Detailed Penetration Testing Report: Cybersecurity Analysis Project
VerifiedAdded on 2023/01/18
|26
|2681
|31
Report
AI Summary
This report details a penetration testing exercise conducted using Kali Linux and Metasploit. The project begins with an overview of penetration testing methodologies, including intelligence gathering, threat modeling, and vulnerability analysis. The report then outlines the steps taken to set up the testing environment, including network configuration. The core of the report covers the practical execution of penetration tests, including information gathering with Nmap, scanning and enumeration techniques. The report then delves into vulnerability exploitation, discussing command injection, outdated applications, and insecure communication channels. Finally, the report addresses vulnerability mitigation strategies, emphasizing the importance of input validation, application updates, and system hardening to secure the target systems. The report concludes with reflections on the process and the importance of proactive cybersecurity measures.

University
Semester
PENETRATION TESTING
Student ID
Student Name
Submission Date
Semester
PENETRATION TESTING
Student ID
Student Name
Submission Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 2 SOP for Pen - Testing................................................................................................................3
1. Pen Test Methodology Discussion.............................................................................................3
2. SOP for Pen Testing..................................................................................................................3
3. Decision Making Tree................................................................................................................5
Task 3 - Penetration Test......................................................................................................................5
3.1 Attacking Narrative...............................................................................................................5
3.2 Information Gathering........................................................................................................18
3.3 Scanning and Enumeration.................................................................................................19
3.4 Vulnerability Exploiting......................................................................................................22
3.5 Vulnerability Mitigation......................................................................................................22
Conclusions and Reflections...............................................................................................................24
References...........................................................................................................................................25
Task 2 SOP for Pen - Testing................................................................................................................3
1. Pen Test Methodology Discussion.............................................................................................3
2. SOP for Pen Testing..................................................................................................................3
3. Decision Making Tree................................................................................................................5
Task 3 - Penetration Test......................................................................................................................5
3.1 Attacking Narrative...............................................................................................................5
3.2 Information Gathering........................................................................................................18
3.3 Scanning and Enumeration.................................................................................................19
3.4 Vulnerability Exploiting......................................................................................................22
3.5 Vulnerability Mitigation......................................................................................................22
Conclusions and Reflections...............................................................................................................24
References...........................................................................................................................................25

Task 2 SOP for Pen - Testing
In this project, we shall be creating a SOP (Standard Operating Procedure), and then do the
test comparisons between the various Penetration Testing techniques. We shall describe the
below given various stages of a Decision making tree,
Vulnerability Analysis
Intelligence Gathering
Vulnerability Identification
Target Exploitation
Post exploitation
All the above shall be discussed further.
1. Pen Test Methodology Discussion
“Penetration Testing”, popularly called as “Pen Testing” or “Ethical Hacking”, is the
practice of examining a computer system, network, mobile application, developing software’s,
online tools, or web application for locating security vulnerabilities and safety soft spots that an
potential attacker might exploit. Penetration testing can carried out both, by automation with
software applications or performed manually.
Pentest tools can scan codes for checking the possibility of a malicious code present that may
lead to the likelihood of safety & security breach. Pentest tools can examine the security
loopholes of a given system by testing the data encryption procedures and determining the hard-
coded parameters for example the password/ username. The Penetration Test types includes the
following types,
1. Social Engineering Test:
2. Web Application Test
3. Physical Penetration Test
In this project, we shall be creating a SOP (Standard Operating Procedure), and then do the
test comparisons between the various Penetration Testing techniques. We shall describe the
below given various stages of a Decision making tree,
Vulnerability Analysis
Intelligence Gathering
Vulnerability Identification
Target Exploitation
Post exploitation
All the above shall be discussed further.
1. Pen Test Methodology Discussion
“Penetration Testing”, popularly called as “Pen Testing” or “Ethical Hacking”, is the
practice of examining a computer system, network, mobile application, developing software’s,
online tools, or web application for locating security vulnerabilities and safety soft spots that an
potential attacker might exploit. Penetration testing can carried out both, by automation with
software applications or performed manually.
Pentest tools can scan codes for checking the possibility of a malicious code present that may
lead to the likelihood of safety & security breach. Pentest tools can examine the security
loopholes of a given system by testing the data encryption procedures and determining the hard-
coded parameters for example the password/ username. The Penetration Test types includes the
following types,
1. Social Engineering Test:
2. Web Application Test
3. Physical Penetration Test
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4. Network Services Test:
5. Client-side test
6. Remote dial-up war dial:
7. Wireless security test
During the process of the Pen Testing, all the devise under examination shall undergo the
exploitation of their safety parameters like firewalls to, analyse the potential vulnerabilities and
linked risks that will put the entire system to further damages.
The below given stages are for the penetration test of SOP (Berdeaux, 2014),
Intelligence Gathering
Exploitation
Vulnerability Analysis
Threat Modelling
Reporting
2. SOP for Pen Testing
Below are the different stages as part of the testing by using the SOP for Pen Testing is used,
Intelligence gathering
By collecting the data intelligence and data assistance in the actions of the
assessment, this stage is utilized for handling the assessment action. Assisting in the aid of
getting the vital access to the vital data and intelligent information related to the target,
intelligence collection is carried out for the sole purpose of gathering all the necessary data
and information about the organizations staff and workers.
Threat Modelling
In this stage, we shall consider the alternate routes which can be utilized for
avoiding and reduction of the after affects in the system organization, thus in this stage
we will be able to recognize the criteria for vulnerability in keeping the efficiency of the
security of the network. For maintaining the security level in the system, threat modeling
is utilized for identifying the best methodology in keeping the security at its highest level.
5. Client-side test
6. Remote dial-up war dial:
7. Wireless security test
During the process of the Pen Testing, all the devise under examination shall undergo the
exploitation of their safety parameters like firewalls to, analyse the potential vulnerabilities and
linked risks that will put the entire system to further damages.
The below given stages are for the penetration test of SOP (Berdeaux, 2014),
Intelligence Gathering
Exploitation
Vulnerability Analysis
Threat Modelling
Reporting
2. SOP for Pen Testing
Below are the different stages as part of the testing by using the SOP for Pen Testing is used,
Intelligence gathering
By collecting the data intelligence and data assistance in the actions of the
assessment, this stage is utilized for handling the assessment action. Assisting in the aid of
getting the vital access to the vital data and intelligent information related to the target,
intelligence collection is carried out for the sole purpose of gathering all the necessary data
and information about the organizations staff and workers.
Threat Modelling
In this stage, we shall consider the alternate routes which can be utilized for
avoiding and reduction of the after affects in the system organization, thus in this stage
we will be able to recognize the criteria for vulnerability in keeping the efficiency of the
security of the network. For maintaining the security level in the system, threat modeling
is utilized for identifying the best methodology in keeping the security at its highest level.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Vulnerability analysis
For recognizing and analysing the risks possibilities for the safety and security by
knowing the systems vulnerabilities, we shall make use of the vulnerability evaluation
and this again is divided into two subsets, vulnerability validation and vulnerability
identification. The difference between these two vulnerability evaluations is,
“Vulnerability Identification” shall be utilised for identifying the vulnerability and
this remains the main goal for the analysis of vulnerabilities.
“Vulnerability Validation” shall be utilized for the reduction is used to reduce and
pick up only those vulnerabilities that are actual affecting the system.
Exploitation
In this stage, we shall look at the breaching of the security of the system and how
this is exploited by recognizing the system vulnerabilities by making use of the
“Vulnerability Analysis”. Now, to make sure that the identified vulnerabilities are
actually exploitable for the system, we shall carry out the “System Exploitation”
procedure for the exploitation of system vulnerability. As this involves complicated
procedures and also intensive manual testing methodologies within the system, it is a
time consuming process. Some of the methods used are SQL injection technique,
Overflow method, OS commending etc.
Post Exploitation
The term “Post Exploitation” is used for the stages for the operation when the
users system has been breached by an attacker. To understand as to how will the attacker
utilizes the information for malicious reasons; the worth of the breached system is
calculated by the worth of the actual data stored in it.
Reporting
The organization whose system has been breached will make use of the reporting phase as to
locate and know as to the vulnerabilities which can be acceptable and understood. To get the
same impact, it shall also consider the deficiencies that let an attacker to exploit the explicit
For recognizing and analysing the risks possibilities for the safety and security by
knowing the systems vulnerabilities, we shall make use of the vulnerability evaluation
and this again is divided into two subsets, vulnerability validation and vulnerability
identification. The difference between these two vulnerability evaluations is,
“Vulnerability Identification” shall be utilised for identifying the vulnerability and
this remains the main goal for the analysis of vulnerabilities.
“Vulnerability Validation” shall be utilized for the reduction is used to reduce and
pick up only those vulnerabilities that are actual affecting the system.
Exploitation
In this stage, we shall look at the breaching of the security of the system and how
this is exploited by recognizing the system vulnerabilities by making use of the
“Vulnerability Analysis”. Now, to make sure that the identified vulnerabilities are
actually exploitable for the system, we shall carry out the “System Exploitation”
procedure for the exploitation of system vulnerability. As this involves complicated
procedures and also intensive manual testing methodologies within the system, it is a
time consuming process. Some of the methods used are SQL injection technique,
Overflow method, OS commending etc.
Post Exploitation
The term “Post Exploitation” is used for the stages for the operation when the
users system has been breached by an attacker. To understand as to how will the attacker
utilizes the information for malicious reasons; the worth of the breached system is
calculated by the worth of the actual data stored in it.
Reporting
The organization whose system has been breached will make use of the reporting phase as to
locate and know as to the vulnerabilities which can be acceptable and understood. To get the
same impact, it shall also consider the deficiencies that let an attacker to exploit the explicit
security policy for getting the same type of impact. As along with the normal system
operations vulnerabilities, it shall also be utilised for gaining entry at higher levels or
interferes.
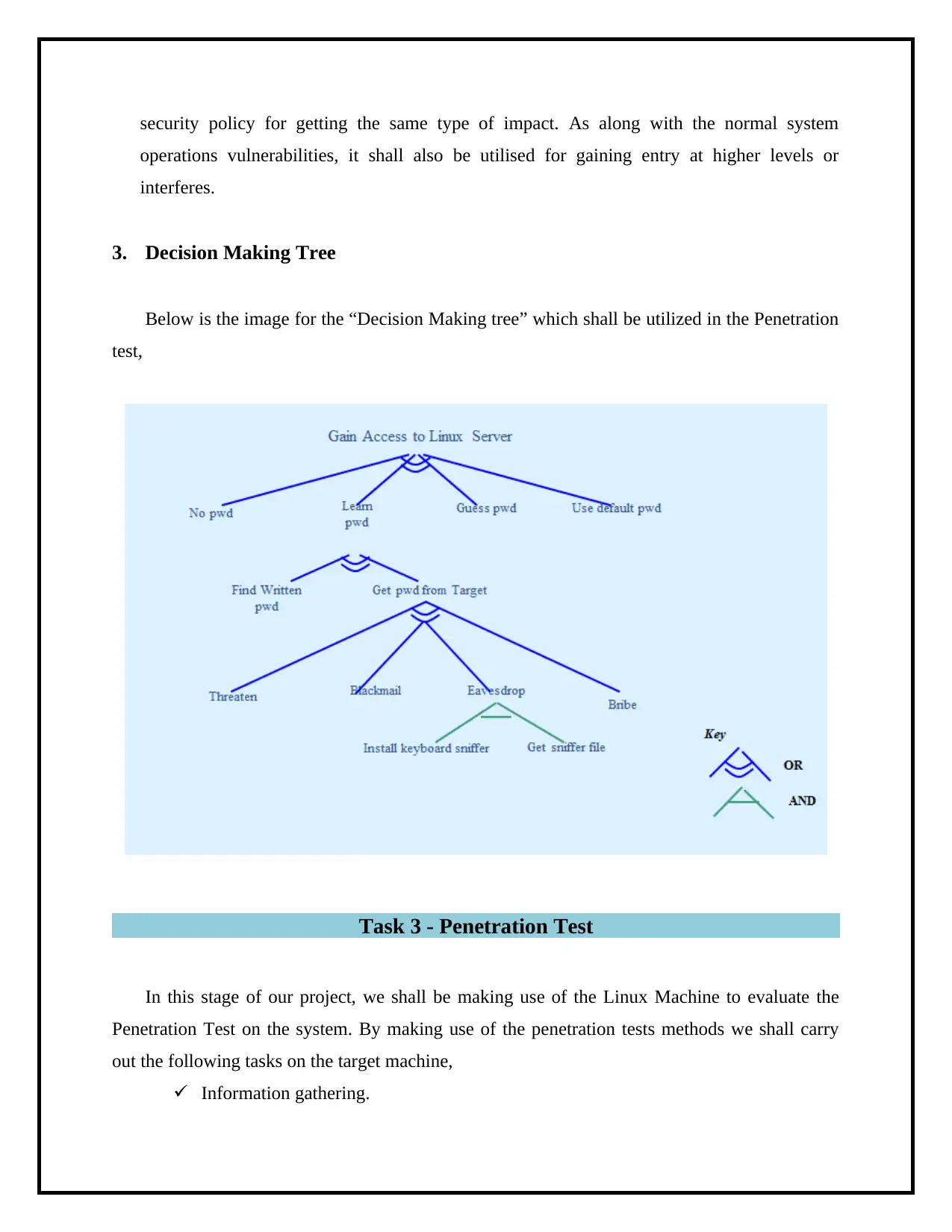
3. Decision Making Tree
Below is the image for the “Decision Making tree” which shall be utilized in the Penetration
test,
Task 3 - Penetration Test
In this stage of our project, we shall be making use of the Linux Machine to evaluate the
Penetration Test on the system. By making use of the penetration tests methods we shall carry
out the following tasks on the target machine,
Information gathering.
operations vulnerabilities, it shall also be utilised for gaining entry at higher levels or
interferes.
3. Decision Making Tree
Below is the image for the “Decision Making tree” which shall be utilized in the Penetration
test,
Task 3 - Penetration Test
In this stage of our project, we shall be making use of the Linux Machine to evaluate the
Penetration Test on the system. By making use of the penetration tests methods we shall carry
out the following tasks on the target machine,
Information gathering.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Vulnerability scanning.
Vulnerability exploiting.
Vulnerability mitigation (Halton et al., 2017).
3.1 Attacking Narrative
In this stage, we shall be utilizing the VMware Workstation and to this we shall add the
Metasploit Virtual machine and Kali Linux.
Next, we shall start with Kali Linux by pressing the “power” tab as shown in the below image,
Vulnerability exploiting.
Vulnerability mitigation (Halton et al., 2017).
3.1 Attacking Narrative
In this stage, we shall be utilizing the VMware Workstation and to this we shall add the
Metasploit Virtual machine and Kali Linux.
Next, we shall start with Kali Linux by pressing the “power” tab as shown in the below image,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Below image is representing when the “power” button is clicked for opening Metasploit LUI.
Next, to set up network setting, open the VMnet3 setup.
Both Metasploit & Kali can carry out this procedure.
Next, we shall configure in Kali Linux, the IP address.
Both Metasploit & Kali can carry out this procedure.
Next, we shall configure in Kali Linux, the IP address.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
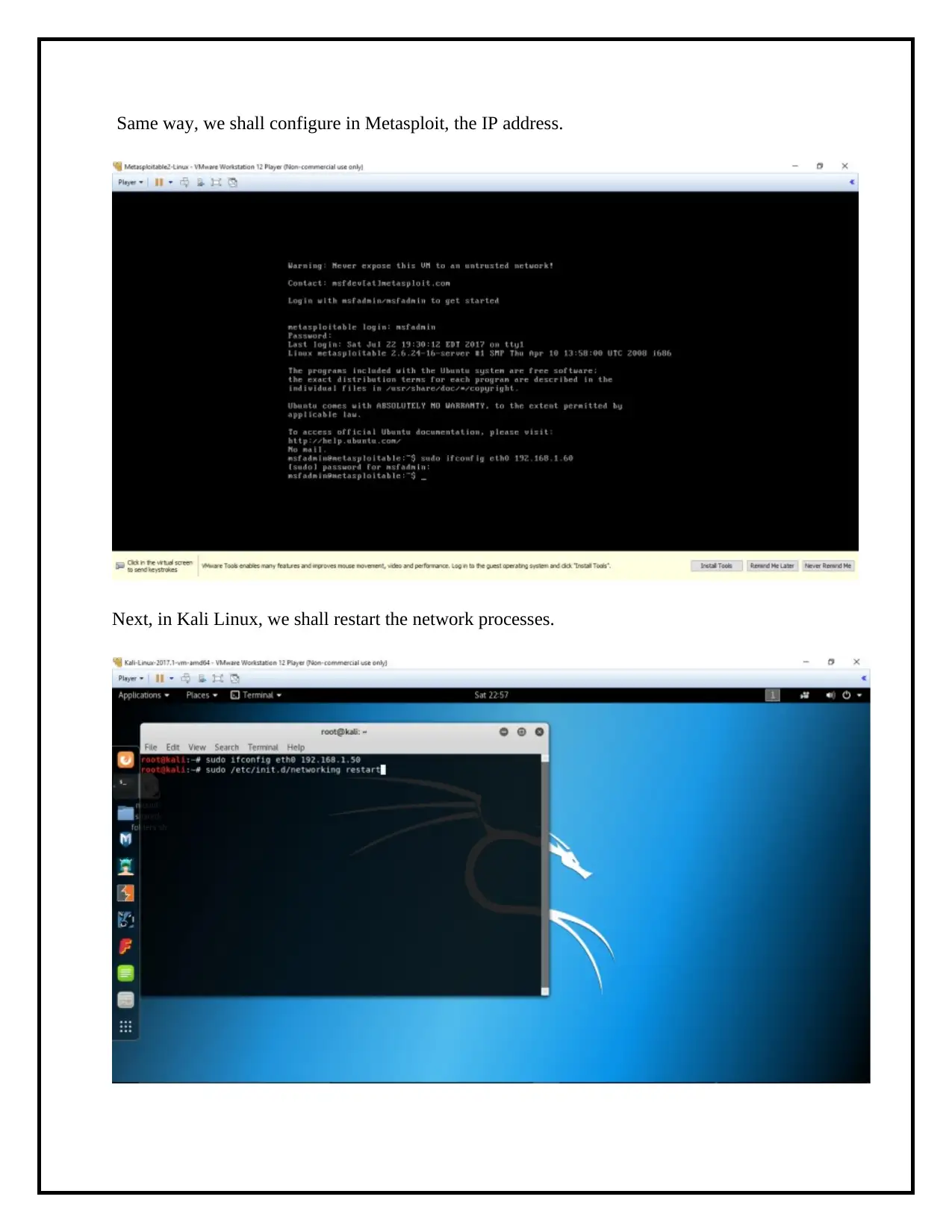
Same way, we shall configure in Metasploit, the IP address.
Next, in Kali Linux, we shall restart the network processes.
Next, in Kali Linux, we shall restart the network processes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
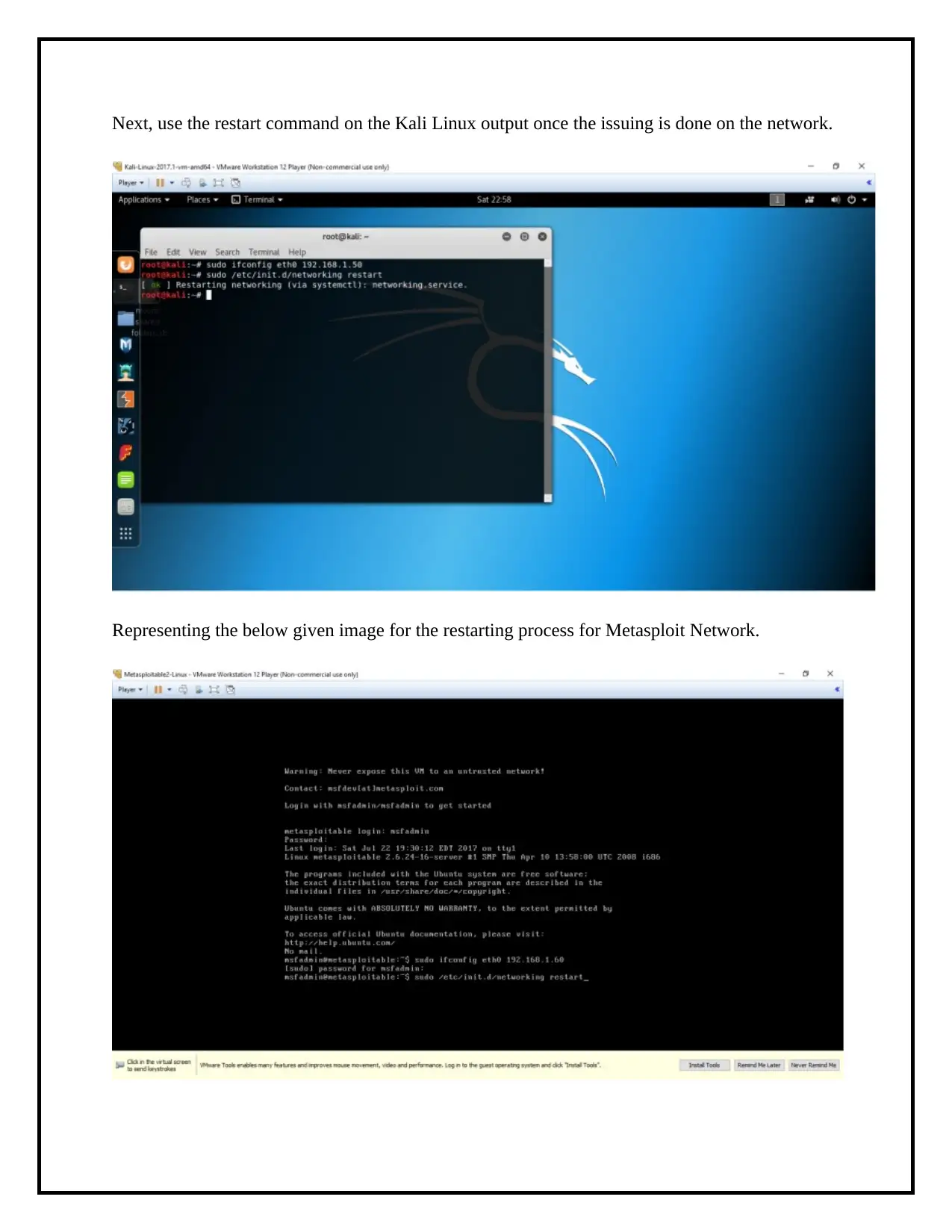
Next, use the restart command on the Kali Linux output once the issuing is done on the network.
Representing the below given image for the restarting process for Metasploit Network.
Representing the below given image for the restarting process for Metasploit Network.
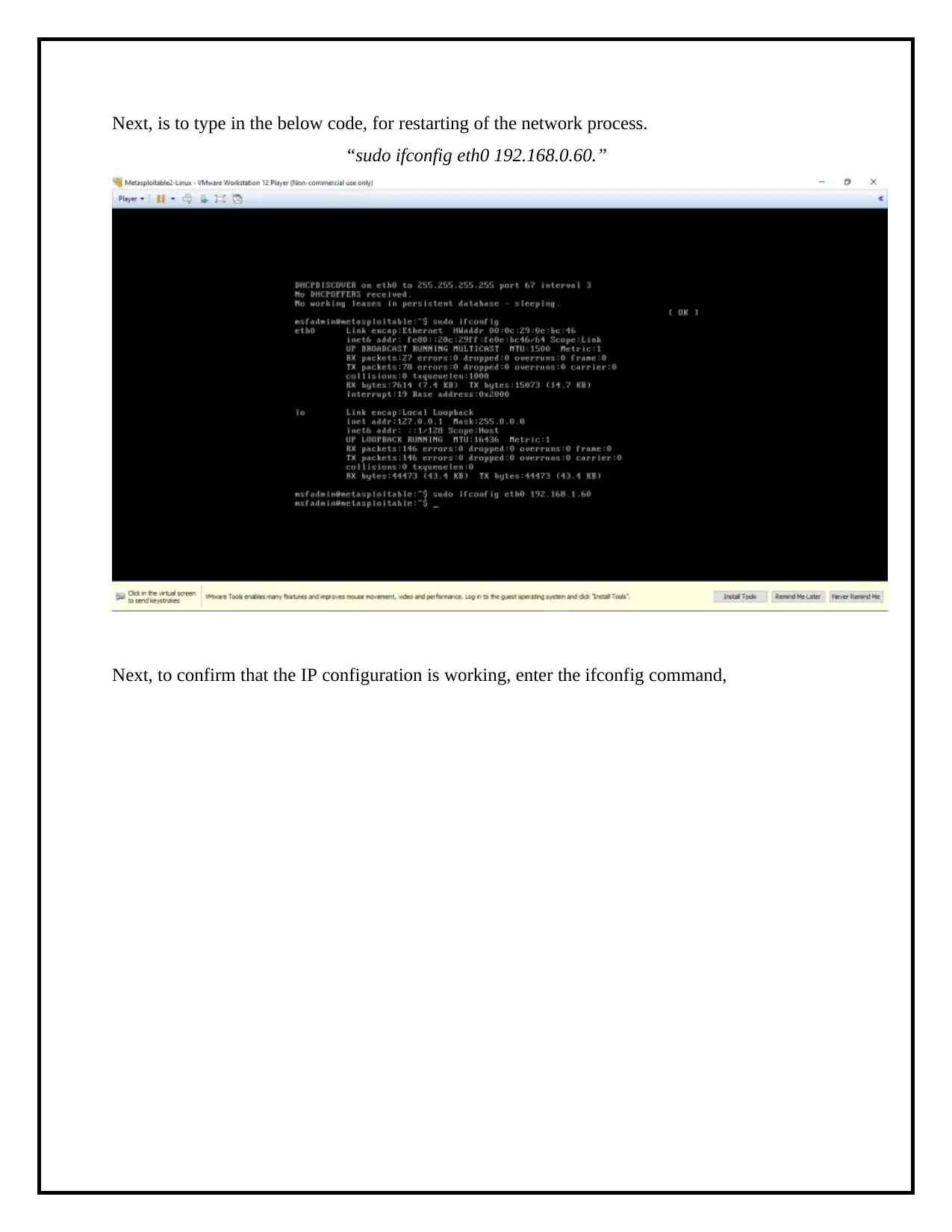
Next, is to type in the below code, for restarting of the network process.
“sudo ifconfig eth0 192.168.0.60.”
Next, to confirm that the IP configuration is working, enter the ifconfig command,
“sudo ifconfig eth0 192.168.0.60.”
Next, to confirm that the IP configuration is working, enter the ifconfig command,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





