Detailed Cyber Security Assessment for ZP Printing Company
VerifiedAdded on 2024/05/30
|12
|2768
|141
Report
AI Summary
This report provides a comprehensive cyber security assessment for ZP Printing Company, which is transitioning to online services. It identifies cyber security as a top concern due to the potential for data breaches, malware infections, and other cybercrimes. The report discusses the consequences of cyber security issues, including financial losses, reputational damage, and legal liabilities. It also proposes solutions such as implementing security software, backup strategies, and employee training to mitigate these risks. The assessment emphasizes the importance of addressing cyber security proactively to protect sensitive data and maintain business continuity. Desklib provides students access to solved assignments and past papers.

COMPUTER SECURITY
ASSESSMENT 2
ASSESSMENT 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.....................................................................................................................................2
Why cyber security include in top 8 issues?....................................................................................3
Consequences with Cyber security..................................................................................................4
Cyber security issue:........................................................................................................................6
Why given solution is better to alternative approaches?...............................................................8
Breakdown of cost of selected issue “Cyber security”....................................................................9
Conclusion......................................................................................................................................10
References.....................................................................................................................................11
1
Introduction.....................................................................................................................................2
Why cyber security include in top 8 issues?....................................................................................3
Consequences with Cyber security..................................................................................................4
Cyber security issue:........................................................................................................................6
Why given solution is better to alternative approaches?...............................................................8
Breakdown of cost of selected issue “Cyber security”....................................................................9
Conclusion......................................................................................................................................10
References.....................................................................................................................................11
1

Introduction
Cyber securities main function is to create a technology which protects the network, system,
and data from cyber-attacks that enter into a network and corrupt the data. Effective cyber
securities reduce the risk of unauthorized exploitation in the system, network, and
technologies. Due to lack of cybersecurity, a malware can enter into the network and
access the important data that is confidential to an organization and can leak that data into
the network. The ZP printing company is moving to online services and their employees
start to uses the laptop and computers to make system online. According to the scenario,
the ZP printing company has some situation like the manager and SEO contains the laptop
that must have antivirus and security software. This report further discusses a cyber issue
which can affect a network and various solutions which can be taken into account in order
to protect the network from cybercrime.
2
Cyber securities main function is to create a technology which protects the network, system,
and data from cyber-attacks that enter into a network and corrupt the data. Effective cyber
securities reduce the risk of unauthorized exploitation in the system, network, and
technologies. Due to lack of cybersecurity, a malware can enter into the network and
access the important data that is confidential to an organization and can leak that data into
the network. The ZP printing company is moving to online services and their employees
start to uses the laptop and computers to make system online. According to the scenario,
the ZP printing company has some situation like the manager and SEO contains the laptop
that must have antivirus and security software. This report further discusses a cyber issue
which can affect a network and various solutions which can be taken into account in order
to protect the network from cybercrime.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Why does cybersecurity include in top 8 issues?
Cybercrime is among top 8 crimes as it’s a crime which can’t be caught up easily in the
network as it’s almost hidden in the network and can’t be diagnosed easily in the system.
This crime is also responsible for leaking personal and confidential information about people
which may lead to in a greater crime such as terrorism. Due to this wrong information about
people, which may lead to wrong identity about someone and may lead to murders or
others crime etc. furthermore internet is accessible to almost 90% of the population in
world which makes it easy for anyone to commit any kind of cybercrime, social networking
sites are full of fake information which lead to more crimes as people are disguised by fake
profiles (Subashini, 2011). There should be a continuous check about the information which
is shared online and the fake ones should be filtered out and should be removed from sites.
In order to save the consequences of cybercrime to be converted into a big crime which
can’t repent later on? The government has taken steps to ensure minimum crime rates
using various methodologies which are reducing cybercrime to a great extent but more
check posts are needed to control cybercrime and stop the crime which is committed due to
the cyber world. As a lot of crimes are stated above which are caused due to the cyber
world and their impact which is been caused is also mentioned so this is the time we take a
step and solve this issue until it converts itself into something bigger. The main issue which
lies behind lack of cybersecurity is that a system may be targeted and breached and it’s not
recognizable by the ZP printing organization. The cyber-attacks can attack a ZP printing
organization or a personal account, to protect personal accounts from threats of cybercrime
the passwords must be different for different accounts, applications such as paytm must be
updated regularly and data should be downloaded only from secured links so that no
malware can enter the device. For big networks like a ZP printing organizational network,
various ant viruses must be used to protect the network from viruses, malware, worms, and
internet threats these precautions can save a network or device from getting affected from
cybercrime or malware (Rowe, 2011).
3
Cybercrime is among top 8 crimes as it’s a crime which can’t be caught up easily in the
network as it’s almost hidden in the network and can’t be diagnosed easily in the system.
This crime is also responsible for leaking personal and confidential information about people
which may lead to in a greater crime such as terrorism. Due to this wrong information about
people, which may lead to wrong identity about someone and may lead to murders or
others crime etc. furthermore internet is accessible to almost 90% of the population in
world which makes it easy for anyone to commit any kind of cybercrime, social networking
sites are full of fake information which lead to more crimes as people are disguised by fake
profiles (Subashini, 2011). There should be a continuous check about the information which
is shared online and the fake ones should be filtered out and should be removed from sites.
In order to save the consequences of cybercrime to be converted into a big crime which
can’t repent later on? The government has taken steps to ensure minimum crime rates
using various methodologies which are reducing cybercrime to a great extent but more
check posts are needed to control cybercrime and stop the crime which is committed due to
the cyber world. As a lot of crimes are stated above which are caused due to the cyber
world and their impact which is been caused is also mentioned so this is the time we take a
step and solve this issue until it converts itself into something bigger. The main issue which
lies behind lack of cybersecurity is that a system may be targeted and breached and it’s not
recognizable by the ZP printing organization. The cyber-attacks can attack a ZP printing
organization or a personal account, to protect personal accounts from threats of cybercrime
the passwords must be different for different accounts, applications such as paytm must be
updated regularly and data should be downloaded only from secured links so that no
malware can enter the device. For big networks like a ZP printing organizational network,
various ant viruses must be used to protect the network from viruses, malware, worms, and
internet threats these precautions can save a network or device from getting affected from
cybercrime or malware (Rowe, 2011).
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Consequences of Cybersecurity
With the cybersecurity issue, the ZP printing organization and its member faces several
problems and it cannot be completely solved. Because of the cybersecurity, an employee of
the ZP printing organization faces consequences that are discussed here:
1. When the employees connect the smartphones with their system, the hackers easily
hack the system and also vulnerable to enter into a network and steal sensitive data
and harm the stored data in the ZP printing system.
2. The hackers easily cracked into a ZP printing organization network that steals the
information and makes money out of leaking the information but the hackers are
also cracked the governmental policies from the ZP printing organization to give the
information to provide the information to their competitors.
3. The internet of things attacks is easy as there are a number of devices which are
connected to a network of ZP printing which makes it easy for a hacker to break into
a network using the bone kit and can hack systems that are connected to the ZP
printing network.
4. With increasing, use of virtual currency and bitcoin hackers are mining the networks
to gain the maximum amount of profit through hacking this. Mining is a process
through which a hacker has a cryptocurrency and he hacks into an account and
keeps the record of transactions, and receive digital coins in return (Yan, 2012).
5. ZP printing has a number of concerns in areas of privacy, safety, and cyber securities.
As more devices are connected to a network the data about the employees and their
use is highly vulnerable. The devices which are directly connected to a user are of a
much more great threat as an attacker can give incorrect services and make harm to
the business. The employees and patient will be hacked records which are now
available online are a great concern of target to the hackers as they contain a huge
amount of sensitive data.
6. Third parties such as contractors and vendors possess a huge risk to organizations
which mostly don’t have a secured network and don’t even possess a team which
can control the third party applications or transactions. According to research third-
party applications can’t be secured effectively and cannot be secured by the ZP
4
With the cybersecurity issue, the ZP printing organization and its member faces several
problems and it cannot be completely solved. Because of the cybersecurity, an employee of
the ZP printing organization faces consequences that are discussed here:
1. When the employees connect the smartphones with their system, the hackers easily
hack the system and also vulnerable to enter into a network and steal sensitive data
and harm the stored data in the ZP printing system.
2. The hackers easily cracked into a ZP printing organization network that steals the
information and makes money out of leaking the information but the hackers are
also cracked the governmental policies from the ZP printing organization to give the
information to provide the information to their competitors.
3. The internet of things attacks is easy as there are a number of devices which are
connected to a network of ZP printing which makes it easy for a hacker to break into
a network using the bone kit and can hack systems that are connected to the ZP
printing network.
4. With increasing, use of virtual currency and bitcoin hackers are mining the networks
to gain the maximum amount of profit through hacking this. Mining is a process
through which a hacker has a cryptocurrency and he hacks into an account and
keeps the record of transactions, and receive digital coins in return (Yan, 2012).
5. ZP printing has a number of concerns in areas of privacy, safety, and cyber securities.
As more devices are connected to a network the data about the employees and their
use is highly vulnerable. The devices which are directly connected to a user are of a
much more great threat as an attacker can give incorrect services and make harm to
the business. The employees and patient will be hacked records which are now
available online are a great concern of target to the hackers as they contain a huge
amount of sensitive data.
6. Third parties such as contractors and vendors possess a huge risk to organizations
which mostly don’t have a secured network and don’t even possess a team which
can control the third party applications or transactions. According to research third-
party applications can’t be secured effectively and cannot be secured by the ZP
4

printing organization and thus can’t be protected well from hackers and information
is well secured (Ralston, 2007).
Figure 1 Cybersecurity
5
is well secured (Ralston, 2007).
Figure 1 Cybersecurity
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cybersecurity issue:
In this section address the Cybersecurity issue in the ZP printing company, how it faces the
cybersecurity issue and how it can be protected. As we know, the cybersecurity is a major
issue that is faced by number organization with their online services. Cyber-attacks are now
not only limited to the private sector but is widely even spreading to governmental
organizations which creates a loss to the nation in all. It is expected that the state-
sponsored attacks would be increasing in future which will create a loss to the nation as a
whole. There are top three bone kits which are nowadays responsible to hack millions of
accounts per month. Millions of unsecured networks are there which are connected to
millions of devices which is a big threat to the internet of things. There is a global advisory
firm which provides security risk management, business strategies to protect a network
from cybercrime and protecting millions of devices from being hacked by hackers.
Researchers have proven that these hackers hack the account which contains virtual
currencies and gains maximum profit by stealing into the network of the ZP printing
organization and stealing money from private as well as governmental networks. This
method of attacks is likely believed to be increased over the course of time as seen by
researchers. This method is thus effective to steal money or virtual currency from the
accounts by the hackers and making a huge amount of profit through hacking into a
network and stealing the information (Yan, 2012).
Cybersecurity is a major problem in the ZP printing company that will be hit by hackers to
steal important and sensitive information. With the recent digitalization of the other
industries, it will take time to adapt the technologies and protect the information of ZP
printing especially the information of the employees and users records safe from viruses
and malware which can be caused by unauthorized access of information by hackers. ZP
printing company will be faced the Cybersecurity issue when a malicious third party got into
the hotel's network and inserted malicious software code into the network of the hotel IT
system and hacked the data and stole all the sensitive information regarding the client's
details and the money they spent in paying the charges for the printing services. As the
more and more online information’s are available and sensitive data is available online so
the risk of hackers attacking the network and getting or stealing sensitive data of the third
6
In this section address the Cybersecurity issue in the ZP printing company, how it faces the
cybersecurity issue and how it can be protected. As we know, the cybersecurity is a major
issue that is faced by number organization with their online services. Cyber-attacks are now
not only limited to the private sector but is widely even spreading to governmental
organizations which creates a loss to the nation in all. It is expected that the state-
sponsored attacks would be increasing in future which will create a loss to the nation as a
whole. There are top three bone kits which are nowadays responsible to hack millions of
accounts per month. Millions of unsecured networks are there which are connected to
millions of devices which is a big threat to the internet of things. There is a global advisory
firm which provides security risk management, business strategies to protect a network
from cybercrime and protecting millions of devices from being hacked by hackers.
Researchers have proven that these hackers hack the account which contains virtual
currencies and gains maximum profit by stealing into the network of the ZP printing
organization and stealing money from private as well as governmental networks. This
method of attacks is likely believed to be increased over the course of time as seen by
researchers. This method is thus effective to steal money or virtual currency from the
accounts by the hackers and making a huge amount of profit through hacking into a
network and stealing the information (Yan, 2012).
Cybersecurity is a major problem in the ZP printing company that will be hit by hackers to
steal important and sensitive information. With the recent digitalization of the other
industries, it will take time to adapt the technologies and protect the information of ZP
printing especially the information of the employees and users records safe from viruses
and malware which can be caused by unauthorized access of information by hackers. ZP
printing company will be faced the Cybersecurity issue when a malicious third party got into
the hotel's network and inserted malicious software code into the network of the hotel IT
system and hacked the data and stole all the sensitive information regarding the client's
details and the money they spent in paying the charges for the printing services. As the
more and more online information’s are available and sensitive data is available online so
the risk of hackers attacking the network and getting or stealing sensitive data of the third
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
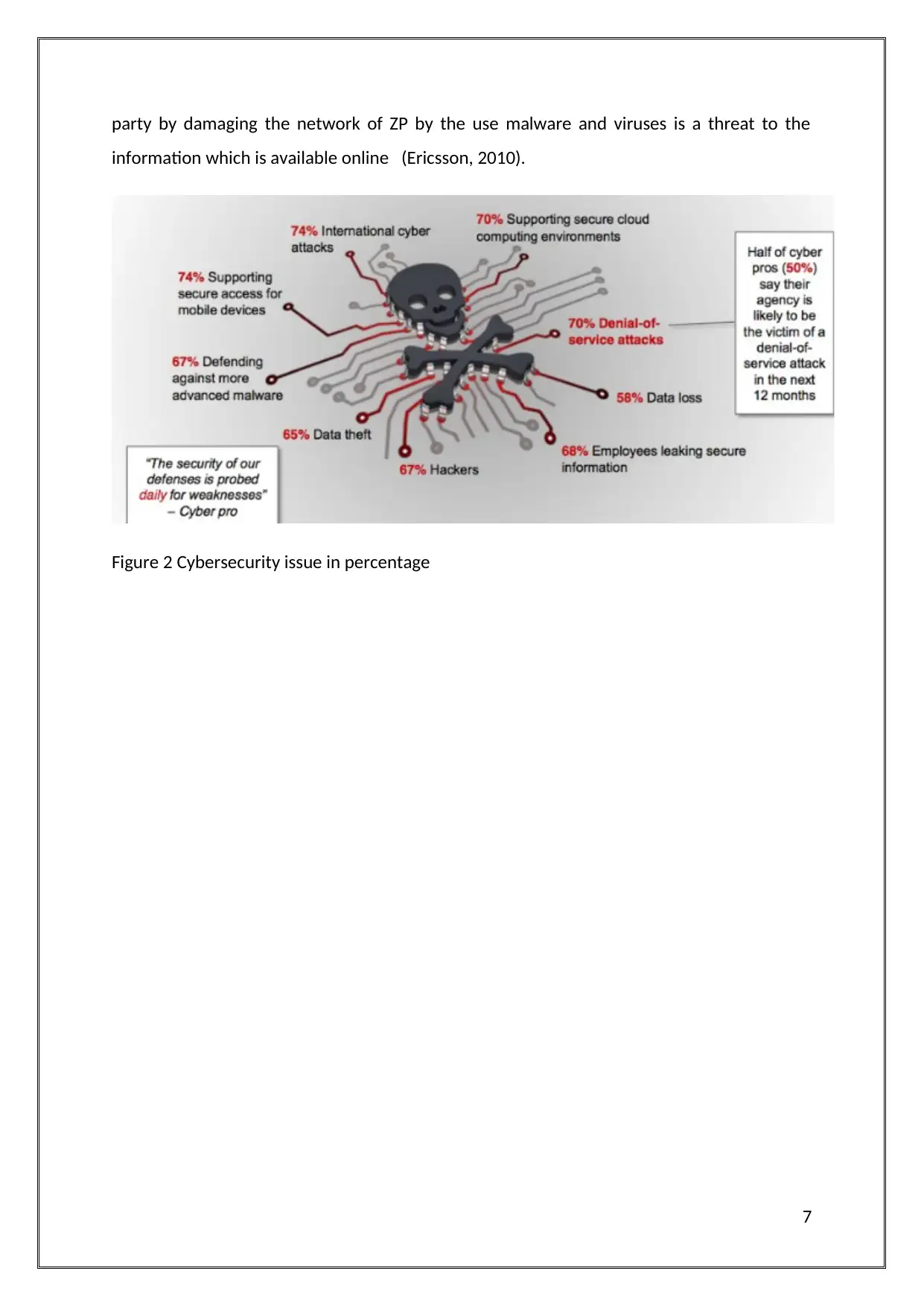
party by damaging the network of ZP by the use malware and viruses is a threat to the
information which is available online (Ericsson, 2010).
Figure 2 Cybersecurity issue in percentage
7
information which is available online (Ericsson, 2010).
Figure 2 Cybersecurity issue in percentage
7

Why is given solution better to alternative approaches?
These above 8 consequences were chosen problems that are affecting every employee of ZP
printing organization in real life, these issues are not only bothering to big organizations or
companies but these are the cyber issues which employees are facing in their daily lives, and
they are not even aware of any such crimes and these crimes have affected a lot of people
as either their sensitive information was being leaked or they were bankrupted or their
virtual transactions were not successfully made.
The above issues are left unseen by the ZP organization employees then that would lead to
leaking of sensitive information or data and company might lose its important and
confidential information which was of a lot of interest to the hackers. Thus, it’s better to
address these crimes as soon as possible and then make the necessary changes to prevent
the leakage of important data from the system or network of the company. To secure the
information, the ZP organization must install the security software and backup software in
the systems. With the security technology, the hacker and the malware users are easily
detected. With the backup technology, the ZP printing organization is able to restore the
lost information and details. They provided a solution is better than other alternative
approaches to securing the devices and system and restoring the data which are lost (Sou,
2013).
Figure 3 Control the cybersecurity issue
8
These above 8 consequences were chosen problems that are affecting every employee of ZP
printing organization in real life, these issues are not only bothering to big organizations or
companies but these are the cyber issues which employees are facing in their daily lives, and
they are not even aware of any such crimes and these crimes have affected a lot of people
as either their sensitive information was being leaked or they were bankrupted or their
virtual transactions were not successfully made.
The above issues are left unseen by the ZP organization employees then that would lead to
leaking of sensitive information or data and company might lose its important and
confidential information which was of a lot of interest to the hackers. Thus, it’s better to
address these crimes as soon as possible and then make the necessary changes to prevent
the leakage of important data from the system or network of the company. To secure the
information, the ZP organization must install the security software and backup software in
the systems. With the security technology, the hacker and the malware users are easily
detected. With the backup technology, the ZP printing organization is able to restore the
lost information and details. They provided a solution is better than other alternative
approaches to securing the devices and system and restoring the data which are lost (Sou,
2013).
Figure 3 Control the cybersecurity issue
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Breakdown of the cost of the selected issue “Cybersecurity”
Implementing a national cyber incident response plan is necessary to be made to figure out
the afterward consequences of cybercrime after the crime is committed by increasing
awareness and using internet of things it would be much more costly for criminals which
would lead to less crime. It is a much reasonable idea.
To overcome or have a precaution over these issues is security updates which should be
timely made such as all the devices must be updated regularly and should be used with the
updated versions. Anti-viruses must be installed on the devices and firewall protection
devices must be used for the protection of desktops systems and peripherals of the ZP
organization. Another way could be to timely change the passwords of the accounts which
contain sensitive information and all the accounts should have different passwords rather
than having the same passwords for all the accounts. The devices must be backed up
regularly nowadays the cloud is available so easily and so cheap that we depend upon it so
much and don’t back up our phones, laptops etc. which must be backed up frequently. The
ZP printing organization must keep a check on the people who are using the data and must
make a record of people who are accessing it as those people having the access of your data
may compromise the data available or steal and misuse the data by keeping a record of all
using the data it would be easy to catch the person hacking into device or misusing the
information (Gordon, 2010).
The breakdown of the cost to secure the ZP printing organization from the cybersecurity
issue:
1. Plan the cost of installing the security software in the ZP printing organization
2. Plan the budget for apply the backup strategy in the system to restore the data.
Where the backup technologies are expensive so, maybe budget going high.
3. Install the firewall to secure the network from the third party.
4. The ZP printing organization should install the technologies for detecting the
hackers.
9
Implementing a national cyber incident response plan is necessary to be made to figure out
the afterward consequences of cybercrime after the crime is committed by increasing
awareness and using internet of things it would be much more costly for criminals which
would lead to less crime. It is a much reasonable idea.
To overcome or have a precaution over these issues is security updates which should be
timely made such as all the devices must be updated regularly and should be used with the
updated versions. Anti-viruses must be installed on the devices and firewall protection
devices must be used for the protection of desktops systems and peripherals of the ZP
organization. Another way could be to timely change the passwords of the accounts which
contain sensitive information and all the accounts should have different passwords rather
than having the same passwords for all the accounts. The devices must be backed up
regularly nowadays the cloud is available so easily and so cheap that we depend upon it so
much and don’t back up our phones, laptops etc. which must be backed up frequently. The
ZP printing organization must keep a check on the people who are using the data and must
make a record of people who are accessing it as those people having the access of your data
may compromise the data available or steal and misuse the data by keeping a record of all
using the data it would be easy to catch the person hacking into device or misusing the
information (Gordon, 2010).
The breakdown of the cost to secure the ZP printing organization from the cybersecurity
issue:
1. Plan the cost of installing the security software in the ZP printing organization
2. Plan the budget for apply the backup strategy in the system to restore the data.
Where the backup technologies are expensive so, maybe budget going high.
3. Install the firewall to secure the network from the third party.
4. The ZP printing organization should install the technologies for detecting the
hackers.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
The report addresses the various cyber-attacks which are affecting the systems and are
causing leakage of sensitive information in the ZP printing organization. With various
strategies, it can be used in order to prevent the attacks so that the information which is
sensitive to the ZP printing technology. It can be secured and is not accessible by the
hackers. Cybercrime is increasing and is spreading its roots not only to the personal
accounts but also to hacking the private organizations and the governmental data. The
hackers crack into the network and steal the private information which is of important use
or sensitive information of an individual or surrounding an organization, these can be done
by using various methodologies by the hackers, some of them are mentioned above which
are of great concern the main problem which lies behind is that a virus or a malware may be
accessing to an account and leaking the information and user being unaware about it. In this
report, provide the various solutions that can be done timely in order to prevent the attack
from cybercrime or which can be done after the account is being accessed and the
information is leaked in the ZP printing organization network.
10
The report addresses the various cyber-attacks which are affecting the systems and are
causing leakage of sensitive information in the ZP printing organization. With various
strategies, it can be used in order to prevent the attacks so that the information which is
sensitive to the ZP printing technology. It can be secured and is not accessible by the
hackers. Cybercrime is increasing and is spreading its roots not only to the personal
accounts but also to hacking the private organizations and the governmental data. The
hackers crack into the network and steal the private information which is of important use
or sensitive information of an individual or surrounding an organization, these can be done
by using various methodologies by the hackers, some of them are mentioned above which
are of great concern the main problem which lies behind is that a virus or a malware may be
accessing to an account and leaking the information and user being unaware about it. In this
report, provide the various solutions that can be done timely in order to prevent the attack
from cybercrime or which can be done after the account is being accessed and the
information is leaked in the ZP printing organization network.
10

References
Ericsson, G. N. (2010). Cyber security and power system communication—essential
parts of a smart grid infrastructure. IEEE Transactions on Power Delivery, 25(3), 1501-
1507.
Gordon, L. A., Loeb, M. P., & Sohail, T. (2010). Market value of voluntary disclosures
concerning information security. MIS quarterly, 567-594.
Ralston, P. A., Graham, J. H., & Hieb, J. L. (2007). Cyber security risk assessment for
SCADA and DCS networks. ISA transactions, 46(4), 583-594.
Rowe, D. C., Lunt, B. M., & Ekstrom, J. J. (2011, October). The role of cyber-security in
information technology education. In Proceedings of the 2011 conference on
Information technology education (pp. 113-122). ACM.
Sou, K. C., Sandberg, H., & Johansson, K. H. (2013). On the exact solution to a smart
grid cyber-security analysis problem. IEEE Transactions on Smart Grid, 4(2), 856-865.
Subashini, S., & Kavitha, V. (2011). A survey on security issues in service delivery
models of cloud computing. Journal of network and computer applications, 34(1), 1-
11.
Yan, Y., Qian, Y., Sharif, H., & Tipper, D. (2012). A survey on cyber security for smart
grid communications. IEEE Communications Surveys and tutorials, 14(4), 998-1010.
Yan, Y., Qian, Y., Sharif, H., & Tipper, D. (2012). A survey on cyber security for smart
grid communications. IEEE Communications Surveys and tutorials, 14(4), 998-1010.
11
Ericsson, G. N. (2010). Cyber security and power system communication—essential
parts of a smart grid infrastructure. IEEE Transactions on Power Delivery, 25(3), 1501-
1507.
Gordon, L. A., Loeb, M. P., & Sohail, T. (2010). Market value of voluntary disclosures
concerning information security. MIS quarterly, 567-594.
Ralston, P. A., Graham, J. H., & Hieb, J. L. (2007). Cyber security risk assessment for
SCADA and DCS networks. ISA transactions, 46(4), 583-594.
Rowe, D. C., Lunt, B. M., & Ekstrom, J. J. (2011, October). The role of cyber-security in
information technology education. In Proceedings of the 2011 conference on
Information technology education (pp. 113-122). ACM.
Sou, K. C., Sandberg, H., & Johansson, K. H. (2013). On the exact solution to a smart
grid cyber-security analysis problem. IEEE Transactions on Smart Grid, 4(2), 856-865.
Subashini, S., & Kavitha, V. (2011). A survey on security issues in service delivery
models of cloud computing. Journal of network and computer applications, 34(1), 1-
11.
Yan, Y., Qian, Y., Sharif, H., & Tipper, D. (2012). A survey on cyber security for smart
grid communications. IEEE Communications Surveys and tutorials, 14(4), 998-1010.
Yan, Y., Qian, Y., Sharif, H., & Tipper, D. (2012). A survey on cyber security for smart
grid communications. IEEE Communications Surveys and tutorials, 14(4), 998-1010.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





