University Cyber Security Report: Authentication and Risk Assessment
VerifiedAdded on 2023/06/05
|10
|1882
|414
Report
AI Summary
This report delves into the cyber security landscape of a university, addressing critical issues such as network authentication, the risks associated with Bring Your Own Device (BYOD) policies, and anti-spam measures. The report begins by assessing the risks of a newly incorporated BYOD policy, highlighting vulnerabilities and recommending risk mitigation strategies. It then compares and contrasts certificate-based authentication with password-based authentication, emphasizing the enhanced security provided by the former. The report also outlines anti-spam guidelines, discussing the nature of spam emails and recommending strategies to minimize spam threats within the university network, including the use of anti-spam software and user awareness. The conclusion summarizes the key findings and offers recommendations for improving overall cyber security posture. This report is a valuable resource for understanding and addressing cyber security challenges in educational institutions.

CYBER SECURITY
Cyber Security
Name of the Student
Name of the University
Author Note
Cyber Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CYBER SECURITY
Table of Contents
Introduction................................................................................................................................2
Task 1: BOYD risk assessment..................................................................................................2
Task 2: Certificate-based Authentication...................................................................................3
Task 3: Anti-spam guideline......................................................................................................5
Conclusion..................................................................................................................................6
Reference....................................................................................................................................7
CYBER SECURITY
Table of Contents
Introduction................................................................................................................................2
Task 1: BOYD risk assessment..................................................................................................2
Task 2: Certificate-based Authentication...................................................................................3
Task 3: Anti-spam guideline......................................................................................................5
Conclusion..................................................................................................................................6
Reference....................................................................................................................................7

2
CYBER SECURITY
Introduction
The prime objective of this paper is to focus on the privacy and security issues
associated with a university. The university has different kinds of stakeholders such as the
internal stakeholder and external stake holder (Yan et al. 2018). The different types of
stakeholders use the private network of the college which is a real matter of concern
considering the network security of the college. The paper will be focusing on the different
threats which the college network might be facing in the coming years. The paper will
provide a perception about the newly adopted policy of the college authority (Liu and
Murphy 2016). The existing and the proposed type of authentication types will be discussed
in this paper with prime importance. The paper will also highlight the effectiveness of the
password-based authentication schemes with the certificate-based authentication.
Task 1: BOYD risk assessment
This unit of the paper will be focusing on the newly incorporated policy of a
university. The new policy was supposed to be helping the college authority to cope up with
the internal threats of the private network used by the college authority (Pusey, Gondree and
Peterson 2016). The website used by the college authority has two major specifications such
as the user module which is maintained by the students and the admin panel which are
maintained by the teaching staffs of the college. Alteration of essential data can be a huge
loss from the point of view of both college authority as well as from student perspective
(Baylis et al. 2017). The library management system is the other essential component of the
college which is very much prone to the security issue as a wide range of users both outside
and inside the environment are accessing the system. The threats coming from the internal
stakeholders is also considered as a cyber-security threat. The newly incorporated BRING
CYBER SECURITY
Introduction
The prime objective of this paper is to focus on the privacy and security issues
associated with a university. The university has different kinds of stakeholders such as the
internal stakeholder and external stake holder (Yan et al. 2018). The different types of
stakeholders use the private network of the college which is a real matter of concern
considering the network security of the college. The paper will be focusing on the different
threats which the college network might be facing in the coming years. The paper will
provide a perception about the newly adopted policy of the college authority (Liu and
Murphy 2016). The existing and the proposed type of authentication types will be discussed
in this paper with prime importance. The paper will also highlight the effectiveness of the
password-based authentication schemes with the certificate-based authentication.
Task 1: BOYD risk assessment
This unit of the paper will be focusing on the newly incorporated policy of a
university. The new policy was supposed to be helping the college authority to cope up with
the internal threats of the private network used by the college authority (Pusey, Gondree and
Peterson 2016). The website used by the college authority has two major specifications such
as the user module which is maintained by the students and the admin panel which are
maintained by the teaching staffs of the college. Alteration of essential data can be a huge
loss from the point of view of both college authority as well as from student perspective
(Baylis et al. 2017). The library management system is the other essential component of the
college which is very much prone to the security issue as a wide range of users both outside
and inside the environment are accessing the system. The threats coming from the internal
stakeholders is also considered as a cyber-security threat. The newly incorporated BRING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CYBER SECURITY
YOUR OWN DEVICE policy has some significant issues related with it such as it increases
the chances of intrusions as the college network gets associated with wide range of personal
devices (Tang 2017). This may have a negative impact on the privacy and security of the
college network. As a security consultant effective risk analysis technique such as the brain
storming should be adopted by the college authorities as the technique can quantify the level
of vulnerability and helpful in proposing a risk mitigating plan (Muhirwe. and White 2016).
The implementation of a dedicated IT security team can be useful under this circumstances.
After considering all the risk associated with the new policy it can be said that this policy is
not at all suited for this organisation as it has more limitations than benefits.
Task 2: Certificate-based Authentication
The foremost determination of this unit of the paper is to focus on the effectiveness of
two types of authentication schemes. The security of a password based systems is very much
less than the certificate based systems. The login credentials of the users can be easily tracked
in the password based systems while in certificate based systems (Raj et al. 2017). The use of
public key cryptography along with the digital certificate for certificate based authentication
purposes is the main reason why it give so much security comparing with the password based
systems. The privacy and security provided by certificate based authentication is helpful in
mitigating the server related issues (Settle, Doyle and Steinbach 2017). The certificate based
authentication involves the application of the digital certificates which enhances the security
of the network. The risks and vulnerabilities associated with the newly incorporated BYOD
policy can be effectively minimised with the help of the certificate based authentication
technique (Simon and Banford 2017). It can be said that the application of the certificate
based authentication scheme can provide more security the college than the password based
authentication process.
CYBER SECURITY
YOUR OWN DEVICE policy has some significant issues related with it such as it increases
the chances of intrusions as the college network gets associated with wide range of personal
devices (Tang 2017). This may have a negative impact on the privacy and security of the
college network. As a security consultant effective risk analysis technique such as the brain
storming should be adopted by the college authorities as the technique can quantify the level
of vulnerability and helpful in proposing a risk mitigating plan (Muhirwe. and White 2016).
The implementation of a dedicated IT security team can be useful under this circumstances.
After considering all the risk associated with the new policy it can be said that this policy is
not at all suited for this organisation as it has more limitations than benefits.
Task 2: Certificate-based Authentication
The foremost determination of this unit of the paper is to focus on the effectiveness of
two types of authentication schemes. The security of a password based systems is very much
less than the certificate based systems. The login credentials of the users can be easily tracked
in the password based systems while in certificate based systems (Raj et al. 2017). The use of
public key cryptography along with the digital certificate for certificate based authentication
purposes is the main reason why it give so much security comparing with the password based
systems. The privacy and security provided by certificate based authentication is helpful in
mitigating the server related issues (Settle, Doyle and Steinbach 2017). The certificate based
authentication involves the application of the digital certificates which enhances the security
of the network. The risks and vulnerabilities associated with the newly incorporated BYOD
policy can be effectively minimised with the help of the certificate based authentication
technique (Simon and Banford 2017). It can be said that the application of the certificate
based authentication scheme can provide more security the college than the password based
authentication process.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
CYBER SECURITY
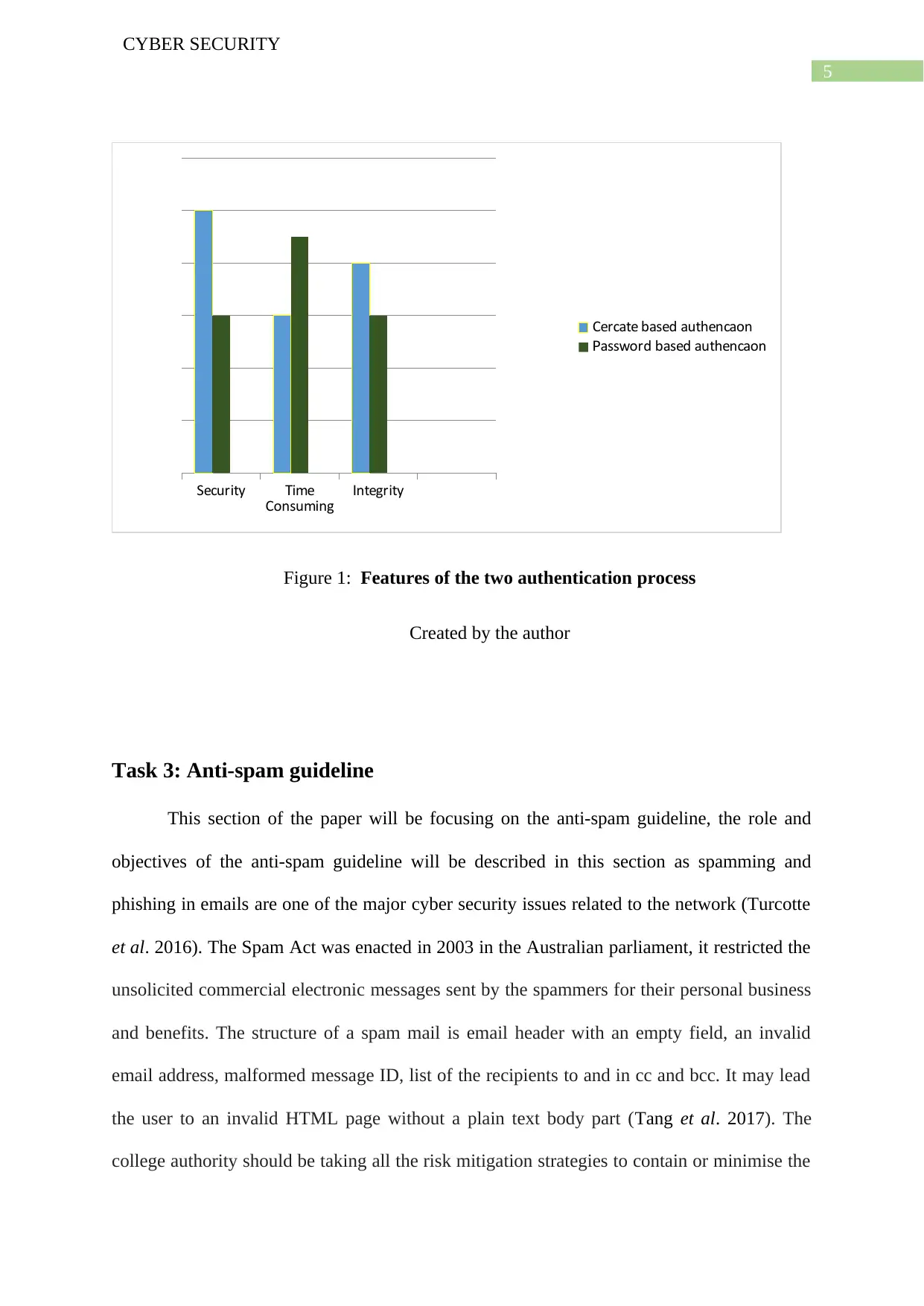
Password based authentication Certificate based authentication
The password based authentication usually
takes more time than the certificate based
authentication scheme.
This authentication scheme is less time
consuming than password based
authentication.
The security provided by this type of
authentication is not enough to main
security and privacy of any network.
The security provided by this authentication
scheme is way better than the password
based authentication.
Complex alphanumeric passwords with
symbols should be used in this
authentication scheme.
Digital certificates are used in this type of
authentication scheme.
Reliability and integrity is not at all
maintained in this technique.
Reliability and integrity of the system can
be achieved with the help of this
authentication technique.
Table 1: Difference between certificate based and password-based authentication
Created by the author
CYBER SECURITY
Password based authentication Certificate based authentication
The password based authentication usually
takes more time than the certificate based
authentication scheme.
This authentication scheme is less time
consuming than password based
authentication.
The security provided by this type of
authentication is not enough to main
security and privacy of any network.
The security provided by this authentication
scheme is way better than the password
based authentication.
Complex alphanumeric passwords with
symbols should be used in this
authentication scheme.
Digital certificates are used in this type of
authentication scheme.
Reliability and integrity is not at all
maintained in this technique.
Reliability and integrity of the system can
be achieved with the help of this
authentication technique.
Table 1: Difference between certificate based and password-based authentication
Created by the author
5
CYBER SECURITY
Security imeT
Consuming ntegrityI
Certificate based authentication
assword based authenticationP
Figure 1: Features of the two authentication process
Created by the author
Task 3: Anti-spam guideline
This section of the paper will be focusing on the anti-spam guideline, the role and
objectives of the anti-spam guideline will be described in this section as spamming and
phishing in emails are one of the major cyber security issues related to the network (Turcotte
et al. 2016). The Spam Act was enacted in 2003 in the Australian parliament, it restricted the
unsolicited commercial electronic messages sent by the spammers for their personal business
and benefits. The structure of a spam mail is email header with an empty field, an invalid
email address, malformed message ID, list of the recipients to and in cc and bcc. It may lead
the user to an invalid HTML page without a plain text body part (Tang et al. 2017). The
college authority should be taking all the risk mitigation strategies to contain or minimise the
CYBER SECURITY
Security imeT
Consuming ntegrityI
Certificate based authentication
assword based authenticationP
Figure 1: Features of the two authentication process
Created by the author
Task 3: Anti-spam guideline
This section of the paper will be focusing on the anti-spam guideline, the role and
objectives of the anti-spam guideline will be described in this section as spamming and
phishing in emails are one of the major cyber security issues related to the network (Turcotte
et al. 2016). The Spam Act was enacted in 2003 in the Australian parliament, it restricted the
unsolicited commercial electronic messages sent by the spammers for their personal business
and benefits. The structure of a spam mail is email header with an empty field, an invalid
email address, malformed message ID, list of the recipients to and in cc and bcc. It may lead
the user to an invalid HTML page without a plain text body part (Tang et al. 2017). The
college authority should be taking all the risk mitigation strategies to contain or minimise the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CYBER SECURITY
issues related to the spam emails. Strict guidelines should be implemented by the governing
body of the college so that the stakeholders are aware of the issues coming from the spam
emails. The practised of using the anti-spam soft wares should be more encouraged in every
computer system in the college network. Ad block options should be installed in the
computer system which can mitigate the risks involved considering the privacy and security
of the college (Calhoun 2017). The stakeholders of the college should not be accessing the
spam messages and avoid the unsubscribe options as it will notify the spammers about the
user activities.
Conclusion
From the above paper, it can be concluded that there are different types of security
and privacy issues in the private network used in the college. The enhanced specifications of
two types of authentication processes are highlighted in this paper in such a way that it will
be helping the readers to know about the usability of those authentication processes. The
paper will also provide an in-depth knowledge about the server validation of those
authentication processes. The extensive development in the field of Information technology
has given rise to different cyber security issues such as ransomeware. The paper highlights an
anti-spam guideline which will be helpful in containing those cyber security issues. The
guideline includes the definition of the spam and the different types of spam emails. The
paper also focuses on the different risk mitigation strategies against the spam threats.
Instructions are given to the IT administrators of the college authorities to minimize the spam
threats as well as the other types of cyber security threats such as ransomeware.
CYBER SECURITY
issues related to the spam emails. Strict guidelines should be implemented by the governing
body of the college so that the stakeholders are aware of the issues coming from the spam
emails. The practised of using the anti-spam soft wares should be more encouraged in every
computer system in the college network. Ad block options should be installed in the
computer system which can mitigate the risks involved considering the privacy and security
of the college (Calhoun 2017). The stakeholders of the college should not be accessing the
spam messages and avoid the unsubscribe options as it will notify the spammers about the
user activities.
Conclusion
From the above paper, it can be concluded that there are different types of security
and privacy issues in the private network used in the college. The enhanced specifications of
two types of authentication processes are highlighted in this paper in such a way that it will
be helping the readers to know about the usability of those authentication processes. The
paper will also provide an in-depth knowledge about the server validation of those
authentication processes. The extensive development in the field of Information technology
has given rise to different cyber security issues such as ransomeware. The paper highlights an
anti-spam guideline which will be helpful in containing those cyber security issues. The
guideline includes the definition of the spam and the different types of spam emails. The
paper also focuses on the different risk mitigation strategies against the spam threats.
Instructions are given to the IT administrators of the college authorities to minimize the spam
threats as well as the other types of cyber security threats such as ransomeware.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CYBER SECURITY
Reference
Calhoun, C.D., 2017. Incorporating Blended Format Cybersecurity Education into a
Community College Information Technology Program. Community College Journal of
Research and Practice, 41(6), pp.344-347.
Tang, C., Tucker, C., Hawthorne, E.K., Servin, C. and Moore, T., 2017, March. Curricular
Guidance for Associate-Degree Transfer Programs in Computer Science with Contemporary
Cybersecurity Concepts. In Proceedings of the 2017 ACM SIGCSE Technical Symposium on
Computer Science Education (pp. 717-717). ACM.
Turcotte, M., Moore, J., Heard, N. and McPhall, A., 2016, September. Poisson factorization
for peer-based anomaly detection. In Intelligence and Security Informatics (ISI), 2016 IEEE
Conference on (pp. 208-210). IEEE.
Simon, N. and Banford, M., 2017, March. Cyber Crime Investigators: Pathways from High
School to Cybersecurity Careers for First Generation College-Bound Students. In
Proceedings of the 2017 ACM SIGCSE Technical Symposium on Computer Science
Education (pp. 717-717). ACM.
Settle, A., Doyle, J. and Steinbach, T., 2017. Participating in a Computer Science Linked-
courses Learning Community Reduces Isolation. arXiv preprint arXiv:1704.07898.
CYBER SECURITY
Reference
Calhoun, C.D., 2017. Incorporating Blended Format Cybersecurity Education into a
Community College Information Technology Program. Community College Journal of
Research and Practice, 41(6), pp.344-347.
Tang, C., Tucker, C., Hawthorne, E.K., Servin, C. and Moore, T., 2017, March. Curricular
Guidance for Associate-Degree Transfer Programs in Computer Science with Contemporary
Cybersecurity Concepts. In Proceedings of the 2017 ACM SIGCSE Technical Symposium on
Computer Science Education (pp. 717-717). ACM.
Turcotte, M., Moore, J., Heard, N. and McPhall, A., 2016, September. Poisson factorization
for peer-based anomaly detection. In Intelligence and Security Informatics (ISI), 2016 IEEE
Conference on (pp. 208-210). IEEE.
Simon, N. and Banford, M., 2017, March. Cyber Crime Investigators: Pathways from High
School to Cybersecurity Careers for First Generation College-Bound Students. In
Proceedings of the 2017 ACM SIGCSE Technical Symposium on Computer Science
Education (pp. 717-717). ACM.
Settle, A., Doyle, J. and Steinbach, T., 2017. Participating in a Computer Science Linked-
courses Learning Community Reduces Isolation. arXiv preprint arXiv:1704.07898.

8
CYBER SECURITY
Raj, R.K., Ekstrom, J.J., Impagliazzo, J., Lingafelt, S., Parrish, A., Reif, H. and Sobiesk, E.,
2017, October. Perspectives on the future of cybersecurity education. In Frontiers in
Education Conference (FIE) (pp. 1-2). IEEE.
Muhirwe, J. and White, N., 2016. CYBERSECURITY AWARENESS AND PRACTICE OF
NEXT GENERATION CORPORATE TECHNOLOGY USERS. Issues in Information
Systems, 17(2).
Tang, C., 2017. COMMUNITY COLLEGE CORNER ACM guidelines for associate-degree
computer science transfer programs. ACM Inroads, 8(3), pp.20-22.
Baylis, T., Williams, A., Piotrowski, V., Peterson, R. and Siraj, A., 2017. Strategies to
Develop a Diverse and Inclusive Cybersecurity Pipeline Panel.
Pusey, P., Gondree, M. and Peterson, Z., 2016. The outcomes of cybersecurity competitions
and implications for underrepresented populations. IEEE Security & Privacy, 14(6), pp.90-
95.
Yan, Z., Robertson, T., Yan, R., Park, S.Y., Bordoff, S., Chen, Q. and Sprissler, E., 2018.
Finding the weakest links in the weakest link: How well do undergraduate students make
cybersecurity judgment?. Computers in Human Behavior, 84, pp.375-382.
CYBER SECURITY
Raj, R.K., Ekstrom, J.J., Impagliazzo, J., Lingafelt, S., Parrish, A., Reif, H. and Sobiesk, E.,
2017, October. Perspectives on the future of cybersecurity education. In Frontiers in
Education Conference (FIE) (pp. 1-2). IEEE.
Muhirwe, J. and White, N., 2016. CYBERSECURITY AWARENESS AND PRACTICE OF
NEXT GENERATION CORPORATE TECHNOLOGY USERS. Issues in Information
Systems, 17(2).
Tang, C., 2017. COMMUNITY COLLEGE CORNER ACM guidelines for associate-degree
computer science transfer programs. ACM Inroads, 8(3), pp.20-22.
Baylis, T., Williams, A., Piotrowski, V., Peterson, R. and Siraj, A., 2017. Strategies to
Develop a Diverse and Inclusive Cybersecurity Pipeline Panel.
Pusey, P., Gondree, M. and Peterson, Z., 2016. The outcomes of cybersecurity competitions
and implications for underrepresented populations. IEEE Security & Privacy, 14(6), pp.90-
95.
Yan, Z., Robertson, T., Yan, R., Park, S.Y., Bordoff, S., Chen, Q. and Sprissler, E., 2018.
Finding the weakest links in the weakest link: How well do undergraduate students make
cybersecurity judgment?. Computers in Human Behavior, 84, pp.375-382.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CYBER SECURITY
Liu, X. and Murphy, D., 2016, September. Engaging females in cybersecurity: K through
Gray. In Intelligence and Security Informatics (ISI), 2016 IEEE Conference on (pp. 255-260).
IEEE.
CYBER SECURITY
Liu, X. and Murphy, D., 2016, September. Engaging females in cybersecurity: K through
Gray. In Intelligence and Security Informatics (ISI), 2016 IEEE Conference on (pp. 255-260).
IEEE.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





