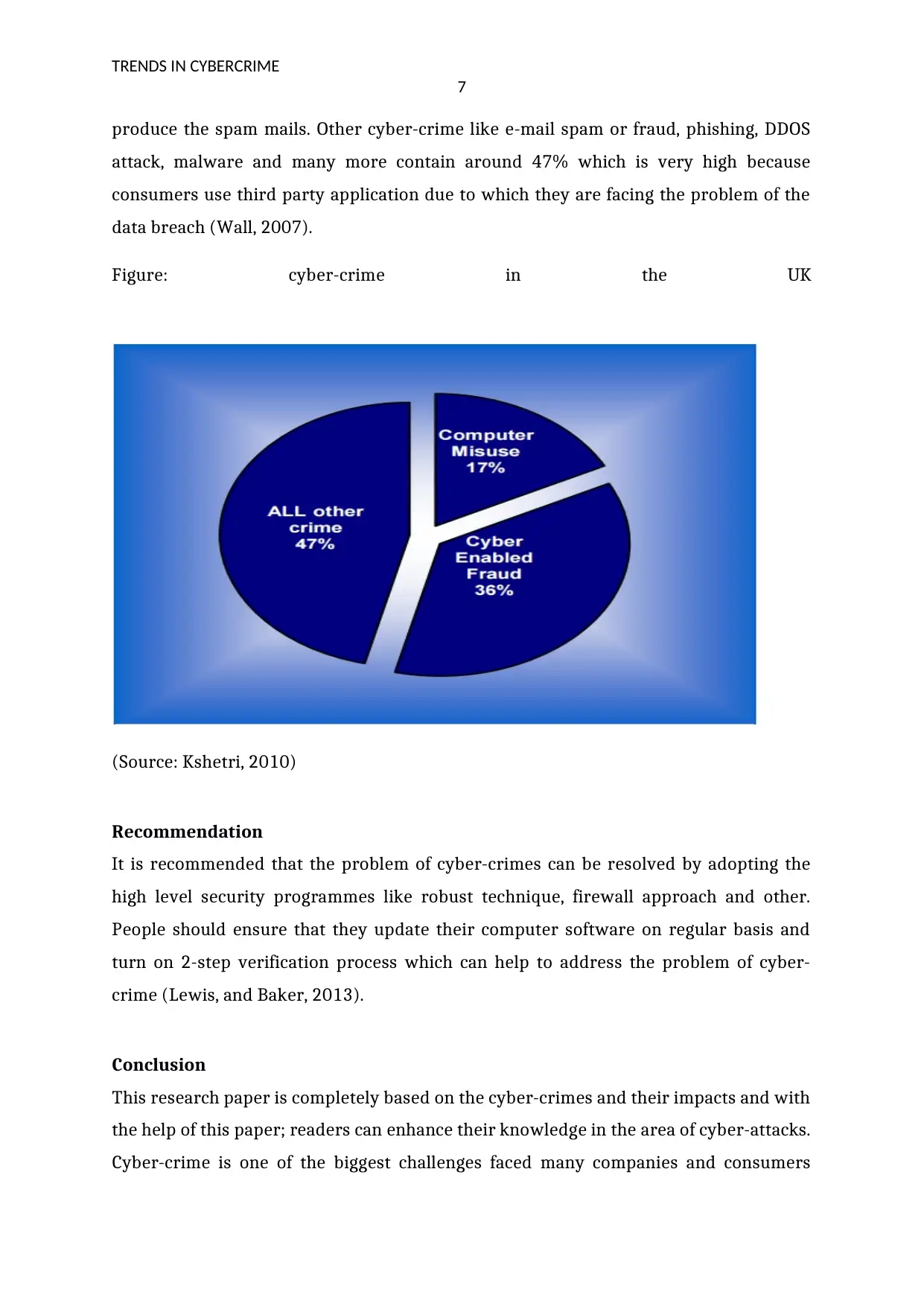
compared to other technologies. Below graph shows that the rate of computer misuse is
very less as compared to the fraud case and many hackers use botnet process to
6
adopt the following mitigation tools and steps:
Use only authentic networks and servers
Adopt the antivirus and firewall software to detect the spam and unauthentic
links
Keep secure data from hackers by Appling the strong passwords
Ensure that all security tools are working properly
Use encryption and cryptography technology during the communication process
If any spam mail occurs in Gmail then use robust technique to handle and block
them
Use backup plans to improve the security of personal data files
Always use only authentic websites or application to avoid the problem of
hacking
With the help of all these steps and methods, consumers can enhance the privacy of
their data or information and they can analysis their security level by using
cryptography approach. If they found any fraud or spam mail in their accounts they can
ignore or delete them because these are produced by hackers or criminals to obtain
personal data.
Discussion
It is discussed that in the year 2014 the rate of cyber-crimes has increased by the 36%
that time consumers used unauthentic servers which are developed by the attackers.
The main problem occurs in cyber-crime is that consumers can lose their personal
information and recent study observed that hackers have the potential to enter into
user computer devices (Kshetri, 2010). Recently, information technology developed
various technologies and approaches to improve the security of the data like firewall,
encryption, and cryptography. It is estimated that these security tools reduced the issue
of cyber-crime and spam mails by 48% in the year 2017 and they are more effective as
compared to other technologies. Below graph shows that the rate of computer misuse is
very less as compared to the fraud case and many hackers use botnet process to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
TRENDS IN CYBERCRIME
7
produce the spam mails. Other cyber-crime like e-mail spam or fraud, phishing, DDOS
attack, malware and many more contain around 47% which is very high because
consumers use third party application due to which they are facing the problem of the
data breach (Wall, 2007).
Figure: cyber-crime in the UK
(Source: Kshetri, 2010)
Recommendation
It is recommended that the problem of cyber-crimes can be resolved by adopting the
high level security programmes like robust technique, firewall approach and other.
People should ensure that they update their computer software on regular basis and
turn on 2-step verification process which can help to address the problem of cyber-
crime (Lewis, and Baker, 2013).
Conclusion
This research paper is completely based on the cyber-crimes and their impacts and with
the help of this paper; readers can enhance their knowledge in the area of cyber-attacks.
Cyber-crime is one of the biggest challenges faced many companies and consumers
7
produce the spam mails. Other cyber-crime like e-mail spam or fraud, phishing, DDOS
attack, malware and many more contain around 47% which is very high because
consumers use third party application due to which they are facing the problem of the
data breach (Wall, 2007).
Figure: cyber-crime in the UK
(Source: Kshetri, 2010)
Recommendation
It is recommended that the problem of cyber-crimes can be resolved by adopting the
high level security programmes like robust technique, firewall approach and other.
People should ensure that they update their computer software on regular basis and
turn on 2-step verification process which can help to address the problem of cyber-
crime (Lewis, and Baker, 2013).
Conclusion
This research paper is completely based on the cyber-crimes and their impacts and with
the help of this paper; readers can enhance their knowledge in the area of cyber-attacks.
Cyber-crime is one of the biggest challenges faced many companies and consumers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TRENDS IN CYBERCRIME
8
because of lack of security. This paper evaluated the issue of cyber-crimes and spam and
also provided mitigation tools to reduce the rate of cybercrimes. The consumer should
ensure that they use only authorized websites and connectivity and turn on security
tools to control and manage the spam mails or messages from their computer networks.
8
because of lack of security. This paper evaluated the issue of cyber-crimes and spam and
also provided mitigation tools to reduce the rate of cybercrimes. The consumer should
ensure that they use only authorized websites and connectivity and turn on security
tools to control and manage the spam mails or messages from their computer networks.

TRENDS IN CYBERCRIME
9
References
Biggs, S. and Vidalis, S., (2009) Cloud computing: The impact on digital forensic
investigations. In Internet Technology and Secured Transactions, 2009. ICITST 2009.
International Conference for, 12(2), pp. 1-6.
Dunn Cavelty, M., (2013) From cyber-bombs to political fallout: Threat representations
with an impact in the cyber-security discourse. International Studies Review, 15(1),
pp.105-122.
Holt, T.J. and Bossler, A.M., (2008) Examining the applicability of lifestyle-routine
activities theory for cybercrime victimization. Deviant Behavior, 30(1), pp.1-25.
Katos, V. and Bednar, P.M., (2008) A cyber-crime investigation framework. Computer
Standards & Interfaces, 30(4), pp.223-228.
Kshetri, N., (2010) The global cybercrime industry: economic, institutional and strategic
perspectives. Springer Science & Business Media.
Lagazio, M., Sherif, N. and Cushman, M., (2014) A multi-level approach to understanding
the impact of cybercrime on the financial sector. Computers & Security, 45(2), pp.58-74.
Lewis, J. and Baker, S., (2013) The economic impact of cybercrime and cyber espionage.
McAfee.
Liang, B. and Lu, H., (2010) Internet development, censorship, and cyber crimes in
China. Journal of Contemporary Criminal Justice, 26(1), pp.103-120.
McGuire, M. and Dowling, S., (2013) Cyber crime: A review of the evidence. Summary of
key findings and implications. Home Office Research report, 75(5), pp. 12-14.
Saini, H., Rao, Y.S. and Panda, T.C., (2012) Cyber-crimes and their impacts: A
review. International Journal of Engineering Research and Applications, 2(2), pp.202-
209.
Salifu, A., (2008) The impact of internet crime on development. Journal of Financial
Crime, 15(4), pp.432-443.
9
References
Biggs, S. and Vidalis, S., (2009) Cloud computing: The impact on digital forensic
investigations. In Internet Technology and Secured Transactions, 2009. ICITST 2009.
International Conference for, 12(2), pp. 1-6.
Dunn Cavelty, M., (2013) From cyber-bombs to political fallout: Threat representations
with an impact in the cyber-security discourse. International Studies Review, 15(1),
pp.105-122.
Holt, T.J. and Bossler, A.M., (2008) Examining the applicability of lifestyle-routine
activities theory for cybercrime victimization. Deviant Behavior, 30(1), pp.1-25.
Katos, V. and Bednar, P.M., (2008) A cyber-crime investigation framework. Computer
Standards & Interfaces, 30(4), pp.223-228.
Kshetri, N., (2010) The global cybercrime industry: economic, institutional and strategic
perspectives. Springer Science & Business Media.
Lagazio, M., Sherif, N. and Cushman, M., (2014) A multi-level approach to understanding
the impact of cybercrime on the financial sector. Computers & Security, 45(2), pp.58-74.
Lewis, J. and Baker, S., (2013) The economic impact of cybercrime and cyber espionage.
McAfee.
Liang, B. and Lu, H., (2010) Internet development, censorship, and cyber crimes in
China. Journal of Contemporary Criminal Justice, 26(1), pp.103-120.
McGuire, M. and Dowling, S., (2013) Cyber crime: A review of the evidence. Summary of
key findings and implications. Home Office Research report, 75(5), pp. 12-14.
Saini, H., Rao, Y.S. and Panda, T.C., (2012) Cyber-crimes and their impacts: A
review. International Journal of Engineering Research and Applications, 2(2), pp.202-
209.
Salifu, A., (2008) The impact of internet crime on development. Journal of Financial
Crime, 15(4), pp.432-443.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TRENDS IN CYBERCRIME
10
Wall*, D.S., (2008) Cybercrime, media and insecurity: The shaping of public perceptions
of cybercrime. International Review of Law, Computers & Technology, 22(1-2), pp.45-63.
Wall, D., 2007. Cybercrime: The transformation of crime in the information age (Vol. 4).
Polity.
10
Wall*, D.S., (2008) Cybercrime, media and insecurity: The shaping of public perceptions
of cybercrime. International Review of Law, Computers & Technology, 22(1-2), pp.45-63.
Wall, D., 2007. Cybercrime: The transformation of crime in the information age (Vol. 4).
Polity.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





