Cybersecurity Framework Report - Risk Assessment and Compliance
VerifiedAdded on 2022/11/28
|6
|610
|343
Report
AI Summary
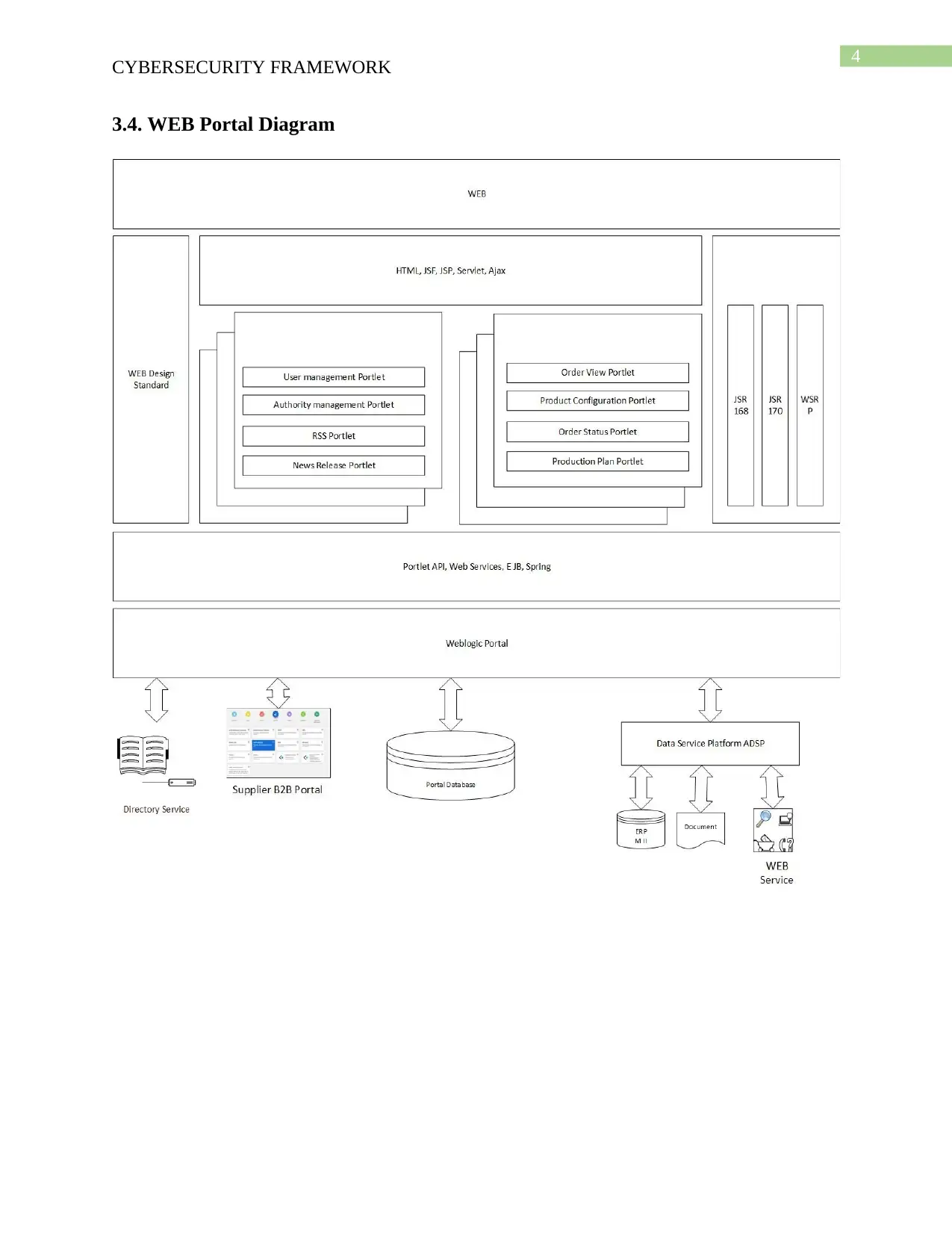
This report examines the cybersecurity framework of ABC Software, Inc., focusing on compliance, risk assessment, and policy implementation. It begins by evaluating the current cybersecurity posture, highlighting vulnerabilities and the need for improved risk control measures. The report then outlines future cybersecurity policy implementations, emphasizing the importance of a strategic action plan to address security gaps and enhance protection levels. A detailed risk assessment is presented, covering various threats, vulnerabilities, and potential impacts, along with proposed mitigation strategies such as implementing new air conditioning, configuring firewalls, and addressing potential natural disasters. The report also addresses privacy risk management, emphasizing the need to protect sensitive customer data through encryption and secure storage. Furthermore, it includes a gap analysis to identify areas where the organization's data protection practices fall short of compliance standards, outlining a process to gather information, interview stakeholders, and document findings to guide necessary actions. Finally, a web portal diagram is referenced, though not detailed in the provided text, suggesting a visual representation of the framework's components.
1 out of 6










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)