Cybersecurity Frameworks, Threats, and Solutions: Research Project
VerifiedAdded on 2020/05/16
|12
|2758
|38
Project
AI Summary
This research project investigates cybersecurity issues faced by contemporary companies, focusing on the impact of the internet and online services. The study aims to analyze cyber threats, including DDoS attacks and IoT vulnerabilities, and propose solutions for businesses. The project employs a mixed-methods approach, combining literature reviews, surveys, and qualitative and quantitative data analysis. It examines factors affecting cybersecurity, challenges encountered by organizations, and effective security measures. The research includes a survey of Australian firms, employing purposive and convenience sampling to gather primary data, and utilizes secondary data from academic journals and official websites. The study acknowledges limitations, such as the focus on cybersecurity and not on company security management, and the potential difficulty in generalizing conclusions beyond the sample of 30 industrial units in Australia. The project concludes with a time schedule outlining key activities over a 10-month period.

Running head: BUSINESS RESEARCH METHOD
Business Research Method
University Name
Student Name
Authors’ Note
Business Research Method
University Name
Student Name
Authors’ Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2BUSINESS RESEARCH METHOD
Table of Contents
1. Introduction............................................................................................................................2
2. Project Objective....................................................................................................................3
3. Scope of the project................................................................................................................3
4. Review of literature................................................................................................................3
5. Research Questions/Hypothesis.............................................................................................6
6. Research Design and Methodology.......................................................................................6
7. Research Limitations..............................................................................................................9
8. Time Schedule........................................................................................................................9
9. Conclusion............................................................................................................................10
10. References..........................................................................................................................12
Table of Contents
1. Introduction............................................................................................................................2
2. Project Objective....................................................................................................................3
3. Scope of the project................................................................................................................3
4. Review of literature................................................................................................................3
5. Research Questions/Hypothesis.............................................................................................6
6. Research Design and Methodology.......................................................................................6
7. Research Limitations..............................................................................................................9
8. Time Schedule........................................................................................................................9
9. Conclusion............................................................................................................................10
10. References..........................................................................................................................12

3BUSINESS RESEARCH METHOD
1. Introduction
Cyber security can be considered to be used interchangeably for mainly information security,
in which the latter takes into account the role of human in process of security whilst the
former deems this as a supplementary element and also, centre person has a prospective
target. Nevertheless, this kind of conversation on cyber security has significant implication
since it stresses on the ethical aspects of the community on the whole. In a bid to deal with
this specific issue of cyber security, diverse frameworks as well as models are designed. The
current study also initiates the notions of cyber security from the dimension of its framework,
workforce as well as information associated to shielding personal information in the
computer.
2. Project Objective
The primary objective of this study is to conduct an assessment of literature on diverse issues
associated to cybersecurity encountered by contemporary companies owing to the reputation
of the internet along with internet-based services. The researcher intends to analyse diverse
firms and the cyber-attacks encountered by these firms to comprehend the influence of
cybercrimes (Massey 2017). Again, the secondary aim is to deliver a variety of suggestions
that can be used by firms to address the threats of cybersecurity.
3. Scope of the project
In the current study, the researcher intends to analytically review the influence of the internet
as well as other online services on the function of firms and comprehend the alterations in
their functions to evaluate their susceptibility towards threats of cyber crime. In addition to
this, the researcher also needs to assess diverse cyber threat, along with online risks
encountered by corporations in current years (Monostori 2014). Different theories along with
1. Introduction
Cyber security can be considered to be used interchangeably for mainly information security,
in which the latter takes into account the role of human in process of security whilst the
former deems this as a supplementary element and also, centre person has a prospective
target. Nevertheless, this kind of conversation on cyber security has significant implication
since it stresses on the ethical aspects of the community on the whole. In a bid to deal with
this specific issue of cyber security, diverse frameworks as well as models are designed. The
current study also initiates the notions of cyber security from the dimension of its framework,
workforce as well as information associated to shielding personal information in the
computer.
2. Project Objective
The primary objective of this study is to conduct an assessment of literature on diverse issues
associated to cybersecurity encountered by contemporary companies owing to the reputation
of the internet along with internet-based services. The researcher intends to analyse diverse
firms and the cyber-attacks encountered by these firms to comprehend the influence of
cybercrimes (Massey 2017). Again, the secondary aim is to deliver a variety of suggestions
that can be used by firms to address the threats of cybersecurity.
3. Scope of the project
In the current study, the researcher intends to analytically review the influence of the internet
as well as other online services on the function of firms and comprehend the alterations in
their functions to evaluate their susceptibility towards threats of cyber crime. In addition to
this, the researcher also needs to assess diverse cyber threat, along with online risks
encountered by corporations in current years (Monostori 2014). Different theories along with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4BUSINESS RESEARCH METHOD
professional advice explained in the section on review of literature can help in understanding
the aims of the study.
4. Review of literature
Critical Issues associated to cyber security
Cyber security mainly upon care that diverse individuals can get and conclusions that they
arrive at whilst they arrange, handle and use systems along with Internet. Efforts are put to
discover solutions for particularly cyber security analysis challenge and diverse structures are
also constructed. Nevertheless, the structure faces diverse intricacies even though it was
initially working at the time of development (Wan et al. 2014). The limitations draw from
different aspects, namely, emerging technologies along with facility restrictions.
As rightly indicated by Ruchkin et al. (2016), progression of the internet in the past decade
has augmented overall utilization of the internet based services in various corporations.
Several corporations utilize infrastructure founded on internet to deliver the services as this
makes it seamless for organizations to reach out to global audience. In place of large firms,
internet use has essentially become substantially accepted among individuals, business
entrepreneurs along with small corporations. As suggested by Taylor et al. (2014),
individuals make use of internet for the purpose of connecting as well as sharing with friends
and families. This also delivers business opportunities to various business entrepreneurs
together with small corporations to expand the business operations. In addition to this, both
business concerns along with people upload various sensitive along with personal data on
particularly the internet that makes them the potential target for cyber attacks. Majority of
cyber crimes are undertaken by individuals who have admittance to the internet as well as
computer as inadequacy of security dimensions can make it seamless for them to target
various innocent individuals. According to Elmaghraby and Losavio (2014), there are
professional advice explained in the section on review of literature can help in understanding
the aims of the study.
4. Review of literature
Critical Issues associated to cyber security
Cyber security mainly upon care that diverse individuals can get and conclusions that they
arrive at whilst they arrange, handle and use systems along with Internet. Efforts are put to
discover solutions for particularly cyber security analysis challenge and diverse structures are
also constructed. Nevertheless, the structure faces diverse intricacies even though it was
initially working at the time of development (Wan et al. 2014). The limitations draw from
different aspects, namely, emerging technologies along with facility restrictions.
As rightly indicated by Ruchkin et al. (2016), progression of the internet in the past decade
has augmented overall utilization of the internet based services in various corporations.
Several corporations utilize infrastructure founded on internet to deliver the services as this
makes it seamless for organizations to reach out to global audience. In place of large firms,
internet use has essentially become substantially accepted among individuals, business
entrepreneurs along with small corporations. As suggested by Taylor et al. (2014),
individuals make use of internet for the purpose of connecting as well as sharing with friends
and families. This also delivers business opportunities to various business entrepreneurs
together with small corporations to expand the business operations. In addition to this, both
business concerns along with people upload various sensitive along with personal data on
particularly the internet that makes them the potential target for cyber attacks. Majority of
cyber crimes are undertaken by individuals who have admittance to the internet as well as
computer as inadequacy of security dimensions can make it seamless for them to target
various innocent individuals. According to Elmaghraby and Losavio (2014), there are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5BUSINESS RESEARCH METHOD
different hackers that undertake various cybercrime for the purpose of collecting personal
data of individuals along with corporations in order to acquire an unfair advantage. In
addition to this, popularity of the internet has made it seamless for them. Particularly, there
are various causes owing to which cyber attacks has augmented in the last decade.
Harel et al. (2017) illustrated that social media sites can be regarded as one of the primary
reasons for individuals’ susceptibility to cybercrime. Reports suggest that there are over and
above 2.9 million active users on multiple social media platforms. However, together with
popularity of the social media stages, the cybercrimes risk has developed thoroughly. Hackers
also target the social media takes into account and corporations to acquire sensitive data.
Majority of the corporations namely the PlayStation, Yahoo as well as HBO had also
encountered cybercrimes that led to loss of important data.
Robinson et al. (2015) suggests that mobile banking can be considered to be another
important ground that contributes to enhancement of the total number of cyber crimes on
particular individuals as well as firms. This is mainly because this presents the chance to
acquire unfair benefit. During the year 2017, approximately 44% of the entire globe’s
population utilizes smart phone and this enhances the overall internet based services.
Utilization of online banking services namely PayPal, online shopping and use of mobile
wallet has enhanced cyber security threats. Mishna et al. (2015) mentioned that in case of
online banking, individuals have the need to share financial data on basically the online
stages of banks.
Several instances of the challenges encountered by corporations as regards online security
include DDoS also known as Distributed Denial of Service attack. This happens mainly over
a server and enhances the traffic of these kinds of server. Instances contain BBC, DYN,
election campaign conducted by Donald Trump and five different Russian banks. In addition
different hackers that undertake various cybercrime for the purpose of collecting personal
data of individuals along with corporations in order to acquire an unfair advantage. In
addition to this, popularity of the internet has made it seamless for them. Particularly, there
are various causes owing to which cyber attacks has augmented in the last decade.
Harel et al. (2017) illustrated that social media sites can be regarded as one of the primary
reasons for individuals’ susceptibility to cybercrime. Reports suggest that there are over and
above 2.9 million active users on multiple social media platforms. However, together with
popularity of the social media stages, the cybercrimes risk has developed thoroughly. Hackers
also target the social media takes into account and corporations to acquire sensitive data.
Majority of the corporations namely the PlayStation, Yahoo as well as HBO had also
encountered cybercrimes that led to loss of important data.
Robinson et al. (2015) suggests that mobile banking can be considered to be another
important ground that contributes to enhancement of the total number of cyber crimes on
particular individuals as well as firms. This is mainly because this presents the chance to
acquire unfair benefit. During the year 2017, approximately 44% of the entire globe’s
population utilizes smart phone and this enhances the overall internet based services.
Utilization of online banking services namely PayPal, online shopping and use of mobile
wallet has enhanced cyber security threats. Mishna et al. (2015) mentioned that in case of
online banking, individuals have the need to share financial data on basically the online
stages of banks.
Several instances of the challenges encountered by corporations as regards online security
include DDoS also known as Distributed Denial of Service attack. This happens mainly over
a server and enhances the traffic of these kinds of server. Instances contain BBC, DYN,
election campaign conducted by Donald Trump and five different Russian banks. In addition

6BUSINESS RESEARCH METHOD
to this, Internet of Things (IOT) is also observed to develop at a fast space, let us say, smart
home appliances have become popular among developed markets (Broy and Schmidt 2014).
IoTs devices linked through single network led to risk of security.
5. Research Questions/Hypothesis
-Primary Questions
-What are fundamentally the critical issues faced in the cyber security?
-What are the factors affecting the cyber security?
Secondary Questions
-What are the challenges that are encountered majority of the time in the organizations?
-What are the proper security measures against the cyber security threats?
6. Research Design and Methodology
The current research makes use of survey mechanism for the purpose of identification of
diverse cyber security concerns along with experiment method for development of the
framework. The current research study is associated to the cyber security management with
reference to firm operating in Australia. In the current study, both primary as well as
secondary data is acquired to discover the significance of network security and detection of
intrusion system. In this case, primary data is gathered by means of survey method whilst
secondary data is acquired from various published together with non-published data (Bogdan
2015).
to this, Internet of Things (IOT) is also observed to develop at a fast space, let us say, smart
home appliances have become popular among developed markets (Broy and Schmidt 2014).
IoTs devices linked through single network led to risk of security.
5. Research Questions/Hypothesis
-Primary Questions
-What are fundamentally the critical issues faced in the cyber security?
-What are the factors affecting the cyber security?
Secondary Questions
-What are the challenges that are encountered majority of the time in the organizations?
-What are the proper security measures against the cyber security threats?
6. Research Design and Methodology
The current research makes use of survey mechanism for the purpose of identification of
diverse cyber security concerns along with experiment method for development of the
framework. The current research study is associated to the cyber security management with
reference to firm operating in Australia. In the current study, both primary as well as
secondary data is acquired to discover the significance of network security and detection of
intrusion system. In this case, primary data is gathered by means of survey method whilst
secondary data is acquired from various published together with non-published data (Bogdan
2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7BUSINESS RESEARCH METHOD
Primary Data:
This current study can be acquired by means of survey method. Essentially, this data is
basically unique in nature. Fundamentally, this data will be acquired by way of distributing
the formulated questionnaire and getting the same filled by the respective respondents for the
current purpose. In this case, the learner aims to use online questionnaire for the present
purpose (Sha and Zeadally 2015).
Sample Design:
Sample design can be regarded as particular plans that can be designed by acquired samples
from a selected population (Johnson 2015). In a bid to serve this specific purpose of the
subject of the research, the learner intends to select a total of 30 sample units. In this case, the
learner intends to utilize the sampling technique of purposive sampling along with
convenience sampling. For the purpose of the present study, the population that the learner
intends to select include various firms operating in different sectors in Australia. Therefore,
in this case, the learner presents the sampling frame that consists of 30 industrial units in
Australia. Essentially, the parameter of interest for the current study is ascertaining the
challenges of cyber security in selected industrial units in Australia.
Selection of respondent:
The learner intends to select respondents of the current study that are operating in the
industrial units in Australia and having over and above 2 years of work experience. In
addition to this, the learner also intends to select the ones working in the IT or the IT security
division of the firms (Mangharam et al. 2016). The researcher intends to send the
questionnaire via mail to the selected respondents with request for reply.
Primary Data:
This current study can be acquired by means of survey method. Essentially, this data is
basically unique in nature. Fundamentally, this data will be acquired by way of distributing
the formulated questionnaire and getting the same filled by the respective respondents for the
current purpose. In this case, the learner aims to use online questionnaire for the present
purpose (Sha and Zeadally 2015).
Sample Design:
Sample design can be regarded as particular plans that can be designed by acquired samples
from a selected population (Johnson 2015). In a bid to serve this specific purpose of the
subject of the research, the learner intends to select a total of 30 sample units. In this case, the
learner intends to utilize the sampling technique of purposive sampling along with
convenience sampling. For the purpose of the present study, the population that the learner
intends to select include various firms operating in different sectors in Australia. Therefore,
in this case, the learner presents the sampling frame that consists of 30 industrial units in
Australia. Essentially, the parameter of interest for the current study is ascertaining the
challenges of cyber security in selected industrial units in Australia.
Selection of respondent:
The learner intends to select respondents of the current study that are operating in the
industrial units in Australia and having over and above 2 years of work experience. In
addition to this, the learner also intends to select the ones working in the IT or the IT security
division of the firms (Mangharam et al. 2016). The researcher intends to send the
questionnaire via mail to the selected respondents with request for reply.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8BUSINESS RESEARCH METHOD
Questionnaire
Questionnaire is primarily meant for the purpose of acquiring specific information regarding
cyber challenges encountered by firm, different aspects of the cyber threats, primary factors
contributing to the threats of cyber security (Massey 2017). In addition to this, the current
study also intends to contain questions that can specifically help in gathering knowledge
regarding different dimensions of cyber challenges, various instances of the cyber security
threats in firms and the suggestions from the standpoint from their standpoint to combat this
issue.
Secondary Data
The learner also intends to make use of secondary data that can be utilized for the purpose of
studying the cyber security. This secondary data can be utilized to discover specific features,
themes of the cyber crime, threats, and dimensions of measuring security measures to protect
the security. Essentially, this secondary data can be obtained from various reputed academic
journals, prior research articles, official websites as well as product documentation (Massey
2017).
The current study has the intention to utilize both qualitative as well as quantitative research
strategy in this regard.
-Qualitative Research- The learner has the intention to utilize focus on in-depth interviews
as well as carry out assessment of documents for different categories of themes. Essentially,
the researcher has the intent to carry out a subjective study in this regards and describe the
problem otherwise the conditions from the viewpoint of the ones experiencing the same. In
this case, no statistical tests necessarily will be used in this regard. The methods of analysis
that can be used in this study include the discourse analysis, case study analysis, observation
Questionnaire
Questionnaire is primarily meant for the purpose of acquiring specific information regarding
cyber challenges encountered by firm, different aspects of the cyber threats, primary factors
contributing to the threats of cyber security (Massey 2017). In addition to this, the current
study also intends to contain questions that can specifically help in gathering knowledge
regarding different dimensions of cyber challenges, various instances of the cyber security
threats in firms and the suggestions from the standpoint from their standpoint to combat this
issue.
Secondary Data
The learner also intends to make use of secondary data that can be utilized for the purpose of
studying the cyber security. This secondary data can be utilized to discover specific features,
themes of the cyber crime, threats, and dimensions of measuring security measures to protect
the security. Essentially, this secondary data can be obtained from various reputed academic
journals, prior research articles, official websites as well as product documentation (Massey
2017).
The current study has the intention to utilize both qualitative as well as quantitative research
strategy in this regard.
-Qualitative Research- The learner has the intention to utilize focus on in-depth interviews
as well as carry out assessment of documents for different categories of themes. Essentially,
the researcher has the intent to carry out a subjective study in this regards and describe the
problem otherwise the conditions from the viewpoint of the ones experiencing the same. In
this case, no statistical tests necessarily will be used in this regard. The methods of analysis
that can be used in this study include the discourse analysis, case study analysis, observation
9BUSINESS RESEARCH METHOD
and thematic analysis (Taylor et al. 2014). In this case, the discourse analysis takes in
process of material coding, assessment of structure together with various assertions together
with recognition of diverse dimensions of cyber security.
-Quantitative Research- The learner also intends to present surveys as well as assess the
available records for specifically numerical information. In this case, the learner has the
intent to use deductive procedure and can be said to be justified as this can help in testing
various pre-specified themes, constructs as well as hypotheses that can help in making up the
theory (Sha and Zeadally 2015). In this case, statistical tests necessarily will be used in this
regard namely descriptive as well as interpretive statistics.
7. Research Limitations
The current research primarily refers to cyber security, challenges associated to cyber
security along with mechanisms that can avert the attack. However, the study does not focus
on proper methods of company’s security management (Sha and Zeadally 2015). Again,
administrators of the corporation can undertake actions for different security management in
30 industrial units in Australia. Therefore, it might become difficult to generalise the
conclusions drawn from the study.
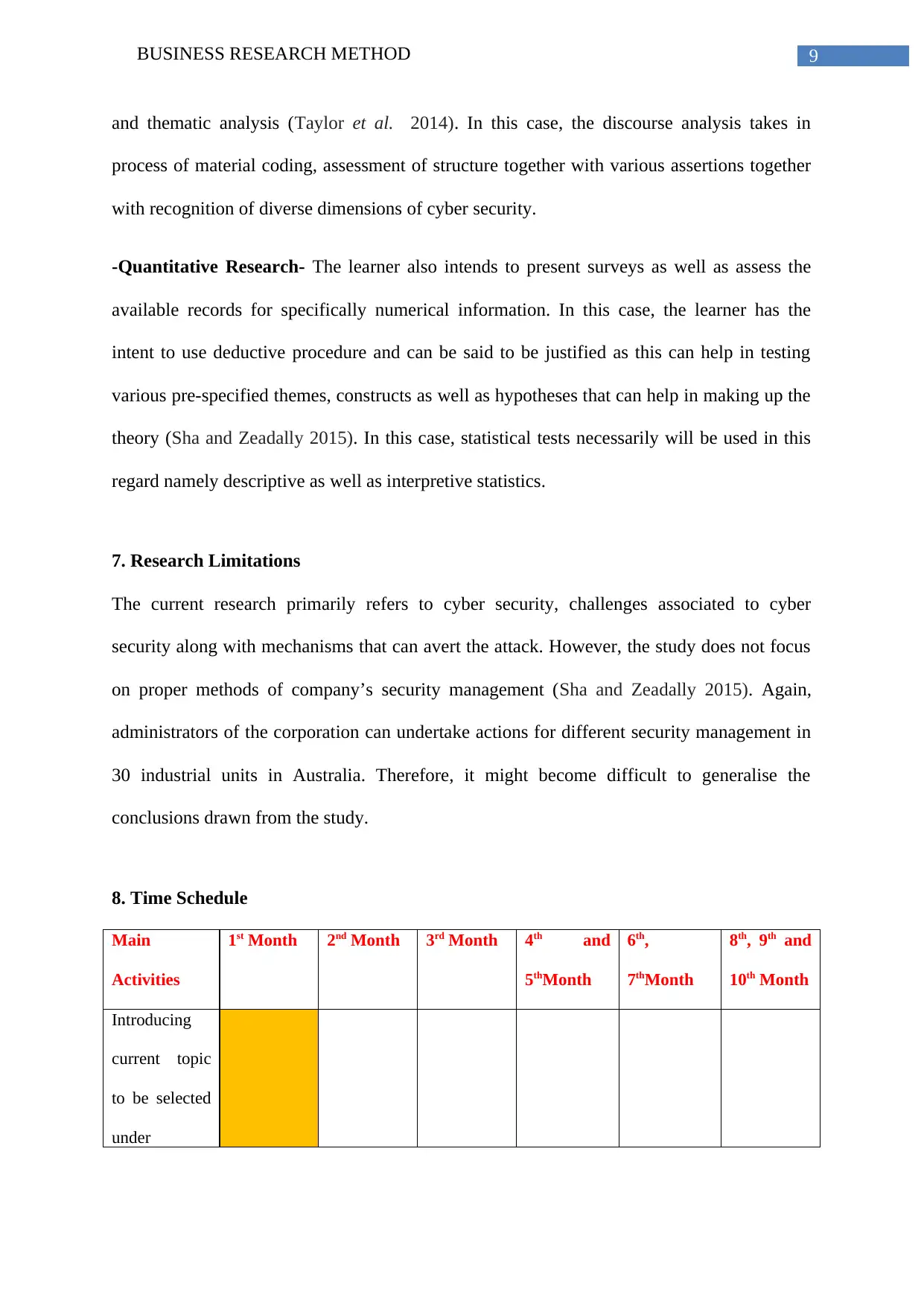
8. Time Schedule
Main
Activities
1st Month 2nd Month 3rd Month 4th and
5thMonth
6th,
7thMonth
8th, 9th and
10th Month
Introducing
current topic
to be selected
under
and thematic analysis (Taylor et al. 2014). In this case, the discourse analysis takes in
process of material coding, assessment of structure together with various assertions together
with recognition of diverse dimensions of cyber security.
-Quantitative Research- The learner also intends to present surveys as well as assess the
available records for specifically numerical information. In this case, the learner has the
intent to use deductive procedure and can be said to be justified as this can help in testing
various pre-specified themes, constructs as well as hypotheses that can help in making up the
theory (Sha and Zeadally 2015). In this case, statistical tests necessarily will be used in this
regard namely descriptive as well as interpretive statistics.
7. Research Limitations
The current research primarily refers to cyber security, challenges associated to cyber
security along with mechanisms that can avert the attack. However, the study does not focus
on proper methods of company’s security management (Sha and Zeadally 2015). Again,
administrators of the corporation can undertake actions for different security management in
30 industrial units in Australia. Therefore, it might become difficult to generalise the
conclusions drawn from the study.
8. Time Schedule
Main
Activities
1st Month 2nd Month 3rd Month 4th and
5thMonth
6th,
7thMonth
8th, 9th and
10th Month
Introducing
current topic
to be selected
under
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10BUSINESS RESEARCH METHOD
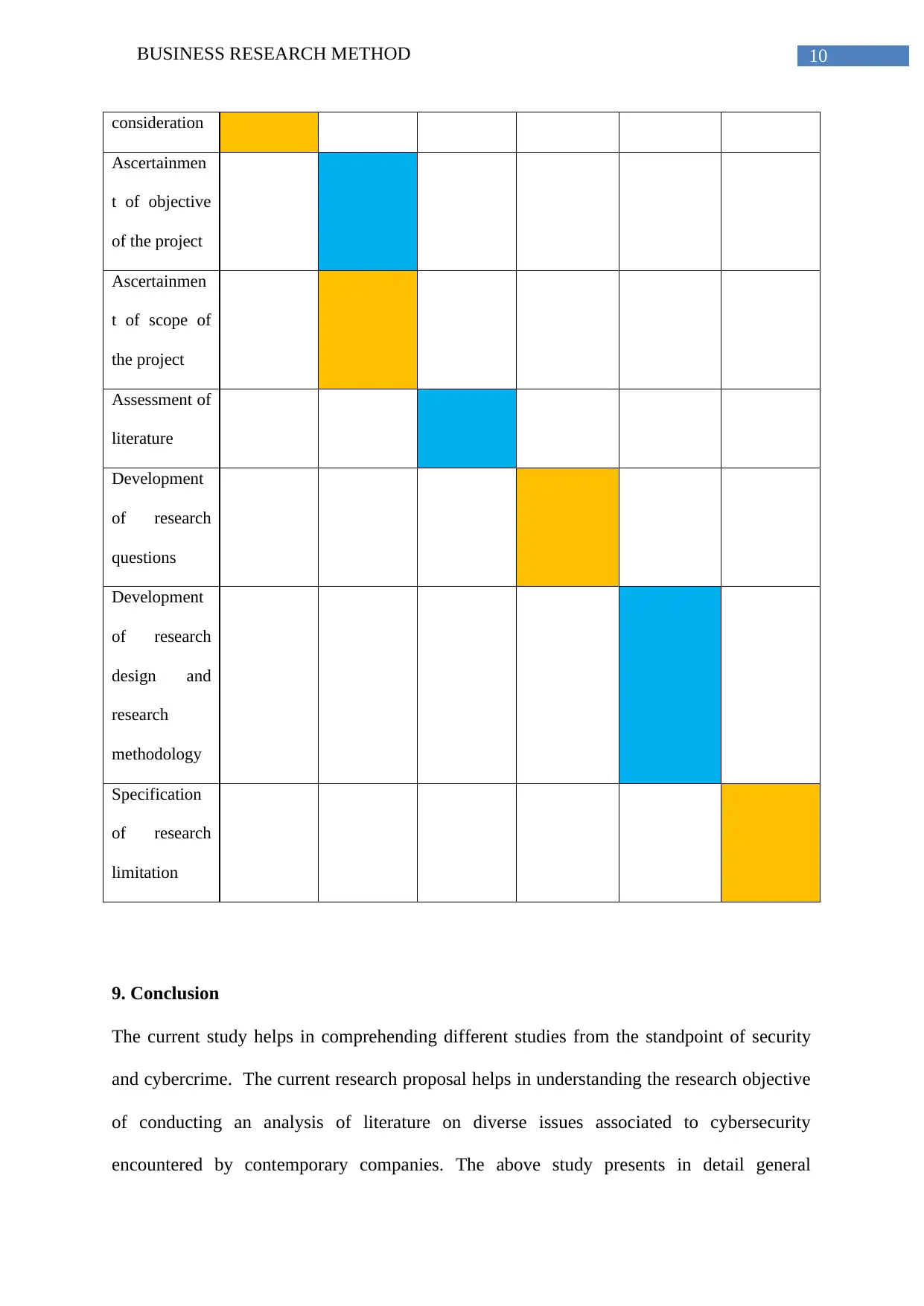
consideration
Ascertainmen
t of objective
of the project
Ascertainmen
t of scope of
the project
Assessment of
literature
Development
of research
questions
Development
of research
design and
research
methodology
Specification
of research
limitation
9. Conclusion
The current study helps in comprehending different studies from the standpoint of security
and cybercrime. The current research proposal helps in understanding the research objective
of conducting an analysis of literature on diverse issues associated to cybersecurity
encountered by contemporary companies. The above study presents in detail general
consideration
Ascertainmen
t of objective
of the project
Ascertainmen
t of scope of
the project
Assessment of
literature
Development
of research
questions
Development
of research
design and
research
methodology
Specification
of research
limitation
9. Conclusion
The current study helps in comprehending different studies from the standpoint of security
and cybercrime. The current research proposal helps in understanding the research objective
of conducting an analysis of literature on diverse issues associated to cybersecurity
encountered by contemporary companies. The above study presents in detail general
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11BUSINESS RESEARCH METHOD
suggestions regarding the way to secure the system the way any kind of authenticated
protocol can be used to defend the system intrinsically.
suggestions regarding the way to secure the system the way any kind of authenticated
protocol can be used to defend the system intrinsically.

12BUSINESS RESEARCH METHOD
10. References
Bogdan, P., 2015, March. A cyber-physical systems approach to personalized medicine:
challenges and opportunities for noc-based multicore platforms. In Proceedings of the 2015
Design, Automation & Test in Europe Conference & Exhibition(pp. 253-258). EDA
Consortium.
Broy, M. and Schmidt, A., 2014. Challenges in engineering cyber-physical
systems. Computer, 47(2), pp.70-72.
Elmaghraby, A.S. and Losavio, M.M., 2014. Cyber security challenges in Smart Cities:
Safety, security and privacy. Journal of advanced research, 5(4), pp.491-497.
Harel, Y., Gal, I.B. and Elovici, Y., 2017. Cyber Security and the Role of Intelligent Systems
in Addressing its Challenges. ACM Transactions on Intelligent Systems and Technology
(TIST), 8(4), p.49.
Johnson, T.A. ed., 2015. Cybersecurity: Protecting critical infrastructures from cyber attack
and cyber warfare. CRC Press.
Mangharam, R., Abbas, H., Behl, M., Jang, K., Pajic, M. and Jiang, Z., 2016, January. Three
challenges in cyber-physical systems. In Communication Systems and Networks
(COMSNETS), 2016 8th International Conference on (pp. 1-8). IEEE.
Massey, D., 2017, November. Applying Cybersecurity Challenges to Medical and Vehicular
Cyber Physical Systems. In Proceedings of the 2017 Workshop on Automated Decision
Making for Active Cyber Defense (pp. 39-39). ACM.
Mishna, F., Bogo, M. and Sawyer, J.L., 2015. Cyber counseling: Illuminating benefits and
challenges. Clinical Social Work Journal, 43(2), pp.169-178.
10. References
Bogdan, P., 2015, March. A cyber-physical systems approach to personalized medicine:
challenges and opportunities for noc-based multicore platforms. In Proceedings of the 2015
Design, Automation & Test in Europe Conference & Exhibition(pp. 253-258). EDA
Consortium.
Broy, M. and Schmidt, A., 2014. Challenges in engineering cyber-physical
systems. Computer, 47(2), pp.70-72.
Elmaghraby, A.S. and Losavio, M.M., 2014. Cyber security challenges in Smart Cities:
Safety, security and privacy. Journal of advanced research, 5(4), pp.491-497.
Harel, Y., Gal, I.B. and Elovici, Y., 2017. Cyber Security and the Role of Intelligent Systems
in Addressing its Challenges. ACM Transactions on Intelligent Systems and Technology
(TIST), 8(4), p.49.
Johnson, T.A. ed., 2015. Cybersecurity: Protecting critical infrastructures from cyber attack
and cyber warfare. CRC Press.
Mangharam, R., Abbas, H., Behl, M., Jang, K., Pajic, M. and Jiang, Z., 2016, January. Three
challenges in cyber-physical systems. In Communication Systems and Networks
(COMSNETS), 2016 8th International Conference on (pp. 1-8). IEEE.
Massey, D., 2017, November. Applying Cybersecurity Challenges to Medical and Vehicular
Cyber Physical Systems. In Proceedings of the 2017 Workshop on Automated Decision
Making for Active Cyber Defense (pp. 39-39). ACM.
Mishna, F., Bogo, M. and Sawyer, J.L., 2015. Cyber counseling: Illuminating benefits and
challenges. Clinical Social Work Journal, 43(2), pp.169-178.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





