Southern Cross University: Risk Assessment in Cybersecurity Report
VerifiedAdded on 2021/06/17
|11
|2072
|1067
Report
AI Summary
This report provides a comprehensive risk assessment of cybersecurity at Southern Cross University. It begins with an introduction to risk assessment in cybersecurity, emphasizing the importance of preparation, knowledge identification, and the use of risk assessment results. The report then identifies critical assets of the university, including strategy, educational services, intellectual property, and student data, and uses a WFA worksheet to evaluate the impact of different criteria. It identifies potential threats such as data breaches, leakage of strategies, and intellectual property theft, and assesses the impact of these threats on the university's operations and financial standing. The report concludes by emphasizing the need for continuous risk assessment to identify vulnerabilities and implement appropriate security measures to protect the university's assets and ensure data security.

Running head: RISK ASSESSMENT
Risk Assessment
Name of the Student
Name of the University
Author Note
Risk Assessment
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: RISK ASSESSMENT

Running head: RISK ASSESSMENT
Table of Contents
Introduction:...............................................................................................................................3
Task 1: Risk Assessment in Cybersecurity................................................................................3
Risk Assesment:.....................................................................................................................3
Knowledge Identification:......................................................................................................3
Use of Risk Assessment Result:.............................................................................................4
Limitations:............................................................................................................................4
Task 2: Critical Asset Identification:.........................................................................................4
Five Questions:.......................................................................................................................5
WFA Worksheet:...................................................................................................................6
Task 3: Threat Identification......................................................................................................6
Top Five Threats:...................................................................................................................6
Task 4: Threat Assessment.........................................................................................................7
Potential Threats:...................................................................................................................7
Impact of the Threats:............................................................................................................8
Conclusion:................................................................................................................................8
Table of Contents
Introduction:...............................................................................................................................3
Task 1: Risk Assessment in Cybersecurity................................................................................3
Risk Assesment:.....................................................................................................................3
Knowledge Identification:......................................................................................................3
Use of Risk Assessment Result:.............................................................................................4
Limitations:............................................................................................................................4
Task 2: Critical Asset Identification:.........................................................................................4
Five Questions:.......................................................................................................................5
WFA Worksheet:...................................................................................................................6
Task 3: Threat Identification......................................................................................................6
Top Five Threats:...................................................................................................................6
Task 4: Threat Assessment.........................................................................................................7
Potential Threats:...................................................................................................................7
Impact of the Threats:............................................................................................................8
Conclusion:................................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: RISK ASSESSMENT
Introduction:
In this report the main task is risk assessment with the context of cyber security. The
organization that is selected for the risk assessment is Southern Cross University. The
university is a public university situated in various part of Australia. The university stores a
huge amount of data. Hence the data security is needed for the university as it possesses lots
of security issues. In the further report the risk associates with the cyber security of university
will be identified. It is necessary to assess the risk that are associated with the organization
and to mitigate it by taking proper measures. In the report the threats and their impact will be
discussed and their rank will be done as per the impact.
Task 1: Risk Assessment in Cybersecurity
Risk Assesment:
The NIST says that the main objective of a risk assessment is for the organization or
the company to understand the risks associated with the organizations cyber security. For any
risk assessment it is required to make a proper preparation. The preparation includes various
type of ground rules, clear understanding of scope and purpose, constraints and assumptions
(Cherdantseva et al., 2016).
Knowledge Identification:
After performing the risk assessment on the university it will be able to identify the
vulnerabilities. The university management will also able to identify the internal and external
threats that are associated with network of the university. Information of the vulnerabilities
and the threats can be acquired from the external sources (Ward, Ibarra and Ruddle, 2013).
The risk assessment also helps the university to identify the impact of the threats in the
business perspective. The threats are reviewed and the information is documented.
Introduction:
In this report the main task is risk assessment with the context of cyber security. The
organization that is selected for the risk assessment is Southern Cross University. The
university is a public university situated in various part of Australia. The university stores a
huge amount of data. Hence the data security is needed for the university as it possesses lots
of security issues. In the further report the risk associates with the cyber security of university
will be identified. It is necessary to assess the risk that are associated with the organization
and to mitigate it by taking proper measures. In the report the threats and their impact will be
discussed and their rank will be done as per the impact.
Task 1: Risk Assessment in Cybersecurity
Risk Assesment:
The NIST says that the main objective of a risk assessment is for the organization or
the company to understand the risks associated with the organizations cyber security. For any
risk assessment it is required to make a proper preparation. The preparation includes various
type of ground rules, clear understanding of scope and purpose, constraints and assumptions
(Cherdantseva et al., 2016).
Knowledge Identification:
After performing the risk assessment on the university it will be able to identify the
vulnerabilities. The university management will also able to identify the internal and external
threats that are associated with network of the university. Information of the vulnerabilities
and the threats can be acquired from the external sources (Ward, Ibarra and Ruddle, 2013).
The risk assessment also helps the university to identify the impact of the threats in the
business perspective. The threats are reviewed and the information is documented.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: RISK ASSESSMENT
Use of Risk Assessment Result:
From the risk assessment the university will be able to learn about the risk and the threats
associated with the university’s cyber security. As the risk are identified, so it will be easy to
mitigate the risks. Risk mitigation technique can be taken on the basis of the information and
the related observation. By the help of risk assessment in the cybersecurity the university will
be able to remove the threats and university assets will be safe (Hartmann and Steup, 2013).
Limitations:
The main limitations with the risk assessment approach is that, it will never give the
proper answer on the risks. It is nearly impossible to determine the actual threat and the
vulnerabilities in the system. The risk assessment answers are not same each of the time. The
risk assessment answers are inconsistent which a limitation of the risk assessment in
cybersecurity.
Task 2: Critical Asset Identification:
Information asset is mainly refers to the information those carries the organizations
financial value. Information asset is mainly used to reduce the cost of future and improve the
rate of revenue generation. For this university the crucial information assets are strategy,
education service, intellectual property, secrets of trade, university projects, content to train
students, media of marketing, data about the staff and students, operations like
documentation, decision support, finance, culture of the organization, legal & compliance,
and the university development (Wang and Lu, 2013).
The information asset goes critical due to lack of importance and security. As the
information assets are the main part which carries the financial value of the organization.
Mainly the information asset converts into the critical assets by the internal people that are
Use of Risk Assessment Result:
From the risk assessment the university will be able to learn about the risk and the threats
associated with the university’s cyber security. As the risk are identified, so it will be easy to
mitigate the risks. Risk mitigation technique can be taken on the basis of the information and
the related observation. By the help of risk assessment in the cybersecurity the university will
be able to remove the threats and university assets will be safe (Hartmann and Steup, 2013).
Limitations:
The main limitations with the risk assessment approach is that, it will never give the
proper answer on the risks. It is nearly impossible to determine the actual threat and the
vulnerabilities in the system. The risk assessment answers are not same each of the time. The
risk assessment answers are inconsistent which a limitation of the risk assessment in
cybersecurity.
Task 2: Critical Asset Identification:
Information asset is mainly refers to the information those carries the organizations
financial value. Information asset is mainly used to reduce the cost of future and improve the
rate of revenue generation. For this university the crucial information assets are strategy,
education service, intellectual property, secrets of trade, university projects, content to train
students, media of marketing, data about the staff and students, operations like
documentation, decision support, finance, culture of the organization, legal & compliance,
and the university development (Wang and Lu, 2013).
The information asset goes critical due to lack of importance and security. As the
information assets are the main part which carries the financial value of the organization.
Mainly the information asset converts into the critical assets by the internal people that are

Running head: RISK ASSESSMENT
associated with the organization. It is needed to take some serious mitigation techniques for
the information assets so that the information assets will not turn into critical assets
(Sommestad, Ekstedt and Holm, 2013).
Five Questions:
Question 1
What kind of strategy will be used for working the assets of the organization?
Question 2
What are the intellectual properties that are working with the organizations asset?
Question 3
Is there any kind of legal procedure that will affect the deal with the critical data?
Question 4
Identify the operations that are included in the critical data sector of the university?
Question 5
Identify the material that are used to secure the organizations critical data?
associated with the organization. It is needed to take some serious mitigation techniques for
the information assets so that the information assets will not turn into critical assets
(Sommestad, Ekstedt and Holm, 2013).
Five Questions:
Question 1
What kind of strategy will be used for working the assets of the organization?
Question 2
What are the intellectual properties that are working with the organizations asset?
Question 3
Is there any kind of legal procedure that will affect the deal with the critical data?
Question 4
Identify the operations that are included in the critical data sector of the university?
Question 5
Identify the material that are used to secure the organizations critical data?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
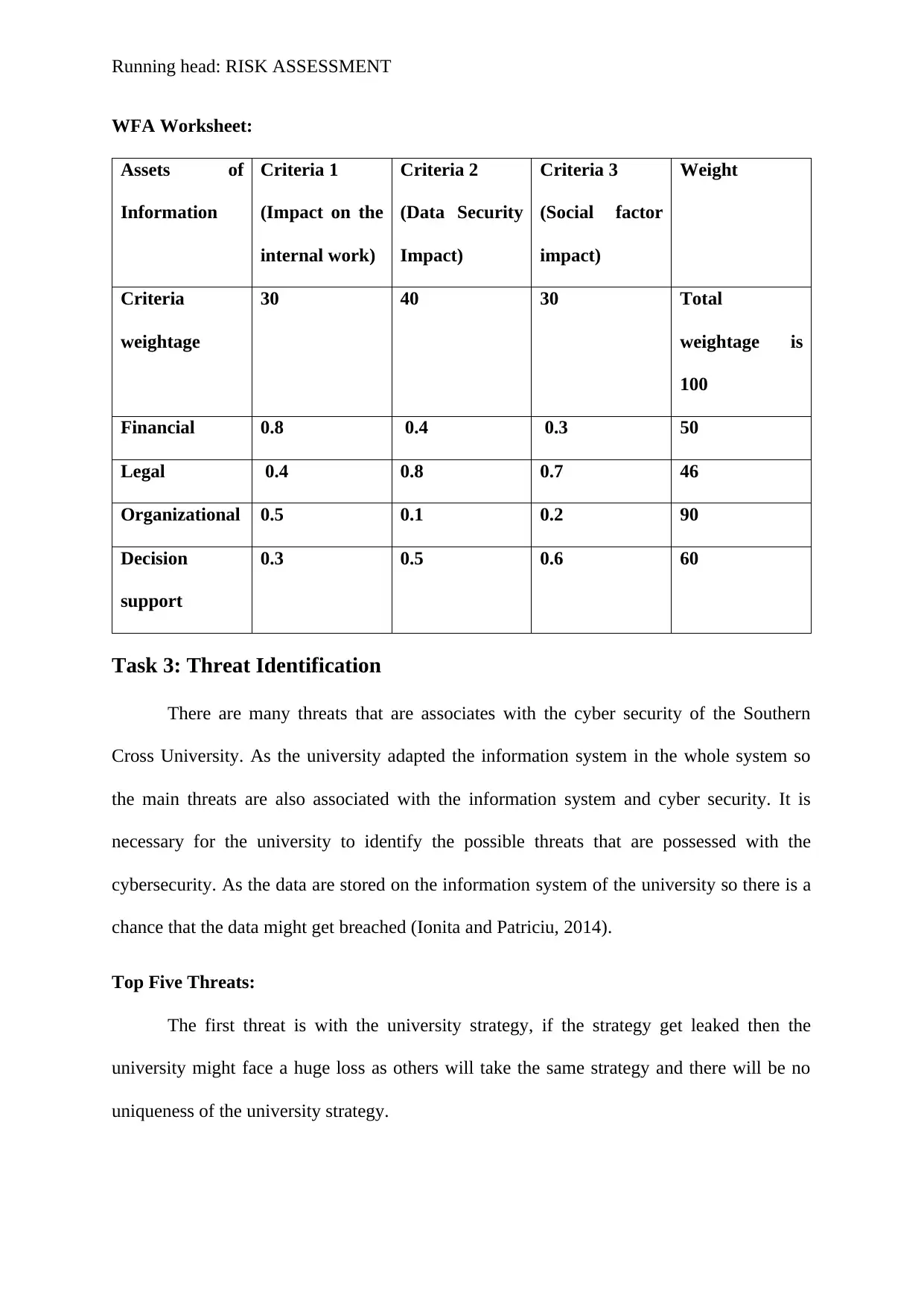
Running head: RISK ASSESSMENT
WFA Worksheet:
Assets of
Information
Criteria 1
(Impact on the
internal work)
Criteria 2
(Data Security
Impact)
Criteria 3
(Social factor
impact)
Weight
Criteria
weightage
30 40 30 Total
weightage is
100
Financial 0.8 0.4 0.3 50
Legal 0.4 0.8 0.7 46
Organizational 0.5 0.1 0.2 90
Decision
support
0.3 0.5 0.6 60
Task 3: Threat Identification
There are many threats that are associates with the cyber security of the Southern
Cross University. As the university adapted the information system in the whole system so
the main threats are also associated with the information system and cyber security. It is
necessary for the university to identify the possible threats that are possessed with the
cybersecurity. As the data are stored on the information system of the university so there is a
chance that the data might get breached (Ionita and Patriciu, 2014).
Top Five Threats:
The first threat is with the university strategy, if the strategy get leaked then the
university might face a huge loss as others will take the same strategy and there will be no
uniqueness of the university strategy.
WFA Worksheet:
Assets of
Information
Criteria 1
(Impact on the
internal work)
Criteria 2
(Data Security
Impact)
Criteria 3
(Social factor
impact)
Weight
Criteria
weightage
30 40 30 Total
weightage is
100
Financial 0.8 0.4 0.3 50
Legal 0.4 0.8 0.7 46
Organizational 0.5 0.1 0.2 90
Decision
support
0.3 0.5 0.6 60
Task 3: Threat Identification
There are many threats that are associates with the cyber security of the Southern
Cross University. As the university adapted the information system in the whole system so
the main threats are also associated with the information system and cyber security. It is
necessary for the university to identify the possible threats that are possessed with the
cybersecurity. As the data are stored on the information system of the university so there is a
chance that the data might get breached (Ionita and Patriciu, 2014).
Top Five Threats:
The first threat is with the university strategy, if the strategy get leaked then the
university might face a huge loss as others will take the same strategy and there will be no
uniqueness of the university strategy.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: RISK ASSESSMENT
The next threat is associated with the data of the university. The rate of cybercrime is
getting higher in the recent time so the university data has the potential threat that a data
beach might happen.
There are risk with the material too which is used to train the students. As the
university use their own material for training purpose of the students so it is necessary for the
university to keep the material confidential as it can be hacked by the hackers to affect the
university.
The university must handle their intellectual property properly in order to gain success
in long term. The intellectual property are subject to copyright, there are many threats that the
intellectual property holds like copying the idea of the university by other competitive
universities.
` One of the main information asset is the financial asset and it has its own threats. As
the transaction is made through online s there is a chance of vulnerability and the money can
be hacked by the hackers.
Task 4: Threat Assessment
Potential Threats:
Asset vulnerability is mainly the weaknesses that the assets are having in them. Each
asset has their own weaknesses. The education strategy has a weakness that this strategy if
leaked then it will lost its value. Same goes for the data of the university which is a main
asset for the university. The data need to be stored properly with measured security, as the
data contains all details of university staffs and the students. It is the duty of the university to
secure their data so any kind of data breach do not happen (Amin et al., 2013). These are the
main reason why the risk assessment is done in the cybersecurity.
The next threat is associated with the data of the university. The rate of cybercrime is
getting higher in the recent time so the university data has the potential threat that a data
beach might happen.
There are risk with the material too which is used to train the students. As the
university use their own material for training purpose of the students so it is necessary for the
university to keep the material confidential as it can be hacked by the hackers to affect the
university.
The university must handle their intellectual property properly in order to gain success
in long term. The intellectual property are subject to copyright, there are many threats that the
intellectual property holds like copying the idea of the university by other competitive
universities.
` One of the main information asset is the financial asset and it has its own threats. As
the transaction is made through online s there is a chance of vulnerability and the money can
be hacked by the hackers.
Task 4: Threat Assessment
Potential Threats:
Asset vulnerability is mainly the weaknesses that the assets are having in them. Each
asset has their own weaknesses. The education strategy has a weakness that this strategy if
leaked then it will lost its value. Same goes for the data of the university which is a main
asset for the university. The data need to be stored properly with measured security, as the
data contains all details of university staffs and the students. It is the duty of the university to
secure their data so any kind of data breach do not happen (Amin et al., 2013). These are the
main reason why the risk assessment is done in the cybersecurity.

Running head: RISK ASSESSMENT
Impact of the Threats:
These threats can affect the university hugely as it consists all the information, data,
strategy, media, and the legal compliance of the system. So if any kind of vulnerability
happens then it can be very harmful for the university (Shin, Son and Heo, 2015). So it
necessary to conduct a risk assessment on the cybersecurity to identify the risks and the
threats that are associated with the cybersecurity of the university. The vulnerabilities are
ranks high among the all aspect because it the main area of concern for the university which
needed to be taken care of. If the correct measurement is taken then the university system will
be more secure and the threats will be less in the university (Linkov et al., 2013). To avoid
any kind of data breach or any kind of cyber-attack in the system the university will have to
be secure their network and the database where they stored the data about the university.
Conclusion:
From the organization overhead report it can be concluded that it is necessary for each
and every organization to do the risk assessment in the context of the cybersecurity. By the
risk assessment the university will be aware of the threats and the risks that can harm the
whole infrastructure of the university. The first method is to identify the risks associated with
the university. After the risk identification the university will be able to take required
measurement for the cyber security. In the above report all the information asset is identified
for the university and threats associated with the information asset are also is identified. The
report also identified that how the information asset converted into critical asset. The impact
of the threats are also discussed in the above report. Risk assessment is basically done to
identify the vulnerabilities in the network.
Impact of the Threats:
These threats can affect the university hugely as it consists all the information, data,
strategy, media, and the legal compliance of the system. So if any kind of vulnerability
happens then it can be very harmful for the university (Shin, Son and Heo, 2015). So it
necessary to conduct a risk assessment on the cybersecurity to identify the risks and the
threats that are associated with the cybersecurity of the university. The vulnerabilities are
ranks high among the all aspect because it the main area of concern for the university which
needed to be taken care of. If the correct measurement is taken then the university system will
be more secure and the threats will be less in the university (Linkov et al., 2013). To avoid
any kind of data breach or any kind of cyber-attack in the system the university will have to
be secure their network and the database where they stored the data about the university.
Conclusion:
From the organization overhead report it can be concluded that it is necessary for each
and every organization to do the risk assessment in the context of the cybersecurity. By the
risk assessment the university will be aware of the threats and the risks that can harm the
whole infrastructure of the university. The first method is to identify the risks associated with
the university. After the risk identification the university will be able to take required
measurement for the cyber security. In the above report all the information asset is identified
for the university and threats associated with the information asset are also is identified. The
report also identified that how the information asset converted into critical asset. The impact
of the threats are also discussed in the above report. Risk assessment is basically done to
identify the vulnerabilities in the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: RISK ASSESSMENT
References:
Amin, S., Litrico, X., Sastry, S. and Bayen, A.M., 2013. Cyber security of water SCADA
systems—Part I: Analysis and experimentation of stealthy deception attacks. IEEE
Transactions on Control Systems Technology, 21(5), pp.1963-1970.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K.,
2016. A review of cyber security risk assessment methods for SCADA systems. Computers
& security, 56, pp.1-27.
Hartmann, K. and Steup, C., 2013, June. The vulnerability of UAVs to cyber attacks-An
approach to the risk assessment. In Cyber Conflict (CyCon), 2013 5th International
Conference on (pp. 1-23). IEEE.
Ionita, M.G. and Patriciu, V.V., 2014, May. Biologically inspired risk assessment in cyber
security using neural networks. In Communications (COMM), 2014 10th International
Conference on (pp. 1-4). IEEE.
Linkov, I., Eisenberg, D.A., Plourde, K., Seager, T.P., Allen, J. and Kott, A., 2013. Resilience
metrics for cyber systems. Environment Systems and Decisions, 33(4), pp.471-476.
Shin, J., Son, H. and Heo, G., 2015. Development of a cyber security risk model using
Bayesian networks. Reliability Engineering & System Safety, 134, pp.208-217.
Sommestad, T., Ekstedt, M. and Holm, H., 2013. The cyber security modeling language: A
tool for assessing the vulnerability of enterprise system architectures. IEEE Systems Journal,
7(3), pp.363-373.
Wang, W. and Lu, Z., 2013. Cyber security in the smart grid: Survey and challenges.
Computer Networks, 57(5), pp.1344-1371.
References:
Amin, S., Litrico, X., Sastry, S. and Bayen, A.M., 2013. Cyber security of water SCADA
systems—Part I: Analysis and experimentation of stealthy deception attacks. IEEE
Transactions on Control Systems Technology, 21(5), pp.1963-1970.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K.,
2016. A review of cyber security risk assessment methods for SCADA systems. Computers
& security, 56, pp.1-27.
Hartmann, K. and Steup, C., 2013, June. The vulnerability of UAVs to cyber attacks-An
approach to the risk assessment. In Cyber Conflict (CyCon), 2013 5th International
Conference on (pp. 1-23). IEEE.
Ionita, M.G. and Patriciu, V.V., 2014, May. Biologically inspired risk assessment in cyber
security using neural networks. In Communications (COMM), 2014 10th International
Conference on (pp. 1-4). IEEE.
Linkov, I., Eisenberg, D.A., Plourde, K., Seager, T.P., Allen, J. and Kott, A., 2013. Resilience
metrics for cyber systems. Environment Systems and Decisions, 33(4), pp.471-476.
Shin, J., Son, H. and Heo, G., 2015. Development of a cyber security risk model using
Bayesian networks. Reliability Engineering & System Safety, 134, pp.208-217.
Sommestad, T., Ekstedt, M. and Holm, H., 2013. The cyber security modeling language: A
tool for assessing the vulnerability of enterprise system architectures. IEEE Systems Journal,
7(3), pp.363-373.
Wang, W. and Lu, Z., 2013. Cyber security in the smart grid: Survey and challenges.
Computer Networks, 57(5), pp.1344-1371.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: RISK ASSESSMENT
Ward, D., Ibarra, I. and Ruddle, A., 2013. Threat analysis and risk assessment in automotive
cyber security. SAE International Journal of Passenger Cars-Electronic and Electrical
Systems, 6(2013-01-1415), pp.507-513.
Ward, D., Ibarra, I. and Ruddle, A., 2013. Threat analysis and risk assessment in automotive
cyber security. SAE International Journal of Passenger Cars-Electronic and Electrical
Systems, 6(2013-01-1415), pp.507-513.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




