Comprehensive Cybersecurity Risk Assessment and Target Profile: ACCU
VerifiedAdded on 2023/01/19
|10
|1954
|60
Report
AI Summary
This report presents a comprehensive cybersecurity risk assessment for Alabama Citizens Credit Union (ACCU), focusing on the identification, analysis, and evaluation of cyber risks. The assessment covers both adversarial and non-adversarial threats, including data security concerns and vulnerabilities within the IT infrastructure. The report details the risk management strategy, including threat identification, risk analysis, development and implementation of a risk management plan, and risk monitoring. It includes a risk matrix, prevention strategies, and a target profile for ACCU, with recommendations for improvement. The report also outlines the implementation of security measures such as physical and digital access controls, data obscuration, and reactive technologies like firewalls and backup systems. The goal is to provide a robust cybersecurity framework for ACCU, ensuring data protection and operational resilience. This report, contributed by a student, can be found on Desklib, a platform offering AI-powered study tools and past assignments.

Running head: RISK ASSESSMENT
Risk Assessment
[Name of the Student]
[Name of the University]
[Author note]
Risk Assessment
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK ASSESSMENT
Risk Assessment:
The cyber risk assessment is generally defined as the process associated with the
identification, analysis and the evaluation of the different kind of cyber risks. This risk
assessment is associated with studying along with analyzing of the entire IT infrastructure and is
also responsible for the identification of the vulnerabilities faced by the system at the juncture of
the people, technology and the process along with the vulnerabilities which exists within the
system.
Besides all this Mr. Brown would be working along with the executive managers for the
purpose of making sure of the fact that the entire risk assessment process is being documented so
as to understand the risks that might arise. There exists lot of internal risks as well as external
risks and for that reason the organization has been planning the implementation of the different
security technologies such as the Physical access control, the digital access control and many
more. Security of the data is one of the major risk that is being faced by the organization and for
this reason special emphasis needs to be put upon this. The basic risk management strategy
which is to be followed by Mr. Brown have been discussed below. The steps discussed below
would be helping the organization in elimination of any kind of risks that are likely to be faced.
The risks which have been identified can be categorized into two types the adversarial
threats and the non-adversarial threats (Dua and Du). The Adversarial threats are associated with
including those risks which can be exploited very easily by the third-party attackers and followed
by this is the non-adversarial threats which mainly happens because of the negligence or due to
mistake or because of some of the other non-,malicious means which can be responsible for
Risk Assessment:
The cyber risk assessment is generally defined as the process associated with the
identification, analysis and the evaluation of the different kind of cyber risks. This risk
assessment is associated with studying along with analyzing of the entire IT infrastructure and is
also responsible for the identification of the vulnerabilities faced by the system at the juncture of
the people, technology and the process along with the vulnerabilities which exists within the
system.
Besides all this Mr. Brown would be working along with the executive managers for the
purpose of making sure of the fact that the entire risk assessment process is being documented so
as to understand the risks that might arise. There exists lot of internal risks as well as external
risks and for that reason the organization has been planning the implementation of the different
security technologies such as the Physical access control, the digital access control and many
more. Security of the data is one of the major risk that is being faced by the organization and for
this reason special emphasis needs to be put upon this. The basic risk management strategy
which is to be followed by Mr. Brown have been discussed below. The steps discussed below
would be helping the organization in elimination of any kind of risks that are likely to be faced.
The risks which have been identified can be categorized into two types the adversarial
threats and the non-adversarial threats (Dua and Du). The Adversarial threats are associated with
including those risks which can be exploited very easily by the third-party attackers and followed
by this is the non-adversarial threats which mainly happens because of the negligence or due to
mistake or because of some of the other non-,malicious means which can be responsible for

2RISK ASSESSMENT
making the organization face risk. The non-adversarial risks generally comes from the typical
users which includes the employees and the admins.
Once the threat identification is completed there would exist a need of assessing the
identified risks. Once the risks are evaluated and identified it becomes necessary for the risk
analysis process to analyze all the risks that would be occurring along with the determination of
the consequences which are linked with each of the risks, this might also be helping in
determination of the ways by which the risk might be associated with affecting the objectives of
the organization.
Development of the risk management plan is followed by the analysis and the risk management
plan would be associated with providing an idea about the assets which are valuable and threats
which would probably be associated with affecting the IT assets in a negative way and in
accordance to that the risk management plan would be prepared (Hubbard and Seiersen.). This
plan in turn would be associated with producing certain control recommendations which might
be used for the purpose of mitigating, transferring, accepting or avoiding of the risk. .
Followed by the development of the risk management plan is the implementation of the
risk management plan and this is considered to the primary goal which includes the
implementation of certain measures for the purpose of removing and reducing the analyses risks
(Ganin). It is possible to remove or reduce the risks which starts from the highest priority or
might be resolving the risk or at least mitigate the risks so as to make sure that the risk is no
longer exist as a threat.
making the organization face risk. The non-adversarial risks generally comes from the typical
users which includes the employees and the admins.
Once the threat identification is completed there would exist a need of assessing the
identified risks. Once the risks are evaluated and identified it becomes necessary for the risk
analysis process to analyze all the risks that would be occurring along with the determination of
the consequences which are linked with each of the risks, this might also be helping in
determination of the ways by which the risk might be associated with affecting the objectives of
the organization.
Development of the risk management plan is followed by the analysis and the risk management
plan would be associated with providing an idea about the assets which are valuable and threats
which would probably be associated with affecting the IT assets in a negative way and in
accordance to that the risk management plan would be prepared (Hubbard and Seiersen.). This
plan in turn would be associated with producing certain control recommendations which might
be used for the purpose of mitigating, transferring, accepting or avoiding of the risk. .
Followed by the development of the risk management plan is the implementation of the
risk management plan and this is considered to the primary goal which includes the
implementation of certain measures for the purpose of removing and reducing the analyses risks
(Ganin). It is possible to remove or reduce the risks which starts from the highest priority or
might be resolving the risk or at least mitigate the risks so as to make sure that the risk is no
longer exist as a threat.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3RISK ASSESSMENT
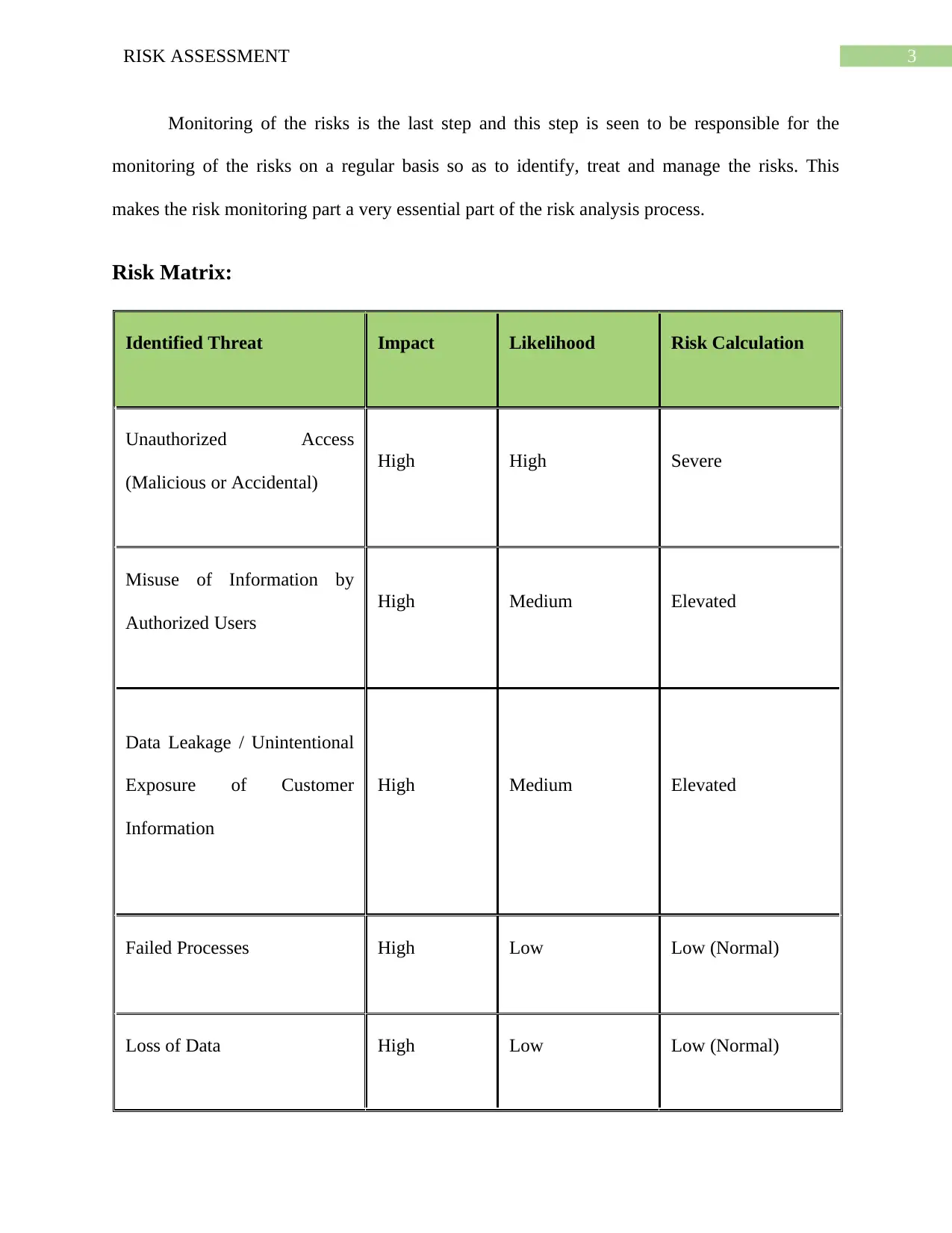
Monitoring of the risks is the last step and this step is seen to be responsible for the
monitoring of the risks on a regular basis so as to identify, treat and manage the risks. This
makes the risk monitoring part a very essential part of the risk analysis process.
Risk Matrix:
Identified Threat Impact Likelihood Risk Calculation
Unauthorized Access
(Malicious or Accidental)
High High Severe
Misuse of Information by
Authorized Users
High Medium Elevated
Data Leakage / Unintentional
Exposure of Customer
Information
High Medium Elevated
Failed Processes High Low Low (Normal)
Loss of Data High Low Low (Normal)
Monitoring of the risks is the last step and this step is seen to be responsible for the
monitoring of the risks on a regular basis so as to identify, treat and manage the risks. This
makes the risk monitoring part a very essential part of the risk analysis process.
Risk Matrix:
Identified Threat Impact Likelihood Risk Calculation
Unauthorized Access
(Malicious or Accidental)
High High Severe
Misuse of Information by
Authorized Users
High Medium Elevated
Data Leakage / Unintentional
Exposure of Customer
Information
High Medium Elevated
Failed Processes High Low Low (Normal)
Loss of Data High Low Low (Normal)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
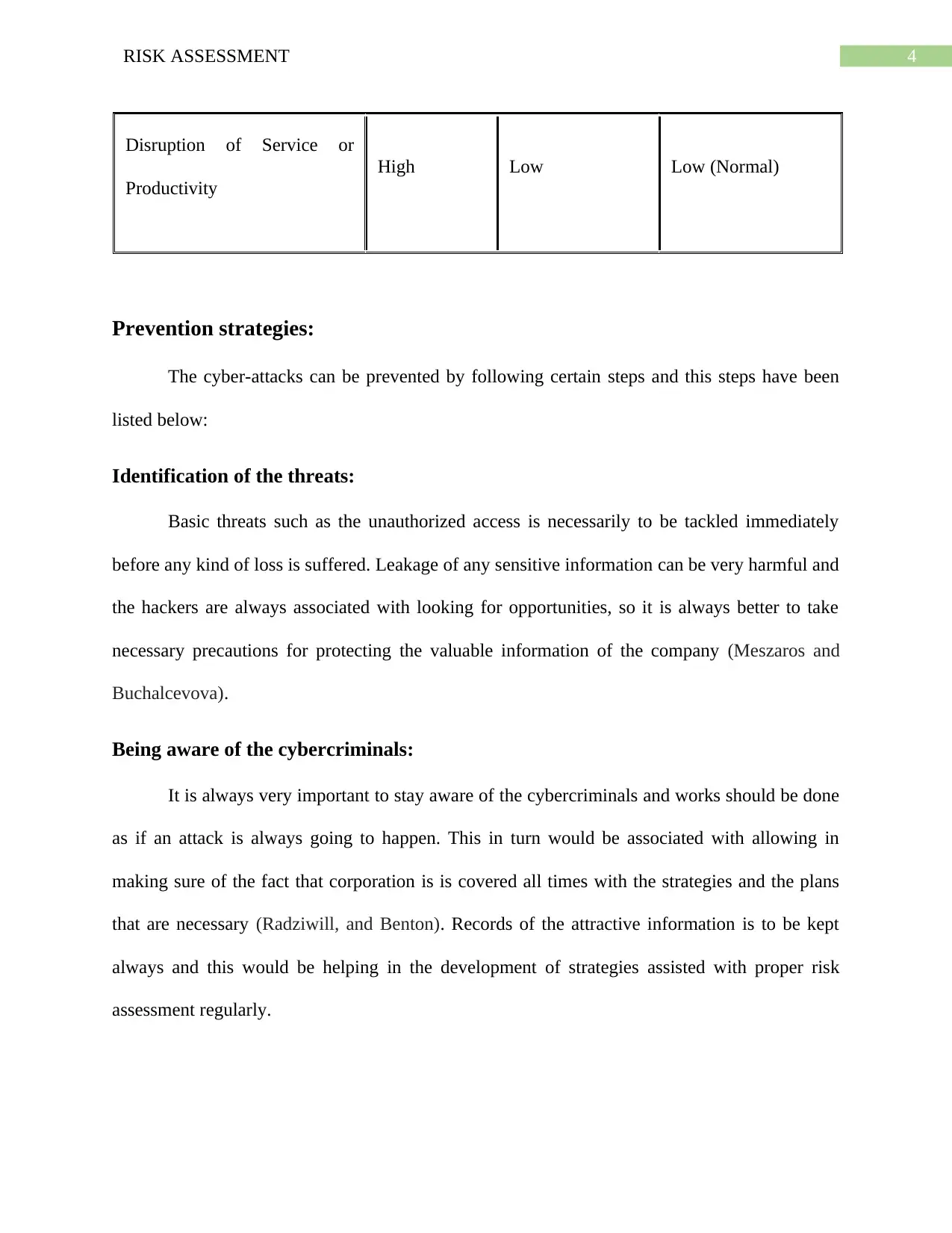
4RISK ASSESSMENT
Disruption of Service or
Productivity
High Low Low (Normal)
Prevention strategies:
The cyber-attacks can be prevented by following certain steps and this steps have been
listed below:
Identification of the threats:
Basic threats such as the unauthorized access is necessarily to be tackled immediately
before any kind of loss is suffered. Leakage of any sensitive information can be very harmful and
the hackers are always associated with looking for opportunities, so it is always better to take
necessary precautions for protecting the valuable information of the company (Meszaros and
Buchalcevova).
Being aware of the cybercriminals:
It is always very important to stay aware of the cybercriminals and works should be done
as if an attack is always going to happen. This in turn would be associated with allowing in
making sure of the fact that corporation is is covered all times with the strategies and the plans
that are necessary (Radziwill, and Benton). Records of the attractive information is to be kept
always and this would be helping in the development of strategies assisted with proper risk
assessment regularly.
Disruption of Service or
Productivity
High Low Low (Normal)
Prevention strategies:
The cyber-attacks can be prevented by following certain steps and this steps have been
listed below:
Identification of the threats:
Basic threats such as the unauthorized access is necessarily to be tackled immediately
before any kind of loss is suffered. Leakage of any sensitive information can be very harmful and
the hackers are always associated with looking for opportunities, so it is always better to take
necessary precautions for protecting the valuable information of the company (Meszaros and
Buchalcevova).
Being aware of the cybercriminals:
It is always very important to stay aware of the cybercriminals and works should be done
as if an attack is always going to happen. This in turn would be associated with allowing in
making sure of the fact that corporation is is covered all times with the strategies and the plans
that are necessary (Radziwill, and Benton). Records of the attractive information is to be kept
always and this would be helping in the development of strategies assisted with proper risk
assessment regularly.

5RISK ASSESSMENT
Tracking the employees:
Employees are to be tracked and this acts as a key element and the reason behind this is
that they are having insights of the business and are seen to be privy to the operations. For this
reason the employees should always be motivated and discouraged from leaking out any of the
crucial information and attempts should be made so as to make the employees more loyal to the
company.
Usage of Two-factor Authentication:
Two factor authentication can be used for the minimization of the risk. The employees
should be encouraged in using the two-factor authentication and the reason behind this is that it
helps in increasing the security by addition of the additional steps so as to access any account
(Malhotra). Which means a password along with a security code needs to be inputted so as to get
access.
Target Profile:
The current profile of Alabama Citizens Credit Union is associated with putting forward
of the overall look of maturity. The overall maturity level after identification would be helping
Alabama Citizens Credit Union in prioritization of the actions which are to be preserved along
with being improved or relaxed. So one of the largest obstacle faced by Alabama Citizens Credit
Union is the inconsistency of the documentation and so it is recommended to focus on this
documentation related to what are the things that are to be done and this in turn would insure that
the existing documentation is also accurate. Besides this the threat related to internal incident
also exists and for this reason Alabama Citizens Credit Union should be associated with focusing
Tracking the employees:
Employees are to be tracked and this acts as a key element and the reason behind this is
that they are having insights of the business and are seen to be privy to the operations. For this
reason the employees should always be motivated and discouraged from leaking out any of the
crucial information and attempts should be made so as to make the employees more loyal to the
company.
Usage of Two-factor Authentication:
Two factor authentication can be used for the minimization of the risk. The employees
should be encouraged in using the two-factor authentication and the reason behind this is that it
helps in increasing the security by addition of the additional steps so as to access any account
(Malhotra). Which means a password along with a security code needs to be inputted so as to get
access.
Target Profile:
The current profile of Alabama Citizens Credit Union is associated with putting forward
of the overall look of maturity. The overall maturity level after identification would be helping
Alabama Citizens Credit Union in prioritization of the actions which are to be preserved along
with being improved or relaxed. So one of the largest obstacle faced by Alabama Citizens Credit
Union is the inconsistency of the documentation and so it is recommended to focus on this
documentation related to what are the things that are to be done and this in turn would insure that
the existing documentation is also accurate. Besides this the threat related to internal incident
also exists and for this reason Alabama Citizens Credit Union should be associated with focusing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RISK ASSESSMENT
upon the activities which would be helping in the mitigation of this particular type of threat.
Activities which mainly includes the creep, activity logging and change control of the
configuration would be helping in protecting, detecting and recovering from any of the internal
incidents.
Identify:
o Asset management:
The hierarchical approach would be helping in accessing the closeness of the production
environment along with determining the restrictiveness of the access. Besides this the
routine inspection of the along with servicing of hardware would be helping in make sure
that the system is not damaged. Listing of the software would be helping in making sure
of the updated certificates along with the patches and licenses. Providing of training
would be helping in practicing the best use of security measures.
o Risk management strategy:
The multiphase approach adopted by Mr. Brown would be helping in documentation of
the risks along with helping the employees. Besides this the merge and the consolidation
of the multi system would be helping in decreasing of the risks.
o Governing policies
List of policies formulated would be helping in the storing of the data along with helping
in handling of the data so as to prevent it from leakage. Briefing of the employees related to the
usage of the technology would be helping in internal usage of the internet and this in turn would
be helping in lowering of the footprint which in turn would help in preventing the site hacking.
o Environments
upon the activities which would be helping in the mitigation of this particular type of threat.
Activities which mainly includes the creep, activity logging and change control of the
configuration would be helping in protecting, detecting and recovering from any of the internal
incidents.
Identify:
o Asset management:
The hierarchical approach would be helping in accessing the closeness of the production
environment along with determining the restrictiveness of the access. Besides this the
routine inspection of the along with servicing of hardware would be helping in make sure
that the system is not damaged. Listing of the software would be helping in making sure
of the updated certificates along with the patches and licenses. Providing of training
would be helping in practicing the best use of security measures.
o Risk management strategy:
The multiphase approach adopted by Mr. Brown would be helping in documentation of
the risks along with helping the employees. Besides this the merge and the consolidation
of the multi system would be helping in decreasing of the risks.
o Governing policies
List of policies formulated would be helping in the storing of the data along with helping
in handling of the data so as to prevent it from leakage. Briefing of the employees related to the
usage of the technology would be helping in internal usage of the internet and this in turn would
be helping in lowering of the footprint which in turn would help in preventing the site hacking.
o Environments
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RISK ASSESSMENT
The multi-tiered environment would be assuring the quality along with the staging and
the production. This in turn would be helping in having a proper production as well as
increased testing. The codes would also be used for making sure of the testing.
Protect-
o Physical Access Control: Would be helping in mitigation of the losses which occurs due
to the physical threats.
o Digital Access Control: this would be helping in reviewing of the existing users so as to
grant them permission.
o Data Obscuration: This would be helping in ensuring the validity of the user by means of
testing the fact that the Name, Account Number, and Tax ID’s are belonging to the same
user.
o Data Security: Security of the data would be ensured by usage of the redundant security
measures and the data stored in the top asset would be treated in a well manner. The
updated encryption techniques would be helping in securing the data as well.
o Reactive Technology: Implementation of the firewall would be helping in providing
security my means of blocking the undesired IP. The backup generators would be
associated sustaining the power to the data warehouse as well as in the server rooms.
Besides this the second independent system would be helping in tackling the difficulties
faced during external failure.
Detect-
The multi-tiered environment would be assuring the quality along with the staging and
the production. This in turn would be helping in having a proper production as well as
increased testing. The codes would also be used for making sure of the testing.
Protect-
o Physical Access Control: Would be helping in mitigation of the losses which occurs due
to the physical threats.
o Digital Access Control: this would be helping in reviewing of the existing users so as to
grant them permission.
o Data Obscuration: This would be helping in ensuring the validity of the user by means of
testing the fact that the Name, Account Number, and Tax ID’s are belonging to the same
user.
o Data Security: Security of the data would be ensured by usage of the redundant security
measures and the data stored in the top asset would be treated in a well manner. The
updated encryption techniques would be helping in securing the data as well.
o Reactive Technology: Implementation of the firewall would be helping in providing
security my means of blocking the undesired IP. The backup generators would be
associated sustaining the power to the data warehouse as well as in the server rooms.
Besides this the second independent system would be helping in tackling the difficulties
faced during external failure.
Detect-

8RISK ASSESSMENT
o Proactive Monitoring: Would be helping in monitoring the system for any kind of
intrusions at the peak time and would be responsible for ensuring the security of the
customers.
o Proactive Monitoring: Would be helping in monitoring the system for any kind of
intrusions at the peak time and would be responsible for ensuring the security of the
customers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RISK ASSESSMENT
References:
Dua, Sumeet, and Xian Du. Data mining and machine learning in cybersecurity. Auerbach
Publications, 2016.
Ganin, Alexander A., et al. "Multicriteria decision framework for cybersecurity risk assessment
and management." Risk Analysis (2017).
Hubbard, Douglas W., and Richard Seiersen. How to measure anything in cybersecurity risk.
John Wiley & Sons, 2016.
Malhotra, Yogesh. "Cybersecurity & Cyber-Finance Risk Management: Strategies, Tactics,
Operations, &, Intelligence: Enterprise Risk Management to Model Risk Management:
Understanding Vulnerabilities, Threats, & Risk Mitigation (Presentation Slides)." (2015).
Meszaros, Jan, and Alena Buchalcevova. "Introducing OSSF: A framework for online service
cybersecurity risk management." computers & security 65 (2017): 300-313.
Radziwill, Nicole M., and Morgan C. Benton. "Cybersecurity Cost of Quality: Managing the
Costs of Cybersecurity Risk Management." arXiv preprint arXiv:1707.02653 (2017).
References:
Dua, Sumeet, and Xian Du. Data mining and machine learning in cybersecurity. Auerbach
Publications, 2016.
Ganin, Alexander A., et al. "Multicriteria decision framework for cybersecurity risk assessment
and management." Risk Analysis (2017).
Hubbard, Douglas W., and Richard Seiersen. How to measure anything in cybersecurity risk.
John Wiley & Sons, 2016.
Malhotra, Yogesh. "Cybersecurity & Cyber-Finance Risk Management: Strategies, Tactics,
Operations, &, Intelligence: Enterprise Risk Management to Model Risk Management:
Understanding Vulnerabilities, Threats, & Risk Mitigation (Presentation Slides)." (2015).
Meszaros, Jan, and Alena Buchalcevova. "Introducing OSSF: A framework for online service
cybersecurity risk management." computers & security 65 (2017): 300-313.
Radziwill, Nicole M., and Morgan C. Benton. "Cybersecurity Cost of Quality: Managing the
Costs of Cybersecurity Risk Management." arXiv preprint arXiv:1707.02653 (2017).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





