Cybersecurity Report: BYOD, Authentication, and Anti-Spam
VerifiedAdded on 2022/08/18
|10
|2358
|23
Report
AI Summary
This cybersecurity report, prepared for Southern Cross University's CMP71001 course, addresses contemporary cyber threats, focusing on BYOD security, authentication, and anti-spam measures. The report begins with a BYOD risk assessment, identifying potential technological, policy, human, and organizational vulnerabilities within the university's information system. It then proposes a certificate-based authentication system to enhance password security and mitigate risks. Finally, the report outlines anti-spam guidelines, including a review of the Spam Act 2003 and a discussion of various spam types and their impact. The report emphasizes the importance of robust security measures to protect sensitive data and maintain the university's operational integrity. The report concludes with recommendations for implementing these security measures effectively.

Running Head: CYBERSECURITY
Information system- Risks and Threats
Name of the Student
Name of the University
Author Note
Information system- Risks and Threats
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBERSECURITY
Table of Contents
Introduction......................................................................................................................................2
Task 1: BYOD risk assessment.......................................................................................................2
Task 2: Certificate-based authentication.........................................................................................5
Task 3: Anti-spam guideline............................................................................................................6
Conclusion.......................................................................................................................................7
Reference.........................................................................................................................................8
Table of Contents
Introduction......................................................................................................................................2
Task 1: BYOD risk assessment.......................................................................................................2
Task 2: Certificate-based authentication.........................................................................................5
Task 3: Anti-spam guideline............................................................................................................6
Conclusion.......................................................................................................................................7
Reference.........................................................................................................................................8

2CYBERSECURITY
Introduction
The key risk that arises within the Southern Cross University information system is
assessed and identified. Threats of cyber security are needed to be assessed properly so that it
becomes easy to protect the organization from unwanted risks (University 2020). The BYOD
policy is designed to ensure that proper safety is offered towards the members associated with
the university. The assessment will focus on assessing the risks associated with the BYOD policy
for managing the universities information system. The second part of the report aims at
designing an authenticated system for managing the passwords. The last part of the report aims
at describing the spamming activities that arises with the use of BYOD.
Task 1: BYOD risk assessment
The assets of information are the knowledge available to the organization and in this case
of the university’s assets. All the details and the information regarding the activities going on in
the university are the assets to the organization (French, Guo and Shim 2014). Along that the
retention of that information is also required. The information assets in the university as the
information about the students, details of the library books. Payment transactions of the
university, tie-ups with other organizations, etc.
The policy of bring your own device is designed for the purpose of offering a better
access towards the information system. With the introduction of BYOD it becomes difficult to
manage the performance (Abomhara 2015). The key risks that are likely to arise in the
organization with the use of BYOD policy within are technological issues, policy and aspects of
regulation, human aspects and the organizational issues.
Introduction
The key risk that arises within the Southern Cross University information system is
assessed and identified. Threats of cyber security are needed to be assessed properly so that it
becomes easy to protect the organization from unwanted risks (University 2020). The BYOD
policy is designed to ensure that proper safety is offered towards the members associated with
the university. The assessment will focus on assessing the risks associated with the BYOD policy
for managing the universities information system. The second part of the report aims at
designing an authenticated system for managing the passwords. The last part of the report aims
at describing the spamming activities that arises with the use of BYOD.
Task 1: BYOD risk assessment
The assets of information are the knowledge available to the organization and in this case
of the university’s assets. All the details and the information regarding the activities going on in
the university are the assets to the organization (French, Guo and Shim 2014). Along that the
retention of that information is also required. The information assets in the university as the
information about the students, details of the library books. Payment transactions of the
university, tie-ups with other organizations, etc.
The policy of bring your own device is designed for the purpose of offering a better
access towards the information system. With the introduction of BYOD it becomes difficult to
manage the performance (Abomhara 2015). The key risks that are likely to arise in the
organization with the use of BYOD policy within are technological issues, policy and aspects of
regulation, human aspects and the organizational issues.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBERSECURITY
Technological risks are considered as the most important security challenges that arise
within the system. It becomes difficult to protect the data within the university. Most important
technical risk that arises with the introduction of BYOD in university is the chances of
employees altering the data or stealing the data for the purpose of harming the university. Data
theft can hamper the overall working procedure. Thus it can be stated that it is crucial to evaluate
the policies of BYOD properly for the purpose of managing the performance. On the other hand
the university performance gets hampered with the use of the BYOD policy (Dhingra 2016). The
identity theft can occur within the system that will eventually lead to hampering the data stored
and maintained within the university.
Threat towards business functionalities and data has the potential to hamper the
performance. The policy will allow the students and employees to bring their own devices for
carrying out any activity. This will eventually lead to hampering the performance. The data
leakage is considered as the biggest concern when using the BYOD policies (Vorakulpipat et al.
2017). The chances of data loss and data theft increases with the implementation of these policy.
It becomes difficult to manage the security that is maintained over the devices. The performance
of the employees and student needs to monitor properly so that it becomes difficult for them to
hamper the data.
The introduction of BYOD policy has the potential to exploit the data by increasing the
risks associated with the data (Putri and Hovav 2014). Beside this the poor management of
devices can hamper the business performance of the university. Thus it is important to ensure
that policy is designed effectively so that the management of data can be carried out properly
without any risks. The possible risks with the assets of the information system of the university
will be increased with the BYOD as it will hamper the network of the university (Armando et al.
Technological risks are considered as the most important security challenges that arise
within the system. It becomes difficult to protect the data within the university. Most important
technical risk that arises with the introduction of BYOD in university is the chances of
employees altering the data or stealing the data for the purpose of harming the university. Data
theft can hamper the overall working procedure. Thus it can be stated that it is crucial to evaluate
the policies of BYOD properly for the purpose of managing the performance. On the other hand
the university performance gets hampered with the use of the BYOD policy (Dhingra 2016). The
identity theft can occur within the system that will eventually lead to hampering the data stored
and maintained within the university.
Threat towards business functionalities and data has the potential to hamper the
performance. The policy will allow the students and employees to bring their own devices for
carrying out any activity. This will eventually lead to hampering the performance. The data
leakage is considered as the biggest concern when using the BYOD policies (Vorakulpipat et al.
2017). The chances of data loss and data theft increases with the implementation of these policy.
It becomes difficult to manage the security that is maintained over the devices. The performance
of the employees and student needs to monitor properly so that it becomes difficult for them to
hamper the data.
The introduction of BYOD policy has the potential to exploit the data by increasing the
risks associated with the data (Putri and Hovav 2014). Beside this the poor management of
devices can hamper the business performance of the university. Thus it is important to ensure
that policy is designed effectively so that the management of data can be carried out properly
without any risks. The possible risks with the assets of the information system of the university
will be increased with the BYOD as it will hamper the network of the university (Armando et al.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
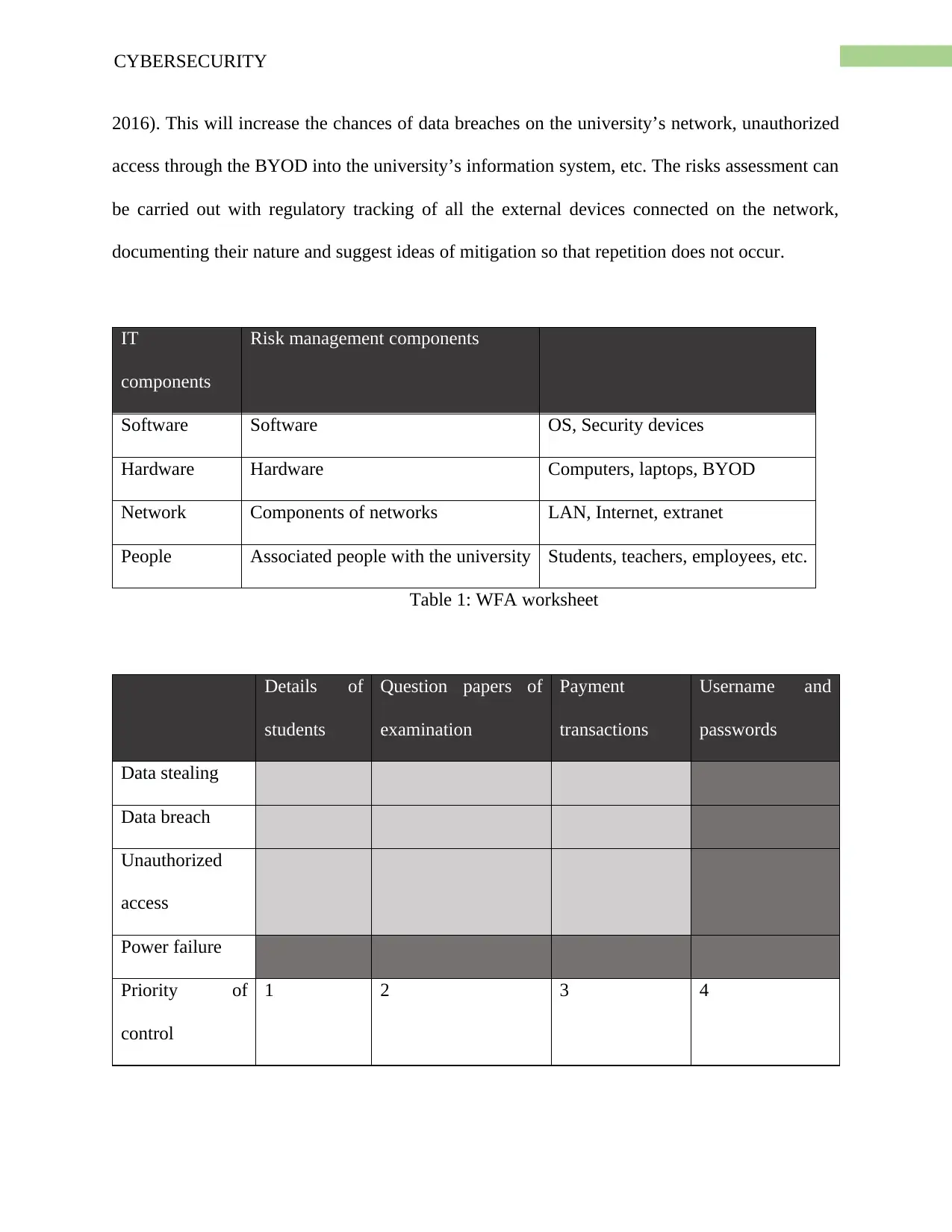
4CYBERSECURITY
2016). This will increase the chances of data breaches on the university’s network, unauthorized
access through the BYOD into the university’s information system, etc. The risks assessment can
be carried out with regulatory tracking of all the external devices connected on the network,
documenting their nature and suggest ideas of mitigation so that repetition does not occur.
IT
components
Risk management components
Software Software OS, Security devices
Hardware Hardware Computers, laptops, BYOD
Network Components of networks LAN, Internet, extranet
People Associated people with the university Students, teachers, employees, etc.
Table 1: WFA worksheet
Details of
students
Question papers of
examination
Payment
transactions
Username and
passwords
Data stealing
Data breach
Unauthorized
access
Power failure
Priority of
control
1 2 3 4
2016). This will increase the chances of data breaches on the university’s network, unauthorized
access through the BYOD into the university’s information system, etc. The risks assessment can
be carried out with regulatory tracking of all the external devices connected on the network,
documenting their nature and suggest ideas of mitigation so that repetition does not occur.
IT
components
Risk management components
Software Software OS, Security devices
Hardware Hardware Computers, laptops, BYOD
Network Components of networks LAN, Internet, extranet
People Associated people with the university Students, teachers, employees, etc.
Table 1: WFA worksheet
Details of
students
Question papers of
examination
Payment
transactions
Username and
passwords
Data stealing
Data breach
Unauthorized
access
Power failure
Priority of
control
1 2 3 4

5CYBERSECURITY
Table 2: TVA worksheet
Task 2: Certificate-based authentication
BYOD policy is introduced for the purpose of managing the business performance. There
is a need to ensure that the risks identified within the BYOD are mitigated properly so that it
becomes easy to manage the benefits. There is a need to identify the risks at the early stages so
that it becomes easy to protect the university from unwanted threats, malicious attacks and data
breaches. It is important to ensure that the system are processes and maintained with proper
authenticated system so that the impacts can be reduced. IT professionals are concerned about
the way BYOD policy can hamper the performance of the university. Thus it is essential to
ensure that proper security measures are integrated within the system for the purpose of reducing
the risks. This will also ensure that the productivity has increased with an effective security
policy. At present the university uses the scheme of password based authentication for the
purpose of managing the way people are utilizing the data (O'Neill et al. 2017). With the help of
proper certificate based authentication scheme it becomes easy to protect the data. This uses a
public key for the purpose of performing the cryptography. This validates that only the
authenticate users are allowed to access the data. The digital certificate is referred to the
electronic form that contains digital signature, identification data and a public key so that it
becomes easy to manage the data. Thus it is highly suggested that the process of certificate based
authentication will ensure that the data are protected effectively within the system (Porambage et
al. 2014). The certificate based authentication is defines as the utilization of certificate that is
utilized for the purpose of identifying the users, devices or machines that are needed to be
accessed while accessing the data. Whenever a user signs on to the server they are responsible
for providing the digital certificate with signature and public key for the authority of
Table 2: TVA worksheet
Task 2: Certificate-based authentication
BYOD policy is introduced for the purpose of managing the business performance. There
is a need to ensure that the risks identified within the BYOD are mitigated properly so that it
becomes easy to manage the benefits. There is a need to identify the risks at the early stages so
that it becomes easy to protect the university from unwanted threats, malicious attacks and data
breaches. It is important to ensure that the system are processes and maintained with proper
authenticated system so that the impacts can be reduced. IT professionals are concerned about
the way BYOD policy can hamper the performance of the university. Thus it is essential to
ensure that proper security measures are integrated within the system for the purpose of reducing
the risks. This will also ensure that the productivity has increased with an effective security
policy. At present the university uses the scheme of password based authentication for the
purpose of managing the way people are utilizing the data (O'Neill et al. 2017). With the help of
proper certificate based authentication scheme it becomes easy to protect the data. This uses a
public key for the purpose of performing the cryptography. This validates that only the
authenticate users are allowed to access the data. The digital certificate is referred to the
electronic form that contains digital signature, identification data and a public key so that it
becomes easy to manage the data. Thus it is highly suggested that the process of certificate based
authentication will ensure that the data are protected effectively within the system (Porambage et
al. 2014). The certificate based authentication is defines as the utilization of certificate that is
utilized for the purpose of identifying the users, devices or machines that are needed to be
accessed while accessing the data. Whenever a user signs on to the server they are responsible
for providing the digital certificate with signature and public key for the authority of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBERSECURITY
certification. The server then focuses on authenticating the users with use of a public key
cryptography.
The main objective behind using certificate based authentication process is that it helps in
ensuring that minimal involvement needed from the users end. In addition to this the
communication process can be secured properly that will further ensure that the data maintained
and shared are authenticate. It becomes very much essential to ensure that the shared data are
authenticated. Apart from this there is no need to have any additional hardware. Certificates are
designed in such a way that it becomes easy to accommodate the multi device users. This will
ensure that the tokens are distributed and managed properly (Gross et al. 2015). There is no need
to make backup plan for managing the tokens. It can be done effectively with the use of
certificate based authentication. Moreover the certificate based authentication solution is
designed with a platform that is cloud based management, it helps in making the administration
process efficiently. Hence it can be stated that with the help of proper support it becomes easy to
manage the university performance. Thus it is crucial to ensure that proper security measures are
followed within the data.
Task 3: Anti-spam guideline
SPAM is defined as the messages sent which is irrelevant in nature via the internet for the
purpose off hampering their lives. The SPAM is referred to the large number of contents that are
sent for the purpose of phishing, advertisement and spreading malware (Nagalingam et al. 2015).
According to the Spam Act 2003, the ban on the electronic message which is commercially
unsolicited, the software of address harvesting must not produces, use or obtains any address list,
the electronic message must follow the regulations that does not allow to send electronic
messages that are commercial, the present of facility that is functionally unsubscribed in the
certification. The server then focuses on authenticating the users with use of a public key
cryptography.
The main objective behind using certificate based authentication process is that it helps in
ensuring that minimal involvement needed from the users end. In addition to this the
communication process can be secured properly that will further ensure that the data maintained
and shared are authenticate. It becomes very much essential to ensure that the shared data are
authenticated. Apart from this there is no need to have any additional hardware. Certificates are
designed in such a way that it becomes easy to accommodate the multi device users. This will
ensure that the tokens are distributed and managed properly (Gross et al. 2015). There is no need
to make backup plan for managing the tokens. It can be done effectively with the use of
certificate based authentication. Moreover the certificate based authentication solution is
designed with a platform that is cloud based management, it helps in making the administration
process efficiently. Hence it can be stated that with the help of proper support it becomes easy to
manage the university performance. Thus it is crucial to ensure that proper security measures are
followed within the data.
Task 3: Anti-spam guideline
SPAM is defined as the messages sent which is irrelevant in nature via the internet for the
purpose off hampering their lives. The SPAM is referred to the large number of contents that are
sent for the purpose of phishing, advertisement and spreading malware (Nagalingam et al. 2015).
According to the Spam Act 2003, the ban on the electronic message which is commercially
unsolicited, the software of address harvesting must not produces, use or obtains any address list,
the electronic message must follow the regulations that does not allow to send electronic
messages that are commercial, the present of facility that is functionally unsubscribed in the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBERSECURITY
electronic message which is commercial in nature, the message must contain all the information
of the organization or the individual who intended to send the message and lastly the act contains
the consequences that will be faced by anyone who disobeys this with injunctions and legal
penalties (Kigerl 2016).
The different types of SPAM that has the potential to hamper the business performance are:
Malicious links: Spreading malicious links for hampering the performance. This links are
created for the purpose of misleading the users or harming or the devices with which they
are interacting.
Bulk messaging: the bulk messaging procedure mainly involves sending a text message
towards a group of people for short period of time. The bulk messages are used for the
spreading malware messages.
Sharing undesired messages: the messages are shared for the purpose of threatening the
users with unwanted content. This automatically hampers the performance. The messages
and malicious contents can hamper the performance. Hence it can be stated that SPAM
messages has the potential to hamper the stability of the users.
Conclusion
It can be concluded from the above report that with the help of an effective policy it
becomes easy to manage the activities and work around any organization. In case of the
university it regulates in the same way. The risks are identified efficiently so that it becomes easy
to manage the activities at the right time. All the sections that is the risks related to BYOD to the
university, the shift to the authentication that is certificate based and following up of the
guidelines of Anti-spam are required to undertake by the organization.
electronic message which is commercial in nature, the message must contain all the information
of the organization or the individual who intended to send the message and lastly the act contains
the consequences that will be faced by anyone who disobeys this with injunctions and legal
penalties (Kigerl 2016).
The different types of SPAM that has the potential to hamper the business performance are:
Malicious links: Spreading malicious links for hampering the performance. This links are
created for the purpose of misleading the users or harming or the devices with which they
are interacting.
Bulk messaging: the bulk messaging procedure mainly involves sending a text message
towards a group of people for short period of time. The bulk messages are used for the
spreading malware messages.
Sharing undesired messages: the messages are shared for the purpose of threatening the
users with unwanted content. This automatically hampers the performance. The messages
and malicious contents can hamper the performance. Hence it can be stated that SPAM
messages has the potential to hamper the stability of the users.
Conclusion
It can be concluded from the above report that with the help of an effective policy it
becomes easy to manage the activities and work around any organization. In case of the
university it regulates in the same way. The risks are identified efficiently so that it becomes easy
to manage the activities at the right time. All the sections that is the risks related to BYOD to the
university, the shift to the authentication that is certificate based and following up of the
guidelines of Anti-spam are required to undertake by the organization.

8CYBERSECURITY
Reference
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Armando, A., Costa, G., Merlo, A., Verderame, L. and Wrona, K., 2016, May. Developing a
NATO BYOD security policy. In 2016 International Conference on Military Communications
and Information Systems (ICMCIS) (pp. 1-6). IEEE.
Dhingra, M., 2016. Legal issues in secure implementation of bring your own device (BYOD).
Procedia Computer Science, 78(C), pp.179-184.
French, A.M., Guo, C. and Shim, J.P., 2014. Current status, issues, and future of bring your own
device (BYOD). Communications of the Association for Information Systems, 35(1), p.10.
Gross, H., Hölbl, M., Slamanig, D. and Spreitzer, R., 2015, December. Privacy-aware
authentication in the internet of things. In International Conference on Cryptology and Network
Security (pp. 32-39). Springer, Cham.
Kigerl, A.C., 2016. Deterring spammers: impact assessment of the CAN SPAM act on email
spam rates. Criminal Justice Policy Review, 27(8), pp.791-811.
Nagalingam, V., Samy, G.N., Maarop, N., Azmi, N.F.M., Shamugam, B. and Ahmad, R., 2015.
Proposing Awareness Guidelines on Phishing Attempts among Students. Open International
Journal of Informatics (OIJI), 3(2), pp.1-9.
O'Neill, M., Heidbrink, S., Ruoti, S., Whitehead, J., Bunker, D., Dickinson, L., Hendershot, T.,
Reynolds, J., Seamons, K. and Zappala, D., 2017. Trustbase: an architecture to repair and
strengthen certificate-based authentication. In 26th {USENIX} Security Symposium ({USENIX}
Security 17) (pp. 609-624).
Reference
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Armando, A., Costa, G., Merlo, A., Verderame, L. and Wrona, K., 2016, May. Developing a
NATO BYOD security policy. In 2016 International Conference on Military Communications
and Information Systems (ICMCIS) (pp. 1-6). IEEE.
Dhingra, M., 2016. Legal issues in secure implementation of bring your own device (BYOD).
Procedia Computer Science, 78(C), pp.179-184.
French, A.M., Guo, C. and Shim, J.P., 2014. Current status, issues, and future of bring your own
device (BYOD). Communications of the Association for Information Systems, 35(1), p.10.
Gross, H., Hölbl, M., Slamanig, D. and Spreitzer, R., 2015, December. Privacy-aware
authentication in the internet of things. In International Conference on Cryptology and Network
Security (pp. 32-39). Springer, Cham.
Kigerl, A.C., 2016. Deterring spammers: impact assessment of the CAN SPAM act on email
spam rates. Criminal Justice Policy Review, 27(8), pp.791-811.
Nagalingam, V., Samy, G.N., Maarop, N., Azmi, N.F.M., Shamugam, B. and Ahmad, R., 2015.
Proposing Awareness Guidelines on Phishing Attempts among Students. Open International
Journal of Informatics (OIJI), 3(2), pp.1-9.
O'Neill, M., Heidbrink, S., Ruoti, S., Whitehead, J., Bunker, D., Dickinson, L., Hendershot, T.,
Reynolds, J., Seamons, K. and Zappala, D., 2017. Trustbase: an architecture to repair and
strengthen certificate-based authentication. In 26th {USENIX} Security Symposium ({USENIX}
Security 17) (pp. 609-624).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBERSECURITY
Porambage, P., Schmitt, C., Kumar, P., Gurtov, A. and Ylianttila, M., 2014, April. Two-phase
authentication protocol for wireless sensor networks in distributed IoT applications. In 2014
IEEE Wireless Communications and Networking Conference (WCNC) (pp. 2728-2733). Ieee.
Putri, F.F. and Hovav, A., 2014. Employees compliance with BYOD security policy: Insights
from reactance, organizational justice, and protection motivation theory.
University, S. (2020). Home - Southern Cross University. [online] Scu.edu.au. Available at:
https://www.scu.edu.au/ [Accessed 31 Jan. 2020].
Vorakulpipat, C., Sirapaisan, S., Rattanalerdnusorn, E. and Savangsuk, V., 2017. A policy-based
framework for preserving confidentiality in BYOD environments: A review of information
security perspectives. Security and communication networks, 2017.
Porambage, P., Schmitt, C., Kumar, P., Gurtov, A. and Ylianttila, M., 2014, April. Two-phase
authentication protocol for wireless sensor networks in distributed IoT applications. In 2014
IEEE Wireless Communications and Networking Conference (WCNC) (pp. 2728-2733). Ieee.
Putri, F.F. and Hovav, A., 2014. Employees compliance with BYOD security policy: Insights
from reactance, organizational justice, and protection motivation theory.
University, S. (2020). Home - Southern Cross University. [online] Scu.edu.au. Available at:
https://www.scu.edu.au/ [Accessed 31 Jan. 2020].
Vorakulpipat, C., Sirapaisan, S., Rattanalerdnusorn, E. and Savangsuk, V., 2017. A policy-based
framework for preserving confidentiality in BYOD environments: A review of information
security perspectives. Security and communication networks, 2017.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





