Challenges in Cybersecurity for Business: Analysis and Solutions
VerifiedAdded on 2020/10/22
|11
|3209
|491
Report
AI Summary
This report examines the multifaceted challenges of cybersecurity within a business context, emphasizing the importance of data protection and the safeguarding of intellectual property. It explores the need for organizations to adopt robust security measures to maintain data integrity and ensure business continuity. The report delves into the objectives, scope, and literature review, identifying key research questions about the impact of cybersecurity on organizational performance, employee and customer security, and gaps in implementation. The research methodology focuses on a qualitative approach, detailing steps such as research question determination, study design, data collection, analysis, and output generation. It also addresses the validation of findings and reliability through expert consultation and background studies. The report underscores the significance of cybersecurity in the digital era, emphasizing its role in maintaining brand image, customer trust, and operational efficiency. Furthermore, the report examines the importance of cybersecurity tools and techniques for business sustainability and revenue generation, and it highlights the need for continuous improvement in cybersecurity measures to effectively address emerging threats and protect vital business information.

Challenges in Cyber Security
for Business
for Business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
Project objectives........................................................................................................................1
Project scope...............................................................................................................................1
Literature review.........................................................................................................................1
Research Question.......................................................................................................................3
Research design and methodologies...........................................................................................3
Research limitation......................................................................................................................5
Time Schedule.............................................................................................................................6
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................8
INTRODUCTION...........................................................................................................................1
Project objectives........................................................................................................................1
Project scope...............................................................................................................................1
Literature review.........................................................................................................................1
Research Question.......................................................................................................................3
Research design and methodologies...........................................................................................3
Research limitation......................................................................................................................5
Time Schedule.............................................................................................................................6
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................8

INTRODUCTION
A wide range of challenges are faced by the organisation to a high extent that helps in
effective rise in compatibility and thus, facilitates a good maintaining of data and cyber security
within the firm. In order to safeguard the data, firm has to take in consideration various measures
that will support protection of intellectual property (Ilyas, 2015). Besides this, the firm will also
look after the adoption of different measures that will facilitate an effective cyber security within
an organisation. This will help in gaining sustainability and revenue generation within market.
For example: the cyber security will help in improving the performance of an organisation like
Marks and Spencer and protect their intellectual property. Apart from this, the gaps or the
differences within the firm will be analysed with their impact on a business organisation.
Project objectives
To gain an idea about cyber security
To analyse various measures related to cyber security
To identify different tools and techniques of online security within the firm (Rawat and
Bajracharya, 2015).
To identify various gaps and problems associated with cyber protection within an
enterprise
Project scope
The research project will help in effective increase in scope of the organisation to gain
good knowledge and insight about different measures and actions that are taken within firm for
cyber security. It will help a firm to handle a wide range of online security measures in a very
effective manner.
Literature review
Cyber security
Maintaining cyber security is essential for an organisation. The safeguarding of data and
important information is very important for an enterprise. According to the views of Carr
(2016.), maintaining cyber security will help in increasing potentiality of business entity. The
rise in capability and handling of business operations will support an effective rise in calibre of
an organisation. The loss of confidential and vital information from an organisation can affect its
1
A wide range of challenges are faced by the organisation to a high extent that helps in
effective rise in compatibility and thus, facilitates a good maintaining of data and cyber security
within the firm. In order to safeguard the data, firm has to take in consideration various measures
that will support protection of intellectual property (Ilyas, 2015). Besides this, the firm will also
look after the adoption of different measures that will facilitate an effective cyber security within
an organisation. This will help in gaining sustainability and revenue generation within market.
For example: the cyber security will help in improving the performance of an organisation like
Marks and Spencer and protect their intellectual property. Apart from this, the gaps or the
differences within the firm will be analysed with their impact on a business organisation.
Project objectives
To gain an idea about cyber security
To analyse various measures related to cyber security
To identify different tools and techniques of online security within the firm (Rawat and
Bajracharya, 2015).
To identify various gaps and problems associated with cyber protection within an
enterprise
Project scope
The research project will help in effective increase in scope of the organisation to gain
good knowledge and insight about different measures and actions that are taken within firm for
cyber security. It will help a firm to handle a wide range of online security measures in a very
effective manner.
Literature review
Cyber security
Maintaining cyber security is essential for an organisation. The safeguarding of data and
important information is very important for an enterprise. According to the views of Carr
(2016.), maintaining cyber security will help in increasing potentiality of business entity. The
rise in capability and handling of business operations will support an effective rise in calibre of
an organisation. The loss of confidential and vital information from an organisation can affect its
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

performance and productivity to a high extent. Besides this, the protection of vital information
will help in increase in functionality and meeting of targeted operations that will help in effective
assessment of business operations. Various cyber security tools are to be analysed by firm, which
will support a good handling of its business operations. Besides this, as per the research of
Haldorai and Ramu, (2018.), cyber threats are to be taken in consideration by the firm in order to
perform well in market. The theft and alteration of vital information related to an enterprise are
required to be taken in consideration which will facilitate effective growth and development and
rise in capability which will support an effective rise in operational capability of a business entity
in a very effective manner. Besides this, the effectiveness to protect data will help the business
entity to gain the customers trust, towards the business firm. This will increase the sales and
support a good revenue generation.
Cyber security, employees and customers
According to the views of Van den Berg and et.al., (2014), cyber security is closely
associated with their employees, customers and their benefits. As many firms, nowadays, tends
to store customers personal details, it is organisations liability to safeguard this data. Besides
this, the process of online transactions and fund transfer has to be made more reliable and safe
for the customers which will help in improvement of functional capability and handling of online
business activities will be made more valid and reliable. Other than this, the outputs of
evaluation by Lam, J., (2016,) indicates that the customer will be more attracted towards the firm
with better data and cyber security capability. This will help in increasing the trust and reliability
level of company's customer base towards a business entity and handling of the wide range of
business activities within the firm.
Importance of Cyber security
In the era of digital and internet based services, the cyber security is comparatively more
important factor for a business organisation. Establishing effective cyber security measures will
help in improving the operational efficiency and thus help in safeguarding the vital information
and data related to the firm and its customers. Other than this, it helps in suitable increase in
scope of business entity. As per the views of Cherdantseva and et.al., (2016.), the proper
management of data and cyber security approach will help in better rise in effectiveness and thus
will support an increase in capability and handling of the vital information related to a business
enterprise. The online security is also important for a firm to maintain its brand image in market
2
will help in increase in functionality and meeting of targeted operations that will help in effective
assessment of business operations. Various cyber security tools are to be analysed by firm, which
will support a good handling of its business operations. Besides this, as per the research of
Haldorai and Ramu, (2018.), cyber threats are to be taken in consideration by the firm in order to
perform well in market. The theft and alteration of vital information related to an enterprise are
required to be taken in consideration which will facilitate effective growth and development and
rise in capability which will support an effective rise in operational capability of a business entity
in a very effective manner. Besides this, the effectiveness to protect data will help the business
entity to gain the customers trust, towards the business firm. This will increase the sales and
support a good revenue generation.
Cyber security, employees and customers
According to the views of Van den Berg and et.al., (2014), cyber security is closely
associated with their employees, customers and their benefits. As many firms, nowadays, tends
to store customers personal details, it is organisations liability to safeguard this data. Besides
this, the process of online transactions and fund transfer has to be made more reliable and safe
for the customers which will help in improvement of functional capability and handling of online
business activities will be made more valid and reliable. Other than this, the outputs of
evaluation by Lam, J., (2016,) indicates that the customer will be more attracted towards the firm
with better data and cyber security capability. This will help in increasing the trust and reliability
level of company's customer base towards a business entity and handling of the wide range of
business activities within the firm.
Importance of Cyber security
In the era of digital and internet based services, the cyber security is comparatively more
important factor for a business organisation. Establishing effective cyber security measures will
help in improving the operational efficiency and thus help in safeguarding the vital information
and data related to the firm and its customers. Other than this, it helps in suitable increase in
scope of business entity. As per the views of Cherdantseva and et.al., (2016.), the proper
management of data and cyber security approach will help in better rise in effectiveness and thus
will support an increase in capability and handling of the vital information related to a business
enterprise. The online security is also important for a firm to maintain its brand image in market
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and retain customer base. It will also support an effective rise in capability and thus will help in
suitable handling of business activities which will aid to good increase in business operations.
Other than this, Kott and Arnold, (2015) stated that the cyber security measures will also
support in effective growth and development of business organisation which will support a good
increase in performance capacity and operations by the business entity and thus, will lead to
improvement in efficiency of organisation. The presence of cyber security measures will increase
the performance of a business enterprise to a greater extent, providing effective opportunity to
fill gaps in implementation in cyber security tools and techniques at work place. These gaps are
required to be handled in order to ensure proper functioning of business organisation to a high
extent.
Research Questions
Primary Question
“Analyse the importance of Cyber security measures within a business organisation?”
Secondary Questions
How does cyber security affect the performance of organisation?
Are the customers and employees within firm affected by problems in cyber security?
What are the gaps present in adoption and implementation of cyber security measures?
How the gaps in implementation and utilization of cyber security within firm can be
managed?
Research design and methodologies
The proper research design and methodologies are been taken in consideration by the
business enterprise that will support a good rise in capability and effectiveness of organisation.
The proper utilization of research designs and methodologies will support a good increase in
capability of the business operations which will support the good growth and development of
business operations in a very effective manner that will support a good increase in meeting of
targeted business operations that will be followed by a business enterprise (Skinner and et.al.,
2018). Other than this, it will also support a good rise in capability and meeting of targeted aims
and objectives within a firm. For the current research, Qualitative research is been taken in
thought process by the scholar. This will help the business enterprise to develop a better insight
3
suitable handling of business activities which will aid to good increase in business operations.
Other than this, Kott and Arnold, (2015) stated that the cyber security measures will also
support in effective growth and development of business organisation which will support a good
increase in performance capacity and operations by the business entity and thus, will lead to
improvement in efficiency of organisation. The presence of cyber security measures will increase
the performance of a business enterprise to a greater extent, providing effective opportunity to
fill gaps in implementation in cyber security tools and techniques at work place. These gaps are
required to be handled in order to ensure proper functioning of business organisation to a high
extent.
Research Questions
Primary Question
“Analyse the importance of Cyber security measures within a business organisation?”
Secondary Questions
How does cyber security affect the performance of organisation?
Are the customers and employees within firm affected by problems in cyber security?
What are the gaps present in adoption and implementation of cyber security measures?
How the gaps in implementation and utilization of cyber security within firm can be
managed?
Research design and methodologies
The proper research design and methodologies are been taken in consideration by the
business enterprise that will support a good rise in capability and effectiveness of organisation.
The proper utilization of research designs and methodologies will support a good increase in
capability of the business operations which will support the good growth and development of
business operations in a very effective manner that will support a good increase in meeting of
targeted business operations that will be followed by a business enterprise (Skinner and et.al.,
2018). Other than this, it will also support a good rise in capability and meeting of targeted aims
and objectives within a firm. For the current research, Qualitative research is been taken in
thought process by the scholar. This will help the business enterprise to develop a better insight
3

about the operations and activities that are been taken in consideration by the firm. The
qualitative assessment of the business operation is as follows:
Process of qualitative research: Various steps are been followed by the firm that will help in
effective improvement in business operations and thus facilitates a good improvement of
research activities. Some major steps that are been followed by the firm are:
Determining the research question: this step will help in assessment of basic question
related to the cyber security within the firm. It will help in development of effective
thinking and support proper decision making.
Designing the study: it accesses the basic questions like when, where, who and how,
related to the cyber security process meant to be followed within a firm. It will help in
rise in confidentiality of the organisation and thus support a good growth of knowledge
and effectiveness of organisation.
Data collection: the effective research process will include the proper data collection
measures that will support a good increase in insight about the research topic like cyber
security. A good collection of data will support proper handling of research and data
analysis process (Rawat and Bajracharya, 2015).
Analysing data: Once the data collection process is been finished, it is followed by data
analysis process that supports a good growth in data creation and generate suitable
outputs based on data or information collected. It supports the decision of further actions
and activities.
Generating outputs: the effective analysis of data will help in good generation of
outputs that will be very vital for effective development of insight and knowledge that
will support a good rise in effectiveness that will support an effective handling of
decision making process. Other than this, it helps in good deciding of future strategies.
Validation of findings: Validation of data is the biggest challenge that is been faced by
the scholar or researcher while carrying out the qualitative research process. As majority
of data is based on the opinion of the people which may vary from person to person.
Thus, this approach causes the variation in the output. Prior to the reporting of data by
researcher, it is required to be properly validated (Carr, 2016.).
The qualitative research process or methodologies which will help the scholar to handle
the business activities and operations that will help in good rise in meeting of targeted operations
4
qualitative assessment of the business operation is as follows:
Process of qualitative research: Various steps are been followed by the firm that will help in
effective improvement in business operations and thus facilitates a good improvement of
research activities. Some major steps that are been followed by the firm are:
Determining the research question: this step will help in assessment of basic question
related to the cyber security within the firm. It will help in development of effective
thinking and support proper decision making.
Designing the study: it accesses the basic questions like when, where, who and how,
related to the cyber security process meant to be followed within a firm. It will help in
rise in confidentiality of the organisation and thus support a good growth of knowledge
and effectiveness of organisation.
Data collection: the effective research process will include the proper data collection
measures that will support a good increase in insight about the research topic like cyber
security. A good collection of data will support proper handling of research and data
analysis process (Rawat and Bajracharya, 2015).
Analysing data: Once the data collection process is been finished, it is followed by data
analysis process that supports a good growth in data creation and generate suitable
outputs based on data or information collected. It supports the decision of further actions
and activities.
Generating outputs: the effective analysis of data will help in good generation of
outputs that will be very vital for effective development of insight and knowledge that
will support a good rise in effectiveness that will support an effective handling of
decision making process. Other than this, it helps in good deciding of future strategies.
Validation of findings: Validation of data is the biggest challenge that is been faced by
the scholar or researcher while carrying out the qualitative research process. As majority
of data is based on the opinion of the people which may vary from person to person.
Thus, this approach causes the variation in the output. Prior to the reporting of data by
researcher, it is required to be properly validated (Carr, 2016.).
The qualitative research process or methodologies which will help the scholar to handle
the business activities and operations that will help in good rise in meeting of targeted operations
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

and gaining of a good insight about the aims and objectives of research process followed by the
scholar. For example, M & S using the effective Cyber security measures to improve the
performance of the retail enterprise in a very effective way.
Approaches to reliability and validity
Different sort of approaches are required to be taken in thought process by the scholar or
researcher that will help in good rise in improvement of reliability and validity of data that is
been taken in consideration by the firm. The proper validation will involve the effective
assessment and analysis of data from verified sources. As in qualitative approach the
questionnaire and survey is been used, it will be dependent of the opinion of the organisation that
will support a good rise in capabilities of organisation. Other than this, the proper and in detail
assessment of business activities will help the firm to improve the effectiveness of organisation
that will support an effective increase in meeting of targeted aims and objectives in a better way.
Apart from this, a background study will be carried out at the organisation that will support an
effective rise in improving the calibre and effectiveness of the firm. It minimizes the risk of error
and reduce the treat of failing of research process by scholar. Besides this, the researcher can
consult with an expert at the enterprise to get the proper guidance about validating the resources
and data that are been collected under the research process. The proper validation of the data and
using of reliable resources for the research activity will increase its effectiveness in positive
manner. For example, the proper accessing of the experts for the validation of data will help the
firm to get a good and precise data.
Sample and Sample size:
The proper sampling of the data is very necessary for the effective handling of the
business operations that will support a good rise in capabilities of firm. It facilitates a good
collection and assessment of data. Besides this, the sample size will determine the amount of
data that is been collected and is meant for assessment in a research process for a better growth
and development of the firm. The basic type of sampling containing of random sampling will
help in good rise in the achieving of the targeted goals and operations that will support an
effective rise in increase in the capability of the organisation which will support a good rise in
effectiveness of research process that will be carried out within a business enterprise (Ilyas,
2015.).
5
scholar. For example, M & S using the effective Cyber security measures to improve the
performance of the retail enterprise in a very effective way.
Approaches to reliability and validity
Different sort of approaches are required to be taken in thought process by the scholar or
researcher that will help in good rise in improvement of reliability and validity of data that is
been taken in consideration by the firm. The proper validation will involve the effective
assessment and analysis of data from verified sources. As in qualitative approach the
questionnaire and survey is been used, it will be dependent of the opinion of the organisation that
will support a good rise in capabilities of organisation. Other than this, the proper and in detail
assessment of business activities will help the firm to improve the effectiveness of organisation
that will support an effective increase in meeting of targeted aims and objectives in a better way.
Apart from this, a background study will be carried out at the organisation that will support an
effective rise in improving the calibre and effectiveness of the firm. It minimizes the risk of error
and reduce the treat of failing of research process by scholar. Besides this, the researcher can
consult with an expert at the enterprise to get the proper guidance about validating the resources
and data that are been collected under the research process. The proper validation of the data and
using of reliable resources for the research activity will increase its effectiveness in positive
manner. For example, the proper accessing of the experts for the validation of data will help the
firm to get a good and precise data.
Sample and Sample size:
The proper sampling of the data is very necessary for the effective handling of the
business operations that will support a good rise in capabilities of firm. It facilitates a good
collection and assessment of data. Besides this, the sample size will determine the amount of
data that is been collected and is meant for assessment in a research process for a better growth
and development of the firm. The basic type of sampling containing of random sampling will
help in good rise in the achieving of the targeted goals and operations that will support an
effective rise in increase in the capability of the organisation which will support a good rise in
effectiveness of research process that will be carried out within a business enterprise (Ilyas,
2015.).
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The sample size will help in good rise in insight about the amount of data that is been
required to handle the business operations and thus will support a good handling of research
processes. It also supports an effective rise in efficiency of the organisation to carry out the
decision making process that will help in identifying the measures of research process that is
been taken in consideration by the firm.
Data collection methods:
Under the qualitative data research process, various data collection methods are been
taken in consideration that helps in good handling of the operations and thus facilitates an
effective gaining of opinion of people over a research topic. The major techniques that are been
taken in consideration for the data collection are the development of an effective Questionnaire,
either open ended or close ended in nature or a survey (Chen, 2017). The developing of the
questionnaire or survey sheet will help the researcher to narrow down the research activity,
making it more precise and accurate for on the point outputs that will support a good handling
and evaluation of data or information that is been gathered by the business entity. For instances,
a good data collection will help in getting a good insight about the importance of cyber security
on a firm.
Variables specification:
This includes the data sources of the persons that will be used for the data collection
process in the questionnaire or survey. This will help in improving the preciseness of the data
collection prices that will support good rise in handling of the business operations and thus
facilitates effective analysis of data or information collected related to cyber security in a firm.
Research limitation
At the current research process, various limitations will be faced by the scholar or
researcher that will impact the execution of research process in an effective handling of the
research operations. Some major limitations related to project are:
The proper validation of the data or the information that is been collected using
questionnaire and surveys under qualitative research method is a big challenge for the
scholar.
Selecting the ideal sample size is a big issue for the scholar that is required to be taken in
consideration (Reddy, 2015).
Evaluation and presentation of the output result requires extensive knowledge and skills.
6
required to handle the business operations and thus will support a good handling of research
processes. It also supports an effective rise in efficiency of the organisation to carry out the
decision making process that will help in identifying the measures of research process that is
been taken in consideration by the firm.
Data collection methods:
Under the qualitative data research process, various data collection methods are been
taken in consideration that helps in good handling of the operations and thus facilitates an
effective gaining of opinion of people over a research topic. The major techniques that are been
taken in consideration for the data collection are the development of an effective Questionnaire,
either open ended or close ended in nature or a survey (Chen, 2017). The developing of the
questionnaire or survey sheet will help the researcher to narrow down the research activity,
making it more precise and accurate for on the point outputs that will support a good handling
and evaluation of data or information that is been gathered by the business entity. For instances,
a good data collection will help in getting a good insight about the importance of cyber security
on a firm.
Variables specification:
This includes the data sources of the persons that will be used for the data collection
process in the questionnaire or survey. This will help in improving the preciseness of the data
collection prices that will support good rise in handling of the business operations and thus
facilitates effective analysis of data or information collected related to cyber security in a firm.
Research limitation
At the current research process, various limitations will be faced by the scholar or
researcher that will impact the execution of research process in an effective handling of the
research operations. Some major limitations related to project are:
The proper validation of the data or the information that is been collected using
questionnaire and surveys under qualitative research method is a big challenge for the
scholar.
Selecting the ideal sample size is a big issue for the scholar that is required to be taken in
consideration (Reddy, 2015).
Evaluation and presentation of the output result requires extensive knowledge and skills.
6
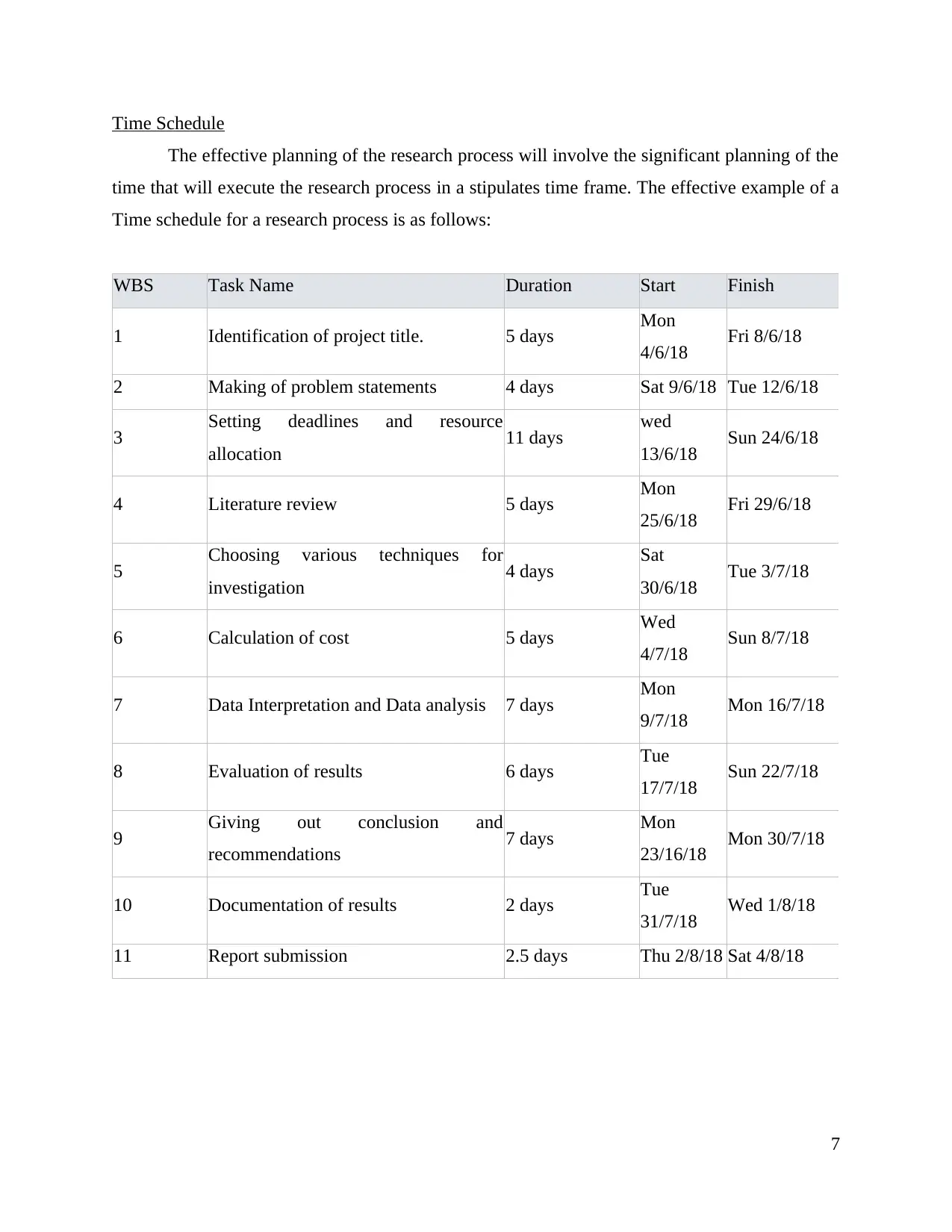
Time Schedule
The effective planning of the research process will involve the significant planning of the
time that will execute the research process in a stipulates time frame. The effective example of a
Time schedule for a research process is as follows:
WBS Task Name Duration Start Finish
1 Identification of project title. 5 days Mon
4/6/18 Fri 8/6/18
2 Making of problem statements 4 days Sat 9/6/18 Tue 12/6/18
3 Setting deadlines and resource
allocation 11 days wed
13/6/18 Sun 24/6/18
4 Literature review 5 days Mon
25/6/18 Fri 29/6/18
5 Choosing various techniques for
investigation 4 days Sat
30/6/18 Tue 3/7/18
6 Calculation of cost 5 days Wed
4/7/18 Sun 8/7/18
7 Data Interpretation and Data analysis 7 days Mon
9/7/18 Mon 16/7/18
8 Evaluation of results 6 days Tue
17/7/18 Sun 22/7/18
9 Giving out conclusion and
recommendations 7 days Mon
23/16/18 Mon 30/7/18
10 Documentation of results 2 days Tue
31/7/18 Wed 1/8/18
11 Report submission 2.5 days Thu 2/8/18 Sat 4/8/18
7
The effective planning of the research process will involve the significant planning of the
time that will execute the research process in a stipulates time frame. The effective example of a
Time schedule for a research process is as follows:
WBS Task Name Duration Start Finish
1 Identification of project title. 5 days Mon
4/6/18 Fri 8/6/18
2 Making of problem statements 4 days Sat 9/6/18 Tue 12/6/18
3 Setting deadlines and resource
allocation 11 days wed
13/6/18 Sun 24/6/18
4 Literature review 5 days Mon
25/6/18 Fri 29/6/18
5 Choosing various techniques for
investigation 4 days Sat
30/6/18 Tue 3/7/18
6 Calculation of cost 5 days Wed
4/7/18 Sun 8/7/18
7 Data Interpretation and Data analysis 7 days Mon
9/7/18 Mon 16/7/18
8 Evaluation of results 6 days Tue
17/7/18 Sun 22/7/18
9 Giving out conclusion and
recommendations 7 days Mon
23/16/18 Mon 30/7/18
10 Documentation of results 2 days Tue
31/7/18 Wed 1/8/18
11 Report submission 2.5 days Thu 2/8/18 Sat 4/8/18
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CONCLUSION
Based on the assessment, this can be said that the effective handling of the operations will
help in good rise in the operations and thus facilitates a good rise in the meeting of business
operations and activities. On the basis of assessment this can be concluded that the maintaining
of cyber security in a firm is very important as it helps in improving the overall performance of
an organisation like Marks and Spencer. The relation of online safety and customers loyalty is
been analysed and importance of the cyber security measures are been taken within the firm.
8
Based on the assessment, this can be said that the effective handling of the operations will
help in good rise in the operations and thus facilitates a good rise in the meeting of business
operations and activities. On the basis of assessment this can be concluded that the maintaining
of cyber security in a firm is very important as it helps in improving the overall performance of
an organisation like Marks and Spencer. The relation of online safety and customers loyalty is
been analysed and importance of the cyber security measures are been taken within the firm.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and journals
Haldorai, A. and Ramu, A., 2018. The Impact of Big Data Analytics and Challenges to Cyber
Security. In Handbook of Research on Network Forensics and Analysis Techniques (pp.
300-314). IGI Global.
Van den Berg, J. and et.al., 2014. On (the Emergence of) Cyber Security Science and its
Challenges for Cyber Security Education. In Proceedings of the NATO IST-122 Cyber
Security Science and Engineering Symposium (pp. 13-14).
Lam, J., 2016, June. IIET: Cyber security in modern power systems-Protecting large and
complex networks. In Cyber Security in Modern Power Systems, IET (pp. 1-12). IET.
Cherdantseva, Y. and et.al., 2016. A review of cyber security risk assessment methods for
SCADA systems. Computers & security, 56, pp.1-27.
Kott, A. and Arnold, C., 2015. Towards Approaches to Continuous Assessment of Cyber Risk in
Security of Computer Networks. arXiv preprint arXiv:1512.07937.
Skinner, T. and et.al., 2018, April. The Development of Intervention E-Learning Materials and
Implementation Techniques For Cyber-Security Behaviour Change. ACM SIG CHI.
Rawat, D.B. and Bajracharya, C., 2015, April. Cyber security for smart grid systems: Status,
challenges and perspectives. In SoutheastCon 2015 (pp. 1-6). IEEE.
Carr, M., 2016. Public–private partnerships in national cyber‐security strategies. International
Affairs, 92(1), pp.43-62.
Ilyas, M.M., 2015. Cyber security.
Chen, E.T., 2017. The Internet of Things: Opportunities, Issues, and Challenges. In The Internet
of Things in the Modern Business Environment (pp. 167-187). IGI Global.
Reddy, Y.B., 2015, April. Security and design challenges in cyber-physical systems.
In Information Technology-New Generations (ITNG), 2015 12th International
Conference on(pp. 200-205). IEEE.
9
Books and journals
Haldorai, A. and Ramu, A., 2018. The Impact of Big Data Analytics and Challenges to Cyber
Security. In Handbook of Research on Network Forensics and Analysis Techniques (pp.
300-314). IGI Global.
Van den Berg, J. and et.al., 2014. On (the Emergence of) Cyber Security Science and its
Challenges for Cyber Security Education. In Proceedings of the NATO IST-122 Cyber
Security Science and Engineering Symposium (pp. 13-14).
Lam, J., 2016, June. IIET: Cyber security in modern power systems-Protecting large and
complex networks. In Cyber Security in Modern Power Systems, IET (pp. 1-12). IET.
Cherdantseva, Y. and et.al., 2016. A review of cyber security risk assessment methods for
SCADA systems. Computers & security, 56, pp.1-27.
Kott, A. and Arnold, C., 2015. Towards Approaches to Continuous Assessment of Cyber Risk in
Security of Computer Networks. arXiv preprint arXiv:1512.07937.
Skinner, T. and et.al., 2018, April. The Development of Intervention E-Learning Materials and
Implementation Techniques For Cyber-Security Behaviour Change. ACM SIG CHI.
Rawat, D.B. and Bajracharya, C., 2015, April. Cyber security for smart grid systems: Status,
challenges and perspectives. In SoutheastCon 2015 (pp. 1-6). IEEE.
Carr, M., 2016. Public–private partnerships in national cyber‐security strategies. International
Affairs, 92(1), pp.43-62.
Ilyas, M.M., 2015. Cyber security.
Chen, E.T., 2017. The Internet of Things: Opportunities, Issues, and Challenges. In The Internet
of Things in the Modern Business Environment (pp. 167-187). IGI Global.
Reddy, Y.B., 2015, April. Security and design challenges in cyber-physical systems.
In Information Technology-New Generations (ITNG), 2015 12th International
Conference on(pp. 200-205). IEEE.
9
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





