Cybercrime Presentation: Types, Prevention, Impact, and Classification
VerifiedAdded on 2023/01/12
|12
|732
|28
Presentation
AI Summary
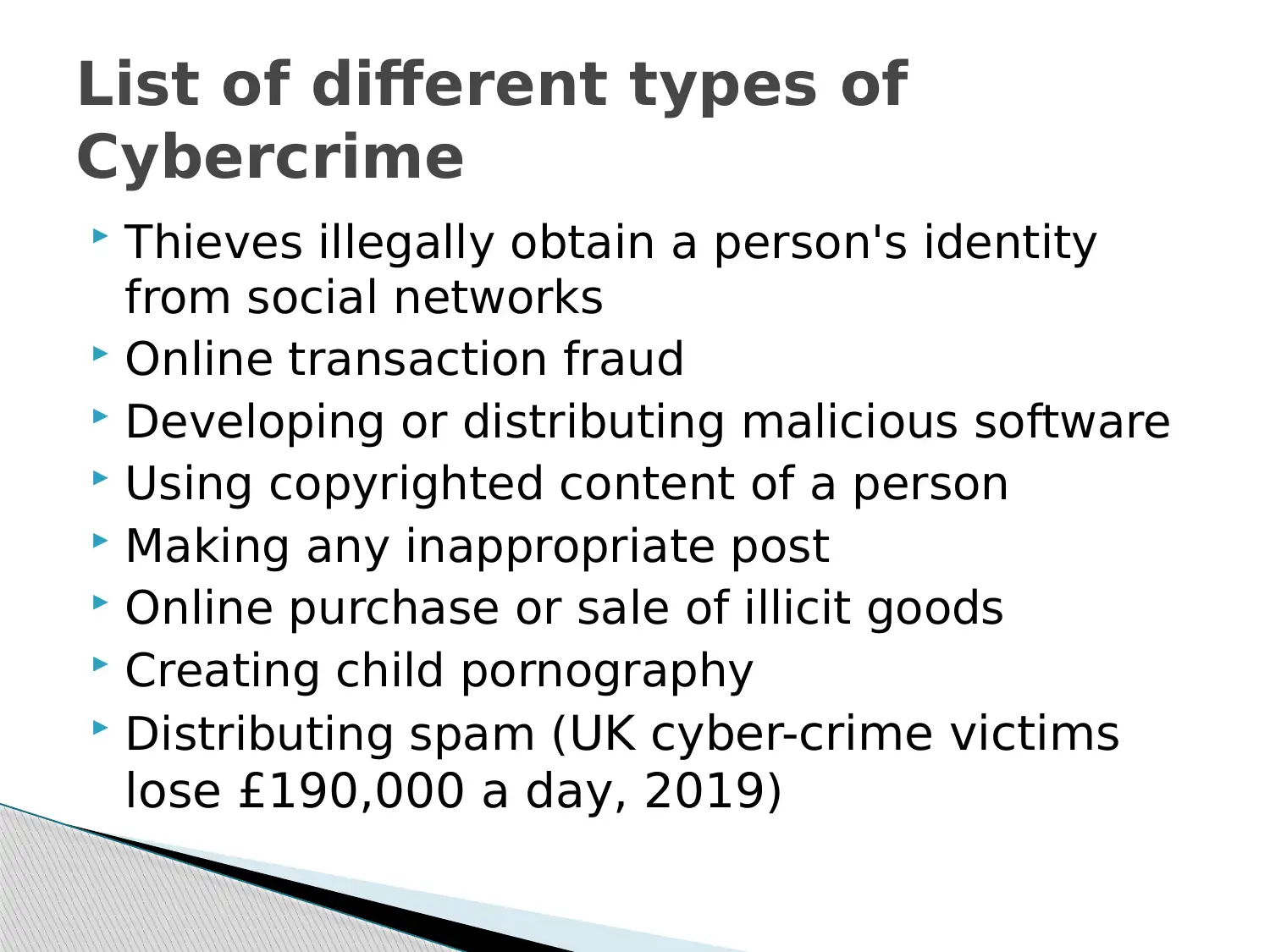
This presentation provides a comprehensive overview of cybercrime, addressing its increasing prevalence in the digital age. It begins with an introduction to computer and internet systems, explaining their role in the context of cybercrime. The presentation then defines cybercrime and discusses its various types, including cyberpiracy, cybertrespass, and cybersabotage. It also covers specific examples such as identity theft, online transaction fraud, and the distribution of malicious software. The classification of cybercrime, including crimes against individuals, organizations, and society, is also discussed. The presentation concludes by offering practical prevention strategies, such as educating oneself, avoiding suspicious websites, and using firewall software. References to relevant sources are provided to support the information presented. This assignment is designed to educate individuals about the risks associated with cybercrime and how to protect themselves.
1 out of 12


















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)