CMP71001: Security Report on BYOD and Authentication Systems
VerifiedAdded on 2022/11/14
|11
|2074
|181
Report
AI Summary
This report, prepared as a cybersecurity consultation, addresses the risks associated with a Bring Your Own Device (BYOD) policy implemented by Southern Cross University. Task 1 focuses on assessing the risks of BYOD, including identifying critical assets, potential threats, and vulnerabilities, and conducting a qualitative risk assessment. Task 2 explores certificate-based authentication as an alternative to password-based systems, detailing its working principles and advantages. Task 3 provides guidelines for handling phishing attacks, including instructions for both users and IT administrators. The report emphasizes the importance of BYOD security, certificate-based authentication, and awareness of phishing threats to maintain a secure information system, with references to relevant academic sources.

cybeR-SEcurity in southern cross university
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1: BOYD risk assessment.......................................................................................................1
1.1 BYOD risk assessment introduction......................................................................................1
1.2 Objectives of BYOD assessment...........................................................................................1
1.3 Scope of risk...........................................................................................................................1
1.4 Risk assessment approach......................................................................................................1
1.5 Critical components and assets that might be affected..........................................................1
1.6 Risk appetite...........................................................................................................................2
1.7 Potential threats and vulnerabilities.......................................................................................2
1.8 Qualitative risk assessment....................................................................................................4
Task 2: Certificate-Based Authentication........................................................................................4
2.1. Introduction...........................................................................................................................4
2.2. Working Principles of password-based authentication.........................................................5
2.3 Working principle of certificate-based authentication...........................................................5
2.4 Certificate-based authentication scheme................................................................................5
2.5 Comparison of username-password-based authentication and certificate-based
authentication...............................................................................................................................6
Task 3. Ant-phishing guidelines......................................................................................................6
3.1 Introduction to definition and characteristics of phishing.....................................................6
3.2 Characteristics of phishing act...............................................................................................7
3.3. Example of phishing activity................................................................................................7
3.4 Instructions for phishing handling to users............................................................................7
3.5 Instructions for phishing handling for IT admin....................................................................8
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
Task 1: BOYD risk assessment.......................................................................................................1
1.1 BYOD risk assessment introduction......................................................................................1
1.2 Objectives of BYOD assessment...........................................................................................1
1.3 Scope of risk...........................................................................................................................1
1.4 Risk assessment approach......................................................................................................1
1.5 Critical components and assets that might be affected..........................................................1
1.6 Risk appetite...........................................................................................................................2
1.7 Potential threats and vulnerabilities.......................................................................................2
1.8 Qualitative risk assessment....................................................................................................4
Task 2: Certificate-Based Authentication........................................................................................4
2.1. Introduction...........................................................................................................................4
2.2. Working Principles of password-based authentication.........................................................5
2.3 Working principle of certificate-based authentication...........................................................5
2.4 Certificate-based authentication scheme................................................................................5
2.5 Comparison of username-password-based authentication and certificate-based
authentication...............................................................................................................................6
Task 3. Ant-phishing guidelines......................................................................................................6
3.1 Introduction to definition and characteristics of phishing.....................................................6
3.2 Characteristics of phishing act...............................................................................................7
3.3. Example of phishing activity................................................................................................7
3.4 Instructions for phishing handling to users............................................................................7
3.5 Instructions for phishing handling for IT admin....................................................................8
Conclusion.......................................................................................................................................8
References........................................................................................................................................9

1
Task 1: BOYD risk assessment
1.1 BYOD risk assessment introduction.
It’s a process whereby individuals bring their devices like hardware and software in their
working place (Keyes, 2016). This technique works better in modern technological companies
and institutions like universities where there is need for technological services.
1.2 Objectives of BYOD assessment.
To find out the necessary technology needed for the success of BYOD.
To determine the cost which might be needed in the implementation of BYOD.
To determine loopholes and security issues that might arise during the usage of
BYOD.
1.3 Scope of risk
This refers to the areas in which the system is going to work and the limits it’s bound to cover
using the technology. Mostly, BYOD revolves around areas where there is minimal risk to be
made, like in the university.
1.4 Risk assessment approach
This refers to the process of identifying the negative occurrence which might hinder the proper
flow activities in the organization. This occurrence might lead to the collapsing of an institution
if not looked in keenly.
1.5 Critical components and assets that might be affected
Software running in the websites and web pages like the fee structures programs might be
hacked.
Task 1: BOYD risk assessment
1.1 BYOD risk assessment introduction.
It’s a process whereby individuals bring their devices like hardware and software in their
working place (Keyes, 2016). This technique works better in modern technological companies
and institutions like universities where there is need for technological services.
1.2 Objectives of BYOD assessment.
To find out the necessary technology needed for the success of BYOD.
To determine the cost which might be needed in the implementation of BYOD.
To determine loopholes and security issues that might arise during the usage of
BYOD.
1.3 Scope of risk
This refers to the areas in which the system is going to work and the limits it’s bound to cover
using the technology. Mostly, BYOD revolves around areas where there is minimal risk to be
made, like in the university.
1.4 Risk assessment approach
This refers to the process of identifying the negative occurrence which might hinder the proper
flow activities in the organization. This occurrence might lead to the collapsing of an institution
if not looked in keenly.
1.5 Critical components and assets that might be affected
Software running in the websites and web pages like the fee structures programs might be
hacked.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2
The databases of students of the institution and their fee structure might have been given
a path of easy interruption hence can end up being hacked by using things like the SQL
injection which are malicious (Bisht, Madhusudan and Venkatakrishnan, 2010)
1.6 Risk appetite
This refers to the level at which the organization is able to take a technology risk in order to
accomplish its objectives (Spear, 2015). It represents potential benefits and losses the
organization may end up having if the particular technology is implemented. The risk appetite
usually contains features like stockholders’ expectations, organization objectives, and plan. It
also includes other features like showing business key assets, tolerance for loss, willingness and
capacity to take risks, skill available, technologies and resources.
1.7 Potential threats and vulnerabilities
There are several vulnerabilities the system of the university might end up having. They include
the following;
Ransomware is a program application made to stop anyone to access the system unless the
agreed amount of money is paid (Gazet, 2010). This is very dangerous especially for institutions
like universities which might have skilled personnel like students to sabotage the system using
their skills.
Social engineering, through psychological manipulation can lead to university management
rendering information to unauthorized personnel (Wondracek et al., 2010). This can lead to
access to the database.
DoS – this is where hackers prevent users from accessing services by sending excess messages
requesting authentication requests that have return addresses that are invalid (Gupta and
Thilagam, 2013).
The databases of students of the institution and their fee structure might have been given
a path of easy interruption hence can end up being hacked by using things like the SQL
injection which are malicious (Bisht, Madhusudan and Venkatakrishnan, 2010)
1.6 Risk appetite
This refers to the level at which the organization is able to take a technology risk in order to
accomplish its objectives (Spear, 2015). It represents potential benefits and losses the
organization may end up having if the particular technology is implemented. The risk appetite
usually contains features like stockholders’ expectations, organization objectives, and plan. It
also includes other features like showing business key assets, tolerance for loss, willingness and
capacity to take risks, skill available, technologies and resources.
1.7 Potential threats and vulnerabilities
There are several vulnerabilities the system of the university might end up having. They include
the following;
Ransomware is a program application made to stop anyone to access the system unless the
agreed amount of money is paid (Gazet, 2010). This is very dangerous especially for institutions
like universities which might have skilled personnel like students to sabotage the system using
their skills.
Social engineering, through psychological manipulation can lead to university management
rendering information to unauthorized personnel (Wondracek et al., 2010). This can lead to
access to the database.
DoS – this is where hackers prevent users from accessing services by sending excess messages
requesting authentication requests that have return addresses that are invalid (Gupta and
Thilagam, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3
Lack of appropriate security controls. The university is unable to prevent unintentional and
intentional interference which pose threats to information systems (Stallings et al., 2012).
Out dated security polies bring about a false sense of security while in reality, technology keeps
on changing and therefore posing threats to the university (Metke and Ekl, 2010).
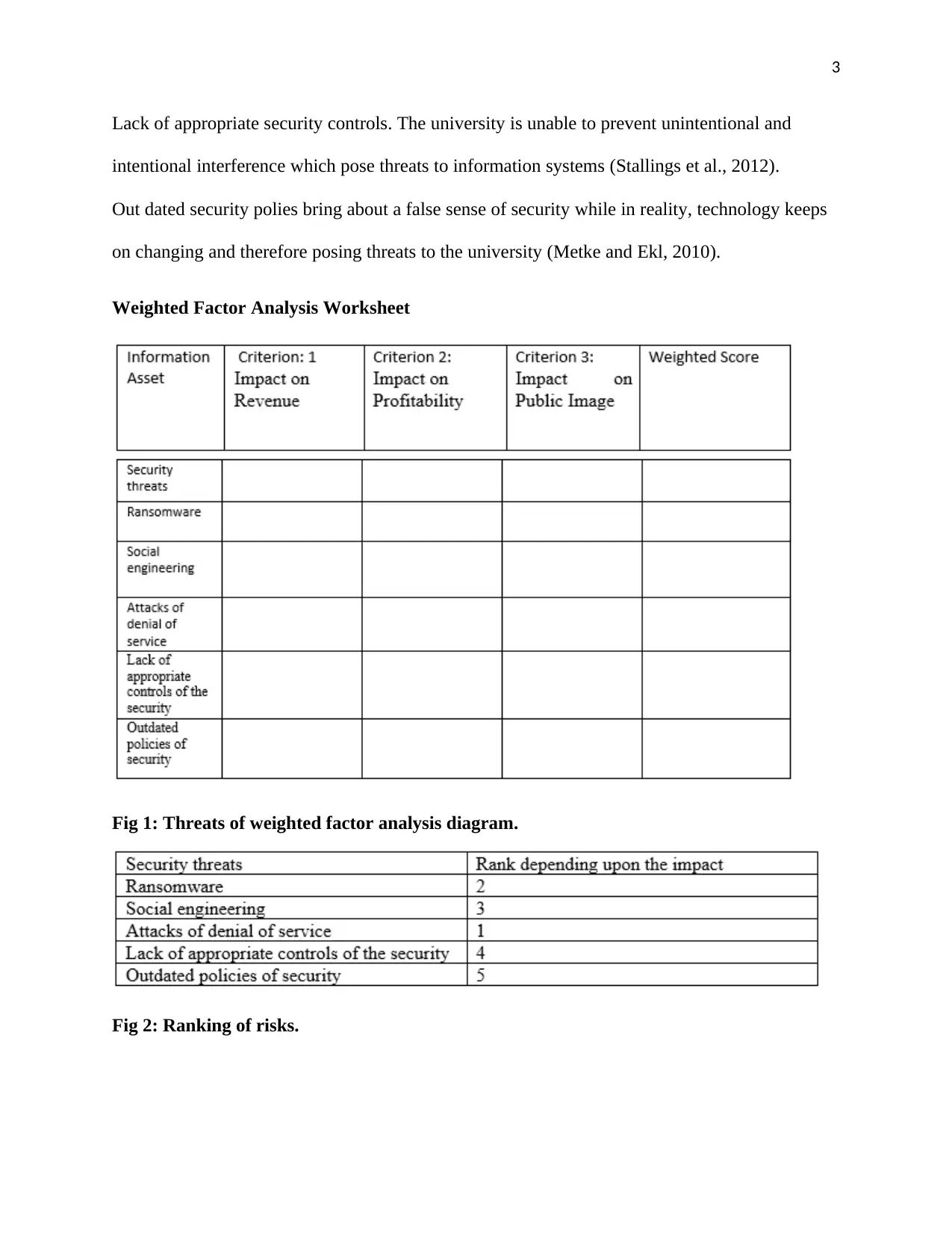
Weighted Factor Analysis Worksheet
Fig 1: Threats of weighted factor analysis diagram.
Fig 2: Ranking of risks.
Lack of appropriate security controls. The university is unable to prevent unintentional and
intentional interference which pose threats to information systems (Stallings et al., 2012).
Out dated security polies bring about a false sense of security while in reality, technology keeps
on changing and therefore posing threats to the university (Metke and Ekl, 2010).
Weighted Factor Analysis Worksheet
Fig 1: Threats of weighted factor analysis diagram.
Fig 2: Ranking of risks.
4
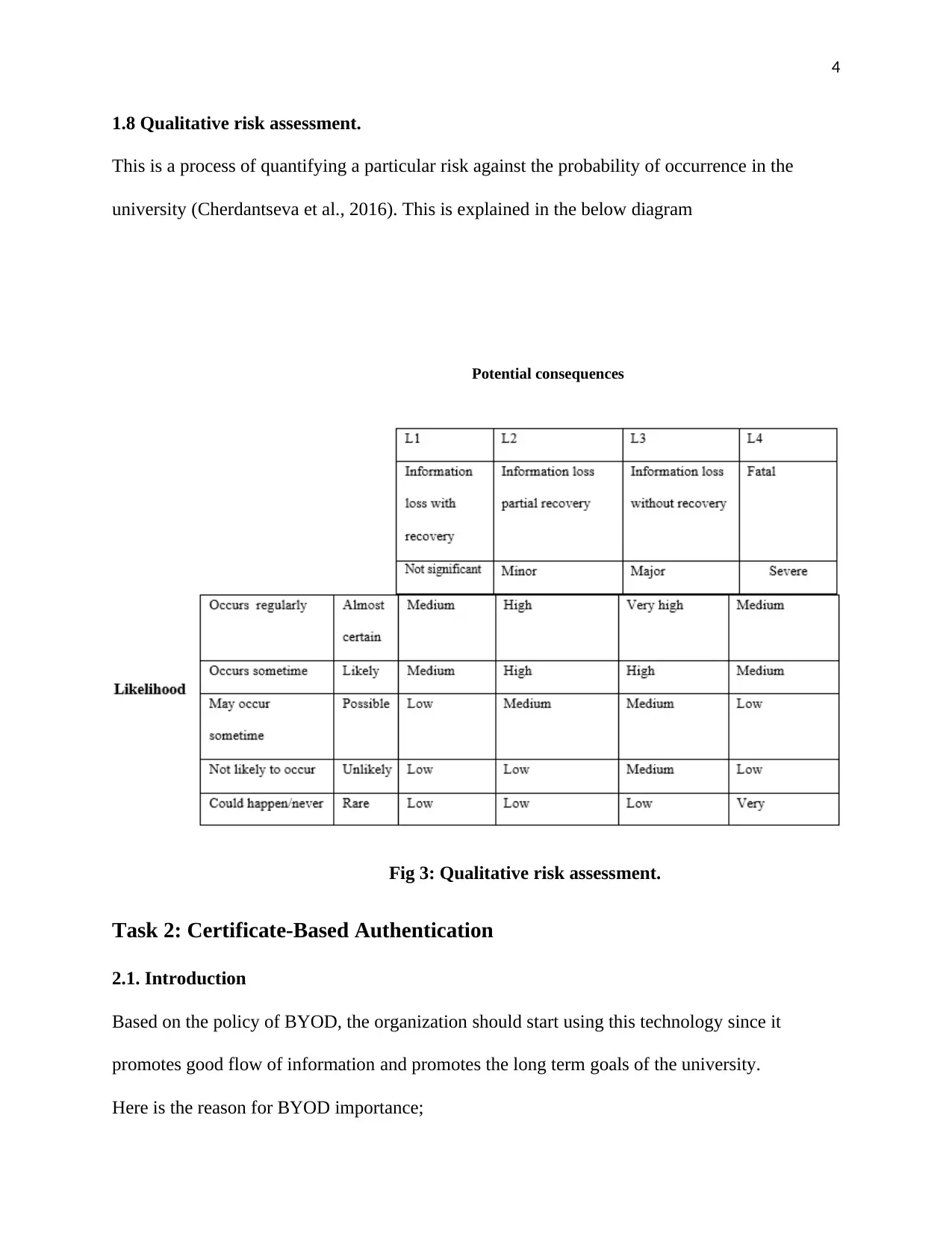
1.8 Qualitative risk assessment.
This is a process of quantifying a particular risk against the probability of occurrence in the
university (Cherdantseva et al., 2016). This is explained in the below diagram
Potential consequences
Fig 3: Qualitative risk assessment.
Task 2: Certificate-Based Authentication
2.1. Introduction
Based on the policy of BYOD, the organization should start using this technology since it
promotes good flow of information and promotes the long term goals of the university.
Here is the reason for BYOD importance;
1.8 Qualitative risk assessment.
This is a process of quantifying a particular risk against the probability of occurrence in the
university (Cherdantseva et al., 2016). This is explained in the below diagram
Potential consequences
Fig 3: Qualitative risk assessment.
Task 2: Certificate-Based Authentication
2.1. Introduction
Based on the policy of BYOD, the organization should start using this technology since it
promotes good flow of information and promotes the long term goals of the university.
Here is the reason for BYOD importance;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5
BYOD will reduce training since the employees associate with the devices daily and its’s also
cost-effective to the organization.
2.2. Working Principles of password-based authentication.
The first step is for the user to enter the password, the user then sends the information to the
server which includes username and password. The server determines whether the password and
the username are correct. If both details are correct, the user can then access the resources else
he/she will be denied the relevant authority. All these data are taken to the server for
confirmation of an individual (Wang et al., 2009).
2.3 Working principle of certificate-based authentication
For one to get id which acts as a certificate, an individual has to provide some level of
confirmation that he/she is a person claiming to be. Authorities of certificate validate identities
and then issue the necessary certificate to be used. Certificate of authentication can be either
independent third parties or their own certificate-provision server software, such as System Pf.
The methods used for validating identity vary depending on the policies of a given CA for that
type of certificate (Zhang, Wang and Li, 2010).
2.4 Certificate-based authentication scheme.
Refers to the scheme that uses digital certificate and cryptography to authenticate the client
(Zhang, Wang and Li, 2010). A certificate contains a digital signature, public key and
identification data. The certificate authenticator must confirm details of an individual.
Only public certified personnel can access the information system hence preventing
impersonating
BYOD will reduce training since the employees associate with the devices daily and its’s also
cost-effective to the organization.
2.2. Working Principles of password-based authentication.
The first step is for the user to enter the password, the user then sends the information to the
server which includes username and password. The server determines whether the password and
the username are correct. If both details are correct, the user can then access the resources else
he/she will be denied the relevant authority. All these data are taken to the server for
confirmation of an individual (Wang et al., 2009).
2.3 Working principle of certificate-based authentication
For one to get id which acts as a certificate, an individual has to provide some level of
confirmation that he/she is a person claiming to be. Authorities of certificate validate identities
and then issue the necessary certificate to be used. Certificate of authentication can be either
independent third parties or their own certificate-provision server software, such as System Pf.
The methods used for validating identity vary depending on the policies of a given CA for that
type of certificate (Zhang, Wang and Li, 2010).
2.4 Certificate-based authentication scheme.
Refers to the scheme that uses digital certificate and cryptography to authenticate the client
(Zhang, Wang and Li, 2010). A certificate contains a digital signature, public key and
identification data. The certificate authenticator must confirm details of an individual.
Only public certified personnel can access the information system hence preventing
impersonating
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
6
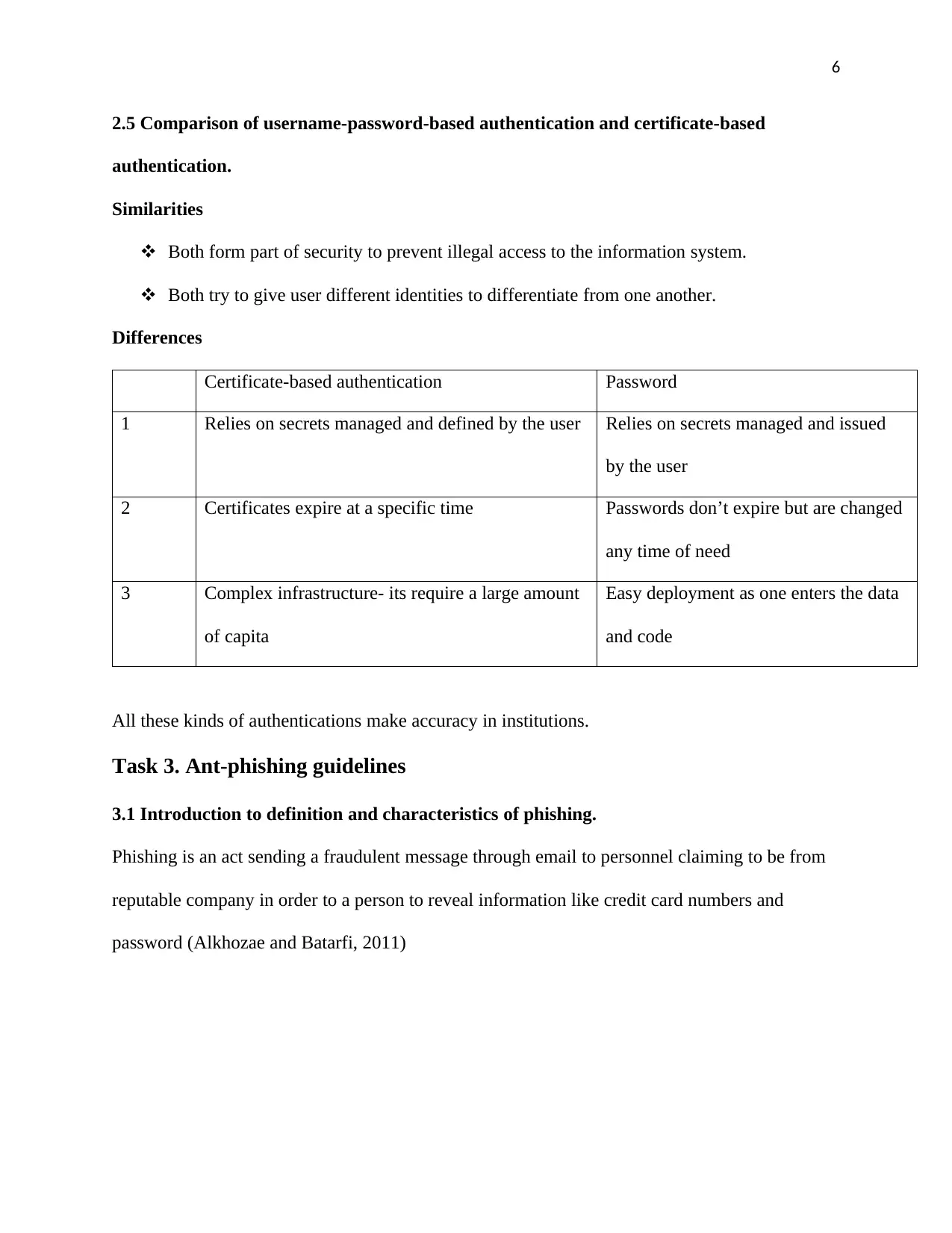
2.5 Comparison of username-password-based authentication and certificate-based
authentication.
Similarities
Both form part of security to prevent illegal access to the information system.
Both try to give user different identities to differentiate from one another.
Differences
Certificate-based authentication Password
1 Relies on secrets managed and defined by the user Relies on secrets managed and issued
by the user
2 Certificates expire at a specific time Passwords don’t expire but are changed
any time of need
3 Complex infrastructure- its require a large amount
of capita
Easy deployment as one enters the data
and code
All these kinds of authentications make accuracy in institutions.
Task 3. Ant-phishing guidelines
3.1 Introduction to definition and characteristics of phishing.
Phishing is an act sending a fraudulent message through email to personnel claiming to be from
reputable company in order to a person to reveal information like credit card numbers and
password (Alkhozae and Batarfi, 2011)
2.5 Comparison of username-password-based authentication and certificate-based
authentication.
Similarities
Both form part of security to prevent illegal access to the information system.
Both try to give user different identities to differentiate from one another.
Differences
Certificate-based authentication Password
1 Relies on secrets managed and defined by the user Relies on secrets managed and issued
by the user
2 Certificates expire at a specific time Passwords don’t expire but are changed
any time of need
3 Complex infrastructure- its require a large amount
of capita
Easy deployment as one enters the data
and code
All these kinds of authentications make accuracy in institutions.
Task 3. Ant-phishing guidelines
3.1 Introduction to definition and characteristics of phishing.
Phishing is an act sending a fraudulent message through email to personnel claiming to be from
reputable company in order to a person to reveal information like credit card numbers and
password (Alkhozae and Batarfi, 2011)

7
3.2 Characteristics of phishing act
The phisher seems to make the appearance of being trusted by the people by creating a
website that mimics the original website which might be a government institution or a
financial institution.
A Phisher sends threats to a user regarding the financial decision to convince him or her
to share details (Kim and Huh, 2011).
3.3. Example of phishing activity
An email sent to request for personal information from users like a bank account. These
emails require the user’s details urgently.
A forged link from an account claiming your account has been suspended due
unreasonable reasons.
A malicious Facebook message that comes from a fake account of with the users is
familiar with directing a person to YouTube spoofed page that later tells users to install a
chrome extension.
A CEO fake account directing customers using the fake account.
3.4 Instructions for phishing handling to users.
Users should use ant phishing authentication. This will prevent phishing activity since it
filters emails which phishers have sent. If users see any grammar error on emails they
should avoid opening them.
Never respond to emails asking for personal information
Always call the bank or Visit to access the financial information
Determine and know who to contact in case you become a victim of phishing
3.2 Characteristics of phishing act
The phisher seems to make the appearance of being trusted by the people by creating a
website that mimics the original website which might be a government institution or a
financial institution.
A Phisher sends threats to a user regarding the financial decision to convince him or her
to share details (Kim and Huh, 2011).
3.3. Example of phishing activity
An email sent to request for personal information from users like a bank account. These
emails require the user’s details urgently.
A forged link from an account claiming your account has been suspended due
unreasonable reasons.
A malicious Facebook message that comes from a fake account of with the users is
familiar with directing a person to YouTube spoofed page that later tells users to install a
chrome extension.
A CEO fake account directing customers using the fake account.
3.4 Instructions for phishing handling to users.
Users should use ant phishing authentication. This will prevent phishing activity since it
filters emails which phishers have sent. If users see any grammar error on emails they
should avoid opening them.
Never respond to emails asking for personal information
Always call the bank or Visit to access the financial information
Determine and know who to contact in case you become a victim of phishing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

8
3.5 Instructions for phishing handling for IT admin
Technology changes with time and phishing has also revolutionized with new techniques coming
up. There is a need to invest more in technology to reduce the cases and incidence of phishing in
society.
Conclusion
The BOYD technique can bring significant growth to an organization given that it saves
resources since employs use their own equipment which they bring at work. The use of
certificated-based authentication will prevent a large amount of fraud in an organization. There is
a need to create more public awareness of phishing to reduce the number of damages caused by
phishing.
3.5 Instructions for phishing handling for IT admin
Technology changes with time and phishing has also revolutionized with new techniques coming
up. There is a need to invest more in technology to reduce the cases and incidence of phishing in
society.
Conclusion
The BOYD technique can bring significant growth to an organization given that it saves
resources since employs use their own equipment which they bring at work. The use of
certificated-based authentication will prevent a large amount of fraud in an organization. There is
a need to create more public awareness of phishing to reduce the number of damages caused by
phishing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

9
References
Alkhozae, M.G. and Batarfi, O.A., 2011. Phishing websites detection based on phishing
characteristics in the webpage source code. International Journal of Information and
Communication Technology Research, 1(6).
Bisht, P., Madhusudan, P. and Venkatakrishnan, V.N., 2010. CANDID: Dynamic candidate
evaluations for automatic prevention of SQL injection attacks. ACM Transactions on
Information and System Security (TISSEC), 13(2), p.14.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. Computers &
security, 56, pp.1-27.
Gazet, A., 2010. Comparative analysis of various ransomware virii. Journal in computer
virology, 6(1), pp.77-90.
Gupta, A.N. and Thilagam, P.S., 2013. Attacks on web services need to secure XML on web.
Computer Science & Engineering, 3(5), p.1.
Keyes, J., 2016. Bring your own devices (BYOD) survival guide. Auerbach Publications.
Kim, H. and Huh, J.H., 2011. Detecting DNS-poisoning-based phishing attacks from their
network performance characteristics. Electronics Letters, 47(11), pp.656-658.
Metke, A.R. and Ekl, R.L., 2010. Security technology for smart grid networks. IEEE
Transactions on Smart Grid, 1(1), pp.99-107.
Spear, M., 2015. Industrial Cyber Security 101. Honeywell Users Group Europe, Middle East
and Africa.
Stallings, W., Brown, L., Bauer, M.D. and Bhattacharjee, A.K., 2012. Computer security:
principles and practice (pp. 978-0). Upper Saddle River (NJ: Pearson Education.
Wang, Y.Y., Liu, J.Y., Xiao, F.X. and Dan, J., 2009. A more efficient and secure dynamic ID-
based remote user authentication scheme. Computer communications, 32(4), pp.583-585.
Wondracek, G., Holz, T., Kirda, E. and Kruegel, C., 2010, May. A practical attack to de-
anonymize social network users. In 2010 IEEE Symposium on Security and Privacy (pp.
223-238). IEEE.
Zhang, J., Wang, C.C. and Li, J., Thomson Licensing SA, 2010. Certificate based authentication
authorization accounting scheme for loose coupling interworking. U.S. Patent 7,735,126.
References
Alkhozae, M.G. and Batarfi, O.A., 2011. Phishing websites detection based on phishing
characteristics in the webpage source code. International Journal of Information and
Communication Technology Research, 1(6).
Bisht, P., Madhusudan, P. and Venkatakrishnan, V.N., 2010. CANDID: Dynamic candidate
evaluations for automatic prevention of SQL injection attacks. ACM Transactions on
Information and System Security (TISSEC), 13(2), p.14.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. Computers &
security, 56, pp.1-27.
Gazet, A., 2010. Comparative analysis of various ransomware virii. Journal in computer
virology, 6(1), pp.77-90.
Gupta, A.N. and Thilagam, P.S., 2013. Attacks on web services need to secure XML on web.
Computer Science & Engineering, 3(5), p.1.
Keyes, J., 2016. Bring your own devices (BYOD) survival guide. Auerbach Publications.
Kim, H. and Huh, J.H., 2011. Detecting DNS-poisoning-based phishing attacks from their
network performance characteristics. Electronics Letters, 47(11), pp.656-658.
Metke, A.R. and Ekl, R.L., 2010. Security technology for smart grid networks. IEEE
Transactions on Smart Grid, 1(1), pp.99-107.
Spear, M., 2015. Industrial Cyber Security 101. Honeywell Users Group Europe, Middle East
and Africa.
Stallings, W., Brown, L., Bauer, M.D. and Bhattacharjee, A.K., 2012. Computer security:
principles and practice (pp. 978-0). Upper Saddle River (NJ: Pearson Education.
Wang, Y.Y., Liu, J.Y., Xiao, F.X. and Dan, J., 2009. A more efficient and secure dynamic ID-
based remote user authentication scheme. Computer communications, 32(4), pp.583-585.
Wondracek, G., Holz, T., Kirda, E. and Kruegel, C., 2010, May. A practical attack to de-
anonymize social network users. In 2010 IEEE Symposium on Security and Privacy (pp.
223-238). IEEE.
Zhang, J., Wang, C.C. and Li, J., Thomson Licensing SA, 2010. Certificate based authentication
authorization accounting scheme for loose coupling interworking. U.S. Patent 7,735,126.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





