IT Audit Report: NSW City Councils IT Audit Findings and Analysis
VerifiedAdded on 2023/01/05
|11
|3139
|98
Report
AI Summary
This report provides an in-depth analysis of an IT audit conducted by the NSW Auditor General, focusing on the IT governance, general controls, and cybersecurity management within the NSW city councils. The audit identifies key areas of focus, including cyber security, and examines the scope, high-risk issues, and specific audit findings related to IT governance, general controls, and cyber security management. The report highlights the importance of formalized IT policies, timely reviews, and risk management practices. It also discusses the application of frameworks like ISACA's COBIT 5 to enhance IT governance. The audit reveals deficiencies in user access management, password controls, change management, and disaster recovery planning. Furthermore, the report addresses the lack of cyber security frameworks, incident registers, penetration testing, and cyber security training within the councils. The report emphasizes the professional, legal, and ethical responsibilities of IT auditors and the potential impacts of poor cyber security administration, including financial loss and reputational damage. The report highlights the need for the local government to establish a cyber protection strategy by June 30, 2021, to ensure a consistent response to cyber security risks across groups.

IT Audit and
Controls
Controls
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION......................................................................................................................3
Identify the audit focus and scope..........................................................................................3
High risk IT issues in the NSW city councils........................................................................3
Audit findings related to IT governance in the NSW city councils.......................................5
Audit findings related to IT general controls in the NSW city councils................................7
Audit findings related to cyber security management in the NSW city councils..................8
Discussion on professional, legal and ethical responsibilities of IT auditor..........................9
CONCLUSION........................................................................................................................10
REFERENCES.........................................................................................................................11
INTRODUCTION......................................................................................................................3
Identify the audit focus and scope..........................................................................................3
High risk IT issues in the NSW city councils........................................................................3
Audit findings related to IT governance in the NSW city councils.......................................5
Audit findings related to IT general controls in the NSW city councils................................7
Audit findings related to cyber security management in the NSW city councils..................8
Discussion on professional, legal and ethical responsibilities of IT auditor..........................9
CONCLUSION........................................................................................................................10
REFERENCES.........................................................................................................................11

INTRODUCTION
The audit analysis is considered as an effective approach which involves the
organization’s system reports. This is an important approach for the purpose of analysing the
ethical and the legal value which is maintained by the business organization. On the other
side, it can be easily determined that analysing the report of a business organization is very
much beneficial as it highlights what are the key requirement the company is have followed
and maintained while other requirements that the company ahs breached. This report is in
context to the IT audit report of conducted by the office of NSW Auditor General. This report
highlights the audit focus and scope, issues faced, finding based on the IT governance and
general controls.
Identify the audit focus and scope
The main areas of focus are on cyber security with the help of performance,
compliance and other audits like financial audit of the local government sectors. The scope of
this report is limited to the determining the strength of the local government council in
information technology along with the cyber security management system (Report on Local
Government. 2019). This report mainly focusses on the key findings and the observations
form the financial audit of 2018-19. The audit office undertakes the financial and
performance audits of the such local entities in NSW to:
To support the reforms pointed toward reinforcing governance and monetary
oversight in the area.
Giving more prominent consistency in the monetary reporting and audit measure
Improve financial administration, financial obligation and public responsibility.
High risk IT issues in the NSW city councils
This audit report has identified 575 issues in regard to the information technology,
for the year 2017-18 it was: 448 issues. The 68% of the issues is in connection with the user
access management for the year 2017-18 it was 60% (Report on Local Government. 2019).
Along with that, the total number of deficiencies in the information technology control has
also increased in contract to the previous year, but the total number of high risk issues has
fallen.
The audit analysis is considered as an effective approach which involves the
organization’s system reports. This is an important approach for the purpose of analysing the
ethical and the legal value which is maintained by the business organization. On the other
side, it can be easily determined that analysing the report of a business organization is very
much beneficial as it highlights what are the key requirement the company is have followed
and maintained while other requirements that the company ahs breached. This report is in
context to the IT audit report of conducted by the office of NSW Auditor General. This report
highlights the audit focus and scope, issues faced, finding based on the IT governance and
general controls.
Identify the audit focus and scope
The main areas of focus are on cyber security with the help of performance,
compliance and other audits like financial audit of the local government sectors. The scope of
this report is limited to the determining the strength of the local government council in
information technology along with the cyber security management system (Report on Local
Government. 2019). This report mainly focusses on the key findings and the observations
form the financial audit of 2018-19. The audit office undertakes the financial and
performance audits of the such local entities in NSW to:
To support the reforms pointed toward reinforcing governance and monetary
oversight in the area.
Giving more prominent consistency in the monetary reporting and audit measure
Improve financial administration, financial obligation and public responsibility.
High risk IT issues in the NSW city councils
This audit report has identified 575 issues in regard to the information technology,
for the year 2017-18 it was: 448 issues. The 68% of the issues is in connection with the user
access management for the year 2017-18 it was 60% (Report on Local Government. 2019).
Along with that, the total number of deficiencies in the information technology control has
also increased in contract to the previous year, but the total number of high risk issues has
fallen.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
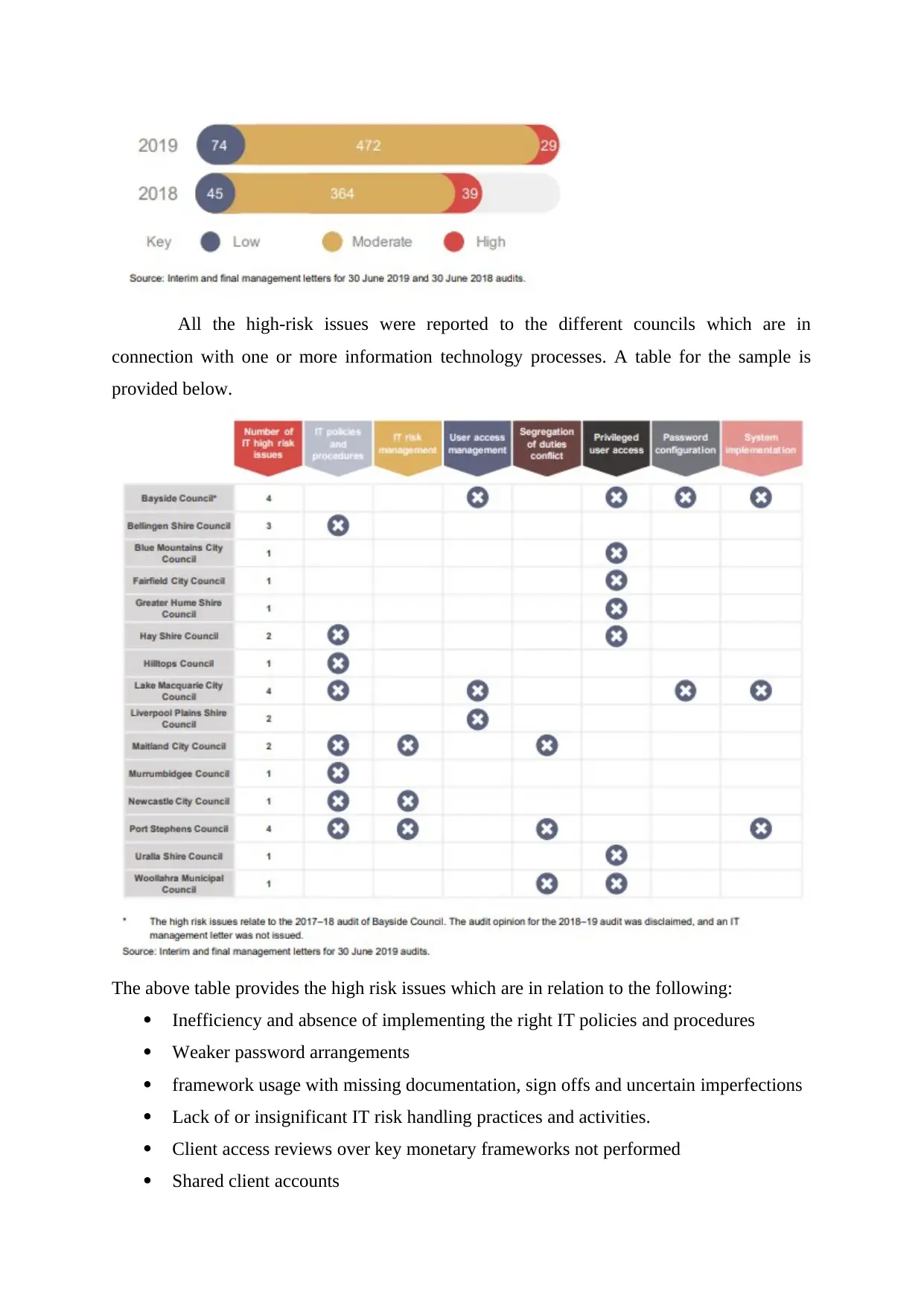
All the high-risk issues were reported to the different councils which are in
connection with one or more information technology processes. A table for the sample is
provided below.
The above table provides the high risk issues which are in relation to the following:
Inefficiency and absence of implementing the right IT policies and procedures
Weaker password arrangements
framework usage with missing documentation, sign offs and uncertain imperfections
Lack of or insignificant IT risk handling practices and activities.
Client access reviews over key monetary frameworks not performed
Shared client accounts
connection with one or more information technology processes. A table for the sample is
provided below.
The above table provides the high risk issues which are in relation to the following:
Inefficiency and absence of implementing the right IT policies and procedures
Weaker password arrangements
framework usage with missing documentation, sign offs and uncertain imperfections
Lack of or insignificant IT risk handling practices and activities.
Client access reviews over key monetary frameworks not performed
Shared client accounts
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Segregation of obligations not appropriately implemented in the key monetary
frameworks
Special client access not being sufficiently restricted and observed to distinguish
suspicious or other unapproved action or activity
The overall IT control discrepancies or the issues which has been identified till 30 June 2019
are bifurcated into 3 areas which are stated below.
1. IT governance
2. Cyber security management
3. IT general controls
Audit findings related to IT governance in the NSW city councils
The IT governance refers to the system or the structure which allows the local
councils in effectively managing the IT risks and ensuring that each and every activity is
properly aligned with the set objectives in order to accomplish it successfully.
Based upon the audit finding, it can be stated that the IT policies are not formalised
and is not up to date. It is very crucial that the important IT related policies and procedures
are formalized and are reviewed on a regular basis in order to make sure that the emerging
risks and risks race being measured considerably and policies highlights the reflective change
in the entire IT environment (Sansom, 2019). Inconsistency and lack in the structured and the
formal IT policies might result into inaccurate and inappropriate practices and this will
consequently result into the inappropriate access to the key systems. In the local council there
has not been much improvement in relation to the implementation of right set of IT policies
and in ensuring timely review (Report on Local Government. 2019). 71% of the councils are
not having any IT policies in respect to the following areas such as IT security, change
management, IT disaster recovery and business continuity. In the previous year the figure
was 73%. The 25% of the existing such IT policies are not even reviewed in accordance with
the council’s scheduled review date for the purpose of ensuring that everything is up to date
and the year 2017-18 it was 21%. Along with that 41% of the councils are not having or
maintained the risk register as compared to the previous year’s 50%. Also, it has been
identified that 22% (2017-18: 34%) councils does not communicate on a daily basis to the
management about the IT risks along with those charged with governance.
In order to effectively implement and improve the situation of the IT governance, the
council can make use of the ISACA’s CORBIT framework. This framework involves the
linking of the business goals with the IT infrastructure through the way of making use of the
models and metrics for measuring the achievements along with determining the related
frameworks
Special client access not being sufficiently restricted and observed to distinguish
suspicious or other unapproved action or activity
The overall IT control discrepancies or the issues which has been identified till 30 June 2019
are bifurcated into 3 areas which are stated below.
1. IT governance
2. Cyber security management
3. IT general controls
Audit findings related to IT governance in the NSW city councils
The IT governance refers to the system or the structure which allows the local
councils in effectively managing the IT risks and ensuring that each and every activity is
properly aligned with the set objectives in order to accomplish it successfully.
Based upon the audit finding, it can be stated that the IT policies are not formalised
and is not up to date. It is very crucial that the important IT related policies and procedures
are formalized and are reviewed on a regular basis in order to make sure that the emerging
risks and risks race being measured considerably and policies highlights the reflective change
in the entire IT environment (Sansom, 2019). Inconsistency and lack in the structured and the
formal IT policies might result into inaccurate and inappropriate practices and this will
consequently result into the inappropriate access to the key systems. In the local council there
has not been much improvement in relation to the implementation of right set of IT policies
and in ensuring timely review (Report on Local Government. 2019). 71% of the councils are
not having any IT policies in respect to the following areas such as IT security, change
management, IT disaster recovery and business continuity. In the previous year the figure
was 73%. The 25% of the existing such IT policies are not even reviewed in accordance with
the council’s scheduled review date for the purpose of ensuring that everything is up to date
and the year 2017-18 it was 21%. Along with that 41% of the councils are not having or
maintained the risk register as compared to the previous year’s 50%. Also, it has been
identified that 22% (2017-18: 34%) councils does not communicate on a daily basis to the
management about the IT risks along with those charged with governance.
In order to effectively implement and improve the situation of the IT governance, the
council can make use of the ISACA’s CORBIT framework. This framework involves the
linking of the business goals with the IT infrastructure through the way of making use of the
models and metrics for measuring the achievements along with determining the related

business responsibilities in respect to the IT processes. The key focused areas are strategic
alignment, value delivery, resource management, risk management and the performance
measurement all together leading to IT governance. the Cobit 5 new framework is based on
the 5 principle if followed will result into effective management of the IT governace.
Figure 1COBIT 5 ISACA's new framework (Source: COBIT 5 ISACA's new framework. 2020)
A detailed analysis is given below.
Meeting stakeholders needs: A business enterprise or an entity is exists for creating
value for the its stakeholders and society and providing the same requires good
governance system of T assets. the members of board and other executives require to
consider IT as the most important part of the organization (Andry and Setiawan,
2019). COBIT 5 offers a framework which provides assistance to the enterprises in
accomplishing their goals and objectives through delivering value by effective
management of IT.
Covering enterprise end to end: It refers to involving all the key components into the
governance system and building a relationship with them.
Imposing single integrated system: It aligns with the other standards in relation to IT
which are – ISO 38500, TOGAF, ISO27000 series, CMMI and so forth.
Enabling holistic approach: This framework sets the enablers n order to support the
implementation of the governance system for the IT enterprise.
Separating governance from the management: Governance guarantees that endeavor
destinations are accomplished by assessing stakeholder needs, conditions and
alignment, value delivery, resource management, risk management and the performance
measurement all together leading to IT governance. the Cobit 5 new framework is based on
the 5 principle if followed will result into effective management of the IT governace.
Figure 1COBIT 5 ISACA's new framework (Source: COBIT 5 ISACA's new framework. 2020)
A detailed analysis is given below.
Meeting stakeholders needs: A business enterprise or an entity is exists for creating
value for the its stakeholders and society and providing the same requires good
governance system of T assets. the members of board and other executives require to
consider IT as the most important part of the organization (Andry and Setiawan,
2019). COBIT 5 offers a framework which provides assistance to the enterprises in
accomplishing their goals and objectives through delivering value by effective
management of IT.
Covering enterprise end to end: It refers to involving all the key components into the
governance system and building a relationship with them.
Imposing single integrated system: It aligns with the other standards in relation to IT
which are – ISO 38500, TOGAF, ISO27000 series, CMMI and so forth.
Enabling holistic approach: This framework sets the enablers n order to support the
implementation of the governance system for the IT enterprise.
Separating governance from the management: Governance guarantees that endeavor
destinations are accomplished by assessing stakeholder needs, conditions and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

alternatives; developing direction by prioritization and decision making; and checking
the performance, consistence and progress against the stated aims and goals.
Audit findings related to IT general controls in the NSW city councils
The IT general controls accounts to the procedures along with the activities which
are designed for the purpose of ensuring the confidentiality and integrity of the IT system. the
financial audit includes the review of the IT general controls which addresses, user access
management, privileged user access, system software acquisition and the disaster recovery
planning (Morris and et.al., 2020). The council has further improved and enhanced their
access management processes but there is additional improvement required for effectively
monitoring the user account activities along with timely review of it.
Based on the audit report, it has been found that the approximately 40% of the
councils are lacking behind in terms of having or implemented adequate internal control for
adding more users and this percentage is a reduction in contrast to the previous year which
was 47%. Another point is that 33% of the councils is not having suitable user access
removal controls in place and this has shown a great improvement as compared to the past
year of 43% (Report on Local Government. 2019). The aspect in relation to the imposition of
stronger password control system shows that there is no change in it and has been at the same
rate as that of the last year which is 43%. It has also been determined that the 71% of the
councils does not review the privileged user a/c activities which is very important and no
improvement has been seen in the same. There has been a new area that councils require to
put focus on which is periodic client access reviews which accounts for the 64%.
Apart from the access management, the program change management also requires
further improvement. From the audit report, it has been found out that the councils have not
made any improvement in the change management in regard to the IT system in contrast to
the year 2017-18. 36% of the councils are not having any segregation in respect to the duties
in between the developer and the implementer (Report on Local Government. 2019). Along
that, the 33% of councils are imposing changes in the systems without having any prior and
proper approval. The council is also lacking behind having proper disaster recovery planning
system. this system helps the council in reducing the risk of disruption to the operation under
the situation of major outage. It requires proper and detailed analysis without which the
council may not be able to predict the influence of such disaster. 31% of councils does not
have a formalized and approved DRP and the DRPs which are formalized has not been
currently reviewed. The 55% of the councils with the have not undertaken any of the tested
plan with significant regularities.
the performance, consistence and progress against the stated aims and goals.
Audit findings related to IT general controls in the NSW city councils
The IT general controls accounts to the procedures along with the activities which
are designed for the purpose of ensuring the confidentiality and integrity of the IT system. the
financial audit includes the review of the IT general controls which addresses, user access
management, privileged user access, system software acquisition and the disaster recovery
planning (Morris and et.al., 2020). The council has further improved and enhanced their
access management processes but there is additional improvement required for effectively
monitoring the user account activities along with timely review of it.
Based on the audit report, it has been found that the approximately 40% of the
councils are lacking behind in terms of having or implemented adequate internal control for
adding more users and this percentage is a reduction in contrast to the previous year which
was 47%. Another point is that 33% of the councils is not having suitable user access
removal controls in place and this has shown a great improvement as compared to the past
year of 43% (Report on Local Government. 2019). The aspect in relation to the imposition of
stronger password control system shows that there is no change in it and has been at the same
rate as that of the last year which is 43%. It has also been determined that the 71% of the
councils does not review the privileged user a/c activities which is very important and no
improvement has been seen in the same. There has been a new area that councils require to
put focus on which is periodic client access reviews which accounts for the 64%.
Apart from the access management, the program change management also requires
further improvement. From the audit report, it has been found out that the councils have not
made any improvement in the change management in regard to the IT system in contrast to
the year 2017-18. 36% of the councils are not having any segregation in respect to the duties
in between the developer and the implementer (Report on Local Government. 2019). Along
that, the 33% of councils are imposing changes in the systems without having any prior and
proper approval. The council is also lacking behind having proper disaster recovery planning
system. this system helps the council in reducing the risk of disruption to the operation under
the situation of major outage. It requires proper and detailed analysis without which the
council may not be able to predict the influence of such disaster. 31% of councils does not
have a formalized and approved DRP and the DRPs which are formalized has not been
currently reviewed. The 55% of the councils with the have not undertaken any of the tested
plan with significant regularities.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Audit findings related to cyber security management in the NSW city councils
At a State Government level, the NSW Cyber Security Policy expresses that solid
network protection is a significant segment of the NSW Digital Government Strategy. The
term network safety covers all estimates used to ensure frameworks and data put away or
conveyed on these frameworks from compromise of secrecy, honesty and accessibility. While
there is presently no necessity for boards to follow the State Governments security strategy,
councils may find it helpful to allude to the approach for additional direction (Report on
Local Government. 2019). It is recommended that the office of local government inside the
Department of Planning, Industry and Environment ought to build up a cyber protection
strategy by 30 June 2021 to guarantee a steady response to the network safety chances across
gatherings.
A high level of assessment is being undertaken in order to determine the whether the
council has met with the basic governance requirement and the internal control systems for
effectively handling the cyber security. According to the audit findings, 80% of the councils
does not have any proper cyber security framework along with that 78% of the councils does
not maintain a centralized register pertaining to the cyber incidents, 46% have not included
the risks in relation to the cyber attack in the risk register (Report on Local Government.
2019). 67% of the councils have not undertaken in the recent times any type of penetration
testing. Apart from this, other important aspect is that 48% of the local counsel’s are not
having insurance policy in association with the cyber security. Together with this, the council
is also lacking in terms of having separate budget for the cyber security. 76% of councils
have not provided the training in regard to the cyber security training to its staffs.
Poor administration of cyber protection can open gatherings to an expansive scope
of dangers, including money related misfortune, reputational harm and information breaches.
The potential effects may include:
burglary of corporate and monetary data and licensed innovation
robbery of cash
denial of administration
demolition of information
costs of fixing influenced frameworks, networks and devices
legal charges or action from misfortunes emerging from refusal of-service attacks
causing framework downtime in basic frameworks
outsider misfortunes when individual data put away on government frameworks is
utilized for criminal purposes.
At a State Government level, the NSW Cyber Security Policy expresses that solid
network protection is a significant segment of the NSW Digital Government Strategy. The
term network safety covers all estimates used to ensure frameworks and data put away or
conveyed on these frameworks from compromise of secrecy, honesty and accessibility. While
there is presently no necessity for boards to follow the State Governments security strategy,
councils may find it helpful to allude to the approach for additional direction (Report on
Local Government. 2019). It is recommended that the office of local government inside the
Department of Planning, Industry and Environment ought to build up a cyber protection
strategy by 30 June 2021 to guarantee a steady response to the network safety chances across
gatherings.
A high level of assessment is being undertaken in order to determine the whether the
council has met with the basic governance requirement and the internal control systems for
effectively handling the cyber security. According to the audit findings, 80% of the councils
does not have any proper cyber security framework along with that 78% of the councils does
not maintain a centralized register pertaining to the cyber incidents, 46% have not included
the risks in relation to the cyber attack in the risk register (Report on Local Government.
2019). 67% of the councils have not undertaken in the recent times any type of penetration
testing. Apart from this, other important aspect is that 48% of the local counsel’s are not
having insurance policy in association with the cyber security. Together with this, the council
is also lacking in terms of having separate budget for the cyber security. 76% of councils
have not provided the training in regard to the cyber security training to its staffs.
Poor administration of cyber protection can open gatherings to an expansive scope
of dangers, including money related misfortune, reputational harm and information breaches.
The potential effects may include:
burglary of corporate and monetary data and licensed innovation
robbery of cash
denial of administration
demolition of information
costs of fixing influenced frameworks, networks and devices
legal charges or action from misfortunes emerging from refusal of-service attacks
causing framework downtime in basic frameworks
outsider misfortunes when individual data put away on government frameworks is
utilized for criminal purposes.

Discussion on professional, legal and ethical responsibilities of IT auditor
With the emergence of exceptionally technology in the enterprise and IT tools,
auditing is the best field for those who are interested in computer networking. An IT auditor
requires to operate in a complex and challenging environment. There are various roles and
responsibilities of an IT auditor in terms of profession, legal and ethical requirements. An IT
auditor is answerable for the internal controls (IC) and dangers of an organization's
technology network or systems (Morris and et.al., 2020). This job incorporates recognizing
the shortcomings in a framework of an organization and making an activity intend to forestall
security breaches in the technology. An IT auditor can likewise be engaged with the planning
and execution of inward review strategies and the formation of internal review reports. An
evaluator must work inside a group to make a strong data IT infrastructure, and team up with
customers to devise and set up approaches and methodology with respect to organize security
issues.
The key role of IT auditor is to examine the internal control systems, determining
the design and the operational requirement of it and therefore, developing the remediation
strategies. On the professional front, troubleshooting the problems and the issues that come
across pertaining to the network problems, timely responding to the any breach in the
network system (Mann–Whitney, 2020). Complying with all the legal requirements and
ensuring that the activities are undertaken within the legal limits in order to avoid the
government intervene. Duty has been executed in an ethical manner by not indulging in any
of the unethical or illegal practices which is against the roles and responsibilities of an IT
auditor. The auditor is required to plan, design, impose and monitor the security systems
which ahs already being implemented and along with that upgrading the system from time to
time with the latest technology and ensuring that everything is working properly or not by
undertaking periodic review (La Torre and et.al., 2019). Performing the professional
practices and responsibility in an ethical way by not compromising on the user’s data and
access information. An IT auditor is required to carry out regular audit testing along with
providing recommendation on the same. Provide direction on account of how to deal with the
identified security and risks having minimal impact over the business operation. All these key
responsibilities of an IT auditor result into building an understanding among corporate and
the system procedures.
With the emergence of exceptionally technology in the enterprise and IT tools,
auditing is the best field for those who are interested in computer networking. An IT auditor
requires to operate in a complex and challenging environment. There are various roles and
responsibilities of an IT auditor in terms of profession, legal and ethical requirements. An IT
auditor is answerable for the internal controls (IC) and dangers of an organization's
technology network or systems (Morris and et.al., 2020). This job incorporates recognizing
the shortcomings in a framework of an organization and making an activity intend to forestall
security breaches in the technology. An IT auditor can likewise be engaged with the planning
and execution of inward review strategies and the formation of internal review reports. An
evaluator must work inside a group to make a strong data IT infrastructure, and team up with
customers to devise and set up approaches and methodology with respect to organize security
issues.
The key role of IT auditor is to examine the internal control systems, determining
the design and the operational requirement of it and therefore, developing the remediation
strategies. On the professional front, troubleshooting the problems and the issues that come
across pertaining to the network problems, timely responding to the any breach in the
network system (Mann–Whitney, 2020). Complying with all the legal requirements and
ensuring that the activities are undertaken within the legal limits in order to avoid the
government intervene. Duty has been executed in an ethical manner by not indulging in any
of the unethical or illegal practices which is against the roles and responsibilities of an IT
auditor. The auditor is required to plan, design, impose and monitor the security systems
which ahs already being implemented and along with that upgrading the system from time to
time with the latest technology and ensuring that everything is working properly or not by
undertaking periodic review (La Torre and et.al., 2019). Performing the professional
practices and responsibility in an ethical way by not compromising on the user’s data and
access information. An IT auditor is required to carry out regular audit testing along with
providing recommendation on the same. Provide direction on account of how to deal with the
identified security and risks having minimal impact over the business operation. All these key
responsibilities of an IT auditor result into building an understanding among corporate and
the system procedures.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CONCLUSION
It can be concluded that IT audit is a very interesting field for those who are having
the right attitude and interest in the computer networking. Based on the IT audit report carried
out by the NSW Auditor General, it can be said that there are areas where the council requires
to work on in order to ensuring and implementing for more safety and security measures
pertaining to the management of the operational system. this has helped in gaining knowledge
about how to analyse an audit report along with the application of the different frameworks
like CORBIT in order to meet with the IT governance. The NSW city council requires to
undertake relevant actions as soon as possible for meeting up with the issue of IT governance,
IT general controls and the cyber security management. There are various roles and
responsibilities of an IT auditor which helps in effectively meeting up the objective of
ensuring security, privacy, risk management along with complying the legal regulations and
working in an ethical manner.
It can be concluded that IT audit is a very interesting field for those who are having
the right attitude and interest in the computer networking. Based on the IT audit report carried
out by the NSW Auditor General, it can be said that there are areas where the council requires
to work on in order to ensuring and implementing for more safety and security measures
pertaining to the management of the operational system. this has helped in gaining knowledge
about how to analyse an audit report along with the application of the different frameworks
like CORBIT in order to meet with the IT governance. The NSW city council requires to
undertake relevant actions as soon as possible for meeting up with the issue of IT governance,
IT general controls and the cyber security management. There are various roles and
responsibilities of an IT auditor which helps in effectively meeting up the objective of
ensuring security, privacy, risk management along with complying the legal regulations and
working in an ethical manner.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and Journals
Andry, J. F. and Setiawan, A. K., 2019. IT Governance Evaluation using COBIT 5
Framework on the National Library. Jurnal Sistem Informasi. 15(1). pp.10-17.
La Torre, M., and et.al., 2019. Protecting a new Achilles heel: the role of auditors within the
practice of data protection. Managerial Auditing Journal.
Mann–Whitney, U., 2020. Research on Professional Responsibility and Ethics in
Accounting. Auditing. 112. p.114.
Morris, A., and et.al., 2020. Project management maturity levels and organizational revenue
in New South Wales local government. The Journal of Modern Project
Management. 8(2).
Nasution, D. and Östermark, R., 2019. The impact of auditors’ awareness of the profession’s
reputation for independence on auditors’ ethical judgement. Social Responsibility
Journal.
Sansom, G., 2019. Is Australian local government ready for localism?. Policy
Quarterly. 15(2).
Online
COBIT 5 ISACA's new framework. 2020. [Online]. Available Through:<
http://www.qualified-audit-partners.be/user_files/QECB_GLC_COBIT_5_ISACA_s
_new_framework_201303.pdf >.
Report on Local Government. 2019. [Online]. Available Through:<
https://www.audit.nsw.gov.au/our-work/reports/report-on-local-government-2019 >.
Books and Journals
Andry, J. F. and Setiawan, A. K., 2019. IT Governance Evaluation using COBIT 5
Framework on the National Library. Jurnal Sistem Informasi. 15(1). pp.10-17.
La Torre, M., and et.al., 2019. Protecting a new Achilles heel: the role of auditors within the
practice of data protection. Managerial Auditing Journal.
Mann–Whitney, U., 2020. Research on Professional Responsibility and Ethics in
Accounting. Auditing. 112. p.114.
Morris, A., and et.al., 2020. Project management maturity levels and organizational revenue
in New South Wales local government. The Journal of Modern Project
Management. 8(2).
Nasution, D. and Östermark, R., 2019. The impact of auditors’ awareness of the profession’s
reputation for independence on auditors’ ethical judgement. Social Responsibility
Journal.
Sansom, G., 2019. Is Australian local government ready for localism?. Policy
Quarterly. 15(2).
Online
COBIT 5 ISACA's new framework. 2020. [Online]. Available Through:<
http://www.qualified-audit-partners.be/user_files/QECB_GLC_COBIT_5_ISACA_s
_new_framework_201303.pdf >.
Report on Local Government. 2019. [Online]. Available Through:<
https://www.audit.nsw.gov.au/our-work/reports/report-on-local-government-2019 >.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





