Cyber Security Challenges on Business Performances in Pakistan SMEs
VerifiedAdded on 2023/06/11
|13
|2783
|192
Report
AI Summary
This report investigates the challenges of cyber security on the business performance of medium and large enterprises in Pakistan. It reviews existing literature, identifies research questions, and proposes a mixed-methods research design involving both qualitative (interviews) and quantitative (surveys) approaches. The research aims to understand the specific cyber threats faced by Pakistani businesses, evaluate existing cyber threat protection policies, and suggest measures for businesses and the government to mitigate these challenges. The study acknowledges limitations related to time, resources, and potential response bias. The ultimate goal is to provide insights and recommendations for enhancing cyber security practices and improving business resilience in Pakistan.

RUNNING HEAD: Business Research
Business Research
Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan
Business Research
Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 1
Table of Contents
Introduction...........................................................................................................................................2
Project objective....................................................................................................................................2
Project scope.........................................................................................................................................2
Literature Review..................................................................................................................................3
Research Questions...............................................................................................................................5
Research Design and Methodology.......................................................................................................6
Qualitative research..........................................................................................................................6
Quantitative research........................................................................................................................6
Research Limitations.............................................................................................................................8
Time Schedule (Research plan)..............................................................................................................8
Conclusion.............................................................................................................................................9
Reference List......................................................................................................................................10
Appendix.............................................................................................................................................12
Gantt chart.......................................................................................................................................12
enterprises in Pakistan 1
Table of Contents
Introduction...........................................................................................................................................2
Project objective....................................................................................................................................2
Project scope.........................................................................................................................................2
Literature Review..................................................................................................................................3
Research Questions...............................................................................................................................5
Research Design and Methodology.......................................................................................................6
Qualitative research..........................................................................................................................6
Quantitative research........................................................................................................................6
Research Limitations.............................................................................................................................8
Time Schedule (Research plan)..............................................................................................................8
Conclusion.............................................................................................................................................9
Reference List......................................................................................................................................10
Appendix.............................................................................................................................................12
Gantt chart.......................................................................................................................................12

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 2
Introduction
Cyber security can be understood as the process and set of technologies which is designed
in order to protect data and systems in the cyber world from the cyber-attacks (James,
2016). Due to the increased use of internet and technology, the number of cyber-attacks
have increased. The research is about the challenges of cyber security on the business
performance of the medium and large scale enterprises in Pakistan. The project proposal
includes the research questions and the methodology which will be used to take up the
research. Conclusion and recommendations will be provided for future of the industries of
Pakistan.
Project objective
The main objective of the project is to find out the challenges through which the medium
and large enterprises of Pakistan are going through. It will further aim at investigation of the
cyber threat protection policies in Pakistan which helps the enterprises in resolving the
problems faced by the companies. It is also to find out the main threats and their effect on
the companies. It will help in combating those threats and finding a way for businesses to
perform well without being a prey to cyber attackers (Hall, 2016).
Project scope
The scope of the project is broad. It is because Cyber security challenges are faced by almost
every next organisation in the world. This is because of the growing use of internet
(Clemente, 2013). The project affirms that if proper actions will be taken up by the
government and companies, a tough fight can be given to the cyber attackers and the threat
can be reduced. The scope is broad because it discusses about the whole medium and large
scale enterprises of Pakistan.
enterprises in Pakistan 2
Introduction
Cyber security can be understood as the process and set of technologies which is designed
in order to protect data and systems in the cyber world from the cyber-attacks (James,
2016). Due to the increased use of internet and technology, the number of cyber-attacks
have increased. The research is about the challenges of cyber security on the business
performance of the medium and large scale enterprises in Pakistan. The project proposal
includes the research questions and the methodology which will be used to take up the
research. Conclusion and recommendations will be provided for future of the industries of
Pakistan.
Project objective
The main objective of the project is to find out the challenges through which the medium
and large enterprises of Pakistan are going through. It will further aim at investigation of the
cyber threat protection policies in Pakistan which helps the enterprises in resolving the
problems faced by the companies. It is also to find out the main threats and their effect on
the companies. It will help in combating those threats and finding a way for businesses to
perform well without being a prey to cyber attackers (Hall, 2016).
Project scope
The scope of the project is broad. It is because Cyber security challenges are faced by almost
every next organisation in the world. This is because of the growing use of internet
(Clemente, 2013). The project affirms that if proper actions will be taken up by the
government and companies, a tough fight can be given to the cyber attackers and the threat
can be reduced. The scope is broad because it discusses about the whole medium and large
scale enterprises of Pakistan.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 3
Literature Review
From the review of literature, it can be said that different authors have different opinions on
the topic. As per Reddy & Reddy (2014), the cyber attackers hit the integrity and
confidentiality of data and pose a serious challenge to the businesses as this information be
leaked to competitors. This is why, it is considered as one of the most common and serious
threats because it might hamper the overall global position of the business (Foreshew,
2017).
In the opinion of Elmaghraby & Losavio (2014), the medium and large enterprises of the
nation plays a major role in its development. These industries or companies helps in
generating employment thereby reducing poverty and giving basic living to people. The loss
of data of these enterprises will indirectly impact the population working in these
companies. The hackers have the main motive to leak the sensitive information either to
blackmail or to use it against the owner of data. In Pakistan, National Database and
Registration Authority (NADRA) is the authority which keep details regarding passports,
networks of mobile, bank passwords, bank details, etc. Cyber attackers might target NADRA
for accessing the information which could have major negative implications in future.
As per Choo (2011), the cyber security issues decreases the overall business performance
and creates a fear of losing the data. The hackers generally attack the single server and then
link it to other servers to destroy all the systems at once. DDoS attacks is the biggest threat
which made its victims like BBC, Rio Olympics and more (Lohrke, Frownfelter-Lohrke and
Ketchen Jr, 2016). Cyber-attacks not only results in the loss of trust between the company
and the customer but also results in the loss of profits. It is very important for the
enterprises to adopt data protection systems and privacy policies so that they can save
themselves from facing the havoc (Nojeim, 2010).
In the words of Awan and Memon, (2016), Pakistan is a developing country and the attacks
like Trojans, frauds, phishing are most commonly faced by the companies operating in the
country. To prevent themselves from the cyber-attacks, the government should run training
programs for the medium and large scale enterprises to let them know how they can
protect their data and business as a whole (Kaplan, Sharma & Weinberg, 2011).
Justification to the research problem
It is evident that no country is now untouched with cyber threat. The countries who are
actively using technology is also facing the repercussions and are becoming the victims of
cyber criminals. This is a serious issue which should not be ignored and should be taken care
of so that the company could play safely with the data without getting in the fear of losing
the confidential data and privacy (Abomhara, 2015).
Gap in literature review
There is a gap in the literature review that it does not discuss about the steps which could
be taken by the collaboration of government and businesses to combat the serious threat.
enterprises in Pakistan 3
Literature Review
From the review of literature, it can be said that different authors have different opinions on
the topic. As per Reddy & Reddy (2014), the cyber attackers hit the integrity and
confidentiality of data and pose a serious challenge to the businesses as this information be
leaked to competitors. This is why, it is considered as one of the most common and serious
threats because it might hamper the overall global position of the business (Foreshew,
2017).
In the opinion of Elmaghraby & Losavio (2014), the medium and large enterprises of the
nation plays a major role in its development. These industries or companies helps in
generating employment thereby reducing poverty and giving basic living to people. The loss
of data of these enterprises will indirectly impact the population working in these
companies. The hackers have the main motive to leak the sensitive information either to
blackmail or to use it against the owner of data. In Pakistan, National Database and
Registration Authority (NADRA) is the authority which keep details regarding passports,
networks of mobile, bank passwords, bank details, etc. Cyber attackers might target NADRA
for accessing the information which could have major negative implications in future.
As per Choo (2011), the cyber security issues decreases the overall business performance
and creates a fear of losing the data. The hackers generally attack the single server and then
link it to other servers to destroy all the systems at once. DDoS attacks is the biggest threat
which made its victims like BBC, Rio Olympics and more (Lohrke, Frownfelter-Lohrke and
Ketchen Jr, 2016). Cyber-attacks not only results in the loss of trust between the company
and the customer but also results in the loss of profits. It is very important for the
enterprises to adopt data protection systems and privacy policies so that they can save
themselves from facing the havoc (Nojeim, 2010).
In the words of Awan and Memon, (2016), Pakistan is a developing country and the attacks
like Trojans, frauds, phishing are most commonly faced by the companies operating in the
country. To prevent themselves from the cyber-attacks, the government should run training
programs for the medium and large scale enterprises to let them know how they can
protect their data and business as a whole (Kaplan, Sharma & Weinberg, 2011).
Justification to the research problem
It is evident that no country is now untouched with cyber threat. The countries who are
actively using technology is also facing the repercussions and are becoming the victims of
cyber criminals. This is a serious issue which should not be ignored and should be taken care
of so that the company could play safely with the data without getting in the fear of losing
the confidential data and privacy (Abomhara, 2015).
Gap in literature review
There is a gap in the literature review that it does not discuss about the steps which could
be taken by the collaboration of government and businesses to combat the serious threat.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 4
Strong laws should be made to punish the cyber attackers, once caught. It has been seen
that there is no strong law and legislation are made to meet cyber threats in Pakistan which
is a danger sign for the companies.
enterprises in Pakistan 4
Strong laws should be made to punish the cyber attackers, once caught. It has been seen
that there is no strong law and legislation are made to meet cyber threats in Pakistan which
is a danger sign for the companies.

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 5
Research Questions
The main research questions are divided into primary and secondary questions.
Primary question
What are the challenges of cyber security on business performances of medium and
large enterprises in Pakistan?
Secondary questions
How Pakistan is facing the challenge of Cyber security in business
What steps the government and business should take to meet these challenges?
enterprises in Pakistan 5
Research Questions
The main research questions are divided into primary and secondary questions.
Primary question
What are the challenges of cyber security on business performances of medium and
large enterprises in Pakistan?
Secondary questions
How Pakistan is facing the challenge of Cyber security in business
What steps the government and business should take to meet these challenges?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 6
Research Design and Methodology
Here in this section, methods will be discussed which will be used to perform the whole
research on the topic. This section is of major importance as this will only determine the
process of research and data collection process which helps in reaching out to a final
conclusion.
Qualitative research
Research process
This type of research begins with a plan where time and scope will be determined. The next
step involves the development of research objectives and questions. Next step includes the
steps which are used to meet the objectives of the research and the last step is to develop
final research project report (Mackey & Gass, 2015).
Reliability and Validity
The data is reliable which is checked through the references and sourcing of data. This is
inductive research because a theoretical base is made for the research.
Sampling technique and sample size
For collecting qualitative data, sampling would be made on non-probability sampling basis.
An interview will be planned with 10 medium and large sized enterprise business employees
or owners which will help in collecting quality data. The sample size is 10.
Data collection
Data is collected over here with the help of structured interview where set of questions will
be asked from the respondents and they will be allowed to answer them in details. The
interview questions will be open ended so that subjective information can be gained from
the respondents.
Quantitative research
Research process
The initial step of quantitative research is identification of the problem after which the
questions are developed for research and then review is conducted of different secondary
sources. Further, research methodology is planned and data is collected through various
sources. The data collected will be analysed after collection. Further, conclusion and
recommendations will be given for giving further suggestions on the future research
(Wilson, 2016).
enterprises in Pakistan 6
Research Design and Methodology
Here in this section, methods will be discussed which will be used to perform the whole
research on the topic. This section is of major importance as this will only determine the
process of research and data collection process which helps in reaching out to a final
conclusion.
Qualitative research
Research process
This type of research begins with a plan where time and scope will be determined. The next
step involves the development of research objectives and questions. Next step includes the
steps which are used to meet the objectives of the research and the last step is to develop
final research project report (Mackey & Gass, 2015).
Reliability and Validity
The data is reliable which is checked through the references and sourcing of data. This is
inductive research because a theoretical base is made for the research.
Sampling technique and sample size
For collecting qualitative data, sampling would be made on non-probability sampling basis.
An interview will be planned with 10 medium and large sized enterprise business employees
or owners which will help in collecting quality data. The sample size is 10.
Data collection
Data is collected over here with the help of structured interview where set of questions will
be asked from the respondents and they will be allowed to answer them in details. The
interview questions will be open ended so that subjective information can be gained from
the respondents.
Quantitative research
Research process
The initial step of quantitative research is identification of the problem after which the
questions are developed for research and then review is conducted of different secondary
sources. Further, research methodology is planned and data is collected through various
sources. The data collected will be analysed after collection. Further, conclusion and
recommendations will be given for giving further suggestions on the future research
(Wilson, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 7
Instrument of research
Data is collected through a set of structured questionnaire which will be used to conduct
survey among 50 employees working in the medium and large enterprises in Pakistan.
Data is also collected through secondary sources like books, journals, publications from
government, online websites and news articles.
Data analysis
The data collected but using research instrument will be analysed with the help of statistical
methods like SPSS and MS excel. These will help in giving the results of the opinions of
sample size and then will help in giving the final results of the research.
Sampling technique and size
Random sampling technique will be used in this assignment to select the employees from
the medium and large enterprises in order to collect data about cyber security challenges to
their business and what steps they take to meet these challenges. The sample size is 50.
Reliability and Validity
The research is reliable as the data is collected after gaining the permissions and orders
from the relevant authorities. The questions are asked which do not mean to hurt the
sentiments of any group of people. No fake information is given in the research and this is
proved by sources used which are genuine and shows real data for the topic.
Data collection
Two types of sources are used in this research to collect data for coming to a conclusion as
to what challenges are faced by business and its performance in maintaining cyber security
(Cooper, Schindler & Sun, 2006). These sources include primary and secondary sources.
Primary sources of data collection used are books, relevant government publications,
reports, websites, journals and more. Also, a set of 10 questions were prepared to develop a
questionnaire on the basis of which the survey will be conducted.
enterprises in Pakistan 7
Instrument of research
Data is collected through a set of structured questionnaire which will be used to conduct
survey among 50 employees working in the medium and large enterprises in Pakistan.
Data is also collected through secondary sources like books, journals, publications from
government, online websites and news articles.
Data analysis
The data collected but using research instrument will be analysed with the help of statistical
methods like SPSS and MS excel. These will help in giving the results of the opinions of
sample size and then will help in giving the final results of the research.
Sampling technique and size
Random sampling technique will be used in this assignment to select the employees from
the medium and large enterprises in order to collect data about cyber security challenges to
their business and what steps they take to meet these challenges. The sample size is 50.
Reliability and Validity
The research is reliable as the data is collected after gaining the permissions and orders
from the relevant authorities. The questions are asked which do not mean to hurt the
sentiments of any group of people. No fake information is given in the research and this is
proved by sources used which are genuine and shows real data for the topic.
Data collection
Two types of sources are used in this research to collect data for coming to a conclusion as
to what challenges are faced by business and its performance in maintaining cyber security
(Cooper, Schindler & Sun, 2006). These sources include primary and secondary sources.
Primary sources of data collection used are books, relevant government publications,
reports, websites, journals and more. Also, a set of 10 questions were prepared to develop a
questionnaire on the basis of which the survey will be conducted.
Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 8
Research Limitations
The research had some limitations which might hamper the final results of the research
process. The first limitation is of time. The time available for the research is limited which
might not give results in details because a small sample size is selected which might not
provide the actual results of the whole population. The resources are limited because of
which more research cannot be done. The responses provided by the respondents might be
biased because they do not want to showcase real picture of their protection methods from
cyber threats. All these limitations will deviate the actual results of the research.
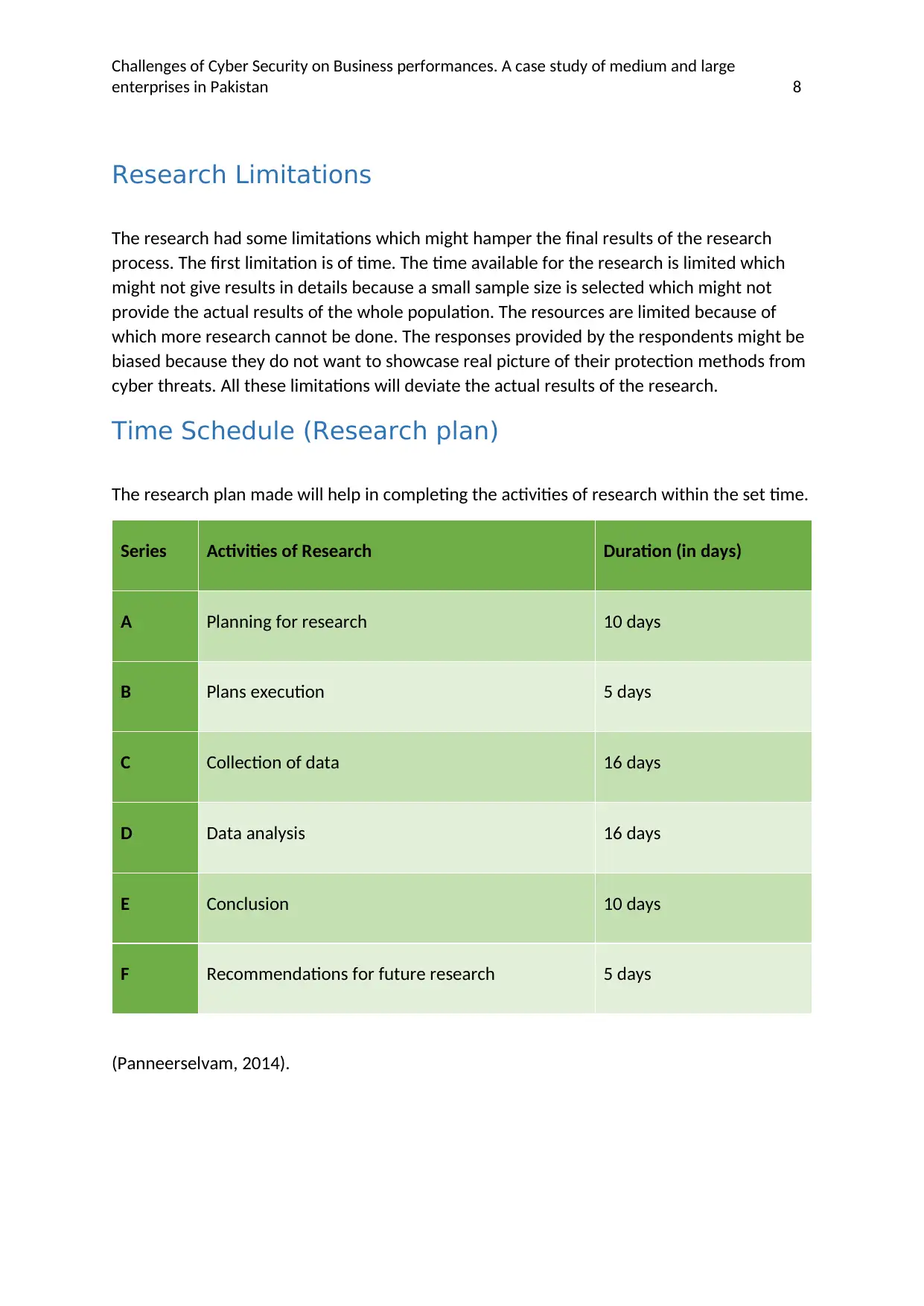
Time Schedule (Research plan)
The research plan made will help in completing the activities of research within the set time.
Series Activities of Research Duration (in days)
A Planning for research 10 days
B Plans execution 5 days
C Collection of data 16 days
D Data analysis 16 days
E Conclusion 10 days
F Recommendations for future research 5 days
(Panneerselvam, 2014).
enterprises in Pakistan 8
Research Limitations
The research had some limitations which might hamper the final results of the research
process. The first limitation is of time. The time available for the research is limited which
might not give results in details because a small sample size is selected which might not
provide the actual results of the whole population. The resources are limited because of
which more research cannot be done. The responses provided by the respondents might be
biased because they do not want to showcase real picture of their protection methods from
cyber threats. All these limitations will deviate the actual results of the research.
Time Schedule (Research plan)
The research plan made will help in completing the activities of research within the set time.
Series Activities of Research Duration (in days)
A Planning for research 10 days
B Plans execution 5 days
C Collection of data 16 days
D Data analysis 16 days
E Conclusion 10 days
F Recommendations for future research 5 days
(Panneerselvam, 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 9
Conclusion
It can be concluded that cybercrimes are increasing drastically because of the increased use
of technology. Data collected from various sources which suggest that the government
should take certain steps which helps in fighting the evils of cybercrime. The government
should frame strong laws and policies which will save the confidential data of the medium
and large enterprises. It will also save employment of people and data in banks, stock
exchanges, government sectors, etc. which could save the country from terror attacks also.
It is recommended that the medium and large industries should work in collaboration with
the government for combating the serious issue and for eliminating it from roots.
enterprises in Pakistan 9
Conclusion
It can be concluded that cybercrimes are increasing drastically because of the increased use
of technology. Data collected from various sources which suggest that the government
should take certain steps which helps in fighting the evils of cybercrime. The government
should frame strong laws and policies which will save the confidential data of the medium
and large enterprises. It will also save employment of people and data in banks, stock
exchanges, government sectors, etc. which could save the country from terror attacks also.
It is recommended that the medium and large industries should work in collaboration with
the government for combating the serious issue and for eliminating it from roots.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 10
Reference List
Abomhara, M. (2015). Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Awan, J. & Memon, S. (2016). Threats of cyber security and challenges for Pakistan.
In International Conference on Cyber Warfare and Security (p. 425). Academic Conferences
International Limited.
Choo, K. K. R. (2011). The cyber threat landscape: Challenges and future research
directions. Computers & Security, 30(8), pp.719-731.
Clemente, D. (2013). Cyber security and global interdependence: what is critical?. Chatham
House, Royal Institute of International Affairs.
Cooper, D.R., Schindler, P.S. & Sun, J. (2006). Business research methods (Vol. 9). New York:
McGraw-Hill Irwin.
Elmaghraby, A.S., & Losavio, M.M. (2014). Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of Advanced Research, vol. 5, no. 4, pp. 491-497.
Foreshew, J. (2017). Australia faces cyber security skills crisis as challenge. Financial Review.
Hall, P. (2016). Smaller banks face cybersecurity challenges. Westchester County Business
Journal, vol. 52, no. 46, pp. 15.
James, C. (2016). Cybersecurity: Threats Challenges Opportunities. ACS.
Kaplan, J., Sharma, S. & Weinberg, A. (2011). Meeting the cybersecurity challenge. McKinsey
& Company.
Lohrke, F.T., Frownfelter-Lohrke, C. & Ketchen Jr, D.J. (2016). The role of information
technology systems in the performance of mergers and acquisitions. Business
Horizons, 59(1), pp.7-12.
enterprises in Pakistan 10
Reference List
Abomhara, M. (2015). Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Awan, J. & Memon, S. (2016). Threats of cyber security and challenges for Pakistan.
In International Conference on Cyber Warfare and Security (p. 425). Academic Conferences
International Limited.
Choo, K. K. R. (2011). The cyber threat landscape: Challenges and future research
directions. Computers & Security, 30(8), pp.719-731.
Clemente, D. (2013). Cyber security and global interdependence: what is critical?. Chatham
House, Royal Institute of International Affairs.
Cooper, D.R., Schindler, P.S. & Sun, J. (2006). Business research methods (Vol. 9). New York:
McGraw-Hill Irwin.
Elmaghraby, A.S., & Losavio, M.M. (2014). Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of Advanced Research, vol. 5, no. 4, pp. 491-497.
Foreshew, J. (2017). Australia faces cyber security skills crisis as challenge. Financial Review.
Hall, P. (2016). Smaller banks face cybersecurity challenges. Westchester County Business
Journal, vol. 52, no. 46, pp. 15.
James, C. (2016). Cybersecurity: Threats Challenges Opportunities. ACS.
Kaplan, J., Sharma, S. & Weinberg, A. (2011). Meeting the cybersecurity challenge. McKinsey
& Company.
Lohrke, F.T., Frownfelter-Lohrke, C. & Ketchen Jr, D.J. (2016). The role of information
technology systems in the performance of mergers and acquisitions. Business
Horizons, 59(1), pp.7-12.

Challenges of Cyber Security on Business performances. A case study of medium and large
enterprises in Pakistan 11
Mackey, A. & Gass, S. M. (2015). Second language research: Methodology and design.
Routledge.
Nojeim, G. T. (2010). Cybersecurity and Freedom on the Internet. J. Nat'l Sec. L. & Pol'y, 4,
p.119.
Panneerselvam, R. (2014). Research methodology. PHI Learning Pvt. Ltd..
Reddy, G.N. &Reddy, G.J. (2014). A Study of Cyber Security Challenges and its emerging
trends on latest technologies. arXiv preprint arXiv:1402.1842.
Wilson, V. (2016). Research Methods: Mixed Methods Research. Evidence Based Library and
Information Practice, 11, 56-59.
enterprises in Pakistan 11
Mackey, A. & Gass, S. M. (2015). Second language research: Methodology and design.
Routledge.
Nojeim, G. T. (2010). Cybersecurity and Freedom on the Internet. J. Nat'l Sec. L. & Pol'y, 4,
p.119.
Panneerselvam, R. (2014). Research methodology. PHI Learning Pvt. Ltd..
Reddy, G.N. &Reddy, G.J. (2014). A Study of Cyber Security Challenges and its emerging
trends on latest technologies. arXiv preprint arXiv:1402.1842.
Wilson, V. (2016). Research Methods: Mixed Methods Research. Evidence Based Library and
Information Practice, 11, 56-59.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





