Cyber Security Report: Ethical Hacking, BCM and Social Engineering
VerifiedAdded on 2022/11/24
|10
|2384
|453
Report
AI Summary
This report provides a detailed analysis of cyber security, focusing on various aspects of system protection and ethical hacking. It begins by identifying and explaining different types of vulnerabilities, including missing authorization, code download issues, broken authentication, missing data encryption, and cross-site scripting, along with recommended mitigation strategies. The report then explores SQL injection, detailing detection and exploitation techniques, including the use of tools like web vulnerability scanners and methods such as limiting result sets, with a step-by-step demonstration using OWASP WebGoat. Furthermore, it examines social engineering methods, such as baiting, phishing, pretexting, and scareware, and illustrates how hackers utilize these tools to carry out attacks. The report also explains Business Community Management (BCM), its features, and its role in responding to cyber threats, along with an evaluation of different backup site types. Finally, it covers the phases of ethical hacking, including reconnaissance, scanning, gaining access, maintaining access, and clearing tracks, along with an explanation of active and passive footprinting techniques. The report concludes by emphasizing the importance of BCM and ethical hacking in enhancing overall system security and protecting against cyberattacks.

CYBER SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


INTRODUCTION
Cyber security is an important practise of protecting system, server, data, financial
information, accounts from any kind of malicious attack because of which damage to system,
theft, or disruption can occur (Apruzzese and et. al., 2018). This assessment will focus upon
identification of vulnerabilities in server, ways in which they can be managed, SQL injection,
social engineering methods used to trick users to provide their person information, social
engineering tools used by hackers, explanation of BCM, sites that can be used for backup, phases
of ethical hacking, and types of Footprinting.
TASK 1: BCM
a. Detailed explanation of ways in which each vulnerabilities identified can be exploited and
recommend for each one of them about what should be done
Missing authorization: When web server do not focus upon authentication check and when a
user simply attempts to access a website or perform an action or can access a data is known as
missing authorization vulnerability. Its exploitation can lead to variety of problems such as
denial of service, information exposure etc. manual static analysis should be conducted for
detecting any kind of missing authorization vulnerabilities within system such as manual score
code review, manual spotcheck.
Download of codes without integrity checks: When without integrity check website or product
download and execute code from remote location is a main vulnerability which is required to be
dealt with. Because of this, an attacker can easily execute any kind of malicious code by simply
compromising server of host by performing DNS spoofing, or bringing modification in code
which is in transit (Maglaras and et. al., 2018). For this, taxonomy mapping can be done such as:
CERT Oracle Secure Coding Standard for Java can be used as it do not rely on verification of
automatic signature which is by default provided by java.util.jar and URLClassLoader.
Broken Authentication and Session Management: It is a vulnerability that can be used to steal
user’s login data, cookies, forge session data, or to gain unauthorized access to website. For this,
web application firewall can be used. It can directly help in protecting web server against cyber
threat of session management and broken authentication.
Missing data encryption: It is a vulnerability in which system misses proper data encryption. It
can reduce guarantees of confidentiality, integrity, and accountability (Nguyen and Reddi, 2019).
1
Cyber security is an important practise of protecting system, server, data, financial
information, accounts from any kind of malicious attack because of which damage to system,
theft, or disruption can occur (Apruzzese and et. al., 2018). This assessment will focus upon
identification of vulnerabilities in server, ways in which they can be managed, SQL injection,
social engineering methods used to trick users to provide their person information, social
engineering tools used by hackers, explanation of BCM, sites that can be used for backup, phases
of ethical hacking, and types of Footprinting.
TASK 1: BCM
a. Detailed explanation of ways in which each vulnerabilities identified can be exploited and
recommend for each one of them about what should be done
Missing authorization: When web server do not focus upon authentication check and when a
user simply attempts to access a website or perform an action or can access a data is known as
missing authorization vulnerability. Its exploitation can lead to variety of problems such as
denial of service, information exposure etc. manual static analysis should be conducted for
detecting any kind of missing authorization vulnerabilities within system such as manual score
code review, manual spotcheck.
Download of codes without integrity checks: When without integrity check website or product
download and execute code from remote location is a main vulnerability which is required to be
dealt with. Because of this, an attacker can easily execute any kind of malicious code by simply
compromising server of host by performing DNS spoofing, or bringing modification in code
which is in transit (Maglaras and et. al., 2018). For this, taxonomy mapping can be done such as:
CERT Oracle Secure Coding Standard for Java can be used as it do not rely on verification of
automatic signature which is by default provided by java.util.jar and URLClassLoader.
Broken Authentication and Session Management: It is a vulnerability that can be used to steal
user’s login data, cookies, forge session data, or to gain unauthorized access to website. For this,
web application firewall can be used. It can directly help in protecting web server against cyber
threat of session management and broken authentication.
Missing data encryption: It is a vulnerability in which system misses proper data encryption. It
can reduce guarantees of confidentiality, integrity, and accountability (Nguyen and Reddi, 2019).
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

For this vulnerability, attack modelling method can be used for detection of different kinds of
vulnerabilities on server.
Cross-site-scripting vulnerabilities: it is a kind of vulnerability that allows a hacker or an
attacker to compromise all kinds of interactions that users might have with an applicationwhich
is vulnarable. For this it is recommended that content security policy of organization should be
updated whose main focus is to mitigate impact of some vulnerabilities or cross-site scripting.
b. Tools and techniques that can be used to detect and exploit "SQL injection"
Some of the most common tools and techniques that can be used for SQL injection
detection and exploitation are:
Good web vulnerability scanner is one of the tools that can be used to detect SQL injection
vulnerability. This third- party tool can help in ensuring that new code isn’t producing
vulnerabilities within system (Lezzi, Lazoi and Corallo, 2018).
One the most common technique that can be used for this SQL injection is limiting result
sets. It can also prevent blank searches.
Demonstration of SQL injection step by step: Using OWASP WebGoat SQL injection will be
demonstrate.
In both login-count and user_id single quite will be used to identify what happens in user_id
and in Login_count.
Then a query will be run in order to revel whose query in error: SELECT * From user_data
WHERE Login_Count = 0 and userid= 1 or 1=1;--
This will help in exploitation of results and will show all the results of user login.
2
vulnerabilities on server.
Cross-site-scripting vulnerabilities: it is a kind of vulnerability that allows a hacker or an
attacker to compromise all kinds of interactions that users might have with an applicationwhich
is vulnarable. For this it is recommended that content security policy of organization should be
updated whose main focus is to mitigate impact of some vulnerabilities or cross-site scripting.
b. Tools and techniques that can be used to detect and exploit "SQL injection"
Some of the most common tools and techniques that can be used for SQL injection
detection and exploitation are:
Good web vulnerability scanner is one of the tools that can be used to detect SQL injection
vulnerability. This third- party tool can help in ensuring that new code isn’t producing
vulnerabilities within system (Lezzi, Lazoi and Corallo, 2018).
One the most common technique that can be used for this SQL injection is limiting result
sets. It can also prevent blank searches.
Demonstration of SQL injection step by step: Using OWASP WebGoat SQL injection will be
demonstrate.
In both login-count and user_id single quite will be used to identify what happens in user_id
and in Login_count.
Then a query will be run in order to revel whose query in error: SELECT * From user_data
WHERE Login_Count = 0 and userid= 1 or 1=1;--
This will help in exploitation of results and will show all the results of user login.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TASK 2: SECURITY TOOLS/ TECHNIQUES
a. Methods used by social engineers for tricking users into handing their important information.
Four most commonly used methods that are used by social engineers that are used by them to
trick users of handing over their login and financial information are:
Baiting: this method uses a false promise to enhance greed or curiosity of users. Using this
method, social engineers lure users into a trap that steal their personal and financial
information. One of the most common form of baiting is in physical form such as infected
flash drives (Coulter and et. al., 2019).
Phishing: It is one of the most common method used by social engineers. It is done by
creating text, or emails that create a sense of urgency, curiosity or fear within users that make
them provide their confidential information by clicking on malicious websites or by opening
attachments.
Pretexting: In this attacker obtain information using series of crafted cleaver lies. It is done
by obtaining a sensitive information of users so that a critical task can be performed. It is
done by making user assure that attacker have connections with a higher authority of right to
know authority. And in order to confirm users’ details, they ask some questions
Scareware: This method is used to bombard user with false alarm or threat because of which
user thinks that their system is infected with malware and in order toc deal with it they need
to install software or program which is basically a malware and has no benefits.
b. Demonstrate ways in which hackers use social-engineering tools to carry out their attacks.
Different kinds of strategies that hackers use and ways in which those strategies can be
used to exploit users.
There are many social engineering tools that can be used by hackers, such as:
3
a. Methods used by social engineers for tricking users into handing their important information.
Four most commonly used methods that are used by social engineers that are used by them to
trick users of handing over their login and financial information are:
Baiting: this method uses a false promise to enhance greed or curiosity of users. Using this
method, social engineers lure users into a trap that steal their personal and financial
information. One of the most common form of baiting is in physical form such as infected
flash drives (Coulter and et. al., 2019).
Phishing: It is one of the most common method used by social engineers. It is done by
creating text, or emails that create a sense of urgency, curiosity or fear within users that make
them provide their confidential information by clicking on malicious websites or by opening
attachments.
Pretexting: In this attacker obtain information using series of crafted cleaver lies. It is done
by obtaining a sensitive information of users so that a critical task can be performed. It is
done by making user assure that attacker have connections with a higher authority of right to
know authority. And in order to confirm users’ details, they ask some questions
Scareware: This method is used to bombard user with false alarm or threat because of which
user thinks that their system is infected with malware and in order toc deal with it they need
to install software or program which is basically a malware and has no benefits.
b. Demonstrate ways in which hackers use social-engineering tools to carry out their attacks.
Different kinds of strategies that hackers use and ways in which those strategies can be
used to exploit users.
There are many social engineering tools that can be used by hackers, such as:
3

Social engineering toolkit: This tool is used for attacking on human elements of pen testing
in order to simulate social engineering attacks. It helps in making a believable attack on
users.
Social media is another too used by hackers for carrying out their attacks. Hackers make a
fake social media account that looks very much real (von Solms and von Solms, 2018).
When a user successfully get tricked in this, they make those users click and install malicious
software or to open a video or picture which is malicious that allows hackers to take control
of users PC and steal information or another other kind of data.
Emails is another tool which is used by hackers for email phishing in which fake emails are
sent to users that help them in stealing credential information of users.
TASK 3: SECURITY CONTROLS
a. Explanation of what BCM is and functions of BCM
Business community management or BCM is a kind of holistic process of management
that helps in identification of potential threats that can impact a busies and that might
impact that business and its operations. It helps in providing a framework for building
operational resilience with capability so that they can effectively respond to any kind of
threat and safeguard their data and interest of stakeholders (Do and et. al., 2017). It helps in
integrating emergency response, crises situation, disaster recovery, business continuity etc.
Some of the main features of BCM are:
Business impact analysis: it helps in finding and prioritizing business services for production
of recovery time and point objective.
Continuity planning: Helps in planning scope to ensure personnel and assets are protected
and functioning of organization can be done quickly after recovery.
Recovery plan exercising: it helps in ensuring that business operations up to date and
accurate.
Crises management: To helps in activating continuity plan for monitoring on going
completion of recovery task during crises event.
b. Evaluation of different types of sites that can be used for backup by companies
There are majorly three types of backup sites that might be used by organizations are:
4
in order to simulate social engineering attacks. It helps in making a believable attack on
users.
Social media is another too used by hackers for carrying out their attacks. Hackers make a
fake social media account that looks very much real (von Solms and von Solms, 2018).
When a user successfully get tricked in this, they make those users click and install malicious
software or to open a video or picture which is malicious that allows hackers to take control
of users PC and steal information or another other kind of data.
Emails is another tool which is used by hackers for email phishing in which fake emails are
sent to users that help them in stealing credential information of users.
TASK 3: SECURITY CONTROLS
a. Explanation of what BCM is and functions of BCM
Business community management or BCM is a kind of holistic process of management
that helps in identification of potential threats that can impact a busies and that might
impact that business and its operations. It helps in providing a framework for building
operational resilience with capability so that they can effectively respond to any kind of
threat and safeguard their data and interest of stakeholders (Do and et. al., 2017). It helps in
integrating emergency response, crises situation, disaster recovery, business continuity etc.
Some of the main features of BCM are:
Business impact analysis: it helps in finding and prioritizing business services for production
of recovery time and point objective.
Continuity planning: Helps in planning scope to ensure personnel and assets are protected
and functioning of organization can be done quickly after recovery.
Recovery plan exercising: it helps in ensuring that business operations up to date and
accurate.
Crises management: To helps in activating continuity plan for monitoring on going
completion of recovery task during crises event.
b. Evaluation of different types of sites that can be used for backup by companies
There are majorly three types of backup sites that might be used by organizations are:
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cold site: it is a kind of backup site with no or little requirement of hardware equipment’s
installed. It is normally on office space with some important and basic utilities installed such
as a kind of cooling system, power supply etc.
Hot site: It is a facility of backup that helps in representing a backup and primary production
centre mirrored copy (Kimani, Oduol and Langat, 2019). It is mostly equipped with some
important and required software, hardware, network connectivity that allows organizations to
perform near real time back-up of create a replica of their critical or important data.
Warm site: It is considered as a middle ground between cold and hot site. It is a kind of
backup facility that require connectivity of network, and necessary hardware equipment’s
that are already pre-installed.
c. Critical evaluation of statement - “BCM: A key element in the fight against cyber security
attacks”
Today data breach and cyber- attacks are rising. With increased business opportunity and
increasing adoption of advance technology, risk for organizations has increased drastically. in
this this it has become important for organizations to understand ways in which they can respond
to cyber- attack and reduce cost of protecting data from data breach (Kimani, Oduol and Langat,
2019). Due to this BCM has today become an important element for organizations that has
successfully helped them to fight against Cyber- attack. BCM has helped organization in fighting
against any kind of cyber threat. It has helped organization in reducing cost of protecting system
from data breach, and further helps in developing an incident response plan.
5
installed. It is normally on office space with some important and basic utilities installed such
as a kind of cooling system, power supply etc.
Hot site: It is a facility of backup that helps in representing a backup and primary production
centre mirrored copy (Kimani, Oduol and Langat, 2019). It is mostly equipped with some
important and required software, hardware, network connectivity that allows organizations to
perform near real time back-up of create a replica of their critical or important data.
Warm site: It is considered as a middle ground between cold and hot site. It is a kind of
backup facility that require connectivity of network, and necessary hardware equipment’s
that are already pre-installed.
c. Critical evaluation of statement - “BCM: A key element in the fight against cyber security
attacks”
Today data breach and cyber- attacks are rising. With increased business opportunity and
increasing adoption of advance technology, risk for organizations has increased drastically. in
this this it has become important for organizations to understand ways in which they can respond
to cyber- attack and reduce cost of protecting data from data breach (Kimani, Oduol and Langat,
2019). Due to this BCM has today become an important element for organizations that has
successfully helped them to fight against Cyber- attack. BCM has helped organization in fighting
against any kind of cyber threat. It has helped organization in reducing cost of protecting system
from data breach, and further helps in developing an incident response plan.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
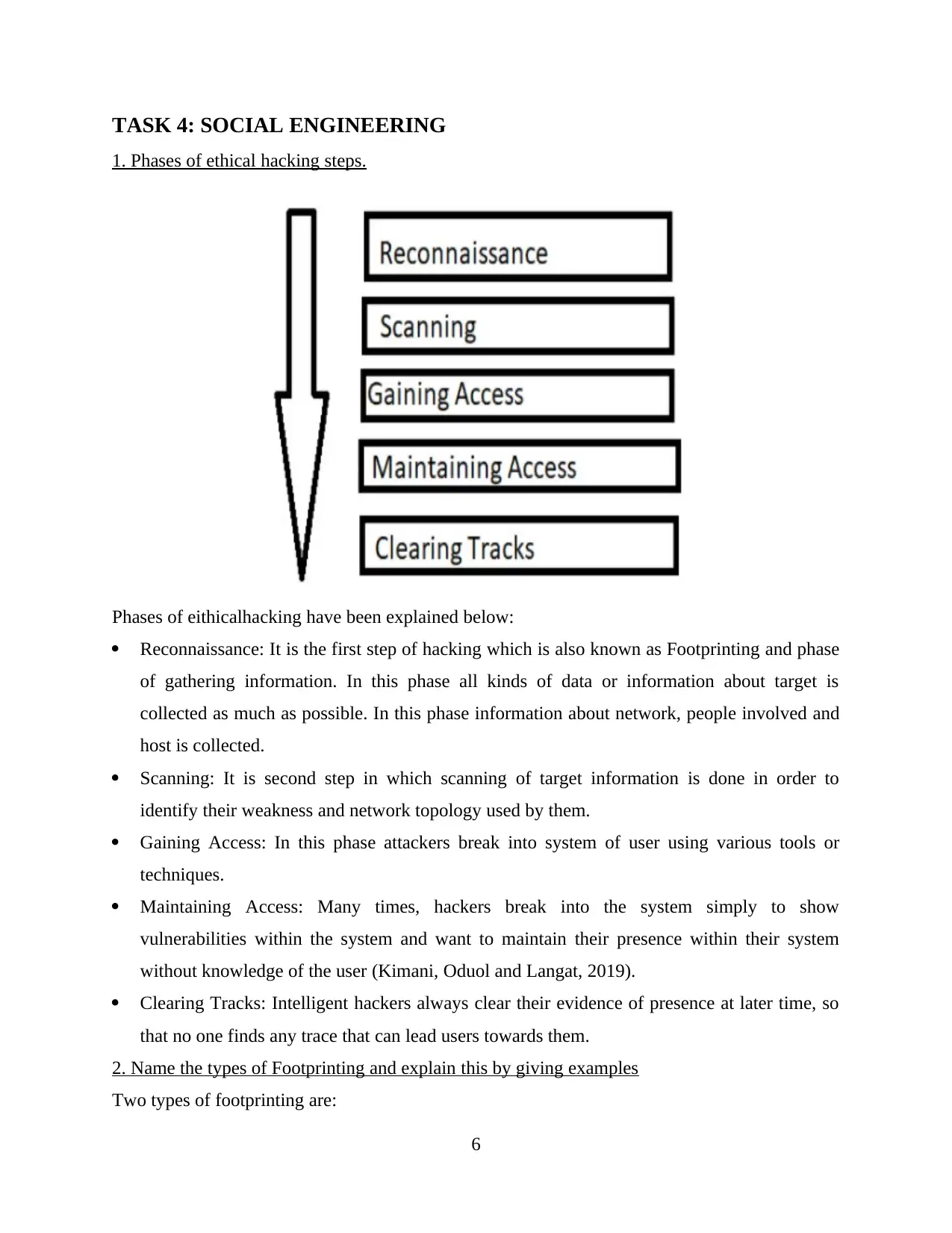
TASK 4: SOCIAL ENGINEERING
1. Phases of ethical hacking steps.
Phases of eithicalhacking have been explained below:
Reconnaissance: It is the first step of hacking which is also known as Footprinting and phase
of gathering information. In this phase all kinds of data or information about target is
collected as much as possible. In this phase information about network, people involved and
host is collected.
Scanning: It is second step in which scanning of target information is done in order to
identify their weakness and network topology used by them.
Gaining Access: In this phase attackers break into system of user using various tools or
techniques.
Maintaining Access: Many times, hackers break into the system simply to show
vulnerabilities within the system and want to maintain their presence within their system
without knowledge of the user (Kimani, Oduol and Langat, 2019).
Clearing Tracks: Intelligent hackers always clear their evidence of presence at later time, so
that no one finds any trace that can lead users towards them.
2. Name the types of Footprinting and explain this by giving examples
Two types of footprinting are:
6
1. Phases of ethical hacking steps.
Phases of eithicalhacking have been explained below:
Reconnaissance: It is the first step of hacking which is also known as Footprinting and phase
of gathering information. In this phase all kinds of data or information about target is
collected as much as possible. In this phase information about network, people involved and
host is collected.
Scanning: It is second step in which scanning of target information is done in order to
identify their weakness and network topology used by them.
Gaining Access: In this phase attackers break into system of user using various tools or
techniques.
Maintaining Access: Many times, hackers break into the system simply to show
vulnerabilities within the system and want to maintain their presence within their system
without knowledge of the user (Kimani, Oduol and Langat, 2019).
Clearing Tracks: Intelligent hackers always clear their evidence of presence at later time, so
that no one finds any trace that can lead users towards them.
2. Name the types of Footprinting and explain this by giving examples
Two types of footprinting are:
6

Active: In this hacker directly interact with target for gathering information about the target
user (Kimani, Oduol and Langat, 2019). For example: usage of Nmap tool or scanning the
target.
Passive: Trying to collect data or information about user or target without directly accessing
target or their system. For example: collecting information through public websites, social
media etc.
CONCLUSION
From the above assessment it has been identified that there are various kinds of methods
or tools that can be used by hackers for hacking because of which vulnerabilities associated with
the system can increase. It is important to understand phases of ethical hacking so that security
measures required to be taken can be enhanced. In future organization facing issues in terms of
security of their system can focus upon BCM for enhancing their overall security of system and
servicer from cyber- attack.
7
user (Kimani, Oduol and Langat, 2019). For example: usage of Nmap tool or scanning the
target.
Passive: Trying to collect data or information about user or target without directly accessing
target or their system. For example: collecting information through public websites, social
media etc.
CONCLUSION
From the above assessment it has been identified that there are various kinds of methods
or tools that can be used by hackers for hacking because of which vulnerabilities associated with
the system can increase. It is important to understand phases of ethical hacking so that security
measures required to be taken can be enhanced. In future organization facing issues in terms of
security of their system can focus upon BCM for enhancing their overall security of system and
servicer from cyber- attack.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Books and Journals
Apruzzese, G., and et. al., 2018, May. On the effectiveness of machine and deep learning for
cyber security. In 2018 10th international conference on cyber Conflict (CyCon) (pp.
371-390). IEEE.
Coulter, R., and et. al., 2019. Data-driven cyber security in perspective—Intelligent traffic
analysis. IEEE transactions on cybernetics. 50(7). pp.3081-3093.
Do, C.T., and et. al., 2017. Game theory for cyber security and privacy. ACM Computing Surveys
(CSUR). 50(2). pp.1-37.
Kimani, K., Oduol, V. and Langat, K., 2019. Cyber security challenges for IoT-based smart grid
networks. International Journal of Critical Infrastructure Protection. 25. pp.36-49.
Lezzi, M., Lazoi, M. and Corallo, A., 2018. Cybersecurity for Industry 4.0 in the current
literature: A reference framework. Computers in Industry. 103. pp.97-110.
Maglaras, L.A., and et. al., 2018. Cyber security of critical infrastructures. Ict Express. 4(1).
pp.42-45.
Nguyen, T.T. and Reddi, V.J., 2019. Deep reinforcement learning for cyber security. arXiv
preprint arXiv:1906.05799.
von Solms, B. and von Solms, R., 2018. Cybersecurity and information security–what goes
where?. Information & Computer Security.
8
Books and Journals
Apruzzese, G., and et. al., 2018, May. On the effectiveness of machine and deep learning for
cyber security. In 2018 10th international conference on cyber Conflict (CyCon) (pp.
371-390). IEEE.
Coulter, R., and et. al., 2019. Data-driven cyber security in perspective—Intelligent traffic
analysis. IEEE transactions on cybernetics. 50(7). pp.3081-3093.
Do, C.T., and et. al., 2017. Game theory for cyber security and privacy. ACM Computing Surveys
(CSUR). 50(2). pp.1-37.
Kimani, K., Oduol, V. and Langat, K., 2019. Cyber security challenges for IoT-based smart grid
networks. International Journal of Critical Infrastructure Protection. 25. pp.36-49.
Lezzi, M., Lazoi, M. and Corallo, A., 2018. Cybersecurity for Industry 4.0 in the current
literature: A reference framework. Computers in Industry. 103. pp.97-110.
Maglaras, L.A., and et. al., 2018. Cyber security of critical infrastructures. Ict Express. 4(1).
pp.42-45.
Nguyen, T.T. and Reddi, V.J., 2019. Deep reinforcement learning for cyber security. arXiv
preprint arXiv:1906.05799.
von Solms, B. and von Solms, R., 2018. Cybersecurity and information security–what goes
where?. Information & Computer Security.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





