University Cybersecurity: Risk Assessment and Threat Analysis
VerifiedAdded on 2023/06/09
|9
|2039
|122
Report
AI Summary
This report on cybersecurity begins by emphasizing the importance of risk assessment as a crucial first step in establishing a robust cybersecurity system within a university setting. It outlines the process of identifying critical assets, such as firewalls, intrusion detection systems, and encryption systems, and employs a WFA table to assess their impact on security, reputation, and cost. The report then delves into threat identification, differentiating between threats, attacks, incidents, hazards, and viruses, using the Yahoo data breach as a case study to illustrate potential vulnerabilities. Furthermore, the report assesses various threats, including DDoS attacks, web application attacks, and brute force attacks, evaluating their potential impact on the confidentiality, integrity, and availability of a university website. It concludes by providing a ranked analysis of these threats and their implications for the university's digital assets, suggesting preventative measures to mitigate potential damage.

Running head: CYBERSECURITY
Cybersecurity
Name of the Student
Name of the University
Author Note
Cybersecurity
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBERSECURITY
Table of Contents
Task 1: The importance of risk assessment................................................................................2
Task 2: Critical asset identification............................................................................................3
WFA Table:............................................................................................................................3
Task 3: Threat identification......................................................................................................4
Task 4: Threat assessment..........................................................................................................5
References:.................................................................................................................................8
Table of Contents
Task 1: The importance of risk assessment................................................................................2
Task 2: Critical asset identification............................................................................................3
WFA Table:............................................................................................................................3
Task 3: Threat identification......................................................................................................4
Task 4: Threat assessment..........................................................................................................5
References:.................................................................................................................................8

2CYBERSECURITY
Task 1: The importance of risk assessment
The risk assessment describes that it a systematic process which is used to evaluate
potential risks which may or may not be involved with a project or with a system setup
(Covello and Merkhoher 2013). To implement a proper cyber security system in the
university the most critical step needed to overcome is the risk assessment step. This is
considered as the most vital step because only this can determine if the chosen cybersecurity
implementation is perfect for the university or not. By performing a risk assessment of
cybersecurity, the university can save the time, resources and efforts needed by the
implementation program of the cybersecurity and can gain enough knowledge how to defend
against the external threats of the cybersecurity program.
The common problem of every risk assessment is the data interpretation. This
common problem is faced by every organization or community while performing a risk
assessment because the amount of the information is increasing with the time and this type of
data does not have any sequential order rather than it just gathered randomly. As the total
amount of data is getting higher day by day the organization or the community face
challenges while interpreting this huge amount of data (Cho et al. 2015). Predicting the
associated risks with the cyber security is tough with this large amount of data. Interpreting
this data can be a very problematic task even for the large companies.
The risk assessment results can help the university to develop and manage a proper
cybersecurity system by providing a list of precautions that need to be followed in that
circumstances. This precautions can include automatic patching system for OS, revised
firewall rules, controlling network access for each and every device, limiting administrative
power and many more. Also, the risk assessment can affect the business decision by
Task 1: The importance of risk assessment
The risk assessment describes that it a systematic process which is used to evaluate
potential risks which may or may not be involved with a project or with a system setup
(Covello and Merkhoher 2013). To implement a proper cyber security system in the
university the most critical step needed to overcome is the risk assessment step. This is
considered as the most vital step because only this can determine if the chosen cybersecurity
implementation is perfect for the university or not. By performing a risk assessment of
cybersecurity, the university can save the time, resources and efforts needed by the
implementation program of the cybersecurity and can gain enough knowledge how to defend
against the external threats of the cybersecurity program.
The common problem of every risk assessment is the data interpretation. This
common problem is faced by every organization or community while performing a risk
assessment because the amount of the information is increasing with the time and this type of
data does not have any sequential order rather than it just gathered randomly. As the total
amount of data is getting higher day by day the organization or the community face
challenges while interpreting this huge amount of data (Cho et al. 2015). Predicting the
associated risks with the cyber security is tough with this large amount of data. Interpreting
this data can be a very problematic task even for the large companies.
The risk assessment results can help the university to develop and manage a proper
cybersecurity system by providing a list of precautions that need to be followed in that
circumstances. This precautions can include automatic patching system for OS, revised
firewall rules, controlling network access for each and every device, limiting administrative
power and many more. Also, the risk assessment can affect the business decision by
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBERSECURITY
determining the potential changes or the adjustments needed by the organization. Following a
proper risk, assessment result can help the university to secure its cybersecurity systems.
Task 2: Critical asset identification
An information asset can be considered as a body of knowledge which is used to
manage and organize a single entity (Bhansali 2013). The information asset can be classified
according to any type of criteria. As an example, the data of an information asset can be
broken down by following the topics at the time of the creation.
An information asset can become a critical asset for the organization based on their
value to the organization. For a cyber-security case, the critical asset of the program becomes
the firewall and the intrusion detection system which is also capable of preventing the
intuition and also the basic antivirus programs and the encryption system is a part of critical
assets information. In the following section, five question will be deduced which will address
the most critical information asset of the university, and the questions are,
Which information assets cost the most for the replacement?
Which information asset has the highest profitability for the university?
Which information assets is the most costly in term of protection of it?
Which information assets generates most of the revenue for the university?
Which asset’s loss can be the great compromise for the university?
WFA Table:
Information
Asset
Impact on
security (30)
Impact on
maintenance
cost (40)
Impact on
reputation (30)
Weighted Score
Replace cost 0.8 0.9 0.5 75
Profitability 0.8 0.9 0.6 78
determining the potential changes or the adjustments needed by the organization. Following a
proper risk, assessment result can help the university to secure its cybersecurity systems.
Task 2: Critical asset identification
An information asset can be considered as a body of knowledge which is used to
manage and organize a single entity (Bhansali 2013). The information asset can be classified
according to any type of criteria. As an example, the data of an information asset can be
broken down by following the topics at the time of the creation.
An information asset can become a critical asset for the organization based on their
value to the organization. For a cyber-security case, the critical asset of the program becomes
the firewall and the intrusion detection system which is also capable of preventing the
intuition and also the basic antivirus programs and the encryption system is a part of critical
assets information. In the following section, five question will be deduced which will address
the most critical information asset of the university, and the questions are,
Which information assets cost the most for the replacement?
Which information asset has the highest profitability for the university?
Which information assets is the most costly in term of protection of it?
Which information assets generates most of the revenue for the university?
Which asset’s loss can be the great compromise for the university?
WFA Table:
Information
Asset
Impact on
security (30)
Impact on
maintenance
cost (40)
Impact on
reputation (30)
Weighted Score
Replace cost 0.8 0.9 0.5 75
Profitability 0.8 0.9 0.6 78
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CYBERSECURITY
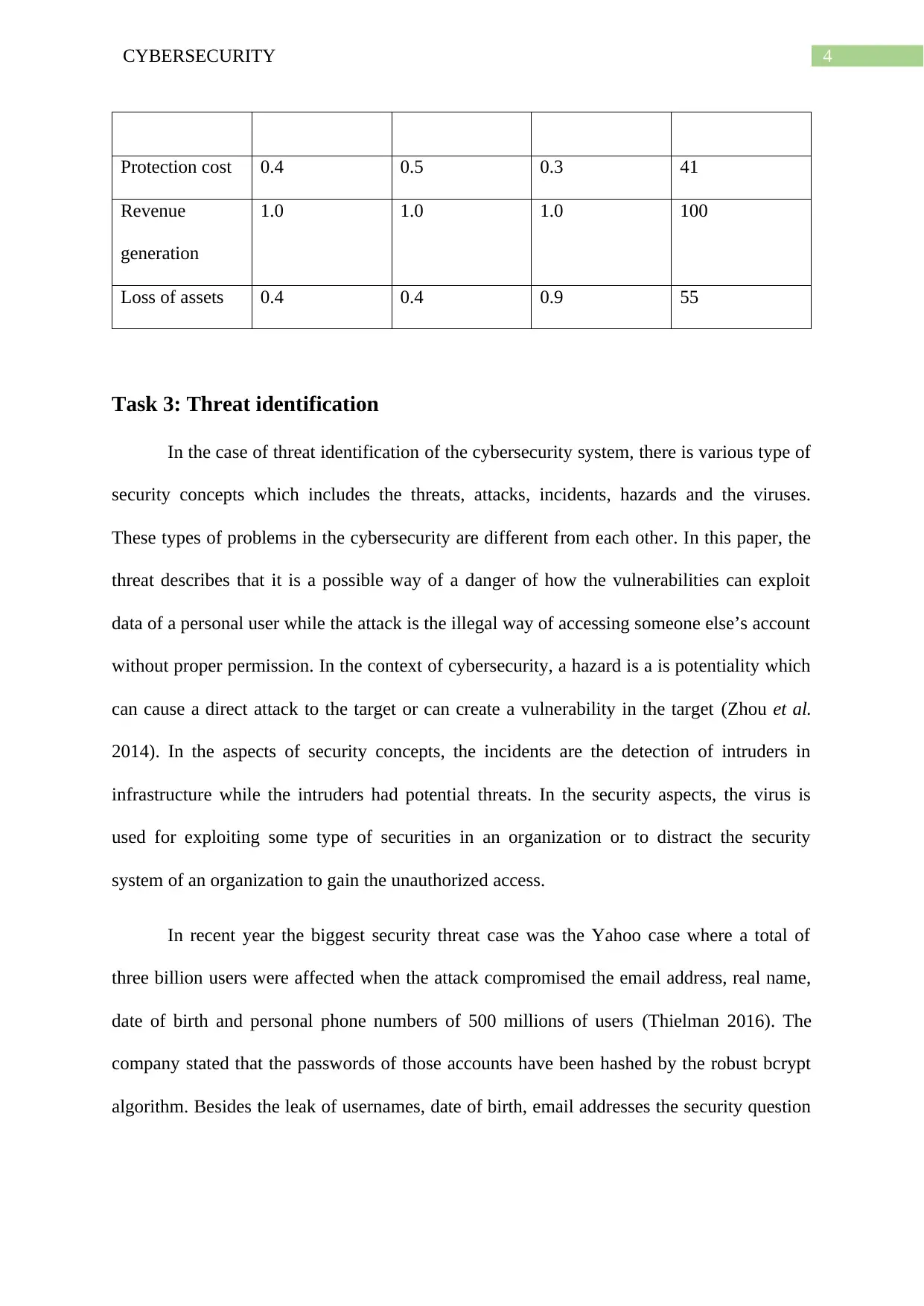
Protection cost 0.4 0.5 0.3 41
Revenue
generation
1.0 1.0 1.0 100
Loss of assets 0.4 0.4 0.9 55
Task 3: Threat identification
In the case of threat identification of the cybersecurity system, there is various type of
security concepts which includes the threats, attacks, incidents, hazards and the viruses.
These types of problems in the cybersecurity are different from each other. In this paper, the
threat describes that it is a possible way of a danger of how the vulnerabilities can exploit
data of a personal user while the attack is the illegal way of accessing someone else’s account
without proper permission. In the context of cybersecurity, a hazard is a is potentiality which
can cause a direct attack to the target or can create a vulnerability in the target (Zhou et al.
2014). In the aspects of security concepts, the incidents are the detection of intruders in
infrastructure while the intruders had potential threats. In the security aspects, the virus is
used for exploiting some type of securities in an organization or to distract the security
system of an organization to gain the unauthorized access.
In recent year the biggest security threat case was the Yahoo case where a total of
three billion users were affected when the attack compromised the email address, real name,
date of birth and personal phone numbers of 500 millions of users (Thielman 2016). The
company stated that the passwords of those accounts have been hashed by the robust bcrypt
algorithm. Besides the leak of usernames, date of birth, email addresses the security question
Protection cost 0.4 0.5 0.3 41
Revenue
generation
1.0 1.0 1.0 100
Loss of assets 0.4 0.4 0.9 55
Task 3: Threat identification
In the case of threat identification of the cybersecurity system, there is various type of
security concepts which includes the threats, attacks, incidents, hazards and the viruses.
These types of problems in the cybersecurity are different from each other. In this paper, the
threat describes that it is a possible way of a danger of how the vulnerabilities can exploit
data of a personal user while the attack is the illegal way of accessing someone else’s account
without proper permission. In the context of cybersecurity, a hazard is a is potentiality which
can cause a direct attack to the target or can create a vulnerability in the target (Zhou et al.
2014). In the aspects of security concepts, the incidents are the detection of intruders in
infrastructure while the intruders had potential threats. In the security aspects, the virus is
used for exploiting some type of securities in an organization or to distract the security
system of an organization to gain the unauthorized access.
In recent year the biggest security threat case was the Yahoo case where a total of
three billion users were affected when the attack compromised the email address, real name,
date of birth and personal phone numbers of 500 millions of users (Thielman 2016). The
company stated that the passwords of those accounts have been hashed by the robust bcrypt
algorithm. Besides the leak of usernames, date of birth, email addresses the security question

5CYBERSECURITY
is also compromised by the Yahoo in October 2017. It is estimated that total 3 billion of users
were affected by this (Thielman 2016).
In the yahoo data breach case potential threat was detected, which was the resetting
the passwords of the users, phishing attempts and the yahoo email listening. In the resting of
the password scheme, the hackers rested the passwords to a default value, and they have used
fake websites to gather user information by using the phishing and in yahoo email listening
the hackers were easily able to read any email of users.
Task 4: Threat assessment
Considering the university website is one of the most valuable assets, the above
discussed top five security threats should not affect if the three information security
components are strong enough to prevent the attacks which are confidentiality, availability
and the integrity of the website. The components are discussed in the following section,
Confidentiality: Confidentiality elaborates that it is a function which works to protect
some confidential data of the website from being used by some unauthorised
personnel or parties. Failing to maintain the confidentiality of the data can lead to a
data breach.
Integrity: The integrity of the website defines the authenticity of a provided
information (Chen and Lee 2014). The data provided by any user of the website must
not be altered in any situation. In case of data alteration of the website or the
alteration of data provided by the user may fail to stand against a malicious attacker
which will lead the university image down globally.
Availability: The availability defines the data required by the website from the users
are accessible only by some selected authorised users. If any outsider or any hacker
get access to this data, they can alter the required data which will create a problem in
is also compromised by the Yahoo in October 2017. It is estimated that total 3 billion of users
were affected by this (Thielman 2016).
In the yahoo data breach case potential threat was detected, which was the resetting
the passwords of the users, phishing attempts and the yahoo email listening. In the resting of
the password scheme, the hackers rested the passwords to a default value, and they have used
fake websites to gather user information by using the phishing and in yahoo email listening
the hackers were easily able to read any email of users.
Task 4: Threat assessment
Considering the university website is one of the most valuable assets, the above
discussed top five security threats should not affect if the three information security
components are strong enough to prevent the attacks which are confidentiality, availability
and the integrity of the website. The components are discussed in the following section,
Confidentiality: Confidentiality elaborates that it is a function which works to protect
some confidential data of the website from being used by some unauthorised
personnel or parties. Failing to maintain the confidentiality of the data can lead to a
data breach.
Integrity: The integrity of the website defines the authenticity of a provided
information (Chen and Lee 2014). The data provided by any user of the website must
not be altered in any situation. In case of data alteration of the website or the
alteration of data provided by the user may fail to stand against a malicious attacker
which will lead the university image down globally.
Availability: The availability defines the data required by the website from the users
are accessible only by some selected authorised users. If any outsider or any hacker
get access to this data, they can alter the required data which will create a problem in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBERSECURITY
the whole system which is not a good thing for the university. Also, the availability
refers to the availability of the university website under any circumstances. The
website should be available whenever needed by any users.
The top five threats related to the university website assets are the DDoS attacks, Web
application attacks, SSL induced security blind spot, Brute force attack and the DNS
infrastructure. Assessing the impact of the threats, it will be discussed according to the rank
of impact which are,
1. DDoS Attack: The University can face heavy damage if the DDoS is implemented
successfully as it can create a loophole in the security by slowing down the
communication speed between server and client (Wang et al. 2015).
2. Web application attack: The cybercriminals always tried to push a SQL injection in
the server to steal the confidential data which can be used for some personal benefits.
A successful web application attack can lead the university to lose some of its very
important data.
3. DNS Infrastructure: The DNS attack is popular in the present situation as this attack
let the hacker easily disconnect the victims from the internet. By disconnecting them
from the internet, the hacker can now control the victim's network and can hack him
easily. The DNS is not the ultimate hacking technique used by the hackers, but still, it
can give some tough time to the university.
4. SSL induced blind spot: To stop the spreading of the viruses from one system to
another the university needs to inspect every traffic. Unfortunately, the hackers are
escaping these criteria by SSL induced blind spot which allows the free movement of
malware over the internet. This type of malware can damage the assets of the
university if proper action not taken.
the whole system which is not a good thing for the university. Also, the availability
refers to the availability of the university website under any circumstances. The
website should be available whenever needed by any users.
The top five threats related to the university website assets are the DDoS attacks, Web
application attacks, SSL induced security blind spot, Brute force attack and the DNS
infrastructure. Assessing the impact of the threats, it will be discussed according to the rank
of impact which are,
1. DDoS Attack: The University can face heavy damage if the DDoS is implemented
successfully as it can create a loophole in the security by slowing down the
communication speed between server and client (Wang et al. 2015).
2. Web application attack: The cybercriminals always tried to push a SQL injection in
the server to steal the confidential data which can be used for some personal benefits.
A successful web application attack can lead the university to lose some of its very
important data.
3. DNS Infrastructure: The DNS attack is popular in the present situation as this attack
let the hacker easily disconnect the victims from the internet. By disconnecting them
from the internet, the hacker can now control the victim's network and can hack him
easily. The DNS is not the ultimate hacking technique used by the hackers, but still, it
can give some tough time to the university.
4. SSL induced blind spot: To stop the spreading of the viruses from one system to
another the university needs to inspect every traffic. Unfortunately, the hackers are
escaping these criteria by SSL induced blind spot which allows the free movement of
malware over the internet. This type of malware can damage the assets of the
university if proper action not taken.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBERSECURITY
5. Brute force attack: Often the hackers use the brute force attack to guess a password
for some internal protected data which can hamper the critical assets of the university
(Cho, Jeong and Park 2015). The success rate of brute force attack is very much low
and also takes a very long time but in case of a successful password guess this attack
can bring huge loss to the critical assets of the university.
5. Brute force attack: Often the hackers use the brute force attack to guess a password
for some internal protected data which can hamper the critical assets of the university
(Cho, Jeong and Park 2015). The success rate of brute force attack is very much low
and also takes a very long time but in case of a successful password guess this attack
can bring huge loss to the critical assets of the university.

8CYBERSECURITY
References:
Bhansali, N. ed., 2013. Data Governance: Creating Value from Information Assets. CRC
Press.
Chen, H.C. and Lee, P.P., 2014. Enabling data integrity protection in regenerating-coding-
based cloud storage: Theory and implementation. IEEE transactions on parallel and
distributed systems, 25(2), pp.407-416.
Cho, J.S., Jeong, Y.S. and Park, S.O., 2015. Consideration on the brute-force attack cost and
retrieval cost: A hash-based radio-frequency identification (RFID) tag mutual authentication
protocol. Computers & Mathematics with Applications, 69(1), pp.58-65.
Cho, Y., Ahmed, A., Islam, A. and Kim, S., 2015. Developments in FT‐ICR MS
instrumentation, ionization techniques, and data interpretation methods for
petroleomics. Mass spectrometry reviews, 34(2), pp.248-263.
Covello, V.T. and Merkhoher, M.W., 2013. Risk assessment methods: approaches for
assessing health and environmental risks. Springer Science & Business Media.
Thielman, S., 2016. Yahoo hack: 1bn accounts compromised by biggest data breach in
history. The Guardian, 15, p.2016.
Wang, B., Zheng, Y., Lou, W. and Hou, Y.T., 2015. DDoS attack protection in the era of
cloud computing and software-defined networking. Computer Networks, 81, pp.308-319.
Zhou, X., Lee, Y., Zhang, N., Naveed, M. and Wang, X., 2014, May. The peril of
fragmentation: Security hazards in android device driver customizations. In Security and
Privacy (SP), 2014 IEEE Symposium on (pp. 409-423). IEEE.
References:
Bhansali, N. ed., 2013. Data Governance: Creating Value from Information Assets. CRC
Press.
Chen, H.C. and Lee, P.P., 2014. Enabling data integrity protection in regenerating-coding-
based cloud storage: Theory and implementation. IEEE transactions on parallel and
distributed systems, 25(2), pp.407-416.
Cho, J.S., Jeong, Y.S. and Park, S.O., 2015. Consideration on the brute-force attack cost and
retrieval cost: A hash-based radio-frequency identification (RFID) tag mutual authentication
protocol. Computers & Mathematics with Applications, 69(1), pp.58-65.
Cho, Y., Ahmed, A., Islam, A. and Kim, S., 2015. Developments in FT‐ICR MS
instrumentation, ionization techniques, and data interpretation methods for
petroleomics. Mass spectrometry reviews, 34(2), pp.248-263.
Covello, V.T. and Merkhoher, M.W., 2013. Risk assessment methods: approaches for
assessing health and environmental risks. Springer Science & Business Media.
Thielman, S., 2016. Yahoo hack: 1bn accounts compromised by biggest data breach in
history. The Guardian, 15, p.2016.
Wang, B., Zheng, Y., Lou, W. and Hou, Y.T., 2015. DDoS attack protection in the era of
cloud computing and software-defined networking. Computer Networks, 81, pp.308-319.
Zhou, X., Lee, Y., Zhang, N., Naveed, M. and Wang, X., 2014, May. The peril of
fragmentation: Security hazards in android device driver customizations. In Security and
Privacy (SP), 2014 IEEE Symposium on (pp. 409-423). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




