Cybersecurity Threats: Trends, Implications, and Predictions
VerifiedAdded on 2021/02/20
|20
|5781
|129
Essay
AI Summary
This essay provides an in-depth analysis of cybersecurity threats, examining their evolution from past incidents to current trends and future predictions. It explores various threats, including email-based attacks, phishing campaigns, ransomware, and mobile security vulnerabilities. The essay delves into the implications of these threats, such as data breaches, financial losses, and damage to brand reputation. It also discusses cloud security, DDOS attacks, and the increasing sophistication of cybercrimes. Furthermore, the essay offers insights into the evolutionary view of security trends, emphasizing the need for proactive measures like multi-factor authentication and strict password policies to mitigate risks. The content includes an analysis of data breaches, malicious software, and the impact of human error, providing a comprehensive overview of the cybersecurity landscape and suggesting strategies for future protection. The essay highlights the importance of understanding and adapting to the ever-changing nature of cyber threats to maintain data security and organizational integrity.

Individual Essay
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
Evolutionary View of Past, Current and future that implication of Security threats and Trend. 3
Prediction: what is yet to happen and what to look out for in future.........................................10
CONCLUSION..............................................................................................................................13
REFERENCES..............................................................................................................................14
2
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
Evolutionary View of Past, Current and future that implication of Security threats and Trend. 3
Prediction: what is yet to happen and what to look out for in future.........................................10
CONCLUSION..............................................................................................................................13
REFERENCES..............................................................................................................................14
2

INTRODUCTION
In this technology based world, most of the human efforts are now replaced with the
machinery and automatized technological advancements. As technology have widened the scope
of users in the form of online market, digital identification and strategic systems which allows
the growth and sustainability of the many organizations. So in this context the threat to the
security will also be focused widely as the criminals get their way towards the many
cybercrimes. In computer security, a threat is a possible danger that might exploit a vulnerability
and confidentiality of the data stored by the user on the internet. This report will help in
exploring about email threats and Phishing campaigns that cause a great threat to the security of
the private and confidential data and information.
Along with this, the report will also help in making a clear understanding about various
common threats to the cyber security that is Ransomware, Mobile security that protects the
personal and private data of the user from access to an unauthorised user. This will help in
identifying various cloud security trends that supports large amount of data over the network.
This is one of the strongest security which consists of the huge data of the many users as well as
many organizations. Along with this, DDOS (Distributed Denial of service) is also one of the
great security threat that may responsible for the loss of confidential data and information. The
document will also assist the learners about the evolutionary view of the trends which possess
the security to the data (Zhu and et.al., 2018). It will also explore the Implication of the security
threats and trends to the world. Also with this, various suggestions and predictions will also have
been explored here.
MAIN BODY
Evolutionary View of Past, Current and future that implication of Security threats and Trend
The organizations across the world recognise for getting the security right to maintain the
critical success in the large information technology transformation projects. Unfortunately,
Cyber threat and attack is too real. In past year, cyber threat may not result in the loss of
intellectual property but it also impacts on the share cost of business and confidence level of
consumers etc. In this way, it brought the different type of threat which causes the enterprises in
terms of public embarrassment (Abu and et.al., 2018). For Example- there are large number of
the element with data loss hack on the 146.5 million people and their accounts. This type of
attack is also known as Equifax Breach. It is one of the most powerful data breach that reported
3
In this technology based world, most of the human efforts are now replaced with the
machinery and automatized technological advancements. As technology have widened the scope
of users in the form of online market, digital identification and strategic systems which allows
the growth and sustainability of the many organizations. So in this context the threat to the
security will also be focused widely as the criminals get their way towards the many
cybercrimes. In computer security, a threat is a possible danger that might exploit a vulnerability
and confidentiality of the data stored by the user on the internet. This report will help in
exploring about email threats and Phishing campaigns that cause a great threat to the security of
the private and confidential data and information.
Along with this, the report will also help in making a clear understanding about various
common threats to the cyber security that is Ransomware, Mobile security that protects the
personal and private data of the user from access to an unauthorised user. This will help in
identifying various cloud security trends that supports large amount of data over the network.
This is one of the strongest security which consists of the huge data of the many users as well as
many organizations. Along with this, DDOS (Distributed Denial of service) is also one of the
great security threat that may responsible for the loss of confidential data and information. The
document will also assist the learners about the evolutionary view of the trends which possess
the security to the data (Zhu and et.al., 2018). It will also explore the Implication of the security
threats and trends to the world. Also with this, various suggestions and predictions will also have
been explored here.
MAIN BODY
Evolutionary View of Past, Current and future that implication of Security threats and Trend
The organizations across the world recognise for getting the security right to maintain the
critical success in the large information technology transformation projects. Unfortunately,
Cyber threat and attack is too real. In past year, cyber threat may not result in the loss of
intellectual property but it also impacts on the share cost of business and confidence level of
consumers etc. In this way, it brought the different type of threat which causes the enterprises in
terms of public embarrassment (Abu and et.al., 2018). For Example- there are large number of
the element with data loss hack on the 146.5 million people and their accounts. This type of
attack is also known as Equifax Breach. It is one of the most powerful data breach that reported
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

by 2021, up from the trillion in 2015. In several areas, it has increased the cyber-crime incidents
and also growing the large number of threats such as denial of service, application and web
based vulnerabilities and persistent threat that carried out through exploits. It is known as
vulnerabilities.
Threats are coming from the inside of business where it has increased the wide range of
internal threat from employee who made some simple mistakes. For example- they are losing the
USB and hard drive which targeted the people who loss the credentials by social engineering. It
is directly damaged on the spectrum of malicious software inside that intent on damaging and
stealing the enterprise information. It has established the security threats such as ransomwares
which are the fastest growing. For Example- in 2017, Carbon black put some efforts to increase
the growth rate of underground ransomware economy at high percentage.
It is an essential for consumer experience to improve the risk through cyber security.
Many hackers are trying to hack the information through website and corporate system.
Nowadays, the business and corporate world around would suffered many type of data breaches.
A single potential data leak was affecting the overall financial and marketing position of business
(Benson McAlaney and Frumkin, 2019). It also involves the exposure of database that contain
various type of personal information records of consumer, import-export and business related
details. It is the biggest trend that emerge in the recent years to identify the management and its
specific role.
Email is basically the primary mode of enterprises and personal communication which
despite to increase the messaging through application and other social media tools. These are the
efficient technique and method for increasing the demand of consumer in global marketplace.
The volume of email is increasing with the proportion of different type of Spam emails. Email is
continually major attack on the vendors with the malicious emails the weapon as per choice. In
past year, Multiple hackers may use the technique to effect on the enterprises process. Malware
is also becoming more sophisticated that increasing the advancement of phishing campaign
(ChoiShin and Cho, 2018). It is easy for detect the threats in the system. Hacker can use the
malware software such as ransomware, adware and spyware etc. These are different type of
software that enter in the system to perform the multiple action on the processing of hardware. In
past year, hacker can use the multiple software to damage the sensitive information.
On the other hand, Phishing is also another technology that can be used to loss the
4
and also growing the large number of threats such as denial of service, application and web
based vulnerabilities and persistent threat that carried out through exploits. It is known as
vulnerabilities.
Threats are coming from the inside of business where it has increased the wide range of
internal threat from employee who made some simple mistakes. For example- they are losing the
USB and hard drive which targeted the people who loss the credentials by social engineering. It
is directly damaged on the spectrum of malicious software inside that intent on damaging and
stealing the enterprise information. It has established the security threats such as ransomwares
which are the fastest growing. For Example- in 2017, Carbon black put some efforts to increase
the growth rate of underground ransomware economy at high percentage.
It is an essential for consumer experience to improve the risk through cyber security.
Many hackers are trying to hack the information through website and corporate system.
Nowadays, the business and corporate world around would suffered many type of data breaches.
A single potential data leak was affecting the overall financial and marketing position of business
(Benson McAlaney and Frumkin, 2019). It also involves the exposure of database that contain
various type of personal information records of consumer, import-export and business related
details. It is the biggest trend that emerge in the recent years to identify the management and its
specific role.
Email is basically the primary mode of enterprises and personal communication which
despite to increase the messaging through application and other social media tools. These are the
efficient technique and method for increasing the demand of consumer in global marketplace.
The volume of email is increasing with the proportion of different type of Spam emails. Email is
continually major attack on the vendors with the malicious emails the weapon as per choice. In
past year, Multiple hackers may use the technique to effect on the enterprises process. Malware
is also becoming more sophisticated that increasing the advancement of phishing campaign
(ChoiShin and Cho, 2018). It is easy for detect the threats in the system. Hacker can use the
malware software such as ransomware, adware and spyware etc. These are different type of
software that enter in the system to perform the multiple action on the processing of hardware. In
past year, hacker can use the multiple software to damage the sensitive information.
On the other hand, Phishing is also another technology that can be used to loss the
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
sensitive information of business. Phishing is based on the email, messages that will use by
attacker to track all information and data. It is delivering the malware and use to collect or obtain
the sensitive data.
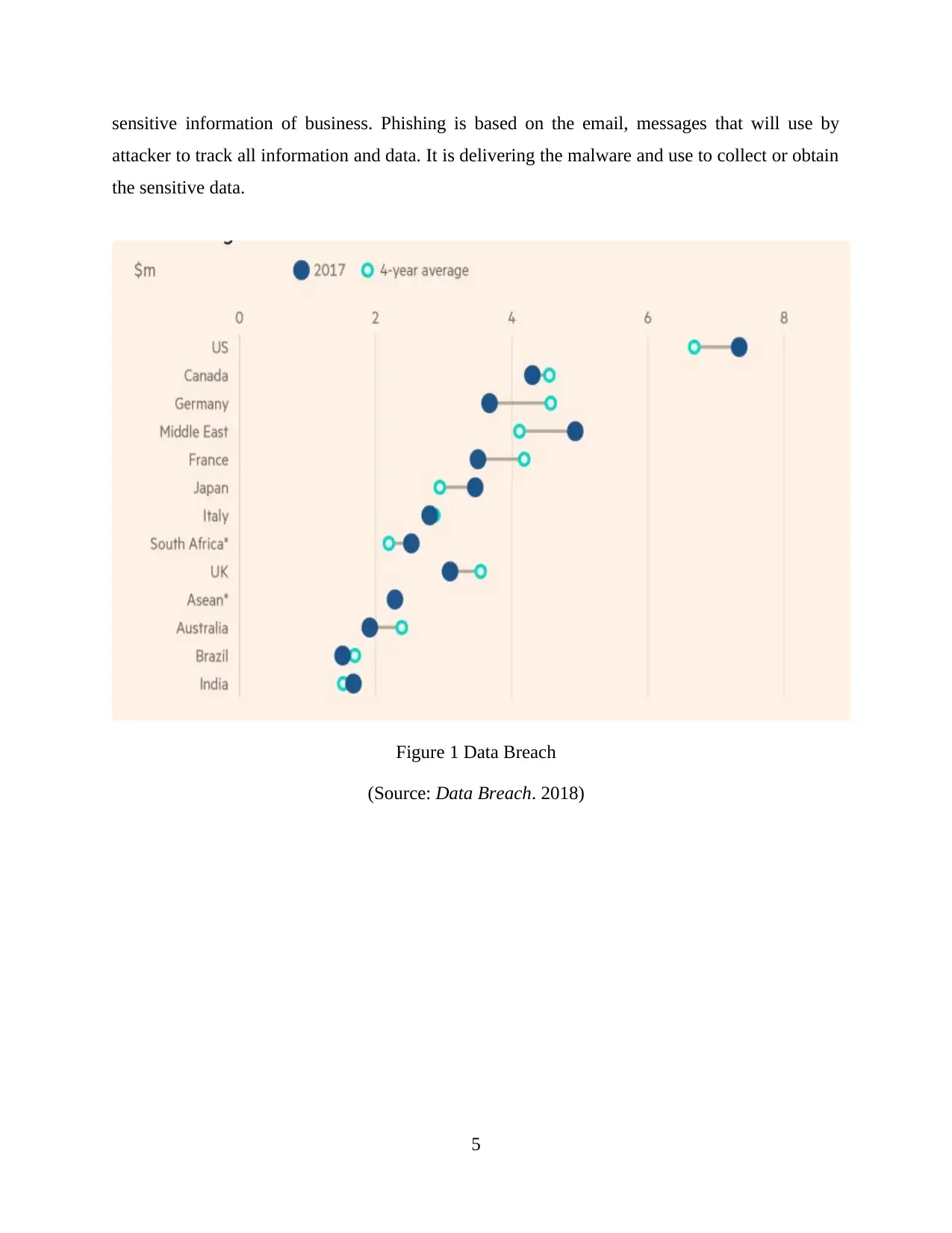
Figure 1 Data Breach
(Source: Data Breach. 2018)
5
attacker to track all information and data. It is delivering the malware and use to collect or obtain
the sensitive data.
Figure 1 Data Breach
(Source: Data Breach. 2018)
5

As per past analysis, there are 68% people and report of enterprise that has been
interrupted due to the security breach in past year. Malicious email and phishing are increasing in
the corporate world. In 2017, 25 % incident happen related the attacks in the global business. it is
the latest tend to have increase the instances on monthly or quarterly basis. Business email
compromise is including the attacker that can use the credential grabbing method to steal the
information of business. some email attacks are designed to increase the accessibility of account
with high level of executives (Hong and et.al., 2018). In past years, it observed the traffic, data
collection which below the radar and associated with the email. For Example- An organizations,
employees and other business partner make the fraudulent payment that can happen while the
person is travelling from one place to another. Attackers are set up the rule to redirect and
remove certain level of threats of mail to avoid the detection. As per survey, it can be determined
when attacker was launched the local company where they can manage or control the
information of email, while sending the sequential maul requesting to the large amount of money
transfer. In fact, companies are not realised that emails were fraudulent and made transfer money
in access amount. In 2016, FBI calculates the scam to the cost of enterprises in the excess of $5.3
dollar.
In current trends, Companies are trying to protect their information through malware
software so that they should take actions towards the fraud email those who were automatically
download the attachments. They can use the different type of anti-virus to identify the malware,
virus and ransomwares. Before downloading, it is automatically scan the email with up to date
antivirus. Some files are sending in the compressed format but it still in email as attachment. In
this way, it is automatically attached with the hard drive and antivirus software better to access
the code in the files (Khakzad and et.al., 2018). In future, the data shows that email based attacks
has required the highest security risk in terms of information technology. In this way, business
has been effected due to the security breach in future that indicate loss. As past experience,
Phishing attack must possible at once a month in future which are significantly damage the
financial conditions of business. In this way, it will reduce the revenue and image of brand
because of the fraudulent transactions.
To improve the data breach in future so that it will implement the corporate policies for
taking preparatory measure the different areas and fields. Some other areas undergo the fake
6
interrupted due to the security breach in past year. Malicious email and phishing are increasing in
the corporate world. In 2017, 25 % incident happen related the attacks in the global business. it is
the latest tend to have increase the instances on monthly or quarterly basis. Business email
compromise is including the attacker that can use the credential grabbing method to steal the
information of business. some email attacks are designed to increase the accessibility of account
with high level of executives (Hong and et.al., 2018). In past years, it observed the traffic, data
collection which below the radar and associated with the email. For Example- An organizations,
employees and other business partner make the fraudulent payment that can happen while the
person is travelling from one place to another. Attackers are set up the rule to redirect and
remove certain level of threats of mail to avoid the detection. As per survey, it can be determined
when attacker was launched the local company where they can manage or control the
information of email, while sending the sequential maul requesting to the large amount of money
transfer. In fact, companies are not realised that emails were fraudulent and made transfer money
in access amount. In 2016, FBI calculates the scam to the cost of enterprises in the excess of $5.3
dollar.
In current trends, Companies are trying to protect their information through malware
software so that they should take actions towards the fraud email those who were automatically
download the attachments. They can use the different type of anti-virus to identify the malware,
virus and ransomwares. Before downloading, it is automatically scan the email with up to date
antivirus. Some files are sending in the compressed format but it still in email as attachment. In
this way, it is automatically attached with the hard drive and antivirus software better to access
the code in the files (Khakzad and et.al., 2018). In future, the data shows that email based attacks
has required the highest security risk in terms of information technology. In this way, business
has been effected due to the security breach in future that indicate loss. As past experience,
Phishing attack must possible at once a month in future which are significantly damage the
financial conditions of business. In this way, it will reduce the revenue and image of brand
because of the fraudulent transactions.
To improve the data breach in future so that it will implement the corporate policies for
taking preparatory measure the different areas and fields. Some other areas undergo the fake
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
phishing attack drill to see that how employee were prepared. Companies should be considered
the policies and procedures on the money transfer and other type of critical data exchange from
one place to another. it will reduce the Phishing attacks on the business.
On the other hand, it will be required to implement the multi-factor authentication for the
purpose of business email and network access that mitigate the potential of attacker to gain the
access through credentials like password and username. It should be considered the sensitive
business of integrated with the authentication for building the management system and other
recognition technique (Meland and et.al., 2018). In additional, it will be implementing the strict
password policies for organizing the multi factor authentication. It should look at the policies on
password and its management. It is frequently change the password with inability to reuse the
previous password which are faster and becoming the norms. In companies, the security
enforcement will help to balance the experience of user to ignore the IT work and also increase
the policy to manage and control security aspects.
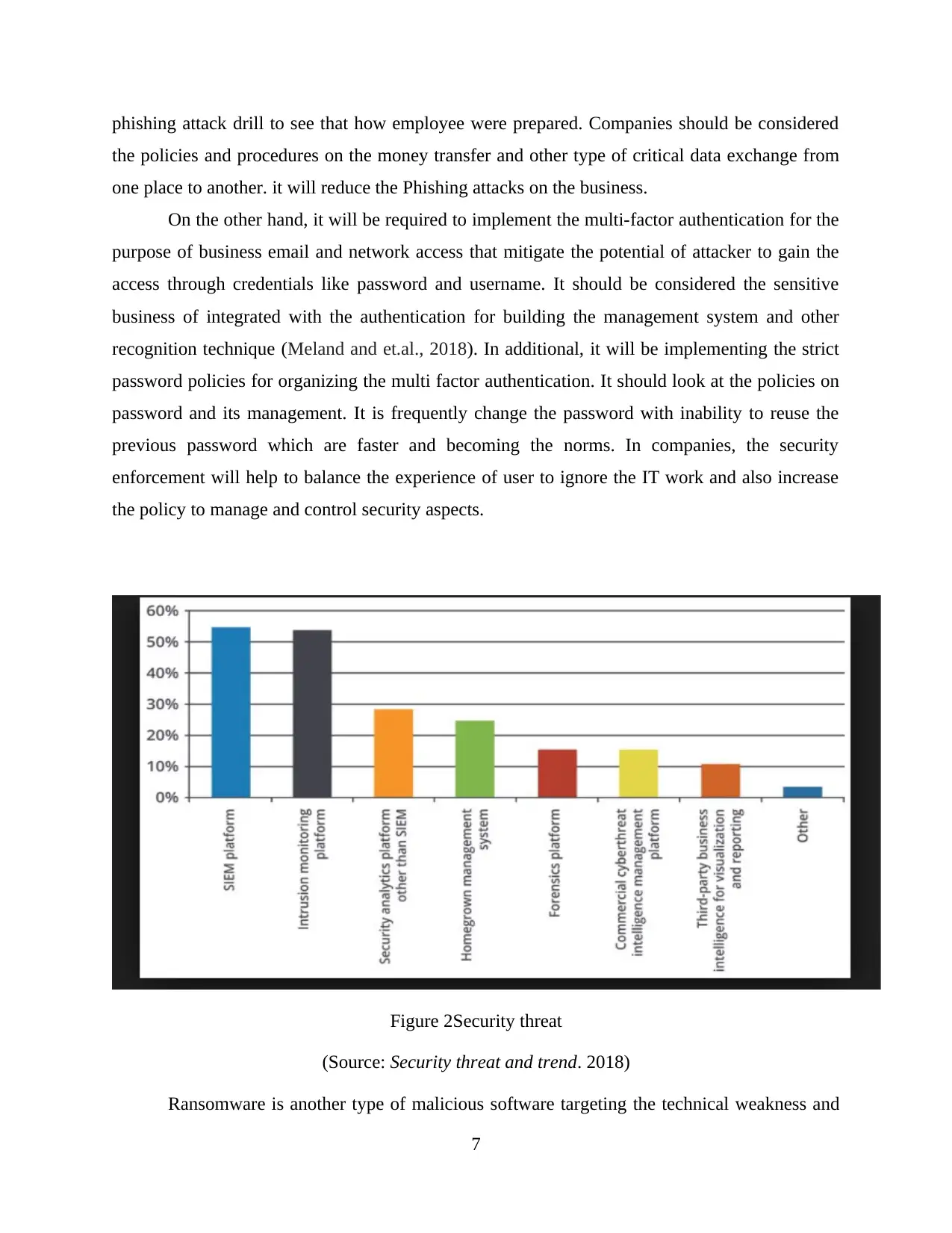
Figure 2Security threat
(Source: Security threat and trend. 2018)
Ransomware is another type of malicious software targeting the technical weakness and
7
the policies and procedures on the money transfer and other type of critical data exchange from
one place to another. it will reduce the Phishing attacks on the business.
On the other hand, it will be required to implement the multi-factor authentication for the
purpose of business email and network access that mitigate the potential of attacker to gain the
access through credentials like password and username. It should be considered the sensitive
business of integrated with the authentication for building the management system and other
recognition technique (Meland and et.al., 2018). In additional, it will be implementing the strict
password policies for organizing the multi factor authentication. It should look at the policies on
password and its management. It is frequently change the password with inability to reuse the
previous password which are faster and becoming the norms. In companies, the security
enforcement will help to balance the experience of user to ignore the IT work and also increase
the policy to manage and control security aspects.
Figure 2Security threat
(Source: Security threat and trend. 2018)
Ransomware is another type of malicious software targeting the technical weakness and
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

humans, it is putting efforts to deny the availability of services. It is frequently delivered the
different type of methods which is one of the most tactics where user is easily to click on the
email that attached (Oprea and et.al., 2018). In case, the victim opens the file so that malware is
frequently installed on the hardware system. Sometimes, the victim goes unnoticed when it
unable to determine the activities of attacker through software. It has increased the demand of
payment through ransom. It is the most common part of payment by using cryptocurrencies such
as Bitcoin. There are various types of method for the ransomware that includes server
vulnerabilities, third party application store, brute force by using remote desktop protocol and
exploit kits etc. It can happen when the users to click on the malware advertisement and
redirected through the website, in many cases, the code is easily embedded into the web pages
which hosted on the compromised servers and carried out by gaining the network access. In
2017, Ransomware was a major issues found in the organization that increase the volume of
emails, they were receiving the incident of ransomware (Oyama, 2018). For Example- there is
one incident happen when the campaign unleased the millions of people email within 24 hours.
In this way, it is systematically found that ransomware marketing is moving towards the tactics
that targeting the consumers by using phishing campaigns. It is the most sophisticated attacks
therefore, criminals are conducted the more reconnaissance, resulting to target the specific
organization regarding health services provided to secure the records of patients in proper
manner.
An attacker can target the electronic devices such as mobile phones because many
consumers are used the sophisticated smartphones. They also wearable the devices to collect the
personal information. The populations of countries are moving towards the broadband services
and adopt the new thing but it turns towards the attack method of hacker which increases the
frequency of threats. Phishing is a method for delivered the security hazards in the mobile
devices. It is another challenges in mobile security of data leakage, this can occur when the users
give the permission of application and services without realising its causes. Sometimes, Free app
can give the features and functionality but it sends the sensitive or personal information to the
remote server (Tuma, Çalikli and Scandariato, 2018). Many mobile users are trying to root their
devices to get around the business mobile device management solution. Other type of known
mobile devices vulnerabilities are unsecured Wi-Fi which is the most common for consumer to
seek the Wi-Fi connectivity or hotspot in different conditions. Wi-Fi points are unsecured that
8
different type of methods which is one of the most tactics where user is easily to click on the
email that attached (Oprea and et.al., 2018). In case, the victim opens the file so that malware is
frequently installed on the hardware system. Sometimes, the victim goes unnoticed when it
unable to determine the activities of attacker through software. It has increased the demand of
payment through ransom. It is the most common part of payment by using cryptocurrencies such
as Bitcoin. There are various types of method for the ransomware that includes server
vulnerabilities, third party application store, brute force by using remote desktop protocol and
exploit kits etc. It can happen when the users to click on the malware advertisement and
redirected through the website, in many cases, the code is easily embedded into the web pages
which hosted on the compromised servers and carried out by gaining the network access. In
2017, Ransomware was a major issues found in the organization that increase the volume of
emails, they were receiving the incident of ransomware (Oyama, 2018). For Example- there is
one incident happen when the campaign unleased the millions of people email within 24 hours.
In this way, it is systematically found that ransomware marketing is moving towards the tactics
that targeting the consumers by using phishing campaigns. It is the most sophisticated attacks
therefore, criminals are conducted the more reconnaissance, resulting to target the specific
organization regarding health services provided to secure the records of patients in proper
manner.
An attacker can target the electronic devices such as mobile phones because many
consumers are used the sophisticated smartphones. They also wearable the devices to collect the
personal information. The populations of countries are moving towards the broadband services
and adopt the new thing but it turns towards the attack method of hacker which increases the
frequency of threats. Phishing is a method for delivered the security hazards in the mobile
devices. It is another challenges in mobile security of data leakage, this can occur when the users
give the permission of application and services without realising its causes. Sometimes, Free app
can give the features and functionality but it sends the sensitive or personal information to the
remote server (Tuma, Çalikli and Scandariato, 2018). Many mobile users are trying to root their
devices to get around the business mobile device management solution. Other type of known
mobile devices vulnerabilities are unsecured Wi-Fi which is the most common for consumer to
seek the Wi-Fi connectivity or hotspot in different conditions. Wi-Fi points are unsecured that
8

can be compromised to connected with the electronic devices such as mobile phones. Network
Spoofing has occurred when adversaries create a fake access points to the legitimate at the public
location. It encourages the user to access the service in their mobile phones and also influence to
create account but it is potentially damage the sensitive information of user. For Example- Key
reinstallation is a vulnerability in the WPA protocol of Wi-Fi in order to steal the personal details
related the files.
Nowadays, the biggest emerging threat of mobile security is related to increase the
Trojanised application in global marketplace. Malware always carried in the applications which
are available in free, open source. For Example- McAfee has discovered the malware it known as
Grabos. It has found the various type of application that can be designed to deceive the users and
they can easily download the application in smartphones. Garbos was able to evade the security
platform by updating if setting has been changed every hour.
Business will support the staff members using the personal devices and other remote
servers. It has needed the own devices which are the most popular in few year ago. Many
companies are moved towards the other model and select the own devices (Tuma, Çalikli and
Scandariato, 2018). It shows the distribution that concern about the mobile device security due to
malware, data loss and access management etc. it helps to maintain and balance the employee
privacy and monitoring in the organization.
Business Mobility Management provide the solution to protect the employee and give
additional security when people can use the data or access the information from personal
devices. It carried out the specific commands such as delete. Remote lock when it helps to
protect through stolen or lost. It is an effective solution that may support the business policies,
rules and regulations, legislations of enterprises. Afterwards, Enterprise mobility solution is
moving towards internet of things that start to cover overall budget of business. IoT is being
integrated with artificial intelligence technology. It is the most effective security factor that can
use the cloud to preserve information. It enables the devices to access data through cloud
network. Sometimes, it is very difficult to create the management and transparent visibility
across the different devices. In this way, it should be considered in the security perspective to
secure the information in proper manner.
Cloud security is important for business to support in the different cloud environment
such as Hybrid cloud. It is based on the running cloud that perform multiple task to maintain the
9
Spoofing has occurred when adversaries create a fake access points to the legitimate at the public
location. It encourages the user to access the service in their mobile phones and also influence to
create account but it is potentially damage the sensitive information of user. For Example- Key
reinstallation is a vulnerability in the WPA protocol of Wi-Fi in order to steal the personal details
related the files.
Nowadays, the biggest emerging threat of mobile security is related to increase the
Trojanised application in global marketplace. Malware always carried in the applications which
are available in free, open source. For Example- McAfee has discovered the malware it known as
Grabos. It has found the various type of application that can be designed to deceive the users and
they can easily download the application in smartphones. Garbos was able to evade the security
platform by updating if setting has been changed every hour.
Business will support the staff members using the personal devices and other remote
servers. It has needed the own devices which are the most popular in few year ago. Many
companies are moved towards the other model and select the own devices (Tuma, Çalikli and
Scandariato, 2018). It shows the distribution that concern about the mobile device security due to
malware, data loss and access management etc. it helps to maintain and balance the employee
privacy and monitoring in the organization.
Business Mobility Management provide the solution to protect the employee and give
additional security when people can use the data or access the information from personal
devices. It carried out the specific commands such as delete. Remote lock when it helps to
protect through stolen or lost. It is an effective solution that may support the business policies,
rules and regulations, legislations of enterprises. Afterwards, Enterprise mobility solution is
moving towards internet of things that start to cover overall budget of business. IoT is being
integrated with artificial intelligence technology. It is the most effective security factor that can
use the cloud to preserve information. It enables the devices to access data through cloud
network. Sometimes, it is very difficult to create the management and transparent visibility
across the different devices. In this way, it should be considered in the security perspective to
secure the information in proper manner.
Cloud security is important for business to support in the different cloud environment
such as Hybrid cloud. It is based on the running cloud that perform multiple task to maintain the
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
standard of environment. The security implication is the more complex environment that can
shift from one direction to another. Business can use the data centre which defined the
interconnectivity between the departments. It is useful for enterprise to access the cloud services
in which improve the content distribution, recovery and enterprises continuity etc. Mobile
application and cloud based environment are increasing the risk of threats and malware because
it can be spreading malware in the information technology environments. In future enhancement,
cloud is to be perfect storm in the information technology. It has required the cost efficiency,
scale and agility to balance the security or managing the risk. In this way, business adopt the
compliances to set up own legislation for maintain the services. As a results, cloud adoption
plans are useful for business within the next years because it integrates with the artificial
intelligence technologies to collaborate with the environment (Oyama, 2018). Companies will
consider the trade-off between the data management through different type of cloud based on
public, hybrid and private. By 2020, companies will be implementing the IoT which deployed
form the cloud services. It is also deployed the more workload to the cloud services, but it will
need to mitigate the potential risk and threats.
To maintain the information technology security in the private and public cloud, when
10
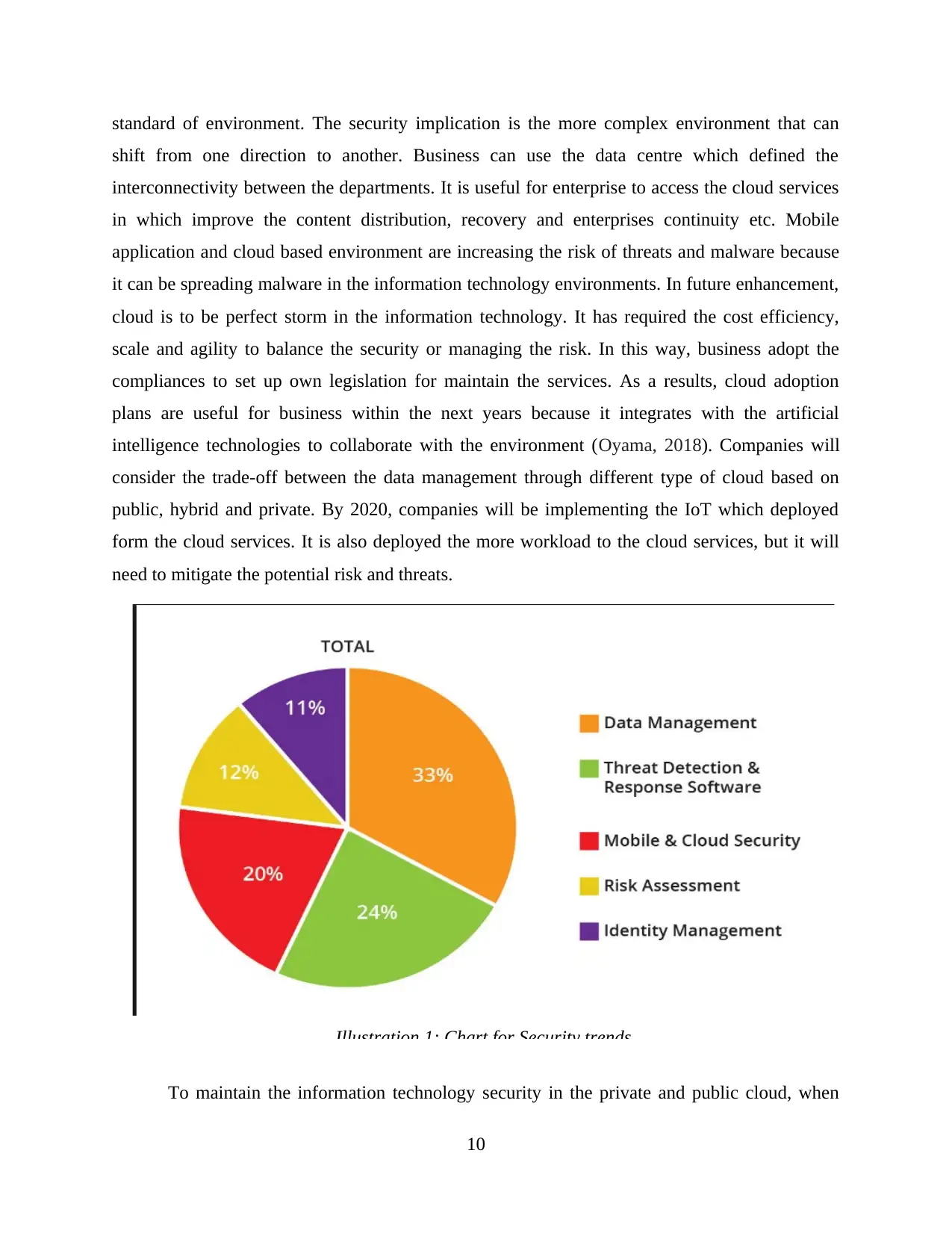
Illustration 1: Chart for Security trends
shift from one direction to another. Business can use the data centre which defined the
interconnectivity between the departments. It is useful for enterprise to access the cloud services
in which improve the content distribution, recovery and enterprises continuity etc. Mobile
application and cloud based environment are increasing the risk of threats and malware because
it can be spreading malware in the information technology environments. In future enhancement,
cloud is to be perfect storm in the information technology. It has required the cost efficiency,
scale and agility to balance the security or managing the risk. In this way, business adopt the
compliances to set up own legislation for maintain the services. As a results, cloud adoption
plans are useful for business within the next years because it integrates with the artificial
intelligence technologies to collaborate with the environment (Oyama, 2018). Companies will
consider the trade-off between the data management through different type of cloud based on
public, hybrid and private. By 2020, companies will be implementing the IoT which deployed
form the cloud services. It is also deployed the more workload to the cloud services, but it will
need to mitigate the potential risk and threats.
To maintain the information technology security in the private and public cloud, when
10
Illustration 1: Chart for Security trends
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

enterprise also look to mitigate threat by dividing the network, user and other application. It
helps to obtain the proper control and visibility on the malicious because it is literally moving
towards the cloud based environment.
Distributed denial of service is a type of threat which are typically render the online
website and also increase the traffic from the different sources. This type of attack is becoming
increasing the large amount of traffic. It is targeting the different type of resources and industries
such as financial firm and banking etc. For Example- In Australia, Business has been interrupted
due to the data breach in the past year and also indicated that 11% companies known about the
denial of services that occurs every month.
In future development, Companies are investing money on the security services that will be
continues in 2018. It is covering the requirement of emerging techniques to improve the services
such as next gen end point security, CCTV and automation system etc. these are the different
type of technologies protect the common threats such as DDoS, Malware, Phishing and
ransomware etc.
11
helps to obtain the proper control and visibility on the malicious because it is literally moving
towards the cloud based environment.
Distributed denial of service is a type of threat which are typically render the online
website and also increase the traffic from the different sources. This type of attack is becoming
increasing the large amount of traffic. It is targeting the different type of resources and industries
such as financial firm and banking etc. For Example- In Australia, Business has been interrupted
due to the data breach in the past year and also indicated that 11% companies known about the
denial of services that occurs every month.
In future development, Companies are investing money on the security services that will be
continues in 2018. It is covering the requirement of emerging techniques to improve the services
such as next gen end point security, CCTV and automation system etc. these are the different
type of technologies protect the common threats such as DDoS, Malware, Phishing and
ransomware etc.
11

Prediction: what is yet to happen and what to look out for in future
As the automation can support cybersecurity professionals but it cannot replace them.
Human can do many evolutions with the support of many technological tools. So in context of
Cyber security, Artificial Intelligence has attempted to perform much more at a large scale that
may consists of processing and analysing data based on the programming done by the humans in
order to build the Artificial intelligence to perform the automatised tasks (Ahuett-Garza and
Kurfess, 2018). Despite of the development and deployment of the sophisticated cyber security
solutions, patches and updates that has been continuously increasing in the number of cyber-
attacks. Due to the Recent breakthroughs in the field of AI, Security experts and firms have been
using the Various Machine learning models, neural networks and AI technologies in order to
detect and anticipate the cyber-attacks.
As the Overall digital attack surface will be significantly increase as we move closer to
the technologies which is being interconnected in the future. So IT security is no longer going to
simply helps in protecting the data and keeping the hackers out of the system but it has been a
great concern for the organizations to focus on leverage, collaboration and monetize their data
without being exposed to the privacy breaches. So only the cyber security is not enough to secure
the most sensitive data or privacy but there are various future predictions that restricts the
attackers to access the data and information (Barmpatsalou and et.al., 2018). Future predictions
for such cyber security and trends will not only restrict the access of the unauthorised user but
these trend will also help in searching the source from where the attack has been initialised. So
the future predictions also allow in identifying the criminal. As any cybercrime occur then it may
trace the location from where the attempt has been made but recognising the criminal from that
source is yet to be happen. So along with identifying the security threats and trends, the
increasing technology advancement not only strengthening the security and privacy of the data
but also it enlist the AI techniques to the criminals which allows them to super charge their own
criminal activities.
Email Threats and Phishing Campaigns is one one of the great concern which requires
to be secured and encrypted in order to support the data security in during the exchange of
information via Emails. Although, automated systems powered by AI could probe the networks
and systems searching for undiscovered vulnerabilities that could be exploited. As the phishing
attempts to gain the sensitive information so the future predictions involve is that Phishing may
12
As the automation can support cybersecurity professionals but it cannot replace them.
Human can do many evolutions with the support of many technological tools. So in context of
Cyber security, Artificial Intelligence has attempted to perform much more at a large scale that
may consists of processing and analysing data based on the programming done by the humans in
order to build the Artificial intelligence to perform the automatised tasks (Ahuett-Garza and
Kurfess, 2018). Despite of the development and deployment of the sophisticated cyber security
solutions, patches and updates that has been continuously increasing in the number of cyber-
attacks. Due to the Recent breakthroughs in the field of AI, Security experts and firms have been
using the Various Machine learning models, neural networks and AI technologies in order to
detect and anticipate the cyber-attacks.
As the Overall digital attack surface will be significantly increase as we move closer to
the technologies which is being interconnected in the future. So IT security is no longer going to
simply helps in protecting the data and keeping the hackers out of the system but it has been a
great concern for the organizations to focus on leverage, collaboration and monetize their data
without being exposed to the privacy breaches. So only the cyber security is not enough to secure
the most sensitive data or privacy but there are various future predictions that restricts the
attackers to access the data and information (Barmpatsalou and et.al., 2018). Future predictions
for such cyber security and trends will not only restrict the access of the unauthorised user but
these trend will also help in searching the source from where the attack has been initialised. So
the future predictions also allow in identifying the criminal. As any cybercrime occur then it may
trace the location from where the attempt has been made but recognising the criminal from that
source is yet to be happen. So along with identifying the security threats and trends, the
increasing technology advancement not only strengthening the security and privacy of the data
but also it enlist the AI techniques to the criminals which allows them to super charge their own
criminal activities.
Email Threats and Phishing Campaigns is one one of the great concern which requires
to be secured and encrypted in order to support the data security in during the exchange of
information via Emails. Although, automated systems powered by AI could probe the networks
and systems searching for undiscovered vulnerabilities that could be exploited. As the phishing
attempts to gain the sensitive information so the future predictions involve is that Phishing may
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





