Cybersecurity Report: Risk Management and Policy Development
VerifiedAdded on 2022/09/21
|13
|2914
|21
Report
AI Summary
This cybersecurity report, prepared for Advanced Medicos Limited (AML), addresses the company's contemporary cyber threats. It includes an introduction to cybersecurity's role in managing risks, emphasizing the importance of security controls for IT assets. The report details the development of a security policy, risk management strategies, and access control policies for AML, considering data, software, and hardware access. It provides a cost-benefit analysis, outlines the six phases of incident response planning, and gives examples of natural and human-made disasters. The report also includes a risk assessment based on the ISO 27005 framework, analyzing vulnerabilities and threats to the system. It offers recommendations for improving AML's cybersecurity posture, including backup policies, computer use policies, and network security improvements. The report aims to provide AML's CIO with actionable insights to mitigate risks and enhance the overall security of the company's IT infrastructure, ensuring data protection and business continuity.

4/14/2020
Running Head: CYBERSECURITY 0
Cybersecurity
Report
Student name
Running Head: CYBERSECURITY 0
Cybersecurity
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBERSECURITY 1
Table of Contents
Introduction................................................................................................................................1
Security policy development and risk management...................................................................1
Access control policy:............................................................................................................1
Data access:........................................................................................................................2
Software access control:.....................................................................................................2
Hardware access control:...................................................................................................2
Cost benefit analysis:.........................................................................................................2
Six phases of developing an incident response plan..........................................................4
Five examples of natural or human-made disasters...........................................................4
Risk assessment..........................................................................................................................4
Risk analysis:.........................................................................................................................6
Conclusion:................................................................................................................................8
References..................................................................................................................................8
Table of Contents
Introduction................................................................................................................................1
Security policy development and risk management...................................................................1
Access control policy:............................................................................................................1
Data access:........................................................................................................................2
Software access control:.....................................................................................................2
Hardware access control:...................................................................................................2
Cost benefit analysis:.........................................................................................................2
Six phases of developing an incident response plan..........................................................4
Five examples of natural or human-made disasters...........................................................4
Risk assessment..........................................................................................................................4
Risk analysis:.........................................................................................................................6
Conclusion:................................................................................................................................8
References..................................................................................................................................8

CYBERSECURITY 2
Introduction
Cybersecurity is necessary for managing the risks and threats of a firm. Most of the
companies have used Information System (IS) and Information Technology (IT). It is an
important part of a system to secure the data and information from different types of threats.
It can be used for managing all the services in a better way. Most of the systems have used an
advanced level of security to improve the basic processes. In Advanced Medicos Limited
(AML), the company sells healthcare products. The company has used IT-assets for
managing its business function. The company has faced emerging and contemporary risk
from cyber threats. Moreover, security controls are necessary to improve the privacy and
security of IT assets. It is a basic need for a system to make secure its components from the
outside world. In the case of the security system, most of the companies have developed their
security system based on the international security standards, such as ISO 27001, ISO 27005,
ISO 31000, and many more (Andrijcic & Horowitz, 2016). Risk management is necessary for
a system in a company. most of the countries have provided a fixed format for risk mitigation
strategies. This report will provide suggestions to the CIO of the company based on the risk
assessment. It will design an access control policy for AML as well.
Security policy development and risk management
Risk assessment can be used for identifying vulnerabilities and threats of the company. it
helps secure a firm from financial loss and bad incidents. It can be better for small, medium,
large scale firms as well (Purdy, 2010). A company should think about the basic processes of
security to avoid cybercrimes and cyber-attacks on its IT infrastructure. The most important
part is that computer systems should updated from antivirus and latest approaches (Arlitsch &
Edelman, 2014).
Access control policy:
In a company, computer systems have used for managing various types of services, as the
AML has provided a platform to sell products online by the customers as well. Thus, it is
necessary to provide web services to manage an online business as well. Access control
policy has used for providing proper access control to the different IT assets and business
processes. AML has stored data of their customers including personal details and credit card
details as well. Thus, it is mandatory to secure that information from other users as well as
Introduction
Cybersecurity is necessary for managing the risks and threats of a firm. Most of the
companies have used Information System (IS) and Information Technology (IT). It is an
important part of a system to secure the data and information from different types of threats.
It can be used for managing all the services in a better way. Most of the systems have used an
advanced level of security to improve the basic processes. In Advanced Medicos Limited
(AML), the company sells healthcare products. The company has used IT-assets for
managing its business function. The company has faced emerging and contemporary risk
from cyber threats. Moreover, security controls are necessary to improve the privacy and
security of IT assets. It is a basic need for a system to make secure its components from the
outside world. In the case of the security system, most of the companies have developed their
security system based on the international security standards, such as ISO 27001, ISO 27005,
ISO 31000, and many more (Andrijcic & Horowitz, 2016). Risk management is necessary for
a system in a company. most of the countries have provided a fixed format for risk mitigation
strategies. This report will provide suggestions to the CIO of the company based on the risk
assessment. It will design an access control policy for AML as well.
Security policy development and risk management
Risk assessment can be used for identifying vulnerabilities and threats of the company. it
helps secure a firm from financial loss and bad incidents. It can be better for small, medium,
large scale firms as well (Purdy, 2010). A company should think about the basic processes of
security to avoid cybercrimes and cyber-attacks on its IT infrastructure. The most important
part is that computer systems should updated from antivirus and latest approaches (Arlitsch &
Edelman, 2014).
Access control policy:
In a company, computer systems have used for managing various types of services, as the
AML has provided a platform to sell products online by the customers as well. Thus, it is
necessary to provide web services to manage an online business as well. Access control
policy has used for providing proper access control to the different IT assets and business
processes. AML has stored data of their customers including personal details and credit card
details as well. Thus, it is mandatory to secure that information from other users as well as
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBERSECURITY 3
attackers. Therefore, access to data should be in limit according to their level as well
(Bendovschi, 2015).
Besides, the company has used a physical database server that is used for storing customer’s
information. Thus, it is necessary to make secure access to centralized data of all the
customers of the company. in addition, office 365 email hosting is used for effective
communication with customers. Therefore, it is mandatory to secure emails using encryption
techniques as well (Bhagat, 2012).
Access control policy can be applied to all the employees and other staff members. They
should know about their limits and security system will stop the unauthorized access of
various people (Caruana, 2016).
There is the main three access control required in AML, which areas:
Data access:
Data must secure from various types of users, as customers can only access their accounts
and general information about the company. Admin can access the server and database server
as well. Moreover, employees can access a limited data and information from servers and
database. It should be restricted as well from outsiders. In addition, there are many benefits
to information access.
Software access control:
Online software should be restricted to other users. It can only access by authorized persons.
Software code should be secure from employees and operators, as anyone can change codes
of the financial data as well. Thus, the software can be access by the admin as well.
Hardware access control:
Server and other networking devices should be in surveillance. It must secure from physical
and technical security. All the servers must be in locked room and only admin can access that
premises. It will provide better security to the system as well.
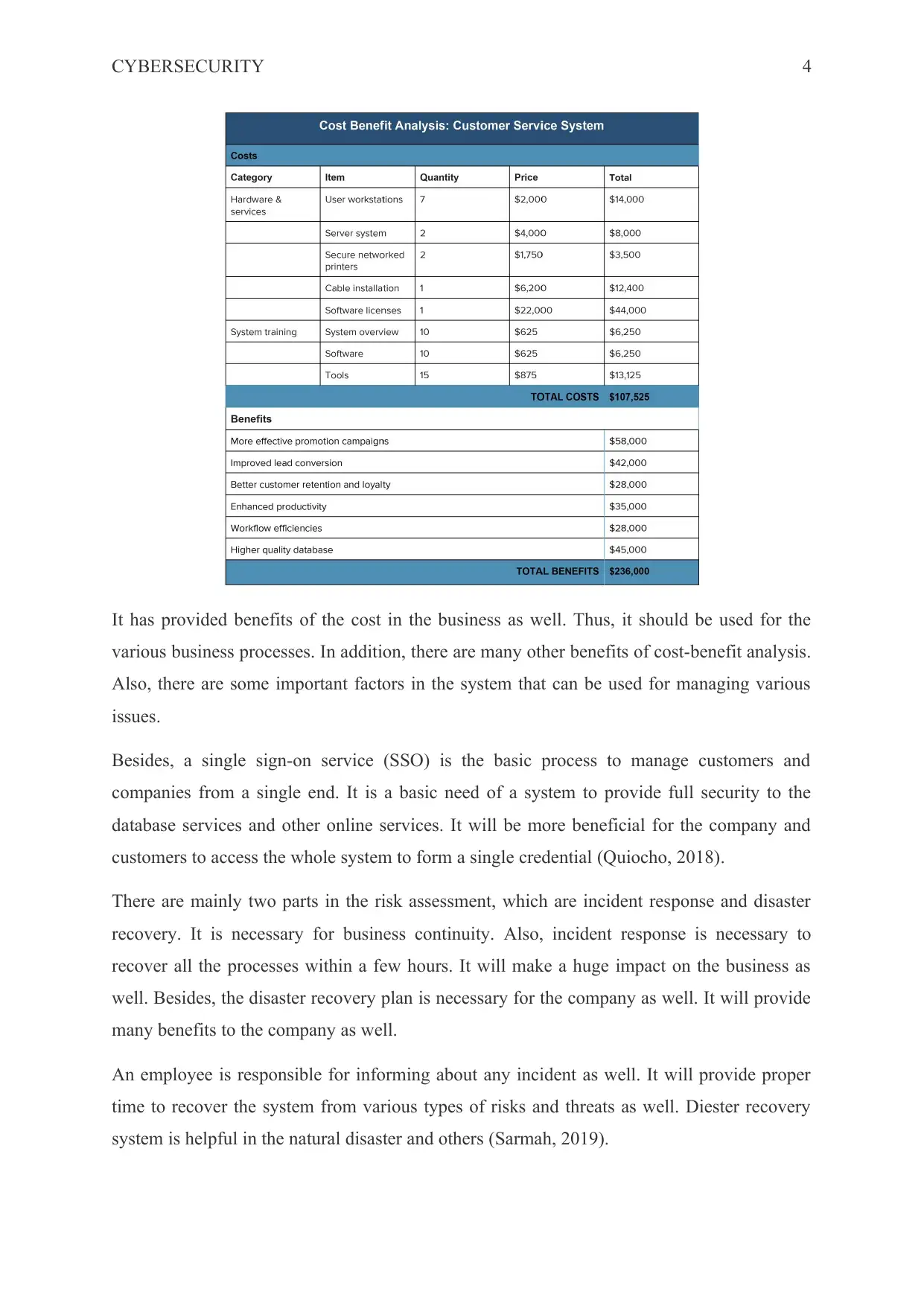
Cost benefit analysis:
It is a necessary process to know about the benefits of various resources. In addition, there is
a huge impact of the cost benefits analysis in the systems as well.
attackers. Therefore, access to data should be in limit according to their level as well
(Bendovschi, 2015).
Besides, the company has used a physical database server that is used for storing customer’s
information. Thus, it is necessary to make secure access to centralized data of all the
customers of the company. in addition, office 365 email hosting is used for effective
communication with customers. Therefore, it is mandatory to secure emails using encryption
techniques as well (Bhagat, 2012).
Access control policy can be applied to all the employees and other staff members. They
should know about their limits and security system will stop the unauthorized access of
various people (Caruana, 2016).
There is the main three access control required in AML, which areas:
Data access:
Data must secure from various types of users, as customers can only access their accounts
and general information about the company. Admin can access the server and database server
as well. Moreover, employees can access a limited data and information from servers and
database. It should be restricted as well from outsiders. In addition, there are many benefits
to information access.
Software access control:
Online software should be restricted to other users. It can only access by authorized persons.
Software code should be secure from employees and operators, as anyone can change codes
of the financial data as well. Thus, the software can be access by the admin as well.
Hardware access control:
Server and other networking devices should be in surveillance. It must secure from physical
and technical security. All the servers must be in locked room and only admin can access that
premises. It will provide better security to the system as well.
Cost benefit analysis:
It is a necessary process to know about the benefits of various resources. In addition, there is
a huge impact of the cost benefits analysis in the systems as well.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CYBERSECURITY 4
It has provided benefits of the cost in the business as well. Thus, it should be used for the
various business processes. In addition, there are many other benefits of cost-benefit analysis.
Also, there are some important factors in the system that can be used for managing various
issues.
Besides, a single sign-on service (SSO) is the basic process to manage customers and
companies from a single end. It is a basic need of a system to provide full security to the
database services and other online services. It will be more beneficial for the company and
customers to access the whole system to form a single credential (Quiocho, 2018).
There are mainly two parts in the risk assessment, which are incident response and disaster
recovery. It is necessary for business continuity. Also, incident response is necessary to
recover all the processes within a few hours. It will make a huge impact on the business as
well. Besides, the disaster recovery plan is necessary for the company as well. It will provide
many benefits to the company as well.
An employee is responsible for informing about any incident as well. It will provide proper
time to recover the system from various types of risks and threats as well. Diester recovery
system is helpful in the natural disaster and others (Sarmah, 2019).
It has provided benefits of the cost in the business as well. Thus, it should be used for the
various business processes. In addition, there are many other benefits of cost-benefit analysis.
Also, there are some important factors in the system that can be used for managing various
issues.
Besides, a single sign-on service (SSO) is the basic process to manage customers and
companies from a single end. It is a basic need of a system to provide full security to the
database services and other online services. It will be more beneficial for the company and
customers to access the whole system to form a single credential (Quiocho, 2018).
There are mainly two parts in the risk assessment, which are incident response and disaster
recovery. It is necessary for business continuity. Also, incident response is necessary to
recover all the processes within a few hours. It will make a huge impact on the business as
well. Besides, the disaster recovery plan is necessary for the company as well. It will provide
many benefits to the company as well.
An employee is responsible for informing about any incident as well. It will provide proper
time to recover the system from various types of risks and threats as well. Diester recovery
system is helpful in the natural disaster and others (Sarmah, 2019).

CYBERSECURITY 5
Six phases of developing an incident response plan
The incident response phases are:
Preparation: it is necessary to prepare for a particular situation based on the security
control.
Identification: risk must be identified based on the response of an employee
Containment: it should be managed using a proper solution as well.
Eradication: the problem must be identified with its impacts as well.
Recovery: recovery process should be used to overcome damages
Lessons Learned: it must have recorded for the learning as well.
All the point is important for the system as well.
Five examples of natural or human-made disasters
Earthquakes: it can damage the structure of the company as well. Thus, data must be secure
from all the points.
Floods: data should be stored at cloud storage as well.
Landslides: data and information can be used from cloud-based services.
Fires: use a fire protection system for security.
Cyclones: physical security can be used for this thing as well.
There are some basics terms in the disaster reconvey plan, which areas:
Recovery Point Objective (RPO): It defines the maximum allowable age of the most
recent backup of data and information. It is a specific copy of the user’s data. In case
of storage device failure because of any reason including files deleted than data
backup can be used for managing all the processes.
Maximum Tolerable Downtime (MTD): it provides a better service in term of time. It
is the maximum amount of time an application or data can be unavailable to users,
according to the business management. It has related to the impact on business
functions of an organization in terms of lost revenue and other costs that are incurred
for every hour, day, or week.
Recovery Time Objective (RTO): it is a recovery time from any failure of the system
as well. it will generally be a technical consideration, to be determined by the IT
Six phases of developing an incident response plan
The incident response phases are:
Preparation: it is necessary to prepare for a particular situation based on the security
control.
Identification: risk must be identified based on the response of an employee
Containment: it should be managed using a proper solution as well.
Eradication: the problem must be identified with its impacts as well.
Recovery: recovery process should be used to overcome damages
Lessons Learned: it must have recorded for the learning as well.
All the point is important for the system as well.
Five examples of natural or human-made disasters
Earthquakes: it can damage the structure of the company as well. Thus, data must be secure
from all the points.
Floods: data should be stored at cloud storage as well.
Landslides: data and information can be used from cloud-based services.
Fires: use a fire protection system for security.
Cyclones: physical security can be used for this thing as well.
There are some basics terms in the disaster reconvey plan, which areas:
Recovery Point Objective (RPO): It defines the maximum allowable age of the most
recent backup of data and information. It is a specific copy of the user’s data. In case
of storage device failure because of any reason including files deleted than data
backup can be used for managing all the processes.
Maximum Tolerable Downtime (MTD): it provides a better service in term of time. It
is the maximum amount of time an application or data can be unavailable to users,
according to the business management. It has related to the impact on business
functions of an organization in terms of lost revenue and other costs that are incurred
for every hour, day, or week.
Recovery Time Objective (RTO): it is a recovery time from any failure of the system
as well. it will generally be a technical consideration, to be determined by the IT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBERSECURITY 6
experts. It will provide estimated time for replace equipment, and restore data from
backup systems.
In addition, disaster recovery is a process in which all the programs can be used for managing
all the terms. It will provide data from data backups if data is missing and lost. Moreover,
business continuity is a process to restart whole processes based on the data backups.
Risk assessment
There are many benefits of risk assessment of a firm, as it has provided risks of the firm
based on the audit in which all the vulnerabilities have founded that can be a reason for threat
for the company as well. In addition, security controls can be created based on the risk
assessment as well.
Besides, ISO 27005 framework has used for risk assessment. It has provided better risk
analysis processes for risk assessment. It is the best way to manage all the processes in a
better way. Moreover, risk assessment can be used for managing all the things in a better
process (Datameer, 2018).
Source: (ITgovernance, 2019)
ISO 27005 framework can be used for managing different types of services in the company
as well (Von Solms & Van Niekerk, 2013). It will provide better risk assessment for the
experts. It will provide estimated time for replace equipment, and restore data from
backup systems.
In addition, disaster recovery is a process in which all the programs can be used for managing
all the terms. It will provide data from data backups if data is missing and lost. Moreover,
business continuity is a process to restart whole processes based on the data backups.
Risk assessment
There are many benefits of risk assessment of a firm, as it has provided risks of the firm
based on the audit in which all the vulnerabilities have founded that can be a reason for threat
for the company as well. In addition, security controls can be created based on the risk
assessment as well.
Besides, ISO 27005 framework has used for risk assessment. It has provided better risk
analysis processes for risk assessment. It is the best way to manage all the processes in a
better way. Moreover, risk assessment can be used for managing all the things in a better
process (Datameer, 2018).
Source: (ITgovernance, 2019)
ISO 27005 framework can be used for managing different types of services in the company
as well (Von Solms & Van Niekerk, 2013). It will provide better risk assessment for the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CYBERSECURITY 7
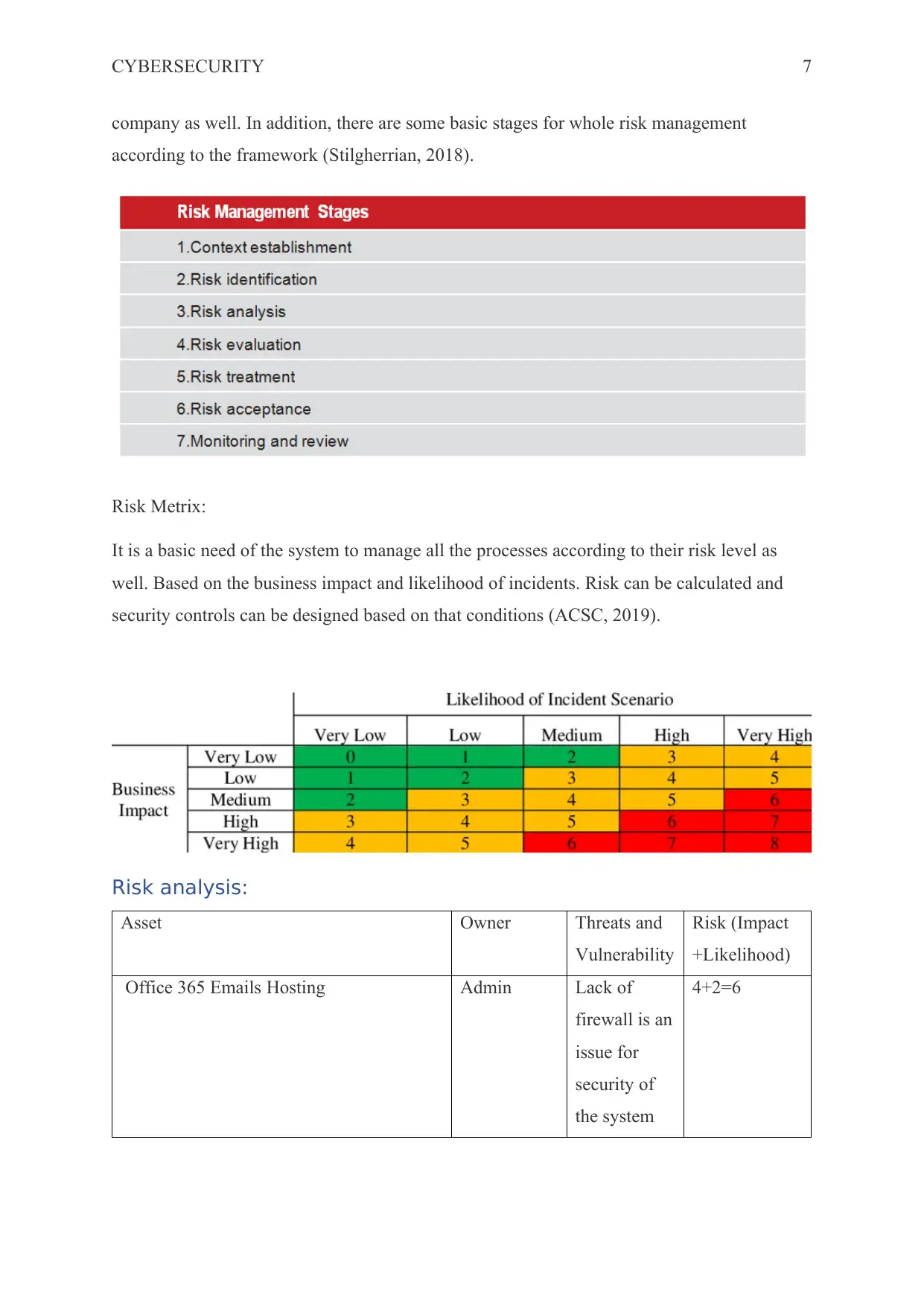
company as well. In addition, there are some basic stages for whole risk management
according to the framework (Stilgherrian, 2018).
Risk Metrix:
It is a basic need of the system to manage all the processes according to their risk level as
well. Based on the business impact and likelihood of incidents. Risk can be calculated and
security controls can be designed based on that conditions (ACSC, 2019).
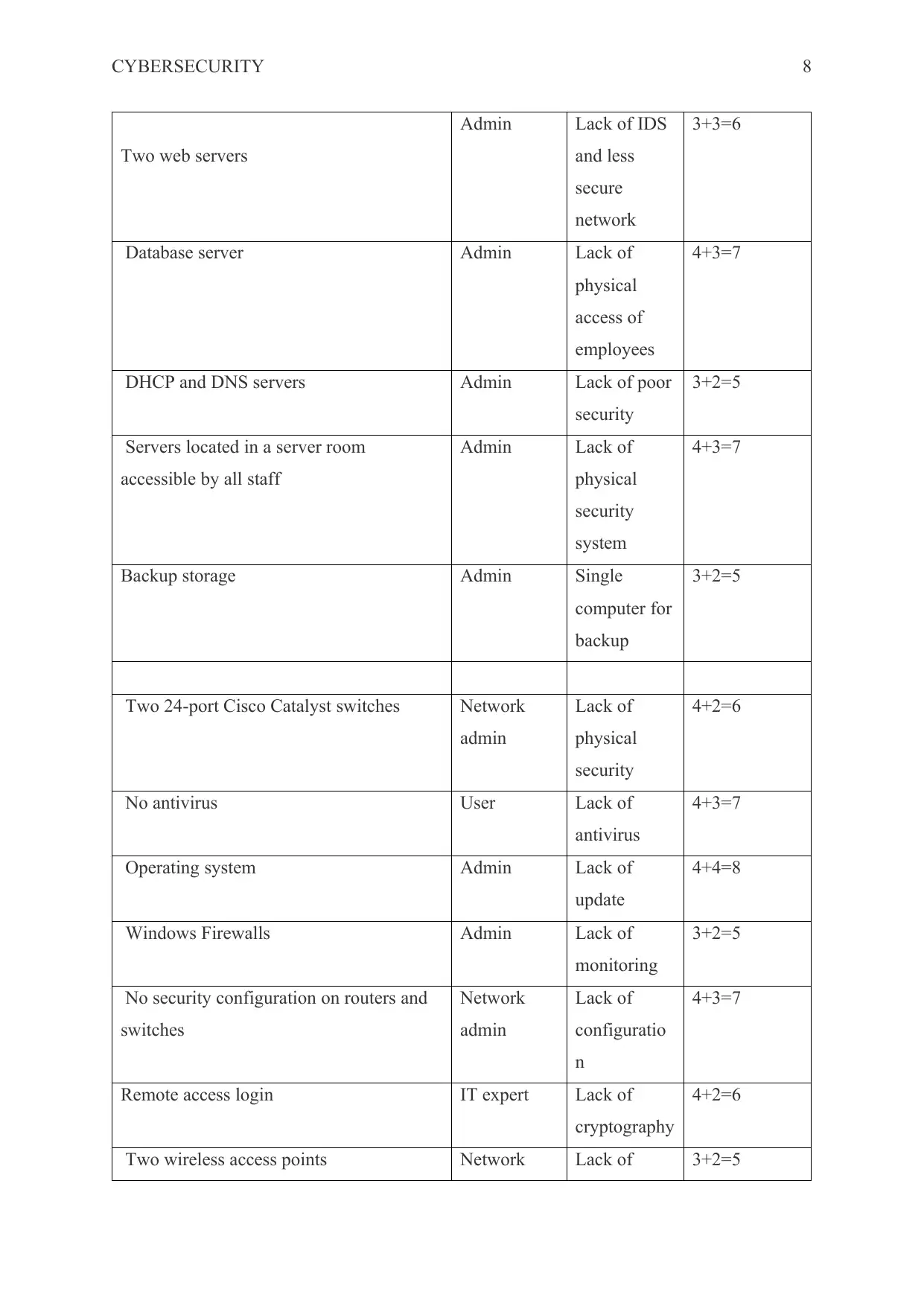
Risk analysis:
Asset Owner Threats and
Vulnerability
Risk (Impact
+Likelihood)
Office 365 Emails Hosting Admin Lack of
firewall is an
issue for
security of
the system
4+2=6
company as well. In addition, there are some basic stages for whole risk management
according to the framework (Stilgherrian, 2018).
Risk Metrix:
It is a basic need of the system to manage all the processes according to their risk level as
well. Based on the business impact and likelihood of incidents. Risk can be calculated and
security controls can be designed based on that conditions (ACSC, 2019).
Risk analysis:
Asset Owner Threats and
Vulnerability
Risk (Impact
+Likelihood)
Office 365 Emails Hosting Admin Lack of
firewall is an
issue for
security of
the system
4+2=6
CYBERSECURITY 8
Two web servers
Admin Lack of IDS
and less
secure
network
3+3=6
Database server Admin Lack of
physical
access of
employees
4+3=7
DHCP and DNS servers Admin Lack of poor
security
3+2=5
Servers located in a server room
accessible by all staff
Admin Lack of
physical
security
system
4+3=7
Backup storage Admin Single
computer for
backup
3+2=5
Two 24-port Cisco Catalyst switches Network
admin
Lack of
physical
security
4+2=6
No antivirus User Lack of
antivirus
4+3=7
Operating system Admin Lack of
update
4+4=8
Windows Firewalls Admin Lack of
monitoring
3+2=5
No security configuration on routers and
switches
Network
admin
Lack of
configuratio
n
4+3=7
Remote access login IT expert Lack of
cryptography
4+2=6
Two wireless access points Network Lack of 3+2=5
Two web servers
Admin Lack of IDS
and less
secure
network
3+3=6
Database server Admin Lack of
physical
access of
employees
4+3=7
DHCP and DNS servers Admin Lack of poor
security
3+2=5
Servers located in a server room
accessible by all staff
Admin Lack of
physical
security
system
4+3=7
Backup storage Admin Single
computer for
backup
3+2=5
Two 24-port Cisco Catalyst switches Network
admin
Lack of
physical
security
4+2=6
No antivirus User Lack of
antivirus
4+3=7
Operating system Admin Lack of
update
4+4=8
Windows Firewalls Admin Lack of
monitoring
3+2=5
No security configuration on routers and
switches
Network
admin
Lack of
configuratio
n
4+3=7
Remote access login IT expert Lack of
cryptography
4+2=6
Two wireless access points Network Lack of 3+2=5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
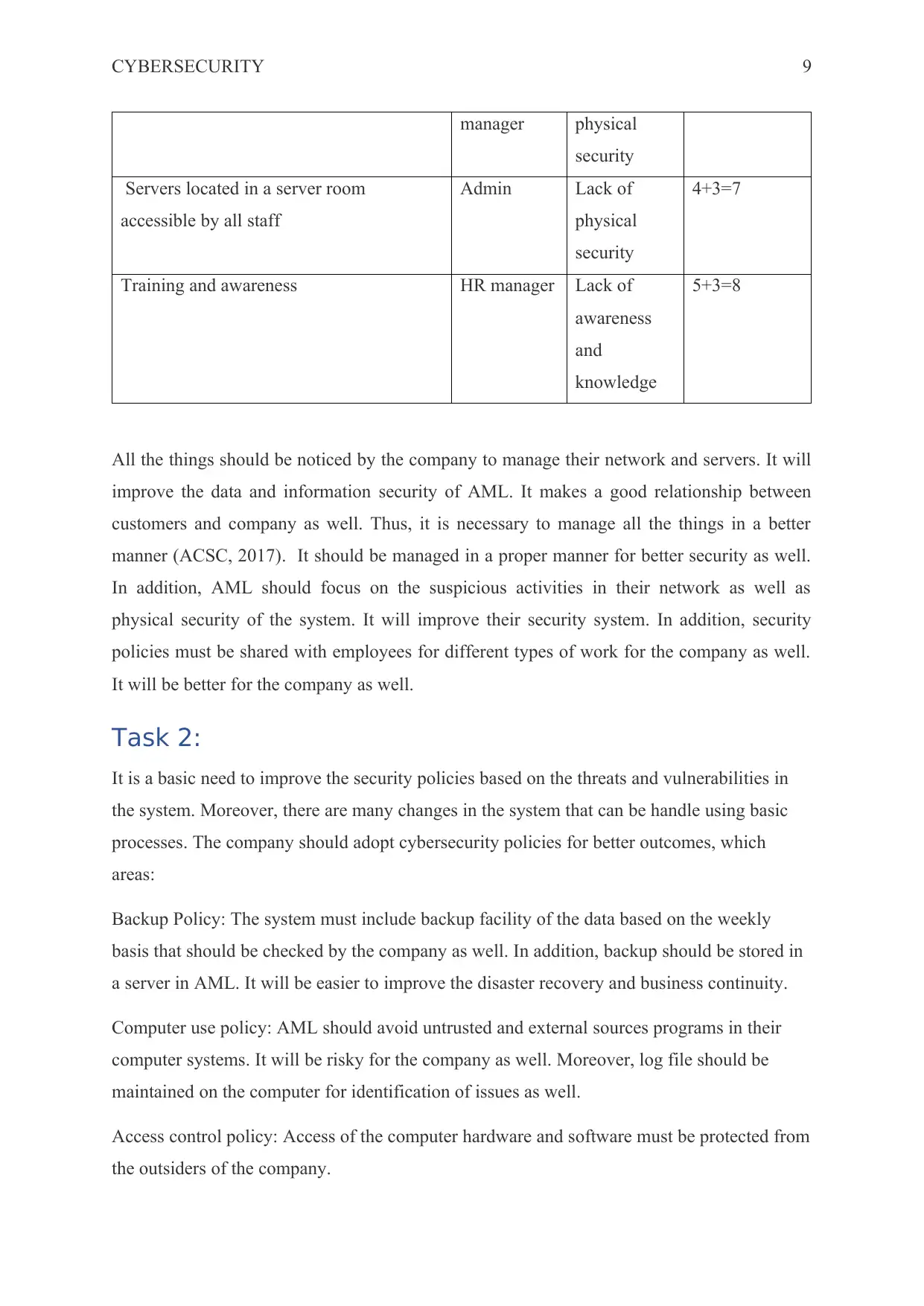
CYBERSECURITY 9
manager physical
security
Servers located in a server room
accessible by all staff
Admin Lack of
physical
security
4+3=7
Training and awareness HR manager Lack of
awareness
and
knowledge
5+3=8
All the things should be noticed by the company to manage their network and servers. It will
improve the data and information security of AML. It makes a good relationship between
customers and company as well. Thus, it is necessary to manage all the things in a better
manner (ACSC, 2017). It should be managed in a proper manner for better security as well.
In addition, AML should focus on the suspicious activities in their network as well as
physical security of the system. It will improve their security system. In addition, security
policies must be shared with employees for different types of work for the company as well.
It will be better for the company as well.
Task 2:
It is a basic need to improve the security policies based on the threats and vulnerabilities in
the system. Moreover, there are many changes in the system that can be handle using basic
processes. The company should adopt cybersecurity policies for better outcomes, which
areas:
Backup Policy: The system must include backup facility of the data based on the weekly
basis that should be checked by the company as well. In addition, backup should be stored in
a server in AML. It will be easier to improve the disaster recovery and business continuity.
Computer use policy: AML should avoid untrusted and external sources programs in their
computer systems. It will be risky for the company as well. Moreover, log file should be
maintained on the computer for identification of issues as well.
Access control policy: Access of the computer hardware and software must be protected from
the outsiders of the company.
manager physical
security
Servers located in a server room
accessible by all staff
Admin Lack of
physical
security
4+3=7
Training and awareness HR manager Lack of
awareness
and
knowledge
5+3=8
All the things should be noticed by the company to manage their network and servers. It will
improve the data and information security of AML. It makes a good relationship between
customers and company as well. Thus, it is necessary to manage all the things in a better
manner (ACSC, 2017). It should be managed in a proper manner for better security as well.
In addition, AML should focus on the suspicious activities in their network as well as
physical security of the system. It will improve their security system. In addition, security
policies must be shared with employees for different types of work for the company as well.
It will be better for the company as well.
Task 2:
It is a basic need to improve the security policies based on the threats and vulnerabilities in
the system. Moreover, there are many changes in the system that can be handle using basic
processes. The company should adopt cybersecurity policies for better outcomes, which
areas:
Backup Policy: The system must include backup facility of the data based on the weekly
basis that should be checked by the company as well. In addition, backup should be stored in
a server in AML. It will be easier to improve the disaster recovery and business continuity.
Computer use policy: AML should avoid untrusted and external sources programs in their
computer systems. It will be risky for the company as well. Moreover, log file should be
maintained on the computer for identification of issues as well.
Access control policy: Access of the computer hardware and software must be protected from
the outsiders of the company.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBERSECURITY 10
Authentication Policy: No one can access the data and information without authentication.
Incident policy: employees should inform about any bad incident in the AML, which is
related to the cybersecurity.
Business continuity policy: all the data backup must be checked every month by IT
department.
Conclusion:
It has concluded that the company should use security policies for managing their services. It
will beneficial for their future as well. Security control must use by the company for
managing their services. It will improve their business processes as well. Finally, security
policies must be used in the company. the company should adopt the international framework
to amend changes in the security policies based on the audit and identification of risk in the
company. finally, AML should consider security policies at the top of the security as it will
help in the security as well. Access control policy must be followed by the staff members for
the security of the system in the future as well.
Authentication Policy: No one can access the data and information without authentication.
Incident policy: employees should inform about any bad incident in the AML, which is
related to the cybersecurity.
Business continuity policy: all the data backup must be checked every month by IT
department.
Conclusion:
It has concluded that the company should use security policies for managing their services. It
will beneficial for their future as well. Security control must use by the company for
managing their services. It will improve their business processes as well. Finally, security
policies must be used in the company. the company should adopt the international framework
to amend changes in the security policies based on the audit and identification of risk in the
company. finally, AML should consider security policies at the top of the security as it will
help in the security as well. Access control policy must be followed by the staff members for
the security of the system in the future as well.

CYBERSECURITY 11
References
ACSC, 2017. A
ustralian Cyber Security Centre. [Online]
Available at: https://www.acsc.gov.au/publications/ACSC_Threat_Report_2017.pdf
[Accessed 12 December 2018].
ACSC, 2019. Strategies to Mitigate Cyber Security Incidents. [Online]
Available at: https://acsc.gov.au/infosec/mitigationstrategies.htm
[Accessed 3 September 2019].
Andrijcic, E. & Horowitz, B., 2016. A Macro‐Economic Framework for Evaluation of Cyber
Security Risks Related to Protection of Intellectual Property. Risk analysis, 26(4), pp. 907-
923.
Arlitsch, K. & Edelman, A., 2014. Staying safe: Cyber security for people and organizations.
Journal of Library Administration, 54(1), pp. 46-56.
Bendovschi, A., 2015. Cyber-attacks–trends, patterns and security countermeasures.
Procedia Economics and Finance, Volume 28, pp. 24-31.
Bhagat, . B. C., 2012. Cloud computing governance, cyber security, risk, and compliance
business rules system and method. U. S., Patent No. 13/016,999.
Caruana, A., 2016. The Six Stages of Incident Response. [Online]
Available at: https://www.csoonline.com/article/3515234/the-six-stages-of-incident-
response.html
[Accessed 15 April 2020].
Datameer, 2018. Challenges to Cyber Security & How Big Data Analytics Can Help.
[Online]
Available at: https://www.datameer.com/blog/challenges-to-cyber-security-and-how-big-
data-analytics-can-help/
[Accessed 3 May 2019].
ITgovernance, 2019. ISO 27005. [Online]
Available at: https://www.itgovernance.co.uk/iso27005
References
ACSC, 2017. A
ustralian Cyber Security Centre. [Online]
Available at: https://www.acsc.gov.au/publications/ACSC_Threat_Report_2017.pdf
[Accessed 12 December 2018].
ACSC, 2019. Strategies to Mitigate Cyber Security Incidents. [Online]
Available at: https://acsc.gov.au/infosec/mitigationstrategies.htm
[Accessed 3 September 2019].
Andrijcic, E. & Horowitz, B., 2016. A Macro‐Economic Framework for Evaluation of Cyber
Security Risks Related to Protection of Intellectual Property. Risk analysis, 26(4), pp. 907-
923.
Arlitsch, K. & Edelman, A., 2014. Staying safe: Cyber security for people and organizations.
Journal of Library Administration, 54(1), pp. 46-56.
Bendovschi, A., 2015. Cyber-attacks–trends, patterns and security countermeasures.
Procedia Economics and Finance, Volume 28, pp. 24-31.
Bhagat, . B. C., 2012. Cloud computing governance, cyber security, risk, and compliance
business rules system and method. U. S., Patent No. 13/016,999.
Caruana, A., 2016. The Six Stages of Incident Response. [Online]
Available at: https://www.csoonline.com/article/3515234/the-six-stages-of-incident-
response.html
[Accessed 15 April 2020].
Datameer, 2018. Challenges to Cyber Security & How Big Data Analytics Can Help.
[Online]
Available at: https://www.datameer.com/blog/challenges-to-cyber-security-and-how-big-
data-analytics-can-help/
[Accessed 3 May 2019].
ITgovernance, 2019. ISO 27005. [Online]
Available at: https://www.itgovernance.co.uk/iso27005
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




