Cybersecurity in Business: Framework for Critical Infrastructure
VerifiedAdded on 2023/04/19
|15
|3052
|490
Report
AI Summary
This report provides an overview of cybersecurity in the context of business, highlighting the increasing risks associated with online transactions and data storage. It discusses previous approaches to cybersecurity, including risk identification, analysis, and evaluation, as well as the implementation of protective measures. The report also covers various types of cybercrimes, such as cyber stalking, intellectual property theft, salami attacks, email bombing, phishing, spoofing, and DoS/DDoS attacks. Furthermore, it presents new findings and recommendations for managing cyber risks, including investing in technology, developing response and recovery plans, fostering a culture of security, and implementing user access controls. The conclusion emphasizes the importance of cybersecurity in safeguarding business assets and maintaining operational integrity. This student-created assignment is available on Desklib, a platform offering a wide range of study tools and resources.

Running head: CYBERSECURITY IN BUSINESS
Cybersecurity in Business
Name of the Student
Name of the University
Author Note:
Cybersecurity in Business
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBERSECURITY IN BUSINESS
Executive Summary
In the last few years, there has been rapid development along with innovation in various domain
of life. Development has been encountered in various field like mobility, purchase, and
interaction. For carrying out business, there has been increasing growth and productivity. Apart
from this, it has intended to bring huge amount of exposure to associated risk. Different business
around the globe makes use of internet for both online transmission and transaction on regular
basis. By the amount of provided online data, business can easily expose themselves to
increasing the number of cyber theft. In addition, business can easily encounter online attacks
and data breaches. Any kind of data loss in business can result in disclosing of consumer data
and revealing out customer information. In news media, there has been large number of reports
related to data breach of big corporations.
Executive Summary
In the last few years, there has been rapid development along with innovation in various domain
of life. Development has been encountered in various field like mobility, purchase, and
interaction. For carrying out business, there has been increasing growth and productivity. Apart
from this, it has intended to bring huge amount of exposure to associated risk. Different business
around the globe makes use of internet for both online transmission and transaction on regular
basis. By the amount of provided online data, business can easily expose themselves to
increasing the number of cyber theft. In addition, business can easily encounter online attacks
and data breaches. Any kind of data loss in business can result in disclosing of consumer data
and revealing out customer information. In news media, there has been large number of reports
related to data breach of big corporations.

2CYBERSECURITY IN BUSINESS
Table of Contents
Introduction..........................................................................................................................3
Previous Approach...............................................................................................................3
New Findings.......................................................................................................................6
Conclusion...........................................................................................................................8
References............................................................................................................................9
Table of Contents
Introduction..........................................................................................................................3
Previous Approach...............................................................................................................3
New Findings.......................................................................................................................6
Conclusion...........................................................................................................................8
References............................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBERSECURITY IN BUSINESS
Introduction
With the passage of time, there has been technological innovation in various aspects of
life. There is an advancement in various aspect like social media, cloud computing and lastly
mobility has changed the way of interacting with people (Weinstein, 2016). For some large
organization, this particular trend will ultimately result in growth and productivity. In the last
few years, Cybercrime is on huge rise that is at an epidemic level, it has ultimately resulted much
greater impact on both small and medium size business. As per the news media, the details of
data breach for big corporation that is SBMs are also at high risk (Bell, 2017). Various
cybercriminals around the globe have assumed the fact that smaller business does not have
required resources. Also, the big organization does not have expertise for defending itself. There
has been continuous development in the domain of cyber attacks like ransomware and others
(Sharma, 2015). It is all about targeting SBMs so that malware is transmitted by emails and
freezing until and unless the ransomware is paid.
In the coming pages of the white paper, an approach has been provided for building a
proper cybersecurity plan for any organization. The provided recommendation is totally based
framework for building critical infrastructure cybersecurity. Apart from this, previous approach
and new findings in the paper has also been discussed in brief.
Previous Approach
Cyberspace can be stated as a virtual place which makes use of both electronics and
electromagnetic spectrum for both storing and modifying information (Jacobs, von Solms &
Grobler, 2016). Cyberspace can be arbitrary space which comprises of objects that neither exits
or represent the present world. It is totally a virtual platform where all the required information
Introduction
With the passage of time, there has been technological innovation in various aspects of
life. There is an advancement in various aspect like social media, cloud computing and lastly
mobility has changed the way of interacting with people (Weinstein, 2016). For some large
organization, this particular trend will ultimately result in growth and productivity. In the last
few years, Cybercrime is on huge rise that is at an epidemic level, it has ultimately resulted much
greater impact on both small and medium size business. As per the news media, the details of
data breach for big corporation that is SBMs are also at high risk (Bell, 2017). Various
cybercriminals around the globe have assumed the fact that smaller business does not have
required resources. Also, the big organization does not have expertise for defending itself. There
has been continuous development in the domain of cyber attacks like ransomware and others
(Sharma, 2015). It is all about targeting SBMs so that malware is transmitted by emails and
freezing until and unless the ransomware is paid.
In the coming pages of the white paper, an approach has been provided for building a
proper cybersecurity plan for any organization. The provided recommendation is totally based
framework for building critical infrastructure cybersecurity. Apart from this, previous approach
and new findings in the paper has also been discussed in brief.
Previous Approach
Cyberspace can be stated as a virtual place which makes use of both electronics and
electromagnetic spectrum for both storing and modifying information (Jacobs, von Solms &
Grobler, 2016). Cyberspace can be arbitrary space which comprises of objects that neither exits
or represent the present world. It is totally a virtual platform where all the required information
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBERSECURITY IN BUSINESS
can be exchanged. All the required information can be exchanged and connection can be
established among 2.7 billion number of people. It is a common platform which is needed for
sharing, viewing. Apart from this, it focuses expanding in borderless way along with growing in
sharply way without any kind of consideration (Tisdale, 2015). The first step which is involved
in developing a cybersecurity is all about identifying, analyzing and lastly evaluation of risk.
There are large number of risks in cyberspace due to digital data, which if exploited can easily
result in negative impact on organization well-being (Barbour, 2017). The following step is all
about putting all the required details through protection and recovery. The second thing is all
about upgrading all the new kind of technology that can reduce huge amount of risk in business
(Tisdale, 2015). There is large number of recommendations for a business which is considered to
be very much easy for any organization to adopt. Both the software that is Microsoft Windows
10 and office 365 is considered to be an affordable solution for any business. It is mainly
inclusive of various kind of security development. The technologies have been mainly designed
in such a way that it can protect the identities of user and blocking malicious software.
The last thing which should be taken into account is that people can understand cyber-
attack (Shields, 2015). A list of preventive measures will be discussed in the coming pages of the
white paper. It will ultimately help in reducing cyber-risk in the business. A proper building and
recovery plan have been discussed considering cyber-insurance coverage. Cybercrimes focus on
some sort of critical activities like internet, system or another kind of inter-connected
infrastructure (Schreider & Noakes-Fry, 2017). The term cybercrime is mainly inclusive of
various things like fraud, cyber terrorism, and distribution of viruses.
can be exchanged. All the required information can be exchanged and connection can be
established among 2.7 billion number of people. It is a common platform which is needed for
sharing, viewing. Apart from this, it focuses expanding in borderless way along with growing in
sharply way without any kind of consideration (Tisdale, 2015). The first step which is involved
in developing a cybersecurity is all about identifying, analyzing and lastly evaluation of risk.
There are large number of risks in cyberspace due to digital data, which if exploited can easily
result in negative impact on organization well-being (Barbour, 2017). The following step is all
about putting all the required details through protection and recovery. The second thing is all
about upgrading all the new kind of technology that can reduce huge amount of risk in business
(Tisdale, 2015). There is large number of recommendations for a business which is considered to
be very much easy for any organization to adopt. Both the software that is Microsoft Windows
10 and office 365 is considered to be an affordable solution for any business. It is mainly
inclusive of various kind of security development. The technologies have been mainly designed
in such a way that it can protect the identities of user and blocking malicious software.
The last thing which should be taken into account is that people can understand cyber-
attack (Shields, 2015). A list of preventive measures will be discussed in the coming pages of the
white paper. It will ultimately help in reducing cyber-risk in the business. A proper building and
recovery plan have been discussed considering cyber-insurance coverage. Cybercrimes focus on
some sort of critical activities like internet, system or another kind of inter-connected
infrastructure (Schreider & Noakes-Fry, 2017). The term cybercrime is mainly inclusive of
various things like fraud, cyber terrorism, and distribution of viruses.
5CYBERSECURITY IN BUSINESS
Cyber Stalking: It can be stated as an act which focuses on any kind of intruding into the
Personal life (Choejey, Murray & Fung, 2016). It can easily result in various kind of things like
anxiety and lastly fear. Cyberstalker makes use of benefits of internet that allow them to continue
their activities without being noticed. An intrusion is only possible on individual life in friend
circle or even sending fake letters and emails to target person (Gcaza & Von Solms, 2017).
Cyber stacking many times result in harasses of person which is also referred to as physiological
terrorism.
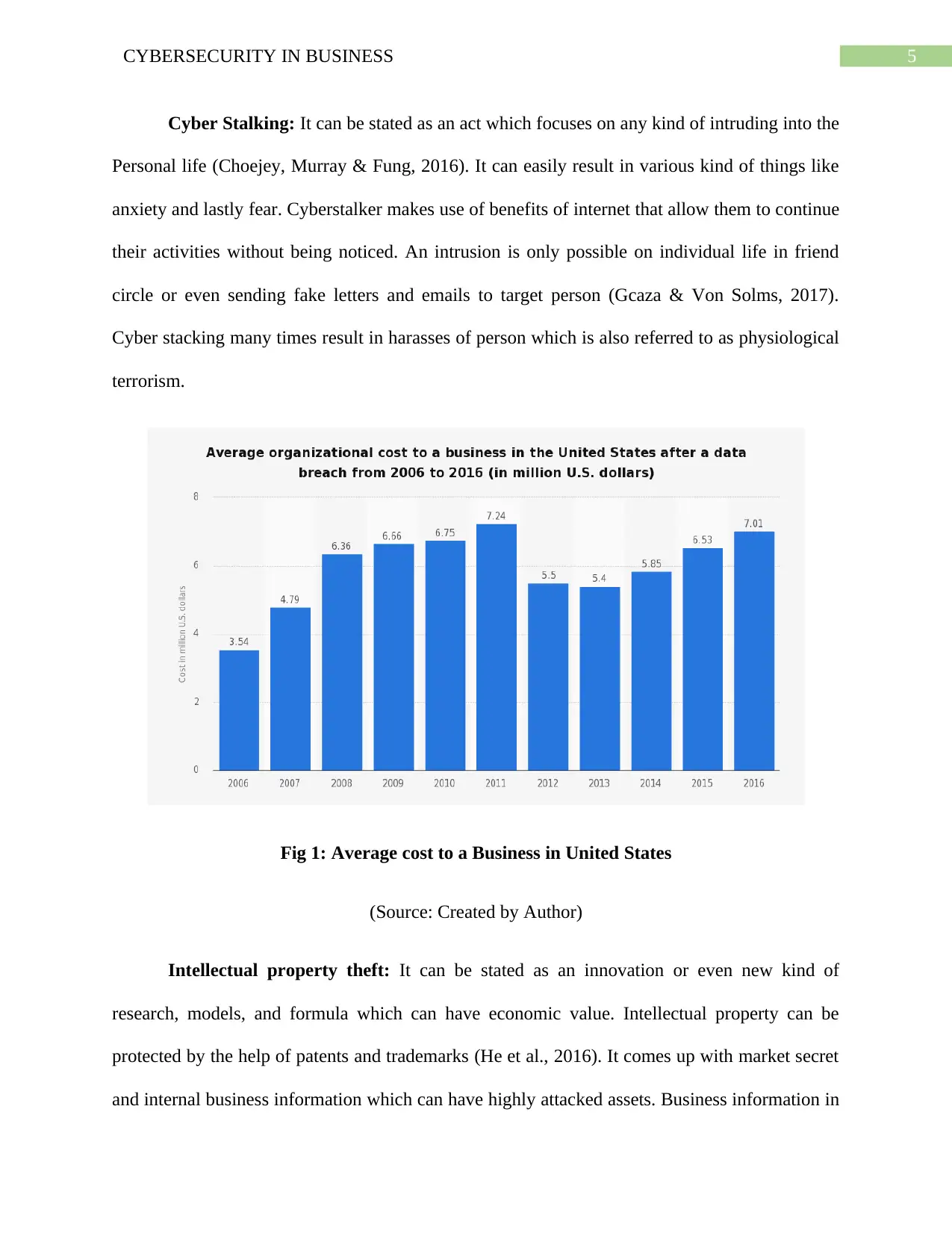
Fig 1: Average cost to a Business in United States
(Source: Created by Author)
Intellectual property theft: It can be stated as an innovation or even new kind of
research, models, and formula which can have economic value. Intellectual property can be
protected by the help of patents and trademarks (He et al., 2016). It comes up with market secret
and internal business information which can have highly attacked assets. Business information in
Cyber Stalking: It can be stated as an act which focuses on any kind of intruding into the
Personal life (Choejey, Murray & Fung, 2016). It can easily result in various kind of things like
anxiety and lastly fear. Cyberstalker makes use of benefits of internet that allow them to continue
their activities without being noticed. An intrusion is only possible on individual life in friend
circle or even sending fake letters and emails to target person (Gcaza & Von Solms, 2017).
Cyber stacking many times result in harasses of person which is also referred to as physiological
terrorism.
Fig 1: Average cost to a Business in United States
(Source: Created by Author)
Intellectual property theft: It can be stated as an innovation or even new kind of
research, models, and formula which can have economic value. Intellectual property can be
protected by the help of patents and trademarks (He et al., 2016). It comes up with market secret
and internal business information which can have highly attacked assets. Business information in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBERSECURITY IN BUSINESS
different forms like future product design and customer names and price list are discussed in
details. Intellectual theft of property can easily result in identifying various kind of network.
Salami Attack: In this attack, both attackers and criminals can easily steal money in very
little amount from different bank accounts for making huge money (Kshetri, 2015). The changes
can become significant that it can be tough to notice.
E-mail bombing: It is all about transmitting huge amount of emails to the target persons.
A very huge amount of e-mails can easily result in fill up of recipient box on the given server. In
some cases, the server can fail to receive huge amount of data and stopping function (Pena,
Ingram & Martin, 2017). There are many ways by email bomb can is able to send to large
number of people. E-mail is bombing and e-mail flooding can easily result in interchangeability
(Pena, Ingram & Martin, 2017). The fact can be stated that e-mail bombing can easily fill up
large number of desired emails and target persons.
different forms like future product design and customer names and price list are discussed in
details. Intellectual theft of property can easily result in identifying various kind of network.
Salami Attack: In this attack, both attackers and criminals can easily steal money in very
little amount from different bank accounts for making huge money (Kshetri, 2015). The changes
can become significant that it can be tough to notice.
E-mail bombing: It is all about transmitting huge amount of emails to the target persons.
A very huge amount of e-mails can easily result in fill up of recipient box on the given server. In
some cases, the server can fail to receive huge amount of data and stopping function (Pena,
Ingram & Martin, 2017). There are many ways by email bomb can is able to send to large
number of people. E-mail is bombing and e-mail flooding can easily result in interchangeability
(Pena, Ingram & Martin, 2017). The fact can be stated that e-mail bombing can easily fill up
large number of desired emails and target persons.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CYBERSECURITY IN BUSINESS
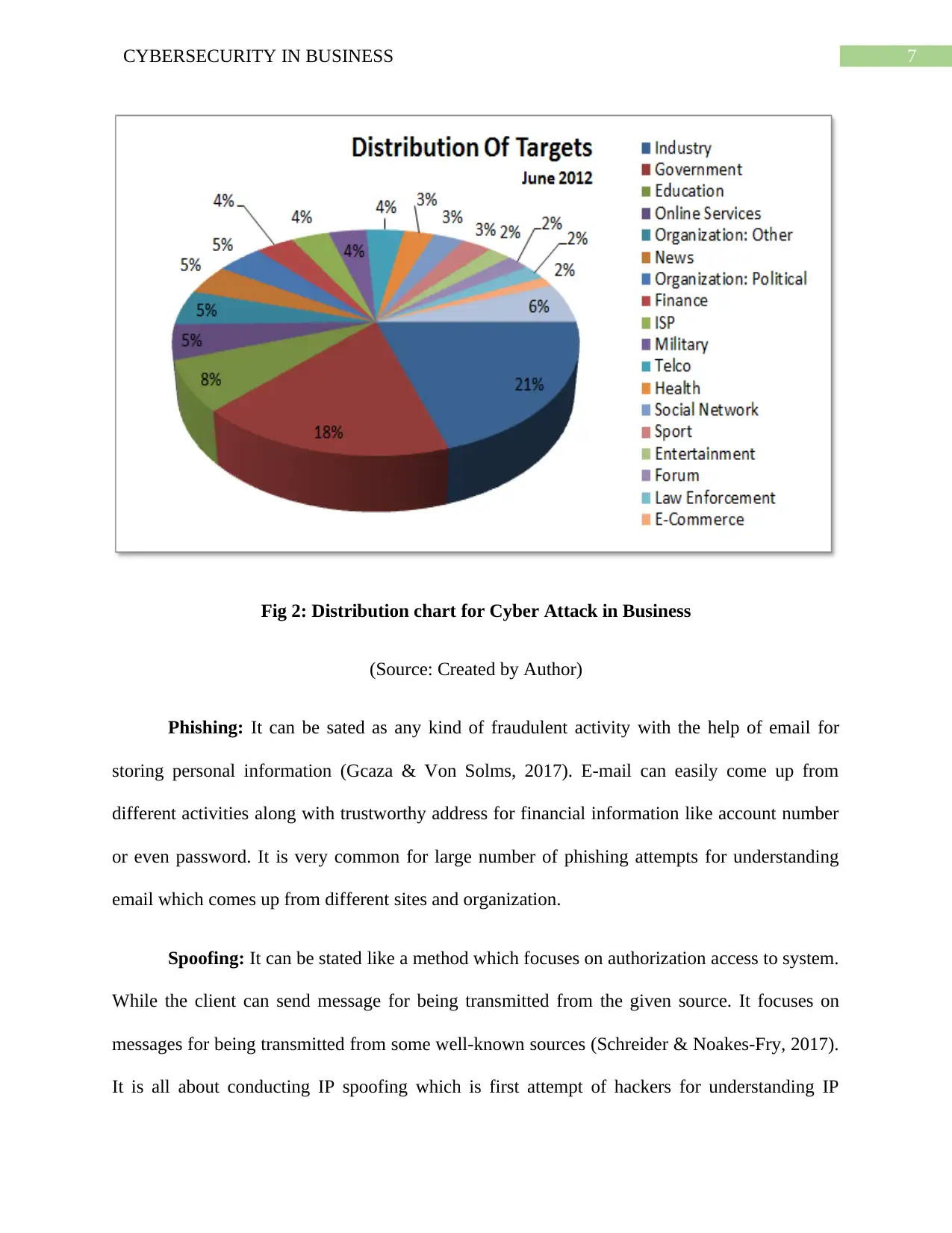
Fig 2: Distribution chart for Cyber Attack in Business
(Source: Created by Author)
Phishing: It can be sated as any kind of fraudulent activity with the help of email for
storing personal information (Gcaza & Von Solms, 2017). E-mail can easily come up from
different activities along with trustworthy address for financial information like account number
or even password. It is very common for large number of phishing attempts for understanding
email which comes up from different sites and organization.
Spoofing: It can be stated like a method which focuses on authorization access to system.
While the client can send message for being transmitted from the given source. It focuses on
messages for being transmitted from some well-known sources (Schreider & Noakes-Fry, 2017).
It is all about conducting IP spoofing which is first attempt of hackers for understanding IP
Fig 2: Distribution chart for Cyber Attack in Business
(Source: Created by Author)
Phishing: It can be sated as any kind of fraudulent activity with the help of email for
storing personal information (Gcaza & Von Solms, 2017). E-mail can easily come up from
different activities along with trustworthy address for financial information like account number
or even password. It is very common for large number of phishing attempts for understanding
email which comes up from different sites and organization.
Spoofing: It can be stated like a method which focuses on authorization access to system.
While the client can send message for being transmitted from the given source. It focuses on
messages for being transmitted from some well-known sources (Schreider & Noakes-Fry, 2017).
It is all about conducting IP spoofing which is first attempt of hackers for understanding IP
8CYBERSECURITY IN BUSINESS
addresses. It helps in modification and alteration of provided packets which is generated from
host.
DoS and DDoS: A denial of service attack can be stated like an attempt for making
computers, server and network resources which is available to him (Barbour, 2017). A
distributed denial service is also referring to a DoS attack which propagates from more than one
system with various software at the same instance.
Year Cases or crimes registered
under IT Act
Person Arrested
2010 966 800
2011 1791 1200
2012 2876 1536
2013 4356 2000
Table 1: Cyber Crime growth in worldwide platform
New Findings
There are large number ways of managing cyber risk in business like
Although perfect cyber security system does not exist there is large number of practices
which can be followed for tackling cyber-security issues. There is new combination of
affordable technology, cyber-security coverages (Sharma, 2015). It can be defined as a
proper coverage and education which help the business owners in easily protecting them
addresses. It helps in modification and alteration of provided packets which is generated from
host.
DoS and DDoS: A denial of service attack can be stated like an attempt for making
computers, server and network resources which is available to him (Barbour, 2017). A
distributed denial service is also referring to a DoS attack which propagates from more than one
system with various software at the same instance.
Year Cases or crimes registered
under IT Act
Person Arrested
2010 966 800
2011 1791 1200
2012 2876 1536
2013 4356 2000
Table 1: Cyber Crime growth in worldwide platform
New Findings
There are large number ways of managing cyber risk in business like
Although perfect cyber security system does not exist there is large number of practices
which can be followed for tackling cyber-security issues. There is new combination of
affordable technology, cyber-security coverages (Sharma, 2015). It can be defined as a
proper coverage and education which help the business owners in easily protecting them
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBERSECURITY IN BUSINESS
any kind of interruption in business. It also focuses on proper education which enables
business owners for protection of business against kind of manipulation. The same kind
of measure can easily help in mitigating various kind of risk in business (Kshetri, 2015).
It is associated with natural disaster and another kind of failures in IT.
The present business needs to safeguard with latest technology. By the help of investment
in time and money, a much greater part of cyber risk can be easily avoided (Weinstein,
2016). The present-day software application and system can easily build security like
encryption and access control for much better business data.
The third step which can be easily taken by business is development of response and
recovery plan. The present kind of cyber-security plans can easily provide proper
response and recovery solution at the time of data breach (Bell, 2017). Cyber- insurance
is not all about covering the involved cost as a result of cybercrime. There is large
number of policies which can be helpful in connecting network of service providers for
help with requirements for notification (He et al., 2016). It can easily focus on addressing
restoration efforts, both first- and third-party efforts and even loss in income.
The fourth stage is all about developing culture of security. Cybersecurity breaches can
be avoided by the implementation of simple control and best practices of security
(Jacobs, von Solms & Grobler, 2016). A proper security practice needs to be developed
along with new and strong password which can violate the cybersecurity policies. Along
with this, there are certain rules to handle and protect customer information and another
kind of data.
Both storing and backup of important of digital data are considered to be important.
Business can lose dollars and hours for restoration of lost data (Tisdale, 2015). Data
any kind of interruption in business. It also focuses on proper education which enables
business owners for protection of business against kind of manipulation. The same kind
of measure can easily help in mitigating various kind of risk in business (Kshetri, 2015).
It is associated with natural disaster and another kind of failures in IT.
The present business needs to safeguard with latest technology. By the help of investment
in time and money, a much greater part of cyber risk can be easily avoided (Weinstein,
2016). The present-day software application and system can easily build security like
encryption and access control for much better business data.
The third step which can be easily taken by business is development of response and
recovery plan. The present kind of cyber-security plans can easily provide proper
response and recovery solution at the time of data breach (Bell, 2017). Cyber- insurance
is not all about covering the involved cost as a result of cybercrime. There is large
number of policies which can be helpful in connecting network of service providers for
help with requirements for notification (He et al., 2016). It can easily focus on addressing
restoration efforts, both first- and third-party efforts and even loss in income.
The fourth stage is all about developing culture of security. Cybersecurity breaches can
be avoided by the implementation of simple control and best practices of security
(Jacobs, von Solms & Grobler, 2016). A proper security practice needs to be developed
along with new and strong password which can violate the cybersecurity policies. Along
with this, there are certain rules to handle and protect customer information and another
kind of data.
Both storing and backup of important of digital data are considered to be important.
Business can lose dollars and hours for restoration of lost data (Tisdale, 2015). Data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBERSECURITY IN BUSINESS
storage consideration is mainly inclusive of security, compliance, and privacy. Based on
the industry, one needs different kind of admins and user control like legal hold and
prevention of data loss. It will ultimately help them in satisfying the given requirements
(Choejey, Murray & Fung, 2016). If a business manages on the own, then it requires to
have experts for suggestion. Both cloud-based storage and backup solution then the
enterprise can easily result in class security and privacy controls. It will become a bit cost
effective for business.
Business needs to have an access to user access control. Business needs to connect
employees to require data at the time of requirement (Yates et al., 2018). There is large
number of challenges which help them to be predictive. It focuses on maintaining some
of the critical business data. It is all about restriction on the access to data depending on
business requirements.
There should be proper access to large number of devices and data which is needed for
authentication (Shields, 2015). It is mainly used for managing rules of business and
permission for access. Any kind of weakness can easily in authentication easily result in
security infraction or inappropriate access.
Conclusion
From the above pages of the white paper, an idea has been provided with respect to
cyberspace. It aims in defining cybersecurity along with requirements in various stages of the
world. The white paper discusses business management along with risk management. It mainly
emphasizes on digitalization of risk management which is considered to be reversible in nature.
With the passage of time, there is a need for continuous management along with connectivity and
collaboration with some old entities. It mainly focuses collaboration with some old entities. The
storage consideration is mainly inclusive of security, compliance, and privacy. Based on
the industry, one needs different kind of admins and user control like legal hold and
prevention of data loss. It will ultimately help them in satisfying the given requirements
(Choejey, Murray & Fung, 2016). If a business manages on the own, then it requires to
have experts for suggestion. Both cloud-based storage and backup solution then the
enterprise can easily result in class security and privacy controls. It will become a bit cost
effective for business.
Business needs to have an access to user access control. Business needs to connect
employees to require data at the time of requirement (Yates et al., 2018). There is large
number of challenges which help them to be predictive. It focuses on maintaining some
of the critical business data. It is all about restriction on the access to data depending on
business requirements.
There should be proper access to large number of devices and data which is needed for
authentication (Shields, 2015). It is mainly used for managing rules of business and
permission for access. Any kind of weakness can easily in authentication easily result in
security infraction or inappropriate access.
Conclusion
From the above pages of the white paper, an idea has been provided with respect to
cyberspace. It aims in defining cybersecurity along with requirements in various stages of the
world. The white paper discusses business management along with risk management. It mainly
emphasizes on digitalization of risk management which is considered to be reversible in nature.
With the passage of time, there is a need for continuous management along with connectivity and
collaboration with some old entities. It mainly focuses collaboration with some old entities. The

11CYBERSECURITY IN BUSINESS
whole idea of cybersecurity can easily provide threat to business management. Digital risk
management is considered like root in every business. In some cases, the executives of a
business are well aware of cybersecurity in business. The major portion is nothing more than the
necessary cost in the business. The potential add-on value is mainly created by the help of
economic digitalization. In the present environment, Cyber-space is considered to be high
populated environment which is considered to be used in both vulnerable and unprotected
devices. It can easily become infected due to malware.
whole idea of cybersecurity can easily provide threat to business management. Digital risk
management is considered like root in every business. In some cases, the executives of a
business are well aware of cybersecurity in business. The major portion is nothing more than the
necessary cost in the business. The potential add-on value is mainly created by the help of
economic digitalization. In the present environment, Cyber-space is considered to be high
populated environment which is considered to be used in both vulnerable and unprotected
devices. It can easily become infected due to malware.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





