A Comprehensive Report on Cyber Security Challenges in Business
VerifiedAdded on 2021/06/14
|13
|3118
|46
Report
AI Summary
This report delves into the multifaceted challenges of cyber security within the business landscape. It begins with an introduction outlining the increasing reliance on internet-based services and the surge in cyber attacks, emphasizing the financial and economic ramifications of data breaches. The report establishes objectives to evaluate existing cybersecurity studies, analyze their impact on profitability, and provide actionable recommendations for businesses. It scopes the research through secondary sources, focusing on data security challenges. A comprehensive literature review examines the competitive advantages and vulnerabilities associated with digital transformation, including the rise of online banking and social media. The report poses key research questions concerning the nature of cyber security challenges, the key users, and the financial implications for small and medium-sized enterprises (SMEs). The methodology section outlines both qualitative and quantitative approaches, detailing sampling techniques, data collection methods (interviews and questionnaires), and data analysis strategies. The analysis will use SPSS software, including the use of tables, graphs, and charts, to explore the challenges and effects of cyber attacks. The report concludes with a discussion on the importance of security policies, encryption, and employee awareness to mitigate risks. The report highlights the importance of implementing security measures and the impact of cyber attacks on businesses.
Challenges in Cyber Security for Business
Report
Report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................1
Objectives....................................................................................................................................1
Scope............................................................................................................................................1
Literature Review............................................................................................................................2
Research Questions..........................................................................................................................4
Methodology....................................................................................................................................5
Sampling..........................................................................................................................................6
Data Collection & Analysis.............................................................................................................7
Conclusion.......................................................................................................................................8
Reliability........................................................................................................................................8
Research Limitation.........................................................................................................................9
Time Schedule.................................................................................................................................9
References......................................................................................................................................10
Introduction......................................................................................................................................1
Objectives....................................................................................................................................1
Scope............................................................................................................................................1
Literature Review............................................................................................................................2
Research Questions..........................................................................................................................4
Methodology....................................................................................................................................5
Sampling..........................................................................................................................................6
Data Collection & Analysis.............................................................................................................7
Conclusion.......................................................................................................................................8
Reliability........................................................................................................................................8
Research Limitation.........................................................................................................................9
Time Schedule.................................................................................................................................9
References......................................................................................................................................10

Introduction
It has been seen that with time there has been a major change in the technology standards which
includes that the different companies are working on the use of internet through the use of
smartphones. Here, the organizations are trying to adapt to the strategies of digital format with
focusing on different products and the services. There are different number of the cyber attacks
which are considerably seen and are a major issue for the companies mainly because there are
different financial and the economic standards, with breaching confidential data. The data
provided focus on the growth of the risks with increased importance set with cybersecurity set
with different challenges that are related to policies of the cybercriminals. The corporations
includes the different forms with implementing the policies that are set with the data of
enterprise breach. The report highlights the recommendations with companies improving the
security standards with the cyber-attacks.
Objectives
The objective is based on the evaluation with the different studies which includes the experts
with cybersecurity. The report analyses the forms with the evaluation that affects the
profitability. The other objectives are related to providing the recommendations with the
companies that are addressing the challenges which are facing the issues related to cybersecurity.
Scope
The scope is depending upon the secondary research with working on the challenges where the
companies include data security standards. The different organizations work on understanding
the cyber attacks risks where the cybercriminals tend to use the different tools with company
data.
It has been seen that with time there has been a major change in the technology standards which
includes that the different companies are working on the use of internet through the use of
smartphones. Here, the organizations are trying to adapt to the strategies of digital format with
focusing on different products and the services. There are different number of the cyber attacks
which are considerably seen and are a major issue for the companies mainly because there are
different financial and the economic standards, with breaching confidential data. The data
provided focus on the growth of the risks with increased importance set with cybersecurity set
with different challenges that are related to policies of the cybercriminals. The corporations
includes the different forms with implementing the policies that are set with the data of
enterprise breach. The report highlights the recommendations with companies improving the
security standards with the cyber-attacks.
Objectives
The objective is based on the evaluation with the different studies which includes the experts
with cybersecurity. The report analyses the forms with the evaluation that affects the
profitability. The other objectives are related to providing the recommendations with the
companies that are addressing the challenges which are facing the issues related to cybersecurity.
Scope
The scope is depending upon the secondary research with working on the challenges where the
companies include data security standards. The different organizations work on understanding
the cyber attacks risks where the cybercriminals tend to use the different tools with company
data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Literature Review
The report highlights about how the companies with emerging market with the gained
competitive advantage over the patterns that includes the internet-based services. The expansion
is based on the use of the internet with providing the new marketing standards for the companies
like Uber, Google, and the other people. The companies are working on the larger enterprise
structure with revenue that includes the sustainability of growth that is based for the internet-
based services. The assistance is based on the communication skills with the customers with the
creation of strong relationship with latest technologies and innovation. The competitive
advantage is set over the competitors where the use of the social media sites tends to increase
between the people and the companies. Here, the use of the social media standards and the sites
need to focus on sharing the personal data with the internet focusing on the accessing the
unauthorized person to gain the unfair advantage. The technologies work on the mobile wallet,
ordering the automation process, with the NFC payment that tends to make the online banking
standards (Bari et al., 2014).
The competition is set with the others with the corporations with adoption of the latest
technologies that tends to improve the services with the expansion form. The cybersecurity
challenges which includes the security services. The competitive advantage is based on the
online based services that results in the increased concern with the security standards with the
consequences related to the cyber-attacks (Brown et al., 2015). The banking corporations works
on the attracting more of the customers with the latest technologies working on the performance
of the banking functions. The popularity is about the mobile wallets with the consideration of
becoming popular, with the quickly offering the services to the different customers (Suh et al.,
The report highlights about how the companies with emerging market with the gained
competitive advantage over the patterns that includes the internet-based services. The expansion
is based on the use of the internet with providing the new marketing standards for the companies
like Uber, Google, and the other people. The companies are working on the larger enterprise
structure with revenue that includes the sustainability of growth that is based for the internet-
based services. The assistance is based on the communication skills with the customers with the
creation of strong relationship with latest technologies and innovation. The competitive
advantage is set over the competitors where the use of the social media sites tends to increase
between the people and the companies. Here, the use of the social media standards and the sites
need to focus on sharing the personal data with the internet focusing on the accessing the
unauthorized person to gain the unfair advantage. The technologies work on the mobile wallet,
ordering the automation process, with the NFC payment that tends to make the online banking
standards (Bari et al., 2014).
The competition is set with the others with the corporations with adoption of the latest
technologies that tends to improve the services with the expansion form. The cybersecurity
challenges which includes the security services. The competitive advantage is based on the
online based services that results in the increased concern with the security standards with the
consequences related to the cyber-attacks (Brown et al., 2015). The banking corporations works
on the attracting more of the customers with the latest technologies working on the performance
of the banking functions. The popularity is about the mobile wallets with the consideration of
becoming popular, with the quickly offering the services to the different customers (Suh et al.,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2014). The security guidelines includes the easy access for the cybercriminals with the hacking
and handling the data breach for the online services standards.
The organization needs to work on the improved security with the software standards that works
on the increased chances of the breach in the data. With this, the large corporations needs to
work on improved cyber security standards with small and medium enterprise working on the
implementation of the policies of the cyber security (Bada et al., 2014). The IT specializes works
on the increased overall expenses. The avoidance of the issues is related to the software working
without any testing with the risks works on the cyber-attacks. The small enterprises needs to
make use of the online based services which includes the investments that works on improved
cyber security that was mainly due to the lower budgeting (Sicari et al., 2015).
There has been lack of the resources with the easy data breach which includes the consideration
with focus on the results with the increased challenges that relates to cyber security (Harrop et
al., 2015). The smaller and medium organizations are not aware with the risks related to the
cyber-attacks where there is a need to avoid the precautionary measures with higher costs set for
the cyber security. The people do not take security with lack of awareness that was related to the
risks of the cyber-attacks. The use of mobile wallets with people working on the security
measures with the challenges that makes it difficult for the organizations with the easy protection
of the privacy online. The number of cyber attacks works on the increased standards and the
ways with the hacking into the business data (Ab Rahman et al., 2015). The common ways of the
attack is for the DDoS attack with the focus on how the hackers working on the services which
are available with sending the larger amount from the multiple sources. The servers of the data
works on the larger enterprise with Amazon, Facebook, YouTube that is able to handle the
amount of the server traffic. The small and the medium organizations works on the limited
and handling the data breach for the online services standards.
The organization needs to work on the improved security with the software standards that works
on the increased chances of the breach in the data. With this, the large corporations needs to
work on improved cyber security standards with small and medium enterprise working on the
implementation of the policies of the cyber security (Bada et al., 2014). The IT specializes works
on the increased overall expenses. The avoidance of the issues is related to the software working
without any testing with the risks works on the cyber-attacks. The small enterprises needs to
make use of the online based services which includes the investments that works on improved
cyber security that was mainly due to the lower budgeting (Sicari et al., 2015).
There has been lack of the resources with the easy data breach which includes the consideration
with focus on the results with the increased challenges that relates to cyber security (Harrop et
al., 2015). The smaller and medium organizations are not aware with the risks related to the
cyber-attacks where there is a need to avoid the precautionary measures with higher costs set for
the cyber security. The people do not take security with lack of awareness that was related to the
risks of the cyber-attacks. The use of mobile wallets with people working on the security
measures with the challenges that makes it difficult for the organizations with the easy protection
of the privacy online. The number of cyber attacks works on the increased standards and the
ways with the hacking into the business data (Ab Rahman et al., 2015). The common ways of the
attack is for the DDoS attack with the focus on how the hackers working on the services which
are available with sending the larger amount from the multiple sources. The servers of the data
works on the larger enterprise with Amazon, Facebook, YouTube that is able to handle the
amount of the server traffic. The small and the medium organizations works on the limited

bandwidth works on the stopped with the traffic amount that the primary reason is for the cyber
criminals with sending the larger traffic for the server (Mukisa et al., 2014). The cyber criminals
works on the larger amount of traffic works on the company that results in the stoppage its
operations.
Justifications
It is important for the company to work on different measures and security policies which can
easily be set with the implementation of the organization. The corporations need to make use of
the encryption which is set through the data protection and then handling the data transmission
which is considered to be highly vulnerable as well. The IoT devices need to work with the
encryption with sharing all the private data that is based on handling the system structure and the
patterns (Han et al., 2014). The employees need to understand about the cyber security issues and
then providing a proper way where the actions can be taken for the different problems for the
breach of data.
Research Questions
Primary Question
1. What are different challenges related to cyber security standards that the company faces
in the business?
Secondary Question
1. Who are the largest users for the cyber security standards?
2. What are different ways which are set for the financial statement with easy carrying out
of the data for the small and medium sized organizations?
criminals with sending the larger traffic for the server (Mukisa et al., 2014). The cyber criminals
works on the larger amount of traffic works on the company that results in the stoppage its
operations.
Justifications
It is important for the company to work on different measures and security policies which can
easily be set with the implementation of the organization. The corporations need to make use of
the encryption which is set through the data protection and then handling the data transmission
which is considered to be highly vulnerable as well. The IoT devices need to work with the
encryption with sharing all the private data that is based on handling the system structure and the
patterns (Han et al., 2014). The employees need to understand about the cyber security issues and
then providing a proper way where the actions can be taken for the different problems for the
breach of data.
Research Questions
Primary Question
1. What are different challenges related to cyber security standards that the company faces
in the business?
Secondary Question
1. Who are the largest users for the cyber security standards?
2. What are different ways which are set for the financial statement with easy carrying out
of the data for the small and medium sized organizations?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3. Are there are variations related to quality of cyber security challenges that tends to
generate the SMEs?
Methodology
There are different standards and variations that are set for the system planning for the
qualitative and the quantitative research. The methods are related to the applied forms include
the collection of the methods with the interviews and the questionnaires survey. The SMEs work
on the use of the different perspectives related to the confidence with data and the results. The
elements are based on qualitative and quantitative data collection where the wider range of
research questions with focusing on meeting the standards and work on the descriptive and the
explanatory methods. The necessitating works on the use of the mixed methods with research
requirements. There are different standards which include the descriptive and the explanatory
research that relates to working on the use of mixed methods.
Qualitative Research
The specifications are based on the qualitative aspects with the collection of data with
possibilities to understand the complex nature where the different standards are related to
understanding (Onyeji et al., 2014). The cyber security challenges tend to involve the human
behaviors with the mixed research with understanding the relation with the focus on detailed
questionnaire. It includes the open ended and the closed ended questions with concurrent
triangulation research approach. Here, one tends to make use of the collection of data with
qualitative and quantitative with analysis set with the interpretation.
Quantitative Research
generate the SMEs?
Methodology
There are different standards and variations that are set for the system planning for the
qualitative and the quantitative research. The methods are related to the applied forms include
the collection of the methods with the interviews and the questionnaires survey. The SMEs work
on the use of the different perspectives related to the confidence with data and the results. The
elements are based on qualitative and quantitative data collection where the wider range of
research questions with focusing on meeting the standards and work on the descriptive and the
explanatory methods. The necessitating works on the use of the mixed methods with research
requirements. There are different standards which include the descriptive and the explanatory
research that relates to working on the use of mixed methods.
Qualitative Research
The specifications are based on the qualitative aspects with the collection of data with
possibilities to understand the complex nature where the different standards are related to
understanding (Onyeji et al., 2014). The cyber security challenges tend to involve the human
behaviors with the mixed research with understanding the relation with the focus on detailed
questionnaire. It includes the open ended and the closed ended questions with concurrent
triangulation research approach. Here, one tends to make use of the collection of data with
qualitative and quantitative with analysis set with the interpretation.
Quantitative Research
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The methodology is set with the well-structured interviews with the conduction related to the
respondents working on face-to-face forms. One needs to ensure of the interviews with different
questions, with the comparisons related to the different SMEs that works on the aggregation with
obtained answers(Goel et al., 2015).
Sampling
The cases are related to different years of 18 people and more which includes the study related to
the forms that tends to ensure about the different perceptions related to the cyber attacks with the
forms that tends to cover through different ages. The SMEs works on the interview with getting
the reactions and views related to cyber attacks that includes the decision-making process. The
identification is related to the population with research working on drawing the samples from the
population with the sampling representations working on the population that includes the study
works on the findings with interpretation for the study population (Xu et al.,2015). The research
is about the sampling size with the SMEs. Here, the study also highlights about the different
variables which re including the research for the proper classification of the sampling techniques.
They need to be analyzed and then worked upon so that one can answer the questions. Here, the
dependent variables are based on the age factors, gender and the respondent capability to answer
the questions. The independent business areas include the nature about the standards set for the
financial accounting with improved level of effectiveness that works for the financial statements.
It then matches with the different business nature patterns and to focus on the tax filing returns as
well.
The study is based on the simplification of the techniques with the interview respondents with
answering the different research questions. The variables are defined for working on the
respondents working on face-to-face forms. One needs to ensure of the interviews with different
questions, with the comparisons related to the different SMEs that works on the aggregation with
obtained answers(Goel et al., 2015).
Sampling
The cases are related to different years of 18 people and more which includes the study related to
the forms that tends to ensure about the different perceptions related to the cyber attacks with the
forms that tends to cover through different ages. The SMEs works on the interview with getting
the reactions and views related to cyber attacks that includes the decision-making process. The
identification is related to the population with research working on drawing the samples from the
population with the sampling representations working on the population that includes the study
works on the findings with interpretation for the study population (Xu et al.,2015). The research
is about the sampling size with the SMEs. Here, the study also highlights about the different
variables which re including the research for the proper classification of the sampling techniques.
They need to be analyzed and then worked upon so that one can answer the questions. Here, the
dependent variables are based on the age factors, gender and the respondent capability to answer
the questions. The independent business areas include the nature about the standards set for the
financial accounting with improved level of effectiveness that works for the financial statements.
It then matches with the different business nature patterns and to focus on the tax filing returns as
well.
The study is based on the simplification of the techniques with the interview respondents with
answering the different research questions. The variables are defined for working on the

dependent and the independent forms which includes the researcher that affect the dependent
variables as well.
Data Collection & Analysis
The analysis is based on the sampling study where the different forms are including the consent
with informing the system about the study for the information that includes the different
participants and the responses. The study is about how the participants and the responses work
on the confidentiality and then working on compiled patterns where the view is about handling
the general conclusions and recommendations (He et al., 2016). The questionnaires are about
how one is able to send the respondents a proper detail through the email addresses. There are
others who tend to work on delivering the hand for the research assistance. The participants tend
to ask for the submission of the filled questionnaires with the interview related to the Microsoft
Excel with handling the editing of the different requirements. The data also require a proper
export into the SPSS with the versions set for 17 data analysis software with 5 Likert scale and
the standardized deviations (Brown et al., 2015). The analysis is based on the summary which
includes the information related to the tables, graphs and the charts, where the multilinear
regression model needs to work on proceeding with the different financial accounting standards
and the accounting for the SMEs. The standards are based on the models which include how the
responses comes with the questionnaires which are then entered into the Microsoft Excel and
then edited with proper coding as needed. There are exploration processes where the cyber
attacks challenges and the information related to it is analyzed with the different effects that are
based on the tables, graphs and the charts.
variables as well.
Data Collection & Analysis
The analysis is based on the sampling study where the different forms are including the consent
with informing the system about the study for the information that includes the different
participants and the responses. The study is about how the participants and the responses work
on the confidentiality and then working on compiled patterns where the view is about handling
the general conclusions and recommendations (He et al., 2016). The questionnaires are about
how one is able to send the respondents a proper detail through the email addresses. There are
others who tend to work on delivering the hand for the research assistance. The participants tend
to ask for the submission of the filled questionnaires with the interview related to the Microsoft
Excel with handling the editing of the different requirements. The data also require a proper
export into the SPSS with the versions set for 17 data analysis software with 5 Likert scale and
the standardized deviations (Brown et al., 2015). The analysis is based on the summary which
includes the information related to the tables, graphs and the charts, where the multilinear
regression model needs to work on proceeding with the different financial accounting standards
and the accounting for the SMEs. The standards are based on the models which include how the
responses comes with the questionnaires which are then entered into the Microsoft Excel and
then edited with proper coding as needed. There are exploration processes where the cyber
attacks challenges and the information related to it is analyzed with the different effects that are
based on the tables, graphs and the charts.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

As per the analysis, there are different forms which includes the entering of the data into the
software which is then exported into the SPSS. Here, the analysis is done for the software which
includes how the processing is done through the descriptive statistics with the means, mode and
the different standard deviations. The results summarizes about the presentations for the tables
charts and the graphs. The regression includes the need to work on the effectiveness with reports
that are set for the SMEs pattern. Here, the models are also defined for easy processing and
working on the information which includes the different independent variable standards.
Conclusion
The use of the internet and the other online services is based on how the people and the
organization is working over the increased substantial patterns. Here, the new business
opportunities with focusing on the plans related to the competitive advantages. It works for the
forms that are related to how the products and the services are related to the increased company
vulnerabilities (Bada et al., 2014). The companies need to work on implementing the different
policies which are set in regard to the cyber security patterns and then working over the
increased issues of the attack related to Ransomware and the Insider Threat. The SMEs need to
work on the different attacks which works on management entities. Here, the focus is to work on
the different purposes which includes the system standards and the planning related to the
internal and the external resource of the reporting standards. The liabilities by the directors are
depending upon how SMEs are working over the different cyberattack issues.
Reliability
The setting is based on the primary data patterns which needs to work on the conducting of the
facts which needs to find out the different results which are reproducible (Arabo, 2015). The
software which is then exported into the SPSS. Here, the analysis is done for the software which
includes how the processing is done through the descriptive statistics with the means, mode and
the different standard deviations. The results summarizes about the presentations for the tables
charts and the graphs. The regression includes the need to work on the effectiveness with reports
that are set for the SMEs pattern. Here, the models are also defined for easy processing and
working on the information which includes the different independent variable standards.
Conclusion
The use of the internet and the other online services is based on how the people and the
organization is working over the increased substantial patterns. Here, the new business
opportunities with focusing on the plans related to the competitive advantages. It works for the
forms that are related to how the products and the services are related to the increased company
vulnerabilities (Bada et al., 2014). The companies need to work on implementing the different
policies which are set in regard to the cyber security patterns and then working over the
increased issues of the attack related to Ransomware and the Insider Threat. The SMEs need to
work on the different attacks which works on management entities. Here, the focus is to work on
the different purposes which includes the system standards and the planning related to the
internal and the external resource of the reporting standards. The liabilities by the directors are
depending upon how SMEs are working over the different cyberattack issues.
Reliability
The setting is based on the primary data patterns which needs to work on the conducting of the
facts which needs to find out the different results which are reproducible (Arabo, 2015). The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

secured forms of the secondary standards include that there is no requirement for the tests to
work on the data patterns which are published and then they are also singed for the cyber-attacks
for different SMEs. The reliability is also including the forms where one need to carry out the
different tests with the data that has been published with signing and then passing the same for
the different companies.
Research Limitation
The limitations are related to the methodology with research related to the long terms standards
and the effort (Gupta et al., 2016). The research is based on the resources which are based on
collecting the information with answering out the different questions of the research. Here, the
focus is on the collaborative measures and then working over the discrepancies of the results
(Bari et al., 2014). The respondents need to include the consideration about how the business
enterprises works with the reaching out the clients and then handling the different possibilities
which are related to the ability to read, write and then make use of the internet services.
work on the data patterns which are published and then they are also singed for the cyber-attacks
for different SMEs. The reliability is also including the forms where one need to carry out the
different tests with the data that has been published with signing and then passing the same for
the different companies.
Research Limitation
The limitations are related to the methodology with research related to the long terms standards
and the effort (Gupta et al., 2016). The research is based on the resources which are based on
collecting the information with answering out the different questions of the research. Here, the
focus is on the collaborative measures and then working over the discrepancies of the results
(Bari et al., 2014). The respondents need to include the consideration about how the business
enterprises works with the reaching out the clients and then handling the different possibilities
which are related to the ability to read, write and then make use of the internet services.
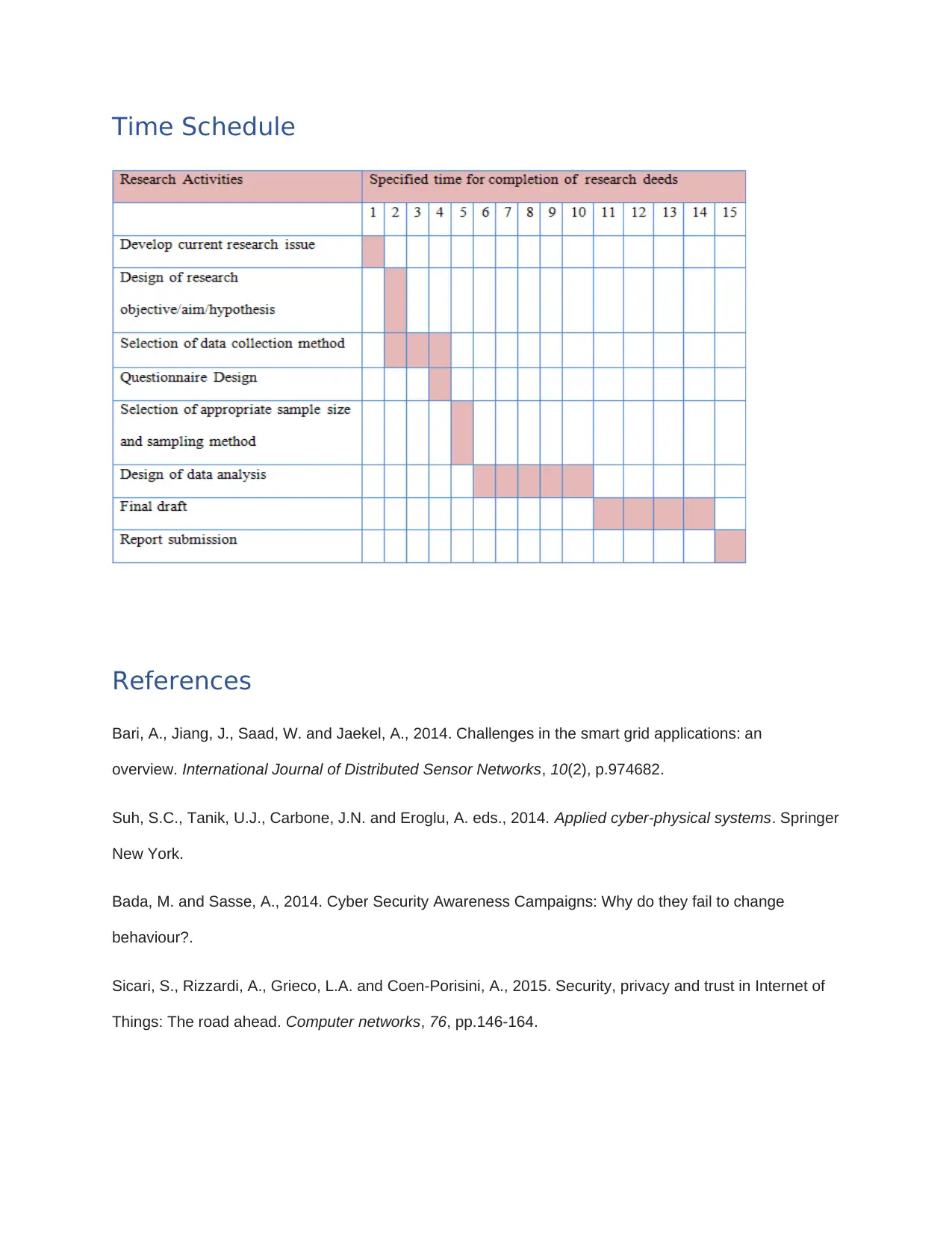
Time Schedule
References
Bari, A., Jiang, J., Saad, W. and Jaekel, A., 2014. Challenges in the smart grid applications: an
overview. International Journal of Distributed Sensor Networks, 10(2), p.974682.
Suh, S.C., Tanik, U.J., Carbone, J.N. and Eroglu, A. eds., 2014. Applied cyber-physical systems. Springer
New York.
Bada, M. and Sasse, A., 2014. Cyber Security Awareness Campaigns: Why do they fail to change
behaviour?.
Sicari, S., Rizzardi, A., Grieco, L.A. and Coen-Porisini, A., 2015. Security, privacy and trust in Internet of
Things: The road ahead. Computer networks, 76, pp.146-164.
References
Bari, A., Jiang, J., Saad, W. and Jaekel, A., 2014. Challenges in the smart grid applications: an
overview. International Journal of Distributed Sensor Networks, 10(2), p.974682.
Suh, S.C., Tanik, U.J., Carbone, J.N. and Eroglu, A. eds., 2014. Applied cyber-physical systems. Springer
New York.
Bada, M. and Sasse, A., 2014. Cyber Security Awareness Campaigns: Why do they fail to change
behaviour?.
Sicari, S., Rizzardi, A., Grieco, L.A. and Coen-Porisini, A., 2015. Security, privacy and trust in Internet of
Things: The road ahead. Computer networks, 76, pp.146-164.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




