Learning and Development Plan: Cybersecurity Career Goals and Ethics
VerifiedAdded on 2022/09/23
|14
|3604
|23
Report
AI Summary
This report outlines a comprehensive learning and development plan focused on achieving a cybersecurity career. It begins with an introduction describing the student's career goals, which include becoming a cyber security expert, and the importance of this role in the current digital landscape. The report then delves into the megatrends and challenges within the cybersecurity field, such as data breaches, the growing demand for professionals, cloud security, and the increasing risks associated with mobile devices. The student sets career goals, including acquiring expertise, leadership skills, and ethical conduct. The report emphasizes the importance of ethical values like obedience to the law, staying updated with the latest technologies, maintaining confidentiality, and practicing diligence and honesty. A competency assessment is also included, evaluating the student's managerial skills. The report concludes by discussing the future of cybersecurity, highlighting the role of artificial intelligence and the need for continuous professional development. The student plans to stay updated with current professional codes of ethics and emerging technologies to ensure high security standards. The report reflects on the significance of self-assessment and career development in managing various aspects of professional life and cybersecurity.

Learning and Development Plan 1
Learning and Development Plan
By (Student’s Name)
Name of the course
Instructor’s Name
Institutional Affiliation
Department
Date
Learning and Development Plan
By (Student’s Name)
Name of the course
Instructor’s Name
Institutional Affiliation
Department
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Learning and Development Plan 2
Introduction
My career goal is to become an expert in cyber security. Almost every company
around the globe requires experts in the area of Information and communication technology.
It is estimated that since 2011, the amount of data that businesses have had to deal with has
been doubling every 40 months (Dua and Du, 2016). This phenomenon has given rise to the
area of big data analytics. Whenever such vast amounts of information are being exchanged,
security becomes an important component. My career aim is to become a cyber security
expert. The main role of such an expert is to ensure that data is protected from various kinds
of threats such as illegal access. In the modern days, it is very easy to learn online. I have
been learning various cyber security skills online. Although, I am not yet a professional when
it comes to this area, I am doing my best to ensure that I gain all the appropriate skills to
become a cyber security expert. These experts are in high demand across the globe (Fielder et
al, 2016). Since I am passionate about Information Technology and Cybersecurity, I will
leave no stone unturned to ensure that I become a professional in this area. Currently, I am
undertaking a Masters of Business and Project. There are many skills that I have gained in
this course that will help me become a better manger at my cyber security career.
Particularly, the leadership and professional ethics that I am learning in this course will come
in handy to help me become a better security expert. Leadership skills are very important for
any person who wishes to become successful in their career (Swierstra, 2017). I appreciate
that I will have to interact with various people in the journey of my career. To be able to
interact with them well, it is important to establish an elaborate and explicit learning and
development plan. In addition, it is important to analyse my strengths, weaknesses,
opportunities and threats. A SWOT analysis is important in helping discover the strong areas
and those that need improvement.
Introduction
My career goal is to become an expert in cyber security. Almost every company
around the globe requires experts in the area of Information and communication technology.
It is estimated that since 2011, the amount of data that businesses have had to deal with has
been doubling every 40 months (Dua and Du, 2016). This phenomenon has given rise to the
area of big data analytics. Whenever such vast amounts of information are being exchanged,
security becomes an important component. My career aim is to become a cyber security
expert. The main role of such an expert is to ensure that data is protected from various kinds
of threats such as illegal access. In the modern days, it is very easy to learn online. I have
been learning various cyber security skills online. Although, I am not yet a professional when
it comes to this area, I am doing my best to ensure that I gain all the appropriate skills to
become a cyber security expert. These experts are in high demand across the globe (Fielder et
al, 2016). Since I am passionate about Information Technology and Cybersecurity, I will
leave no stone unturned to ensure that I become a professional in this area. Currently, I am
undertaking a Masters of Business and Project. There are many skills that I have gained in
this course that will help me become a better manger at my cyber security career.
Particularly, the leadership and professional ethics that I am learning in this course will come
in handy to help me become a better security expert. Leadership skills are very important for
any person who wishes to become successful in their career (Swierstra, 2017). I appreciate
that I will have to interact with various people in the journey of my career. To be able to
interact with them well, it is important to establish an elaborate and explicit learning and
development plan. In addition, it is important to analyse my strengths, weaknesses,
opportunities and threats. A SWOT analysis is important in helping discover the strong areas
and those that need improvement.

Learning and Development Plan 3
Megatrends and Challenges in Cyber Security
There have been various trends in the field of cyber security in the last few years.
First, data breaches have become a major security concern both locally and internationally.
Due to increased data breaches, companies and other organization have has to rethink their
planning concerning management of data (Hubbard and Seiersen, 2016). The focus has been
on ensuring that there are mechanisms in place to ensure that security of personal data is
maintained. Data breaches may lead to great losses while it may portray the image of
companies or organizations in negative light (Tavani, 2016). Flaws in web application apps
has been identified as the major source of security breaches (Kreutzer, Neugebauer and
Pattloch, 2017). Consequently, ensuring that there are no such flaws has become one of the
top priorities for most organizations.
In the last few years, a growing need for cyber security professionals has been a major
trend. This need is being experienced both locally and internationally. For instance, it is
estimated that Australia will need an additional 18000 cyber security experts by the year 2026
(McCormac et al, 2017). At both the local and international arena, the demand for cyber
security experts is more than the supply (Zhu et al, 2017). It is worrying that there are not
enough cyber security professionals in the wake of increased threats for data breaches and
cybercrimes (Putra and Cho, 2019). It is estimated that as many as 2 in every 3 organizations
in the world have a shortage of IT security staff (Newhouse et al, 2016). The shortage has led
to deployment of automated online security tools in most organizations to ensure that data is
protected (Marchewka, 2016). Therefore, as a far as competition is concerned, a cyber
security expert with the appropriate competencies is unlikely to be competing for a job.
Cloud security is another trending issue in the cyber security profession. It is
important to note that most businesses are transferring most of their data to cloud storage
Megatrends and Challenges in Cyber Security
There have been various trends in the field of cyber security in the last few years.
First, data breaches have become a major security concern both locally and internationally.
Due to increased data breaches, companies and other organization have has to rethink their
planning concerning management of data (Hubbard and Seiersen, 2016). The focus has been
on ensuring that there are mechanisms in place to ensure that security of personal data is
maintained. Data breaches may lead to great losses while it may portray the image of
companies or organizations in negative light (Tavani, 2016). Flaws in web application apps
has been identified as the major source of security breaches (Kreutzer, Neugebauer and
Pattloch, 2017). Consequently, ensuring that there are no such flaws has become one of the
top priorities for most organizations.
In the last few years, a growing need for cyber security professionals has been a major
trend. This need is being experienced both locally and internationally. For instance, it is
estimated that Australia will need an additional 18000 cyber security experts by the year 2026
(McCormac et al, 2017). At both the local and international arena, the demand for cyber
security experts is more than the supply (Zhu et al, 2017). It is worrying that there are not
enough cyber security professionals in the wake of increased threats for data breaches and
cybercrimes (Putra and Cho, 2019). It is estimated that as many as 2 in every 3 organizations
in the world have a shortage of IT security staff (Newhouse et al, 2016). The shortage has led
to deployment of automated online security tools in most organizations to ensure that data is
protected (Marchewka, 2016). Therefore, as a far as competition is concerned, a cyber
security expert with the appropriate competencies is unlikely to be competing for a job.
Cloud security is another trending issue in the cyber security profession. It is
important to note that most businesses are transferring most of their data to cloud storage
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Learning and Development Plan 4
(Steinhouse, 2017). Cloud storage offers great amounts of data storage and is less costly that
the traditional methods of data storage (Mikolic et al 2017). With cloud storage, companies
can store data in terabytes and exabytes. However, with the implementation of cloud storage,
it has become increasingly important to ensure that there are new approaches to ensure data
security (Winch 2020). Cloud storage poses relatively new challenges and it is important to
for organizations to have cyber security experts to help ensure that data breaches are
minimised or completely eradicated (Schneider and Gersting, 2018). In the light of this, it
would be true to conclude that investment in cloud storage comes with subsequent investment
in cyber security expertise.
There has been an increase in the awareness of importance of cyber security. With
immense digital transformation in most industries, both locally and internationally, there has
been an increased awareness in the important role of cyber security (Gupta, Agrawal and
Yamaguchi, 2016). Businesses, both small and large have appreciated that employing cyber
security professionals is not important but vital in the success of their businesses (Peterson,
2017). Technological advancements are taking place at an unprecedent rate (Vallor, Green
and Raicu, 2018). Therefore, businesses have to adapt to these changes if they are to remain
relevant and competitive. The cost of employing cyber security experts is less compared to
the threat that exists if there are no such professionals in organizations (Peterson, 2018). This
phenomenon could help explain why there is a high demand for cyber security professionals.
Lastly, mobile devices have become a major cyber security risk. The number of
people who use mobile phones has been increasing and projected to continue increasing. This
increase has been observed both at the local level and around the globe. The rise of the
number of mobile phones has led to a consequent increase in the amount of business
information stored in the devices. Consequently, there has been increased malware attacks
targeting mobile phone which could put both business and personal data at risk of being
(Steinhouse, 2017). Cloud storage offers great amounts of data storage and is less costly that
the traditional methods of data storage (Mikolic et al 2017). With cloud storage, companies
can store data in terabytes and exabytes. However, with the implementation of cloud storage,
it has become increasingly important to ensure that there are new approaches to ensure data
security (Winch 2020). Cloud storage poses relatively new challenges and it is important to
for organizations to have cyber security experts to help ensure that data breaches are
minimised or completely eradicated (Schneider and Gersting, 2018). In the light of this, it
would be true to conclude that investment in cloud storage comes with subsequent investment
in cyber security expertise.
There has been an increase in the awareness of importance of cyber security. With
immense digital transformation in most industries, both locally and internationally, there has
been an increased awareness in the important role of cyber security (Gupta, Agrawal and
Yamaguchi, 2016). Businesses, both small and large have appreciated that employing cyber
security professionals is not important but vital in the success of their businesses (Peterson,
2017). Technological advancements are taking place at an unprecedent rate (Vallor, Green
and Raicu, 2018). Therefore, businesses have to adapt to these changes if they are to remain
relevant and competitive. The cost of employing cyber security experts is less compared to
the threat that exists if there are no such professionals in organizations (Peterson, 2018). This
phenomenon could help explain why there is a high demand for cyber security professionals.
Lastly, mobile devices have become a major cyber security risk. The number of
people who use mobile phones has been increasing and projected to continue increasing. This
increase has been observed both at the local level and around the globe. The rise of the
number of mobile phones has led to a consequent increase in the amount of business
information stored in the devices. Consequently, there has been increased malware attacks
targeting mobile phone which could put both business and personal data at risk of being
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Learning and Development Plan 5
breached (Mendel, 2017). To enhance protection, cyber security professionals are developing
various systems. One example of this is the real time vulnerability management which can
detect and prevent a security breach in real time. In the light of the above trends, it is true to
conclude that there are many challenges and improvements needed in as far as cyber security
is concerned.
Goals
Forecasting into the near future, I see myself as an experienced cyber security
professional who has the ability to equip companies with the tools and sills necessary to deal
with cyber threats. The sort of expectation that businesses and organizations would have on
me is to ensure that their data is as safe as possible from any kind of cyber threat. Employer/
clients have various goals when it comes to cyber security. First, they need experts who can
create appropriate web-based tools to keep their data in check and prevent any form of
security threat. Since a great deal of data is shared online, companies need an implantation of
web tools that can help ensure security. In addition, employers expect that a cyber security
professional will help train their employees on what they can do to prevent data breaches.
When employees are trained on appropriate ways of ensuring data protection, the work of the
cyber security professional is eased and the probability of a security breach is tremendously
reduced.
I have several career goals. First, I aim to become a cyber security expert within the
next three years. I plan to achieve this through enrolling for a course on the same. In addition,
I will carry out a lot of learning online since there is plenty of information and courses on
cyber security. In addition to becoming an expert, I also aim possess appropriate leadership
skills. I know that leadership skills are vital in the success of my career. I plan to achieve this
through putting into practice the skills I am learning at college. With leadership skills, it will
breached (Mendel, 2017). To enhance protection, cyber security professionals are developing
various systems. One example of this is the real time vulnerability management which can
detect and prevent a security breach in real time. In the light of the above trends, it is true to
conclude that there are many challenges and improvements needed in as far as cyber security
is concerned.
Goals
Forecasting into the near future, I see myself as an experienced cyber security
professional who has the ability to equip companies with the tools and sills necessary to deal
with cyber threats. The sort of expectation that businesses and organizations would have on
me is to ensure that their data is as safe as possible from any kind of cyber threat. Employer/
clients have various goals when it comes to cyber security. First, they need experts who can
create appropriate web-based tools to keep their data in check and prevent any form of
security threat. Since a great deal of data is shared online, companies need an implantation of
web tools that can help ensure security. In addition, employers expect that a cyber security
professional will help train their employees on what they can do to prevent data breaches.
When employees are trained on appropriate ways of ensuring data protection, the work of the
cyber security professional is eased and the probability of a security breach is tremendously
reduced.
I have several career goals. First, I aim to become a cyber security expert within the
next three years. I plan to achieve this through enrolling for a course on the same. In addition,
I will carry out a lot of learning online since there is plenty of information and courses on
cyber security. In addition to becoming an expert, I also aim possess appropriate leadership
skills. I know that leadership skills are vital in the success of my career. I plan to achieve this
through putting into practice the skills I am learning at college. With leadership skills, it will

Learning and Development Plan 6
be easy to interact well with different kinds of people. Such interactions are also likely to be
productive and fruitful. To further enhance these skills, I plan to enrol in a short leadership
course within the next three years. The other main career goal that I have is to be an ethical
cyber security expert. As a cyber security expert, I will have access to a lot of information,
some of which will be private. It is important to act ethically and ensure confidentiality is
always ensured. To improve my competence when it comes to ethics, I will be sure to abide
by ethical standards for cyber security professionals, both locally and internationally. Ethical
behaviour is paramount and it is important to endeavour to be ethical.
Ethics and Professional Values
One the values that consider appropriate for a cyber security professional is
obedience to the law. As a professional, it is only ethical to ensure that I abide
by all applicable laws, both local and international. Failure to observe the laid-
out laws is unethical and may amount to a crime which can attract a penalty in
a court of law.
Being up to date with the relevant developments in cyber security is another
important value. The advantage of being up to date is that it will help
implement the latest technologies in data protections. Newer technologies are
usually better and more efficient than older ones. Therefore, I owe it to my
clients/ employers to ensure that I am implementing the best technologies in
the market. It is ethical for a cyber security professional to carry out their work
on the basis of the accepted and current best practices.
Confidentiality is a value that I consider key to building trust. I must always
ensure confidentiality of the data I come across when working with clients/
be easy to interact well with different kinds of people. Such interactions are also likely to be
productive and fruitful. To further enhance these skills, I plan to enrol in a short leadership
course within the next three years. The other main career goal that I have is to be an ethical
cyber security expert. As a cyber security expert, I will have access to a lot of information,
some of which will be private. It is important to act ethically and ensure confidentiality is
always ensured. To improve my competence when it comes to ethics, I will be sure to abide
by ethical standards for cyber security professionals, both locally and internationally. Ethical
behaviour is paramount and it is important to endeavour to be ethical.
Ethics and Professional Values
One the values that consider appropriate for a cyber security professional is
obedience to the law. As a professional, it is only ethical to ensure that I abide
by all applicable laws, both local and international. Failure to observe the laid-
out laws is unethical and may amount to a crime which can attract a penalty in
a court of law.
Being up to date with the relevant developments in cyber security is another
important value. The advantage of being up to date is that it will help
implement the latest technologies in data protections. Newer technologies are
usually better and more efficient than older ones. Therefore, I owe it to my
clients/ employers to ensure that I am implementing the best technologies in
the market. It is ethical for a cyber security professional to carry out their work
on the basis of the accepted and current best practices.
Confidentiality is a value that I consider key to building trust. I must always
ensure confidentiality of the data I come across when working with clients/
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Learning and Development Plan 7
organizations. One of the ethical standards for cyber security and most other
professionals is to ensure that confidentiality is maintained.
Diligence and honesty are important for a cyber security professional. In case
of a threat or any development, it is essential for a cyber security professional
to ensure that the same is shared with the relevant persons/ teams in a manner
that is honest. It is quite unethical to cover up for a threat since it could lead to
great losses.
The future of cyber security is one with more challenges but also one with better
technologies. Most companies will be running knowledge-based systems in the future. With
artificial intelligence, there will be better ways of dealing with threats since computers will be
programmed to think like human beings. To promote ethics in the future, I will keep myself
up to date with current professional code of ethics and any revisions that may be made in the
future. In addition, I will keep myself up to date with the emerging cyber security
technologies so that I can ensure high security standards for my clients/ employers.
Competency Assessment
Competency Level
Managerial Conscious Competence (Stage 3)
There are several reasons why I feels that I
am the level of conscious competence. First,
although I command knowledge in various
managerial skills, I am yet to put them into
thorough practice. For instance, one of the
roles of a manager is to ensure that set goals
organizations. One of the ethical standards for cyber security and most other
professionals is to ensure that confidentiality is maintained.
Diligence and honesty are important for a cyber security professional. In case
of a threat or any development, it is essential for a cyber security professional
to ensure that the same is shared with the relevant persons/ teams in a manner
that is honest. It is quite unethical to cover up for a threat since it could lead to
great losses.
The future of cyber security is one with more challenges but also one with better
technologies. Most companies will be running knowledge-based systems in the future. With
artificial intelligence, there will be better ways of dealing with threats since computers will be
programmed to think like human beings. To promote ethics in the future, I will keep myself
up to date with current professional code of ethics and any revisions that may be made in the
future. In addition, I will keep myself up to date with the emerging cyber security
technologies so that I can ensure high security standards for my clients/ employers.
Competency Assessment
Competency Level
Managerial Conscious Competence (Stage 3)
There are several reasons why I feels that I
am the level of conscious competence. First,
although I command knowledge in various
managerial skills, I am yet to put them into
thorough practice. For instance, one of the
roles of a manager is to ensure that set goals
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Learning and Development Plan 8
are being achieved. There are times I have
been placed in charge of group work in
college. We set goals, and although they are
achieved, they are not achieved within the
timelines achieved. Sometimes, it is also not
an easy to task to command group members
to focus more on the objectives of the
group. Therefore, I still got some learning to
do. To ensure that I have a shared
competence, I will ensure that I do
appropriate practice. With experience, it
will be easier to achieve this.
Leadership Unconscious Competence (Stage 4)
The main role of a leader is to convince
people into buying a vision. The leader then
leads the way for the others to follow. As
far as this is concerned, I would consider
myself as having stage 4 competency. I have
held various leadership positions both in
high school, university and other areas. I
have had the ability to influence those I am
leading into taking a certain course of
direction. I am quite eloquent and chose
words well to achieve this. Even with my
friends, I am able to influence them take a
are being achieved. There are times I have
been placed in charge of group work in
college. We set goals, and although they are
achieved, they are not achieved within the
timelines achieved. Sometimes, it is also not
an easy to task to command group members
to focus more on the objectives of the
group. Therefore, I still got some learning to
do. To ensure that I have a shared
competence, I will ensure that I do
appropriate practice. With experience, it
will be easier to achieve this.
Leadership Unconscious Competence (Stage 4)
The main role of a leader is to convince
people into buying a vision. The leader then
leads the way for the others to follow. As
far as this is concerned, I would consider
myself as having stage 4 competency. I have
held various leadership positions both in
high school, university and other areas. I
have had the ability to influence those I am
leading into taking a certain course of
direction. I am quite eloquent and chose
words well to achieve this. Even with my
friends, I am able to influence them take a

Learning and Development Plan 9
certain course action with a lot of ease.
To achieve stage 5 competence, I am
planning to take a leadership course within
the next three years.
Socio-cultural Conscious competence (stage 2)
While I know that having appropriate socio-
cultural interaction skills is important, I
appreciate that I have a lot of learning to do.
I find it somewhat hard to interact with
people from different cultural or social
backgrounds. I am working on this to ensure
that I become a global citizen who can
interact with people from any part of the
world in the future. To achieve this, I will
work more on my emotional intelligence
and other sociocultural skills.
Personal Unconscious Competence (stage 4)
I have invested a great deal of time and
resources in an attempt to know myself. I
have well laid out personal goals and
ambitions and I am consistently working
towards their achievement. I however have
some weak areas that prevent me from
having level 5 competency. An example is
the lack of socio-cultural skills. As
certain course action with a lot of ease.
To achieve stage 5 competence, I am
planning to take a leadership course within
the next three years.
Socio-cultural Conscious competence (stage 2)
While I know that having appropriate socio-
cultural interaction skills is important, I
appreciate that I have a lot of learning to do.
I find it somewhat hard to interact with
people from different cultural or social
backgrounds. I am working on this to ensure
that I become a global citizen who can
interact with people from any part of the
world in the future. To achieve this, I will
work more on my emotional intelligence
and other sociocultural skills.
Personal Unconscious Competence (stage 4)
I have invested a great deal of time and
resources in an attempt to know myself. I
have well laid out personal goals and
ambitions and I am consistently working
towards their achievement. I however have
some weak areas that prevent me from
having level 5 competency. An example is
the lack of socio-cultural skills. As
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Learning and Development Plan 10
explained above I am working on the same
so that I can achieve a stage 5 competency
in future.
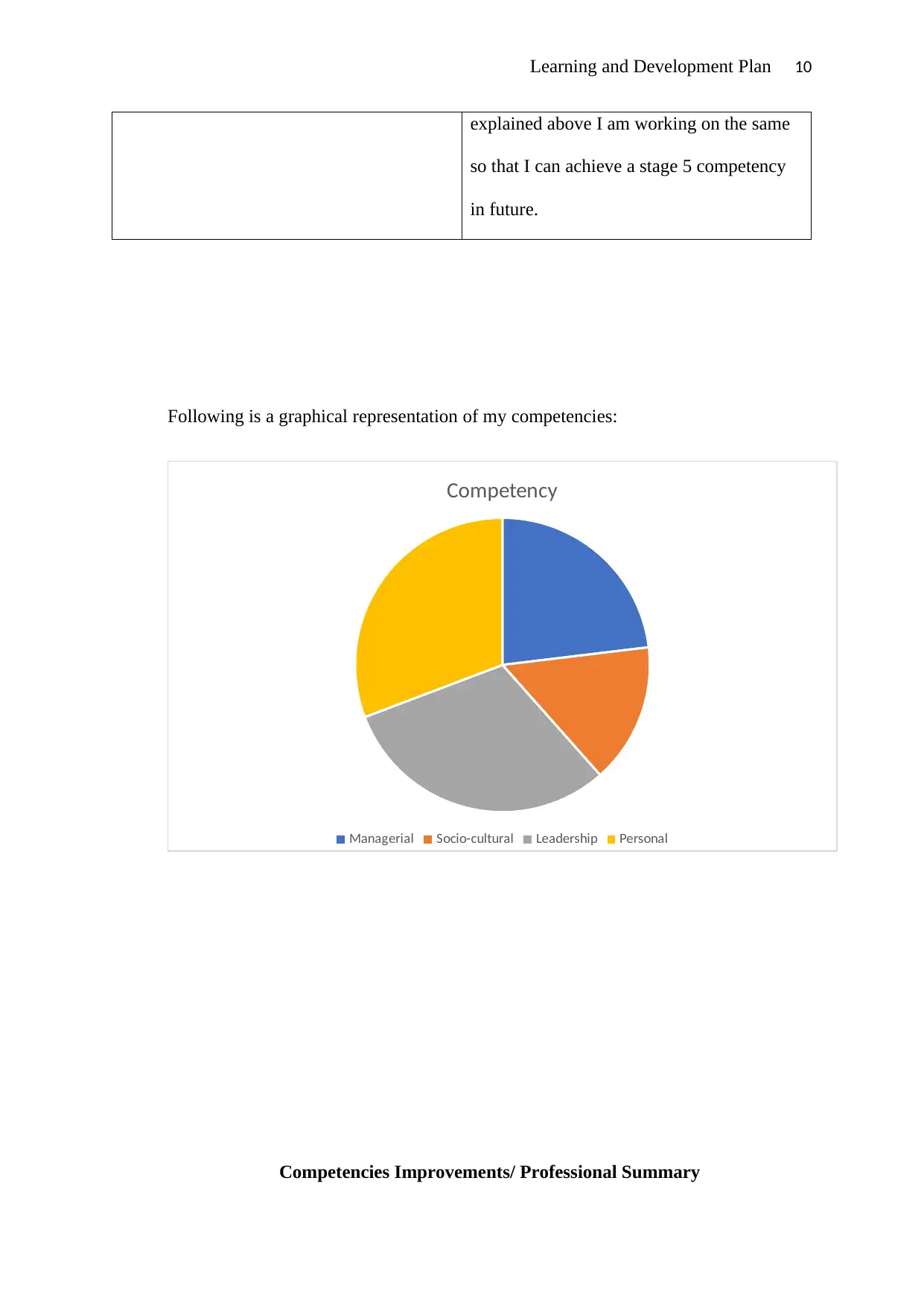
Following is a graphical representation of my competencies:
Competency
Managerial Socio-cultural Leadership Personal
Competencies Improvements/ Professional Summary
explained above I am working on the same
so that I can achieve a stage 5 competency
in future.
Following is a graphical representation of my competencies:
Competency
Managerial Socio-cultural Leadership Personal
Competencies Improvements/ Professional Summary
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Learning and Development Plan 11
I wish to improve on managerial and sociocultural competencies. Managerial
competence is very important since I will need to manage people sometimes now and even
more frequently in the future. To ensure that I improve on this skill, I will improve on such
skills as being assertive, emotionally intelligent and strategic planning skills. There exists
extensive evidence to show that managers who have these qualities are more likely to succeed
in achieving set goals compared to those who are not. While appreciating that I need to
improve on my managerial skills, it is also important to note that I am more inclined towards
being a leader rather than a manager. When it comes to the socio-cultural competency, I am
reading various books on the same. In addition, I am planning to watch movies and
documentaries of that have people from different socio-cultural backgrounds so that I can
have a glimpse of other cultures. Here at the university, I am learning to build good
relationships with different people.
There are different industries and projects that may help me gain the competencies
explained above. One way to gain both is team works, for instance group discussions here in
school. More than often, I am appointed by team members to manage the group. Team work
will provide me an opportunity to practice managerial skills as well as interact with people
from different socio-cultural backgrounds. In addition, my future career as a cyber security
will grant me a chance to travel and interact with people from various parts of the country
and even around the world. Such interactions will surely help me increase my competency. In
addition, I plan to open a cyber security firm. Since, I will be one of the people at top
positions within the firm, I will gain appropriate skills on management. The position will
therefore help me improve on my managerial competency.
References
I wish to improve on managerial and sociocultural competencies. Managerial
competence is very important since I will need to manage people sometimes now and even
more frequently in the future. To ensure that I improve on this skill, I will improve on such
skills as being assertive, emotionally intelligent and strategic planning skills. There exists
extensive evidence to show that managers who have these qualities are more likely to succeed
in achieving set goals compared to those who are not. While appreciating that I need to
improve on my managerial skills, it is also important to note that I am more inclined towards
being a leader rather than a manager. When it comes to the socio-cultural competency, I am
reading various books on the same. In addition, I am planning to watch movies and
documentaries of that have people from different socio-cultural backgrounds so that I can
have a glimpse of other cultures. Here at the university, I am learning to build good
relationships with different people.
There are different industries and projects that may help me gain the competencies
explained above. One way to gain both is team works, for instance group discussions here in
school. More than often, I am appointed by team members to manage the group. Team work
will provide me an opportunity to practice managerial skills as well as interact with people
from different socio-cultural backgrounds. In addition, my future career as a cyber security
will grant me a chance to travel and interact with people from various parts of the country
and even around the world. Such interactions will surely help me increase my competency. In
addition, I plan to open a cyber security firm. Since, I will be one of the people at top
positions within the firm, I will gain appropriate skills on management. The position will
therefore help me improve on my managerial competency.
References

Learning and Development Plan 12
Dua, S. and Du, X. (2016). Data mining and machine learning in cybersecurity. 3rd
ed. New York: CRC press.
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F. (2016).
Decision support approaches for cyber security investment. Decision support systems.
86(1), pp.13-23.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds. (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. 4th ed.
Pennsylvania: IGI global.
Hubbard, D.W. and Seiersen, R. (2016). How to measure anything in cybersecurity
risk. 5th ed. New York: John Wiley & Sons.
Kreutzer, R.T., Neugebauer, T. and Pattloch, A. (2017). Digital business leadership.
Digital Transformation–Geschäftsmodell-Innovation–agile Organisation–Change-
Management. 78(4), pp 7-21.
Marchewka, J.T. (2016). Information technology project management: Providing
measurable organizational value. 7th ed. New York: John Wiley & Sons.
McCormac, A., Calic, D., Butavicius, M., Parsons, K., Zwaans, T. and Pattinson, M.,
(2017). A reliable measure of information security awareness and the identification of
bias in responses. Australasian Journal of Information Systems. 21(3), pp 56-77.
Mendel, J. (2017). Smart grid cyber security challenges: Overview and classification.
e-mentor, 68(1), pp.55-66.
Mikolic-Torreira, I., Snyder, D., Price, M., Shlapak, D.A., Beaghley, S.M., Bishop,
M., Harting, S.J., Oberholtzer, J., Pettyjohn, S., Weinbaum, C. and Westerman, E.
Dua, S. and Du, X. (2016). Data mining and machine learning in cybersecurity. 3rd
ed. New York: CRC press.
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F. (2016).
Decision support approaches for cyber security investment. Decision support systems.
86(1), pp.13-23.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds. (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. 4th ed.
Pennsylvania: IGI global.
Hubbard, D.W. and Seiersen, R. (2016). How to measure anything in cybersecurity
risk. 5th ed. New York: John Wiley & Sons.
Kreutzer, R.T., Neugebauer, T. and Pattloch, A. (2017). Digital business leadership.
Digital Transformation–Geschäftsmodell-Innovation–agile Organisation–Change-
Management. 78(4), pp 7-21.
Marchewka, J.T. (2016). Information technology project management: Providing
measurable organizational value. 7th ed. New York: John Wiley & Sons.
McCormac, A., Calic, D., Butavicius, M., Parsons, K., Zwaans, T. and Pattinson, M.,
(2017). A reliable measure of information security awareness and the identification of
bias in responses. Australasian Journal of Information Systems. 21(3), pp 56-77.
Mendel, J. (2017). Smart grid cyber security challenges: Overview and classification.
e-mentor, 68(1), pp.55-66.
Mikolic-Torreira, I., Snyder, D., Price, M., Shlapak, D.A., Beaghley, S.M., Bishop,
M., Harting, S.J., Oberholtzer, J., Pettyjohn, S., Weinbaum, C. and Westerman, E.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





