CSI6199: Investigation into Cybersecurity Countermeasures for PPS
VerifiedAdded on 2022/10/01
|11
|2527
|237
Report
AI Summary
This report provides a comprehensive investigation into cybersecurity countermeasures for Peanut Processing Services (PPS), a data collection and analysis company. It identifies key vulnerabilities, including zero-day exploits, malware, ransomware, phishing scams, and AI/ML-related threats. The report details the threats and vulnerabilities PPS faces, stemming from its reliance on technology, data collection practices, and employee awareness. It then proposes a range of cybersecurity solutions, encompassing technical, organizational, and training measures. The technical solutions include implementing anti-virus software, firewalls, intrusion detection and prevention systems, and content filtering. Organizational measures involve establishing security policies, backup systems, and a comprehensive incident response plan. Training recommendations focus on educating employees about cybersecurity threats, including phishing scams and social engineering techniques. The report also assesses the initial, maintenance, and training costs associated with implementing these countermeasures. The conclusion emphasizes the need for PPS to adopt a multi-faceted approach to cybersecurity, combining technical, organizational, and training measures to protect its data and maintain its business operations.

ASSESSMENT 2: INVESTIGATION INTO CYBER-SECURITY COUNTERMEASURES
(Student’s Name)
(Course Name)
(Tutor’s Name)
(Date)
(Student’s Name)
(Course Name)
(Tutor’s Name)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................2
Identification of threats and vulnerabilities.....................................................................................3
Zero-day vulnerability..................................................................................................................3
Malware type of vulnerability......................................................................................................3
Ransomware vulnerability...........................................................................................................4
Phishing scam vulnerability.........................................................................................................4
Artificial intelligence and machine learning vulnerability..........................................................5
Application of cyber security solutions...........................................................................................5
First line of defense......................................................................................................................5
Zero-day exploit solution.............................................................................................................6
Malware type of vulnerability solution........................................................................................6
Ransomware vulnerability solution.............................................................................................7
Phishing scam vulnerability solution...........................................................................................7
AI/ML vulnerability solution.......................................................................................................7
Assessment and documentation of initial, maintenance and training costs.....................................8
Conclusion.......................................................................................................................................8
Introduction......................................................................................................................................2
Identification of threats and vulnerabilities.....................................................................................3
Zero-day vulnerability..................................................................................................................3
Malware type of vulnerability......................................................................................................3
Ransomware vulnerability...........................................................................................................4
Phishing scam vulnerability.........................................................................................................4
Artificial intelligence and machine learning vulnerability..........................................................5
Application of cyber security solutions...........................................................................................5
First line of defense......................................................................................................................5
Zero-day exploit solution.............................................................................................................6
Malware type of vulnerability solution........................................................................................6
Ransomware vulnerability solution.............................................................................................7
Phishing scam vulnerability solution...........................................................................................7
AI/ML vulnerability solution.......................................................................................................7
Assessment and documentation of initial, maintenance and training costs.....................................8
Conclusion.......................................................................................................................................8

Introduction
Cyber-security is one of the major concerns for Industrial Control Systems (ICS) and
Supervisory Control and Data Acquisition (SCADA). It is the one of the major consideration by
any organization since it has worked its way to the top of any organization agenda. Example
cybercriminals gave managed to steal over 124 million US dollar through the internet in 2016.
Peanut Processing Service (PPS) is a data collection and analysis company located in Western
Australia. The company is used to conduct data analysis and surveys. Most instances, the data
collected by the company is highly confidential. The company collects data through online
website and through paper. The company operates a four-business day turn-around time. This
means that the company cannot afford downtime. Currently the company operates with twelve
people, each of the employees has been issues with windows 10 laptop. At one time one of the
employee laptop crashed which resulted to loss of data which resulted to loss of one of their
valuable customers. In addition to this the company has been facing several data breaches. As a
cyber-security architect this paper will address five cyber security issues and give a
recommendation on how to address these issues.
Identification of threats and vulnerabilities
Security threat or security event is a malicious act which aims at corrupting and stealing
data on organization systems. Cyber threat is driven by an array of vulnerabilities and attacks
which grow constantly both in sophistication and diversity.
PPS company reliance to technology grows day, and so do the need of an improved cyber
security. From the description it evident that there so much which is stored in the twelve
company laptops. By simply gathering data from an online website has left the company
vulnerable to any form of data breach. Second, almost all of the employees are not well-versed in
Cyber-security is one of the major concerns for Industrial Control Systems (ICS) and
Supervisory Control and Data Acquisition (SCADA). It is the one of the major consideration by
any organization since it has worked its way to the top of any organization agenda. Example
cybercriminals gave managed to steal over 124 million US dollar through the internet in 2016.
Peanut Processing Service (PPS) is a data collection and analysis company located in Western
Australia. The company is used to conduct data analysis and surveys. Most instances, the data
collected by the company is highly confidential. The company collects data through online
website and through paper. The company operates a four-business day turn-around time. This
means that the company cannot afford downtime. Currently the company operates with twelve
people, each of the employees has been issues with windows 10 laptop. At one time one of the
employee laptop crashed which resulted to loss of data which resulted to loss of one of their
valuable customers. In addition to this the company has been facing several data breaches. As a
cyber-security architect this paper will address five cyber security issues and give a
recommendation on how to address these issues.
Identification of threats and vulnerabilities
Security threat or security event is a malicious act which aims at corrupting and stealing
data on organization systems. Cyber threat is driven by an array of vulnerabilities and attacks
which grow constantly both in sophistication and diversity.
PPS company reliance to technology grows day, and so do the need of an improved cyber
security. From the description it evident that there so much which is stored in the twelve
company laptops. By simply gathering data from an online website has left the company
vulnerable to any form of data breach. Second, almost all of the employees are not well-versed in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

cyber-security and is the reasons as to why the company is facing a lot of data breaches. It is also
important to note that PPS need not to necessary have a technician to ensure that the
organizational data is protected. The company needs only to be have a few changes on their
laptops and have be aware of cyber-security related issues and how an organization can protect
itself from these issues (Ali & Awad, 2018).
Zero-day vulnerability
First is the main vulnerability is zero-day vulnerability. This is a weakness to a hole in a
software which is unknown to a vendor. The security is then exploited by an attacker before a
vendor or an organization becomes aware and hurries to fix it. Zero-day exploit abuses local
privilege escalation weakness in windows platform specifically a NULL pointer, the win32k.sys
component. Once the exploit is analyzed and discovered, it is supposed to be reported to
Microsoft security response. It is important to note that with Zero-vulnerability an attacker is
capable of creating two windows; one for the first stage and the second stage of exploit. For the
first exploit an attacker is capable of creating a popup menu object(Ashok, Hahn, &
Govindarasu, 2014)
Malware type of vulnerability
Malware refers to malicious software, this means that the software can be used to
compromise laptop functions, bypass access controls, and steal data. The common used type of
malware is sand-box evading software. This said to be a prominent tool in the hands of cyber
hackers in 2019. The software has the ability to bypass protection controls and execute its
malicious codes without being detected by modern cyber security solutions. Some of examples
of sandbox-evading software is locky malware which was released in 2016. This type sand-box
malware is spread through JavaScript code. Another example is shamoon malware which was
important to note that PPS need not to necessary have a technician to ensure that the
organizational data is protected. The company needs only to be have a few changes on their
laptops and have be aware of cyber-security related issues and how an organization can protect
itself from these issues (Ali & Awad, 2018).
Zero-day vulnerability
First is the main vulnerability is zero-day vulnerability. This is a weakness to a hole in a
software which is unknown to a vendor. The security is then exploited by an attacker before a
vendor or an organization becomes aware and hurries to fix it. Zero-day exploit abuses local
privilege escalation weakness in windows platform specifically a NULL pointer, the win32k.sys
component. Once the exploit is analyzed and discovered, it is supposed to be reported to
Microsoft security response. It is important to note that with Zero-vulnerability an attacker is
capable of creating two windows; one for the first stage and the second stage of exploit. For the
first exploit an attacker is capable of creating a popup menu object(Ashok, Hahn, &
Govindarasu, 2014)
Malware type of vulnerability
Malware refers to malicious software, this means that the software can be used to
compromise laptop functions, bypass access controls, and steal data. The common used type of
malware is sand-box evading software. This said to be a prominent tool in the hands of cyber
hackers in 2019. The software has the ability to bypass protection controls and execute its
malicious codes without being detected by modern cyber security solutions. Some of examples
of sandbox-evading software is locky malware which was released in 2016. This type sand-box
malware is spread through JavaScript code. Another example is shamoon malware which was
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

discovered in 2012. This type of malware was designed to execute its logic at a certain time and
date. Other types of malwares are computer viruses, BOT, keyloggers, and worms. In addition,
malware also includes malicious code example is spyware, which is a deceptive program
installed without authorization to monitor user activities without their consent. Spyware can be
used to send unwanted popups ad thus able to monitor user browser activities
Ransomware vulnerability
This is a type of malware which has the ability of encrypting all data which is saved
within a user computer. This type of malware uses military grade encryption algorithm and
pioneering social engineering to exploit potential. Usually this cyber security weakness is
propagated via user-initiated actions like clicking on a malicious link in a spam e-mail.
Specifically hackers uses phone calls and social media as a form of communication to steal
vulnerable data (Adams-Collman, 2018).
Phishing scam vulnerability
This is a type of social engineering technique which is usually used by an attacker to steal
user data which includes login credentials. The major goal of this type of attack is to trick the
email recipient into believing that a certain message is something that a reader wants. An
example of phishing type of attack happened in 2016 where a cyber-attacker managed to get
Clinton’s campaign chair. There was the fappening attack which made it possible to make a
number of celebrities’ photos public. The common type of phishing attacks are deceptive
phishing, spear phishing where most attacks uses social media, CEO fraud, vishing, and
smishing
date. Other types of malwares are computer viruses, BOT, keyloggers, and worms. In addition,
malware also includes malicious code example is spyware, which is a deceptive program
installed without authorization to monitor user activities without their consent. Spyware can be
used to send unwanted popups ad thus able to monitor user browser activities
Ransomware vulnerability
This is a type of malware which has the ability of encrypting all data which is saved
within a user computer. This type of malware uses military grade encryption algorithm and
pioneering social engineering to exploit potential. Usually this cyber security weakness is
propagated via user-initiated actions like clicking on a malicious link in a spam e-mail.
Specifically hackers uses phone calls and social media as a form of communication to steal
vulnerable data (Adams-Collman, 2018).
Phishing scam vulnerability
This is a type of social engineering technique which is usually used by an attacker to steal
user data which includes login credentials. The major goal of this type of attack is to trick the
email recipient into believing that a certain message is something that a reader wants. An
example of phishing type of attack happened in 2016 where a cyber-attacker managed to get
Clinton’s campaign chair. There was the fappening attack which made it possible to make a
number of celebrities’ photos public. The common type of phishing attacks are deceptive
phishing, spear phishing where most attacks uses social media, CEO fraud, vishing, and
smishing

Artificial intelligence and machine learning vulnerability
Machine learning and artificial intelligence software are used to learn consequences of
the past events. There is high chances that cyber criminals are using AI/ML tools as an
innovative technique to perform sophisticated cyber-attacks. Example Cyber criminals are using
chatbots to send vast amount of fraud messages (Connole, 2016).
Application of cyber security solutions
First line of defense
Cyber-crime countermeasure is a process, an action, device, or technology which serves
to mitigate the effects of a cyber-attack or a vulnerability. Most companies believe that they can
do very little in cyber related crimes but there three types of counter measures to combat these
cyber related crimes. These are Hi-tech, No-Tech, and Lo-Tech. These three cyber security
measures need to be combined to create what cyber security professionals refer to as a three
layered and an effective security program. Hi Tech security measure the act of including all
electronic systems to counter cyber related attack. Here PPS Company needs to use access
control systems, communication systems, computerized systems, and special detection systems
to protect network related resources. Hi-tech systems usually server to automate repetitive
functions. The systems are able to continuously monitor without error. In addition with Hi-tech
systems PPS Company is able to handle vast amount of data which cannot be handled by the
twelve employees. For PPS company to employ Hi-tech systems there need to include intelligent
video analytics which analyzes video scenes; thus able to evaluate employee activities when at
work place. With this the company will be in a position to monitor unwanted behaviors.
On the other hand Lo-tech systems are physical security elements which is cost-effective.
This will include the use of locks and other physical barriers which assists of protecting
Machine learning and artificial intelligence software are used to learn consequences of
the past events. There is high chances that cyber criminals are using AI/ML tools as an
innovative technique to perform sophisticated cyber-attacks. Example Cyber criminals are using
chatbots to send vast amount of fraud messages (Connole, 2016).
Application of cyber security solutions
First line of defense
Cyber-crime countermeasure is a process, an action, device, or technology which serves
to mitigate the effects of a cyber-attack or a vulnerability. Most companies believe that they can
do very little in cyber related crimes but there three types of counter measures to combat these
cyber related crimes. These are Hi-tech, No-Tech, and Lo-Tech. These three cyber security
measures need to be combined to create what cyber security professionals refer to as a three
layered and an effective security program. Hi Tech security measure the act of including all
electronic systems to counter cyber related attack. Here PPS Company needs to use access
control systems, communication systems, computerized systems, and special detection systems
to protect network related resources. Hi-tech systems usually server to automate repetitive
functions. The systems are able to continuously monitor without error. In addition with Hi-tech
systems PPS Company is able to handle vast amount of data which cannot be handled by the
twelve employees. For PPS company to employ Hi-tech systems there need to include intelligent
video analytics which analyzes video scenes; thus able to evaluate employee activities when at
work place. With this the company will be in a position to monitor unwanted behaviors.
On the other hand Lo-tech systems are physical security elements which is cost-effective.
This will include the use of locks and other physical barriers which assists of protecting
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

organizational laptops. The basic elements which PPS Company needs to implement here are
natural surveillance, natural access control and territorial reinforcement. Lastly is the No-tech
elements which is a security measure that uses no technology. Here PPS Company needs to have
a comprehensive risk analysis, security guard programs, and needs to security awareness and
training (Degaspari, 2014)
Zero-day exploit solution
PPS Company can protect itself from zero-day exploits via updating its operating
systems. Second, the company needs to avoid the use of vulnerable software; example of
software that the company needs to avoid is adobe reader, adobe flash and java. Third the
company needs to run an anti-virus in all its laptops. Example Kaspersky’s anti-virus assists in
reducing zero-day attacks. In addition the company needs to deploy intrusion detection and
prevention systems which offer comprehensive protection. In addition, the company needs to
have a well-planed incident response which assists in immediately compacting any form of cyber
security breach. The company also needs to note that the three key signs for zero-day exploits are
unexpected traffic on a legitimate port, unexpected potentially legitimate traffic, and similar
behavior from compromised client or server (Harrop & Matteson, 2013).
Malware type of vulnerability solution
The first line of defense of malware related attacks is installing anti-virus programs in all
the laptops. Second, to protect sandbox evading malware, the company needs to always hide all
its configurations as hackers always get difficulties crack hidden configurations. Third is using
non-administrator account whenever possible; here attackers will always find it hard to install
malware from non-administrators account. Lastly, the company needs to limit file sharing
natural surveillance, natural access control and territorial reinforcement. Lastly is the No-tech
elements which is a security measure that uses no technology. Here PPS Company needs to have
a comprehensive risk analysis, security guard programs, and needs to security awareness and
training (Degaspari, 2014)
Zero-day exploit solution
PPS Company can protect itself from zero-day exploits via updating its operating
systems. Second, the company needs to avoid the use of vulnerable software; example of
software that the company needs to avoid is adobe reader, adobe flash and java. Third the
company needs to run an anti-virus in all its laptops. Example Kaspersky’s anti-virus assists in
reducing zero-day attacks. In addition the company needs to deploy intrusion detection and
prevention systems which offer comprehensive protection. In addition, the company needs to
have a well-planed incident response which assists in immediately compacting any form of cyber
security breach. The company also needs to note that the three key signs for zero-day exploits are
unexpected traffic on a legitimate port, unexpected potentially legitimate traffic, and similar
behavior from compromised client or server (Harrop & Matteson, 2013).
Malware type of vulnerability solution
The first line of defense of malware related attacks is installing anti-virus programs in all
the laptops. Second, to protect sandbox evading malware, the company needs to always hide all
its configurations as hackers always get difficulties crack hidden configurations. Third is using
non-administrator account whenever possible; here attackers will always find it hard to install
malware from non-administrators account. Lastly, the company needs to limit file sharing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ransomware vulnerability solution
To protect oneself from this type of threat, PPS Company needs to employ content
scanning and filtering on their mail servers. All inbound e-mails needs to be scanned. The
company needs to block any attachment. In addition the company needs to use a reputable
firewall such Cisco types of firewalls. Also the company needs to have full visibility of traffic
within the company’s needs. This allows one to make the right decisions. It also helps in
highlighting unknown events which require further investigations.
Phishing scam vulnerability solution
One example of phishing attack which have ever occurred is the Nigerian scam
commonly known as 419. To protect oneself from phishing vulnerability is a having software
which has the ability to filter out unsolicited emails. Second, PPS Company needs to always
check the source of information from the incoming emails. Third the company needs not click on
hyper-links or links attached in the emails. In addition, the company needs to have the most
recent updates on the laptop operating systems and on their web browsers. Lastly, the company
needs to train its staff to only open those sites which are secure.
AI/ML vulnerability solution
An example of AI/ML related threat is spear phishing but PS Company needs to have a
multi-faceted strategy which needs to remain a priority. It is also important that the company
allocate enough time to conduct a thorough data labelling on potential AI/ML related threats. In
addition, the company needs to apply the use of secure user authentication, and spam filter
applications (McCreight & Leece, 2016).
To protect oneself from this type of threat, PPS Company needs to employ content
scanning and filtering on their mail servers. All inbound e-mails needs to be scanned. The
company needs to block any attachment. In addition the company needs to use a reputable
firewall such Cisco types of firewalls. Also the company needs to have full visibility of traffic
within the company’s needs. This allows one to make the right decisions. It also helps in
highlighting unknown events which require further investigations.
Phishing scam vulnerability solution
One example of phishing attack which have ever occurred is the Nigerian scam
commonly known as 419. To protect oneself from phishing vulnerability is a having software
which has the ability to filter out unsolicited emails. Second, PPS Company needs to always
check the source of information from the incoming emails. Third the company needs not click on
hyper-links or links attached in the emails. In addition, the company needs to have the most
recent updates on the laptop operating systems and on their web browsers. Lastly, the company
needs to train its staff to only open those sites which are secure.
AI/ML vulnerability solution
An example of AI/ML related threat is spear phishing but PS Company needs to have a
multi-faceted strategy which needs to remain a priority. It is also important that the company
allocate enough time to conduct a thorough data labelling on potential AI/ML related threats. In
addition, the company needs to apply the use of secure user authentication, and spam filter
applications (McCreight & Leece, 2016).
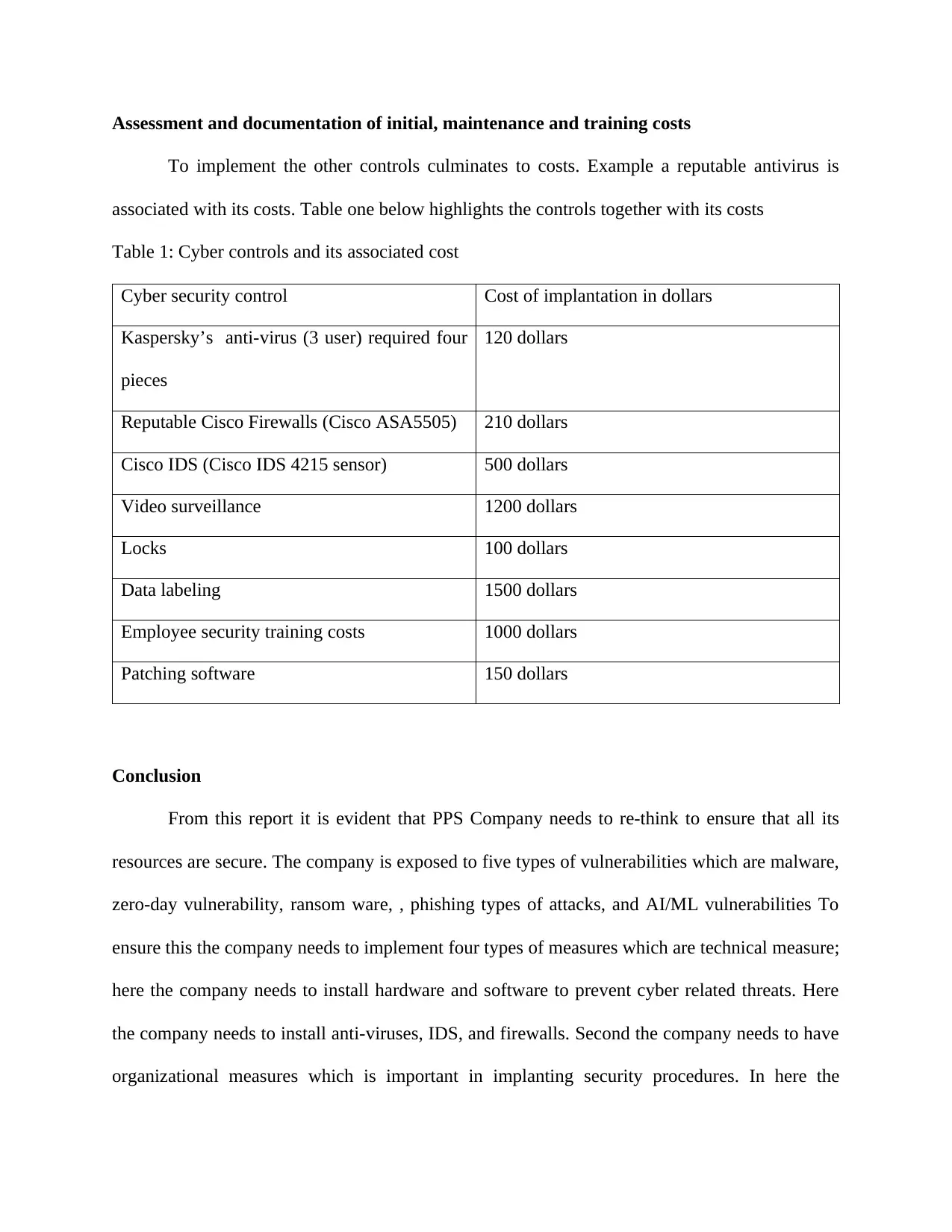
Assessment and documentation of initial, maintenance and training costs
To implement the other controls culminates to costs. Example a reputable antivirus is
associated with its costs. Table one below highlights the controls together with its costs
Table 1: Cyber controls and its associated cost
Cyber security control Cost of implantation in dollars
Kaspersky’s anti-virus (3 user) required four
pieces
120 dollars
Reputable Cisco Firewalls (Cisco ASA5505) 210 dollars
Cisco IDS (Cisco IDS 4215 sensor) 500 dollars
Video surveillance 1200 dollars
Locks 100 dollars
Data labeling 1500 dollars
Employee security training costs 1000 dollars
Patching software 150 dollars
Conclusion
From this report it is evident that PPS Company needs to re-think to ensure that all its
resources are secure. The company is exposed to five types of vulnerabilities which are malware,
zero-day vulnerability, ransom ware, , phishing types of attacks, and AI/ML vulnerabilities To
ensure this the company needs to implement four types of measures which are technical measure;
here the company needs to install hardware and software to prevent cyber related threats. Here
the company needs to install anti-viruses, IDS, and firewalls. Second the company needs to have
organizational measures which is important in implanting security procedures. In here the
To implement the other controls culminates to costs. Example a reputable antivirus is
associated with its costs. Table one below highlights the controls together with its costs
Table 1: Cyber controls and its associated cost
Cyber security control Cost of implantation in dollars
Kaspersky’s anti-virus (3 user) required four
pieces
120 dollars
Reputable Cisco Firewalls (Cisco ASA5505) 210 dollars
Cisco IDS (Cisco IDS 4215 sensor) 500 dollars
Video surveillance 1200 dollars
Locks 100 dollars
Data labeling 1500 dollars
Employee security training costs 1000 dollars
Patching software 150 dollars
Conclusion
From this report it is evident that PPS Company needs to re-think to ensure that all its
resources are secure. The company is exposed to five types of vulnerabilities which are malware,
zero-day vulnerability, ransom ware, , phishing types of attacks, and AI/ML vulnerabilities To
ensure this the company needs to implement four types of measures which are technical measure;
here the company needs to install hardware and software to prevent cyber related threats. Here
the company needs to install anti-viruses, IDS, and firewalls. Second the company needs to have
organizational measures which is important in implanting security procedures. In here the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

organization needs to have a security program and also have a contingency plan in case a data
breach happens. Third, the company needs to have capacity building measures aiming at
enhancing knowledge and promoting cyber security among its employees. Here the report has
encouraged periodic awareness and training programs to employees. Lastly is cooperation
measures which aims and establishing partnership between employees. In addition, cooperation
measures will entail increasing resiliency against cyber attacks
breach happens. Third, the company needs to have capacity building measures aiming at
enhancing knowledge and promoting cyber security among its employees. Here the report has
encouraged periodic awareness and training programs to employees. Lastly is cooperation
measures which aims and establishing partnership between employees. In addition, cooperation
measures will entail increasing resiliency against cyber attacks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Adams-Collman, J. (2018). Ransomware and Cyber Security: the King That Did Not Wannacry. Prim Dent
J, 7(1), 44-47. doi:10.1308/205016818822610307
Ali, B., & Awad, A. I. (2018). Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart
Homes. Sensors (Basel), 18(3). doi:10.3390/s18030817
Ashok, A., Hahn, A., & Govindarasu, M. (2014). Cyber-physical security of Wide-Area Monitoring,
Protection and Control in a smart grid environment. J Adv Res, 5(4), 481-489.
doi:10.1016/j.jare.2013.12.005
Connole, P. (2016). Ransomware Cyber Security Threat Tests Providers' Defenses. Provider, 42(11), 19,
21, 23, 29, 32, 35.
Degaspari, J. (2014). Cyber security watch list for 2014: seven trends. Healthc Inform, 31(1), 44-46.
Harrop, W., & Matteson, A. (2013). Cyber resilience: a review of critical national infrastructure and cyber
security protection measures applied in the UK and USA. J Bus Contin Emer Plan, 7(2), 149-162.
McCreight, T., & Leece, D. (2016). Physical security and IT convergence: Managing the cyber-related
risks. J Bus Contin Emer Plan, 10(1), 18-30.
J, 7(1), 44-47. doi:10.1308/205016818822610307
Ali, B., & Awad, A. I. (2018). Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart
Homes. Sensors (Basel), 18(3). doi:10.3390/s18030817
Ashok, A., Hahn, A., & Govindarasu, M. (2014). Cyber-physical security of Wide-Area Monitoring,
Protection and Control in a smart grid environment. J Adv Res, 5(4), 481-489.
doi:10.1016/j.jare.2013.12.005
Connole, P. (2016). Ransomware Cyber Security Threat Tests Providers' Defenses. Provider, 42(11), 19,
21, 23, 29, 32, 35.
Degaspari, J. (2014). Cyber security watch list for 2014: seven trends. Healthc Inform, 31(1), 44-46.
Harrop, W., & Matteson, A. (2013). Cyber resilience: a review of critical national infrastructure and cyber
security protection measures applied in the UK and USA. J Bus Contin Emer Plan, 7(2), 149-162.
McCreight, T., & Leece, D. (2016). Physical security and IT convergence: Managing the cyber-related
risks. J Bus Contin Emer Plan, 10(1), 18-30.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





