Detailed Analysis of Security Principles in Cybersecurity Report
VerifiedAdded on 2023/04/03
|8
|1397
|436
Report
AI Summary
This report delves into the core principles of information security: confidentiality, integrity, and availability (CIA). It examines a specific cyber attack on an Australian defense firm, where sensitive data related to military projects was stolen. The report analyzes the motives behind the attack, the vulnerabilities exploited, and the potential impact on national security. It also explores risk assessment, incident response plans, and strategies for mitigating future cyber threats, including recommendations for improving security measures related to people, processes, and technology. The report also includes a response plan for cyber attacks. The report provides a comprehensive overview of the security principles and defense strategies.

Running head: SECURITY PRINCIPLES
SECURITY PRINCIPLES
Name of the Student
Name of the University
Author Note:
SECURITY PRINCIPLES
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY PRINCIPLES
Table of Contents
Answer to Question 1..........................................................................................................2
Answer to Question 2..........................................................................................................2
Answer to Question 3..........................................................................................................3
Answer to Question 4..........................................................................................................4
Answer to Question 5..........................................................................................................4
References............................................................................................................................6
Table of Contents
Answer to Question 1..........................................................................................................2
Answer to Question 2..........................................................................................................2
Answer to Question 3..........................................................................................................3
Answer to Question 4..........................................................................................................4
Answer to Question 5..........................................................................................................4
References............................................................................................................................6

2SECURITY PRINCIPLES
Answer to Question 1
Confidentiality, integrity and Availability are known to be CIA trio which is known to be
building block of information security. Hacked Australia defence lost around 30 GB of
commercially available documents for projects like Joint Strike program and complete design of
Australian ship (Crozier et al., 2019). Any kind of attack will ultimately lead to compromising
with all three given components. Depending on the components which are compromised can
easily result in proper security control which has been designed properly.
Confidentiality is all about understanding the fact that something is secret and not
supposed to be completely disclosed to any of the unintended people. Australian government did
not disclose the complete hack on Tuesday and came up with far scant details (Gupta, Agrawal
and Yamaguchi, 2016). Confidentiality mainly aims to ensure the fact all the sensitive
information is accessed by authorized person (Buczak and Guven 2015). Integrity highlights the
fact that all the transmitted data given by sender is exactly received by receiver and there is no
kind of alternation in it. Availability ensures that information is available to only the authorized
parties.
This particular attack on the three important aspects of information security like
confidentiality, Integrity and availability (O’HANLON 2019). In attack, the hacker stole some of
the detail information about the submarine killer plane. The whole attack is being carried out by
either advanced persistent threat or even national state group.
Answer to Question 2
In this attack, some of the vital and sensitive about the Australian joint fire strike fighter
program were stolen. Having a proper idea behind the targeted attack is very much vital as it
Answer to Question 1
Confidentiality, integrity and Availability are known to be CIA trio which is known to be
building block of information security. Hacked Australia defence lost around 30 GB of
commercially available documents for projects like Joint Strike program and complete design of
Australian ship (Crozier et al., 2019). Any kind of attack will ultimately lead to compromising
with all three given components. Depending on the components which are compromised can
easily result in proper security control which has been designed properly.
Confidentiality is all about understanding the fact that something is secret and not
supposed to be completely disclosed to any of the unintended people. Australian government did
not disclose the complete hack on Tuesday and came up with far scant details (Gupta, Agrawal
and Yamaguchi, 2016). Confidentiality mainly aims to ensure the fact all the sensitive
information is accessed by authorized person (Buczak and Guven 2015). Integrity highlights the
fact that all the transmitted data given by sender is exactly received by receiver and there is no
kind of alternation in it. Availability ensures that information is available to only the authorized
parties.
This particular attack on the three important aspects of information security like
confidentiality, Integrity and availability (O’HANLON 2019). In attack, the hacker stole some of
the detail information about the submarine killer plane. The whole attack is being carried out by
either advanced persistent threat or even national state group.
Answer to Question 2
In this attack, some of the vital and sensitive about the Australian joint fire strike fighter
program were stolen. Having a proper idea behind the targeted attack is very much vital as it
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SECURITY PRINCIPLES
helps the analysing the target of attackers (Bada, Sasse and Nurse, 2019). It is very much
important to have an idea concerning motives which can help the idea of protecting and ways of
protecting. The main notion behind this attack is list of political factors which encouraged the
attacker to steal some of the vital data. In this attack, politics may also encourage the attacker to
take down the whole thing on their own hands. The main notion behind this attack is the theft of
information. Attacker focus on acquiring information that is owned by the target and is
completely stored in the target network (Carr, 2016). The whole of the information is in the form
of military information and intellectual property of the military. Apart from this, there was
another target of the hacker is all about monitoring the activities of the available information
which can compromise with the national security (Knowles et al. 2015). Also, hackers may use
the collected data for destruction, defamation or even blacking the whole Australian government.
Defence firm need to understand both legal and ethical issues that which is needed by
corporation. It needs to be taken into account at the instance of use of the offensive cyberspace.
Answer to Question 3
Hacker in this attack stole information concerning Australian Joint Strike fighter program
and another military test. The whole thing has come into picture for the breach of the defence
contractor (Crozier et al., 2019). Various officials of Australian intelligence agency come up
with information that various kind of technical information with respects military equipments
were stolen. All the required details concerning smart bombs and Joint strike fighter and
Poseidon patrol were stolen. The most common approach behind the attacking modelling and
assessment of impact is completely based on representing behaviours and generating graph (Lee,
Bagheri and Jin, 2016). The mere focus is all about making a calculation of security metrics and
providing procedure for risk analysis. Some of the major aspects are all about achieving real time
helps the analysing the target of attackers (Bada, Sasse and Nurse, 2019). It is very much
important to have an idea concerning motives which can help the idea of protecting and ways of
protecting. The main notion behind this attack is list of political factors which encouraged the
attacker to steal some of the vital data. In this attack, politics may also encourage the attacker to
take down the whole thing on their own hands. The main notion behind this attack is the theft of
information. Attacker focus on acquiring information that is owned by the target and is
completely stored in the target network (Carr, 2016). The whole of the information is in the form
of military information and intellectual property of the military. Apart from this, there was
another target of the hacker is all about monitoring the activities of the available information
which can compromise with the national security (Knowles et al. 2015). Also, hackers may use
the collected data for destruction, defamation or even blacking the whole Australian government.
Defence firm need to understand both legal and ethical issues that which is needed by
corporation. It needs to be taken into account at the instance of use of the offensive cyberspace.
Answer to Question 3
Hacker in this attack stole information concerning Australian Joint Strike fighter program
and another military test. The whole thing has come into picture for the breach of the defence
contractor (Crozier et al., 2019). Various officials of Australian intelligence agency come up
with information that various kind of technical information with respects military equipments
were stolen. All the required details concerning smart bombs and Joint strike fighter and
Poseidon patrol were stolen. The most common approach behind the attacking modelling and
assessment of impact is completely based on representing behaviours and generating graph (Lee,
Bagheri and Jin, 2016). The mere focus is all about making a calculation of security metrics and
providing procedure for risk analysis. Some of the major aspects are all about achieving real time
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURITY PRINCIPLES
mode and analysis of event. Apart from this, there were event analysis, mechanism and lastly
security and assessment of impact. For reducing the impact of the graph generation and its
security evaluation a proper approach can be applied on it (O’HANLON 2019). For this
particular attack, the complete architecture of cyber-attack modelling and impact assessment
component (CAMIAC) has been given out.
Vulnerability in cyber-attack security can be stated as the flaws in the whole system. It
can be leave the whole thing easily open to attack. In other words, vulnerability can be stated as a
weakness in the system which leaves the information exposed to the threat.
Answer to Question 4
The overall cost of cyber-security is high all the time, and all the required incidents take
around huge for overall discovery (Buczak and Guven 2015). Advanced persistent threats are a
continuous hacking method which is needed for gaining access to the system. It can remain
inside the system before detection of intrusion (Crozier et al., 2019). Cyber-attacks of this kind
can easily cause huge amount of damage to the security of the whole nation. Impact nation tends
to encounter loss of overall assets, business, fines and remediation loss.
People: Every employee of the defence firm needs to be completely aware of their role in
the organization, which will help them in prevention and reduction of threats (Gupta, Agrawal
and Yamaguchi, 2016). It is the dedication from staff end to the cyber-security, so they keep
themselves updated.
Processes: It is known to be as one of the important steps which is needed for
communication within the organization. It is all about documenting the whole processes which
are clearly defined with proper roles and responsibilities (Bada, Sasse and Nurse, 2019). It is all
about understanding the procedure that needs to be followed.
mode and analysis of event. Apart from this, there were event analysis, mechanism and lastly
security and assessment of impact. For reducing the impact of the graph generation and its
security evaluation a proper approach can be applied on it (O’HANLON 2019). For this
particular attack, the complete architecture of cyber-attack modelling and impact assessment
component (CAMIAC) has been given out.
Vulnerability in cyber-attack security can be stated as the flaws in the whole system. It
can be leave the whole thing easily open to attack. In other words, vulnerability can be stated as a
weakness in the system which leaves the information exposed to the threat.
Answer to Question 4
The overall cost of cyber-security is high all the time, and all the required incidents take
around huge for overall discovery (Buczak and Guven 2015). Advanced persistent threats are a
continuous hacking method which is needed for gaining access to the system. It can remain
inside the system before detection of intrusion (Crozier et al., 2019). Cyber-attacks of this kind
can easily cause huge amount of damage to the security of the whole nation. Impact nation tends
to encounter loss of overall assets, business, fines and remediation loss.
People: Every employee of the defence firm needs to be completely aware of their role in
the organization, which will help them in prevention and reduction of threats (Gupta, Agrawal
and Yamaguchi, 2016). It is the dedication from staff end to the cyber-security, so they keep
themselves updated.
Processes: It is known to be as one of the important steps which is needed for
communication within the organization. It is all about documenting the whole processes which
are clearly defined with proper roles and responsibilities (Bada, Sasse and Nurse, 2019). It is all
about understanding the procedure that needs to be followed.

5SECURITY PRINCIPLES
Technology: Organization measures are known to be very part of the whole cyber-
security, which has technical controls in it (Carr, 2016). It starts from gain control for antivirus
software where technology can be easily deployed for mitigating various kind of security risks.
Answer to Question 5
Australian defence needs to come with cyber incidence response plan. The capabilities
are completely weighted for short term responses along with IT-issues. The mitigation plan tends
to impact the cyber incident and keeping a reach of crisis proportion. Various kind of cyber crisis
can be easily mitigated at the time incident before and during the unfolds (Crozier et al., 2019).
There is a need for effective address for the crisis management plan for making response and
recovery. Every phase of lifecycle opportunities’ need to protect the given firm for any kind of
risk, damage and overall cost. It is all about emanating any kind of damage arising from the
incident. The mere focus is all about defending the organization (Knowles et al. 2015).
Management of the defence firm can either escalate the given incident and poor kind of response.
The mere response is tackling the crisis of the cyber-security breach.
The response plan for this attack can be prepared by taking following steps like
Preparation.
Proper analysis and detection.
Recovery and containment.
Post- Incident activity.
Technology: Organization measures are known to be very part of the whole cyber-
security, which has technical controls in it (Carr, 2016). It starts from gain control for antivirus
software where technology can be easily deployed for mitigating various kind of security risks.
Answer to Question 5
Australian defence needs to come with cyber incidence response plan. The capabilities
are completely weighted for short term responses along with IT-issues. The mitigation plan tends
to impact the cyber incident and keeping a reach of crisis proportion. Various kind of cyber crisis
can be easily mitigated at the time incident before and during the unfolds (Crozier et al., 2019).
There is a need for effective address for the crisis management plan for making response and
recovery. Every phase of lifecycle opportunities’ need to protect the given firm for any kind of
risk, damage and overall cost. It is all about emanating any kind of damage arising from the
incident. The mere focus is all about defending the organization (Knowles et al. 2015).
Management of the defence firm can either escalate the given incident and poor kind of response.
The mere response is tackling the crisis of the cyber-security breach.
The response plan for this attack can be prepared by taking following steps like
Preparation.
Proper analysis and detection.
Recovery and containment.
Post- Incident activity.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
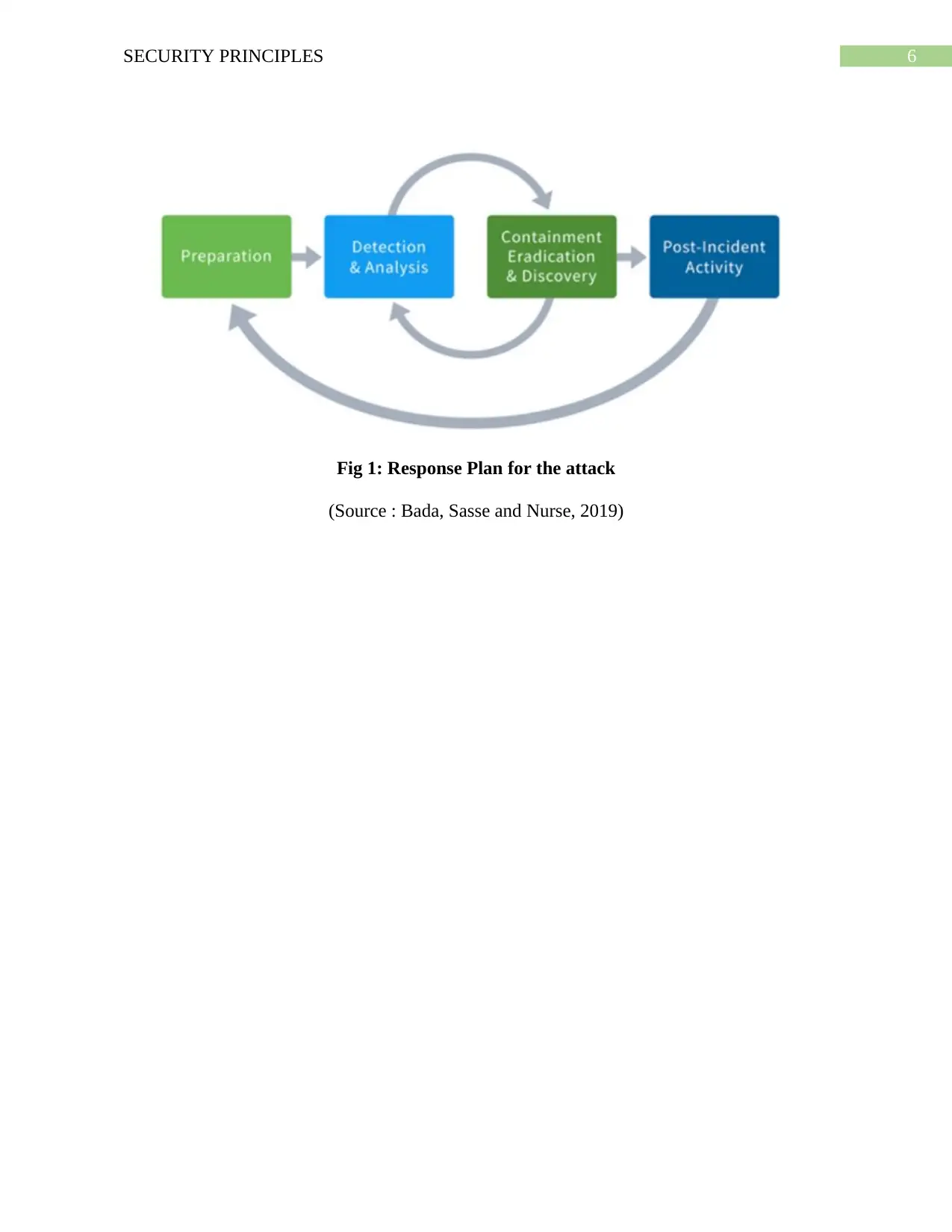
6SECURITY PRINCIPLES
Fig 1: Response Plan for the attack
(Source : Bada, Sasse and Nurse, 2019)
Fig 1: Response Plan for the attack
(Source : Bada, Sasse and Nurse, 2019)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SECURITY PRINCIPLES
References
Bada, M., Sasse, A. M., and Nurse, J. R. (2019). Cyber security awareness campaigns: Why do
they fail to change behaviour?. arXiv preprint arXiv:1901.02672.
Buczak, A. L., and Guven, E. (2015). A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), 1153-
1176.
Carr, M. (2016). Public–private partnerships in national cyber-security strategies. International
Affairs, 92(1), 43-62.
Crozier, R., Corner, S., Crozier, R. and Corner, S. (2019). Hacked Aussie Defence firm lost
fighter jet, bomb, ship plans. [online] iTnews. Available at:
https://www.itnews.com.au/news/hacked-aussie-defence-firm-lost-fighter-jet-bomb-ship-plans-
475211 [Accessed 1 Jun. 2019].
Gupta, B., Agrawal, D. P., and Yamaguchi, S. (Eds.). (2016). Handbook of research on modern
cryptographic solutions for computer and cyber security. IGI global.
Knowles, W., Prince, D., Hutchison, D., Disso, J. F. P., and Jones, K. (2015). A survey of cyber
security management in industrial control systems. International journal of critical
infrastructure protection, 9, 52-80.
Lee, J., Bagheri, B., and Jin, C. (2016). Introduction to cyber manufacturing. Manufacturing
Letters, 8, 11-15.
O’HANLON, M. I. C. H. A. E. L. (2019). Forecasting change in military technology, 2020-
2040. MILITARY TECHNOLOGY, 2020, 2040.
References
Bada, M., Sasse, A. M., and Nurse, J. R. (2019). Cyber security awareness campaigns: Why do
they fail to change behaviour?. arXiv preprint arXiv:1901.02672.
Buczak, A. L., and Guven, E. (2015). A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), 1153-
1176.
Carr, M. (2016). Public–private partnerships in national cyber-security strategies. International
Affairs, 92(1), 43-62.
Crozier, R., Corner, S., Crozier, R. and Corner, S. (2019). Hacked Aussie Defence firm lost
fighter jet, bomb, ship plans. [online] iTnews. Available at:
https://www.itnews.com.au/news/hacked-aussie-defence-firm-lost-fighter-jet-bomb-ship-plans-
475211 [Accessed 1 Jun. 2019].
Gupta, B., Agrawal, D. P., and Yamaguchi, S. (Eds.). (2016). Handbook of research on modern
cryptographic solutions for computer and cyber security. IGI global.
Knowles, W., Prince, D., Hutchison, D., Disso, J. F. P., and Jones, K. (2015). A survey of cyber
security management in industrial control systems. International journal of critical
infrastructure protection, 9, 52-80.
Lee, J., Bagheri, B., and Jin, C. (2016). Introduction to cyber manufacturing. Manufacturing
Letters, 8, 11-15.
O’HANLON, M. I. C. H. A. E. L. (2019). Forecasting change in military technology, 2020-
2040. MILITARY TECHNOLOGY, 2020, 2040.
1 out of 8
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.