Data Security, Privacy, and Online Threats: A Research Report
VerifiedAdded on 2023/06/06
|12
|427
|237
Report
AI Summary
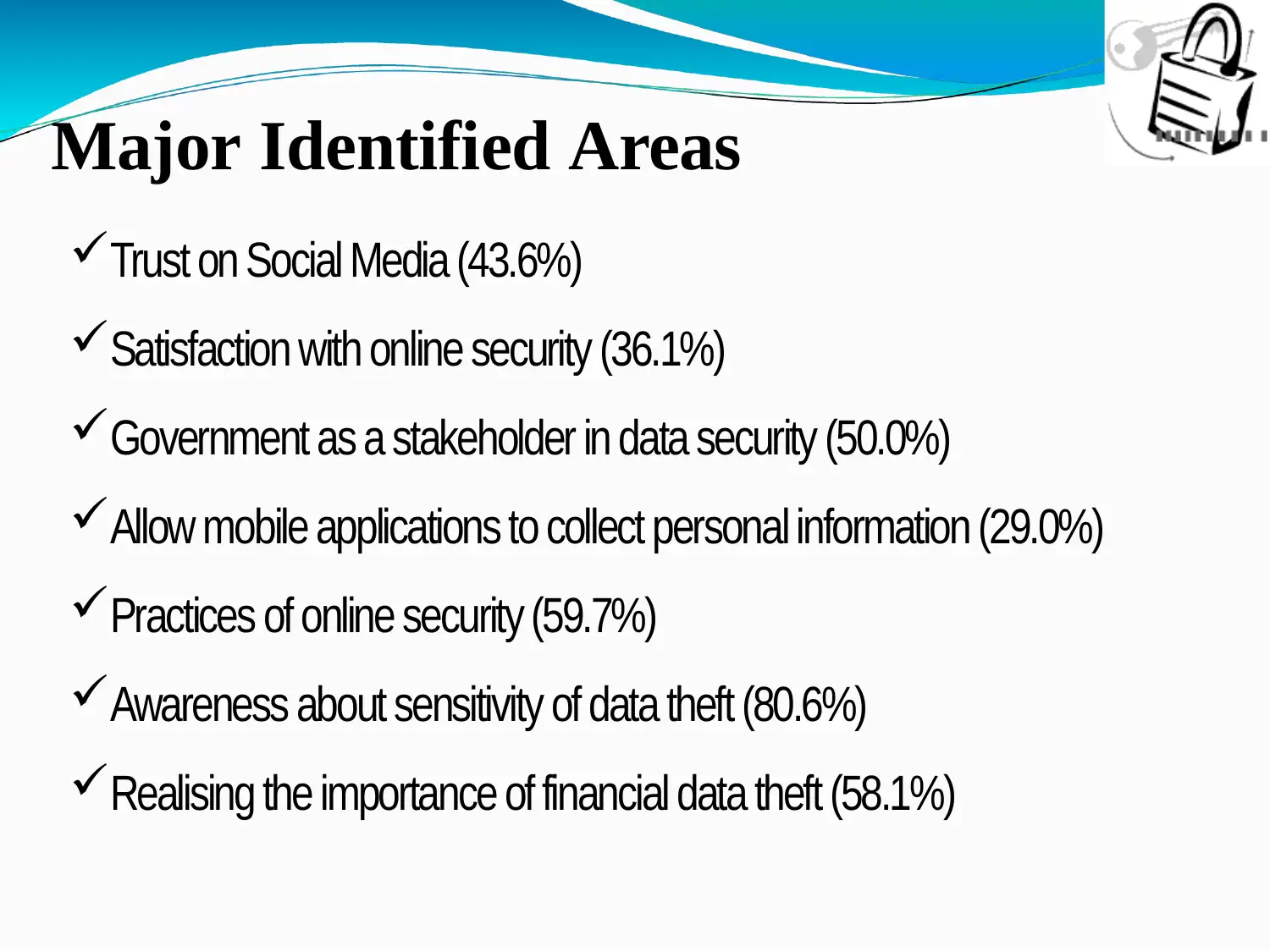
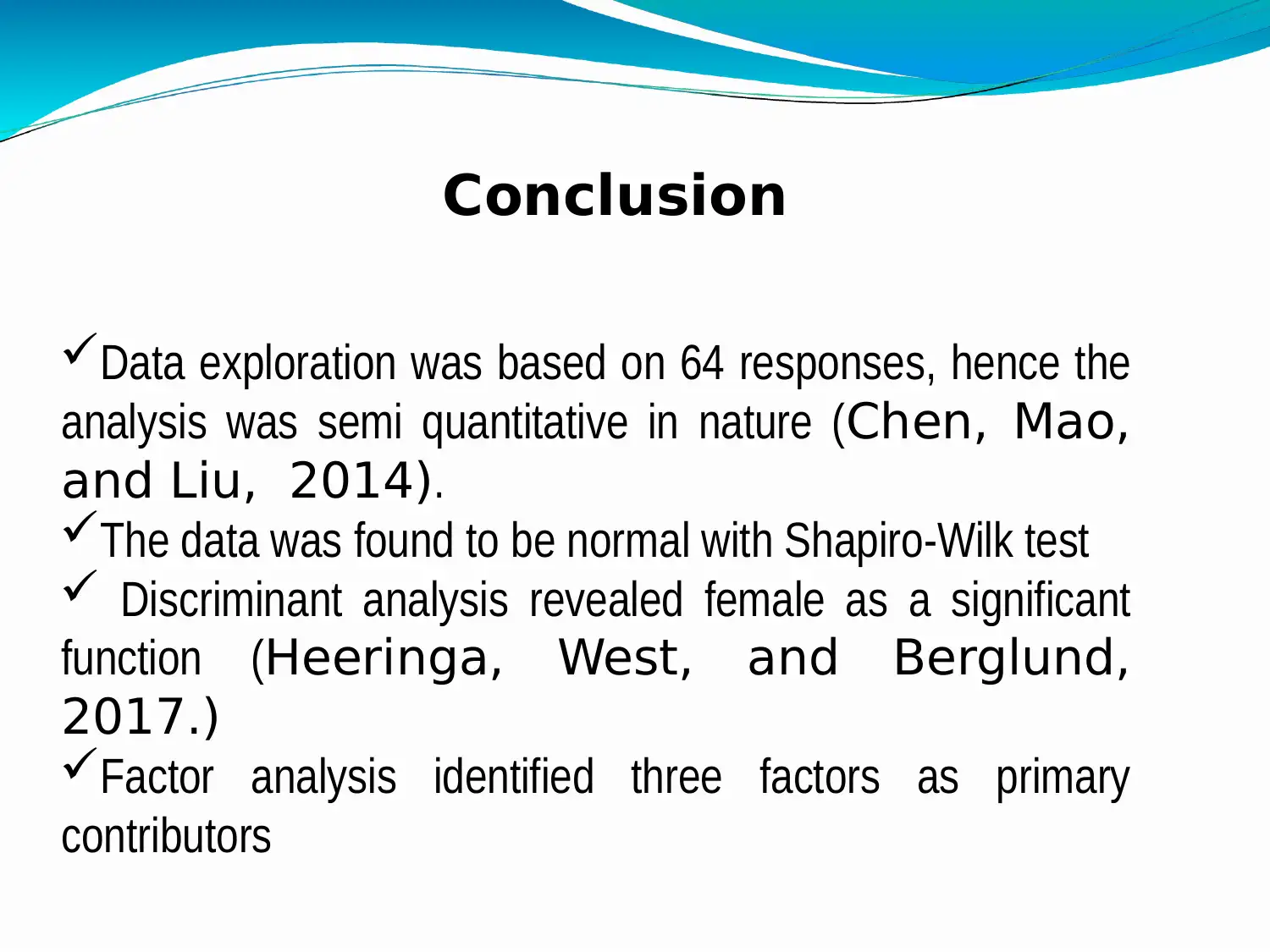
This report presents a research analysis on cybersecurity and data protection, focusing on online threats and the importance of data privacy. The study involved a survey of 64 respondents, exploring their perceptions of online security, trust in social media, and awareness of data theft. Key findings include insights into the significance of financial data protection, the role of government in data security, and the impact of mobile applications on personal information. The report also outlines practical steps to enhance data security, such as using security shields, regularly updating passwords, and being aware of website security certificates and malware. Statistical analyses, including the Shapiro-Wilk test and discriminant analysis, were employed to interpret the data. The report concludes with a discussion of the limitations and implications of the research, providing a foundation for further exploration in this critical area of digital security.
1 out of 12








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)