SIT792: Research Proposal on Cyber Security in the Shipping Industry
VerifiedAdded on 2022/10/04
|9
|1431
|233
Project
AI Summary
This research proposal examines the critical cybersecurity threats facing the shipping industry, focusing on malware and ransomware attacks. The study investigates the impact of these threats on business operations, data security, and the global economy. It outlines a research methodology that includes both primary and secondary data collection through surveys and interviews with industry professionals. The proposal addresses key research questions concerning the importance of technology in shipping, the effects of cyberattacks, and potential countermeasures. The research aims to identify vulnerabilities, analyze risks, and propose strategies to mitigate the impact of cyberattacks, ultimately enhancing business processes and improving security within the maritime sector. The proposal also includes a work breakdown structure, ethical considerations, and limitations of the research, ensuring a comprehensive approach to the study.

Running head: Research Proposal
CYBER – SECURITY IN SHIPPING INDUSTRY
Name of the Student:
Name of the University:
Author Note:
CYBER – SECURITY IN SHIPPING INDUSTRY
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2Research Proposal
Abstract
The shipping industry plays an important role in the global economy of a country. In this
competitive market, the shipping industry is facing loss in economy of efficiency and scale. To
overcome such issues the shipping industry started to implement information systems. These
systems provide a greater efficiency and business development for such industry. These systems
need to secured as they holds many sensitive information for an organization and thus they have
many vulnerable threats. Some serious attacks can impact negatively on the organization’s
manufacturing, production and business operation. This research proposal aims on two such
vulnerable threats of cyber - security in the shipping industry. The chosen threats for this report
are ransom ware and malware.
Abstract
The shipping industry plays an important role in the global economy of a country. In this
competitive market, the shipping industry is facing loss in economy of efficiency and scale. To
overcome such issues the shipping industry started to implement information systems. These
systems provide a greater efficiency and business development for such industry. These systems
need to secured as they holds many sensitive information for an organization and thus they have
many vulnerable threats. Some serious attacks can impact negatively on the organization’s
manufacturing, production and business operation. This research proposal aims on two such
vulnerable threats of cyber - security in the shipping industry. The chosen threats for this report
are ransom ware and malware.

3Research Proposal
Table of Contents
Introduction..........................................................................................................................4
Key aims of the research......................................................................................................4
Research Problem................................................................................................................5
Research Questions..............................................................................................................5
Research Methodology........................................................................................................5
Data Collection Method...................................................................................................5
Data Analysis Method.....................................................................................................6
Sample Size.....................................................................................................................6
Ethical Issues...................................................................................................................6
Research Limitations.......................................................................................................7
Work Breakdown Structure.............................................................................................7
References............................................................................................................................8
Table of Contents
Introduction..........................................................................................................................4
Key aims of the research......................................................................................................4
Research Problem................................................................................................................5
Research Questions..............................................................................................................5
Research Methodology........................................................................................................5
Data Collection Method...................................................................................................5
Data Analysis Method.....................................................................................................6
Sample Size.....................................................................................................................6
Ethical Issues...................................................................................................................6
Research Limitations.......................................................................................................7
Work Breakdown Structure.............................................................................................7
References............................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4Research Proposal
Introduction
Malware is a type of attack which deals with malicious program or code used by the
attacker to gain access on the target’s system. These malicious programs or code includes
adware, Trojans, rootkits, bots, bugs, viruses, spyware, viruses and so on. The system gets
blocked and it does not respond to the user’s commands. Ransom ware is the sub – set of
malware where the target’s system is blocked with some malicious code and the target can gain
the access only after paying some ransom. The ransom ware attack is a vulnerable threat to the
shipping industry (Kharraz et al. 2015). All business operations can be put to hold due to these
attacks where the business can face a huge loss. This suspension of the business operation can
lead to many losses for the industry. The basic differences between malware and ransom ware
are as follows:
Ransom ware Malware
It is a form of crypto virology which blocks
all the access to target’s system unless some
ransom is paid to the target.
It is the computer virus that is designed to
copy all the user files.
It is spread by phishing the user emails. It usually piggybacks the malicious links,
social media messages, and fraudulent email
attachments and so on.
Two types of ransom ware are Locker and
Crypto
All malicious attacks can be referred as
malware.
The primary focus of the maritime industry is its security. In this report two vulnerable
threats will be discussed like ransom ware and malware. The report also conveys about how
these attacks can affect the industry and the report will also convey various methods to counter
these attacks (Acciaro and Serra 2013).
Introduction
Malware is a type of attack which deals with malicious program or code used by the
attacker to gain access on the target’s system. These malicious programs or code includes
adware, Trojans, rootkits, bots, bugs, viruses, spyware, viruses and so on. The system gets
blocked and it does not respond to the user’s commands. Ransom ware is the sub – set of
malware where the target’s system is blocked with some malicious code and the target can gain
the access only after paying some ransom. The ransom ware attack is a vulnerable threat to the
shipping industry (Kharraz et al. 2015). All business operations can be put to hold due to these
attacks where the business can face a huge loss. This suspension of the business operation can
lead to many losses for the industry. The basic differences between malware and ransom ware
are as follows:
Ransom ware Malware
It is a form of crypto virology which blocks
all the access to target’s system unless some
ransom is paid to the target.
It is the computer virus that is designed to
copy all the user files.
It is spread by phishing the user emails. It usually piggybacks the malicious links,
social media messages, and fraudulent email
attachments and so on.
Two types of ransom ware are Locker and
Crypto
All malicious attacks can be referred as
malware.
The primary focus of the maritime industry is its security. In this report two vulnerable
threats will be discussed like ransom ware and malware. The report also conveys about how
these attacks can affect the industry and the report will also convey various methods to counter
these attacks (Acciaro and Serra 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5Research Proposal
Key aims of the research
This research aims on the vulnerable effects of ransom ware and malware on the shipping
industry. The research also provides some countermeasures to mitigate the risks. The research
will help the industry to improve their business. It will also help the business with a regular
business growth. The research also aims to involve more clients to their business by enhancing
all the business process.
Research Problem
The maritime industry plays an important role for the global economy of the country.
Information technology is the primary key of this industry and hence the security of these
information systems is the primary motive of the industry (McNicholas 2016). The data transport
process in this industry is very costly and hence the internet connections are kept limited which
also limit the vulnerable risk of the organization. The vulnerable mode of ransom ware or
malware are infection by the physical file transfer, Infection through World Wide Web, viruses,
Trojans and worms. Thus this project will convey all the possible effects of malware and ransom
ware in the shipping industry and also will also provide some countermeasures for the industry to
fight against these attacks (Kraska and Pedrozo 2013).
Research Questions
RQ1. What is the importance of technology in the shipping industry?
RQ2. What are the effects of ransom ware and malware on the shipping industry?
RQ3. What are the countermeasures to mitigate the risks?
Key aims of the research
This research aims on the vulnerable effects of ransom ware and malware on the shipping
industry. The research also provides some countermeasures to mitigate the risks. The research
will help the industry to improve their business. It will also help the business with a regular
business growth. The research also aims to involve more clients to their business by enhancing
all the business process.
Research Problem
The maritime industry plays an important role for the global economy of the country.
Information technology is the primary key of this industry and hence the security of these
information systems is the primary motive of the industry (McNicholas 2016). The data transport
process in this industry is very costly and hence the internet connections are kept limited which
also limit the vulnerable risk of the organization. The vulnerable mode of ransom ware or
malware are infection by the physical file transfer, Infection through World Wide Web, viruses,
Trojans and worms. Thus this project will convey all the possible effects of malware and ransom
ware in the shipping industry and also will also provide some countermeasures for the industry to
fight against these attacks (Kraska and Pedrozo 2013).
Research Questions
RQ1. What is the importance of technology in the shipping industry?
RQ2. What are the effects of ransom ware and malware on the shipping industry?
RQ3. What are the countermeasures to mitigate the risks?

6Research Proposal
Research Methodology
Data Collection Method
The data will be collected from both primary as well as secondary sources. A survey will
be conducted where all the employees and clients will provide their views regarding the possible
effects of the ransom ware and malware on the shipping industry. Interviews will also conducted
where all the Board of Directors will meet and provide their feedback regarding the security
issues in their respective organization. Many online documents will be researched before
implementing the project (Johnston 2017).
Data Analysis Method
All the information gathered from the survey will be transferred into some percentage
traits which will help to get a comparable and comprehensible data. Those converted data will be
presented in graphs or charts which will help the audience to know the importance of the security
in the shipping industry. The Secondary data will be analyzed by means of some debates,
personal interview and group discussions (Coakley 2013).
Sample Size
It is expected that over 500+ employees and clients will participate in the survey process
and 250+ Board of Directors will participate in the personal interview process. This will assist
the research to be more accurate regarding the harmful impacts and the countermeasures of
ransom ware and malware in the shipping industry.
Ethical Issues
The research will be conducted keeping all the ethical guidelines in mind. When the
primary data will be collected nobody should be forced to take participation in the survey
Research Methodology
Data Collection Method
The data will be collected from both primary as well as secondary sources. A survey will
be conducted where all the employees and clients will provide their views regarding the possible
effects of the ransom ware and malware on the shipping industry. Interviews will also conducted
where all the Board of Directors will meet and provide their feedback regarding the security
issues in their respective organization. Many online documents will be researched before
implementing the project (Johnston 2017).
Data Analysis Method
All the information gathered from the survey will be transferred into some percentage
traits which will help to get a comparable and comprehensible data. Those converted data will be
presented in graphs or charts which will help the audience to know the importance of the security
in the shipping industry. The Secondary data will be analyzed by means of some debates,
personal interview and group discussions (Coakley 2013).
Sample Size
It is expected that over 500+ employees and clients will participate in the survey process
and 250+ Board of Directors will participate in the personal interview process. This will assist
the research to be more accurate regarding the harmful impacts and the countermeasures of
ransom ware and malware in the shipping industry.
Ethical Issues
The research will be conducted keeping all the ethical guidelines in mind. When the
primary data will be collected nobody should be forced to take participation in the survey
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7Research Proposal
process, this will examined when the candidates will sign a form which will guarantee that the
participants are participating the survey process without any force (Rivers and Lewis 2014). The
gathered secondary data should be plagiarism free and should be analyzed carefully. Thus, in this
way the research obey all the rules and regulation of the ethical guidelines.
Research Limitations
The time – work structure of the project is too early for describing the paper. Getting the
appointments of the Board of Directors will be huge problem for this research. The budget of this
research can be another issue of the project. The main motive is to complete the whole project
within the estimated cost. Thus, some security money should be conserved in case if the overall
cost exceeds the estimated cost of the project (Shipman 2014).
process, this will examined when the candidates will sign a form which will guarantee that the
participants are participating the survey process without any force (Rivers and Lewis 2014). The
gathered secondary data should be plagiarism free and should be analyzed carefully. Thus, in this
way the research obey all the rules and regulation of the ethical guidelines.
Research Limitations
The time – work structure of the project is too early for describing the paper. Getting the
appointments of the Board of Directors will be huge problem for this research. The budget of this
research can be another issue of the project. The main motive is to complete the whole project
within the estimated cost. Thus, some security money should be conserved in case if the overall
cost exceeds the estimated cost of the project (Shipman 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
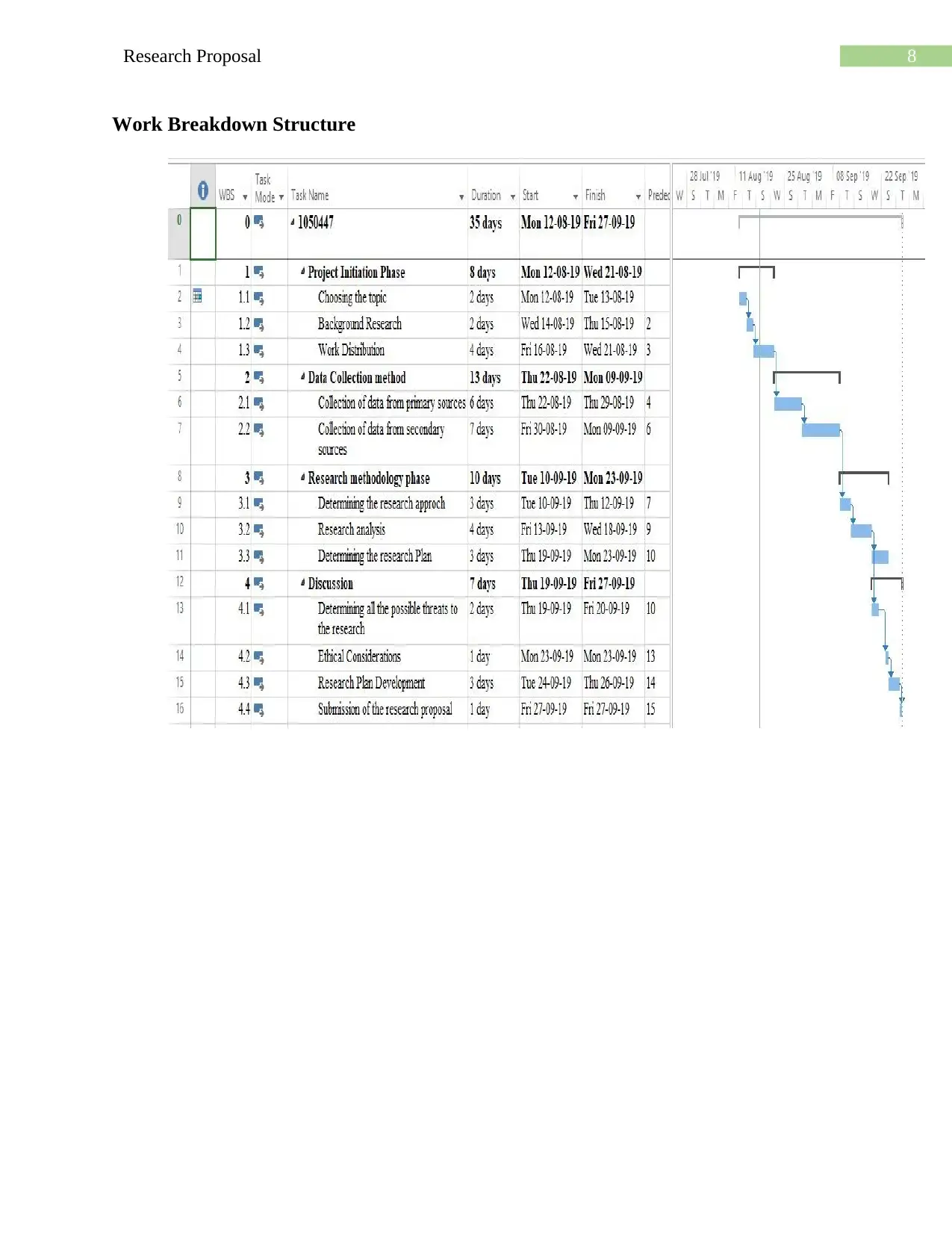
8Research Proposal
Work Breakdown Structure
Work Breakdown Structure

9Research Proposal
References
Acciaro, M. and Serra, P., 2013, August. Maritime supply chain security: a critical review. In
Proceedings of the International Forum on Shipping, Ports and Airports (IFSPA) (pp. 636-651).
Coakley, T.M., 2013. The influence of father involvement on child welfare permanency
outcomes: A secondary data analysis. Children and Youth Services Review, 35(1), pp.174-182.
Johnston, M.P., 2017. Secondary data analysis: A method of which the time has come.
Qualitative and quantitative methods in libraries, 3(3), pp.619-626.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L. and Kirda, E., 2015, July. Cutting the
gordian knot: A look under the hood of ransomware attacks. In International Conference on
Detection of Intrusions and Malware, and Vulnerability Assessment (pp. 3-24). Springer, Cham.
Kraska, J. and Pedrozo, R., 2013. International maritime security law. Martinus Nijhoff
Publishers.
McNicholas, M., 2016. Maritime security: an introduction. Butterworth-Heinemann.
Rivers, C.M. and Lewis, B.L., 2014. Ethical research standards in a world of big data.
F1000Research, 3.
Shipman, M.D., 2014. The limitations of social research. Routledge.
References
Acciaro, M. and Serra, P., 2013, August. Maritime supply chain security: a critical review. In
Proceedings of the International Forum on Shipping, Ports and Airports (IFSPA) (pp. 636-651).
Coakley, T.M., 2013. The influence of father involvement on child welfare permanency
outcomes: A secondary data analysis. Children and Youth Services Review, 35(1), pp.174-182.
Johnston, M.P., 2017. Secondary data analysis: A method of which the time has come.
Qualitative and quantitative methods in libraries, 3(3), pp.619-626.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L. and Kirda, E., 2015, July. Cutting the
gordian knot: A look under the hood of ransomware attacks. In International Conference on
Detection of Intrusions and Malware, and Vulnerability Assessment (pp. 3-24). Springer, Cham.
Kraska, J. and Pedrozo, R., 2013. International maritime security law. Martinus Nijhoff
Publishers.
McNicholas, M., 2016. Maritime security: an introduction. Butterworth-Heinemann.
Rivers, C.M. and Lewis, B.L., 2014. Ethical research standards in a world of big data.
F1000Research, 3.
Shipman, M.D., 2014. The limitations of social research. Routledge.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





