Cyber-Security Concerns Regarding Internet of Things Assets
VerifiedAdded on 2022/11/25
|17
|4696
|194
Report
AI Summary
This research report explores the cyber-security concerns associated with the Internet of Things (IoT) and its application in cyber-physical systems. It begins with an introduction to the evolution of IoT and its impact on various aspects of life and business, highlighting the increasing demand for security measures. The report identifies the research problem as the growing number of cyber threats, including data theft and unauthorized access, which restrict the implementation of IoT. The research aims to identify prevalent security issues, analyze acceptable security levels, and recommend remedial strategies. The report covers background information, research problem, aims, objectives, research questions, and research structure. Chapter 2 provides a literature review, examining the definition of IoT, the concerns for shielding the ICT framework, and the different types of security breaches. The report also discusses various security threats, like malware attacks, DDoS attacks, and vulnerabilities in IoT devices, and suggests measures like VPN technology and password changes to maintain device security. The report identifies various causes that caused the breaches and the attacks over the network of the organizations and companies. Ranging from malware attack and distributed denial-of-service the list of the causes end with simple human error, some of which can be considered as unethical too (Lin et al. 2017). It has been investigated that many of such attacks are not just due to the weak systems and the primary cause behind them is the centralization of the services that gives a gateway to the attackers (Sajid, Abbas & Saleem 2016). As various organizations failed to cope up with the modern cyber attacks and their remedies, there is a scope left where research could be done for securing the devices under the domain of IoT and its environment.

The Cyber-Security Concerns regarding the Internet of Things Associated with Cyber-Physical
Assets
Name of the Student
Name of the University
Assets
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction..................................................................................................................................3
1.1 Background............................................................................................................................3
1.2 Research Problem or Opportunity.........................................................................................4
1.3 Research Aim, Objectives and Research Questions..............................................................5
1.4 Research Structure.................................................................................................................6
References........................................................................................................................................7
1. Introduction..................................................................................................................................3
1.1 Background............................................................................................................................3
1.2 Research Problem or Opportunity.........................................................................................4
1.3 Research Aim, Objectives and Research Questions..............................................................5
1.4 Research Structure.................................................................................................................6
References........................................................................................................................................7

1. Introduction
1.1 Background
Technology and Internet received a vast change after the development of Internet of
Things along with a change in the behavior of its usage. Apart from that, the hands of IoT
reached to the social life and environment of the business as well as leaving a huge impact over
these areas (Abomhara 2015). Besides, this technology of connected devices started penetrating
into the aspects of human life as well. Starting from education and healthcare IoT started taking
responsibility for home security services too. Along with that, this gradually developing
technology initiated the demand for security of using such services as well. Hence, the
involvement of IoT not only made the human life more interesting but also played a role as an
investment towards the business that deals with the security services for technological
equipments. The market of IoT has to be entangled with the security issues as the entire
technology is a digital network based system that involves security threats from the cyber
criminals. Security has always been the primary point of concern from its very start. Being on the
digital platform, IoT has been subjected to several security threats such as data theft, data loss,
unauthorized access and so on (Lee, Bagheri & Jin 2016). The concept of IoT got is root in the
Machine to machine communication. The only difference between the conventional
communication and IoT is that the entire technology of IoT takes place in a wireless setup.
According to the sources of Business Insider it was confirmed that till date over than 24 billion
Cyber-Physical systems are created worldwide (Conti et al. 2018). This revolutionary technology
modified the entire usage of the personal devices. As this technology gets stuck with its security
issues, its implementation is still limited. The primary objective of this paper is to investigate and
1.1 Background
Technology and Internet received a vast change after the development of Internet of
Things along with a change in the behavior of its usage. Apart from that, the hands of IoT
reached to the social life and environment of the business as well as leaving a huge impact over
these areas (Abomhara 2015). Besides, this technology of connected devices started penetrating
into the aspects of human life as well. Starting from education and healthcare IoT started taking
responsibility for home security services too. Along with that, this gradually developing
technology initiated the demand for security of using such services as well. Hence, the
involvement of IoT not only made the human life more interesting but also played a role as an
investment towards the business that deals with the security services for technological
equipments. The market of IoT has to be entangled with the security issues as the entire
technology is a digital network based system that involves security threats from the cyber
criminals. Security has always been the primary point of concern from its very start. Being on the
digital platform, IoT has been subjected to several security threats such as data theft, data loss,
unauthorized access and so on (Lee, Bagheri & Jin 2016). The concept of IoT got is root in the
Machine to machine communication. The only difference between the conventional
communication and IoT is that the entire technology of IoT takes place in a wireless setup.
According to the sources of Business Insider it was confirmed that till date over than 24 billion
Cyber-Physical systems are created worldwide (Conti et al. 2018). This revolutionary technology
modified the entire usage of the personal devices. As this technology gets stuck with its security
issues, its implementation is still limited. The primary objective of this paper is to investigate and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

identify the prevalent security issues that are an integral part of the IoT implementation in such
Cyber-Physical systems.
The threats and vulnerabilities for the technology that are getting common for private use
of IoT are the key questions that need to be answered. Personal data for the individuals and
sensitive data for several organizations are the basic areas where data theft has been a
considerable threat. Securing the information by the companies is necessary that can be done
with the help of a primary risk analysis and the gaps that facilitates the data to reach to the hands
of the cyber criminals. Special attention has to be given over the security issues as the
technology is new and standardization and legislation is yet to be documented.
1.2 Research Problem or Opportunity
In past years, there are reports of several cases being reported regarding the cyber threats
over the Cyber-Physical systems. Some of the cases that are registered are of data theft at a large
scale and the theft was committed at a personal level from the servers of the companies. With the
advent of IoT, a great amount of flexibility has been added to the usage of the devices, both for
personal and business uses. Moreover, the addition of the cyber threats and issues have restricted
the implementation of such technological flexibility. According to the report by Lu & Da Xu
(2018), almost two-third of the global enterprises have experienced such security issues in the
year of 2018. Additionally, informations were presented that claim that 25% of the enterprises
have a probability of facing such cyber attacks at a global scale by the year 2020. Surveys
conducted worldwide revealed that over than 3000 companies are there who implemented IoT in
their business operations (Sadeghi, Wachsmann & Waidner 2015). In addition, 84% of these
companies already faced breaching over their network and similar cyber attacks. Last year these
breaches over several organizations have been to found to be worth between US$4 million to
Cyber-Physical systems.
The threats and vulnerabilities for the technology that are getting common for private use
of IoT are the key questions that need to be answered. Personal data for the individuals and
sensitive data for several organizations are the basic areas where data theft has been a
considerable threat. Securing the information by the companies is necessary that can be done
with the help of a primary risk analysis and the gaps that facilitates the data to reach to the hands
of the cyber criminals. Special attention has to be given over the security issues as the
technology is new and standardization and legislation is yet to be documented.
1.2 Research Problem or Opportunity
In past years, there are reports of several cases being reported regarding the cyber threats
over the Cyber-Physical systems. Some of the cases that are registered are of data theft at a large
scale and the theft was committed at a personal level from the servers of the companies. With the
advent of IoT, a great amount of flexibility has been added to the usage of the devices, both for
personal and business uses. Moreover, the addition of the cyber threats and issues have restricted
the implementation of such technological flexibility. According to the report by Lu & Da Xu
(2018), almost two-third of the global enterprises have experienced such security issues in the
year of 2018. Additionally, informations were presented that claim that 25% of the enterprises
have a probability of facing such cyber attacks at a global scale by the year 2020. Surveys
conducted worldwide revealed that over than 3000 companies are there who implemented IoT in
their business operations (Sadeghi, Wachsmann & Waidner 2015). In addition, 84% of these
companies already faced breaching over their network and similar cyber attacks. Last year these
breaches over several organizations have been to found to be worth between US$4 million to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
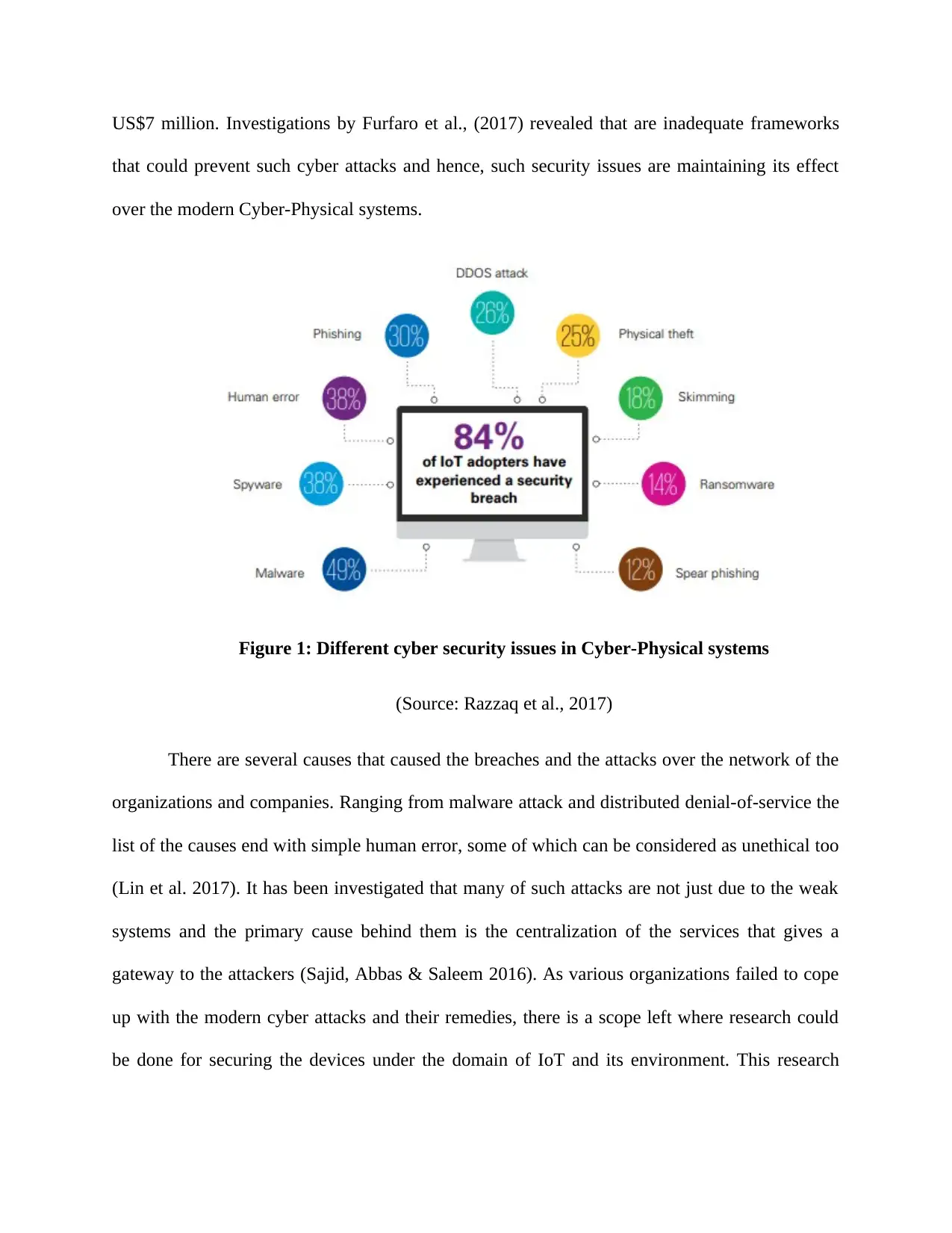
US$7 million. Investigations by Furfaro et al., (2017) revealed that are inadequate frameworks
that could prevent such cyber attacks and hence, such security issues are maintaining its effect
over the modern Cyber-Physical systems.
Figure 1: Different cyber security issues in Cyber-Physical systems
(Source: Razzaq et al., 2017)
There are several causes that caused the breaches and the attacks over the network of the
organizations and companies. Ranging from malware attack and distributed denial-of-service the
list of the causes end with simple human error, some of which can be considered as unethical too
(Lin et al. 2017). It has been investigated that many of such attacks are not just due to the weak
systems and the primary cause behind them is the centralization of the services that gives a
gateway to the attackers (Sajid, Abbas & Saleem 2016). As various organizations failed to cope
up with the modern cyber attacks and their remedies, there is a scope left where research could
be done for securing the devices under the domain of IoT and its environment. This research
that could prevent such cyber attacks and hence, such security issues are maintaining its effect
over the modern Cyber-Physical systems.
Figure 1: Different cyber security issues in Cyber-Physical systems
(Source: Razzaq et al., 2017)
There are several causes that caused the breaches and the attacks over the network of the
organizations and companies. Ranging from malware attack and distributed denial-of-service the
list of the causes end with simple human error, some of which can be considered as unethical too
(Lin et al. 2017). It has been investigated that many of such attacks are not just due to the weak
systems and the primary cause behind them is the centralization of the services that gives a
gateway to the attackers (Sajid, Abbas & Saleem 2016). As various organizations failed to cope
up with the modern cyber attacks and their remedies, there is a scope left where research could
be done for securing the devices under the domain of IoT and its environment. This research

paper will focus into both identification and solution of such security issues for the IoT devices
and environment.
1.3 Research Aim, Objectives and Research Questions
The research objectives are as follows:
To identify cyber security issues faced in Cyber-Physical systems
To analyze the minimum acceptable level of cyber security in such systems
To recommend remedial strategies for these issues in Cyber-Physical systems
The research questions are as follows:
What cyber security issues are faced in Cyber-Physical systems?
What is the minimum acceptable level of cyber security in Cyber-Physical systems?
How to mitigate these cyber security issues in Cyber-Physical systems?
1.4 Research Structure
Chapter 1: Introduction
Chapter 2: Literature Review
Chapter 3: Research Methodology
Chapter 4: Data Findings and Analysis
Chapter 5: Conclusion and Recommendations
and environment.
1.3 Research Aim, Objectives and Research Questions
The research objectives are as follows:
To identify cyber security issues faced in Cyber-Physical systems
To analyze the minimum acceptable level of cyber security in such systems
To recommend remedial strategies for these issues in Cyber-Physical systems
The research questions are as follows:
What cyber security issues are faced in Cyber-Physical systems?
What is the minimum acceptable level of cyber security in Cyber-Physical systems?
How to mitigate these cyber security issues in Cyber-Physical systems?
1.4 Research Structure
Chapter 1: Introduction
Chapter 2: Literature Review
Chapter 3: Research Methodology
Chapter 4: Data Findings and Analysis
Chapter 5: Conclusion and Recommendations
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 1: Research Structure
(Source: Created by author)
(Source: Created by author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Chapter 2: Literature Review
According to Sajid, Abbas and Saleem (2016), IoT can be defined as a technology that
uses sensors and actuators and few physical items for the collection of data and the collected data
is utilized to operate various devices that are connected in a network. In general it can be said
that, with the help of IoT, users can operate the devices without spending their energy and the
control of the device will be at their fingertips. Irrespective of the location of the user, the device
can be accessed by the user, provided both the controlling and controlled devices are connected
to a network. In simple words, IoT can be termed as an efficient and energy saving technique for
the users. Therefore, its implementations can be seen over various areas that includes education,
healthcare, communication and security as well. On the other hand, Ali and Awad (2018) stated
in their reports that over the past few years various policymakers and specialists emphasized the
concerns for shielding of the ICT framework in context of cyber attacks. The attention towards
the security of the IoT devices is considerably less as compared to the exponential growth of the
implementation of the technology. It is opined by Sani et al. (2019) that utilization of unsecured
IoT based devices helps in providing an easy as well as proper gateway to the cybercriminals.
The problem of cyber security for IoT prevails mainly due to the fast expansion of smart
home automation devices and the data that is stored within the device. It is stated by Conti et al.
(2018) that the smart home automation devices have the same computing power as a modern
Smartphone or tablet has and therefore it can be concluded that these automated devices can be
hacked too and can be turned into an email server. In the year 2014, investigation related with
information security reflected that thousands of spam email messages were transferred without
its owner’s knowledge. Apart from that Pan et al. (2017) stated that IoT devices are also forced
to join different types of malicious botnets for the entire purpose of conducting the distributed
According to Sajid, Abbas and Saleem (2016), IoT can be defined as a technology that
uses sensors and actuators and few physical items for the collection of data and the collected data
is utilized to operate various devices that are connected in a network. In general it can be said
that, with the help of IoT, users can operate the devices without spending their energy and the
control of the device will be at their fingertips. Irrespective of the location of the user, the device
can be accessed by the user, provided both the controlling and controlled devices are connected
to a network. In simple words, IoT can be termed as an efficient and energy saving technique for
the users. Therefore, its implementations can be seen over various areas that includes education,
healthcare, communication and security as well. On the other hand, Ali and Awad (2018) stated
in their reports that over the past few years various policymakers and specialists emphasized the
concerns for shielding of the ICT framework in context of cyber attacks. The attention towards
the security of the IoT devices is considerably less as compared to the exponential growth of the
implementation of the technology. It is opined by Sani et al. (2019) that utilization of unsecured
IoT based devices helps in providing an easy as well as proper gateway to the cybercriminals.
The problem of cyber security for IoT prevails mainly due to the fast expansion of smart
home automation devices and the data that is stored within the device. It is stated by Conti et al.
(2018) that the smart home automation devices have the same computing power as a modern
Smartphone or tablet has and therefore it can be concluded that these automated devices can be
hacked too and can be turned into an email server. In the year 2014, investigation related with
information security reflected that thousands of spam email messages were transferred without
its owner’s knowledge. Apart from that Pan et al. (2017) stated that IoT devices are also forced
to join different types of malicious botnets for the entire purpose of conducting the distributed

DoS attacks. It is found that the hackers generally target different types of streaming boxes,
webcams for carrying out massive DDoS attacks, which crippled domain name system that is
related with the servers.
Sani et al. (2019), identified that different types of skilled hackers make the damage by
properly determining an unsecured IoT device, which is leaking the internet protocol address that
can in turn utilized for pinpointing residential location. There are different types of experts of
information security recommending IoT connections could be done with the help of VPN
technology. With the correct VPN, one can protect the home network by keeping the IP private.
On the other hand, it is opined by Bertino et al. (2016) that unsecured devices function
insidiously due to the complicit relationship the manufacturers have. When IoT devices are
shipped to the customer, the devices contain the ID and the password, which is pre-defined by
the administrator. The customers keep using them as in general, the customers do not intend to
change these credentials unless insisted by the manufacturer and hence, it becomes easier for the
cyber attackers to track down the traffic and to decode the password. It is always advised to the
users to keep changing their password for maintaining the security of the particular device. This
measure can certainly avoid the primary threats.
It is opined by Furfaro et al. (2017) that remote vehicle hijacking is one of the major
issues and the instances that the attacker is performing over the system gradually provides the
control of the functionality of the vehicle. Sync IS developed a partnership with the Ford Motor
Company and Microsoft and has presented a list of the issues that can compromise various types
of connections. In addition to this, it is stated by Burg, Chattopadhyay and Lam (2017) that easy
exposure is one of the most important fundamental issues that are faced within the IoT industry.
If any of the device remains unattended or remains exposed to the trouble makers then there is an
webcams for carrying out massive DDoS attacks, which crippled domain name system that is
related with the servers.
Sani et al. (2019), identified that different types of skilled hackers make the damage by
properly determining an unsecured IoT device, which is leaking the internet protocol address that
can in turn utilized for pinpointing residential location. There are different types of experts of
information security recommending IoT connections could be done with the help of VPN
technology. With the correct VPN, one can protect the home network by keeping the IP private.
On the other hand, it is opined by Bertino et al. (2016) that unsecured devices function
insidiously due to the complicit relationship the manufacturers have. When IoT devices are
shipped to the customer, the devices contain the ID and the password, which is pre-defined by
the administrator. The customers keep using them as in general, the customers do not intend to
change these credentials unless insisted by the manufacturer and hence, it becomes easier for the
cyber attackers to track down the traffic and to decode the password. It is always advised to the
users to keep changing their password for maintaining the security of the particular device. This
measure can certainly avoid the primary threats.
It is opined by Furfaro et al. (2017) that remote vehicle hijacking is one of the major
issues and the instances that the attacker is performing over the system gradually provides the
control of the functionality of the vehicle. Sync IS developed a partnership with the Ford Motor
Company and Microsoft and has presented a list of the issues that can compromise various types
of connections. In addition to this, it is stated by Burg, Chattopadhyay and Lam (2017) that easy
exposure is one of the most important fundamental issues that are faced within the IoT industry.
If any of the device remains unattended or remains exposed to the trouble makers then there is an
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

open invitation to various discomforting situation. In some of the cases, it is identified that the
IoT devices are generally not resilient towards the exposure of the third party as they lay open
and provide an easy access to anyone. This means that an intruder takes the control of the device
and then makes a connection with other devices that contain different types of harmful data.
These data are used to make modifications within the program or replaces devices with different
malicious ones in which the intruder has entire control (Khatoun & Zeadally, 2017). In addition
to this, as the IoT devices are also used for personal usage, hence, the attackers try to take control
over the device so that they can have an unsolicited access to this personal information of the
users. Moreover, IoT devices can also run on low power as well as consumes fewer resources.
This functionality also provides an easy access to the intruders.
According to Kumar, Vealey and Srivastava (2016), a proper reflexive approach of IoT
based security can be formulated that will be based on different type of earlier IoT exploits and
exposures. Different types of cameras as well as payment-based card readers are subverted and
skimmed for passing data to different unauthorized users. It is identified that different types of
embedded systems are generally targeted by ransomware schemes, which is programmed in such
a way that the moment when the attackers would receive the demanded ransom the malware will
be out of the system (Geneiatakis et al., 2017). Or else they can make unprecedented shutdowns
or suspension of the processes according to their wish. IoT devices are engineered for proper
convenience but this convenience creates a number of risks. Proper cybersecurity-based hygiene
within the IoT initiated by ensuring that superuser credentials are prompted. It is found that
blocking as well as disability of Universal Plug and Play capabilities for shutting down the entire
traffic on different types of non-essential ports can be done that are frequently utilized for IoT
attacks.
IoT devices are generally not resilient towards the exposure of the third party as they lay open
and provide an easy access to anyone. This means that an intruder takes the control of the device
and then makes a connection with other devices that contain different types of harmful data.
These data are used to make modifications within the program or replaces devices with different
malicious ones in which the intruder has entire control (Khatoun & Zeadally, 2017). In addition
to this, as the IoT devices are also used for personal usage, hence, the attackers try to take control
over the device so that they can have an unsolicited access to this personal information of the
users. Moreover, IoT devices can also run on low power as well as consumes fewer resources.
This functionality also provides an easy access to the intruders.
According to Kumar, Vealey and Srivastava (2016), a proper reflexive approach of IoT
based security can be formulated that will be based on different type of earlier IoT exploits and
exposures. Different types of cameras as well as payment-based card readers are subverted and
skimmed for passing data to different unauthorized users. It is identified that different types of
embedded systems are generally targeted by ransomware schemes, which is programmed in such
a way that the moment when the attackers would receive the demanded ransom the malware will
be out of the system (Geneiatakis et al., 2017). Or else they can make unprecedented shutdowns
or suspension of the processes according to their wish. IoT devices are engineered for proper
convenience but this convenience creates a number of risks. Proper cybersecurity-based hygiene
within the IoT initiated by ensuring that superuser credentials are prompted. It is found that
blocking as well as disability of Universal Plug and Play capabilities for shutting down the entire
traffic on different types of non-essential ports can be done that are frequently utilized for IoT
attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

According to Plageras et al. (2018), when a breach is discovered, it is quite important to
act accordingly as well as promptly in order to close the exposure of the functions. The first and
the most important step is to mobilise the entire incident response team. The team should be
formed with the help of different internal stakeholder group including the technical team for
investigating the breach. In addition to this, the team must also include members from different
teams and legal representative. There are a lot of legal implications which are mainly associated
with the cyber attack and therefore it is considered to be important for the entire organization for
seeking legal advice about the attack. Majstorovic et al. (2016) stated that security systems as
well as ensuring business continuity within the business is also important. By following a
security breach, the first and the most important step from different technical perspective is to
properly secure the entire IT systems in order to restrict the breach. Additionally, it is also
important to investigate the reason behind the breach.
As stated by Abomhara (2015), maintenance of legal and regulatory requirements is
necessary. As legislation contain different types of regulatory and notification-based
requirements, which are applied within the event of a specific breach. It is found that as most of
the jurisdictions do not have a proper all-encompassing law hence, there is proper patchwork that
is based on regulations that has developed in context to different types of evolving threats. Some
of the laws are applied across different sectors while the industry-based legislation is continuing
to develop in order to target the risk sectors. Moreover, incurring liability within the event of
cybersecurity breach is important. Liability that is based on the cyber security can be incurred
within the litigation for the breach of different statutory obligations, negligence as well as breach
of contract. According to Weber and Studer (2016), the longer it is taken in order to identify a
hack, the more costly the consequences become. It is found that that with around 60 seconds of
act accordingly as well as promptly in order to close the exposure of the functions. The first and
the most important step is to mobilise the entire incident response team. The team should be
formed with the help of different internal stakeholder group including the technical team for
investigating the breach. In addition to this, the team must also include members from different
teams and legal representative. There are a lot of legal implications which are mainly associated
with the cyber attack and therefore it is considered to be important for the entire organization for
seeking legal advice about the attack. Majstorovic et al. (2016) stated that security systems as
well as ensuring business continuity within the business is also important. By following a
security breach, the first and the most important step from different technical perspective is to
properly secure the entire IT systems in order to restrict the breach. Additionally, it is also
important to investigate the reason behind the breach.
As stated by Abomhara (2015), maintenance of legal and regulatory requirements is
necessary. As legislation contain different types of regulatory and notification-based
requirements, which are applied within the event of a specific breach. It is found that as most of
the jurisdictions do not have a proper all-encompassing law hence, there is proper patchwork that
is based on regulations that has developed in context to different types of evolving threats. Some
of the laws are applied across different sectors while the industry-based legislation is continuing
to develop in order to target the risk sectors. Moreover, incurring liability within the event of
cybersecurity breach is important. Liability that is based on the cyber security can be incurred
within the litigation for the breach of different statutory obligations, negligence as well as breach
of contract. According to Weber and Studer (2016), the longer it is taken in order to identify a
hack, the more costly the consequences become. It is found that that with around 60 seconds of

notifications, the results are compromised by 40%. In addition to this, Cyber-insurance is also
important that generally limit the capacity between $5 million to $100 million per client.
Moreover, organizations must have a scheme of paying to the outsiders, who will notify them
about the different types of security flaws. The companies ranging from Dropbox to Google and
LinkedIn have already adopted this type of practice.
According to Ali et al. (2017), cybersecurity related threats as well as attacks could not
be removed if proper security-based strategies are not adopted within the organization. The first
and the most important step is to provide proper training facility to the users as their accounts are
considered as one of the largest sources of attack within the organization. Thus, it is quite
important to train the organization personnel in preventing different type of incidents. On the
other hand, it is opined by De Bruijn and Janssen (2017) that investing within the perimeter is
necessary as the attackers search for vulnerable default settings as well as electronic holes within
the firewalls, routers as well as switches in order to penetrate the defence system. This helps in
properly exploiting the flaws within the devices in order to gain an access within the network for
redirecting traffic on a desired network for intercepting various types of information while being
in transmission. In addition to this, it is quite necessary to make sure that external facing
hardware should be properly configured with the best practices which is generally running within
the latest patches as well as firmware.
According to Sicari et al. (2015), back up of data is also considered as one of the
important steps in order to resolve the IoT based cyber security. Though backing up of data does
not protect the environment but a robust backup solution helps in ensuring that returning to work
will become much faster within the event of cyber-infection. Proper establishment as well as
multiple restore points will be helpful in preventing a number of risks that are related with data
important that generally limit the capacity between $5 million to $100 million per client.
Moreover, organizations must have a scheme of paying to the outsiders, who will notify them
about the different types of security flaws. The companies ranging from Dropbox to Google and
LinkedIn have already adopted this type of practice.
According to Ali et al. (2017), cybersecurity related threats as well as attacks could not
be removed if proper security-based strategies are not adopted within the organization. The first
and the most important step is to provide proper training facility to the users as their accounts are
considered as one of the largest sources of attack within the organization. Thus, it is quite
important to train the organization personnel in preventing different type of incidents. On the
other hand, it is opined by De Bruijn and Janssen (2017) that investing within the perimeter is
necessary as the attackers search for vulnerable default settings as well as electronic holes within
the firewalls, routers as well as switches in order to penetrate the defence system. This helps in
properly exploiting the flaws within the devices in order to gain an access within the network for
redirecting traffic on a desired network for intercepting various types of information while being
in transmission. In addition to this, it is quite necessary to make sure that external facing
hardware should be properly configured with the best practices which is generally running within
the latest patches as well as firmware.
According to Sicari et al. (2015), back up of data is also considered as one of the
important steps in order to resolve the IoT based cyber security. Though backing up of data does
not protect the environment but a robust backup solution helps in ensuring that returning to work
will become much faster within the event of cyber-infection. Proper establishment as well as
multiple restore points will be helpful in preventing a number of risks that are related with data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





