Cybersecurity Report: Analyzing Vulnerabilities and Mitigation
VerifiedAdded on 2022/08/09
|7
|1356
|51
Report
AI Summary
This cybersecurity report analyzes the vulnerabilities, risks, and threats faced by Abdullah Al-Othaim Markets Company, operating in the retail sector. The report identifies device-based, software and database, network-based, and cryptographic vulnerabilities, highlighting issues like outdated systems, SQL injection, malware attacks, and man-in-the-middle attacks. It emphasizes the importance of ethical practices and the potential impact of data breaches. The report proposes potential solutions including risk assessment, system updates, mitigation strategies, and employee training. Furthermore, it suggests utilizing frameworks like ISO 31000 to identify and manage risks effectively, ultimately aiming to enhance the company's security posture and protect its confidential data and customer information. The report concludes by emphasizing the need for robust security policies and systems to safeguard the company's online services and IT assets.

2/20/2020
Running Head: CYBERSECURITY 0
Cybersecurity
Report
Student name
Running Head: CYBERSECURITY 0
Cybersecurity
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBERSECURITY 1
Introduction
Cybercrime has increased day-by-day in various industries, which is a huge issue in
the market for many businesses. The number of cyber-attacks has increased in the retail
industry because of vulnerabilities in their systems as well as other reasons, such as lack of
knowledge, lack of security systems, and security policies (Chang, 2017). This report will
analyze the vulnerabilities of the Abdullah Al-Othaim Markets Company based on many
criteria. This report will be discussed about the risks and threats for the company as well as
the retail industry. In this report, protentional solutions will provide for the company to
manage its different processes using cybersecurity. mitigations strategies will provide for the
company in the later section of this report. The firm has operated their business at two places,
which are Egypt and Saudi Arabia. The firm has focused on three main activities which are
malls, grocery stores, and food wholesaling (Othaimmarkets, 2020).
Risks, Threats, and Vulnerabilities
The company is running 231 stores in Saudi Arabia. The company has created a good
position in the market as well. In addition, there are some vulnerabilities on the website of the
company as well as lack of knowledge in the managers and employees about the online retail
business, which is a huge issue in front of the firm (Fruhlinger, 2018). We can categorize the
risks, threats, and vulnerabilities, which areas:
Device-based risks:
The company has used basic computer systems and servers, which are not secure from
firewalls and other IDS/IPS systems. Hackers can access those systems and servers using a
different types of malicious programs (Klemash, 2018). The firm has stored its customer's
data in its database, which can be breached by the attacks as well. In addition, hackers can
exchange information from databases as well. It is a huge risk that systems have used without
updating operating systems as well.
Software and database risks:
There is some basic software have used for managing and monitoring retail business.
It is necessary to use legal and ethical software for managing the website. SQL Injection can
be used for accessing data and devices of the company (Loader & Thomas, 2013).
Introduction
Cybercrime has increased day-by-day in various industries, which is a huge issue in
the market for many businesses. The number of cyber-attacks has increased in the retail
industry because of vulnerabilities in their systems as well as other reasons, such as lack of
knowledge, lack of security systems, and security policies (Chang, 2017). This report will
analyze the vulnerabilities of the Abdullah Al-Othaim Markets Company based on many
criteria. This report will be discussed about the risks and threats for the company as well as
the retail industry. In this report, protentional solutions will provide for the company to
manage its different processes using cybersecurity. mitigations strategies will provide for the
company in the later section of this report. The firm has operated their business at two places,
which are Egypt and Saudi Arabia. The firm has focused on three main activities which are
malls, grocery stores, and food wholesaling (Othaimmarkets, 2020).
Risks, Threats, and Vulnerabilities
The company is running 231 stores in Saudi Arabia. The company has created a good
position in the market as well. In addition, there are some vulnerabilities on the website of the
company as well as lack of knowledge in the managers and employees about the online retail
business, which is a huge issue in front of the firm (Fruhlinger, 2018). We can categorize the
risks, threats, and vulnerabilities, which areas:
Device-based risks:
The company has used basic computer systems and servers, which are not secure from
firewalls and other IDS/IPS systems. Hackers can access those systems and servers using a
different types of malicious programs (Klemash, 2018). The firm has stored its customer's
data in its database, which can be breached by the attacks as well. In addition, hackers can
exchange information from databases as well. It is a huge risk that systems have used without
updating operating systems as well.
Software and database risks:
There is some basic software have used for managing and monitoring retail business.
It is necessary to use legal and ethical software for managing the website. SQL Injection can
be used for accessing data and devices of the company (Loader & Thomas, 2013).
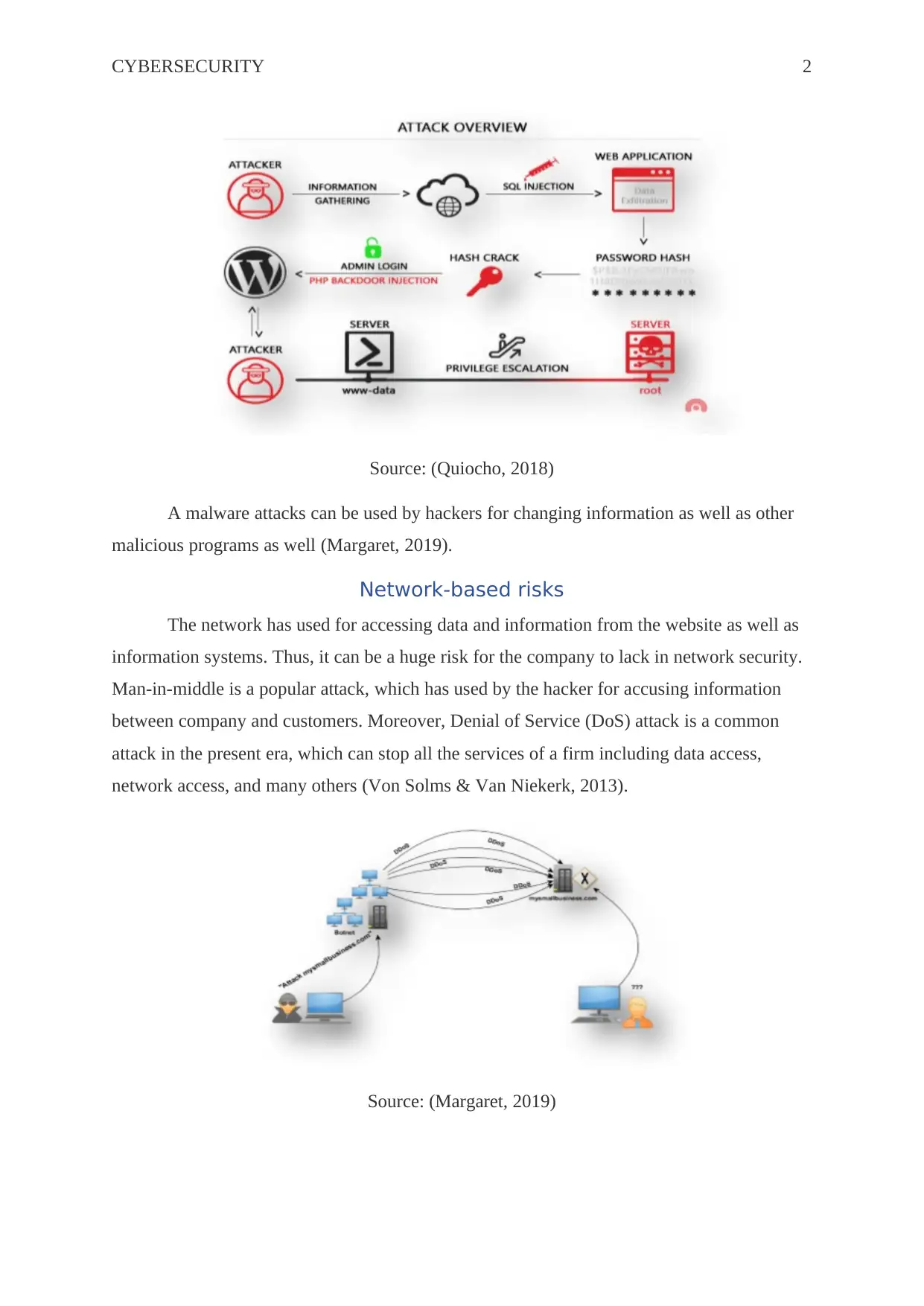
CYBERSECURITY 2
Source: (Quiocho, 2018)
A malware attacks can be used by hackers for changing information as well as other
malicious programs as well (Margaret, 2019).
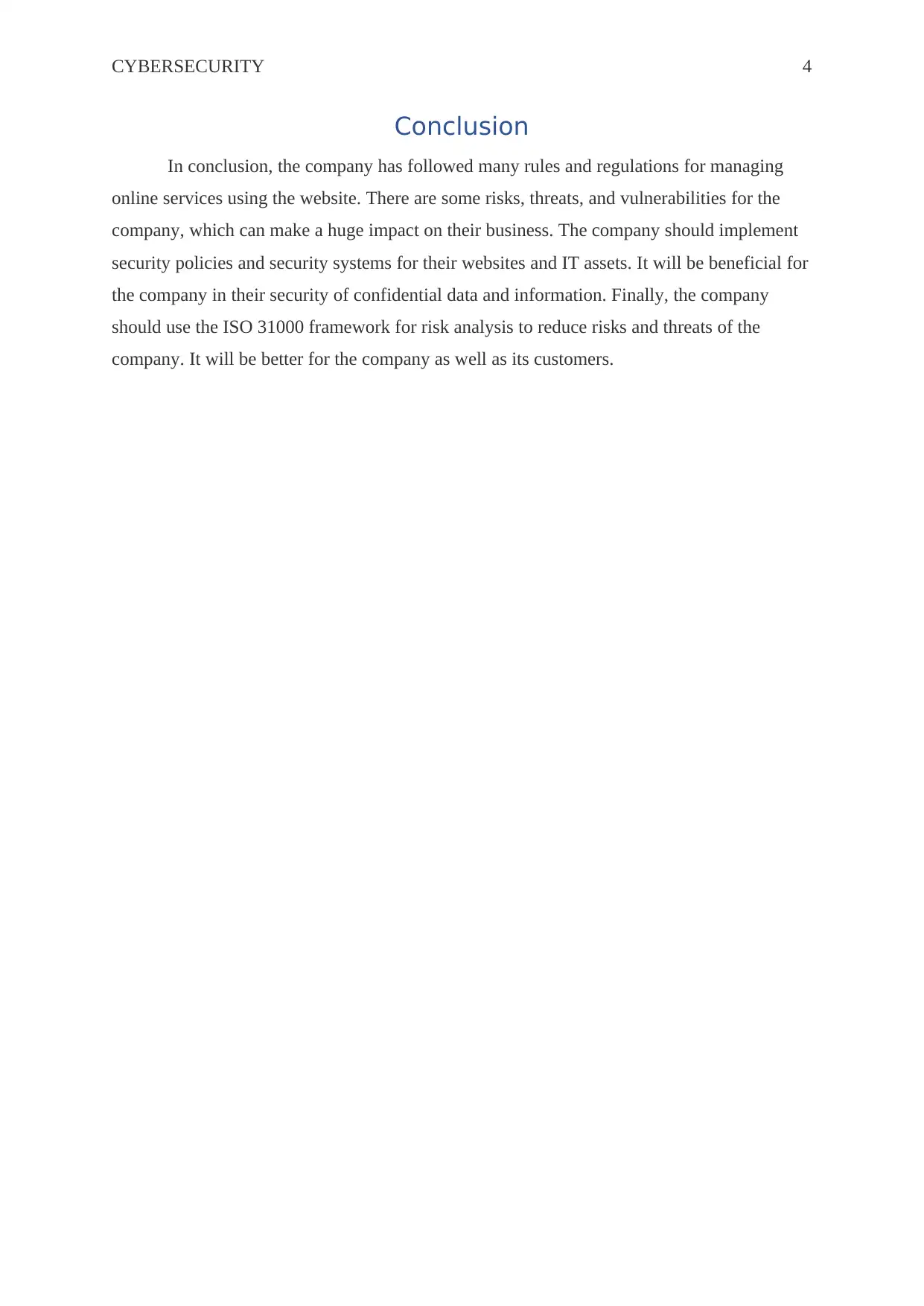
Network-based risks
The network has used for accessing data and information from the website as well as
information systems. Thus, it can be a huge risk for the company to lack in network security.
Man-in-middle is a popular attack, which has used by the hacker for accusing information
between company and customers. Moreover, Denial of Service (DoS) attack is a common
attack in the present era, which can stop all the services of a firm including data access,
network access, and many others (Von Solms & Van Niekerk, 2013).
Source: (Margaret, 2019)
Source: (Quiocho, 2018)
A malware attacks can be used by hackers for changing information as well as other
malicious programs as well (Margaret, 2019).
Network-based risks
The network has used for accessing data and information from the website as well as
information systems. Thus, it can be a huge risk for the company to lack in network security.
Man-in-middle is a popular attack, which has used by the hacker for accusing information
between company and customers. Moreover, Denial of Service (DoS) attack is a common
attack in the present era, which can stop all the services of a firm including data access,
network access, and many others (Von Solms & Van Niekerk, 2013).
Source: (Margaret, 2019)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBERSECURITY 3
Cryptographic vulnerabilities
The company has used a website for online sales and purchase. Moreover,
cryptography is necessary for securing information. Hackers can identify cryptography
techniques to identify actual messages from the company side, which can be confidential for
the company as well.
Ethical problems
Ethics are necessary for the online business, as customers have connected with online
services only. Thus, it can be a threat to the company because of some unethical practices
used by the employees because of less knowledge.
Potential Solutions
Vulnerabilities are the main reason for risks and threats for the website. There are
some basic processes to mitigate all the risks and threats using reducing vulnerabilities as
well. The company should implement a risk assessment for managing. In addition, the
company must update all the operating systems and servers for managing their online
services. Besides, mitigation strategies can be used to reduce vulnerabilities from the website
of the company (Bendovschi, 2015). Moreover, risk analysis can be used for the
identification of vulnerabilities, such as lack of firewalls, poor security, lack of security
policies, and many more. In addition, employees should know about the risks and threats of
online business to avoid any mistakes (Bradford, 2018).
Risks can be identified using international frameworks, such as ISO 31000, and more.
It will provide different types of risks of the website of the company as well as other
operations. Therefore, the firm can develop new mitigation strategies and policies to reduce
the cyber-attacks. A data breach is a huge threat for the company, which make a huge impact
on the reputation and financial conditions as well (Zadelhoff, 2016).
Threats can be identified using risk assessment and other processes, such as network
monitoring, server monitoring as well. There are some basic processes to avoid those risks,
such as education and training about the use of websites and servers. The company has
provided grocery, beverage, home care, and other products (Othaimmarkets, 2020).
Cryptographic vulnerabilities
The company has used a website for online sales and purchase. Moreover,
cryptography is necessary for securing information. Hackers can identify cryptography
techniques to identify actual messages from the company side, which can be confidential for
the company as well.
Ethical problems
Ethics are necessary for the online business, as customers have connected with online
services only. Thus, it can be a threat to the company because of some unethical practices
used by the employees because of less knowledge.
Potential Solutions
Vulnerabilities are the main reason for risks and threats for the website. There are
some basic processes to mitigate all the risks and threats using reducing vulnerabilities as
well. The company should implement a risk assessment for managing. In addition, the
company must update all the operating systems and servers for managing their online
services. Besides, mitigation strategies can be used to reduce vulnerabilities from the website
of the company (Bendovschi, 2015). Moreover, risk analysis can be used for the
identification of vulnerabilities, such as lack of firewalls, poor security, lack of security
policies, and many more. In addition, employees should know about the risks and threats of
online business to avoid any mistakes (Bradford, 2018).
Risks can be identified using international frameworks, such as ISO 31000, and more.
It will provide different types of risks of the website of the company as well as other
operations. Therefore, the firm can develop new mitigation strategies and policies to reduce
the cyber-attacks. A data breach is a huge threat for the company, which make a huge impact
on the reputation and financial conditions as well (Zadelhoff, 2016).
Threats can be identified using risk assessment and other processes, such as network
monitoring, server monitoring as well. There are some basic processes to avoid those risks,
such as education and training about the use of websites and servers. The company has
provided grocery, beverage, home care, and other products (Othaimmarkets, 2020).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CYBERSECURITY 4
Conclusion
In conclusion, the company has followed many rules and regulations for managing
online services using the website. There are some risks, threats, and vulnerabilities for the
company, which can make a huge impact on their business. The company should implement
security policies and security systems for their websites and IT assets. It will be beneficial for
the company in their security of confidential data and information. Finally, the company
should use the ISO 31000 framework for risk analysis to reduce risks and threats of the
company. It will be better for the company as well as its customers.
Conclusion
In conclusion, the company has followed many rules and regulations for managing
online services using the website. There are some risks, threats, and vulnerabilities for the
company, which can make a huge impact on their business. The company should implement
security policies and security systems for their websites and IT assets. It will be beneficial for
the company in their security of confidential data and information. Finally, the company
should use the ISO 31000 framework for risk analysis to reduce risks and threats of the
company. It will be better for the company as well as its customers.

CYBERSECURITY 5
References
Bendovschi, A. (2015). Cyber-attacks–trends, patterns and security countermeasures.
Procedia Economics and Finance, 28, 24-31.
Bradford, L. (2018). What You Need To Know About Cybersecurity In 2018. Retrieved
December 11, 2018, from https://www.forbes.com:
https://www.forbes.com/sites/laurencebradford/2018/03/30/why-people-should-learn-
about-cybersecurity-in-2018/#7c88f6fe5d00
Chang, L. Y. (2017). Cybercrime and Cyber security in ASEAN. In Comparative
Criminology in Asia, 135-148.
Fruhlinger, J. (2018). Top cybersecurity facts, figures and statistics for 2018. Retrieved
december 11, 2018, from https://www.csoonline.com/article/3153707/security/top-
cybersecurity-facts-figures-and-statistics.html
Klemash, S. (2018, July 17). As cybersecurity threats grow, boards examine the options for
overseeing the risks. Retrieved from https://www.ey.com:
https://www.ey.com/en_gl/board-matters/how-boards-can-prepare-for-the-next-
cybersecurity-threat
Loader, B. D., & Thomas, D. (2013). Cybercrime: Security and surveillance in the
information age (1st ed.). London: Routledge.
Margaret, R. (2019). cybersecurity. Retrieved Feburary 2, 2020, from
https://searchsecurity.techtarget.com/definition/cybersecurity
Othaimmarkets. (2020, February 21). About Company. Retrieved from
https://www.othaimmarkets.com: https://www.othaimmarkets.com/about-us
Quiocho, C. (2018, August 31). Why Cybersecurity Is Becoming A Top-Priority Investment .
Retrieved from https://www.forbes.com:
https://www.forbes.com/sites/theyec/2018/08/31/why-cybersecurity-is-becoming-a-
top-priority-investment/#851a14811f32
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber security.
computers & security, 38, 97-102.
References
Bendovschi, A. (2015). Cyber-attacks–trends, patterns and security countermeasures.
Procedia Economics and Finance, 28, 24-31.
Bradford, L. (2018). What You Need To Know About Cybersecurity In 2018. Retrieved
December 11, 2018, from https://www.forbes.com:
https://www.forbes.com/sites/laurencebradford/2018/03/30/why-people-should-learn-
about-cybersecurity-in-2018/#7c88f6fe5d00
Chang, L. Y. (2017). Cybercrime and Cyber security in ASEAN. In Comparative
Criminology in Asia, 135-148.
Fruhlinger, J. (2018). Top cybersecurity facts, figures and statistics for 2018. Retrieved
december 11, 2018, from https://www.csoonline.com/article/3153707/security/top-
cybersecurity-facts-figures-and-statistics.html
Klemash, S. (2018, July 17). As cybersecurity threats grow, boards examine the options for
overseeing the risks. Retrieved from https://www.ey.com:
https://www.ey.com/en_gl/board-matters/how-boards-can-prepare-for-the-next-
cybersecurity-threat
Loader, B. D., & Thomas, D. (2013). Cybercrime: Security and surveillance in the
information age (1st ed.). London: Routledge.
Margaret, R. (2019). cybersecurity. Retrieved Feburary 2, 2020, from
https://searchsecurity.techtarget.com/definition/cybersecurity
Othaimmarkets. (2020, February 21). About Company. Retrieved from
https://www.othaimmarkets.com: https://www.othaimmarkets.com/about-us
Quiocho, C. (2018, August 31). Why Cybersecurity Is Becoming A Top-Priority Investment .
Retrieved from https://www.forbes.com:
https://www.forbes.com/sites/theyec/2018/08/31/why-cybersecurity-is-becoming-a-
top-priority-investment/#851a14811f32
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber security.
computers & security, 38, 97-102.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBERSECURITY 6
Zadelhoff, M. v. (2016). The Biggest Cybersecurity Threats Are Inside Your Company.
Retrieved Jaunary 22, 2020, from https://hbr.org/2016/09/the-biggest-cybersecurity-
threats-are-inside-your-company
Zadelhoff, M. v. (2016). The Biggest Cybersecurity Threats Are Inside Your Company.
Retrieved Jaunary 22, 2020, from https://hbr.org/2016/09/the-biggest-cybersecurity-
threats-are-inside-your-company
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




