CMP71001 Cybersecurity Report: Southern Cross University Analysis
VerifiedAdded on 2022/10/19
|12
|2542
|257
Report
AI Summary
This cybersecurity report, prepared for Southern Cross University as a consultant, addresses contemporary and emerging cyber threats. The report begins with an assessment of risks associated with the Bring Your Own Device (BYOD) policy, examining potential data breaches and security vulnerabilities. It then compares password-based authentication with certificate-based authentication, advocating for the latter's enhanced security features. Furthermore, the report provides detailed anti-phishing guidelines for both users and IT administrators, outlining the characteristics of phishing attacks, providing representative examples, and offering instructions to mitigate these threats. The report concludes by emphasizing the importance of the certificate-based authentication system and the need to remain vigilant against phishing scams to safeguard the university's information system. The report uses references from various sources like journals and patents to support the content and has been prepared to meet the requirements of the CMP71001 unit at Southern Cross University.

Running head: CYBER SECURITY
CYBER SECURITY
Name of the Student:
Name of the University:
Author Note:
CYBER SECURITY
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY
Table of Contents
Introduction................................................................................................................................3
BOYD Risk Assessment............................................................................................................3
BYOD Risk assessment Introduction.....................................................................................3
Objective/Purpose of BYOD Risk assessment......................................................................4
Scope of the Risk Assessment................................................................................................4
Risk Register..........................................................................................................................4
Risk Assessment Matrix.........................................................................................................6
Certificate-Based Authentication...............................................................................................6
Introduction............................................................................................................................6
Working principle of Password-based authentication scheme...............................................7
Certificate-based authentication scheme................................................................................7
Working principle of Certificate-based authentication scheme.............................................7
Comparison of the username-password and certificate–based Authentication......................8
Anti-phishing Guideline.............................................................................................................8
Definition and characteristics of Phishing.............................................................................8
Representative Examples of Phishing....................................................................................9
Instructions for Phishing Handling (users)............................................................................9
Instructions for Phishing Handling (IT admin)......................................................................9
Conclusion................................................................................................................................10
References................................................................................................................................11
Table of Contents
Introduction................................................................................................................................3
BOYD Risk Assessment............................................................................................................3
BYOD Risk assessment Introduction.....................................................................................3
Objective/Purpose of BYOD Risk assessment......................................................................4
Scope of the Risk Assessment................................................................................................4
Risk Register..........................................................................................................................4
Risk Assessment Matrix.........................................................................................................6
Certificate-Based Authentication...............................................................................................6
Introduction............................................................................................................................6
Working principle of Password-based authentication scheme...............................................7
Certificate-based authentication scheme................................................................................7
Working principle of Certificate-based authentication scheme.............................................7
Comparison of the username-password and certificate–based Authentication......................8
Anti-phishing Guideline.............................................................................................................8
Definition and characteristics of Phishing.............................................................................8
Representative Examples of Phishing....................................................................................9
Instructions for Phishing Handling (users)............................................................................9
Instructions for Phishing Handling (IT admin)......................................................................9
Conclusion................................................................................................................................10
References................................................................................................................................11

2CYBER SECURITY
Introduction
As appointed by the Southern Cross University to be the consultant for the cyber
security, the report specifically aims at the working of the consultant towards the security
program in relation to the emerging risks that have been posed by the cyber security threats to
the organization. This report particularly makes a brief analysis of the transition from the
password based authentication system to that of Bring Your Own Device (BYOD) that has
led to the rise of some serious concerns. Assessment of the risk that has been posed by the
BYOD policy has been done down this discussion (Song and Kong, 2017). Following that,
the transition from the password authentication system to that of the certificate authentication
system has been discussed in brief. Reasons have been stated in favor of the usage of the new
certificate based authentication. In addition to this, Phishing has been identified as the most
posing threat to the data of the organization; hence, a proper guideline of how to mitigate the
threat along with the consequences that are caused by the threat has been discussed in a brief
manner as well (McGeehan et al., 2017).
BOYD Risk Assessment
BYOD Risk assessment Introduction
Bring Your Own Device (BYOD) particularly allows every employees to makes
utilization of their own smartphones as well as the carrying out of the business related
activities through their mobile phones, and in turn make profit of the respective organization
that they have been working in. BYOD carries the primary aim to improve the productivity as
well as the speed related to the work so that the employees can carry out their activities from
anywhere, at any given point of time. However, BYOD puts forward the big security related
risks such as the leak of information such as the likes of confidential data belonging to the
company as well as the personal information of the customers to the organization (Lee et al.,
Introduction
As appointed by the Southern Cross University to be the consultant for the cyber
security, the report specifically aims at the working of the consultant towards the security
program in relation to the emerging risks that have been posed by the cyber security threats to
the organization. This report particularly makes a brief analysis of the transition from the
password based authentication system to that of Bring Your Own Device (BYOD) that has
led to the rise of some serious concerns. Assessment of the risk that has been posed by the
BYOD policy has been done down this discussion (Song and Kong, 2017). Following that,
the transition from the password authentication system to that of the certificate authentication
system has been discussed in brief. Reasons have been stated in favor of the usage of the new
certificate based authentication. In addition to this, Phishing has been identified as the most
posing threat to the data of the organization; hence, a proper guideline of how to mitigate the
threat along with the consequences that are caused by the threat has been discussed in a brief
manner as well (McGeehan et al., 2017).
BOYD Risk Assessment
BYOD Risk assessment Introduction
Bring Your Own Device (BYOD) particularly allows every employees to makes
utilization of their own smartphones as well as the carrying out of the business related
activities through their mobile phones, and in turn make profit of the respective organization
that they have been working in. BYOD carries the primary aim to improve the productivity as
well as the speed related to the work so that the employees can carry out their activities from
anywhere, at any given point of time. However, BYOD puts forward the big security related
risks such as the leak of information such as the likes of confidential data belonging to the
company as well as the personal information of the customers to the organization (Lee et al.,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3CYBER SECURITY
2017). For example, whenever an employee is working on the phone, it consists of a huge
amount of company as well as private data. Hence, the phone getting lost may lead to the
leakage of the data that is contained within the phone.
Objective/Purpose of BYOD Risk assessment
Primary motive for the assessment of the risks belonging to the concerns that have
been upcoming in relation to the BYOD has been necessarily approached to assess the risks
as well as put forward the basic measures aimed towards the mitigation of the same.
Scope of the Risk Assessment
Utilizing such measures related to the analysis of the risk, the mitigation techniques
shall be implemented upon the number of concerns that have been visible under the
installation of the BYOD method for the carrying out of the business procedures.
Primarily, the leakage of data that can occur whenever the mobile phone of the
employee gets stolen shall be mitigated having the most primary importance in relation to the
mitigation of the issues related to the BYOD (Hong et al., 2016). In addition to this, some
other existing security concerns have been mitigated along with the primary concerns.
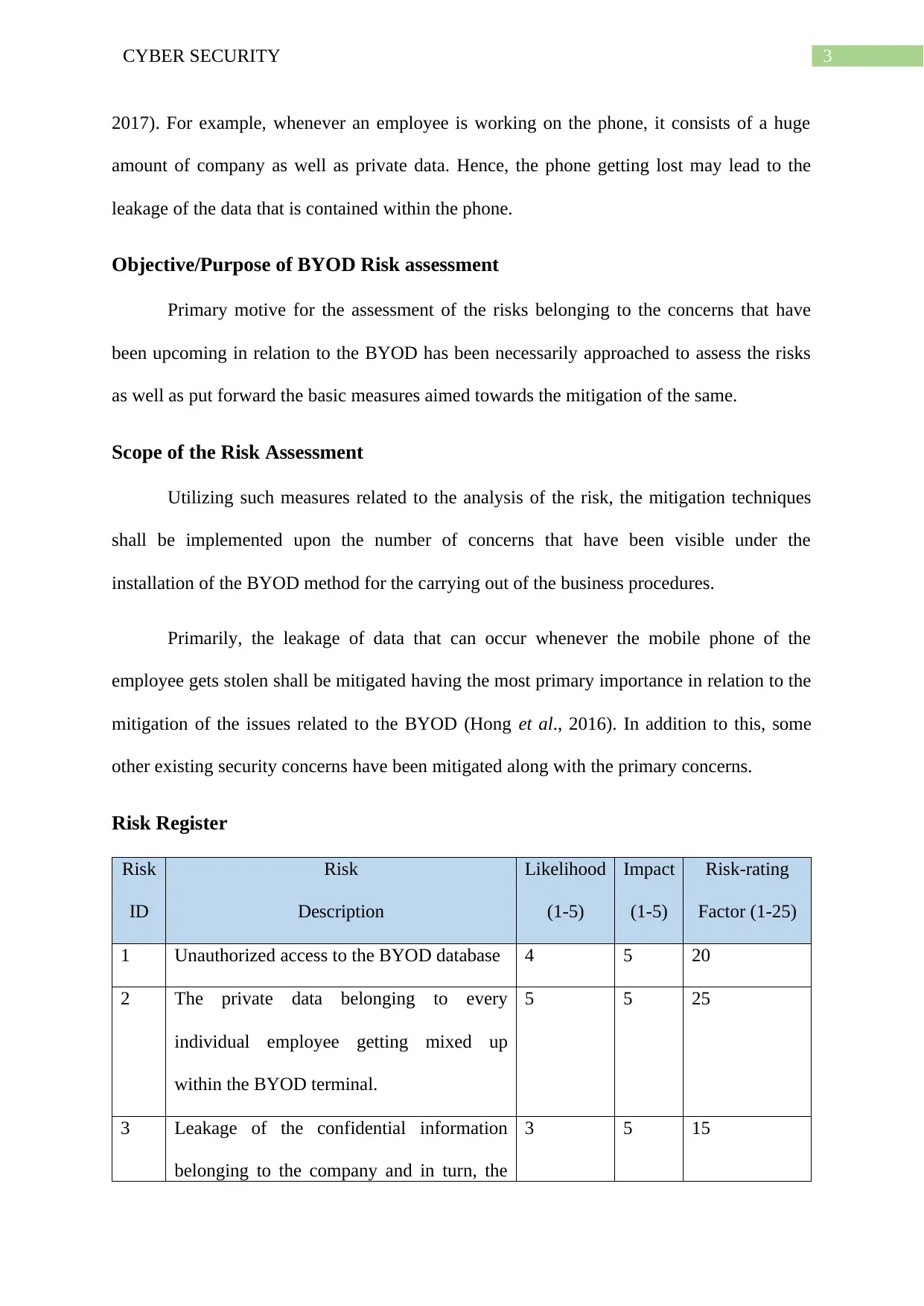
Risk Register
Risk
ID
Risk
Description
Likelihood
(1-5)
Impact
(1-5)
Risk-rating
Factor (1-25)
1 Unauthorized access to the BYOD database 4 5 20
2 The private data belonging to every
individual employee getting mixed up
within the BYOD terminal.
5 5 25
3 Leakage of the confidential information
belonging to the company and in turn, the
3 5 15
2017). For example, whenever an employee is working on the phone, it consists of a huge
amount of company as well as private data. Hence, the phone getting lost may lead to the
leakage of the data that is contained within the phone.
Objective/Purpose of BYOD Risk assessment
Primary motive for the assessment of the risks belonging to the concerns that have
been upcoming in relation to the BYOD has been necessarily approached to assess the risks
as well as put forward the basic measures aimed towards the mitigation of the same.
Scope of the Risk Assessment
Utilizing such measures related to the analysis of the risk, the mitigation techniques
shall be implemented upon the number of concerns that have been visible under the
installation of the BYOD method for the carrying out of the business procedures.
Primarily, the leakage of data that can occur whenever the mobile phone of the
employee gets stolen shall be mitigated having the most primary importance in relation to the
mitigation of the issues related to the BYOD (Hong et al., 2016). In addition to this, some
other existing security concerns have been mitigated along with the primary concerns.
Risk Register
Risk
ID
Risk
Description
Likelihood
(1-5)
Impact
(1-5)
Risk-rating
Factor (1-25)
1 Unauthorized access to the BYOD database 4 5 20
2 The private data belonging to every
individual employee getting mixed up
within the BYOD terminal.
5 5 25
3 Leakage of the confidential information
belonging to the company and in turn, the
3 5 15
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CYBER SECURITY
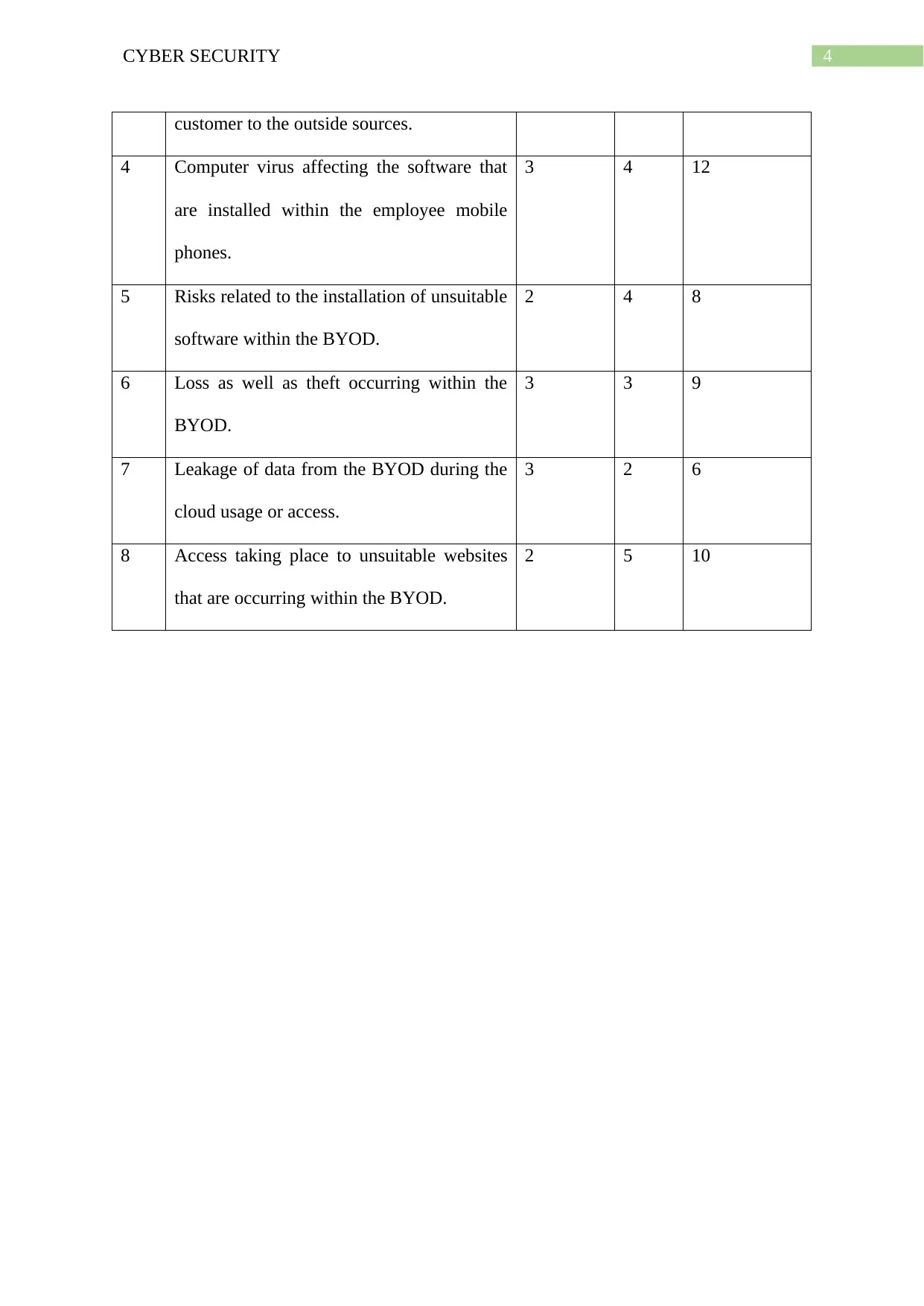
customer to the outside sources.
4 Computer virus affecting the software that
are installed within the employee mobile
phones.
3 4 12
5 Risks related to the installation of unsuitable
software within the BYOD.
2 4 8
6 Loss as well as theft occurring within the
BYOD.
3 3 9
7 Leakage of data from the BYOD during the
cloud usage or access.
3 2 6
8 Access taking place to unsuitable websites
that are occurring within the BYOD.
2 5 10
customer to the outside sources.
4 Computer virus affecting the software that
are installed within the employee mobile
phones.
3 4 12
5 Risks related to the installation of unsuitable
software within the BYOD.
2 4 8
6 Loss as well as theft occurring within the
BYOD.
3 3 9
7 Leakage of data from the BYOD during the
cloud usage or access.
3 2 6
8 Access taking place to unsuitable websites
that are occurring within the BYOD.
2 5 10
5CYBER SECURITY
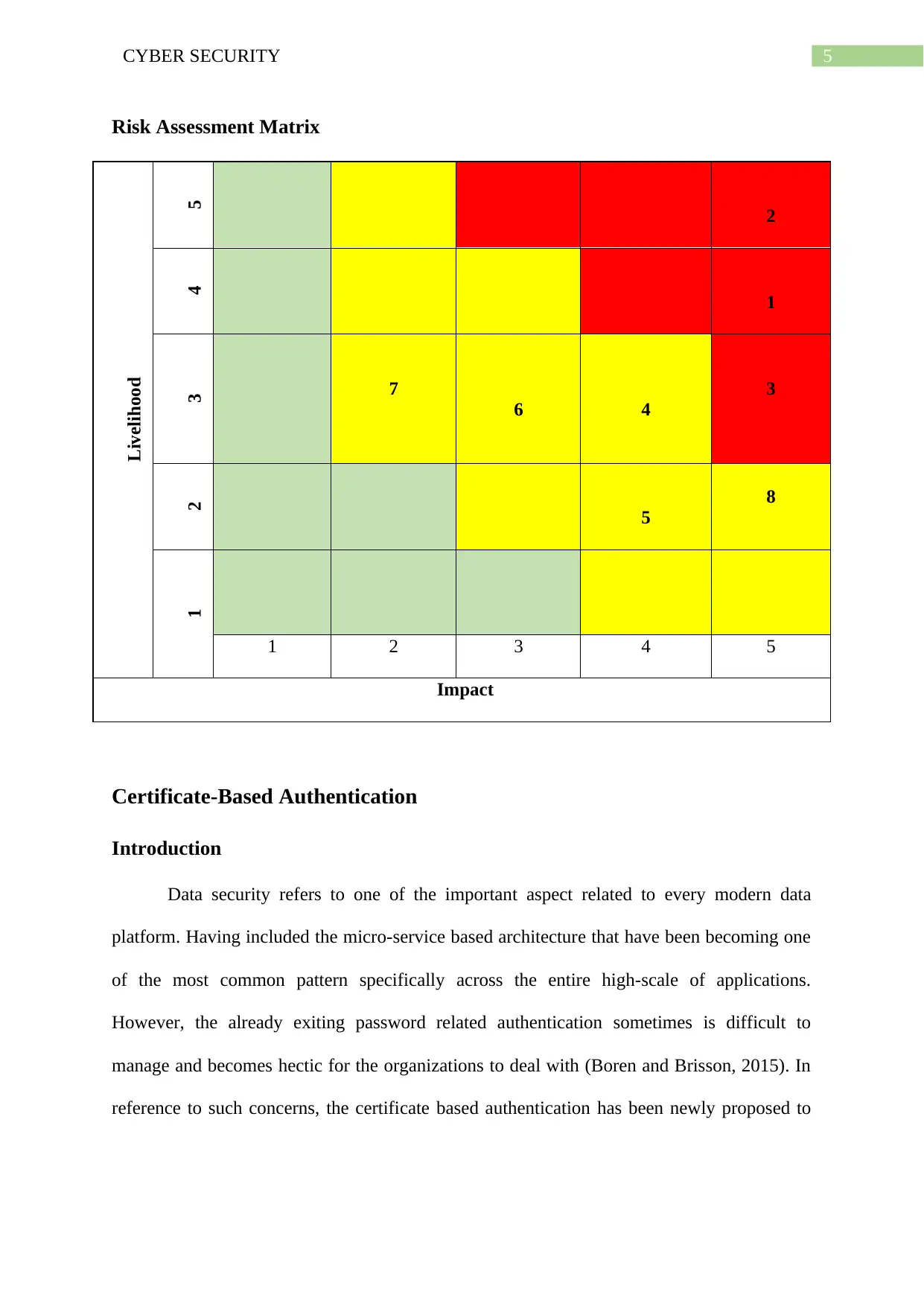
Risk Assessment Matrix
Livelihood
5
2
4
1
3 7
6 4
3
2
5
8
1
1 2 3 4 5
Impact
Certificate-Based Authentication
Introduction
Data security refers to one of the important aspect related to every modern data
platform. Having included the micro-service based architecture that have been becoming one
of the most common pattern specifically across the entire high-scale of applications.
However, the already exiting password related authentication sometimes is difficult to
manage and becomes hectic for the organizations to deal with (Boren and Brisson, 2015). In
reference to such concerns, the certificate based authentication has been newly proposed to
Risk Assessment Matrix
Livelihood
5
2
4
1
3 7
6 4
3
2
5
8
1
1 2 3 4 5
Impact
Certificate-Based Authentication
Introduction
Data security refers to one of the important aspect related to every modern data
platform. Having included the micro-service based architecture that have been becoming one
of the most common pattern specifically across the entire high-scale of applications.
However, the already exiting password related authentication sometimes is difficult to
manage and becomes hectic for the organizations to deal with (Boren and Brisson, 2015). In
reference to such concerns, the certificate based authentication has been newly proposed to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER SECURITY
the organization in order to have a better understanding as well as management of the
security concerns that have been upcoming recently.
Working principle of Password-based authentication scheme
Simply the validation of password had offered an easy method of authenticating every
individual users in relation to the entry or exit to any kind of application or system to be
specific. In such password authentication systems, firstly the user is asked for the input of the
correct password that is already registered into the database whenever the specific user tries
to gain entry into the system. The password is entered by the user, which is then sent to the
server from the client (Farash, 2017). In the server, the password is tallied with the password
that is already present within the database and checks if the entered password is correct, and
then grants the access to the user which is then informed to the user by the client.
Certificate-based authentication scheme
A Certificate-based scheme of authentication refers to the specific scheme, which
makes the utilization of the publicized key related cryptography as well as the digital
certificate to provide access to the user by granting the permission (Manvi and Tangade,
2017). A digital certificate refers to an electronic form that consists of all the existing data
related to the particular identification of the user along with the inclusion of the digital key as
well as the digital signature of the concerned individual.
Working principle of Certificate-based authentication scheme
Whenever such concerned users makes a sign into the specific server, the individual is
required to present the digital certificate of the concerned individual that consists of the
public key related to the individual along with the signature belonging to the authorized
certification. The server on the other end puts forward the confirmation of all the digitalized
signature as well as to check if the specific certificate has been issues by the trusted
the organization in order to have a better understanding as well as management of the
security concerns that have been upcoming recently.
Working principle of Password-based authentication scheme
Simply the validation of password had offered an easy method of authenticating every
individual users in relation to the entry or exit to any kind of application or system to be
specific. In such password authentication systems, firstly the user is asked for the input of the
correct password that is already registered into the database whenever the specific user tries
to gain entry into the system. The password is entered by the user, which is then sent to the
server from the client (Farash, 2017). In the server, the password is tallied with the password
that is already present within the database and checks if the entered password is correct, and
then grants the access to the user which is then informed to the user by the client.
Certificate-based authentication scheme
A Certificate-based scheme of authentication refers to the specific scheme, which
makes the utilization of the publicized key related cryptography as well as the digital
certificate to provide access to the user by granting the permission (Manvi and Tangade,
2017). A digital certificate refers to an electronic form that consists of all the existing data
related to the particular identification of the user along with the inclusion of the digital key as
well as the digital signature of the concerned individual.
Working principle of Certificate-based authentication scheme
Whenever such concerned users makes a sign into the specific server, the individual is
required to present the digital certificate of the concerned individual that consists of the
public key related to the individual along with the signature belonging to the authorized
certification. The server on the other end puts forward the confirmation of all the digitalized
signature as well as to check if the specific certificate has been issues by the trusted
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY
authorities (Medvinsky et al., 2015). The server after this authenticates the user with the help
of the publicized key related cryptography towards confirming that the user is in well
possession of the correct credentials to log in to the server.
Comparison of the username-password and certificate–based Authentication
Within the existing password related system that has been previously existent within
the Southern Cross University takes into consideration only of a single line password
belonging to the user. Hence, if somehow the password gets leaked, there is no way possible
to stop the person from barging into the account and taking away all the sensitive
information.
However, on the other hand the certificate-based authentication server takes into
consideration a number of materials such as the digital certificate, which has the inclusion of
a number of key inclusions such as the likes of the digital key as well as the digital signature
that completely belongs to the customer itself (Jiang et al., 2015). Hence, such an
implementation within the system for the Southern Cross University is considered to be much
more beneficial.
Anti-phishing Guideline
Definition and characteristics of Phishing
Phishing particularly puts forward the unethical practice relating to the methods of
sending emails making use of the identity of renowned and respectable organizations having
the common aim of attracting the victims and taking away all the sensitive information
related to the individual concerned (Akerlof and Shiller, 2015).
Some of the characteristics of phishing are,
i) Such emails make certain unrealistic threats or demands to the users.
authorities (Medvinsky et al., 2015). The server after this authenticates the user with the help
of the publicized key related cryptography towards confirming that the user is in well
possession of the correct credentials to log in to the server.
Comparison of the username-password and certificate–based Authentication
Within the existing password related system that has been previously existent within
the Southern Cross University takes into consideration only of a single line password
belonging to the user. Hence, if somehow the password gets leaked, there is no way possible
to stop the person from barging into the account and taking away all the sensitive
information.
However, on the other hand the certificate-based authentication server takes into
consideration a number of materials such as the digital certificate, which has the inclusion of
a number of key inclusions such as the likes of the digital key as well as the digital signature
that completely belongs to the customer itself (Jiang et al., 2015). Hence, such an
implementation within the system for the Southern Cross University is considered to be much
more beneficial.
Anti-phishing Guideline
Definition and characteristics of Phishing
Phishing particularly puts forward the unethical practice relating to the methods of
sending emails making use of the identity of renowned and respectable organizations having
the common aim of attracting the victims and taking away all the sensitive information
related to the individual concerned (Akerlof and Shiller, 2015).
Some of the characteristics of phishing are,
i) Such emails make certain unrealistic threats or demands to the users.

8CYBER SECURITY
ii) Such emails consists of a lot of grammatical errors.
iii) A suspicious URL is another characteristic belonging to such phishing emails.
iv) Sensitive information is asked for.
Representative Examples of Phishing
For example, the emails related to phishing are usually sent to the victims in large
batches. To make it a lot less time consuming, the hackers make use of generic names so that
they do not have to type the entire name of the victims (Arachchilage, Love and Beznosov,
2016).
Another example of phishing refer to the sending of specific links to another webpage
where the victim is then required to input all the sensitive information belonging to the
individual itself.
In the third example, the criminals present up on the internet makes the users
confused at times by compelling the user to input all the personal information in a rapid way
by portraying the issue to be in need of urgent attention (Moghimi and Varjani, 2016).
Instructions for Phishing Handling (users)
Instructions that shall be followed by the users while working online to avoid
phishing have been discussed below (Higbee, Belani and Greaux, 2016). These are,
i) Being cautious to all of the communications that are being received online.
ii) The users shall not click on each and every link that is coming in with emails as
well as present on the webpages.
iii) The users shall not enter anything even close to the personal information.
iv) Installation of a filter related to phishing.
ii) Such emails consists of a lot of grammatical errors.
iii) A suspicious URL is another characteristic belonging to such phishing emails.
iv) Sensitive information is asked for.
Representative Examples of Phishing
For example, the emails related to phishing are usually sent to the victims in large
batches. To make it a lot less time consuming, the hackers make use of generic names so that
they do not have to type the entire name of the victims (Arachchilage, Love and Beznosov,
2016).
Another example of phishing refer to the sending of specific links to another webpage
where the victim is then required to input all the sensitive information belonging to the
individual itself.
In the third example, the criminals present up on the internet makes the users
confused at times by compelling the user to input all the personal information in a rapid way
by portraying the issue to be in need of urgent attention (Moghimi and Varjani, 2016).
Instructions for Phishing Handling (users)
Instructions that shall be followed by the users while working online to avoid
phishing have been discussed below (Higbee, Belani and Greaux, 2016). These are,
i) Being cautious to all of the communications that are being received online.
ii) The users shall not click on each and every link that is coming in with emails as
well as present on the webpages.
iii) The users shall not enter anything even close to the personal information.
iv) Installation of a filter related to phishing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY
Instructions for Phishing Handling (IT admin)
The instructions that shall be followed by the IT administrators to avoid frauds related
to phishing have been listed below (Gupta, Tanbeer and Mohandas, 2017). These are,
i) Proper checking of all the details related to the sender of the specific email.
ii) Having proper means of password protecting the system so as to stop the hackers
from sending such emails into the user account.
iii) Installing of specific software within the user systems to detect phishing emails as
well as links.
Conclusion
To conclude the above discussion it can be stated that the security reasons that have
been facing by the Southern Cross University took the right decision to replace the prevalent
password related system authentication to that of the certificate based system authentication.
The report specifically puts forward the BOYD risk assessment, that is added by the detail
description of the password protected authentication system having the inclusion of the
certificate based authentication. Lastly, the report identifies phishing scams to be the primary
threat imposer to the information system of the Southern Cross University, and hence the
ways to tackle as well as be aware of it has been mentioned in detail all together.
Instructions for Phishing Handling (IT admin)
The instructions that shall be followed by the IT administrators to avoid frauds related
to phishing have been listed below (Gupta, Tanbeer and Mohandas, 2017). These are,
i) Proper checking of all the details related to the sender of the specific email.
ii) Having proper means of password protecting the system so as to stop the hackers
from sending such emails into the user account.
iii) Installing of specific software within the user systems to detect phishing emails as
well as links.
Conclusion
To conclude the above discussion it can be stated that the security reasons that have
been facing by the Southern Cross University took the right decision to replace the prevalent
password related system authentication to that of the certificate based system authentication.
The report specifically puts forward the BOYD risk assessment, that is added by the detail
description of the password protected authentication system having the inclusion of the
certificate based authentication. Lastly, the report identifies phishing scams to be the primary
threat imposer to the information system of the Southern Cross University, and hence the
ways to tackle as well as be aware of it has been mentioned in detail all together.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY
References
Akerlof, G.A. and Shiller, R.J., 2015. Phishing for phools: The economics of manipulation
and deception. Princeton University Press.
Arachchilage, N.A.G., Love, S. and Beznosov, K., 2016. Phishing threat avoidance
behaviour: An empirical investigation. Computers in Human Behavior, 60, pp.185-197.
Boren, S.L. and Brisson, A.J., 2015. Dynamic distributed key system and method for identity
management, authentication servers, data security and preventing man-in-the-middle attacks.
U.S. Patent 9,166,782.
Farash, M.S., 2017. An improved password‐based authentication scheme for session
initiation protocol using smart cards without verification table. International Journal of
Communication Systems, 30(1), p.e2879.
Gupta, D.S., Tanbeer, S.K. and Mohandas, R., ADI LABS INCORPORATED, 2017. System
and method for detecting phishing webpages. U.S. Patent 9,621,566.
Higbee, A., Belani, R. and Greaux, S., PhishMe Inc, 2016. Collaborative phishing attack
detection. U.S. Patent 9,356,948.
Hong, S., Baykov, R., Xu, L., Nadimpalli, S. and Gu, G., 2016, February. Towards SDN-
Defined Programmable BYOD (Bring Your Own Device) Security. In NDSS.
Jiang, Q., Ma, J., Li, G. and Li, X., 2015. Improvement of robust smart‐card‐based password
authentication scheme. International Journal of Communication Systems, 28(2), pp.383-393.
Lee Jr, J., Warkentin, M., Crossler, R.E. and Otondo, R.F., 2017. Implications of monitoring
mechanisms on bring your own device adoption. Journal of Computer Information
Systems, 57(4), pp.309-318.
References
Akerlof, G.A. and Shiller, R.J., 2015. Phishing for phools: The economics of manipulation
and deception. Princeton University Press.
Arachchilage, N.A.G., Love, S. and Beznosov, K., 2016. Phishing threat avoidance
behaviour: An empirical investigation. Computers in Human Behavior, 60, pp.185-197.
Boren, S.L. and Brisson, A.J., 2015. Dynamic distributed key system and method for identity
management, authentication servers, data security and preventing man-in-the-middle attacks.
U.S. Patent 9,166,782.
Farash, M.S., 2017. An improved password‐based authentication scheme for session
initiation protocol using smart cards without verification table. International Journal of
Communication Systems, 30(1), p.e2879.
Gupta, D.S., Tanbeer, S.K. and Mohandas, R., ADI LABS INCORPORATED, 2017. System
and method for detecting phishing webpages. U.S. Patent 9,621,566.
Higbee, A., Belani, R. and Greaux, S., PhishMe Inc, 2016. Collaborative phishing attack
detection. U.S. Patent 9,356,948.
Hong, S., Baykov, R., Xu, L., Nadimpalli, S. and Gu, G., 2016, February. Towards SDN-
Defined Programmable BYOD (Bring Your Own Device) Security. In NDSS.
Jiang, Q., Ma, J., Li, G. and Li, X., 2015. Improvement of robust smart‐card‐based password
authentication scheme. International Journal of Communication Systems, 28(2), pp.383-393.
Lee Jr, J., Warkentin, M., Crossler, R.E. and Otondo, R.F., 2017. Implications of monitoring
mechanisms on bring your own device adoption. Journal of Computer Information
Systems, 57(4), pp.309-318.

11CYBER SECURITY
Manvi, S.S. and Tangade, S., 2017. A survey on authentication schemes in VANETs for
secured communication. Vehicular Communications, 9, pp.19-30.
McGeehan, R., Popov, L.T., Palow, C.W., Read, R.J. and Keyani, P., Facebook Inc,
2017. Preventing phishing attacks based on reputation of user locations. U.S. Patent
9,576,119.
Medvinsky, G., Nice, N., Shiran, T., Teplitsky, A., Leach, P. and Neystadt, J., Microsoft
Technology Licensing LLC, 2015. Authentication delegation based on re-verification of
cryptographic evidence. U.S. Patent 9,055,107.
Moghimi, M. and Varjani, A.Y., 2016. New rule-based phishing detection method. Expert
systems with applications, 53, pp.231-242.
Song, Y. and Kong, S.C., 2017. Affordances and constraints of BYOD (Bring Your Own
Device) for learning and teaching in higher education: Teachers’ perspectives. The Internet
and Higher Education, 32(1), pp.39-46.
Manvi, S.S. and Tangade, S., 2017. A survey on authentication schemes in VANETs for
secured communication. Vehicular Communications, 9, pp.19-30.
McGeehan, R., Popov, L.T., Palow, C.W., Read, R.J. and Keyani, P., Facebook Inc,
2017. Preventing phishing attacks based on reputation of user locations. U.S. Patent
9,576,119.
Medvinsky, G., Nice, N., Shiran, T., Teplitsky, A., Leach, P. and Neystadt, J., Microsoft
Technology Licensing LLC, 2015. Authentication delegation based on re-verification of
cryptographic evidence. U.S. Patent 9,055,107.
Moghimi, M. and Varjani, A.Y., 2016. New rule-based phishing detection method. Expert
systems with applications, 53, pp.231-242.
Song, Y. and Kong, S.C., 2017. Affordances and constraints of BYOD (Bring Your Own
Device) for learning and teaching in higher education: Teachers’ perspectives. The Internet
and Higher Education, 32(1), pp.39-46.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




