Challenges in Cybersecurity for Businesses: A Literature Review Report
VerifiedAdded on 2020/03/04
|14
|3517
|493
Report
AI Summary
This report, a literature review on the challenges of cybersecurity for businesses, delves into various aspects of cyber threats and their impact. It begins with an introduction highlighting the daily evolution of cyber threats and the importance of protecting confidential information. The report then explores the management of cybersecurity risks, including threats, vulnerabilities, and their impacts. It identifies major actors in cybersecurity and discusses the economic consequences of cyber attacks, citing costs, statistics, and examples of affected organizations. The analysis covers the threat landscape, internal cooperation strategies, and offers a glimpse into the future of cybersecurity. The study also addresses gaps in the literature, providing a comprehensive overview of the challenges faced by businesses in the digital age. The report references various academic journals and studies to support its findings.

Running head: BUSINESS RESEARCH METHOD
Business Research Method
Name of the Student
Name of the University
Author Note
Business Research Method
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BUSINESS RESEARCH METHOD
Table of Content
Literature Review............................................................................................................................2
1.1 Introduction................................................................................................................................2
1.2 Management of Cyber Security risk..........................................................................................3
1.3 Major actors in cyber-security...................................................................................................4
1.4 Price of Cyber attack.................................................................................................................6
1.5 The threat landscape..................................................................................................................7
1.6 Internal cooperation...................................................................................................................7
1.7 A look to the future....................................................................................................................9
1.8 Gaps in the literature................................................................................................................10
References list................................................................................................................................12
Table of Content
Literature Review............................................................................................................................2
1.1 Introduction................................................................................................................................2
1.2 Management of Cyber Security risk..........................................................................................3
1.3 Major actors in cyber-security...................................................................................................4
1.4 Price of Cyber attack.................................................................................................................6
1.5 The threat landscape..................................................................................................................7
1.6 Internal cooperation...................................................................................................................7
1.7 A look to the future....................................................................................................................9
1.8 Gaps in the literature................................................................................................................10
References list................................................................................................................................12

2BUSINESS RESEARCH METHOD
Topic- Challenges in Cyber security for Business
Literature Review
1.1 Introduction
It has been identified that challenges in cyber security are developing on a daily basis.
Even though, the organizations are in the rush of developing their strategies to protect their
confidential information, the flaws always remain. The negligence to single occurrence could
lead to a significant failure. It has also been identified that Information technology sector has
evolved widely over the last half century. Over the past several years, the experts as well as the
policymakers have expressed an increasing concern regarding the ICT system from cyber attack.
Hence, the cyber attack means the international access to unauthorized data- such as damaging,
tempering file and stealing significant information.
It has also been observed that cyber security is also conflated inappropriately in public
discussion with other concepts such as privacy, information exchange and sharing, intelligence,
gathering and surveillance. In this context, Wang and Lu (2013) commented that privacy is
associated with the ability of an individual member to have control over the access by others. A
developed cyber security could help to protect the privacy in an electronic environment;
however, the information that is shared to assist in cyber security efforts could sometimes
contain personal information. This section of research provides a critical discussion regarding the
challenges of cyber security on business. A critical analysis has been conducted considering
some particular journals articles that have been conducted on cyber security challenges and its
impact on the business.
Topic- Challenges in Cyber security for Business
Literature Review
1.1 Introduction
It has been identified that challenges in cyber security are developing on a daily basis.
Even though, the organizations are in the rush of developing their strategies to protect their
confidential information, the flaws always remain. The negligence to single occurrence could
lead to a significant failure. It has also been identified that Information technology sector has
evolved widely over the last half century. Over the past several years, the experts as well as the
policymakers have expressed an increasing concern regarding the ICT system from cyber attack.
Hence, the cyber attack means the international access to unauthorized data- such as damaging,
tempering file and stealing significant information.
It has also been observed that cyber security is also conflated inappropriately in public
discussion with other concepts such as privacy, information exchange and sharing, intelligence,
gathering and surveillance. In this context, Wang and Lu (2013) commented that privacy is
associated with the ability of an individual member to have control over the access by others. A
developed cyber security could help to protect the privacy in an electronic environment;
however, the information that is shared to assist in cyber security efforts could sometimes
contain personal information. This section of research provides a critical discussion regarding the
challenges of cyber security on business. A critical analysis has been conducted considering
some particular journals articles that have been conducted on cyber security challenges and its
impact on the business.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3BUSINESS RESEARCH METHOD
1.2 Management of Cyber Security risk
The studies on cyber security claim that risk associated with any particular attack could
depend on three significant factors such as threats, vulnerabilities and impact. Hence, Yan et al.
(2012) commented that the management of risk to information system is usually considered as
the core base to enhanced cyber security. The existing journals claim that the individuals who
actually perform the cyber attack are largely cited as falling into one or more categories such as –
the criminals intention on monetary benefits from the crime and extortion. In addition, the spies
may steal classified or proprietary information utilized by the government.
Vulnerabilities
As put forward by Choo (2011), there is an ongoing battle in between the attackers and
defenders. It has been studied that Information Technology systems are continuously investing
the weaknesses that could take place at several areas. The defenders have been observed to be
protecting against the weakness but three significant aspects are significantly challenging such as
deliberate act by the insiders along with an access to a system, supply chain vulnerabilities,
which allows the insertion of malicious software at the time of acquisition process and zero-day
vulnerability (Li et al. 2012).
Impacts
It is often observed a successful attack could compromise the confidentiality, availability
of an ICT system, integrity and other significant information to deal with it (Sridhar, Hahn &
Govindarasu 2012). Cyber theft could result in exfiltration of financial and personal information
from which the attackers could gain the advantages. It is further studied that denial-of-service
attacks could slow down or restrict the legitimate users from accessing a system. Likewise, the
1.2 Management of Cyber Security risk
The studies on cyber security claim that risk associated with any particular attack could
depend on three significant factors such as threats, vulnerabilities and impact. Hence, Yan et al.
(2012) commented that the management of risk to information system is usually considered as
the core base to enhanced cyber security. The existing journals claim that the individuals who
actually perform the cyber attack are largely cited as falling into one or more categories such as –
the criminals intention on monetary benefits from the crime and extortion. In addition, the spies
may steal classified or proprietary information utilized by the government.
Vulnerabilities
As put forward by Choo (2011), there is an ongoing battle in between the attackers and
defenders. It has been studied that Information Technology systems are continuously investing
the weaknesses that could take place at several areas. The defenders have been observed to be
protecting against the weakness but three significant aspects are significantly challenging such as
deliberate act by the insiders along with an access to a system, supply chain vulnerabilities,
which allows the insertion of malicious software at the time of acquisition process and zero-day
vulnerability (Li et al. 2012).
Impacts
It is often observed a successful attack could compromise the confidentiality, availability
of an ICT system, integrity and other significant information to deal with it (Sridhar, Hahn &
Govindarasu 2012). Cyber theft could result in exfiltration of financial and personal information
from which the attackers could gain the advantages. It is further studied that denial-of-service
attacks could slow down or restrict the legitimate users from accessing a system. Likewise, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4BUSINESS RESEARCH METHOD
attacks on industrial control system could result in the destruction of the equipment. It is
identified that most of the cyber attacks have limited impacts, but a successful attack on some
significant components of critical infrastructure might have a significant effect on the security.
Therefore, Liu et al. (2012) mentioned that a rare successful attack with the high impact could
pose a significant risk compared to a general successful attack with low impact. In this context,
O’Connell (2012) mentioned that while it is recognized that cyber attacks could be costly to
individuals as well as the organizations, the economic influence could be difficult to measure and
estimate. Yan et al. (2013) also suggested that managing the risks from cyber attacks
conventionally engage the restricted threat source, identification of vulnerabilities by
strengthening the ICT infrastructure and lessening impacts by mitigating the damage and
restoring the function.
1.3 Major actors in cyber-security
A study conducted by Aloul et al. (2012), provided the below mentioned graph, which
presents the general position of the major actors on the question in internet governance and cyber
security such as the roles and responsibilities of governments and other stakeholders. The studies
claim that on one side, the USA and the business sector are arguing for the maintenance of
current and non-governmental model, with the strong participation by business sector.
Conversely, Russia and China like many other developing nations are arguing that internet needs
to be governed at the international extent by internal-governmental organizations (Line et al.
2011). Nonetheless, the clustering of nations around the specific barriers or issues such as
security, data protection provide a more conducive space for trade-offs as well as the possible
package deals in Internet governance negotiations. It has been identified that the closer people
attacks on industrial control system could result in the destruction of the equipment. It is
identified that most of the cyber attacks have limited impacts, but a successful attack on some
significant components of critical infrastructure might have a significant effect on the security.
Therefore, Liu et al. (2012) mentioned that a rare successful attack with the high impact could
pose a significant risk compared to a general successful attack with low impact. In this context,
O’Connell (2012) mentioned that while it is recognized that cyber attacks could be costly to
individuals as well as the organizations, the economic influence could be difficult to measure and
estimate. Yan et al. (2013) also suggested that managing the risks from cyber attacks
conventionally engage the restricted threat source, identification of vulnerabilities by
strengthening the ICT infrastructure and lessening impacts by mitigating the damage and
restoring the function.
1.3 Major actors in cyber-security
A study conducted by Aloul et al. (2012), provided the below mentioned graph, which
presents the general position of the major actors on the question in internet governance and cyber
security such as the roles and responsibilities of governments and other stakeholders. The studies
claim that on one side, the USA and the business sector are arguing for the maintenance of
current and non-governmental model, with the strong participation by business sector.
Conversely, Russia and China like many other developing nations are arguing that internet needs
to be governed at the international extent by internal-governmental organizations (Line et al.
2011). Nonetheless, the clustering of nations around the specific barriers or issues such as
security, data protection provide a more conducive space for trade-offs as well as the possible
package deals in Internet governance negotiations. It has been identified that the closer people
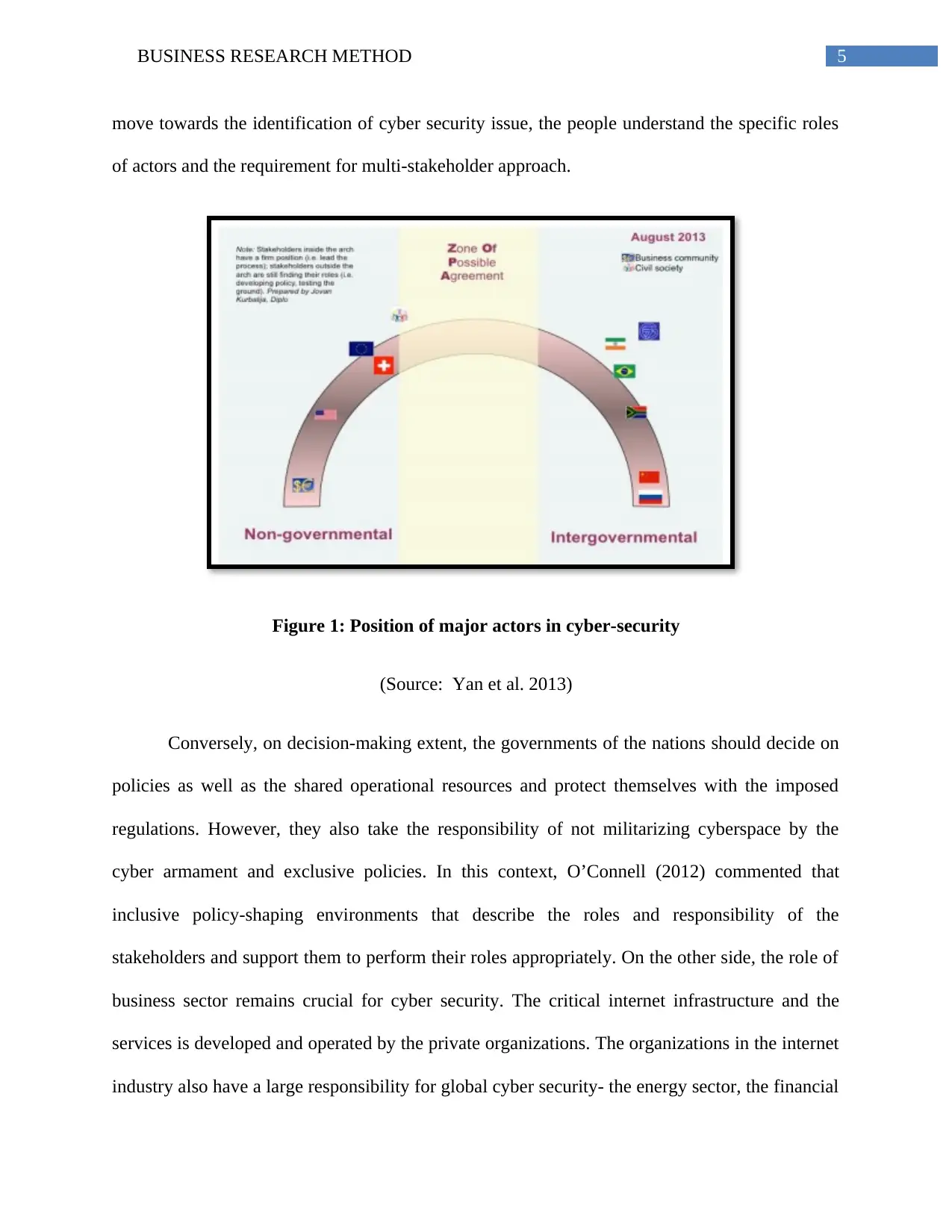
5BUSINESS RESEARCH METHOD
move towards the identification of cyber security issue, the people understand the specific roles
of actors and the requirement for multi-stakeholder approach.
Figure 1: Position of major actors in cyber-security
(Source: Yan et al. 2013)
Conversely, on decision-making extent, the governments of the nations should decide on
policies as well as the shared operational resources and protect themselves with the imposed
regulations. However, they also take the responsibility of not militarizing cyberspace by the
cyber armament and exclusive policies. In this context, O’Connell (2012) commented that
inclusive policy-shaping environments that describe the roles and responsibility of the
stakeholders and support them to perform their roles appropriately. On the other side, the role of
business sector remains crucial for cyber security. The critical internet infrastructure and the
services is developed and operated by the private organizations. The organizations in the internet
industry also have a large responsibility for global cyber security- the energy sector, the financial
move towards the identification of cyber security issue, the people understand the specific roles
of actors and the requirement for multi-stakeholder approach.
Figure 1: Position of major actors in cyber-security
(Source: Yan et al. 2013)
Conversely, on decision-making extent, the governments of the nations should decide on
policies as well as the shared operational resources and protect themselves with the imposed
regulations. However, they also take the responsibility of not militarizing cyberspace by the
cyber armament and exclusive policies. In this context, O’Connell (2012) commented that
inclusive policy-shaping environments that describe the roles and responsibility of the
stakeholders and support them to perform their roles appropriately. On the other side, the role of
business sector remains crucial for cyber security. The critical internet infrastructure and the
services is developed and operated by the private organizations. The organizations in the internet
industry also have a large responsibility for global cyber security- the energy sector, the financial
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BUSINESS RESEARCH METHOD
sector, manufacturing and technology sectors are the most frequent targets of the cyber attacks.
As mentioned by Dumitras and Neamtiu, (2011) awareness of the risks as well as the capacity to
prevent and react to incidents are the responsibility of the corporate sector where small and
medium size organizations are included. Hence, Waxman (2011) emphasized on the fact that
corporate sector should be incentivized to record these occurrence. Presently, there is a very
significant availability of information on the format and effects of cyber attack and sustained
incidents.
1.4 Price of Cyber attack
The United State National security directors Alexander referred cyber espionage as the
largest transfer of wealth. In this context, Aloul et al. (2012) mentioned that the cost of cyber
crime is anticipated to be upwards of $385 billion. On the other side, Waxman (2011) reported
that UK national Audit Office estimates cyber crime costs the nation UK between £18 billion
and £27 billion. The studies also claim that in 2013, almost 54% of overall cyber occurred in
United State, followed by China and Russia (Bonaci et al. 2015). It was studied that nearly half
of the attacks were originated in China and US. The studies indicate that cyber attack could
cause significant loss of business intelligence and drive up the cost of security, destroy the
workflow and damage organizational reputation. The organizations reporting major attacks
suffered a significant percentage of drops in stock value. Hence, some organizations recover and
others may lose everything. As put forward by Hay, Nance and Bishop (2011) Canadian telecom
Norter Network Ltd. had been infiltrated by Chinese hackers for almost a decade before filling
the bankruptcy in 2011. It is further observed that cyber espionage could be a significant threat
faced by the private sector. Hence, the theft of intellectual property is expected to account for
nearly three quarters of financial loss from cyber attack for the organizations. On the other side,
sector, manufacturing and technology sectors are the most frequent targets of the cyber attacks.
As mentioned by Dumitras and Neamtiu, (2011) awareness of the risks as well as the capacity to
prevent and react to incidents are the responsibility of the corporate sector where small and
medium size organizations are included. Hence, Waxman (2011) emphasized on the fact that
corporate sector should be incentivized to record these occurrence. Presently, there is a very
significant availability of information on the format and effects of cyber attack and sustained
incidents.
1.4 Price of Cyber attack
The United State National security directors Alexander referred cyber espionage as the
largest transfer of wealth. In this context, Aloul et al. (2012) mentioned that the cost of cyber
crime is anticipated to be upwards of $385 billion. On the other side, Waxman (2011) reported
that UK national Audit Office estimates cyber crime costs the nation UK between £18 billion
and £27 billion. The studies also claim that in 2013, almost 54% of overall cyber occurred in
United State, followed by China and Russia (Bonaci et al. 2015). It was studied that nearly half
of the attacks were originated in China and US. The studies indicate that cyber attack could
cause significant loss of business intelligence and drive up the cost of security, destroy the
workflow and damage organizational reputation. The organizations reporting major attacks
suffered a significant percentage of drops in stock value. Hence, some organizations recover and
others may lose everything. As put forward by Hay, Nance and Bishop (2011) Canadian telecom
Norter Network Ltd. had been infiltrated by Chinese hackers for almost a decade before filling
the bankruptcy in 2011. It is further observed that cyber espionage could be a significant threat
faced by the private sector. Hence, the theft of intellectual property is expected to account for
nearly three quarters of financial loss from cyber attack for the organizations. On the other side,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BUSINESS RESEARCH METHOD
the organizations are turning to insurance as financial protection against the inevitable threat of
attacks. When the cyber insurance often covers the expense to repair systems security breaches
and regulatory fees, the most regulations and most policies have exception restricting the scope
of coverage to exclude the loss of stolen intellectual property.
1.5 The threat landscape
Cyber crime is often associated with small organizations or rough actors, nonetheless a
UN study discovered that almost 80% of 500 incidents evaluated some form of organized
activity and most of them affiliated. A survey conducted by Kwon, Liu and Hwang (2013),
indicates that almost 62% of the respondents believe that their organizations would be targeted in
a state-sponsored attack within the coming months. Hence, Dunn Cavelty (2013) in 2012, a large
financial cyber-heist attack dubbed “Operational High Roller” was introduced from network
storage in Russia. The attack caused significant loss because of the global banking system across
which includes between $78 million and $2.5 billion in losses from the bank setting across
Europe. It is also observed that successful breaches on the energy sector have skyrocketed
causing insurance organizations to consider several energy firms uninsurable. In this context,
Busch and Givens (2012)commented that defense of intellectual property as well as the business
is a key security priority in public and private sector.
1.6 Internal cooperation
The technology has evolved to acquire international effort to operate cyber space. The
cyber attacks represents a multitude of border issues, developing the jurisdiction is complicated
and made more challenging by the difficult task of attributing the attack to a particular
organization. In spite of the barriers, the organizations have implemented some particular
the organizations are turning to insurance as financial protection against the inevitable threat of
attacks. When the cyber insurance often covers the expense to repair systems security breaches
and regulatory fees, the most regulations and most policies have exception restricting the scope
of coverage to exclude the loss of stolen intellectual property.
1.5 The threat landscape
Cyber crime is often associated with small organizations or rough actors, nonetheless a
UN study discovered that almost 80% of 500 incidents evaluated some form of organized
activity and most of them affiliated. A survey conducted by Kwon, Liu and Hwang (2013),
indicates that almost 62% of the respondents believe that their organizations would be targeted in
a state-sponsored attack within the coming months. Hence, Dunn Cavelty (2013) in 2012, a large
financial cyber-heist attack dubbed “Operational High Roller” was introduced from network
storage in Russia. The attack caused significant loss because of the global banking system across
which includes between $78 million and $2.5 billion in losses from the bank setting across
Europe. It is also observed that successful breaches on the energy sector have skyrocketed
causing insurance organizations to consider several energy firms uninsurable. In this context,
Busch and Givens (2012)commented that defense of intellectual property as well as the business
is a key security priority in public and private sector.
1.6 Internal cooperation
The technology has evolved to acquire international effort to operate cyber space. The
cyber attacks represents a multitude of border issues, developing the jurisdiction is complicated
and made more challenging by the difficult task of attributing the attack to a particular
organization. In spite of the barriers, the organizations have implemented some particular

8BUSINESS RESEARCH METHOD
procedures to defend the cyber attack. In the year, 2004, the Convention on Cyber crime became
the first global treaty to identify internet crime with the help of harmonization of national law
(Dumitras & Neamtiu 2011). As there was a belief that cyber crime is effectively approached on
a global level, the European councils have been observed to be underwent for many years of
negotiation to create the convention which promote inter-industry cooperation between the
country and the organizations in the private sector.
It emphasizes on the security of public assets and develops to follow a crime policy to
fight against the cyber attack. Hence, the convention has been ratified by almost 30 nations at the
initial stage from the council of Europe. In addition, it is widely considered as one of the best
method mechanism for global cooperation and hacking. In order to fight against these continuous
cyber attacks, the nations have developed two different resolutions criminalizing the misuse of
Information Technology and declared that international law applies to cyberspace. In this
context, Aloul et al. (2012) also commented that Cybercrime, a vast majority of cyber incidents
encountered by the police were transactional. Some of the governments of the nations with the
help of most advanced technological capabilities have contradictory views on cyber-security
policy, which develops a significant barrier to an effective global agreement. As the
consequence, many countries depend on bilateral an agreement, which is opposed to
international agreements. As put forward by O’Connell (2012), nearly 60% of the nations in the
UN research revealed that they depend on bilateral instruments as the legal base for extradition
in cybercrime cases.
procedures to defend the cyber attack. In the year, 2004, the Convention on Cyber crime became
the first global treaty to identify internet crime with the help of harmonization of national law
(Dumitras & Neamtiu 2011). As there was a belief that cyber crime is effectively approached on
a global level, the European councils have been observed to be underwent for many years of
negotiation to create the convention which promote inter-industry cooperation between the
country and the organizations in the private sector.
It emphasizes on the security of public assets and develops to follow a crime policy to
fight against the cyber attack. Hence, the convention has been ratified by almost 30 nations at the
initial stage from the council of Europe. In addition, it is widely considered as one of the best
method mechanism for global cooperation and hacking. In order to fight against these continuous
cyber attacks, the nations have developed two different resolutions criminalizing the misuse of
Information Technology and declared that international law applies to cyberspace. In this
context, Aloul et al. (2012) also commented that Cybercrime, a vast majority of cyber incidents
encountered by the police were transactional. Some of the governments of the nations with the
help of most advanced technological capabilities have contradictory views on cyber-security
policy, which develops a significant barrier to an effective global agreement. As the
consequence, many countries depend on bilateral an agreement, which is opposed to
international agreements. As put forward by O’Connell (2012), nearly 60% of the nations in the
UN research revealed that they depend on bilateral instruments as the legal base for extradition
in cybercrime cases.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BUSINESS RESEARCH METHOD
1.7 A look to the future
As cyber attack increases in complexity, the private sector should try to reduce as much
vulnerability as possible. On the basis of the recent studies, the attackers are considered as the
group of criminals with wide network and resource. Several organizations were state-affiliated,
presenting an increasing complex political frontier for the private as well as public sector
organizations. When the organizations face the present and existing issues, they could also face
the activity of preparing for future ones. For example, the attacks against the pharmaceutical and
healthcare sectors are projected to continue to increase. It was studied that medical records
contain significant information permitting hackers to steal identities as well as commit
unauthorized users in a way that seems difficult for the agencies to catch. As mentioned by Line,
Tøndel and Jaatun (2011), criminal attacks on healthcare organizations between 2010 and 2013
increased to 100% and this will continue to rise with time if the policies are not implemented.
This particular shift by several organizations to cloud computing carries an enormous security
threat as nearly three quarters of respondents are using the cloud computing. Since the degree of
information stored in cloud in cloud increases, there remains the risk of cyber attack and
necessity for the tools to protect detect the tools to protect the significant cloud data. The rapid
growth in personal device use on organizational networks has developed increasing threats. For
instance, an employee’s individual device is infected with the malware on a public network, the
employees brings the device to work and connects the internet. This practice unknowingly
provides the anonymous users with the access to confidential and vital information. In order to
manage the threat, the organizations should counteract the flow in personal device use with the
policies and education to mitigate the potential loss connected with the control devices.
1.7 A look to the future
As cyber attack increases in complexity, the private sector should try to reduce as much
vulnerability as possible. On the basis of the recent studies, the attackers are considered as the
group of criminals with wide network and resource. Several organizations were state-affiliated,
presenting an increasing complex political frontier for the private as well as public sector
organizations. When the organizations face the present and existing issues, they could also face
the activity of preparing for future ones. For example, the attacks against the pharmaceutical and
healthcare sectors are projected to continue to increase. It was studied that medical records
contain significant information permitting hackers to steal identities as well as commit
unauthorized users in a way that seems difficult for the agencies to catch. As mentioned by Line,
Tøndel and Jaatun (2011), criminal attacks on healthcare organizations between 2010 and 2013
increased to 100% and this will continue to rise with time if the policies are not implemented.
This particular shift by several organizations to cloud computing carries an enormous security
threat as nearly three quarters of respondents are using the cloud computing. Since the degree of
information stored in cloud in cloud increases, there remains the risk of cyber attack and
necessity for the tools to protect detect the tools to protect the significant cloud data. The rapid
growth in personal device use on organizational networks has developed increasing threats. For
instance, an employee’s individual device is infected with the malware on a public network, the
employees brings the device to work and connects the internet. This practice unknowingly
provides the anonymous users with the access to confidential and vital information. In order to
manage the threat, the organizations should counteract the flow in personal device use with the
policies and education to mitigate the potential loss connected with the control devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10BUSINESS RESEARCH METHOD
As mentioned by Sridhar, Hahn and Govindarasu (2012) Cyber security is now one of
the significant security priorities for large global organizations. O’Connell (2012) categorized the
organizations in two ways-those who have infiltrated and those who still do not know about it.
Even though, it is widely impossible to prevent the attack completely applying the formal
policies and security tools to protect the networks and mitigate the break of a breach. Internally,
the organizations in the private sector tend to control a significant portion of critical
infrastructure and the government services. As the consequence, the cyber threats are a massive
danger to both private as well as public security. As the organizations work towards the
improvement of effective practices, they are also tasked with keeping the governmental the laws
and regulations. Conversely, the governments should incentivize the organizations to exchange
information as well as allocate larger source for security. Hence, Dumitras and Neamtiu (2011)
commented that as the cyber landscape change and the threats evolve, the attacks on the private
organizations could continue to impose enormous risk to innovation, national security and
economic growth.
1.8 Gaps in the literature
The analysis conducted above helps to state that existing studies have only focused on
how cyber security challenges have been affecting the technological base of the organizations. In
addition, the studies have emphasized on the type of attacks that organizations face or might
have to face during the operation. The studies have provided some evidence where cyber attacks
proved to be significant threats for the business operation. However, none of the paper disused
about how the business is suffering or it is going to suffer in the coming days. The journals on
cyber attacks did not discuss about the how the business is negatively impacted such as an
As mentioned by Sridhar, Hahn and Govindarasu (2012) Cyber security is now one of
the significant security priorities for large global organizations. O’Connell (2012) categorized the
organizations in two ways-those who have infiltrated and those who still do not know about it.
Even though, it is widely impossible to prevent the attack completely applying the formal
policies and security tools to protect the networks and mitigate the break of a breach. Internally,
the organizations in the private sector tend to control a significant portion of critical
infrastructure and the government services. As the consequence, the cyber threats are a massive
danger to both private as well as public security. As the organizations work towards the
improvement of effective practices, they are also tasked with keeping the governmental the laws
and regulations. Conversely, the governments should incentivize the organizations to exchange
information as well as allocate larger source for security. Hence, Dumitras and Neamtiu (2011)
commented that as the cyber landscape change and the threats evolve, the attacks on the private
organizations could continue to impose enormous risk to innovation, national security and
economic growth.
1.8 Gaps in the literature
The analysis conducted above helps to state that existing studies have only focused on
how cyber security challenges have been affecting the technological base of the organizations. In
addition, the studies have emphasized on the type of attacks that organizations face or might
have to face during the operation. The studies have provided some evidence where cyber attacks
proved to be significant threats for the business operation. However, none of the paper disused
about how the business is suffering or it is going to suffer in the coming days. The journals on
cyber attacks did not discuss about the how the business is negatively impacted such as an
11BUSINESS RESEARCH METHOD
enormous loss and ethical challenges. The studies did not present any evidence regarding the
organizations suffering from significant financial loss due to cyber attack.
enormous loss and ethical challenges. The studies did not present any evidence regarding the
organizations suffering from significant financial loss due to cyber attack.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





