Analysis of Cybersecurity Threats and Organizational Investment
VerifiedAdded on 2023/01/18
|8
|1472
|91
Report
AI Summary
This report investigates the impact of misconceptions about cybersecurity threats on organizational investment. The study employs a qualitative research methodology, including conceptual content analysis of interviews conducted with experts from five Dutch companies. The research question focuses on the reasons behind these misconceptions and their influence on investment decisions. The report analyzes data collected through semi-structured interviews, exploring topics such as employee awareness, the reasons for misconceptions, and the impact of cyber threats. The analysis utilizes NVivo software to identify recurring themes, revealing that cyber security awareness plays a vital role in organizations and influences investment strategies. The findings suggest that organizations should carry out thorough data analysis on cyber threats and promote awareness among employees across different departments, rather than solely relying on the technology department for mitigation.

Running head: CYBER SECURITY THREAT IN ORGANISATION
How misconceptions about cybersecurity threats impact on organizational investment
in cybersecurity?
How misconceptions about cybersecurity threats impact on organizational investment
in cybersecurity?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY THREAT IN ORGANISATION
DATA COLLECTION METHODOLOGY
This chapter highlights the chosen methodological approach and the justification
of the research based on the nature of the research aim. Furthermore, the chapter also raises
some of the methodological analysis, limitations and benefits. The primary aim of the study
was to explore how misconceptions about cybersecurity threats impact on organizational
cybersecurity investments. In this study, 5 Dutch companies were analyzed.
The following analysis is made based on the interview done on each separate
organisation. It is also revealed in the literature review that there has been relatively little
research conducted on misconceptions about cybersecurity threats impact on organization
cybersecurity investments. A majority of existing research are largely dominated by
quantitative approach to research methodology. This study aims to contribute to these under-
researched areas by employing a qualitative research methodology and conceptual content
analysis based on an interpretive research design.
Conceptual content analysis is widely acknowledged to be the most useful tool in
studying organizational cybersecurity issues by establishing the existence and frequency of
concepts most represented by words or phrases in a text. After a thoughtful consideration, the
method of conceptual qualitative content analysis has been chosen to answer the research
question below. While quantitative content analysis aims to make statistical interference of
frequencies from counting of huge data sets, it has been decided that qualitative content
analysis better suits the scope of this project. Especially the idea that qualitative content
analysis offers the opportunity to examine the material on a latent level complements the
research questions. Qualitative methods rather evaluate the underlying argumentation of
material as they go beyond the counting of words. The justification for choosing approach is
highlighted in the following.
DATA COLLECTION METHODOLOGY
This chapter highlights the chosen methodological approach and the justification
of the research based on the nature of the research aim. Furthermore, the chapter also raises
some of the methodological analysis, limitations and benefits. The primary aim of the study
was to explore how misconceptions about cybersecurity threats impact on organizational
cybersecurity investments. In this study, 5 Dutch companies were analyzed.
The following analysis is made based on the interview done on each separate
organisation. It is also revealed in the literature review that there has been relatively little
research conducted on misconceptions about cybersecurity threats impact on organization
cybersecurity investments. A majority of existing research are largely dominated by
quantitative approach to research methodology. This study aims to contribute to these under-
researched areas by employing a qualitative research methodology and conceptual content
analysis based on an interpretive research design.
Conceptual content analysis is widely acknowledged to be the most useful tool in
studying organizational cybersecurity issues by establishing the existence and frequency of
concepts most represented by words or phrases in a text. After a thoughtful consideration, the
method of conceptual qualitative content analysis has been chosen to answer the research
question below. While quantitative content analysis aims to make statistical interference of
frequencies from counting of huge data sets, it has been decided that qualitative content
analysis better suits the scope of this project. Especially the idea that qualitative content
analysis offers the opportunity to examine the material on a latent level complements the
research questions. Qualitative methods rather evaluate the underlying argumentation of
material as they go beyond the counting of words. The justification for choosing approach is
highlighted in the following.

2CYBER SECURITY THREAT IN ORGANISATION
To collect the data semi-structured expert face-face interviews were conducted
to probe participants about cybersecurity misconception and investment related issues. Semi-
structured interview approach was chosen to enable concretize the discussion by directing
participants’ towards cybersecurity issues in organizations, while still allowing participants
the flexibility to expand on the their undoubtedly unique experiences. Experts from different
mainly fields of information technology, human resource management, production
management and top- level management.
All the interviewee ’s were made with experts in the tech department and
organizational management function. Most of them had years of experiences in the industries
in which they are working and are independent experts who are capable of its evaluation. The
process of finding interview partners proved very complicated and time-consuming due to
issues of accessibility. Several individual persons as well as marketing departments were
approached by email or phone call with the aim to get in touch with the above described
groups of experts. Altogether approximately 35 messages were sent as most of these people
are always busy. In summary, the accessibility of fitting experts became a challenge, which
led to compromises in the acceptance of interviewees.
RESEARCH QUESTION:
What is the reason behind the misconception about cyber security in organisations and how
it creates an impact on organizational investment?
HYPOTHESIS:
There is a misconception about the fact that smaller companies are better protected than
larger companies and so this lack in cyber awareness impacts majority of the organizational
investment.
To collect the data semi-structured expert face-face interviews were conducted
to probe participants about cybersecurity misconception and investment related issues. Semi-
structured interview approach was chosen to enable concretize the discussion by directing
participants’ towards cybersecurity issues in organizations, while still allowing participants
the flexibility to expand on the their undoubtedly unique experiences. Experts from different
mainly fields of information technology, human resource management, production
management and top- level management.
All the interviewee ’s were made with experts in the tech department and
organizational management function. Most of them had years of experiences in the industries
in which they are working and are independent experts who are capable of its evaluation. The
process of finding interview partners proved very complicated and time-consuming due to
issues of accessibility. Several individual persons as well as marketing departments were
approached by email or phone call with the aim to get in touch with the above described
groups of experts. Altogether approximately 35 messages were sent as most of these people
are always busy. In summary, the accessibility of fitting experts became a challenge, which
led to compromises in the acceptance of interviewees.
RESEARCH QUESTION:
What is the reason behind the misconception about cyber security in organisations and how
it creates an impact on organizational investment?
HYPOTHESIS:
There is a misconception about the fact that smaller companies are better protected than
larger companies and so this lack in cyber awareness impacts majority of the organizational
investment.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
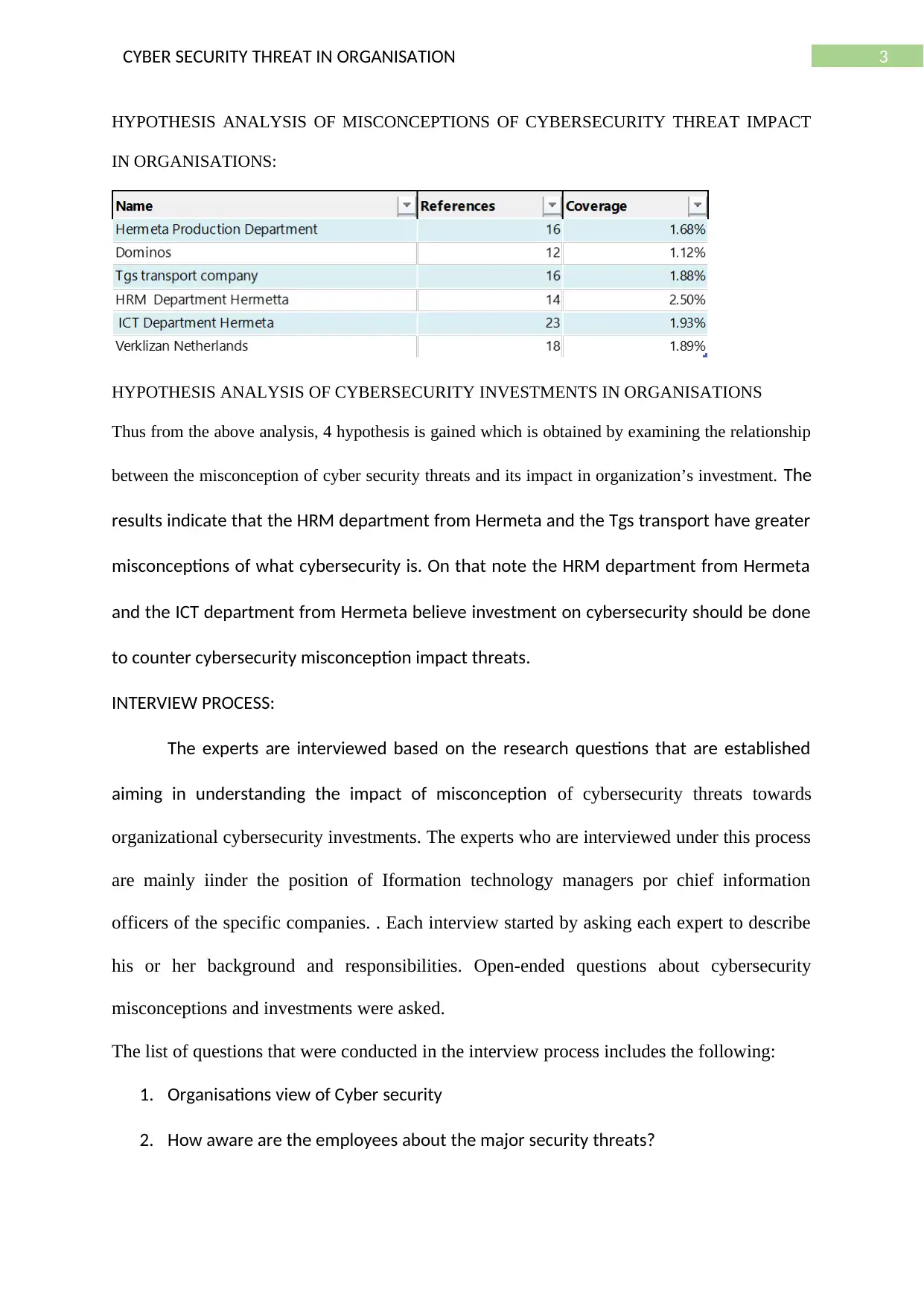
3CYBER SECURITY THREAT IN ORGANISATION
HYPOTHESIS ANALYSIS OF MISCONCEPTIONS OF CYBERSECURITY THREAT IMPACT
IN ORGANISATIONS:
HYPOTHESIS ANALYSIS OF CYBERSECURITY INVESTMENTS IN ORGANISATIONS
Thus from the above analysis, 4 hypothesis is gained which is obtained by examining the relationship
between the misconception of cyber security threats and its impact in organization’s investment. The
results indicate that the HRM department from Hermeta and the Tgs transport have greater
misconceptions of what cybersecurity is. On that note the HRM department from Hermeta
and the ICT department from Hermeta believe investment on cybersecurity should be done
to counter cybersecurity misconception impact threats.
INTERVIEW PROCESS:
The experts are interviewed based on the research questions that are established
aiming in understanding the impact of misconception of cybersecurity threats towards
organizational cybersecurity investments. The experts who are interviewed under this process
are mainly iinder the position of Iformation technology managers por chief information
officers of the specific companies. . Each interview started by asking each expert to describe
his or her background and responsibilities. Open-ended questions about cybersecurity
misconceptions and investments were asked.
The list of questions that were conducted in the interview process includes the following:
1. Organisations view of Cyber security
2. How aware are the employees about the major security threats?
HYPOTHESIS ANALYSIS OF MISCONCEPTIONS OF CYBERSECURITY THREAT IMPACT
IN ORGANISATIONS:
HYPOTHESIS ANALYSIS OF CYBERSECURITY INVESTMENTS IN ORGANISATIONS
Thus from the above analysis, 4 hypothesis is gained which is obtained by examining the relationship
between the misconception of cyber security threats and its impact in organization’s investment. The
results indicate that the HRM department from Hermeta and the Tgs transport have greater
misconceptions of what cybersecurity is. On that note the HRM department from Hermeta
and the ICT department from Hermeta believe investment on cybersecurity should be done
to counter cybersecurity misconception impact threats.
INTERVIEW PROCESS:
The experts are interviewed based on the research questions that are established
aiming in understanding the impact of misconception of cybersecurity threats towards
organizational cybersecurity investments. The experts who are interviewed under this process
are mainly iinder the position of Iformation technology managers por chief information
officers of the specific companies. . Each interview started by asking each expert to describe
his or her background and responsibilities. Open-ended questions about cybersecurity
misconceptions and investments were asked.
The list of questions that were conducted in the interview process includes the following:
1. Organisations view of Cyber security
2. How aware are the employees about the major security threats?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CYBER SECURITY THREAT IN ORGANISATION
3. Reason for the misconception about some cyber security threats within the
organisation
4. Impact of Cyber security threat within the organisation
5. Analysis of Company’s investment towards cyber threats
The time frame that is invested for each interview process with different organizations is
represented below:
Interview Partner Interview
Invitation
Follow up
Questionnaire
Initial Interviewee
Interview Partner 1
ICT Manager
Hermeta.
Email sent on the
14th of March.
Follow up email with
interview questions
sent on the 16th of
March
19 March 2018
Interview Partner 2
HRM Manager
Hermeta.
Sent a text message
on the 14th of
March
Follow up email with
interview questions
sent on the 16th of
March
19 March 2018
Interview Partner 3
Production
Manager
Hermeta.
Email sent on the
14th of March
Follow up email with
interview questions
sent on the 16th of
March
19 March 2018
Interview Partner 4
TGS Transport
company.
Sent a text message
on the 25th of
March
Follow up email with
interview questions
sent on the 16th of
March
21 March 2018
Interview Partner 5
Verklizan
Company.
Email sent on the
14th of March
Follow up email with
interview questions
sent on the 16th of
March
22 March 2018
Interview Partner 6
Dominos company,
Email sent on the
14th of March
Follow up email with
interview questions
sent on the 16th of
March
23 March 2018
Both email based interview as well as face to face interview is conducted in the entire
process.
DATA ANALYSIS:
3. Reason for the misconception about some cyber security threats within the
organisation
4. Impact of Cyber security threat within the organisation
5. Analysis of Company’s investment towards cyber threats
The time frame that is invested for each interview process with different organizations is
represented below:
Interview Partner Interview
Invitation
Follow up
Questionnaire
Initial Interviewee
Interview Partner 1
ICT Manager
Hermeta.
Email sent on the
14th of March.
Follow up email with
interview questions
sent on the 16th of
March
19 March 2018
Interview Partner 2
HRM Manager
Hermeta.
Sent a text message
on the 14th of
March
Follow up email with
interview questions
sent on the 16th of
March
19 March 2018
Interview Partner 3
Production
Manager
Hermeta.
Email sent on the
14th of March
Follow up email with
interview questions
sent on the 16th of
March
19 March 2018
Interview Partner 4
TGS Transport
company.
Sent a text message
on the 25th of
March
Follow up email with
interview questions
sent on the 16th of
March
21 March 2018
Interview Partner 5
Verklizan
Company.
Email sent on the
14th of March
Follow up email with
interview questions
sent on the 16th of
March
22 March 2018
Interview Partner 6
Dominos company,
Email sent on the
14th of March
Follow up email with
interview questions
sent on the 16th of
March
23 March 2018
Both email based interview as well as face to face interview is conducted in the entire
process.
DATA ANALYSIS:

5CYBER SECURITY THREAT IN ORGANISATION
After completing each interview, the transcription audio interview recordings and was
recorded Microsoft word document. An analysis of the interview results was coducted using
conceptual content analysis, synthesized series of findings and accompanying
recommendations. In this analysis, the synthesized experts’ opinions were selected by
choosing the most appearing themes that recurred most frequently across all interviews. The
NVivo software was used to conduct the analysis of all the six interview transcripts.
DATA ANALYSIS PROCESS:
The NVivo software is used to analyze the data that is obtained. The data analysis
process includes a series of steps. The first step includes uploading the interview
transcripts into the software. In the next step, the data collection unit is established
by the frequently occurring words and phrases like cybersecurity misconceptions and
cybersecurity investments’’. In the third step of the data analysis, the thematic coding
schemes are established while testing the hypothesis and running the queries in the
NVivo software. In the final step, the data are coded by selective reduction checking
the most frequent recurring themes in each interview transcript.
After completing each interview, the transcription audio interview recordings and was
recorded Microsoft word document. An analysis of the interview results was coducted using
conceptual content analysis, synthesized series of findings and accompanying
recommendations. In this analysis, the synthesized experts’ opinions were selected by
choosing the most appearing themes that recurred most frequently across all interviews. The
NVivo software was used to conduct the analysis of all the six interview transcripts.
DATA ANALYSIS PROCESS:
The NVivo software is used to analyze the data that is obtained. The data analysis
process includes a series of steps. The first step includes uploading the interview
transcripts into the software. In the next step, the data collection unit is established
by the frequently occurring words and phrases like cybersecurity misconceptions and
cybersecurity investments’’. In the third step of the data analysis, the thematic coding
schemes are established while testing the hypothesis and running the queries in the
NVivo software. In the final step, the data are coded by selective reduction checking
the most frequent recurring themes in each interview transcript.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6CYBER SECURITY THREAT IN ORGANISATION
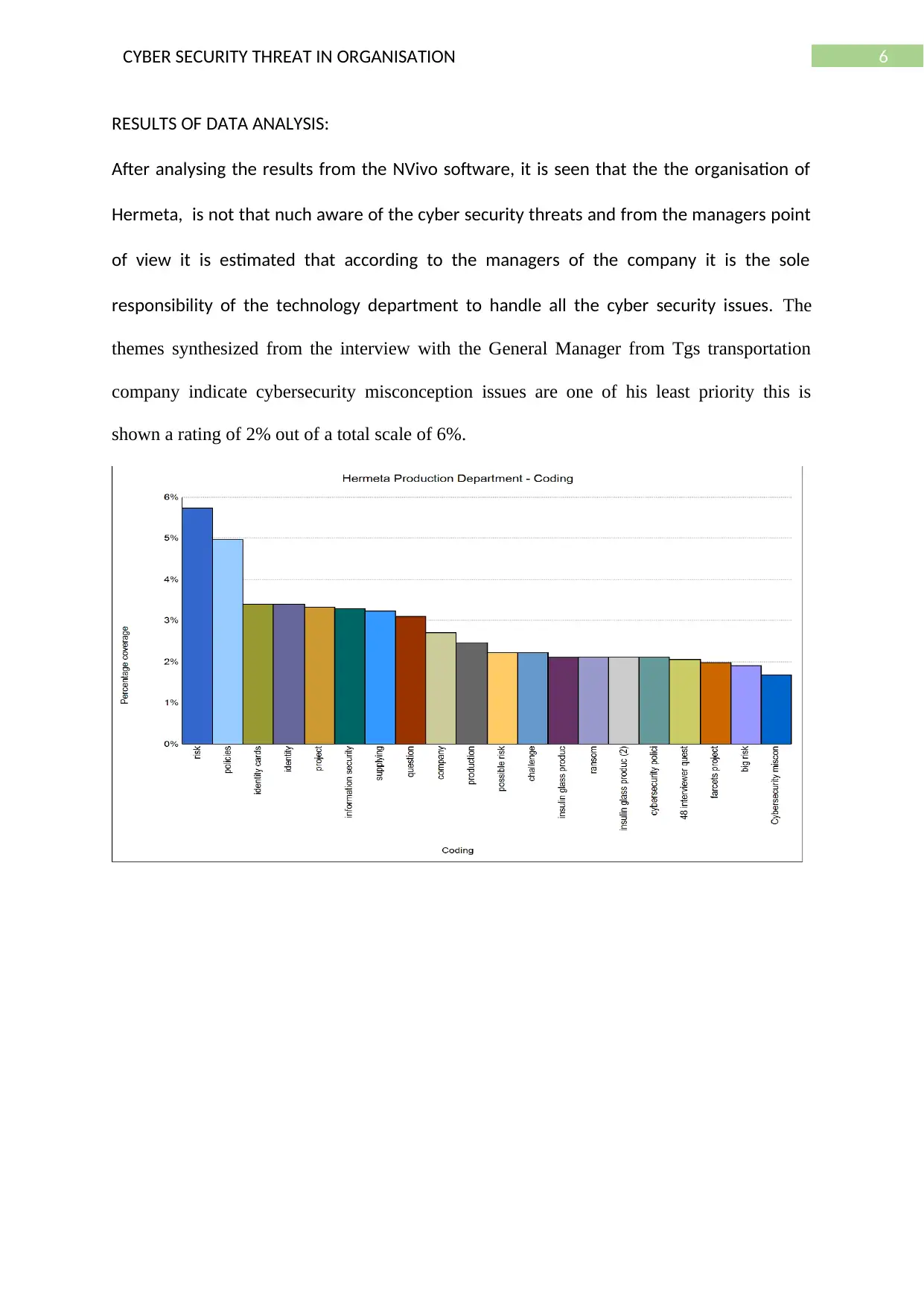
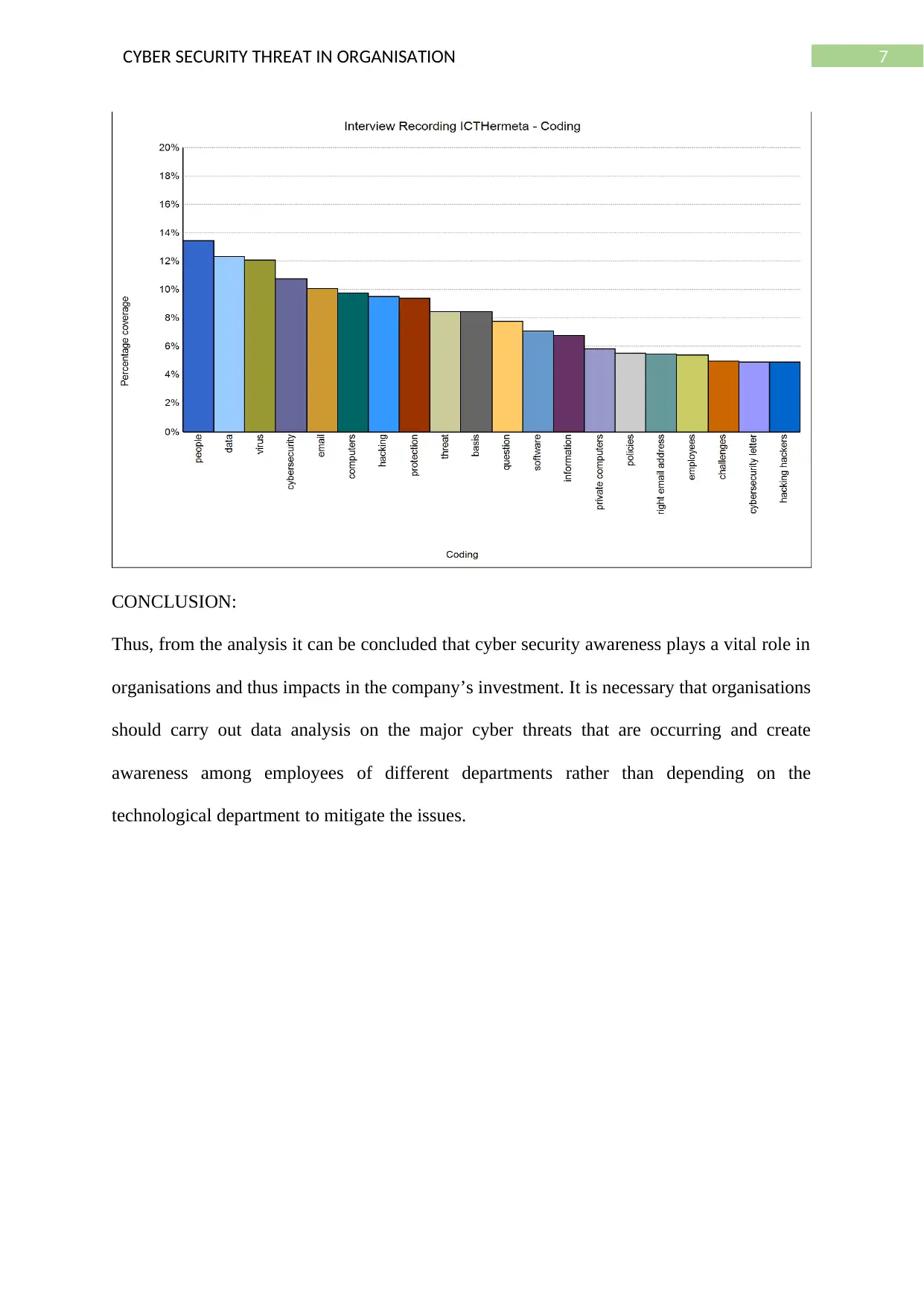
RESULTS OF DATA ANALYSIS:
After analysing the results from the NVivo software, it is seen that the the organisation of
Hermeta, is not that nuch aware of the cyber security threats and from the managers point
of view it is estimated that according to the managers of the company it is the sole
responsibility of the technology department to handle all the cyber security issues. The
themes synthesized from the interview with the General Manager from Tgs transportation
company indicate cybersecurity misconception issues are one of his least priority this is
shown a rating of 2% out of a total scale of 6%.
RESULTS OF DATA ANALYSIS:
After analysing the results from the NVivo software, it is seen that the the organisation of
Hermeta, is not that nuch aware of the cyber security threats and from the managers point
of view it is estimated that according to the managers of the company it is the sole
responsibility of the technology department to handle all the cyber security issues. The
themes synthesized from the interview with the General Manager from Tgs transportation
company indicate cybersecurity misconception issues are one of his least priority this is
shown a rating of 2% out of a total scale of 6%.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CYBER SECURITY THREAT IN ORGANISATION
CONCLUSION:
Thus, from the analysis it can be concluded that cyber security awareness plays a vital role in
organisations and thus impacts in the company’s investment. It is necessary that organisations
should carry out data analysis on the major cyber threats that are occurring and create
awareness among employees of different departments rather than depending on the
technological department to mitigate the issues.
CONCLUSION:
Thus, from the analysis it can be concluded that cyber security awareness plays a vital role in
organisations and thus impacts in the company’s investment. It is necessary that organisations
should carry out data analysis on the major cyber threats that are occurring and create
awareness among employees of different departments rather than depending on the
technological department to mitigate the issues.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





