Cyber Security Report: CMP71001 - Security Consultation for SCU
VerifiedAdded on 2022/10/19
|12
|2224
|335
Report
AI Summary
This report, prepared for Southern Cross University's CMP71001 course, serves as a cybersecurity consultation, addressing contemporary and emerging risks. It begins with an assessment of the Bring Your Own Device (BYOD) policy, identifying potential threats such as viruses, phishing, and unauthorized installations. The report then explores certificate-based authentication as a robust security measure, comparing it with traditional password-based methods and highlighting its advantages in a BYOD environment. Furthermore, the report provides a detailed analysis of phishing, including its characteristics, examples, and guidelines for both users and IT administrators to mitigate its impact. The conclusion emphasizes the importance of a multi-layered security approach, including user education, to safeguard information systems against evolving cyber threats. The report provides recommendations to enhance the security posture of the organization.

Cyber Security 1
CYBER SECURITY
by Student’s Name
Code + Course Name
Professor’s Name
University Name
City, State
Date
CYBER SECURITY
by Student’s Name
Code + Course Name
Professor’s Name
University Name
City, State
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 2
Abstract
This paper assesses cybersecurity in an organization. This includes the assessment of the Bring
Your Own Device policy at the workplace. Based on these assessments of the risk factors of the
policy, different preventive methods are discussed and recommended based on the policy that
has already been implemented. The paper then goes further to assess Phishing as a significant
risk factor that can be in an organizations Information system. The document outlines this and
goes ahead to give recommendations to both users of the system and the IT administrators on
how to reduce the effects of this.
Abstract
This paper assesses cybersecurity in an organization. This includes the assessment of the Bring
Your Own Device policy at the workplace. Based on these assessments of the risk factors of the
policy, different preventive methods are discussed and recommended based on the policy that
has already been implemented. The paper then goes further to assess Phishing as a significant
risk factor that can be in an organizations Information system. The document outlines this and
goes ahead to give recommendations to both users of the system and the IT administrators on
how to reduce the effects of this.

Cyber Security 3
Table of Contents
Abstract......................................................................................................................................................2
Boyd Risk Assessment...............................................................................................................................4
1.1 Boyd Risk Assessment Introduction...............................................................................................4
1.2 Objective of BOYD Risk Assessment.............................................................................................4
1.3 Critical information systems assets...............................................................................................4
1.4 Threats to Information systems.....................................................................................................5
2. Certificate-Based Authentication.........................................................................................................6
2.1 Introduction.....................................................................................................................................6
2.2 Password-based Protection.............................................................................................................6
2.3 How an Authentication Certificate Works....................................................................................7
2.4 Why Certificate-Based Authentication is used..............................................................................7
2.5 Comparison of Certificate-based Authentication and the Username-password.........................8
authentication method...........................................................................................................................8
3.0 Anti-Phishing Guideline......................................................................................................................8
3.1 Definition and Characteristics of Phishing....................................................................................8
3.2 Phishing Examples.....................................................................................................................9
3.3 Instructions of Phishing Handling to Users.............................................................................9
3.4 Instructions of Phishing Handling to IT Admin....................................................................10
Conclusion................................................................................................................................................10
References................................................................................................................................................11
Table of Contents
Abstract......................................................................................................................................................2
Boyd Risk Assessment...............................................................................................................................4
1.1 Boyd Risk Assessment Introduction...............................................................................................4
1.2 Objective of BOYD Risk Assessment.............................................................................................4
1.3 Critical information systems assets...............................................................................................4
1.4 Threats to Information systems.....................................................................................................5
2. Certificate-Based Authentication.........................................................................................................6
2.1 Introduction.....................................................................................................................................6
2.2 Password-based Protection.............................................................................................................6
2.3 How an Authentication Certificate Works....................................................................................7
2.4 Why Certificate-Based Authentication is used..............................................................................7
2.5 Comparison of Certificate-based Authentication and the Username-password.........................8
authentication method...........................................................................................................................8
3.0 Anti-Phishing Guideline......................................................................................................................8
3.1 Definition and Characteristics of Phishing....................................................................................8
3.2 Phishing Examples.....................................................................................................................9
3.3 Instructions of Phishing Handling to Users.............................................................................9
3.4 Instructions of Phishing Handling to IT Admin....................................................................10
Conclusion................................................................................................................................................10
References................................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 4
Boyd Risk Assessment
1.1 Boyd Risk Assessment Introduction
For most organizations, it is always harder to ensure that all the employees are having access to
Equipment that enables them to perform their work functionalities continuously. Due to that
reason, some organizations are adopting the Bring Your own Device (BOYD) policy to save on
cost and also improve efficiency (Dhingra 2016). As much as this might be a good idea, there are
a lot of risks that are involved in the use of these machines.
1.2 Objective of BOYD Risk Assessment
The primary purpose of carrying out this risk assessment is to get to identify all the potential
risks that are involved in the use of personal computing devices in a working environment. This
is mainly because working systems might get easily compromised.
1.3 Critical information systems assets.
The risk assessment report seeks to explore the company’s IT systems, identify the policies that
are related to the uses of the BOYD policy. The reasons as to why the procedure might be
implemented and the downside of the plan. The paper will give some recommendation on the use
of this policy. With the current use of a password-based protection system considered to be very
poor in terms of protecting the company's data (Keyes, 2016).
With the introduction of a policy such as the BOYD policy, the risks to the organization's
information systems are very much compromised. In an organization such as this, Data for both
the employees and the customers, suppliers and even investors is always critical. This is
inaddition to financial records and transactions that may be compromised when such a policy is
implemented and the threats get to
Boyd Risk Assessment
1.1 Boyd Risk Assessment Introduction
For most organizations, it is always harder to ensure that all the employees are having access to
Equipment that enables them to perform their work functionalities continuously. Due to that
reason, some organizations are adopting the Bring Your own Device (BOYD) policy to save on
cost and also improve efficiency (Dhingra 2016). As much as this might be a good idea, there are
a lot of risks that are involved in the use of these machines.
1.2 Objective of BOYD Risk Assessment
The primary purpose of carrying out this risk assessment is to get to identify all the potential
risks that are involved in the use of personal computing devices in a working environment. This
is mainly because working systems might get easily compromised.
1.3 Critical information systems assets.
The risk assessment report seeks to explore the company’s IT systems, identify the policies that
are related to the uses of the BOYD policy. The reasons as to why the procedure might be
implemented and the downside of the plan. The paper will give some recommendation on the use
of this policy. With the current use of a password-based protection system considered to be very
poor in terms of protecting the company's data (Keyes, 2016).
With the introduction of a policy such as the BOYD policy, the risks to the organization's
information systems are very much compromised. In an organization such as this, Data for both
the employees and the customers, suppliers and even investors is always critical. This is
inaddition to financial records and transactions that may be compromised when such a policy is
implemented and the threats get to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber Security 5
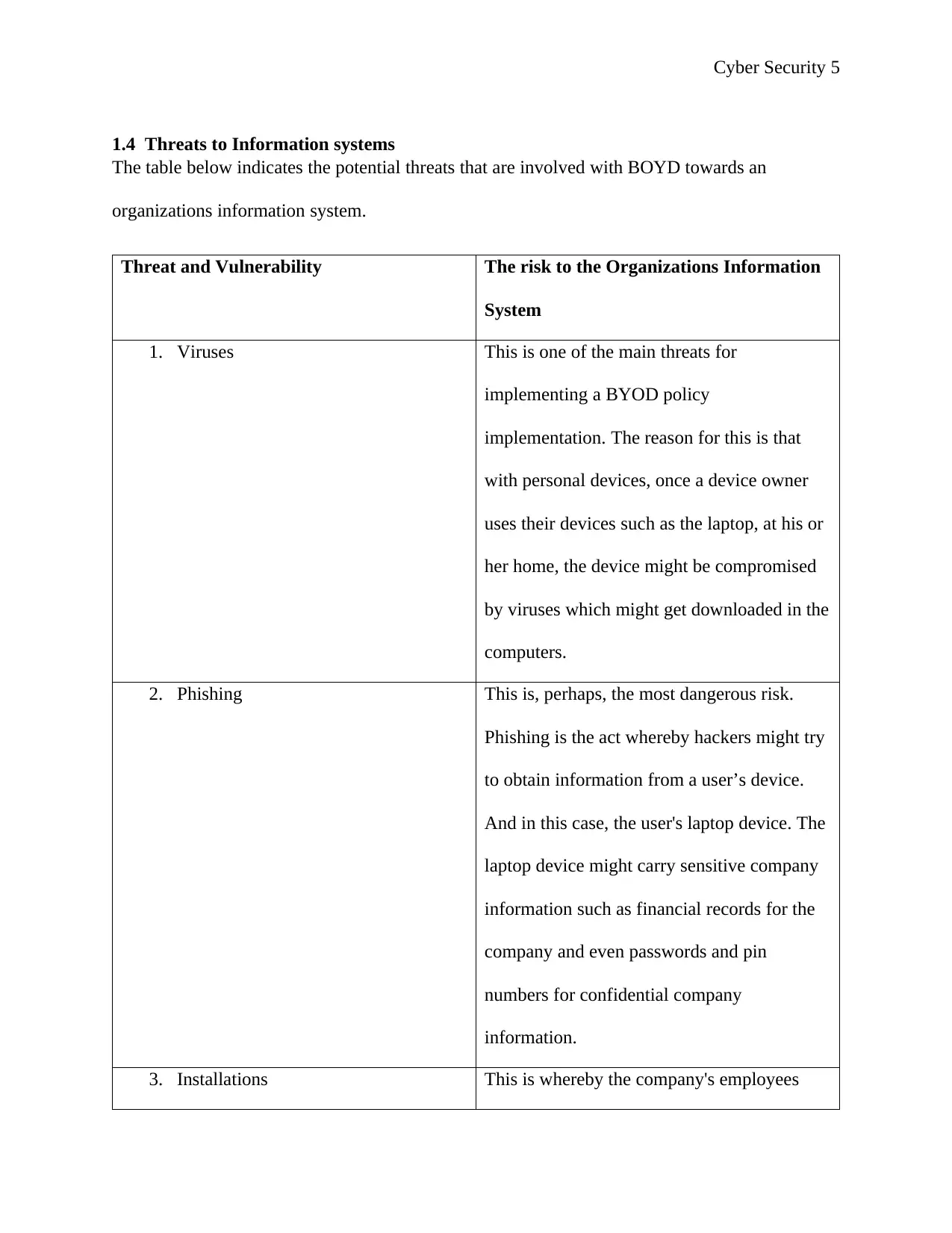
1.4 Threats to Information systems
The table below indicates the potential threats that are involved with BOYD towards an
organizations information system.
Threat and Vulnerability The risk to the Organizations Information
System
1. Viruses This is one of the main threats for
implementing a BYOD policy
implementation. The reason for this is that
with personal devices, once a device owner
uses their devices such as the laptop, at his or
her home, the device might be compromised
by viruses which might get downloaded in the
computers.
2. Phishing This is, perhaps, the most dangerous risk.
Phishing is the act whereby hackers might try
to obtain information from a user’s device.
And in this case, the user's laptop device. The
laptop device might carry sensitive company
information such as financial records for the
company and even passwords and pin
numbers for confidential company
information.
3. Installations This is whereby the company's employees
1.4 Threats to Information systems
The table below indicates the potential threats that are involved with BOYD towards an
organizations information system.
Threat and Vulnerability The risk to the Organizations Information
System
1. Viruses This is one of the main threats for
implementing a BYOD policy
implementation. The reason for this is that
with personal devices, once a device owner
uses their devices such as the laptop, at his or
her home, the device might be compromised
by viruses which might get downloaded in the
computers.
2. Phishing This is, perhaps, the most dangerous risk.
Phishing is the act whereby hackers might try
to obtain information from a user’s device.
And in this case, the user's laptop device. The
laptop device might carry sensitive company
information such as financial records for the
company and even passwords and pin
numbers for confidential company
information.
3. Installations This is whereby the company's employees

Cyber Security 6
who use their own devices make application
installations to their systems. This is made
easy by the fact that it is their own devices;
therefore, they are at liberty to install any
applications at their will without any
intervention by the IT department. This
application might lead to loss of data because
some of them are created by individuals with
malicious information.
2. Certificate-Based Authentication
2.1 Introduction
With all these risks being brought about by the use of BYOD, companies through their
Information systems and Security department are coming up with ways of mitigating some of the
risks involved. One of the best ways to handle this is by the use of a certificate-based
Authentication method.
2.2 Password-based Protection
This is the traditional and most common method of data protection that is used by most
companies. However, it has been noted that this method of protection is not so secure as most
people use weak passwords that are easily identified. In addition to that, with malware that
hackers install to people’s devices, the passwords are easily read and stored (Boodaei 2017). This
means that potential hackers have easy access to the passwords that employees type on their
who use their own devices make application
installations to their systems. This is made
easy by the fact that it is their own devices;
therefore, they are at liberty to install any
applications at their will without any
intervention by the IT department. This
application might lead to loss of data because
some of them are created by individuals with
malicious information.
2. Certificate-Based Authentication
2.1 Introduction
With all these risks being brought about by the use of BYOD, companies through their
Information systems and Security department are coming up with ways of mitigating some of the
risks involved. One of the best ways to handle this is by the use of a certificate-based
Authentication method.
2.2 Password-based Protection
This is the traditional and most common method of data protection that is used by most
companies. However, it has been noted that this method of protection is not so secure as most
people use weak passwords that are easily identified. In addition to that, with malware that
hackers install to people’s devices, the passwords are easily read and stored (Boodaei 2017). This
means that potential hackers have easy access to the passwords that employees type on their
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 7
machines. This means that hackers can easily access organizational passwords when someone
uses their own devices containing malicious software to access company information.
2.3 How an Authentication Certificate Works
According to Zink (2017), Certificate-Based Authentication is a method of protection that
employs the use of a digital certificate that is used to identify a specific user and the machine that
computing device that they are using. This is done before granting them access to applications
that are shared over a network, resources, and even accessing specifically secured resources on a
network.
2.4 Why Certificate-Based Authentication is used.
Certificate-based Authentication is mainly used because it provides a simple but efficient way
for organizations to implement the BYOD policy but still ensure that their information systems
remain secure. An excellent example of this the fact that the Certificates are easily created by the
systems admin and are issued to employees as soon as they are brought to the company. Once the
certificates are designed and released to the employees and installed, they create a leeway that
allows the employees to access the company's information in a secure path (Medhi, 2016).
The certificate-based system creates a platform whereby the employees can securely access the
company's information in addition to the traditionally used Password protection method. This is
because the certificates that are created by the companies Information Technology team allows
them to monitor the devices which are accessing particular files. This is in addition to the
presence of a Virtual Private Network (VPN), which secures the connection to that specific
network, therefore, preventing Network intrusion (Falk, 2016).
machines. This means that hackers can easily access organizational passwords when someone
uses their own devices containing malicious software to access company information.
2.3 How an Authentication Certificate Works
According to Zink (2017), Certificate-Based Authentication is a method of protection that
employs the use of a digital certificate that is used to identify a specific user and the machine that
computing device that they are using. This is done before granting them access to applications
that are shared over a network, resources, and even accessing specifically secured resources on a
network.
2.4 Why Certificate-Based Authentication is used.
Certificate-based Authentication is mainly used because it provides a simple but efficient way
for organizations to implement the BYOD policy but still ensure that their information systems
remain secure. An excellent example of this the fact that the Certificates are easily created by the
systems admin and are issued to employees as soon as they are brought to the company. Once the
certificates are designed and released to the employees and installed, they create a leeway that
allows the employees to access the company's information in a secure path (Medhi, 2016).
The certificate-based system creates a platform whereby the employees can securely access the
company's information in addition to the traditionally used Password protection method. This is
because the certificates that are created by the companies Information Technology team allows
them to monitor the devices which are accessing particular files. This is in addition to the
presence of a Virtual Private Network (VPN), which secures the connection to that specific
network, therefore, preventing Network intrusion (Falk, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber Security 8
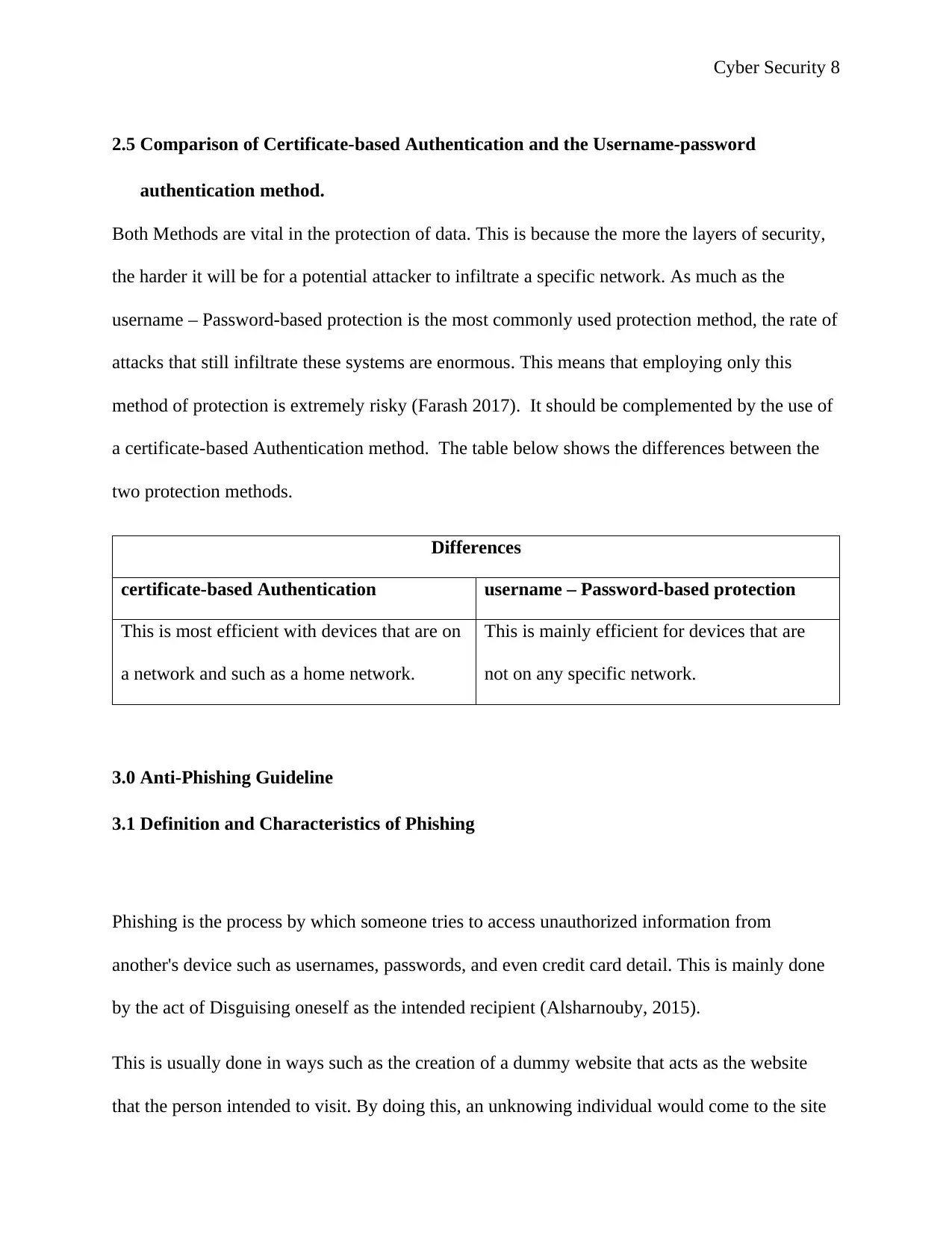
2.5 Comparison of Certificate-based Authentication and the Username-password
authentication method.
Both Methods are vital in the protection of data. This is because the more the layers of security,
the harder it will be for a potential attacker to infiltrate a specific network. As much as the
username – Password-based protection is the most commonly used protection method, the rate of
attacks that still infiltrate these systems are enormous. This means that employing only this
method of protection is extremely risky (Farash 2017). It should be complemented by the use of
a certificate-based Authentication method. The table below shows the differences between the
two protection methods.
Differences
certificate-based Authentication username – Password-based protection
This is most efficient with devices that are on
a network and such as a home network.
This is mainly efficient for devices that are
not on any specific network.
3.0 Anti-Phishing Guideline
3.1 Definition and Characteristics of Phishing
Phishing is the process by which someone tries to access unauthorized information from
another's device such as usernames, passwords, and even credit card detail. This is mainly done
by the act of Disguising oneself as the intended recipient (Alsharnouby, 2015).
This is usually done in ways such as the creation of a dummy website that acts as the website
that the person intended to visit. By doing this, an unknowing individual would come to the site
2.5 Comparison of Certificate-based Authentication and the Username-password
authentication method.
Both Methods are vital in the protection of data. This is because the more the layers of security,
the harder it will be for a potential attacker to infiltrate a specific network. As much as the
username – Password-based protection is the most commonly used protection method, the rate of
attacks that still infiltrate these systems are enormous. This means that employing only this
method of protection is extremely risky (Farash 2017). It should be complemented by the use of
a certificate-based Authentication method. The table below shows the differences between the
two protection methods.
Differences
certificate-based Authentication username – Password-based protection
This is most efficient with devices that are on
a network and such as a home network.
This is mainly efficient for devices that are
not on any specific network.
3.0 Anti-Phishing Guideline
3.1 Definition and Characteristics of Phishing
Phishing is the process by which someone tries to access unauthorized information from
another's device such as usernames, passwords, and even credit card detail. This is mainly done
by the act of Disguising oneself as the intended recipient (Alsharnouby, 2015).
This is usually done in ways such as the creation of a dummy website that acts as the website
that the person intended to visit. By doing this, an unknowing individual would come to the site

Cyber Security 9
and input their credentials as they usually do on their original website. Once they do this, the
hackers are able to obtain the user's information such as usernames and passwords/pins.
Some of the well-known characteristics of Phishing include:
a) The poor spelling on the websites
b) Request for unusual details
c) Unusual URL
3.2 Phishing Examples
1) Deciptive phishing- this is whereby an attacker impersonates a legitimate company and
attempts to steal peoples information such as login credentials.
2) Spear phishing- this is a more personalized form of attack as it incoprates the use of
personal information so as to initiate some form of attack on the users credentials.
3) CEO Phishing- this is whereby the attackers use domain based email addresses to
impersonate the CEO of a particular organization so as to obtain other sensitive data.
3.3 Instructions of Phishing Handling to Users
Phishing is quite a common practice, and it is one of the most common ways that data gets lost.
However, there are specific procedures that when are addressed well might reduce the rate of
data loss through Phishing. Some of these include:
1) Getting educated- this is perhaps the most important. The first step is to ensure that the
users know exactly what is Phishing. This will help them identify potential risks of
Phishing.
2) Spellings- Advising the users to pay attention to fundamental issues such as checking
spellings of the website would be great as this would help them avoid the same risks.
and input their credentials as they usually do on their original website. Once they do this, the
hackers are able to obtain the user's information such as usernames and passwords/pins.
Some of the well-known characteristics of Phishing include:
a) The poor spelling on the websites
b) Request for unusual details
c) Unusual URL
3.2 Phishing Examples
1) Deciptive phishing- this is whereby an attacker impersonates a legitimate company and
attempts to steal peoples information such as login credentials.
2) Spear phishing- this is a more personalized form of attack as it incoprates the use of
personal information so as to initiate some form of attack on the users credentials.
3) CEO Phishing- this is whereby the attackers use domain based email addresses to
impersonate the CEO of a particular organization so as to obtain other sensitive data.
3.3 Instructions of Phishing Handling to Users
Phishing is quite a common practice, and it is one of the most common ways that data gets lost.
However, there are specific procedures that when are addressed well might reduce the rate of
data loss through Phishing. Some of these include:
1) Getting educated- this is perhaps the most important. The first step is to ensure that the
users know exactly what is Phishing. This will help them identify potential risks of
Phishing.
2) Spellings- Advising the users to pay attention to fundamental issues such as checking
spellings of the website would be great as this would help them avoid the same risks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 10
3.4 Instructions of Phishing Handling to IT Admin
According to (Chaudhry & Rittenhouse) 2016 IT administrators in the organization should be
at the forefront of the fight against Phishing. They can do this by:
1) Continually education staff members on potential risks of Phishing and how to identify
them.
2) Implementing Firewalls that are used to sniff out potentially dangerous attacks.
3) Continually updating the company’s systems and policies. This will ensure that the
company’s operations have all the right patches that will enable it to be more resilient to
these attacks.
Conclusion
In conclusion, it is wise to say that in any organization, security is one of the key areas and all
the details pertaining to it is always crucial. The protection levels have to be constantly updated
and added, meaning that, the company should always have a couple of security procedures to
ensure that their systems are safe enough. To prevent attacks such as Phishing, the company
should use a multi-factor authentication method which encompasses the use of Username-
password, One Time Passwords (OTP), certificate-based authentication and the use of Firewalls
(Jensen 2017 ). However, despite all this, user education is most important when dealing with
Information Systems security.
3.4 Instructions of Phishing Handling to IT Admin
According to (Chaudhry & Rittenhouse) 2016 IT administrators in the organization should be
at the forefront of the fight against Phishing. They can do this by:
1) Continually education staff members on potential risks of Phishing and how to identify
them.
2) Implementing Firewalls that are used to sniff out potentially dangerous attacks.
3) Continually updating the company’s systems and policies. This will ensure that the
company’s operations have all the right patches that will enable it to be more resilient to
these attacks.
Conclusion
In conclusion, it is wise to say that in any organization, security is one of the key areas and all
the details pertaining to it is always crucial. The protection levels have to be constantly updated
and added, meaning that, the company should always have a couple of security procedures to
ensure that their systems are safe enough. To prevent attacks such as Phishing, the company
should use a multi-factor authentication method which encompasses the use of Username-
password, One Time Passwords (OTP), certificate-based authentication and the use of Firewalls
(Jensen 2017 ). However, despite all this, user education is most important when dealing with
Information Systems security.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 11
References
Alsharnouby, M., 2015. Why Phishing still works: User strategies for combating phishing
attacks. International Journal of Human-Computer Studies, 82, pp.69-82.
Chaudhry, J.A., and Rittenhouse, R.G., 2016. Phishing attacks and defenses. International
Journal of Security and Its Applications, 10(1), pp.247-256.
Jensen, M.L., 2017. Training to mitigate phishing attacks using mindfulness techniques. Journal
of Management Information Systems, 34(2), pp.597-626.
Boodaei, M., 2017. Authentication method and system using a password as the authentication
key. U.S. Patent 9,727,715.
Dhingra, M., 2016. Legal issues insecure implementation of bringing your own device (BYOD).
Procedia Computer Science, 78, pp.179-184.
Farash, M.S., 2017. An improved password‐based authentication scheme for session initiation
protocol using smart cards without a verification table — International Journal of
Communication Systems, 30(1), p.e2879.
Falk, R., 2016. Method for certificate-based Authentication. U.S. Patent 9,432,198.
Keyes, J., 2016. Bring your own devices (BYOD) survival guide. Auerbach Publications.
References
Alsharnouby, M., 2015. Why Phishing still works: User strategies for combating phishing
attacks. International Journal of Human-Computer Studies, 82, pp.69-82.
Chaudhry, J.A., and Rittenhouse, R.G., 2016. Phishing attacks and defenses. International
Journal of Security and Its Applications, 10(1), pp.247-256.
Jensen, M.L., 2017. Training to mitigate phishing attacks using mindfulness techniques. Journal
of Management Information Systems, 34(2), pp.597-626.
Boodaei, M., 2017. Authentication method and system using a password as the authentication
key. U.S. Patent 9,727,715.
Dhingra, M., 2016. Legal issues insecure implementation of bringing your own device (BYOD).
Procedia Computer Science, 78, pp.179-184.
Farash, M.S., 2017. An improved password‐based authentication scheme for session initiation
protocol using smart cards without a verification table — International Journal of
Communication Systems, 30(1), p.e2879.
Falk, R., 2016. Method for certificate-based Authentication. U.S. Patent 9,432,198.
Keyes, J., 2016. Bring your own devices (BYOD) survival guide. Auerbach Publications.

Cyber Security 12
Medhi, S., 2016. Security Impact on e-ATM Windows Communication Foundation Services
using Certificate-based Authentication and Protection: An implementation of Message Level
Security based on. NET Technique. International Journal of Information Retrieval Research
(IJIRR), 6(3), pp.37-51.
Zink, T., 2017. X. 509 users certificate-based two-factor Authentication for web applications.
Medhi, S., 2016. Security Impact on e-ATM Windows Communication Foundation Services
using Certificate-based Authentication and Protection: An implementation of Message Level
Security based on. NET Technique. International Journal of Information Retrieval Research
(IJIRR), 6(3), pp.37-51.
Zink, T., 2017. X. 509 users certificate-based two-factor Authentication for web applications.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




