CMP71001: Cybersecurity Risk Assessment Report for BHP Billiton
VerifiedAdded on 2022/09/09
|17
|3222
|10
Report
AI Summary
This report, prepared from the perspective of a cybersecurity consultant at Deloitte Australia, examines the importance of cybersecurity risk assessments, focusing on BHP Billiton as a case study. The report outlines the organization's structure, mission, vision, and business profile, along with identified threats such as data breaches and malware attacks. Task 1 involves a detailed risk assessment, evaluating the probability, impact, and contingency plans for various threats. Task 2 poses critical questions about the organization's assets, ranking them by importance and analyzing associated management challenges. Task 3 identifies top threats like data loss, software vulnerabilities, and human resource risks, supported by relevant literature. Finally, Task 4 assesses the impact of these threats, ranking them by severity. The report concludes with recommendations to improve cybersecurity posture, emphasizing the critical need for comprehensive risk assessment to protect organizational assets and ensure business continuity.

Running head: IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
Importance of cybersecurity risk assessments
Enter: Name of the Student:
Enter: Name of the University:
Enter: Author Note:
Importance of cybersecurity risk assessments
Enter: Name of the Student:
Enter: Name of the University:
Enter: Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
Table of Contents
1. Introduction............................................................................................................................2
1.1 Organization structure......................................................................................................2
1.2 Organization mission.......................................................................................................2
1.3 Organization vision..........................................................................................................2
1.4 Business profile................................................................................................................3
1.5 Threats..............................................................................................................................3
2. Task 1: Risk assessment.........................................................................................................3
2.1 Performing risks assessment............................................................................................3
2.2 Application of risk management results...........................................................................4
2.3 Limitations of current risk assessment methods..............................................................4
3. Task 2: Creation of five questions.........................................................................................5
3.1 Ranking of the assets........................................................................................................0
4. Task 3: Identification of threats.............................................................................................0
4.1 Supporting evidence.........................................................................................................1
5. Task 4: Impact of the threats..................................................................................................2
6. Recommendations..................................................................................................................4
7. Conclusions............................................................................................................................4
8. References..............................................................................................................................6
Table of Contents
1. Introduction............................................................................................................................2
1.1 Organization structure......................................................................................................2
1.2 Organization mission.......................................................................................................2
1.3 Organization vision..........................................................................................................2
1.4 Business profile................................................................................................................3
1.5 Threats..............................................................................................................................3
2. Task 1: Risk assessment.........................................................................................................3
2.1 Performing risks assessment............................................................................................3
2.2 Application of risk management results...........................................................................4
2.3 Limitations of current risk assessment methods..............................................................4
3. Task 2: Creation of five questions.........................................................................................5
3.1 Ranking of the assets........................................................................................................0
4. Task 3: Identification of threats.............................................................................................0
4.1 Supporting evidence.........................................................................................................1
5. Task 4: Impact of the threats..................................................................................................2
6. Recommendations..................................................................................................................4
7. Conclusions............................................................................................................................4
8. References..............................................................................................................................6

2IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
1. Introduction
Cyber security program can be defined as the framework which can be very much
useful to address the risks coming from the cyber security threats such as ransomware and
phishing emails. This report shall be presented from the perspective of a cyber-security
consultant who works in Deloitte Australia. This is one of the big four consultancy firms
who works work different business organizations such as an SME, an educational institution,
and government organizations.
The notable determination of this report is to focus on the cyber security risk
assessment for BHP Bill which is one of the most reputed natural resource company which
was established in the year 2001.
1.1 Organization structure
There are two parenting organizations who works on a collaboration to form this
SME. There is a unified board and management who works dedicatedly in this organization.
1.2 Organization mission
The prime mission of this SME is to have best capabilities, best commodities, and
best assets to create higher returns and long terms value (Deloitte Australia. 2019). Having
stable and predictable operations are also considered among the mission of this organization.
1.3 Organization vision
Maximization of value as well as the returns are the notable vision of this organization
as it can help them to improve the efficiency and productivity of the resources working in this
business.
1. Introduction
Cyber security program can be defined as the framework which can be very much
useful to address the risks coming from the cyber security threats such as ransomware and
phishing emails. This report shall be presented from the perspective of a cyber-security
consultant who works in Deloitte Australia. This is one of the big four consultancy firms
who works work different business organizations such as an SME, an educational institution,
and government organizations.
The notable determination of this report is to focus on the cyber security risk
assessment for BHP Bill which is one of the most reputed natural resource company which
was established in the year 2001.
1.1 Organization structure
There are two parenting organizations who works on a collaboration to form this
SME. There is a unified board and management who works dedicatedly in this organization.
1.2 Organization mission
The prime mission of this SME is to have best capabilities, best commodities, and
best assets to create higher returns and long terms value (Deloitte Australia. 2019). Having
stable and predictable operations are also considered among the mission of this organization.
1.3 Organization vision
Maximization of value as well as the returns are the notable vision of this organization
as it can help them to improve the efficiency and productivity of the resources working in this
business.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
1.4 Business profile
The balance sheet of this business is very much on the higher side, it was about $17B
at the end of the financial year 2017. Huge investments are done by this organization every
year to optimize the existing operations (DiMase et al. 2015). Portfolio development is one of
the prime ways used by this organization to keep a track of business reputation of this
organization.
1.5 Threats
The diverse categories of threats associated with this organization are data breach,
data security issues of the data stored in cloud servers, malware attacks, ethical hacking and
insecure APIs.
2. Task 1: Risk assessment
The productivity and the growth of this commercial organization depends hugely on
the data protection procedures which are adopted by this organization as there are diverse
categories of threats coming from both inside and outside the business environment. Risk
assessment procedure is one of the most significant business process which are deployed in
this business for the identification of risks (Frésard and Valta 2016). The vulnerabilities in the
organizational networks and the networks which are deployed among the subsidiary
organization and the third party vendors can be identified in the first place using the risk
management plan. Contingency of each of the identified risks can be formulated with the help
of the risk assessment plan.
1.4 Business profile
The balance sheet of this business is very much on the higher side, it was about $17B
at the end of the financial year 2017. Huge investments are done by this organization every
year to optimize the existing operations (DiMase et al. 2015). Portfolio development is one of
the prime ways used by this organization to keep a track of business reputation of this
organization.
1.5 Threats
The diverse categories of threats associated with this organization are data breach,
data security issues of the data stored in cloud servers, malware attacks, ethical hacking and
insecure APIs.
2. Task 1: Risk assessment
The productivity and the growth of this commercial organization depends hugely on
the data protection procedures which are adopted by this organization as there are diverse
categories of threats coming from both inside and outside the business environment. Risk
assessment procedure is one of the most significant business process which are deployed in
this business for the identification of risks (Frésard and Valta 2016). The vulnerabilities in the
organizational networks and the networks which are deployed among the subsidiary
organization and the third party vendors can be identified in the first place using the risk
management plan. Contingency of each of the identified risks can be formulated with the help
of the risk assessment plan.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
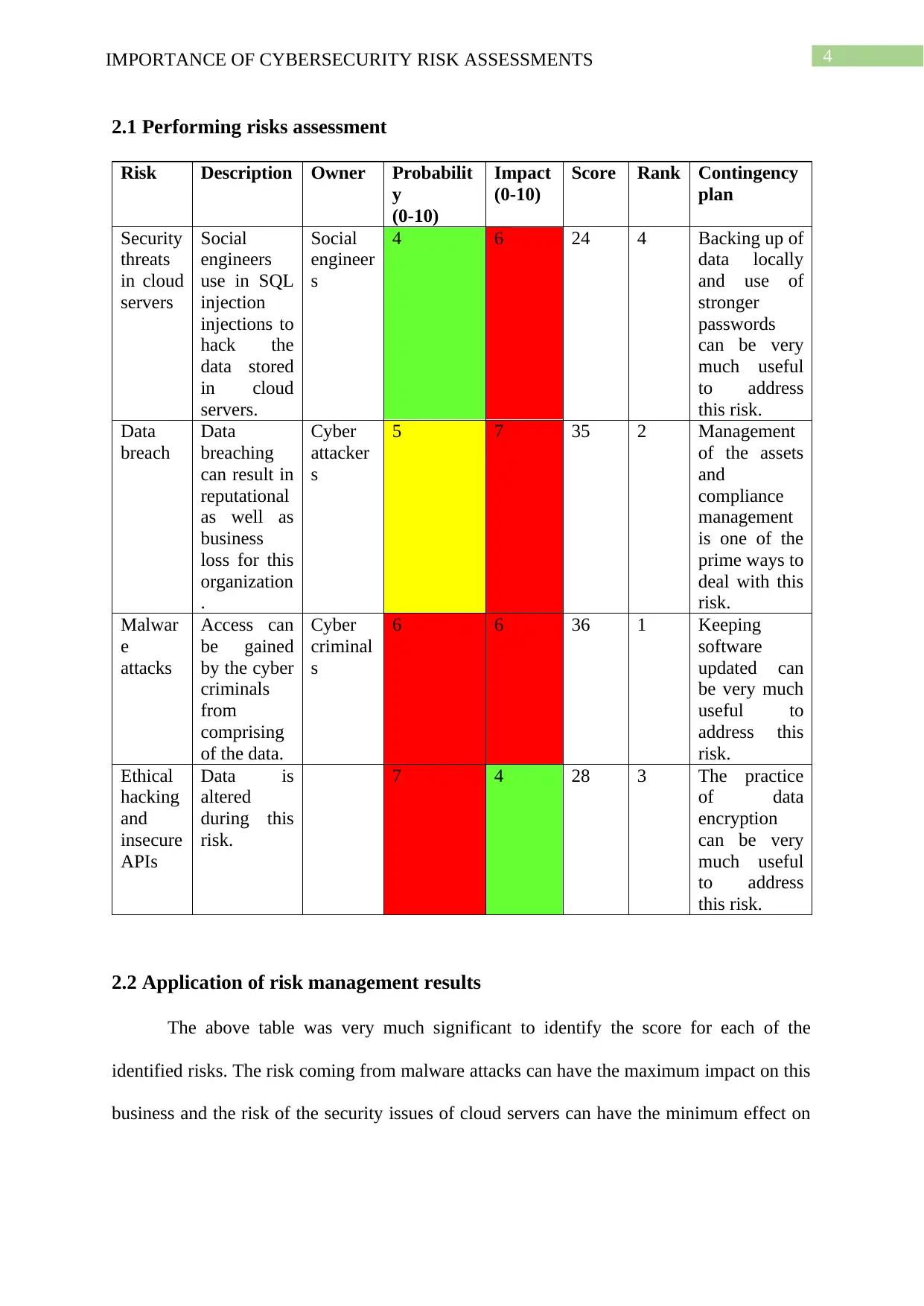
4IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
2.1 Performing risks assessment
Risk Description Owner Probabilit
y
(0-10)
Impact
(0-10)
Score Rank Contingency
plan
Security
threats
in cloud
servers
Social
engineers
use in SQL
injection
injections to
hack the
data stored
in cloud
servers.
Social
engineer
s
4 6 24 4 Backing up of
data locally
and use of
stronger
passwords
can be very
much useful
to address
this risk.
Data
breach
Data
breaching
can result in
reputational
as well as
business
loss for this
organization
.
Cyber
attacker
s
5 7 35 2 Management
of the assets
and
compliance
management
is one of the
prime ways to
deal with this
risk.
Malwar
e
attacks
Access can
be gained
by the cyber
criminals
from
comprising
of the data.
Cyber
criminal
s
6 6 36 1 Keeping
software
updated can
be very much
useful to
address this
risk.
Ethical
hacking
and
insecure
APIs
Data is
altered
during this
risk.
7 4 28 3 The practice
of data
encryption
can be very
much useful
to address
this risk.
2.2 Application of risk management results
The above table was very much significant to identify the score for each of the
identified risks. The risk coming from malware attacks can have the maximum impact on this
business and the risk of the security issues of cloud servers can have the minimum effect on
2.1 Performing risks assessment
Risk Description Owner Probabilit
y
(0-10)
Impact
(0-10)
Score Rank Contingency
plan
Security
threats
in cloud
servers
Social
engineers
use in SQL
injection
injections to
hack the
data stored
in cloud
servers.
Social
engineer
s
4 6 24 4 Backing up of
data locally
and use of
stronger
passwords
can be very
much useful
to address
this risk.
Data
breach
Data
breaching
can result in
reputational
as well as
business
loss for this
organization
.
Cyber
attacker
s
5 7 35 2 Management
of the assets
and
compliance
management
is one of the
prime ways to
deal with this
risk.
Malwar
e
attacks
Access can
be gained
by the cyber
criminals
from
comprising
of the data.
Cyber
criminal
s
6 6 36 1 Keeping
software
updated can
be very much
useful to
address this
risk.
Ethical
hacking
and
insecure
APIs
Data is
altered
during this
risk.
7 4 28 3 The practice
of data
encryption
can be very
much useful
to address
this risk.
2.2 Application of risk management results
The above table was very much significant to identify the score for each of the
identified risks. The risk coming from malware attacks can have the maximum impact on this
business and the risk of the security issues of cloud servers can have the minimum effect on

5IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
this business. The risks coming from data breaches and malware attacks are the risks having
low scores.
2.3 Limitations of current risk assessment methods
The current risk assessments method which is used in this organization are the
management of the assets and compliance (Henshel et al. 2015). Keeping the software
updated is the other decisive step which is taken by this organization to deal with the two
major risks in their business environment.
Risk assessment methods Limitations
Asset management Under maintenance is one of the prime limitations of this
risk assessment method.
Compliance management Improper organizational policy of this organization is the
main limitation of this risk assessment method.
Keeping the software updated New bugs arises when a software is frequently updated
Table 1: Limitations of the risk assessment
(Source: Created by author)
3. Task 2: Creation of five questions
What are the facts of this organization?
The most significant assets of this business can be classified into two categories such
as the intangible assets and the tangible assets (Huang et al. 2017). The intangible is the data
which are circulated widely across each department and the tangible assets are the physical
goods present in the business environment such as the computer systems and server.
What are the issues in managing the organizational assets?
Aligning the risk mitigation strategies with the business process is one of the notable
challenge for the management team of this business to secure the organizational assets.
this business. The risks coming from data breaches and malware attacks are the risks having
low scores.
2.3 Limitations of current risk assessment methods
The current risk assessments method which is used in this organization are the
management of the assets and compliance (Henshel et al. 2015). Keeping the software
updated is the other decisive step which is taken by this organization to deal with the two
major risks in their business environment.
Risk assessment methods Limitations
Asset management Under maintenance is one of the prime limitations of this
risk assessment method.
Compliance management Improper organizational policy of this organization is the
main limitation of this risk assessment method.
Keeping the software updated New bugs arises when a software is frequently updated
Table 1: Limitations of the risk assessment
(Source: Created by author)
3. Task 2: Creation of five questions
What are the facts of this organization?
The most significant assets of this business can be classified into two categories such
as the intangible assets and the tangible assets (Huang et al. 2017). The intangible is the data
which are circulated widely across each department and the tangible assets are the physical
goods present in the business environment such as the computer systems and server.
What are the issues in managing the organizational assets?
Aligning the risk mitigation strategies with the business process is one of the notable
challenge for the management team of this business to secure the organizational assets.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
How is organizational growth achieved?
Organizational growth of this business can maintained with the help of the
management of the organizational assets.
What are the critical assets of this organization?
The most critical assets of this organization is the corporate financial data, proprietary
software, information about the human resources, schematics and sales information.
How is organizational growth achieved?
Organizational growth of this business can maintained with the help of the
management of the organizational assets.
What are the critical assets of this organization?
The most critical assets of this organization is the corporate financial data, proprietary
software, information about the human resources, schematics and sales information.
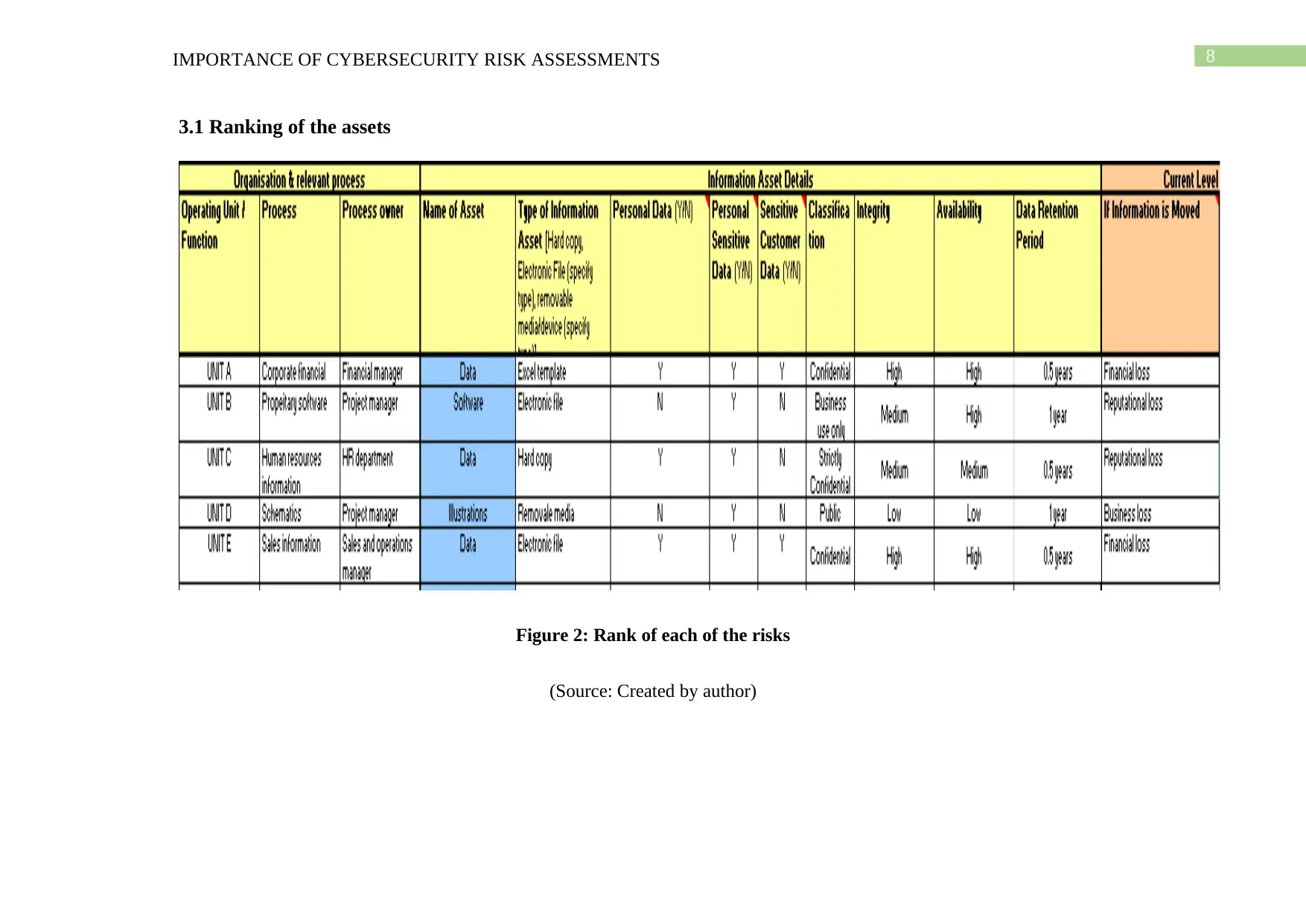
8IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
3.1 Ranking of the assets
Figure 2: Rank of each of the risks
(Source: Created by author)
3.1 Ranking of the assets
Figure 2: Rank of each of the risks
(Source: Created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
Based on the above template it can be said that the management of the corporate
financial data is one of the prime asset associated with this business. After this asset,
proprietary software is the other asset of this business, management of the human resource
information is the following asset associated with this business, management of the
schematics is also one of the other assets of this business. The assets which have the
minimum impact on this business is the management of the sales information (Johnson et al.
2016). The personal data associated with each of the organizational can also be understood
from the following table. The integrity and the availability of each of the assets can also be
understood from the above template. The data retention period of the corporate financial data,
human resource information and sales information is 0.5 years and for proprietary software
and schematics are 1 years. Compromise of corporate financial data and sales information
may result in financial loss, compromise in proprietary software, human resource information
can result in reputational loss and compromise of the schematics may result in business loss
for the organization.
4. Task 3: Identification of threats
This unit of the report shall be identifying the top five threats associated with the
organization assets.
Threats of corporate financial data: Data loss and business disruption are the most
significant threats associated with the corporate financial data which are circulated across
each department of this business organization (Loebbecke and Picot 2015). Employee
training and disaster recovery is a required to address these threats
Threats of proprietary software: Management of the open source components of the
software is one of the most significant threats associated with the software used in this
Based on the above template it can be said that the management of the corporate
financial data is one of the prime asset associated with this business. After this asset,
proprietary software is the other asset of this business, management of the human resource
information is the following asset associated with this business, management of the
schematics is also one of the other assets of this business. The assets which have the
minimum impact on this business is the management of the sales information (Johnson et al.
2016). The personal data associated with each of the organizational can also be understood
from the following table. The integrity and the availability of each of the assets can also be
understood from the above template. The data retention period of the corporate financial data,
human resource information and sales information is 0.5 years and for proprietary software
and schematics are 1 years. Compromise of corporate financial data and sales information
may result in financial loss, compromise in proprietary software, human resource information
can result in reputational loss and compromise of the schematics may result in business loss
for the organization.
4. Task 3: Identification of threats
This unit of the report shall be identifying the top five threats associated with the
organization assets.
Threats of corporate financial data: Data loss and business disruption are the most
significant threats associated with the corporate financial data which are circulated across
each department of this business organization (Loebbecke and Picot 2015). Employee
training and disaster recovery is a required to address these threats
Threats of proprietary software: Management of the open source components of the
software is one of the most significant threats associated with the software used in this
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
business. The licensing software which are used in this business (Ramezani and Camarinha-
Matos 2019). There are other security issues related with this software as well.
Threats of human resource information: There are numerous risks associated with
this threat are the employee engagement and managing the benefits. Each of these two threats
can have a disastrous impact on the growth and productivity of this business organization.
Threats of schematics: The cyber security threats like ransomware have the
maximum impact on this business as the entire flow of operations depends upon how these
security threats are addressed.
Threats of sales information: Human errors and lack of customer journey alignment
are the prime threats associated with the sales information of this business (Sadgrove 2016).
The recruitment of the skilled resources based upon their work experience can be very much
useful to address this threat.
4.1 Supporting evidence
According to Sagara and Das (2020), threats to the organizational assets must be
identified in the first place to maintain the organizational growth. The journal focused on the
protection of both the tangible and the intangible assets of a SME in a detailed manner. The
paper highlighted that employee training is very much beneficial to secure the data assets
from the threats like data losses.
However, as deliberated by Sallam (2015), each software component must be tested in
the first place so that there are very less issues associated with the software. The journal
helped in understanding that licenses of the software must be checked before being added in a
business environment. The journal mentioned that the human resource information can be
secured if data encryption method is introduced in this business.
business. The licensing software which are used in this business (Ramezani and Camarinha-
Matos 2019). There are other security issues related with this software as well.
Threats of human resource information: There are numerous risks associated with
this threat are the employee engagement and managing the benefits. Each of these two threats
can have a disastrous impact on the growth and productivity of this business organization.
Threats of schematics: The cyber security threats like ransomware have the
maximum impact on this business as the entire flow of operations depends upon how these
security threats are addressed.
Threats of sales information: Human errors and lack of customer journey alignment
are the prime threats associated with the sales information of this business (Sadgrove 2016).
The recruitment of the skilled resources based upon their work experience can be very much
useful to address this threat.
4.1 Supporting evidence
According to Sagara and Das (2020), threats to the organizational assets must be
identified in the first place to maintain the organizational growth. The journal focused on the
protection of both the tangible and the intangible assets of a SME in a detailed manner. The
paper highlighted that employee training is very much beneficial to secure the data assets
from the threats like data losses.
However, as deliberated by Sallam (2015), each software component must be tested in
the first place so that there are very less issues associated with the software. The journal
helped in understanding that licenses of the software must be checked before being added in a
business environment. The journal mentioned that the human resource information can be
secured if data encryption method is introduced in this business.
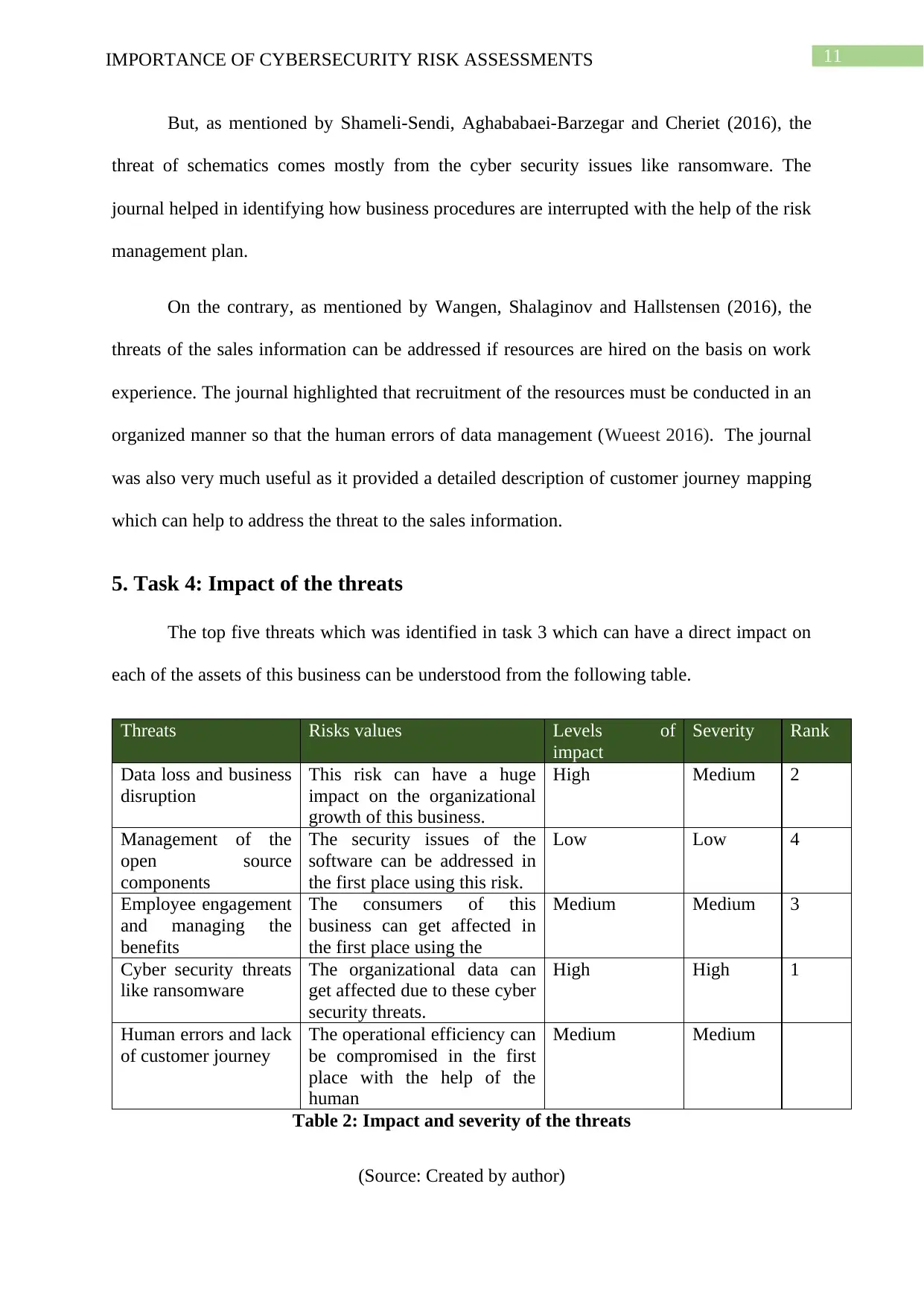
11IMPORTANCE OF CYBERSECURITY RISK ASSESSMENTS
But, as mentioned by Shameli-Sendi, Aghababaei-Barzegar and Cheriet (2016), the
threat of schematics comes mostly from the cyber security issues like ransomware. The
journal helped in identifying how business procedures are interrupted with the help of the risk
management plan.
On the contrary, as mentioned by Wangen, Shalaginov and Hallstensen (2016), the
threats of the sales information can be addressed if resources are hired on the basis on work
experience. The journal highlighted that recruitment of the resources must be conducted in an
organized manner so that the human errors of data management (Wueest 2016). The journal
was also very much useful as it provided a detailed description of customer journey mapping
which can help to address the threat to the sales information.
5. Task 4: Impact of the threats
The top five threats which was identified in task 3 which can have a direct impact on
each of the assets of this business can be understood from the following table.
Threats Risks values Levels of
impact
Severity Rank
Data loss and business
disruption
This risk can have a huge
impact on the organizational
growth of this business.
High Medium 2
Management of the
open source
components
The security issues of the
software can be addressed in
the first place using this risk.
Low Low 4
Employee engagement
and managing the
benefits
The consumers of this
business can get affected in
the first place using the
Medium Medium 3
Cyber security threats
like ransomware
The organizational data can
get affected due to these cyber
security threats.
High High 1
Human errors and lack
of customer journey
The operational efficiency can
be compromised in the first
place with the help of the
human
Medium Medium
Table 2: Impact and severity of the threats
(Source: Created by author)
But, as mentioned by Shameli-Sendi, Aghababaei-Barzegar and Cheriet (2016), the
threat of schematics comes mostly from the cyber security issues like ransomware. The
journal helped in identifying how business procedures are interrupted with the help of the risk
management plan.
On the contrary, as mentioned by Wangen, Shalaginov and Hallstensen (2016), the
threats of the sales information can be addressed if resources are hired on the basis on work
experience. The journal highlighted that recruitment of the resources must be conducted in an
organized manner so that the human errors of data management (Wueest 2016). The journal
was also very much useful as it provided a detailed description of customer journey mapping
which can help to address the threat to the sales information.
5. Task 4: Impact of the threats
The top five threats which was identified in task 3 which can have a direct impact on
each of the assets of this business can be understood from the following table.
Threats Risks values Levels of
impact
Severity Rank
Data loss and business
disruption
This risk can have a huge
impact on the organizational
growth of this business.
High Medium 2
Management of the
open source
components
The security issues of the
software can be addressed in
the first place using this risk.
Low Low 4
Employee engagement
and managing the
benefits
The consumers of this
business can get affected in
the first place using the
Medium Medium 3
Cyber security threats
like ransomware
The organizational data can
get affected due to these cyber
security threats.
High High 1
Human errors and lack
of customer journey
The operational efficiency can
be compromised in the first
place with the help of the
human
Medium Medium
Table 2: Impact and severity of the threats
(Source: Created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





