Cybersecurity Project: Developing a Robust Security Framework
VerifiedAdded on 2023/06/10
|14
|2637
|186
Project
AI Summary
This cybersecurity project addresses the increasing threat of cybercrime by proposing a comprehensive security framework. The project begins with a rationale highlighting the need for robust cybersecurity measures in organizations heavily reliant on information technology. It identifies the problem domain, which includes the evolving nature of cyberattacks and the need for proactive security strategies. The project's purpose is to create a secure environment for data and online activities, with a vision of providing continuous cybersecurity solutions. The project follows an agile methodology to accommodate changing requirements and emphasizes risk analysis throughout the development process. The project incorporates both qualitative and quantitative data collection methods, including surveys and examination of existing records. Ethical issues are addressed to ensure responsible implementation, and compliance requirements are outlined. The project plan includes a detailed WBS and Gantt chart, outlining tasks, durations, and dependencies. A risk analysis identifies potential challenges, and the project culminates in final execution and completion. This project provides a valuable framework for understanding and implementing cybersecurity measures.

Running head: CYBER SECURITY
Cyber Security
Name of the Student
Name of the University
Author Note
Cyber Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY
Table of Contents
Rationale:...................................................................................................................................3
Problem Domain:...................................................................................................................3
Purpose:..................................................................................................................................3
Sponsor or Supervisor Recommendation:..................................................................................4
Theoretical Framework:.............................................................................................................4
Methodology:.............................................................................................................................5
Research & System Development Method:...........................................................................5
Data Collection Method:........................................................................................................5
Ethical Issues:.........................................................................................................................6
Compliance Requirements:....................................................................................................6
Analysis of Data:....................................................................................................................6
Project Plan:...............................................................................................................................7
Duration:................................................................................................................................7
WBS:......................................................................................................................................9
Gantt chart:...........................................................................................................................10
Risks Analysis:.....................................................................................................................10
Table of Contents
Rationale:...................................................................................................................................3
Problem Domain:...................................................................................................................3
Purpose:..................................................................................................................................3
Sponsor or Supervisor Recommendation:..................................................................................4
Theoretical Framework:.............................................................................................................4
Methodology:.............................................................................................................................5
Research & System Development Method:...........................................................................5
Data Collection Method:........................................................................................................5
Ethical Issues:.........................................................................................................................6
Compliance Requirements:....................................................................................................6
Analysis of Data:....................................................................................................................6
Project Plan:...............................................................................................................................7
Duration:................................................................................................................................7
WBS:......................................................................................................................................9
Gantt chart:...........................................................................................................................10
Risks Analysis:.....................................................................................................................10

2CYBER SECURITY
Rationale:
In the recent time the number of cybercrime is increasing rapidly so it is necessary for
the organization to develop a cybersecurity measurement for the organization. The businesses
and the companies are in front of the risks as they are over dependent on the information
technology. The decision maker and the policy makers are managing the challenges without
concerning about the consequences of the risks. It is necessary for the business or the
organization to establish a proper cyber security so that the data get safe and will not be
breached by the cyber attackers (Dark et al., 2015). It is necessary to identify the particular
risk and then apply the proper method of cyber security.
Problem Domain:
There are many problem that are associated with cyber security implementation
because day by day the scenario of cyber-attacks are changing rapidly. Several techniques of
cyber-attack needs different method of cyber security. Many old problems that are used
earlier for cyber-attack is used now a days like the ransom ware attack. It is a major worry for
the cyber security officer to implement all the measures properly according to the
requirement (Phillips, 2017). The cyber assets and the sensitive data must be protected from
being violated. To protect the data integrity it is necessary to develop a project of cyber
security that will mitigate all the risks associated with cybercrime.
Purpose:
The main purpose of the project is to create an environment which will protect the
data and the activities on the internet. Cyber security project will be applied to the several
business and the organization to provide data security on the organization (August &
Learning, 2015). The vision of the project is to provide cyber security solutions continuously
to the organizations that are in the market right now. In the recent time the amount of
problem related to cyber security is increasing rapidly. As the data rate is increasing the
Rationale:
In the recent time the number of cybercrime is increasing rapidly so it is necessary for
the organization to develop a cybersecurity measurement for the organization. The businesses
and the companies are in front of the risks as they are over dependent on the information
technology. The decision maker and the policy makers are managing the challenges without
concerning about the consequences of the risks. It is necessary for the business or the
organization to establish a proper cyber security so that the data get safe and will not be
breached by the cyber attackers (Dark et al., 2015). It is necessary to identify the particular
risk and then apply the proper method of cyber security.
Problem Domain:
There are many problem that are associated with cyber security implementation
because day by day the scenario of cyber-attacks are changing rapidly. Several techniques of
cyber-attack needs different method of cyber security. Many old problems that are used
earlier for cyber-attack is used now a days like the ransom ware attack. It is a major worry for
the cyber security officer to implement all the measures properly according to the
requirement (Phillips, 2017). The cyber assets and the sensitive data must be protected from
being violated. To protect the data integrity it is necessary to develop a project of cyber
security that will mitigate all the risks associated with cybercrime.
Purpose:
The main purpose of the project is to create an environment which will protect the
data and the activities on the internet. Cyber security project will be applied to the several
business and the organization to provide data security on the organization (August &
Learning, 2015). The vision of the project is to provide cyber security solutions continuously
to the organizations that are in the market right now. In the recent time the amount of
problem related to cyber security is increasing rapidly. As the data rate is increasing the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY
amount of the cyber-attacks also increased to attack the sensitive data of the victims. These
attacks has a huge impact on the victims as their digital identity is also at stake so it is
necessary for the individuals also to protect their own data by apply several precautions of
cyber security (Chapman, 2017). There are many strategic objectives of the project which
encounter with the new risks that are identified in the current market of the information
technology.
Sponsor or Supervisor Recommendation:
In the recent time the data is being stored on the cloud platform. The cloud has three
different services SaaS, PaaS and IaaS. Among these three the SaaS is less secure as the data
is protected by the SaaS provider to it is necessary and recommended that proper security
measures must be taken to secure the data when the data will be migrated to the SaaS. It is
required to the project supervisor to assess all the requirement and the after consequences
while implementing the cyber security project (Knowles et al., 2015). The pattern of cyber-
attacks is changes as the time goes on so it is necessary for the project sponsor to make the
development which will be capable of tackling the future attacks as well. The project must
follow all the assessment while implementing otherwise there will be chance that the project
might get fail.
Theoretical Framework:
It is necessary for any kind of project to describe the theoretical framework properly
so that it will guide all the processes that are related with the project. In the project of cyber
security implementation it is necessary to assess the conceptual and theoretical framework
properly, so that all the processes of the cyber security project will be implemented properly.
By the use of the framework the developer will assess the future prediction of the project like
amount of the cyber-attacks also increased to attack the sensitive data of the victims. These
attacks has a huge impact on the victims as their digital identity is also at stake so it is
necessary for the individuals also to protect their own data by apply several precautions of
cyber security (Chapman, 2017). There are many strategic objectives of the project which
encounter with the new risks that are identified in the current market of the information
technology.
Sponsor or Supervisor Recommendation:
In the recent time the data is being stored on the cloud platform. The cloud has three
different services SaaS, PaaS and IaaS. Among these three the SaaS is less secure as the data
is protected by the SaaS provider to it is necessary and recommended that proper security
measures must be taken to secure the data when the data will be migrated to the SaaS. It is
required to the project supervisor to assess all the requirement and the after consequences
while implementing the cyber security project (Knowles et al., 2015). The pattern of cyber-
attacks is changes as the time goes on so it is necessary for the project sponsor to make the
development which will be capable of tackling the future attacks as well. The project must
follow all the assessment while implementing otherwise there will be chance that the project
might get fail.
Theoretical Framework:
It is necessary for any kind of project to describe the theoretical framework properly
so that it will guide all the processes that are related with the project. In the project of cyber
security implementation it is necessary to assess the conceptual and theoretical framework
properly, so that all the processes of the cyber security project will be implemented properly.
By the use of the framework the developer will assess the future prediction of the project like
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER SECURITY
whether the project will succeeded or not (Schoitsch et al., 2016). The framework will be
made by running some inductive processes.
Methodology:
Methodology is the main part for many project development, in this part the project
method is chosen and the requirement that are needed for developing the project.
Research & System Development Method:
The methodology that will be used in the project development is the agile
methodology. In the development of cyber security project many requirements will be
followed and the requirement will change over a certain time period. For these changing
requirement the length of the project development gets higher. Agile methodology is best
suited for this kind of project because agile methodology is flexible as it will help the projects
to make changes whenever required. The processes of the project is done in a linear and
sequential manner so the project completed successfully without any error (Fukushima &
Sasaki, 2016). It is efficient because it emphasizes on the people interaction rather than the
use of tools.
For a successful implementation of cyber security project it is necessary to identify
the problem and the project definition, which will contribute to the whole project. For this, a
progressive and a structured approach is taken for analysing the risks that are associated with
the cybersecurity. Losses that has potential for the information technology needed to be
identified first and then quantified (Carr, 2016). The developer who will make the project
must analyse the risks first then make their decision that how to implement the project. The
development must be done in several steps so that the project is successfully implemented.
whether the project will succeeded or not (Schoitsch et al., 2016). The framework will be
made by running some inductive processes.
Methodology:
Methodology is the main part for many project development, in this part the project
method is chosen and the requirement that are needed for developing the project.
Research & System Development Method:
The methodology that will be used in the project development is the agile
methodology. In the development of cyber security project many requirements will be
followed and the requirement will change over a certain time period. For these changing
requirement the length of the project development gets higher. Agile methodology is best
suited for this kind of project because agile methodology is flexible as it will help the projects
to make changes whenever required. The processes of the project is done in a linear and
sequential manner so the project completed successfully without any error (Fukushima &
Sasaki, 2016). It is efficient because it emphasizes on the people interaction rather than the
use of tools.
For a successful implementation of cyber security project it is necessary to identify
the problem and the project definition, which will contribute to the whole project. For this, a
progressive and a structured approach is taken for analysing the risks that are associated with
the cybersecurity. Losses that has potential for the information technology needed to be
identified first and then quantified (Carr, 2016). The developer who will make the project
must analyse the risks first then make their decision that how to implement the project. The
development must be done in several steps so that the project is successfully implemented.

5CYBER SECURITY
Data Collection Method:
For these project both the qualitative and quantitative data collection will be used. As
the main job is to collect the risks that people are facing right now. For the data collection
many different method will be used. Surveys will be in a zone to know exactly what kind of
cybercrime has been happening in those area then planning the project as per the data
(Tetrick et al., 2016). Documents and old records will be followed also for seeing the old
trend in this technology.
Ethical Issues:
Ethical issues are some action that will rise if an approach is taken in a wrong way.
The hackers are exploiting the system as they want without the concern of the victim. Many
ethical issues are there for the project development. The developer must not abstract the
cyber security procedure of implementation, the report of the project must be correct. The
responsibility must be accepted which is assigned to the developer for making the project if
not then it will be unethical.
Compliance Requirements:
For this project of cyber security many compliance requirements are needed. The
main requirement is the legal permission for the project which had to be taken from the
government. Then the project must get certified as per the projects standards. The workplace
where the project is made is needs several requirements as well.
Analysis of Data:
Data that are collected from the interview or from the survey needed to be analysed
properly so that the project meet all the requirements. If all the requirements of the project is
met then it will be able to mitigate all the risks that are associated with the cyber security
Data Collection Method:
For these project both the qualitative and quantitative data collection will be used. As
the main job is to collect the risks that people are facing right now. For the data collection
many different method will be used. Surveys will be in a zone to know exactly what kind of
cybercrime has been happening in those area then planning the project as per the data
(Tetrick et al., 2016). Documents and old records will be followed also for seeing the old
trend in this technology.
Ethical Issues:
Ethical issues are some action that will rise if an approach is taken in a wrong way.
The hackers are exploiting the system as they want without the concern of the victim. Many
ethical issues are there for the project development. The developer must not abstract the
cyber security procedure of implementation, the report of the project must be correct. The
responsibility must be accepted which is assigned to the developer for making the project if
not then it will be unethical.
Compliance Requirements:
For this project of cyber security many compliance requirements are needed. The
main requirement is the legal permission for the project which had to be taken from the
government. Then the project must get certified as per the projects standards. The workplace
where the project is made is needs several requirements as well.
Analysis of Data:
Data that are collected from the interview or from the survey needed to be analysed
properly so that the project meet all the requirements. If all the requirements of the project is
met then it will be able to mitigate all the risks that are associated with the cyber security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER SECURITY
(Brangetto & Aubyn, 2015). The source of the data must be genuine otherwise it will be
difficult for the project developer to develop the project as per the need and requirements.
(Brangetto & Aubyn, 2015). The source of the data must be genuine otherwise it will be
difficult for the project developer to develop the project as per the need and requirements.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
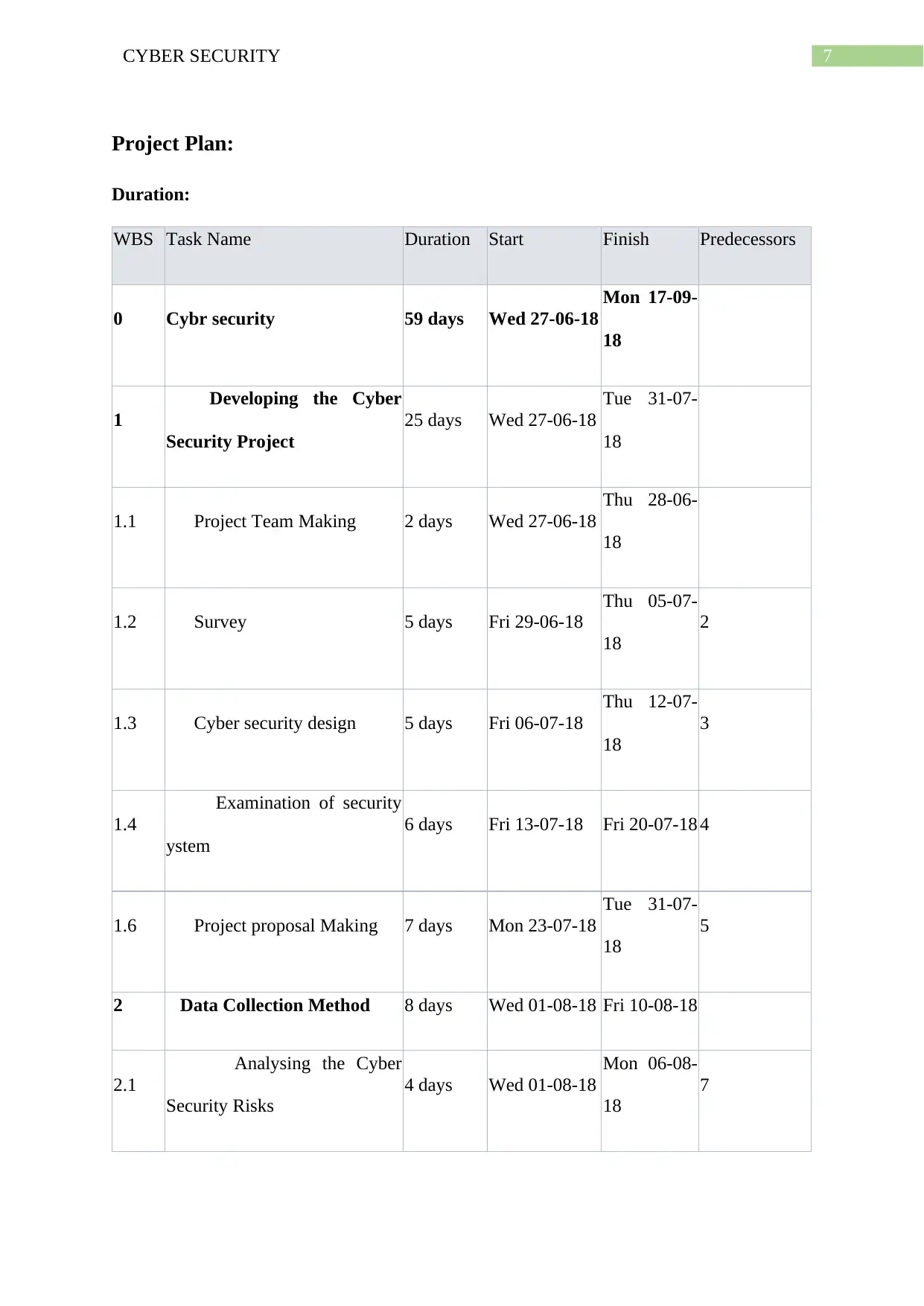
7CYBER SECURITY
Project Plan:
Duration:
WBS Task Name Duration Start Finish Predecessors
0 Cybr security 59 days Wed 27-06-18
Mon 17-09-
18
1
Developing the Cyber
Security Project
25 days Wed 27-06-18
Tue 31-07-
18
1.1 Project Team Making 2 days Wed 27-06-18
Thu 28-06-
18
1.2 Survey 5 days Fri 29-06-18
Thu 05-07-
18
2
1.3 Cyber security design 5 days Fri 06-07-18
Thu 12-07-
18
3
1.4
Examination of security
ystem
6 days Fri 13-07-18 Fri 20-07-18 4
1.6 Project proposal Making 7 days Mon 23-07-18
Tue 31-07-
18
5
2 Data Collection Method 8 days Wed 01-08-18 Fri 10-08-18
2.1
Analysing the Cyber
Security Risks
4 days Wed 01-08-18
Mon 06-08-
18
7
Project Plan:
Duration:
WBS Task Name Duration Start Finish Predecessors
0 Cybr security 59 days Wed 27-06-18
Mon 17-09-
18
1
Developing the Cyber
Security Project
25 days Wed 27-06-18
Tue 31-07-
18
1.1 Project Team Making 2 days Wed 27-06-18
Thu 28-06-
18
1.2 Survey 5 days Fri 29-06-18
Thu 05-07-
18
2
1.3 Cyber security design 5 days Fri 06-07-18
Thu 12-07-
18
3
1.4
Examination of security
ystem
6 days Fri 13-07-18 Fri 20-07-18 4
1.6 Project proposal Making 7 days Mon 23-07-18
Tue 31-07-
18
5
2 Data Collection Method 8 days Wed 01-08-18 Fri 10-08-18
2.1
Analysing the Cyber
Security Risks
4 days Wed 01-08-18
Mon 06-08-
18
7

8CYBER SECURITY
2.2
Assesment of collected
data
4 days Tue 07-08-18 Fri 10-08-18 10
2.4 Data Collection Completed 0 days Fri 10-08-18 Fri 10-08-18 11
3
Implementing Architecture
of Cyber Security
22 days Mon 13-08-18
Tue 11-09-
18
3.1
Assessment of the
requirments
1 day Mon 13-08-18
Mon 13-08-
18
13
3.2
Making the implementation
method
3 days Tue 14-08-18
Thu 16-08-
18
15
3.3
Structure the whole
architecture
5 days Fri 17-08-18
Thu 23-08-
18
16
3.4
Installing the require
measurement
6 days Fri 24-08-18 Fri 31-08-18 17
3.5
Final analisys of whole
structure
7 days Mon 03-09-18
Tue 11-09-
18
18
3.7 Architecture Done Properly 0 days Tue 11-09-18
Tue 11-09-
18
19
4
Executing The Final
Project
4 days Wed 12-09-18
Mon 17-09-
18
4.1 Transition Period 1 day Wed 12-09-18
Wed 12-09-
18
21
2.2
Assesment of collected
data
4 days Tue 07-08-18 Fri 10-08-18 10
2.4 Data Collection Completed 0 days Fri 10-08-18 Fri 10-08-18 11
3
Implementing Architecture
of Cyber Security
22 days Mon 13-08-18
Tue 11-09-
18
3.1
Assessment of the
requirments
1 day Mon 13-08-18
Mon 13-08-
18
13
3.2
Making the implementation
method
3 days Tue 14-08-18
Thu 16-08-
18
15
3.3
Structure the whole
architecture
5 days Fri 17-08-18
Thu 23-08-
18
16
3.4
Installing the require
measurement
6 days Fri 24-08-18 Fri 31-08-18 17
3.5
Final analisys of whole
structure
7 days Mon 03-09-18
Tue 11-09-
18
18
3.7 Architecture Done Properly 0 days Tue 11-09-18
Tue 11-09-
18
19
4
Executing The Final
Project
4 days Wed 12-09-18
Mon 17-09-
18
4.1 Transition Period 1 day Wed 12-09-18
Wed 12-09-
18
21
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9CYBER SECURITY
4.2 Test Application 1 day Thu 13-09-18
Thu 13-09-
18
23
4.3 Progress analysis 1 day Fri 14-09-18 Fri 14-09-18 24
4.4 Final Execution 1 day Mon 17-09-18
Mon 17-09-
18
25
4.5 `Project Completed 0 days Mon 17-09-18
Mon 17-09-
18
26
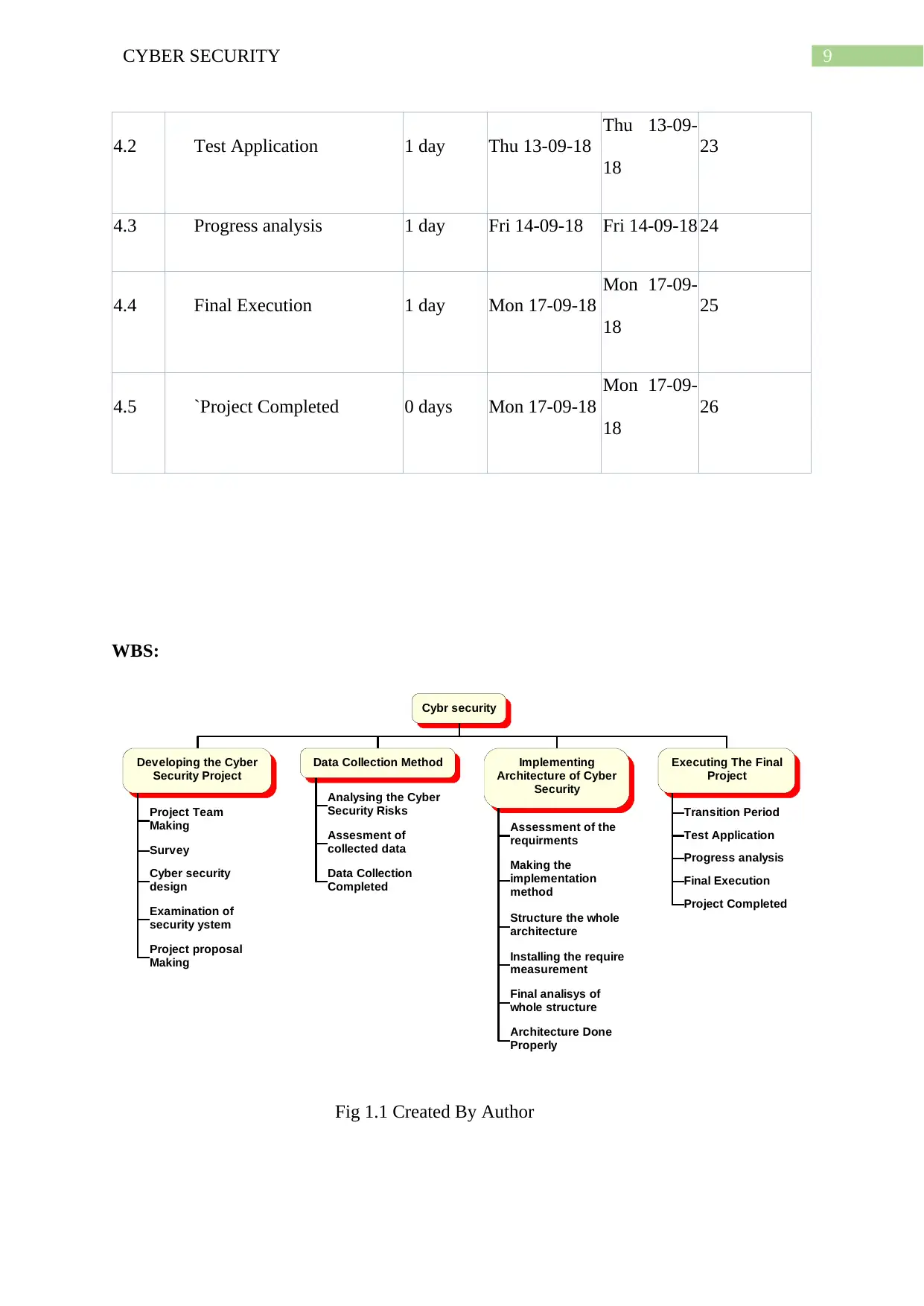
WBS:
Cybr security
Developing the Cyber
Security Project
Project Team
Making
Survey
Cyber security
design
Examination of
security ystem
Project proposal
Making
Data Collection Method
Analysing the Cyber
Security Risks
Assesment of
collected data
Data Collection
Completed
Implementing
Architecture of Cyber
Security
Assessment of the
requirments
Making the
implementation
method
Structure the whole
architecture
Installing the require
measurement
Final analisys of
whole structure
Architecture Done
Properly
Executing The Final
Project
Transition Period
Test Application
Progress analysis
Final Execution
Project Completed
Fig 1.1 Created By Author
4.2 Test Application 1 day Thu 13-09-18
Thu 13-09-
18
23
4.3 Progress analysis 1 day Fri 14-09-18 Fri 14-09-18 24
4.4 Final Execution 1 day Mon 17-09-18
Mon 17-09-
18
25
4.5 `Project Completed 0 days Mon 17-09-18
Mon 17-09-
18
26
WBS:
Cybr security
Developing the Cyber
Security Project
Project Team
Making
Survey
Cyber security
design
Examination of
security ystem
Project proposal
Making
Data Collection Method
Analysing the Cyber
Security Risks
Assesment of
collected data
Data Collection
Completed
Implementing
Architecture of Cyber
Security
Assessment of the
requirments
Making the
implementation
method
Structure the whole
architecture
Installing the require
measurement
Final analisys of
whole structure
Architecture Done
Properly
Executing The Final
Project
Transition Period
Test Application
Progress analysis
Final Execution
Project Completed
Fig 1.1 Created By Author
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10CYBER SECURITY
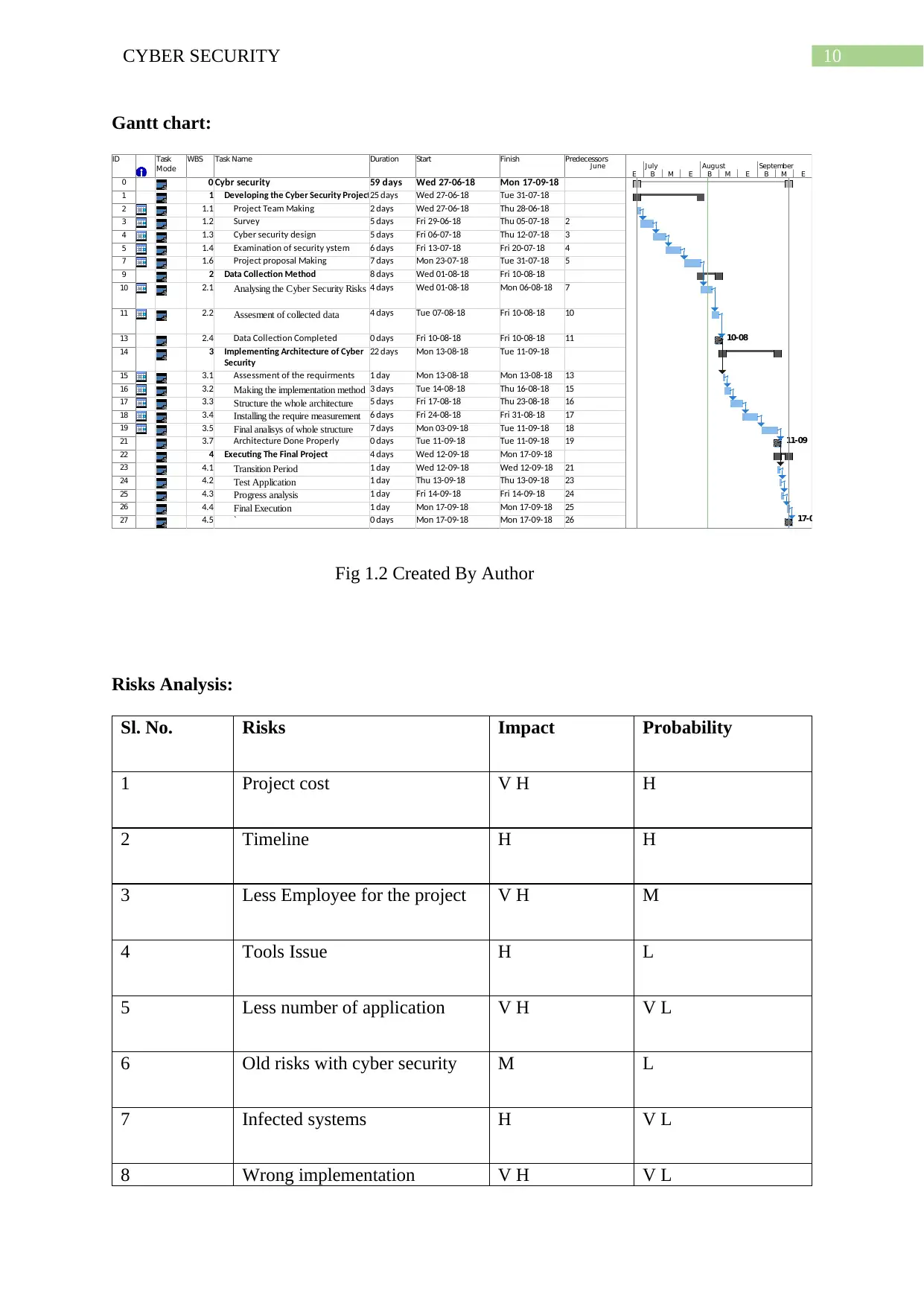
Gantt chart:
ID Task
Mode
WBS Task Name Duration Start Finish Predecessors
0 0 Cybr security 59 days Wed 27-06-18 Mon 17-09-18
1 1 Developing the Cyber Security Project25 days Wed 27-06-18 Tue 31-07-18
2 1.1 Project Team Making 2 days Wed 27-06-18 Thu 28-06-18
3 1.2 Survey 5 days Fri 29-06-18 Thu 05-07-18 2
4 1.3 Cyber security design 5 days Fri 06-07-18 Thu 12-07-18 3
5 1.4 Examination of security ystem 6 days Fri 13-07-18 Fri 20-07-18 4
7 1.6 Project proposal Making 7 days Mon 23-07-18 Tue 31-07-18 5
9 2 Data Collection Method 8 days Wed 01-08-18 Fri 10-08-18
10 2.1 Analysing the Cyber Security Risks 4 days Wed 01-08-18 Mon 06-08-18 7
11 2.2 Assesment of collected data 4 days Tue 07-08-18 Fri 10-08-18 10
13 2.4 Data Collection Completed 0 days Fri 10-08-18 Fri 10-08-18 11
14 3 Implementing Architecture of Cyber
Security
22 days Mon 13-08-18 Tue 11-09-18
15 3.1 Assessment of the requirments 1 day Mon 13-08-18 Mon 13-08-18 13
16 3.2 Making the implementation method 3 days Tue 14-08-18 Thu 16-08-18 15
17 3.3 Structure the whole architecture 5 days Fri 17-08-18 Thu 23-08-18 16
18 3.4 Installing the require measurement 6 days Fri 24-08-18 Fri 31-08-18 17
19 3.5 Final analisys of whole structure 7 days Mon 03-09-18 Tue 11-09-18 18
21 3.7 Architecture Done Properly 0 days Tue 11-09-18 Tue 11-09-18 19
22 4 Executing The Final Project 4 days Wed 12-09-18 Mon 17-09-18
23 4.1 Transition Period 1 day Wed 12-09-18 Wed 12-09-18 21
24 4.2 Test Application 1 day Thu 13-09-18 Thu 13-09-18 23
25 4.3 Progress analysis 1 day Fri 14-09-18 Fri 14-09-18 24
26 4.4 Final Execution 1 day Mon 17-09-18 Mon 17-09-18 25
27 4.5 ` 0 days Mon 17-09-18 Mon 17-09-18 26
10-08
11-09
17-09
E B M E B M E B M E
June July August September
Fig 1.2 Created By Author
Risks Analysis:
Sl. No. Risks Impact Probability
1 Project cost V H H
2 Timeline H H
3 Less Employee for the project V H M
4 Tools Issue H L
5 Less number of application V H V L
6 Old risks with cyber security M L
7 Infected systems H V L
8 Wrong implementation V H V L
Gantt chart:
ID Task
Mode
WBS Task Name Duration Start Finish Predecessors
0 0 Cybr security 59 days Wed 27-06-18 Mon 17-09-18
1 1 Developing the Cyber Security Project25 days Wed 27-06-18 Tue 31-07-18
2 1.1 Project Team Making 2 days Wed 27-06-18 Thu 28-06-18
3 1.2 Survey 5 days Fri 29-06-18 Thu 05-07-18 2
4 1.3 Cyber security design 5 days Fri 06-07-18 Thu 12-07-18 3
5 1.4 Examination of security ystem 6 days Fri 13-07-18 Fri 20-07-18 4
7 1.6 Project proposal Making 7 days Mon 23-07-18 Tue 31-07-18 5
9 2 Data Collection Method 8 days Wed 01-08-18 Fri 10-08-18
10 2.1 Analysing the Cyber Security Risks 4 days Wed 01-08-18 Mon 06-08-18 7
11 2.2 Assesment of collected data 4 days Tue 07-08-18 Fri 10-08-18 10
13 2.4 Data Collection Completed 0 days Fri 10-08-18 Fri 10-08-18 11
14 3 Implementing Architecture of Cyber
Security
22 days Mon 13-08-18 Tue 11-09-18
15 3.1 Assessment of the requirments 1 day Mon 13-08-18 Mon 13-08-18 13
16 3.2 Making the implementation method 3 days Tue 14-08-18 Thu 16-08-18 15
17 3.3 Structure the whole architecture 5 days Fri 17-08-18 Thu 23-08-18 16
18 3.4 Installing the require measurement 6 days Fri 24-08-18 Fri 31-08-18 17
19 3.5 Final analisys of whole structure 7 days Mon 03-09-18 Tue 11-09-18 18
21 3.7 Architecture Done Properly 0 days Tue 11-09-18 Tue 11-09-18 19
22 4 Executing The Final Project 4 days Wed 12-09-18 Mon 17-09-18
23 4.1 Transition Period 1 day Wed 12-09-18 Wed 12-09-18 21
24 4.2 Test Application 1 day Thu 13-09-18 Thu 13-09-18 23
25 4.3 Progress analysis 1 day Fri 14-09-18 Fri 14-09-18 24
26 4.4 Final Execution 1 day Mon 17-09-18 Mon 17-09-18 25
27 4.5 ` 0 days Mon 17-09-18 Mon 17-09-18 26
10-08
11-09
17-09
E B M E B M E B M E
June July August September
Fig 1.2 Created By Author
Risks Analysis:
Sl. No. Risks Impact Probability
1 Project cost V H H
2 Timeline H H
3 Less Employee for the project V H M
4 Tools Issue H L
5 Less number of application V H V L
6 Old risks with cyber security M L
7 Infected systems H V L
8 Wrong implementation V H V L
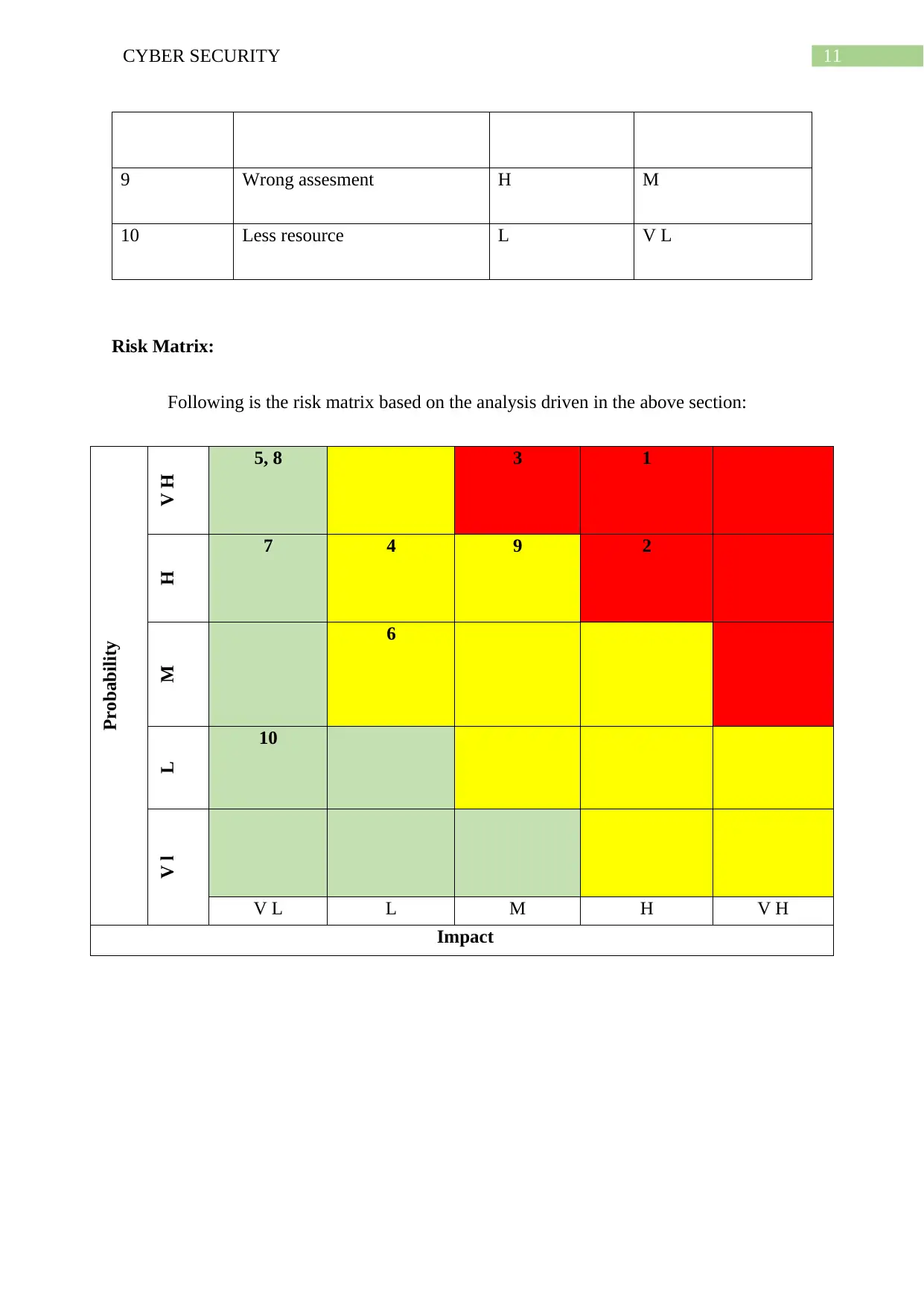
11CYBER SECURITY
9 Wrong assesment H M
10 Less resource L V L
Risk Matrix:
Following is the risk matrix based on the analysis driven in the above section:
Probability
V H 5, 8 3 1
H
7 4 9 2
M
6
L 10
V l
V L L M H V H
Impact
9 Wrong assesment H M
10 Less resource L V L
Risk Matrix:
Following is the risk matrix based on the analysis driven in the above section:
Probability
V H 5, 8 3 1
H
7 4 9 2
M
6
L 10
V l
V L L M H V H
Impact
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





