Cybersecurity Consultant Report - Security Risk Assessment and Threats
VerifiedAdded on 2022/10/10
|8
|1523
|12
Report
AI Summary
This report presents a comprehensive analysis of cybersecurity from the perspective of a consultant, addressing critical aspects of risk assessment, information asset management, and threat mitigation. The report begins by emphasizing the importance of risk assessment in identifying and managing cyber security vulnerabilities, highlighting limitations of current methods. It then delves into the concept of information assets, explaining their value and the need for robust security measures. The consultant develops questions to identify critical information assets and provides a WFA template for ranking them. The report also explores various cyber threats, including phishing attacks, DDoS attacks, malware, and SQL injection, and discusses the impacts of data breaches, such as the Yahoo incident. Finally, the report outlines strategies for mitigating these threats and protecting organizational data, referencing multiple research papers to support the findings.

Running head: CYBERSECURITY CONSULTANT
.
CYBERSECURITY CONSULTANT
Name of the Student:
Name of the University:
Author Note:
.
CYBERSECURITY CONSULTANT
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBERSECURITY CONSULTANT
Table of Contents
Task 1...................................................................................................................................2
Task 2...................................................................................................................................3
Task 3...................................................................................................................................4
Task 4...................................................................................................................................5
References............................................................................................................................6
Table of Contents
Task 1...................................................................................................................................2
Task 2...................................................................................................................................3
Task 3...................................................................................................................................4
Task 4...................................................................................................................................5
References............................................................................................................................6

2CYBERSECURITY CONSULTANT
Task 1
Risk assessment is the term usually used for describing overall methods where as a cyber-
security consultant (Hughes and Cybenko 2013):
Determine the risk and the hazardous factors that are harmful for the business
(hazard identification phase)
Determine and analyze the risks that are related with the attack (Risk analysis and
risk evaluation phase)
Evaluate the mitigating process to omit the identified hazard (risk control)
The cyber security consultant conduct the risk assessment t identify all business related
risk and also implement some mitigating steps in the business for removing all the identified
risks. Risk assessment helps an organization in various ways like it helps to generate the
awareness regarding the business risks and hazards, it also helps to meet all the legal
requirements of an organization. Cyber security operations deals with many sensitive
information of the business clients and the internal stakeholders of the organization and thus
these data should be kept secured. Therefore, as a cyber – security consultant he or she should
conduct the assessment in a regular basis which ensures the prevention of the data and
encourages the business.
The cyber security consultant perform the risk assessment to identify all the possible risks
and the hazards that could be faced by the organization. Risk assessment helps the organization
to increase the awareness regarding all the possible hazards of the organization (Macaulay and
Singer 2016). These hazards include possible losses that can be faced by the business, security
attacks like phishing attack, losing all the sensitive information of various stakeholders.
Task 1
Risk assessment is the term usually used for describing overall methods where as a cyber-
security consultant (Hughes and Cybenko 2013):
Determine the risk and the hazardous factors that are harmful for the business
(hazard identification phase)
Determine and analyze the risks that are related with the attack (Risk analysis and
risk evaluation phase)
Evaluate the mitigating process to omit the identified hazard (risk control)
The cyber security consultant conduct the risk assessment t identify all business related
risk and also implement some mitigating steps in the business for removing all the identified
risks. Risk assessment helps an organization in various ways like it helps to generate the
awareness regarding the business risks and hazards, it also helps to meet all the legal
requirements of an organization. Cyber security operations deals with many sensitive
information of the business clients and the internal stakeholders of the organization and thus
these data should be kept secured. Therefore, as a cyber – security consultant he or she should
conduct the assessment in a regular basis which ensures the prevention of the data and
encourages the business.
The cyber security consultant perform the risk assessment to identify all the possible risks
and the hazards that could be faced by the organization. Risk assessment helps the organization
to increase the awareness regarding all the possible hazards of the organization (Macaulay and
Singer 2016). These hazards include possible losses that can be faced by the business, security
attacks like phishing attack, losing all the sensitive information of various stakeholders.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBERSECURITY CONSULTANT
The difficulties that are faced by the cyber consultant while conducting a cyber-security
risk assessment are as follows:
Fighting fraud
Business decisions and the User experience
Securing IoT
Filling all the gaps of the security defenses.
Mitigating all the risks related to the GDPR compliance.
The cyber – security risk assessment helps the authority to conduct all the business
operation in an efficient way. This helps the business to achieve all the business goals and also
allow the business to fulfill all the customer demands. This also helps the business to take quick
as well as efficient business decisions (Singer and Friedman 2014). The business can also take
decisions based on the collected information from the cyber – security risk assessment, for
example, if it is found that usage of the official database without any access requirement is a risk
for the business then the business should implement some methods to gain access before
accessing the official database which could help the business to improve the business quality
without any fear
Task 2
Information Asset is the set of knowledge which is structured and handled considering all
as a single entity. Information asset for an organization holds some financial value for the
organization. Thus, it should kept secured. Security of these information assets should be one of
the primary factor any type of organization. Information assets can be of many types like IT
The difficulties that are faced by the cyber consultant while conducting a cyber-security
risk assessment are as follows:
Fighting fraud
Business decisions and the User experience
Securing IoT
Filling all the gaps of the security defenses.
Mitigating all the risks related to the GDPR compliance.
The cyber – security risk assessment helps the authority to conduct all the business
operation in an efficient way. This helps the business to achieve all the business goals and also
allow the business to fulfill all the customer demands. This also helps the business to take quick
as well as efficient business decisions (Singer and Friedman 2014). The business can also take
decisions based on the collected information from the cyber – security risk assessment, for
example, if it is found that usage of the official database without any access requirement is a risk
for the business then the business should implement some methods to gain access before
accessing the official database which could help the business to improve the business quality
without any fear
Task 2
Information Asset is the set of knowledge which is structured and handled considering all
as a single entity. Information asset for an organization holds some financial value for the
organization. Thus, it should kept secured. Security of these information assets should be one of
the primary factor any type of organization. Information assets can be of many types like IT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CYBERSECURITY CONSULTANT
assets which is the type of information that is owned by the company and is used for some
business operations (Shaw 1991).
Each and every information asset of an organization holds some value for the
organization. Thus the value of these assets get increased as the value increases. The data stored
in the set plays an important role for the business like some customer’s details are stored in the
database. This database is an important tool for the business and thus should be secured such that
the information cannot be misused for some purpose which will impact negatively in the
business. Therefore, it can be concluded that the data stored in the set consider the value of the
information asset for any organization.
Access security should be developed such that the security factor of the organization gets
enhanced and the information are kept secured (Peltier 2016). The access should be given to
some specific authorities who can easily access the data set and will not misuse the information
of the clients. The access process should be of one way which means that the only network
administrator or the work force administrator should provide all the access of the data set and
should not involve any other person in this process.
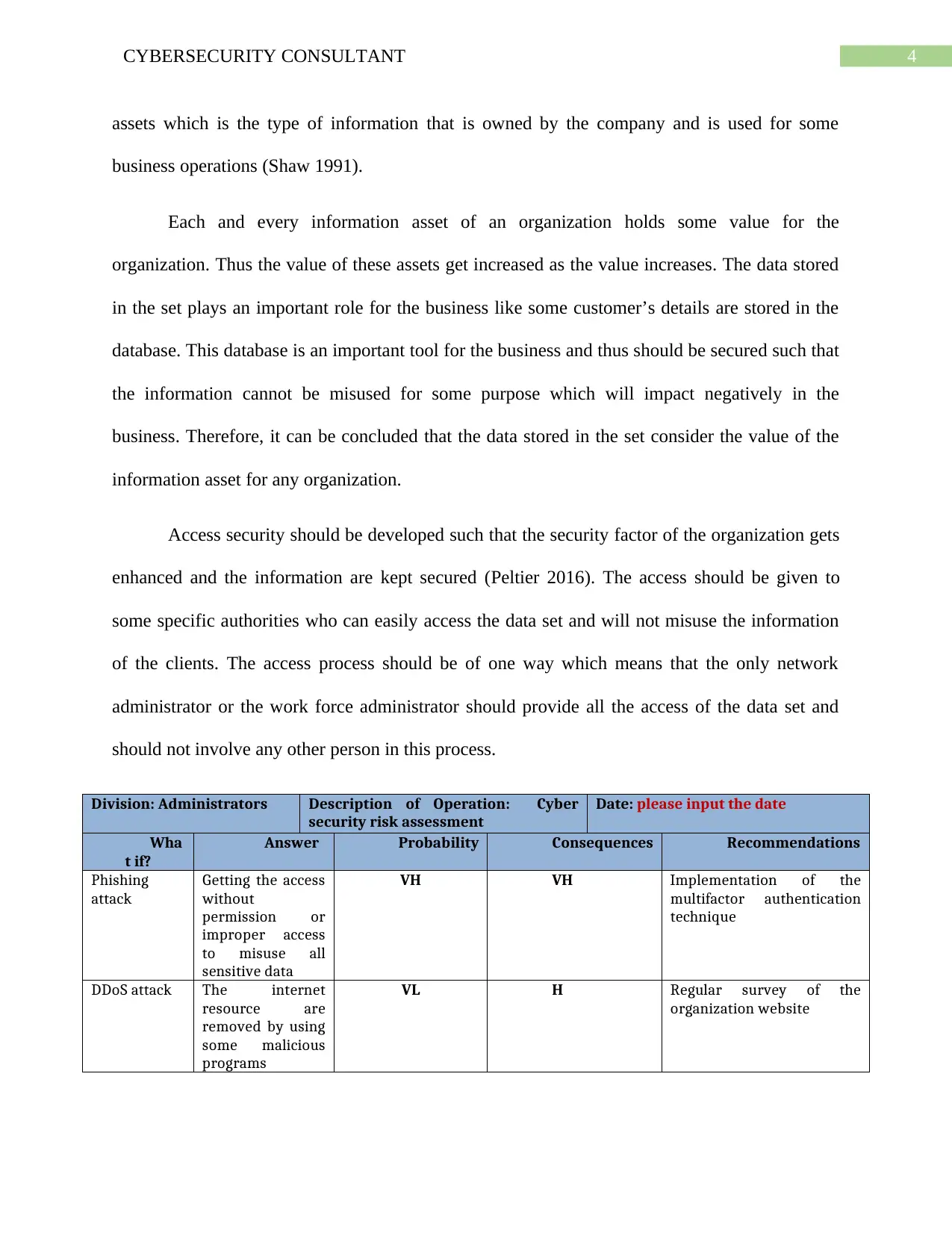
Division: Administrators Description of Operation: Cyber
security risk assessment
Date: please input the date
Wha
t if?
Answer Probability Consequences Recommendations
Phishing
attack
Getting the access
without
permission or
improper access
to misuse all
sensitive data
VH VH Implementation of the
multifactor authentication
technique
DDoS attack The internet
resource are
removed by using
some malicious
programs
VL H Regular survey of the
organization website
assets which is the type of information that is owned by the company and is used for some
business operations (Shaw 1991).
Each and every information asset of an organization holds some value for the
organization. Thus the value of these assets get increased as the value increases. The data stored
in the set plays an important role for the business like some customer’s details are stored in the
database. This database is an important tool for the business and thus should be secured such that
the information cannot be misused for some purpose which will impact negatively in the
business. Therefore, it can be concluded that the data stored in the set consider the value of the
information asset for any organization.
Access security should be developed such that the security factor of the organization gets
enhanced and the information are kept secured (Peltier 2016). The access should be given to
some specific authorities who can easily access the data set and will not misuse the information
of the clients. The access process should be of one way which means that the only network
administrator or the work force administrator should provide all the access of the data set and
should not involve any other person in this process.
Division: Administrators Description of Operation: Cyber
security risk assessment
Date: please input the date
Wha
t if?
Answer Probability Consequences Recommendations
Phishing
attack
Getting the access
without
permission or
improper access
to misuse all
sensitive data
VH VH Implementation of the
multifactor authentication
technique
DDoS attack The internet
resource are
removed by using
some malicious
programs
VL H Regular survey of the
organization website
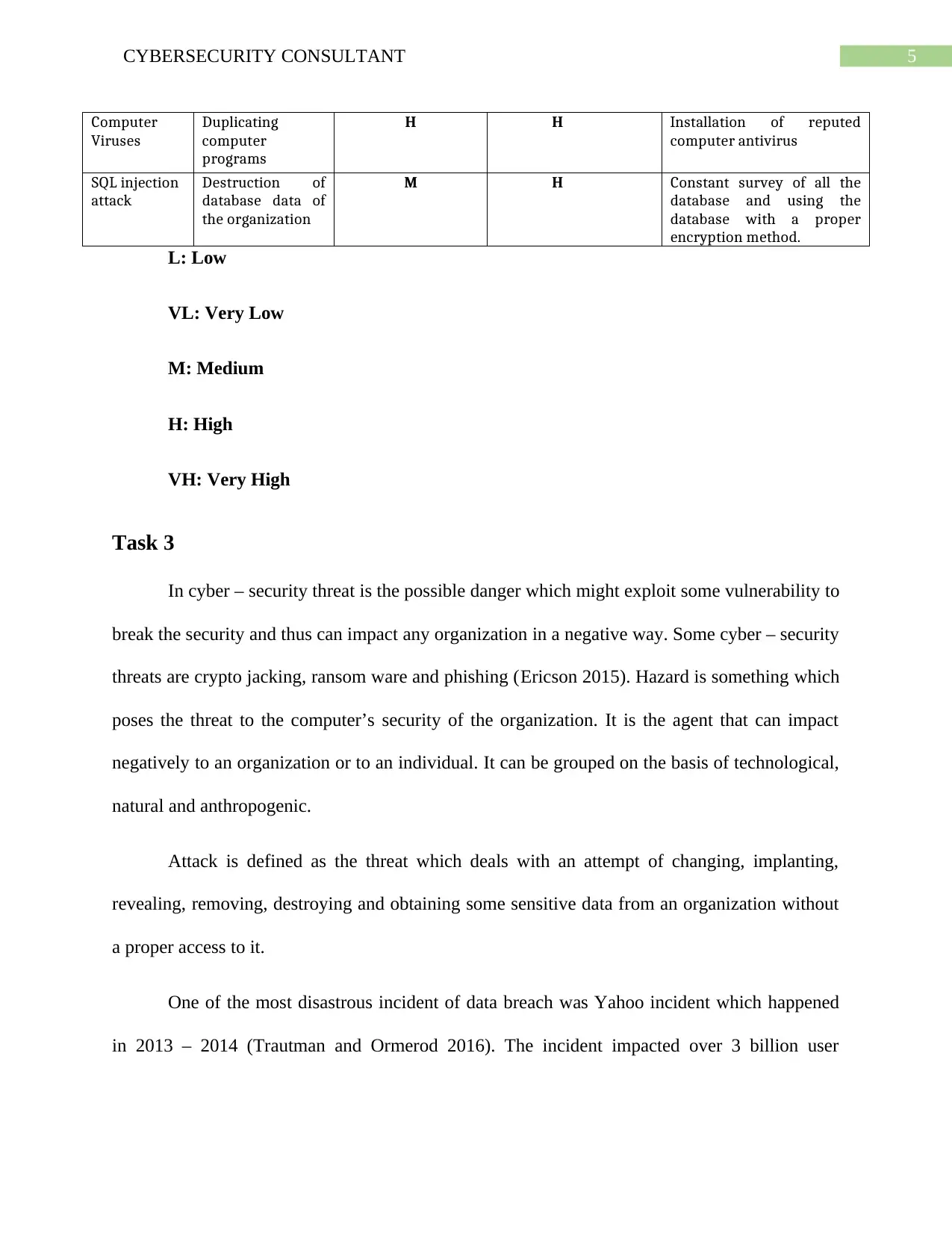
5CYBERSECURITY CONSULTANT
Computer
Viruses
Duplicating
computer
programs
H H Installation of reputed
computer antivirus
SQL injection
attack
Destruction of
database data of
the organization
M H Constant survey of all the
database and using the
database with a proper
encryption method.
L: Low
VL: Very Low
M: Medium
H: High
VH: Very High
Task 3
In cyber – security threat is the possible danger which might exploit some vulnerability to
break the security and thus can impact any organization in a negative way. Some cyber – security
threats are crypto jacking, ransom ware and phishing (Ericson 2015). Hazard is something which
poses the threat to the computer’s security of the organization. It is the agent that can impact
negatively to an organization or to an individual. It can be grouped on the basis of technological,
natural and anthropogenic.
Attack is defined as the threat which deals with an attempt of changing, implanting,
revealing, removing, destroying and obtaining some sensitive data from an organization without
a proper access to it.
One of the most disastrous incident of data breach was Yahoo incident which happened
in 2013 – 2014 (Trautman and Ormerod 2016). The incident impacted over 3 billion user
Computer
Viruses
Duplicating
computer
programs
H H Installation of reputed
computer antivirus
SQL injection
attack
Destruction of
database data of
the organization
M H Constant survey of all the
database and using the
database with a proper
encryption method.
L: Low
VL: Very Low
M: Medium
H: High
VH: Very High
Task 3
In cyber – security threat is the possible danger which might exploit some vulnerability to
break the security and thus can impact any organization in a negative way. Some cyber – security
threats are crypto jacking, ransom ware and phishing (Ericson 2015). Hazard is something which
poses the threat to the computer’s security of the organization. It is the agent that can impact
negatively to an organization or to an individual. It can be grouped on the basis of technological,
natural and anthropogenic.
Attack is defined as the threat which deals with an attempt of changing, implanting,
revealing, removing, destroying and obtaining some sensitive data from an organization without
a proper access to it.
One of the most disastrous incident of data breach was Yahoo incident which happened
in 2013 – 2014 (Trautman and Ormerod 2016). The incident impacted over 3 billion user
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBERSECURITY CONSULTANT
accounts. 500 million user details was breached which includes email address, name, date of
birth and other details too.
This incident is an appropriate example which portrays that the security issues should be
a primary factor for any organization. The organization can face a huge loss from this type of
incident. Every business should focus on the security of the sensitive information. Any kind of
indifference in the organization can lead to a huge loss for the organization.
Some threats of the organization are phishing attack, DDoS attack and Viruses. In case of
phishing attack, the attacker collects all the information without the proper access. This can be
prevented by strongly protecting all the accessing method used in the organization (Kumar,
Srivastava and Lazarevic 2006). Every organization should implement multifactor
authentication. Computer viruses can be obstructed or mitigated by implementing a good quality
antivirus.
Task 4
Some most critical threats for the information assets of an organization are ransom ware,
phishing, DDoS, malware, computer viruses, SQL injection attack and data breach.
Each and every threat mainly aims to steal all information to misuse them. The stole
information can be misused in various ways.
accounts. 500 million user details was breached which includes email address, name, date of
birth and other details too.
This incident is an appropriate example which portrays that the security issues should be
a primary factor for any organization. The organization can face a huge loss from this type of
incident. Every business should focus on the security of the sensitive information. Any kind of
indifference in the organization can lead to a huge loss for the organization.
Some threats of the organization are phishing attack, DDoS attack and Viruses. In case of
phishing attack, the attacker collects all the information without the proper access. This can be
prevented by strongly protecting all the accessing method used in the organization (Kumar,
Srivastava and Lazarevic 2006). Every organization should implement multifactor
authentication. Computer viruses can be obstructed or mitigated by implementing a good quality
antivirus.
Task 4
Some most critical threats for the information assets of an organization are ransom ware,
phishing, DDoS, malware, computer viruses, SQL injection attack and data breach.
Each and every threat mainly aims to steal all information to misuse them. The stole
information can be misused in various ways.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBERSECURITY CONSULTANT
References
Ericson, C.A., 2015. Hazard analysis techniques for system safety. John Wiley & Sons.
Hughes, J. and Cybenko, G., 2013. Quantitative metrics and risk assessment: The three tenets
model of cybersecurity. Technology Innovation Management Review, 3(8).
Kumar, V., Srivastava, J. and Lazarevic, A. eds., 2006. Managing cyber threats: issues,
approaches, and challenges (Vol. 5). Springer Science & Business Media.
Macaulay, T. and Singer, B.L., 2016. Cybersecurity for industrial control systems: SCADA,
DCS, PLC, HMI, and SIS. Auerbach Publications.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Shaw, R., 1991. Computer-aided marketing and selling: information asset management. Robert
Shaw.
Singer, P.W. and Friedman, A., 2014. Cybersecurity: What everyone needs to know. OUP USA.
Trautman, L.J. and Ormerod, P.C., 2016. Corporate Directors' and Officers' Cybersecurity
Standard of Care: The Yahoo Data Breach. Am. UL Rev., 66, p.1231.
References
Ericson, C.A., 2015. Hazard analysis techniques for system safety. John Wiley & Sons.
Hughes, J. and Cybenko, G., 2013. Quantitative metrics and risk assessment: The three tenets
model of cybersecurity. Technology Innovation Management Review, 3(8).
Kumar, V., Srivastava, J. and Lazarevic, A. eds., 2006. Managing cyber threats: issues,
approaches, and challenges (Vol. 5). Springer Science & Business Media.
Macaulay, T. and Singer, B.L., 2016. Cybersecurity for industrial control systems: SCADA,
DCS, PLC, HMI, and SIS. Auerbach Publications.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Shaw, R., 1991. Computer-aided marketing and selling: information asset management. Robert
Shaw.
Singer, P.W. and Friedman, A., 2014. Cybersecurity: What everyone needs to know. OUP USA.
Trautman, L.J. and Ormerod, P.C., 2016. Corporate Directors' and Officers' Cybersecurity
Standard of Care: The Yahoo Data Breach. Am. UL Rev., 66, p.1231.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




