Cybersecurity Risk Management Plan for MyHealth Company (CMP73001)
VerifiedAdded on 2023/01/17
|1
|339
|66
Report
AI Summary
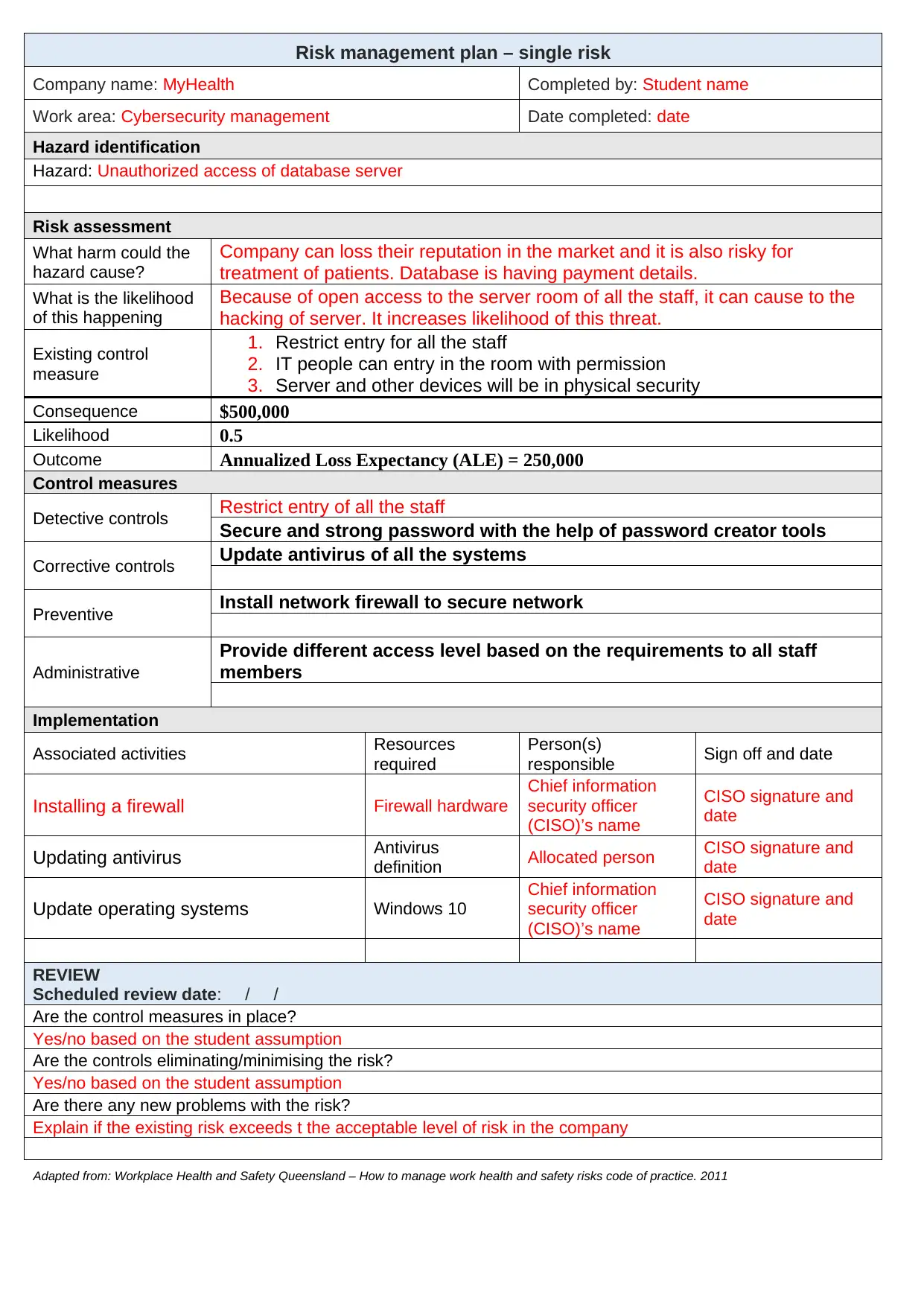
This report presents a cybersecurity risk assessment for MyHealth Company, focusing on the potential threat of unauthorized database access. The assessment identifies the hazard, evaluates the risk based on consequence and likelihood, and proposes control measures. These measures include restricting staff entry, implementing strong passwords, updating antivirus software, installing a network firewall, and providing role-based access levels. The report outlines implementation steps, responsible parties, and review schedules. The assignment, completed by a student, addresses the company's need to protect patient data and payment information, aligning with the assignment brief's requirements for cybersecurity management and risk assessment within the context of the CMP73001 unit at the School of Business and Tourism.






![[object Object]](/_next/static/media/star-bottom.7253800d.svg)