Cybersecurity Report: Threats, Business Continuity, and Security
VerifiedAdded on 2023/01/11
|27
|5578
|23
Report
AI Summary
This cybersecurity report provides an in-depth analysis of various threats and potential solutions, focusing on business continuity management (BCM) and its importance in mitigating risks. The report explores the BCM framework, its advantages, and the critical role of top management support and effective training. It details different types of cyber threats, including viruses, malware, spamming, data theft, spyware, rootkits, and man-in-the-middle attacks. The report also discusses various platforms for data backup, such as hot, warm, and cold sites, and their respective advantages and disadvantages. Furthermore, it covers access control, incident response, auditing, and physical and environmental procedures. The report also addresses how to prevent hackers from finding and reading files, emphasizing the importance of security measures like using encrypted wireless keys, installing anti-malware software, and practicing safe email habits. This report provides a comprehensive overview of cybersecurity concepts and practical solutions to safeguard systems from potential threats.

Cybersecurity
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction...................................................................................................3
L01...............................................................................................................4
P1..............................................................................................................4
P2..............................................................................................................6
Lo2...............................................................................................................7
P3.................................................................................................................7
1.................................................................................................................7
2.................................................................................................................7
3.................................................................................................................8
P4.................................................................................................................8
Lo3...............................................................................................................9
P5..............................................................................................................9
P6..............................................................................................................9
Lo4.............................................................................................................10
P7............................................................................................................10
P8............................................................................................................10
Conclusion..................................................................................................11
References.................................................................................................12
2
Introduction...................................................................................................3
L01...............................................................................................................4
P1..............................................................................................................4
P2..............................................................................................................6
Lo2...............................................................................................................7
P3.................................................................................................................7
1.................................................................................................................7
2.................................................................................................................7
3.................................................................................................................8
P4.................................................................................................................8
Lo3...............................................................................................................9
P5..............................................................................................................9
P6..............................................................................................................9
Lo4.............................................................................................................10
P7............................................................................................................10
P8............................................................................................................10
Conclusion..................................................................................................11
References.................................................................................................12
2

Introduction
This assessment provides information about the threats of security that can
be faced at a maximum level in the present scenario. This assessment
represents the possible solutions that can be used by users to protect their
systems from hackers. There is a discussion of four tasks. The report will
initiate with task 1 discussion that provides data about the management of
business continuity. In the next phase, this report will discuss 3 different
task which deals with cybersecurity concept. The topics covered in this
report are management of business continuity, techniques for security,
controlling of security & social engineering.
Figure 1: Cyber security breach
3
This assessment provides information about the threats of security that can
be faced at a maximum level in the present scenario. This assessment
represents the possible solutions that can be used by users to protect their
systems from hackers. There is a discussion of four tasks. The report will
initiate with task 1 discussion that provides data about the management of
business continuity. In the next phase, this report will discuss 3 different
task which deals with cybersecurity concept. The topics covered in this
report are management of business continuity, techniques for security,
controlling of security & social engineering.
Figure 1: Cyber security breach
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

L01.
P1
Business Continuity Management: The substructure used for knowing
the risk of disclosure of an organization to external risk and internal risk is
referred to as a business continuity management framework. BCM can
react to threats like data breaches and also the business interest of the
organization. It also consists of recovery from disaster, emergency,
business recovery, incident, and the hazards of management(Goff, 2017).
4
P1
Business Continuity Management: The substructure used for knowing
the risk of disclosure of an organization to external risk and internal risk is
referred to as a business continuity management framework. BCM can
react to threats like data breaches and also the business interest of the
organization. It also consists of recovery from disaster, emergency,
business recovery, incident, and the hazards of management(Goff, 2017).
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
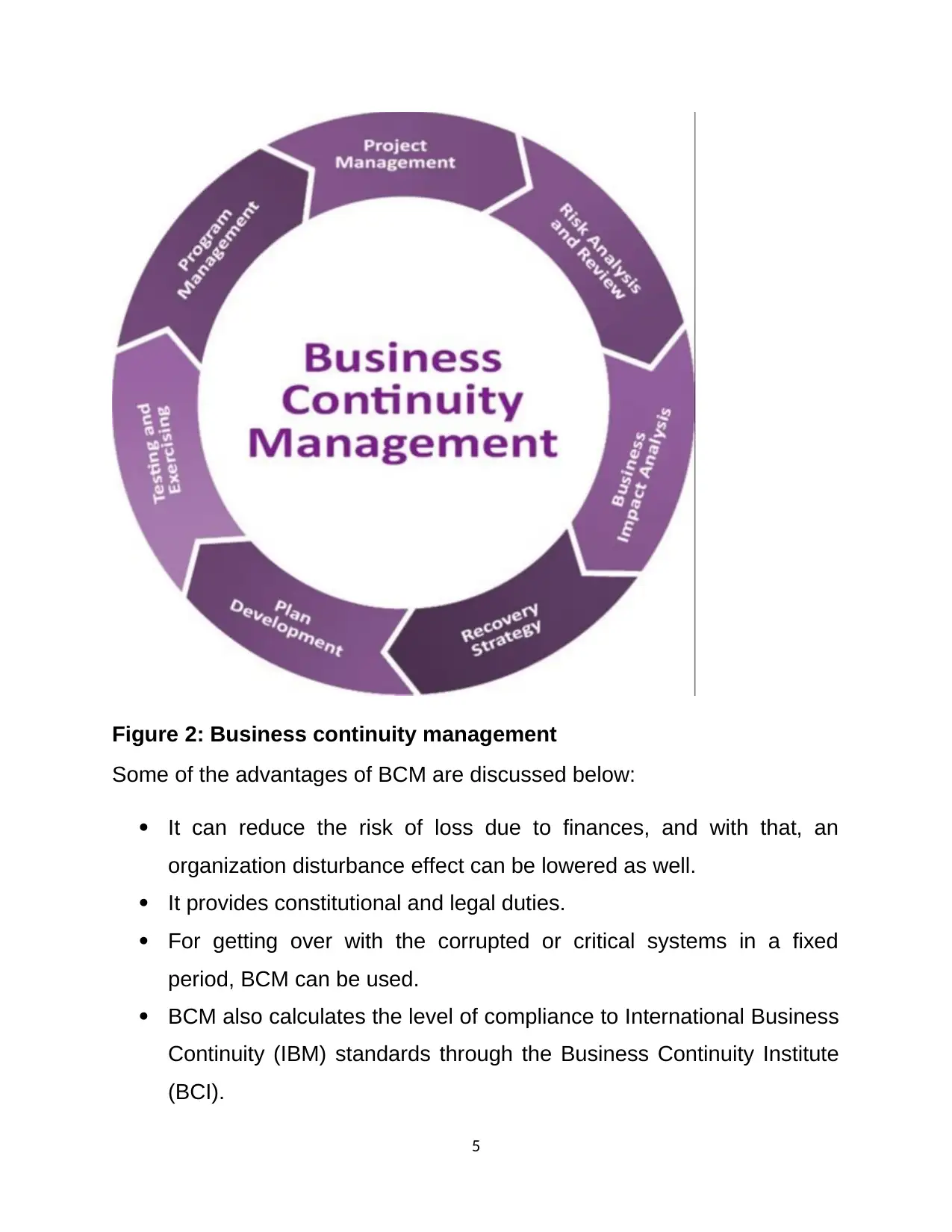
Figure 2: Business continuity management
Some of the advantages of BCM are discussed below:
It can reduce the risk of loss due to finances, and with that, an
organization disturbance effect can be lowered as well.
It provides constitutional and legal duties.
For getting over with the corrupted or critical systems in a fixed
period, BCM can be used.
BCM also calculates the level of compliance to International Business
Continuity (IBM) standards through the Business Continuity Institute
(BCI).
5
Some of the advantages of BCM are discussed below:
It can reduce the risk of loss due to finances, and with that, an
organization disturbance effect can be lowered as well.
It provides constitutional and legal duties.
For getting over with the corrupted or critical systems in a fixed
period, BCM can be used.
BCM also calculates the level of compliance to International Business
Continuity (IBM) standards through the Business Continuity Institute
(BCI).
5

All the different countries and various organizations are interested in the
implementation of BCM. The reason behind that is, BCM can control all the
threats of the organization. However, for each organization due to the
tough competitive pressure, BCM has become the best high-interest topic,
the reason being the nonstop business. BCM's importance in an
organization is due to many great reasons. Some of the reasons are
discussed below:
a. ‘Top Management Support’, for better implementation of BCM on any
company this is the first important factor. If any company has this
factor than there will be no obstacles in implementing BCM in any
company because it would be funded sufficiently and that’s enough
for enduring the program of the company.
b. 'Ability to deliver the best effective training', for an organization's
implementation this the second important factor. The staff of the
organization gets the best training regarding the use of the system by
the trainers. This step minimizes the level of threats.
c. Companies or organization that supports IT (Information Technology)
department can also get BCM implemented in their company. That
means it is not limited to the IT sector only.
d. For better and flexible delivery of the good to the client, many
companies or businesses use this program.
e. Every staff member of different departments of an organization at
each level must be able to do their job honestly, that is why
awareness is also an essential factor of BCM.
Every business that uses that uses their systems over internet are
surrounded with various risks such as:
6
implementation of BCM. The reason behind that is, BCM can control all the
threats of the organization. However, for each organization due to the
tough competitive pressure, BCM has become the best high-interest topic,
the reason being the nonstop business. BCM's importance in an
organization is due to many great reasons. Some of the reasons are
discussed below:
a. ‘Top Management Support’, for better implementation of BCM on any
company this is the first important factor. If any company has this
factor than there will be no obstacles in implementing BCM in any
company because it would be funded sufficiently and that’s enough
for enduring the program of the company.
b. 'Ability to deliver the best effective training', for an organization's
implementation this the second important factor. The staff of the
organization gets the best training regarding the use of the system by
the trainers. This step minimizes the level of threats.
c. Companies or organization that supports IT (Information Technology)
department can also get BCM implemented in their company. That
means it is not limited to the IT sector only.
d. For better and flexible delivery of the good to the client, many
companies or businesses use this program.
e. Every staff member of different departments of an organization at
each level must be able to do their job honestly, that is why
awareness is also an essential factor of BCM.
Every business that uses that uses their systems over internet are
surrounded with various risks such as:
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Virus: These are the malicious files that were entered into the client
system by the hacker to steal data and harm system resources.
2. Malware: These are the type of virus that are known specially for
stealing information from user’s system.
3. Spamming: In this type of risk the user is redirected to the similar
looking website that the user is used to of and steal the information
related to their login credentials, credit card information and more.
4. Data theft: In this type of threat the user data is steal by the hacker
from the users system without knowing the user with the help of
various malicious software.
5. Spyware: it gathers information of user and transmit it to third party
which is unauthorized. It works similar as other forms of malware in
which it takes benefit of web browser and software vulnerabilities.
Due to its undetectable and embedded features, its host might
convince user that it is a legal website, program or email which
convince user to check the link and download a program in order to
get access. It is designed to eliminate detection but can have issues
like increase pop ups, slow computer performance, frequent
unexpected browsing searches etc. It is the most prevalent network
risk which can infect complete network through one computer as well
as can convey crucial information or data back to the attacker (Dalby,
2016).
6. Rootkit: it is a software tools collection that allow administration level
access and remote control over computer networks a computer.
When remote access is acquired once, the rootkit can carry out
various malicious actions which are equipped with antivirus disablers,
password stealers and key loggers. These are installed by hiding
7
system by the hacker to steal data and harm system resources.
2. Malware: These are the type of virus that are known specially for
stealing information from user’s system.
3. Spamming: In this type of risk the user is redirected to the similar
looking website that the user is used to of and steal the information
related to their login credentials, credit card information and more.
4. Data theft: In this type of threat the user data is steal by the hacker
from the users system without knowing the user with the help of
various malicious software.
5. Spyware: it gathers information of user and transmit it to third party
which is unauthorized. It works similar as other forms of malware in
which it takes benefit of web browser and software vulnerabilities.
Due to its undetectable and embedded features, its host might
convince user that it is a legal website, program or email which
convince user to check the link and download a program in order to
get access. It is designed to eliminate detection but can have issues
like increase pop ups, slow computer performance, frequent
unexpected browsing searches etc. It is the most prevalent network
risk which can infect complete network through one computer as well
as can convey crucial information or data back to the attacker (Dalby,
2016).
6. Rootkit: it is a software tools collection that allow administration level
access and remote control over computer networks a computer.
When remote access is acquired once, the rootkit can carry out
various malicious actions which are equipped with antivirus disablers,
password stealers and key loggers. These are installed by hiding
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

legal software. When a business give permission to that software in
order to make changes to operating system, the rootkit installs itself
in system and wait for hacker to active it.
7. Man in the middle attacks: these are the cyber security attacks
which enable attacker to eavesdrop on interaction between two
targets. This attack occurs when attackers want to interrupt a
communication between individual A and individual B. Individual A
send public key to individual B, yet attacker intercepts it and a forged
message is sent to individual B, representing themselves as A.
Apart from these, there are certain another risks including unauthorised
use of a system, damage to or destruction of physical system
environment and asset, destruction of data or code outside or inside the
system, unauthorised copying or removal of data from a system,
naturally occurring risks etc. All these are the other types of risks for
organisation (Nathan, and Scobell, 2015).
8
order to make changes to operating system, the rootkit installs itself
in system and wait for hacker to active it.
7. Man in the middle attacks: these are the cyber security attacks
which enable attacker to eavesdrop on interaction between two
targets. This attack occurs when attackers want to interrupt a
communication between individual A and individual B. Individual A
send public key to individual B, yet attacker intercepts it and a forged
message is sent to individual B, representing themselves as A.
Apart from these, there are certain another risks including unauthorised
use of a system, damage to or destruction of physical system
environment and asset, destruction of data or code outside or inside the
system, unauthorised copying or removal of data from a system,
naturally occurring risks etc. All these are the other types of risks for
organisation (Nathan, and Scobell, 2015).
8

P2
Given below are the platforms available for a different organization for
backing up their important data:
1. HOT SITE:
A hot site is also referred to as a backup site that runs continuously.
This site helps the company to maintain its business process and
perform its operations normally. This will take very little time after
facing any threat or risk. The hot site helps to arrange the business
operations of the company that will be arranged with cloud
technology. A hot site related to the main concept is that it will always
work in online mode & perform all operations vastly. The overall hot
site has to be furnished and connected with appropriate hardware,
software, network & effective internet connection. At this, continuous
back up of data has been taken at the constant tome. The hot site is
not looking the same as the normal sites within an organization due
to disasters happening within an organization as they affect the site.
Hence, hot sites have been used because of its additional
features(wpadmin, 2016).
2. Warm site:
This site is also referred to as the backup file but it seems to differ
with the hot site as per the difference of its equipped. The warm site
has been furnished with the power, network, or the phone. The user
of warm sit works with different resources as it works over multiple
servers. A warm site is not working as same as the hot site as it
responds after some delay as compared to the hot site. The warm
site uses organization can easily affect by the disasters as it takes
9
Given below are the platforms available for a different organization for
backing up their important data:
1. HOT SITE:
A hot site is also referred to as a backup site that runs continuously.
This site helps the company to maintain its business process and
perform its operations normally. This will take very little time after
facing any threat or risk. The hot site helps to arrange the business
operations of the company that will be arranged with cloud
technology. A hot site related to the main concept is that it will always
work in online mode & perform all operations vastly. The overall hot
site has to be furnished and connected with appropriate hardware,
software, network & effective internet connection. At this, continuous
back up of data has been taken at the constant tome. The hot site is
not looking the same as the normal sites within an organization due
to disasters happening within an organization as they affect the site.
Hence, hot sites have been used because of its additional
features(wpadmin, 2016).
2. Warm site:
This site is also referred to as the backup file but it seems to differ
with the hot site as per the difference of its equipped. The warm site
has been furnished with the power, network, or the phone. The user
of warm sit works with different resources as it works over multiple
servers. A warm site is not working as same as the hot site as it
responds after some delay as compared to the hot site. The warm
site uses organization can easily affect by the disasters as it takes
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

time to service operations. Its main advantage is that this site is not
costly.
3. Cold site:
A cold site is also referred to as the backup file but it offers very fewer
facilities as compared with the other sites. The switch-off time from an
affection of disaster is very less as compared with both warm and hot
sites. This site provides an effective benefit that it is cheaper from all
other options. This site has to be furnished with tables, chairs,
bathrooms & some technical facilities that are associated with the
organization functioning.
this is also a backup file but it provides fewer facilities than among
other sites such as hot and warm. This site takes more time to switch
over from the disaster affected to the cold site. The main advantage
of this site is that it is the cheapest option. This site is furnished with
chairs, bathrooms, tables, and basic technical facilities but it takes
more than a week to set up correctly and then starts the operation
from this site.
Access control: these are the procedures that can be utilized to
have duties separation among individuals charged with monitoring
and operating the system. These processes are where a business
can show that database managers must not be seeing firewall logs.
Incident response: this type of process covers each thing from
detection to the way to address an incident. Incident response
procedures must discuss the way to involve administration in the
response and when to include law enforcement (Peoples and
Vaughan-Williams, 2014).
10
costly.
3. Cold site:
A cold site is also referred to as the backup file but it offers very fewer
facilities as compared with the other sites. The switch-off time from an
affection of disaster is very less as compared with both warm and hot
sites. This site provides an effective benefit that it is cheaper from all
other options. This site has to be furnished with tables, chairs,
bathrooms & some technical facilities that are associated with the
organization functioning.
this is also a backup file but it provides fewer facilities than among
other sites such as hot and warm. This site takes more time to switch
over from the disaster affected to the cold site. The main advantage
of this site is that it is the cheapest option. This site is furnished with
chairs, bathrooms, tables, and basic technical facilities but it takes
more than a week to set up correctly and then starts the operation
from this site.
Access control: these are the procedures that can be utilized to
have duties separation among individuals charged with monitoring
and operating the system. These processes are where a business
can show that database managers must not be seeing firewall logs.
Incident response: this type of process covers each thing from
detection to the way to address an incident. Incident response
procedures must discuss the way to involve administration in the
response and when to include law enforcement (Peoples and
Vaughan-Williams, 2014).
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Auditing: this procedure can involve what to audit, the way to
manage audit logs as well as the objective of what is being audited.
Work processes and procedures: workforce of a company must be
enough capable to secure their workstations when they are not in
use. A process of logging off can be imposed by policy before leaving
workstation.
Physical and environmental: the physical and environmental
procedures not only cover environmental controls and air conditioning
in rooms where other equipment and servers are stored, but also
Ethernet cable shielding in order to prevent them of being trapped.
Administrative procedure: this procedure can be utilizing to have
duty separation among individuals charged which monitoring and
operating the systems. These procedures or processes are where a
business can show that the administrators of database must be
seeing the fire wall logs (Schneier, 2015).
The concern of network administrators regarding security of
networks is increasing when they are expose to networking
infrastructure and private date of organisation to internet crackers.
Firewall security policy is act as safeguard to control access between
less trusted and trusted network. Firewall is not a sole component,
yet it is a strategy that helps an organisation in protecting its internet
reachable resources. It also supports in securing segments of intranet
of organisation. It enforces a security policy that helps in securing the
data of business (Ang, Choong, and Ng, 2015).
11
manage audit logs as well as the objective of what is being audited.
Work processes and procedures: workforce of a company must be
enough capable to secure their workstations when they are not in
use. A process of logging off can be imposed by policy before leaving
workstation.
Physical and environmental: the physical and environmental
procedures not only cover environmental controls and air conditioning
in rooms where other equipment and servers are stored, but also
Ethernet cable shielding in order to prevent them of being trapped.
Administrative procedure: this procedure can be utilizing to have
duty separation among individuals charged which monitoring and
operating the systems. These procedures or processes are where a
business can show that the administrators of database must be
seeing the fire wall logs (Schneier, 2015).
The concern of network administrators regarding security of
networks is increasing when they are expose to networking
infrastructure and private date of organisation to internet crackers.
Firewall security policy is act as safeguard to control access between
less trusted and trusted network. Firewall is not a sole component,
yet it is a strategy that helps an organisation in protecting its internet
reachable resources. It also supports in securing segments of intranet
of organisation. It enforces a security policy that helps in securing the
data of business (Ang, Choong, and Ng, 2015).
11

Lo2
P3
1.
Prevent hackers from finding a file.If a user is intending to sell one of the
data storage units, you erase all sensitive details and important information.
For removing the hard drive, D-ban may be included. And you can face
other problems if you are trying to access the data. It serves to eliminate
knowledge by extracting platters of preserved data or even then deleting
them.
i. It’s easier to find a file if someone is using open Wi-Fi on a router
because hackers can steal and control your connection. The use of
encrypted wireless keys will avoid this hazard. Every few years it can
also be helpful to refresh or replace equipment. New routers assist
with regular password changes and allow wireless connectivity to be
segregated(Osborne and Whittaker, 2019).
ii. Installation of anti-malware software has been performed from getting
rid by the risk of ransomware, viruses & spyware. This will help in
maintaining the file safely. AI technology has been used for this
concept because it is a very popular technology nowadays and
provides effective features.
2.
Prevent hackers from reading a file. Cybercriminals are smart; they often
use phishing to read a file of somebody. It is up to a person to do it safely,
like emailing intelligently, whatever job one does. Check for the email from
an actual individual or company that says or may not give it. Pay heed, if
12
P3
1.
Prevent hackers from finding a file.If a user is intending to sell one of the
data storage units, you erase all sensitive details and important information.
For removing the hard drive, D-ban may be included. And you can face
other problems if you are trying to access the data. It serves to eliminate
knowledge by extracting platters of preserved data or even then deleting
them.
i. It’s easier to find a file if someone is using open Wi-Fi on a router
because hackers can steal and control your connection. The use of
encrypted wireless keys will avoid this hazard. Every few years it can
also be helpful to refresh or replace equipment. New routers assist
with regular password changes and allow wireless connectivity to be
segregated(Osborne and Whittaker, 2019).
ii. Installation of anti-malware software has been performed from getting
rid by the risk of ransomware, viruses & spyware. This will help in
maintaining the file safely. AI technology has been used for this
concept because it is a very popular technology nowadays and
provides effective features.
2.
Prevent hackers from reading a file. Cybercriminals are smart; they often
use phishing to read a file of somebody. It is up to a person to do it safely,
like emailing intelligently, whatever job one does. Check for the email from
an actual individual or company that says or may not give it. Pay heed, if
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





