Cybersecurity Essay: Cyber Threats in United States Communities
VerifiedAdded on 2022/08/12
|5
|1172
|24
Essay
AI Summary
This essay delves into the realm of cybersecurity, examining the nature of cyber threats and their impact on businesses and communities in the United States. It begins by defining cyber-crime and its increasing prevalence due to the expansion of IT networks. The essay evaluates a scenario involving a ransomware attack, highlighting its potential to cause data breaches. It then explores the concept of insider threats, where employees or internal IT structures contribute to cyber-attacks. The essay contrasts the ransomware scenario with phishing attacks, arguing that phishing is the most likely cyber-attack faced by US communities. It supports this argument by referencing the 2017 phishing attack that compromised data from numerous businesses. The essay concludes by emphasizing the need for companies to address insider threats, provide employee training, and implement robust IT infrastructures, including anti-phishing techniques, to mitigate the risks of cyber-crimes. This essay is available on Desklib, a platform offering AI-based study tools for students.
CYBERSECURITY 0
Cyber Security
Cyber Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBERSECURITY 1
Cyber-security
Cyber-crime is a kind of security threat faced by the business communities where
the criminals transfer larger unwanted signals and produce data breach activities. In this
generation, the use of information technology is growing quickly and many companies are
moving towards IT networks that also lead cyber-attacks and security threats in the
business. The purpose of the essay is to evaluate the concept behind the cyber threat and
evaluate the most likely cyber threat that happened in the United States communities. As
per the given scenario, ransomware is a kind of security attack that has the potential to
gather information from the business communities and produce data breach issues in the
workplace. This essay will evaluate and examine the key reasons that lead to such kinds of
problems in the business communities.
In the given fake scenario, the ransomware is one of the leading cyber-attacks where
the criminals transfer unwanted signals to the main servers and encrypt the private details
of the consumers using malicious codes. If the highlighted scenario could happen in this
real world then it is defined as an insider cyber threat where the employees and internal IT
structures are responsible for cyber-terrorist. According to Von Solms, & Van Niekerk,
(2013) cyber threats are capable to reduce the privacy of data and obtain all sensitive data
of the communities using advanced algorithms. Most of the companies are facing cyber-
crimes due to insider cyber-threat as the employees are not aware of cyber-attacks due to
which they can access unauthorized networks and lose the privacy of data.
In the last five years, more than 56% of the business communities in the United
States were faced by the ransomware attack due to insider attacks where the employees
clicked on the unwanted links transferred by the hackers. After evaluating the provided
case it is found that the hackers transfer fraud and spam signals to the main servers where
the developed IT systems were not able to manage such signals and produced hacking
issues in the workplace. Moreover, the developed email system has become non-
operational for the consumers and internal networks are not capable to identify the fraud
signals from the systems. Therefore, it is reported that insider security threat is a major
reason behind cyber-crimes where the consumers can lose the privacy of data and suffer
from the data breach related issues. However, most of the United States communities are
suffering from the data breach and cyber-crimes related issues due to major three reasons
including lack of awareness, misconfiguration of networks and unauthorized access of the
computing networks.
In my opinion, the highlighted scenario is not the most likely cyber-attack as the
ransomware is an attack that can be done by transferring unwanted signals and obtaining
accessibility of computing devices used by the companies. Such kind of attacks can be
managed easily by using advanced security tools and private networks. From recent
studies, it is found that phishing is the most likely cyber-attack faced by the United States
communities where the criminals transfer spam mails to the employees with the purpose
of hacking and data breach. In the last five years, around 56% of the U.S. communities were
suffered from the phishing attack where the hackers obtained the confidentiality of
thousands of computing devices. Fraud Watch, (2019) supported this argument and
Cyber-security
Cyber-crime is a kind of security threat faced by the business communities where
the criminals transfer larger unwanted signals and produce data breach activities. In this
generation, the use of information technology is growing quickly and many companies are
moving towards IT networks that also lead cyber-attacks and security threats in the
business. The purpose of the essay is to evaluate the concept behind the cyber threat and
evaluate the most likely cyber threat that happened in the United States communities. As
per the given scenario, ransomware is a kind of security attack that has the potential to
gather information from the business communities and produce data breach issues in the
workplace. This essay will evaluate and examine the key reasons that lead to such kinds of
problems in the business communities.
In the given fake scenario, the ransomware is one of the leading cyber-attacks where
the criminals transfer unwanted signals to the main servers and encrypt the private details
of the consumers using malicious codes. If the highlighted scenario could happen in this
real world then it is defined as an insider cyber threat where the employees and internal IT
structures are responsible for cyber-terrorist. According to Von Solms, & Van Niekerk,
(2013) cyber threats are capable to reduce the privacy of data and obtain all sensitive data
of the communities using advanced algorithms. Most of the companies are facing cyber-
crimes due to insider cyber-threat as the employees are not aware of cyber-attacks due to
which they can access unauthorized networks and lose the privacy of data.
In the last five years, more than 56% of the business communities in the United
States were faced by the ransomware attack due to insider attacks where the employees
clicked on the unwanted links transferred by the hackers. After evaluating the provided
case it is found that the hackers transfer fraud and spam signals to the main servers where
the developed IT systems were not able to manage such signals and produced hacking
issues in the workplace. Moreover, the developed email system has become non-
operational for the consumers and internal networks are not capable to identify the fraud
signals from the systems. Therefore, it is reported that insider security threat is a major
reason behind cyber-crimes where the consumers can lose the privacy of data and suffer
from the data breach related issues. However, most of the United States communities are
suffering from the data breach and cyber-crimes related issues due to major three reasons
including lack of awareness, misconfiguration of networks and unauthorized access of the
computing networks.
In my opinion, the highlighted scenario is not the most likely cyber-attack as the
ransomware is an attack that can be done by transferring unwanted signals and obtaining
accessibility of computing devices used by the companies. Such kind of attacks can be
managed easily by using advanced security tools and private networks. From recent
studies, it is found that phishing is the most likely cyber-attack faced by the United States
communities where the criminals transfer spam mails to the employees with the purpose
of hacking and data breach. In the last five years, around 56% of the U.S. communities were
suffered from the phishing attack where the hackers obtained the confidentiality of
thousands of computing devices. Fraud Watch, (2019) supported this argument and
CYBERSECURITY 2
reported that in the case of phishing attack, the criminals transfer fraudulent signals that
appear to come from effective sources and helps to gather login credentials of the
consumer’s devices without taking their permission. It is reported that phishing attacks
would have orchestrated by the cyber-criminals for obtaining sensitive data of the
consumers and misuse gathered information for earning money.
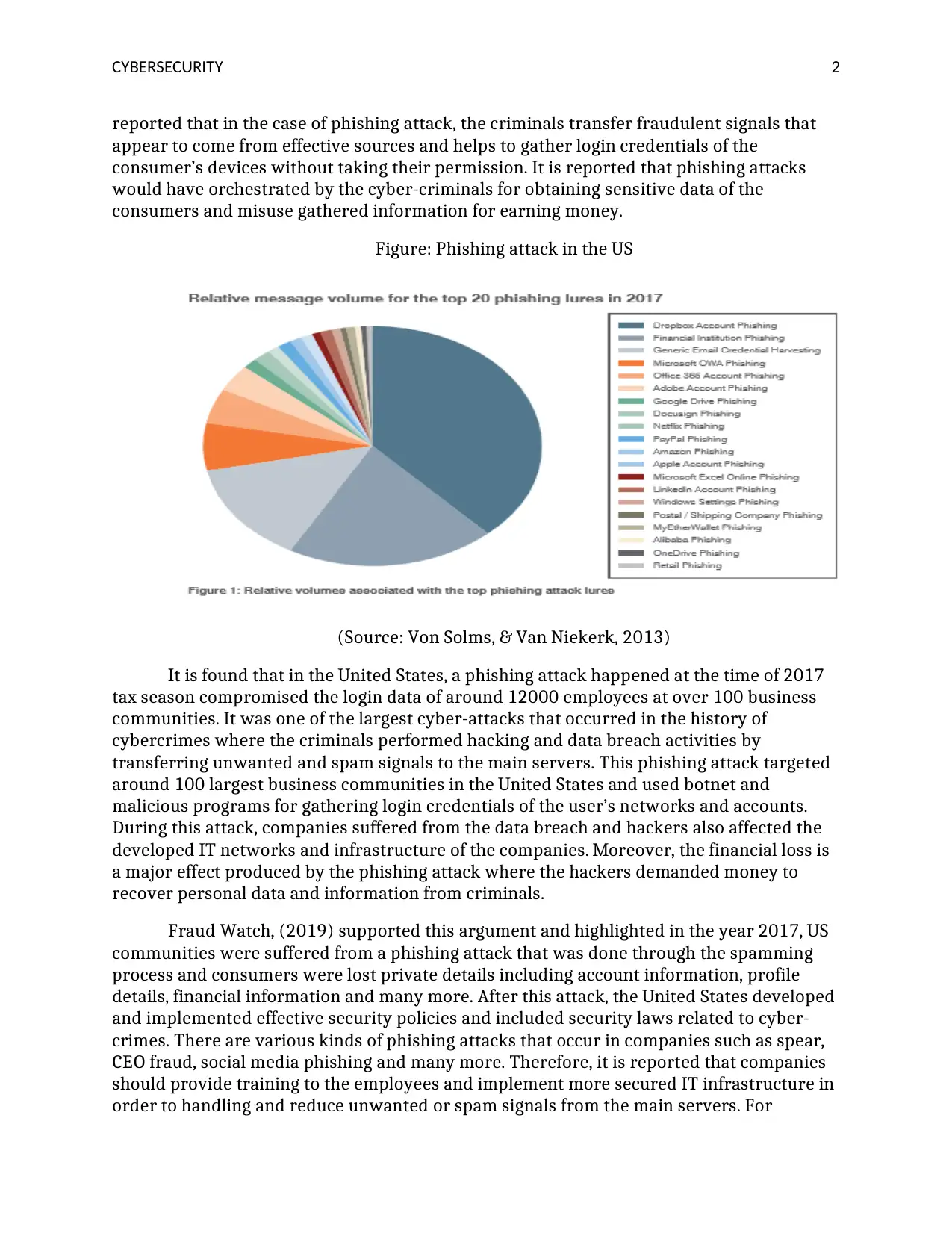
Figure: Phishing attack in the US
(Source: Von Solms, & Van Niekerk, 2013)
It is found that in the United States, a phishing attack happened at the time of 2017
tax season compromised the login data of around 12000 employees at over 100 business
communities. It was one of the largest cyber-attacks that occurred in the history of
cybercrimes where the criminals performed hacking and data breach activities by
transferring unwanted and spam signals to the main servers. This phishing attack targeted
around 100 largest business communities in the United States and used botnet and
malicious programs for gathering login credentials of the user’s networks and accounts.
During this attack, companies suffered from the data breach and hackers also affected the
developed IT networks and infrastructure of the companies. Moreover, the financial loss is
a major effect produced by the phishing attack where the hackers demanded money to
recover personal data and information from criminals.
Fraud Watch, (2019) supported this argument and highlighted in the year 2017, US
communities were suffered from a phishing attack that was done through the spamming
process and consumers were lost private details including account information, profile
details, financial information and many more. After this attack, the United States developed
and implemented effective security policies and included security laws related to cyber-
crimes. There are various kinds of phishing attacks that occur in companies such as spear,
CEO fraud, social media phishing and many more. Therefore, it is reported that companies
should provide training to the employees and implement more secured IT infrastructure in
order to handling and reduce unwanted or spam signals from the main servers. For
reported that in the case of phishing attack, the criminals transfer fraudulent signals that
appear to come from effective sources and helps to gather login credentials of the
consumer’s devices without taking their permission. It is reported that phishing attacks
would have orchestrated by the cyber-criminals for obtaining sensitive data of the
consumers and misuse gathered information for earning money.
Figure: Phishing attack in the US
(Source: Von Solms, & Van Niekerk, 2013)
It is found that in the United States, a phishing attack happened at the time of 2017
tax season compromised the login data of around 12000 employees at over 100 business
communities. It was one of the largest cyber-attacks that occurred in the history of
cybercrimes where the criminals performed hacking and data breach activities by
transferring unwanted and spam signals to the main servers. This phishing attack targeted
around 100 largest business communities in the United States and used botnet and
malicious programs for gathering login credentials of the user’s networks and accounts.
During this attack, companies suffered from the data breach and hackers also affected the
developed IT networks and infrastructure of the companies. Moreover, the financial loss is
a major effect produced by the phishing attack where the hackers demanded money to
recover personal data and information from criminals.
Fraud Watch, (2019) supported this argument and highlighted in the year 2017, US
communities were suffered from a phishing attack that was done through the spamming
process and consumers were lost private details including account information, profile
details, financial information and many more. After this attack, the United States developed
and implemented effective security policies and included security laws related to cyber-
crimes. There are various kinds of phishing attacks that occur in companies such as spear,
CEO fraud, social media phishing and many more. Therefore, it is reported that companies
should provide training to the employees and implement more secured IT infrastructure in
order to handling and reduce unwanted or spam signals from the main servers. For
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBERSECURITY 3
managing such attacks companies can use anti-phishing techniques and aware employees
to access only authentic sources in the computing devices.
It can be concluded that insider cyber-threat is a major reason behind cyber-attacks
where criminals can perform data breach and hacking issues easily. Phishing and
ransomware both are major cyber-attacks but phishing is the most likely cyber-crime that
affected more than 100 business communities in the year 2017 and obtained data of the
consumers effectively. This research essay highlighted and reviewed the impact of cyber-
crimes on the privacy of companies and identified the most likely cyber-attack occurred in
the United States communities. Therefore, it is suggested that companies should focus on
insider attacks and provide complete training to the employees in regard to data
communication and cyber-crimes. Moreover, the involvement of anti-phishing techniques
can help the US communities to manage and enhance the privacy of data by blocking spam
emails from the systems.
managing such attacks companies can use anti-phishing techniques and aware employees
to access only authentic sources in the computing devices.
It can be concluded that insider cyber-threat is a major reason behind cyber-attacks
where criminals can perform data breach and hacking issues easily. Phishing and
ransomware both are major cyber-attacks but phishing is the most likely cyber-crime that
affected more than 100 business communities in the year 2017 and obtained data of the
consumers effectively. This research essay highlighted and reviewed the impact of cyber-
crimes on the privacy of companies and identified the most likely cyber-attack occurred in
the United States communities. Therefore, it is suggested that companies should focus on
insider attacks and provide complete training to the employees in regard to data
communication and cyber-crimes. Moreover, the involvement of anti-phishing techniques
can help the US communities to manage and enhance the privacy of data by blocking spam
emails from the systems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBERSECURITY 4
References
Fraud Watch, (2019). What is a Phishing Attack? Retrieved from:
https://fraudwatchinternational.com/phishing/what-is-a-phishing-attack/
Von Solms, R., & Van Niekerk, J. (2013). From information security to
cybersecurity. computers & security, 38, 97-102.
References
Fraud Watch, (2019). What is a Phishing Attack? Retrieved from:
https://fraudwatchinternational.com/phishing/what-is-a-phishing-attack/
Von Solms, R., & Van Niekerk, J. (2013). From information security to
cybersecurity. computers & security, 38, 97-102.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





