Cybersecurity Issues, Solutions, and Cost Analysis for JL Company
VerifiedAdded on 2023/04/11
|15
|2532
|124
Report
AI Summary
This report provides a detailed analysis of cybersecurity issues facing JL Company. It identifies vulnerabilities such as lack of security software, outdated routers, inadequate backup policies, and susceptibility to spam and malware. The report then proposes several solutions, including implementing secure communication methods, creating a sophisticated password strategy, utilizing a secure backup plan, being aware of internal threats, designating a point person for cybersecurity, and upgrading the Windows server. Each solution is accompanied by a discussion of potential consequences, alternative approaches, and associated costs. The report emphasizes the increasing importance of cybersecurity in protecting customer data and maintaining business integrity, advocating for a proactive and comprehensive approach to address the identified weaknesses and safeguard the company's assets.
Assignment
Issues to be addressed in JL company
Issues to be addressed in JL company
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INTRODUCTION
For any organization hoping to make a fruitful computerized change, cybersecurity must be a top
need—hard stop. Harms and information misfortune identified with cybercrime has now raised to at
no other time seen extents, and reports recommend the unsafe impacts of cybercrime will before
long cause a yearly expense of around $6 trillion by 2021(Peng, Li, & Fei, 2017). Therefore, it has
turned out to be progressively significant for associations to make adequate strides in ensuring their
frameworks and the information they hold, including their hierarchical just as close to home client
information. Organizations of all size must keep up a sharp familiarity with how cybersecurity is
changing, how it tends to be connected, and in particular how it very well may be undermined in the
event that they would like to end up as the winner(Yuan, Yuan, Guo, Yang, & Sun, 2016).
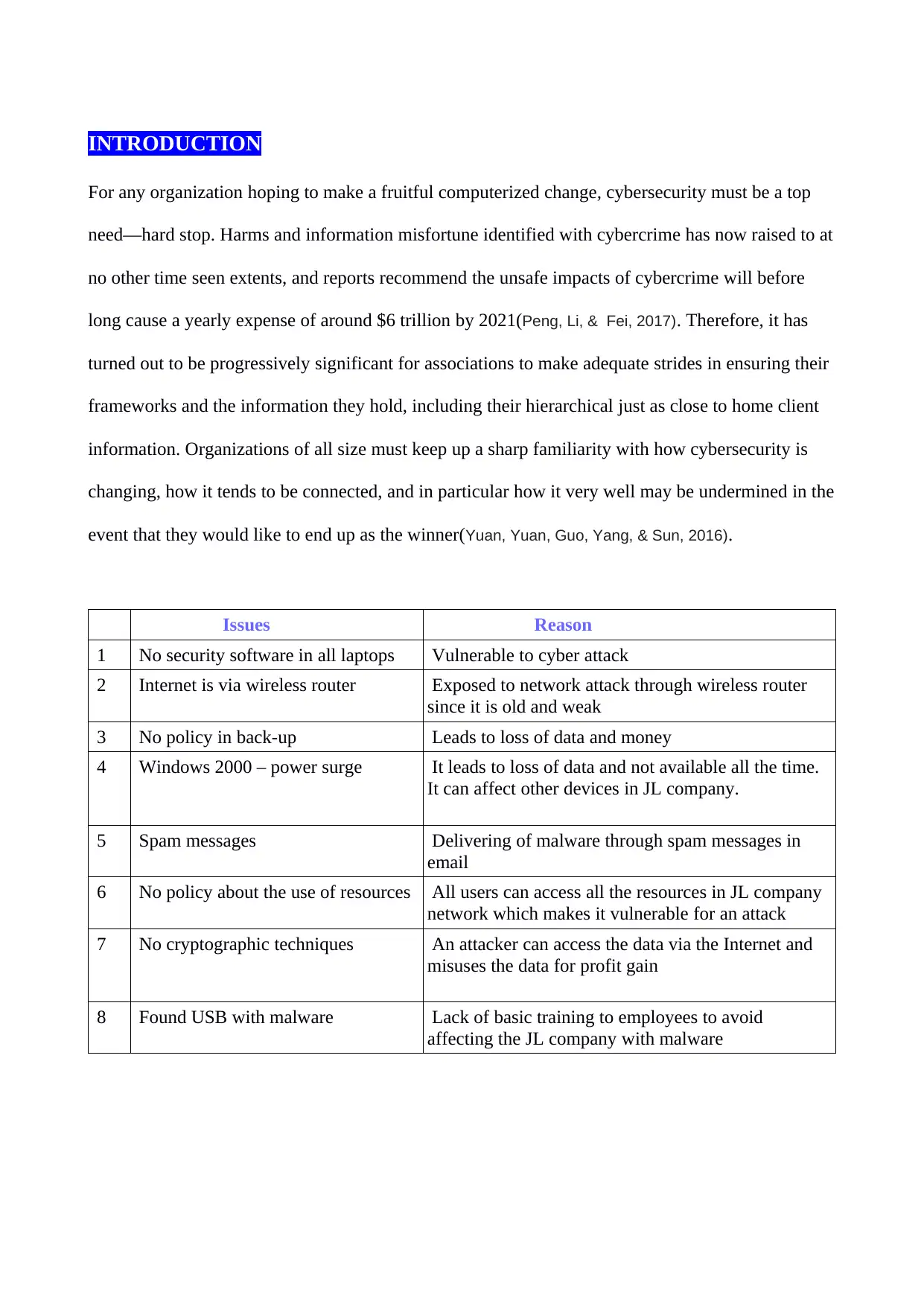
Issues Reason
1 No security software in all laptops Vulnerable to cyber attack
2 Internet is via wireless router Exposed to network attack through wireless router
since it is old and weak
3 No policy in back-up Leads to loss of data and money
4 Windows 2000 – power surge It leads to loss of data and not available all the time.
It can affect other devices in JL company.
5 Spam messages Delivering of malware through spam messages in
email
6 No policy about the use of resources All users can access all the resources in JL company
network which makes it vulnerable for an attack
7 No cryptographic techniques An attacker can access the data via the Internet and
misuses the data for profit gain
8 Found USB with malware Lack of basic training to employees to avoid
affecting the JL company with malware
For any organization hoping to make a fruitful computerized change, cybersecurity must be a top
need—hard stop. Harms and information misfortune identified with cybercrime has now raised to at
no other time seen extents, and reports recommend the unsafe impacts of cybercrime will before
long cause a yearly expense of around $6 trillion by 2021(Peng, Li, & Fei, 2017). Therefore, it has
turned out to be progressively significant for associations to make adequate strides in ensuring their
frameworks and the information they hold, including their hierarchical just as close to home client
information. Organizations of all size must keep up a sharp familiarity with how cybersecurity is
changing, how it tends to be connected, and in particular how it very well may be undermined in the
event that they would like to end up as the winner(Yuan, Yuan, Guo, Yang, & Sun, 2016).
Issues Reason
1 No security software in all laptops Vulnerable to cyber attack
2 Internet is via wireless router Exposed to network attack through wireless router
since it is old and weak
3 No policy in back-up Leads to loss of data and money
4 Windows 2000 – power surge It leads to loss of data and not available all the time.
It can affect other devices in JL company.
5 Spam messages Delivering of malware through spam messages in
6 No policy about the use of resources All users can access all the resources in JL company
network which makes it vulnerable for an attack
7 No cryptographic techniques An attacker can access the data via the Internet and
misuses the data for profit gain
8 Found USB with malware Lack of basic training to employees to avoid
affecting the JL company with malware
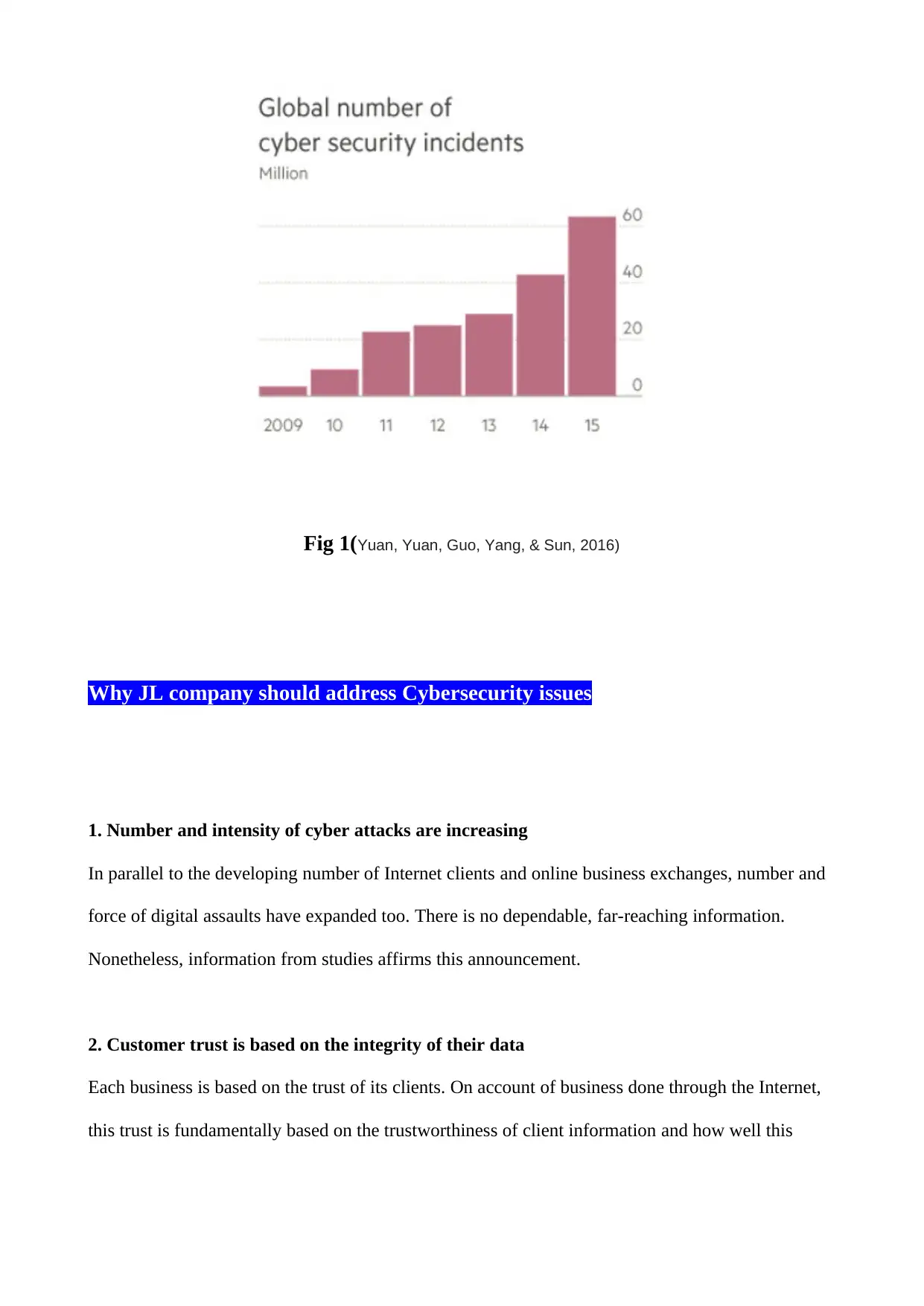
Fig 1(Yuan, Yuan, Guo, Yang, & Sun, 2016)
Why JL company should address Cybersecurity issues
1. Number and intensity of cyber attacks are increasing
In parallel to the developing number of Internet clients and online business exchanges, number and
force of digital assaults have expanded too. There is no dependable, far-reaching information.
Nonetheless, information from studies affirms this announcement.
2. Customer trust is based on the integrity of their data
Each business is based on the trust of its clients. On account of business done through the Internet,
this trust is fundamentally based on the trustworthiness of client information and how well this
Why JL company should address Cybersecurity issues
1. Number and intensity of cyber attacks are increasing
In parallel to the developing number of Internet clients and online business exchanges, number and
force of digital assaults have expanded too. There is no dependable, far-reaching information.
Nonetheless, information from studies affirms this announcement.
2. Customer trust is based on the integrity of their data
Each business is based on the trust of its clients. On account of business done through the Internet,
this trust is fundamentally based on the trustworthiness of client information and how well this
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

information is ensured by organizations.
3. Cybersecurity is more than a task for the IT department
In various organizations, cybersecurity is dealt with primarily as an assignment for the IT office.
Through specialized measures, IT experts are relied upon to guarantee that the computerized
business of their organizations is shielded from digital assaults.
4. Employees could either be a security risk or an asset
Cybersecurity is as much an issue of the workforce as it is an IT subject. Numerous cybersecurity
dangers are made or expanded by scatterbrained workers. Assume for instance the loss of cell
phones, which establishes a noteworthy security chance, as information found on those gadgets
could give access to delicate organization information.
Issues to be addressed in JL company
a) Implement Secure Communication Methods.
Here's a tip that may astonish you: Did you realize that fax is the most secure type of
correspondence in the business world? (Ding, Li, Quevedo, Dey, & Shi, 2017).
"At the point when a record is sent by fax it's changed over into paired code (0s), sent via phone
system and after that reassembled at the opposite end," says Karol Waldron of XMedius, a pioneer
in big business grade fax arrangements. "Hacking into the phone system would require direct
manual access to the phone line, and regardless of whether a record was caught it would introduce
itself as the only clamor, making it for all intents and purposes difficult to translate/read."
Notwithstanding utilizing fax, you ought to likewise survey your organization's way to deal with
versatile correspondences. On the off chance that your staff utilizes cell phones for work purposes,
3. Cybersecurity is more than a task for the IT department
In various organizations, cybersecurity is dealt with primarily as an assignment for the IT office.
Through specialized measures, IT experts are relied upon to guarantee that the computerized
business of their organizations is shielded from digital assaults.
4. Employees could either be a security risk or an asset
Cybersecurity is as much an issue of the workforce as it is an IT subject. Numerous cybersecurity
dangers are made or expanded by scatterbrained workers. Assume for instance the loss of cell
phones, which establishes a noteworthy security chance, as information found on those gadgets
could give access to delicate organization information.
Issues to be addressed in JL company
a) Implement Secure Communication Methods.
Here's a tip that may astonish you: Did you realize that fax is the most secure type of
correspondence in the business world? (Ding, Li, Quevedo, Dey, & Shi, 2017).
"At the point when a record is sent by fax it's changed over into paired code (0s), sent via phone
system and after that reassembled at the opposite end," says Karol Waldron of XMedius, a pioneer
in big business grade fax arrangements. "Hacking into the phone system would require direct
manual access to the phone line, and regardless of whether a record was caught it would introduce
itself as the only clamor, making it for all intents and purposes difficult to translate/read."
Notwithstanding utilizing fax, you ought to likewise survey your organization's way to deal with
versatile correspondences. On the off chance that your staff utilizes cell phones for work purposes,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
there should be limitations on the data gadgets can get to, rules on whether gadgets can be brought
home, and clear rules for when IT divisions can clean a gadget off.
Consequences:
1 Cyber attack on the JL company’s network
2 Loss of money
3 Slow devices leading to downtime
4 Loss of important data
Alternative:
There are various options. A few choices incorporate free online courses
a large number of which should be possible in a multi-day(Wu, Zhang, & Yue, 2016).
Cost:
The training camp costs $5000 per individual and spreads a scope of subjects recorded
beneath((Ding, Li, Quevedo, Dey, & Shi, 2017):
Fig 2
b) Create a Sophisticated Password Strategy.
home, and clear rules for when IT divisions can clean a gadget off.
Consequences:
1 Cyber attack on the JL company’s network
2 Loss of money
3 Slow devices leading to downtime
4 Loss of important data
Alternative:
There are various options. A few choices incorporate free online courses
a large number of which should be possible in a multi-day(Wu, Zhang, & Yue, 2016).
Cost:
The training camp costs $5000 per individual and spreads a scope of subjects recorded
beneath((Ding, Li, Quevedo, Dey, & Shi, 2017):
Fig 2
b) Create a Sophisticated Password Strategy.

In all honesty, a lot of digital security attacks succeed on the grounds that passwords are excessively
straightforward. Programmers approach advancements that empower them to take encoded
passwords and split them. Some call this "beast constraining."
"Beast power is tied in with overwhelming the PC's protections by utilizing reiteration," tech master
Paul Gil clarifies. "On account of secret key hacking, lexicon assaults include lexicon programming
that recombines English lexicon words with a huge number of different blends."
This is the kind of stuff you find in the motion pictures, where the program breaks one letter at any
given moment utilizing a huge number of varieties every moment. You can't counteract 100 percent
of secret key dangers, you can make it a lot harder for programmers and decrease the odds of being
undermined(Dridi, Zhani, 2016, October).
Everything begins with making a complex secret key procedure. Here are a couple of things to
know:
Representatives ought to be required to make passwords with mixes of capitalized and
lowercase letters, numbers, and images. Moreover, passwords ought to be reset at regular
intervals.
Managerial records should utilize considerably progressively complex passwords. Never set
basic passwords like "Password01" or "Admin123." Hackers every now and again attempt
these abused codes.
Actualize genuine ramifications for representatives who don't pursue secret phrase rules and
consistently direct reviews. Workers need to realize you pay attention to secret phrase
quality and uprightness(Fotohi, Ebazadeh, & Geshlag, 2016).
Notwithstanding when you pursue systems, for example, these, you won't be 100 percent ensured.
Ensure you can disavow a client's entrance and consents whenever. This engages you to react
quickly should a record become traded off(Wei, Fung, 2015, June).
straightforward. Programmers approach advancements that empower them to take encoded
passwords and split them. Some call this "beast constraining."
"Beast power is tied in with overwhelming the PC's protections by utilizing reiteration," tech master
Paul Gil clarifies. "On account of secret key hacking, lexicon assaults include lexicon programming
that recombines English lexicon words with a huge number of different blends."
This is the kind of stuff you find in the motion pictures, where the program breaks one letter at any
given moment utilizing a huge number of varieties every moment. You can't counteract 100 percent
of secret key dangers, you can make it a lot harder for programmers and decrease the odds of being
undermined(Dridi, Zhani, 2016, October).
Everything begins with making a complex secret key procedure. Here are a couple of things to
know:
Representatives ought to be required to make passwords with mixes of capitalized and
lowercase letters, numbers, and images. Moreover, passwords ought to be reset at regular
intervals.
Managerial records should utilize considerably progressively complex passwords. Never set
basic passwords like "Password01" or "Admin123." Hackers every now and again attempt
these abused codes.
Actualize genuine ramifications for representatives who don't pursue secret phrase rules and
consistently direct reviews. Workers need to realize you pay attention to secret phrase
quality and uprightness(Fotohi, Ebazadeh, & Geshlag, 2016).
Notwithstanding when you pursue systems, for example, these, you won't be 100 percent ensured.
Ensure you can disavow a client's entrance and consents whenever. This engages you to react
quickly should a record become traded off(Wei, Fung, 2015, June).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Consequence:
1 Loss of important data
2 Loss of client's personal data
3 Mistrust by the public
4 Loss of clients
Alternative:
There are numerous options on the web. They all spread something very similar and appear to be of
equivalent quality(Gope, Lee, & Quek, 2016).
Cost:
Assumption: manager earning $90,000 a year based on rough average(Ding, Li, Quevedo, Dey, & Shi,
2017).
$1600 a week
4days/6days a week=50%.
0.5X1600
Fig 3(Ding, Li, Quevedo, Dey, & Shi, 2017)
1 Loss of important data
2 Loss of client's personal data
3 Mistrust by the public
4 Loss of clients
Alternative:
There are numerous options on the web. They all spread something very similar and appear to be of
equivalent quality(Gope, Lee, & Quek, 2016).
Cost:
Assumption: manager earning $90,000 a year based on rough average(Ding, Li, Quevedo, Dey, & Shi,
2017).
$1600 a week
4days/6days a week=50%.
0.5X1600
Fig 3(Ding, Li, Quevedo, Dey, & Shi, 2017)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

c) Use a Secure Backup Plan.
You should as of now have a protected reinforcement plan, however, feel free to audit the
subtleties. Numerous digital lawbreakers utilize a strategy known as "digital coercion" when they
assault an independent venture(Chen, Ho, Zhang, & Yu, 2017). They'll hold a portion of your
significant information prisoner and request a payoff consequently. In the event that you have a
sufficient reinforcement plan, you'll have significantly more influence in this circumstance. With a
safe reinforcement plan, your information ought to be spared and put away in various areas.
In a perfect world, one of these is a cloud arrangement that is free of any physical equipment in
your office. This won't naturally keep information from being undermined, however, it ensures you
never lose your entrance to it(Cheng, Yue, Hu, & Chen, 2019, April).
Consequence:
1 Loss of important data
2 Loss of integrity
3 Not available all the time
4 Slower backups
Alternative:
There is a lot of options and all appear to be genuinely comparable. This report selected the
Synology NAS as it was frequently audited profoundly. Nonetheless, there is an alternative for
$270. Recognition may suit ZP yet this lacks speed, and capacity limit nearly.
Cost:
You should as of now have a protected reinforcement plan, however, feel free to audit the
subtleties. Numerous digital lawbreakers utilize a strategy known as "digital coercion" when they
assault an independent venture(Chen, Ho, Zhang, & Yu, 2017). They'll hold a portion of your
significant information prisoner and request a payoff consequently. In the event that you have a
sufficient reinforcement plan, you'll have significantly more influence in this circumstance. With a
safe reinforcement plan, your information ought to be spared and put away in various areas.
In a perfect world, one of these is a cloud arrangement that is free of any physical equipment in
your office. This won't naturally keep information from being undermined, however, it ensures you
never lose your entrance to it(Cheng, Yue, Hu, & Chen, 2019, April).
Consequence:
1 Loss of important data
2 Loss of integrity
3 Not available all the time
4 Slower backups
Alternative:
There is a lot of options and all appear to be genuinely comparable. This report selected the
Synology NAS as it was frequently audited profoundly. Nonetheless, there is an alternative for
$270. Recognition may suit ZP yet this lacks speed, and capacity limit nearly.
Cost:
The Synology is $500
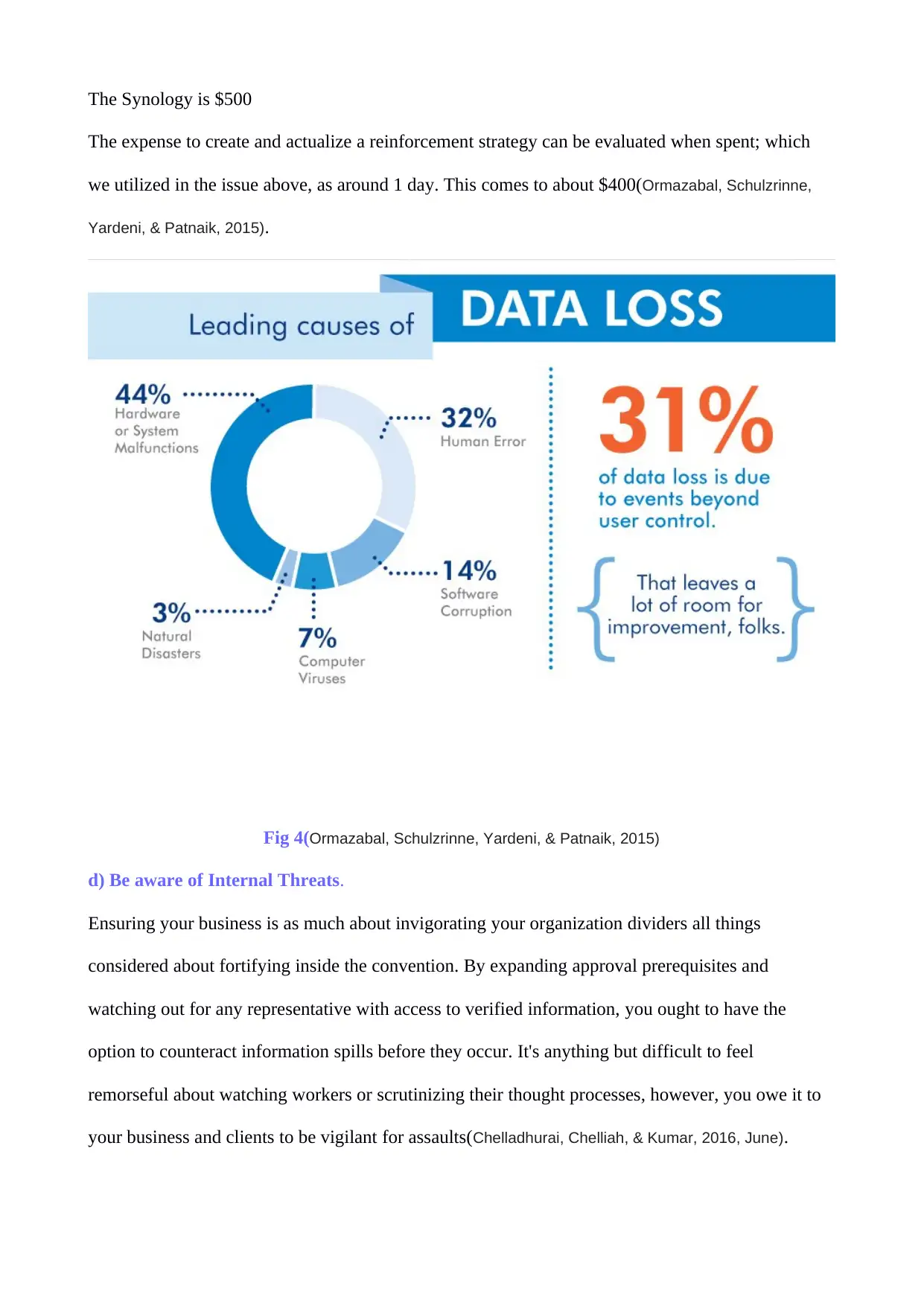
The expense to create and actualize a reinforcement strategy can be evaluated when spent; which
we utilized in the issue above, as around 1 day. This comes to about $400(Ormazabal, Schulzrinne,
Yardeni, & Patnaik, 2015).
Fig 4(Ormazabal, Schulzrinne, Yardeni, & Patnaik, 2015)
d) Be aware of Internal Threats.
Ensuring your business is as much about invigorating your organization dividers all things
considered about fortifying inside the convention. By expanding approval prerequisites and
watching out for any representative with access to verified information, you ought to have the
option to counteract information spills before they occur. It's anything but difficult to feel
remorseful about watching workers or scrutinizing their thought processes, however, you owe it to
your business and clients to be vigilant for assaults(Chelladhurai, Chelliah, & Kumar, 2016, June).
The expense to create and actualize a reinforcement strategy can be evaluated when spent; which
we utilized in the issue above, as around 1 day. This comes to about $400(Ormazabal, Schulzrinne,
Yardeni, & Patnaik, 2015).
Fig 4(Ormazabal, Schulzrinne, Yardeni, & Patnaik, 2015)
d) Be aware of Internal Threats.
Ensuring your business is as much about invigorating your organization dividers all things
considered about fortifying inside the convention. By expanding approval prerequisites and
watching out for any representative with access to verified information, you ought to have the
option to counteract information spills before they occur. It's anything but difficult to feel
remorseful about watching workers or scrutinizing their thought processes, however, you owe it to
your business and clients to be vigilant for assaults(Chelladhurai, Chelliah, & Kumar, 2016, June).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Consequence:
1 Using non-secure devices
2 Not available all the time
3 Difficult to monitor user’s devices
Cost:
This report recommends the IT overseer plays out this assignment. It is evaluated that it will as it
took 3-4 days(Zhang, Zhang, & Lee, 2017, April).
Pay of $1700 per week (Payscale, 2018)
0.4 X 1700 = $680
Fig 5(Zhang, Zhang, & Lee, 2017, April)
e) Designate a Point Person.
1 Using non-secure devices
2 Not available all the time
3 Difficult to monitor user’s devices
Cost:
This report recommends the IT overseer plays out this assignment. It is evaluated that it will as it
took 3-4 days(Zhang, Zhang, & Lee, 2017, April).
Pay of $1700 per week (Payscale, 2018)
0.4 X 1700 = $680
Fig 5(Zhang, Zhang, & Lee, 2017, April)
e) Designate a Point Person.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The obstruction for independent companies is an absence of assets. SBOs will say things like, "We
can't stand to contract a full-time IT individual." Or possibly: "Our IT individual has such a great
amount to do, we can't toss something else on his plate." Regardless of whether representatives are
wearing numerous caps and taking care of an assortment of obligations, it should be somebody's
business to concentrate on security. "Your go-to person has three essential duties: to remain
educated regarding real news and changes in computerized security, to know the fundamental
necessities for your business to work safely and effectively, and to guarantee that those
prerequisites are set up and kept refreshed," says advisor Ty Kiisel. "This doesn't imply that the
individual in control needs to by and by doing practically everything, except that the individual
needs to locate the correct administrations or experts who can do the important updates and
enhancements(Mukherjee, Shirazi, Ray, Daily, & Gamble, 2016, December)."
Consequence:
Without an administrator JL company will lack the expertise to identify issues such as backup plan,
malware infection and server upgrade among many other issues.
Alternative:
The option in contrast to this employing in‐house. ZP unquestionably does not require a full-time
position and finding a reasonable low maintenance representative might be troublesome. The
expenses of a full clock would probably exceed the advantages as the normal pay is around
$90,000.
Cost:
90,000/52 = $1800 every week 1800 X 3 = $5400
Continuous 2‐3 days seven days: 1800 X 0.5(FTE)= $800
700 X 52 = $36,400
36,400 + 1800 = 38,200
38,200 X 0.7 (30% sparing) = $26,740
can't stand to contract a full-time IT individual." Or possibly: "Our IT individual has such a great
amount to do, we can't toss something else on his plate." Regardless of whether representatives are
wearing numerous caps and taking care of an assortment of obligations, it should be somebody's
business to concentrate on security. "Your go-to person has three essential duties: to remain
educated regarding real news and changes in computerized security, to know the fundamental
necessities for your business to work safely and effectively, and to guarantee that those
prerequisites are set up and kept refreshed," says advisor Ty Kiisel. "This doesn't imply that the
individual in control needs to by and by doing practically everything, except that the individual
needs to locate the correct administrations or experts who can do the important updates and
enhancements(Mukherjee, Shirazi, Ray, Daily, & Gamble, 2016, December)."
Consequence:
Without an administrator JL company will lack the expertise to identify issues such as backup plan,
malware infection and server upgrade among many other issues.
Alternative:
The option in contrast to this employing in‐house. ZP unquestionably does not require a full-time
position and finding a reasonable low maintenance representative might be troublesome. The
expenses of a full clock would probably exceed the advantages as the normal pay is around
$90,000.
Cost:
90,000/52 = $1800 every week 1800 X 3 = $5400
Continuous 2‐3 days seven days: 1800 X 0.5(FTE)= $800
700 X 52 = $36,400
36,400 + 1800 = 38,200
38,200 X 0.7 (30% sparing) = $26,740

f) Upgrading windows server to the latest version.
Replacing the server and upgrading to Windows Server 2016 will make a lot of things simpler for
JL company. All traffic will go through the server, making the system increasingly secure. The
server will keep up a firewall and Anti‐Virus. Since all PCs will switch Windows 10 it bodes well
to utilize Windows Server 2016 which it's server partner. In extra server programming; JL company
should buy another pinnacle server too. This is key to the usage of a great deal of the arrangements
proposed in this report. The server will be the center of the system for JL. It will push updates and
fixes to the PCs, screen the system for security issues, control traffic, perform reinforcements and
ensure protection from malware.
Consequence:
1 Fail to comply with other software
2 Security issues
3 Loss of productivity
Alternative:
There are no much options for this situation. The representatives are well-known
with Windows system so recommending a Linux based server would convolute things significantly.
There are different Windows Server 2016 choices. Windows Server 2016 Datacentre is a very
genuine bit of system and begins at around $8500. It is proposed for the substantial association and
is unacceptable for JL organization.
Cost:
The Windows Server 2016 Standard version costs around $1100. Another server tower would cost
around $3000, likely somewhat more as buying extra RAM and storage ought to be considered so a
gauge around $3000 is sensible. This report suggests the HPE ProLiant ML110 for $3000 + extra
Replacing the server and upgrading to Windows Server 2016 will make a lot of things simpler for
JL company. All traffic will go through the server, making the system increasingly secure. The
server will keep up a firewall and Anti‐Virus. Since all PCs will switch Windows 10 it bodes well
to utilize Windows Server 2016 which it's server partner. In extra server programming; JL company
should buy another pinnacle server too. This is key to the usage of a great deal of the arrangements
proposed in this report. The server will be the center of the system for JL. It will push updates and
fixes to the PCs, screen the system for security issues, control traffic, perform reinforcements and
ensure protection from malware.
Consequence:
1 Fail to comply with other software
2 Security issues
3 Loss of productivity
Alternative:
There are no much options for this situation. The representatives are well-known
with Windows system so recommending a Linux based server would convolute things significantly.
There are different Windows Server 2016 choices. Windows Server 2016 Datacentre is a very
genuine bit of system and begins at around $8500. It is proposed for the substantial association and
is unacceptable for JL organization.
Cost:
The Windows Server 2016 Standard version costs around $1100. Another server tower would cost
around $3000, likely somewhat more as buying extra RAM and storage ought to be considered so a
gauge around $3000 is sensible. This report suggests the HPE ProLiant ML110 for $3000 + extra
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

