Impact of Legal and Political Environment on Cyber Security Functions
VerifiedAdded on 2022/07/27
|13
|965
|14
Report
AI Summary
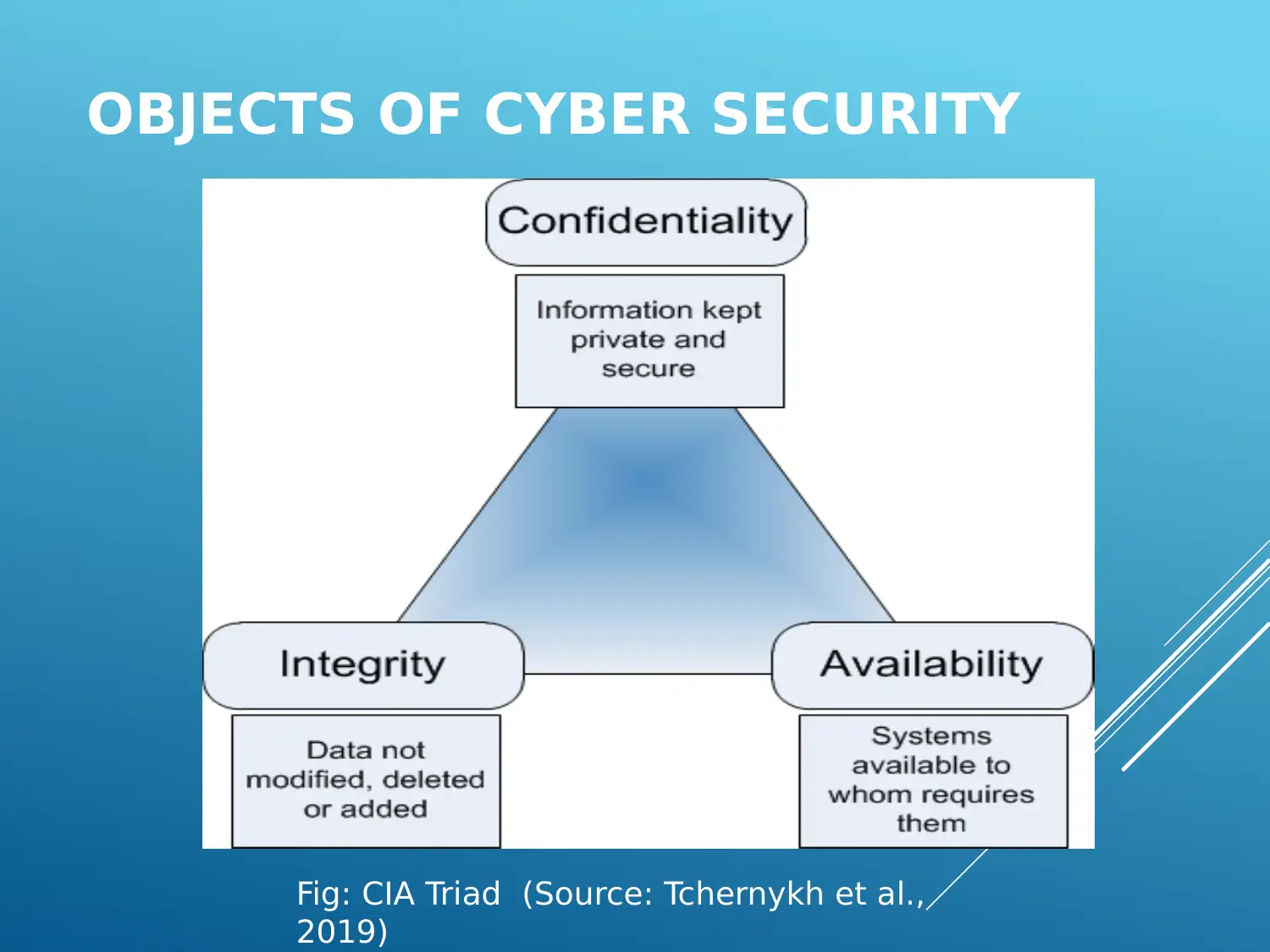
This report delves into the multifaceted realm of cyber security, elucidating its core principles, encompassing the protection of data through technologies, practices, and processes. The report explores the critical importance of cyber security in safeguarding organizations from breaches, protecting sensitive information, and ensuring system integrity. It also examines the crucial 'CIA Triad' of confidentiality, integrity, and availability. The report then transitions to the organizational context, outlining the role of cyber security management tools, risk management strategies, and security awareness programs. It also covers cyber security governance, emphasizing decision-making and accountability, followed by an analysis of the legal and political implications of cyber security on businesses. Key areas include legal policies combating cybercrime and the prioritization of cyber security as a national issue. The report also touches upon the evolution of national cyber security strategies, including policy development and the significance of standards in mitigating risks. The conclusion emphasizes the need for skilled cyber security professionals and the application of appropriate regulations and policies to prevent cyber threats. The report incorporates references to relevant academic sources.
1 out of 13


















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)