Brunel University CS3609 Cybersecurity Coursework: Task 1 Analysis
VerifiedAdded on 2022/09/10
|7
|1604
|31
Homework Assignment
AI Summary
This document presents a comprehensive cybersecurity solution for a CS3609 assignment, focusing on the hypothetical Brunel Tech Startup. The solution begins with a detailed system architecture diagram and a narrative description of the IT environment, including nodes, networks, and applications. It identifies potential risks within the network, devices, and applications, such as ransomware, malware, and hacking. A risk model is then developed using a recognized cybersecurity risk modeling technique, linking identified risks to specific countermeasures. The document further describes three essential cybersecurity tools: Intrusion Detection and Prevention Systems (IDS/IPS), anti-malware software, and next-generation firewalls, explaining their role in mitigating risks. The assignment adheres to the provided coursework template and includes a bibliography in Harvard format, referencing relevant cybersecurity literature. The document highlights proactive measures such as employee education, software configuration, and the use of advanced security technologies to safeguard the organization's data and network infrastructure.

CS3609 CYBERSECURITY COURSEWORK TEMPLATE
STUDENT NUMBER:______________________
SYSTEM ARCHITECTURE DIAGRAM ( 1 PAGE ):
A diagram depicting the environment (nodes, networks, applications)
SYSTEM ARCHITECTURE DESCRIPTION ( UP TO 2 PAGES ):
A narrative analysis of the environment that covers nodes, networks, and applications.
STUDENT NUMBER:______________________
SYSTEM ARCHITECTURE DIAGRAM ( 1 PAGE ):
A diagram depicting the environment (nodes, networks, applications)
SYSTEM ARCHITECTURE DESCRIPTION ( UP TO 2 PAGES ):
A narrative analysis of the environment that covers nodes, networks, and applications.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This must include the articulation of the elements of the office network, identifying possible
risks in the network, devices, and applications (and any assumption made).
Setting up the new office requires a complete Information Technology (IT)
infrastructural setup. In the case of Brunel tech startup, different IT infrastructure would be
required for effective operations. Brunel tech startup would require laptops to be used by
employees while in the office. The laptops should be connected to the office network to
access operational data from an organizational database or from Amazon backup service.
Accessing organizational data requires a secure connection to avoid unauthorized access to
the data. In the work desks, users would be supplied with the network through a WLAN
router. All laptops would be assigned a static Internet Protocol (IP) address to make it
possible to tracker all incoming and outgoing signals in the firewall. Considering
employees would be required to access organizational data from home and through their
personal laptops and smartphones, it would be important to use secure network
connections. Employees are advised not to connect to the organizational databases from
public networks to avoid eavesdropping.
The meeting room needs to be equipped with modern tools and equipment. The
Brunel tech startup meeting room would be installed with a projector that would be used
for presentations. During training sessions within the organization or from outside the
organizations, employees would be able to showcase their work. Important to note is that
projection during the presentation is one of the aspects that firms are adopting to avoid
manual processes such as whiteboards and paper presentations. In the meeting, a gaming
laptop is installed for presentation when connected with the projector. It has gaming
capability to make it possible to present any form of a graphical interface such as 3D
during demonstration and pieces of training. The room is also installed with a voice-over
device that would be used during conference calls. The voice-over devices are very
risks in the network, devices, and applications (and any assumption made).
Setting up the new office requires a complete Information Technology (IT)
infrastructural setup. In the case of Brunel tech startup, different IT infrastructure would be
required for effective operations. Brunel tech startup would require laptops to be used by
employees while in the office. The laptops should be connected to the office network to
access operational data from an organizational database or from Amazon backup service.
Accessing organizational data requires a secure connection to avoid unauthorized access to
the data. In the work desks, users would be supplied with the network through a WLAN
router. All laptops would be assigned a static Internet Protocol (IP) address to make it
possible to tracker all incoming and outgoing signals in the firewall. Considering
employees would be required to access organizational data from home and through their
personal laptops and smartphones, it would be important to use secure network
connections. Employees are advised not to connect to the organizational databases from
public networks to avoid eavesdropping.
The meeting room needs to be equipped with modern tools and equipment. The
Brunel tech startup meeting room would be installed with a projector that would be used
for presentations. During training sessions within the organization or from outside the
organizations, employees would be able to showcase their work. Important to note is that
projection during the presentation is one of the aspects that firms are adopting to avoid
manual processes such as whiteboards and paper presentations. In the meeting, a gaming
laptop is installed for presentation when connected with the projector. It has gaming
capability to make it possible to present any form of a graphical interface such as 3D
during demonstration and pieces of training. The room is also installed with a voice-over
device that would be used during conference calls. The voice-over devices are very

essential as they are used to conference all stakeholders from different parts of the world.
The machine room is equipped with very sensitive devices such as database and
application server, mail server, network server, and a firewall. A single server would be
used as a database and application server to minimize the cost of IT infrastructure setup. In
this regard, the Linux server in the machine room would host databases and applications.
Organization operational data such as customer and employees’ data would be hosted on
this server. The same Linux server would be used to host applications such as an
organizational website. Some applications hosted in this server would be accessible by
different users from home and each user should be provided with specific access privileges
for security reasons. Employees would be connected to all organizational applications
through a network from the network server. Each user would be assigned an IP address to
the network server to be connected through either Ethernet cable or Wi-Fi. For users to
connect to either the application or database, all requests would be routed to the firewall for
internal security checks. The firewall should be configured to prevent unauthorized users
from accessing organizational data. Notably, Brunel tech startup would require a mail
server which hosts the organization's internal and external mail communications. Each
employee would be provided with an internal mail associated with the Company which
would be the official communication channel either internal or externally. Mails are
commonly used by unauthorized persons to gain access to organizational systems and it is
important to educate employees on responsible. Employees should be sensitive to spam
emails and avoid opening any on their attached documents or links.
With advanced technology, the security of the organizational network and devices
remains an essential aspect. It is important to protect devices, information systems,
The machine room is equipped with very sensitive devices such as database and
application server, mail server, network server, and a firewall. A single server would be
used as a database and application server to minimize the cost of IT infrastructure setup. In
this regard, the Linux server in the machine room would host databases and applications.
Organization operational data such as customer and employees’ data would be hosted on
this server. The same Linux server would be used to host applications such as an
organizational website. Some applications hosted in this server would be accessible by
different users from home and each user should be provided with specific access privileges
for security reasons. Employees would be connected to all organizational applications
through a network from the network server. Each user would be assigned an IP address to
the network server to be connected through either Ethernet cable or Wi-Fi. For users to
connect to either the application or database, all requests would be routed to the firewall for
internal security checks. The firewall should be configured to prevent unauthorized users
from accessing organizational data. Notably, Brunel tech startup would require a mail
server which hosts the organization's internal and external mail communications. Each
employee would be provided with an internal mail associated with the Company which
would be the official communication channel either internal or externally. Mails are
commonly used by unauthorized persons to gain access to organizational systems and it is
important to educate employees on responsible. Employees should be sensitive to spam
emails and avoid opening any on their attached documents or links.
With advanced technology, the security of the organizational network and devices
remains an essential aspect. It is important to protect devices, information systems,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

networks, and databases against external and internal attackers. IT infrastructure security
risks that security administrators should prioritize are hacking which can be done by both
external and internal agents. Hacking has been a major security problem that many
organizations have been trying to address. The next security problem that the cybersecurity
team should consider is Ransomware attackers which are propagated as malware or viruses
hidden in attachments. The malware attacks organizational data or locks their devices
rendering them unusable. The final cybersecurity risk that should be addressed is data
corruption. The database requires special protection to secure it from unauthorized access
and use by third parties. Data protection involves several processes that start from network
protection, and information systems authentication and authorization measures.
RISKS & COUNTERMEASURES: A RISK MODEL ( 1 PAGE ):
A risk model presenting identified risks (in a) using a recognized cybersecurity risk
modeling technique. Clear links to at least three countermeasures should be highlighted.
The risk model would be developed by adopting risk and impact modeling analysis. The
risks that security administrators should prioritize are hacking which can be done by both
external and internal agents. Hacking has been a major security problem that many
organizations have been trying to address. The next security problem that the cybersecurity
team should consider is Ransomware attackers which are propagated as malware or viruses
hidden in attachments. The malware attacks organizational data or locks their devices
rendering them unusable. The final cybersecurity risk that should be addressed is data
corruption. The database requires special protection to secure it from unauthorized access
and use by third parties. Data protection involves several processes that start from network
protection, and information systems authentication and authorization measures.
RISKS & COUNTERMEASURES: A RISK MODEL ( 1 PAGE ):
A risk model presenting identified risks (in a) using a recognized cybersecurity risk
modeling technique. Clear links to at least three countermeasures should be highlighted.
The risk model would be developed by adopting risk and impact modeling analysis. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
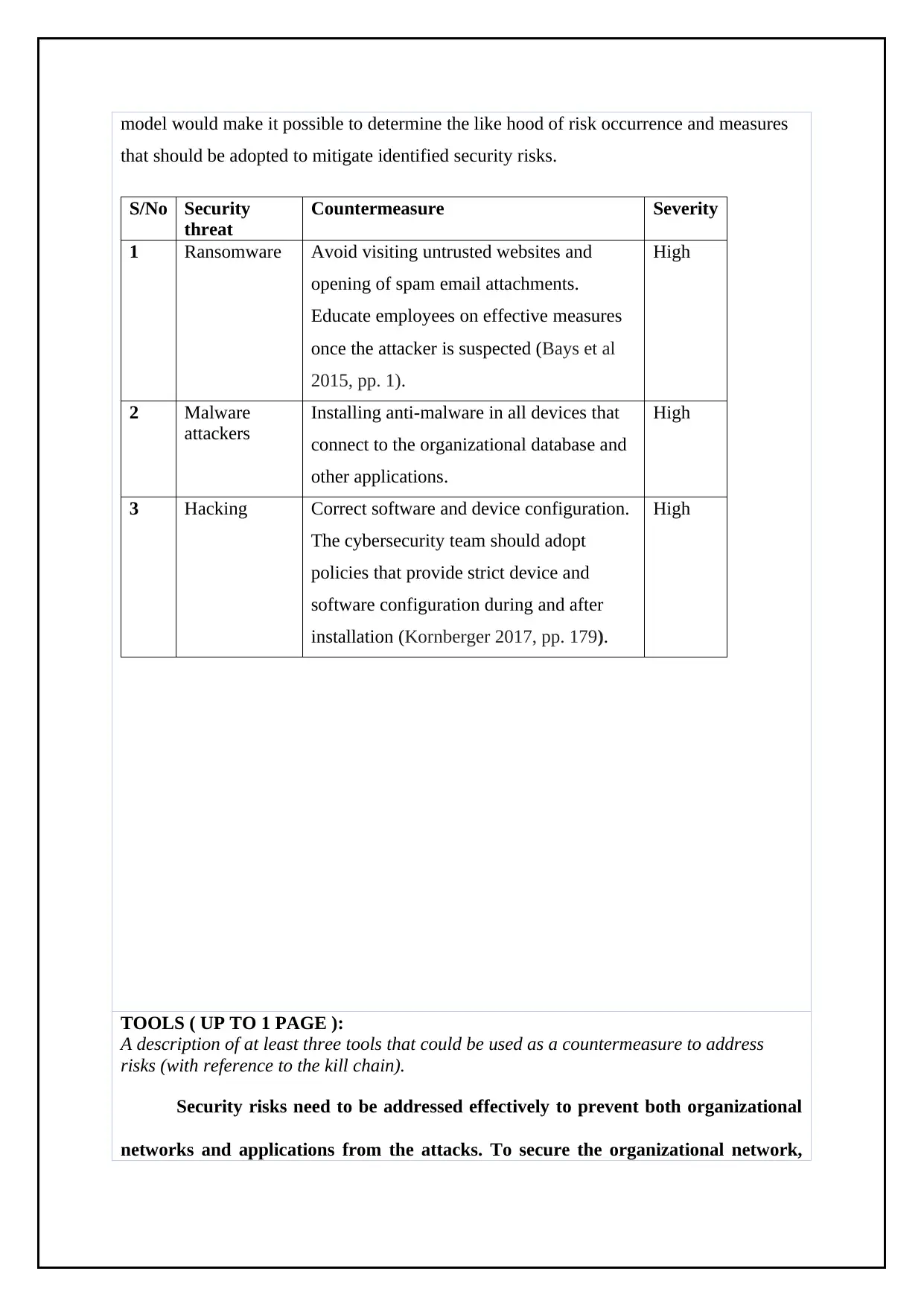
model would make it possible to determine the like hood of risk occurrence and measures
that should be adopted to mitigate identified security risks.
S/No Security
threat
Countermeasure Severity
1 Ransomware Avoid visiting untrusted websites and
opening of spam email attachments.
Educate employees on effective measures
once the attacker is suspected (Bays et al
2015, pp. 1).
High
2 Malware
attackers
Installing anti-malware in all devices that
connect to the organizational database and
other applications.
High
3 Hacking Correct software and device configuration.
The cybersecurity team should adopt
policies that provide strict device and
software configuration during and after
installation (Kornberger 2017, pp. 179).
High
TOOLS ( UP TO 1 PAGE ):
A description of at least three tools that could be used as a countermeasure to address
risks (with reference to the kill chain).
Security risks need to be addressed effectively to prevent both organizational
networks and applications from the attacks. To secure the organizational network,
that should be adopted to mitigate identified security risks.
S/No Security
threat
Countermeasure Severity
1 Ransomware Avoid visiting untrusted websites and
opening of spam email attachments.
Educate employees on effective measures
once the attacker is suspected (Bays et al
2015, pp. 1).
High
2 Malware
attackers
Installing anti-malware in all devices that
connect to the organizational database and
other applications.
High
3 Hacking Correct software and device configuration.
The cybersecurity team should adopt
policies that provide strict device and
software configuration during and after
installation (Kornberger 2017, pp. 179).
High
TOOLS ( UP TO 1 PAGE ):
A description of at least three tools that could be used as a countermeasure to address
risks (with reference to the kill chain).
Security risks need to be addressed effectively to prevent both organizational
networks and applications from the attacks. To secure the organizational network,

Brunel tech cybersecurity team should make use of various tools to prevent risks
from occurring. Some of the tools that can be used to secure the network are
Intrusion detection and prevention system (IDS/IPS). These tools help the
cybersecurity team to both identify and protect wireless and WLAN networks
(Conteh, & Schmick 2016, pp. 31). These tools have the capability to monitor the
network from any suspicious traffic flow and alert the administrator. It is a useful
tool because it can both detect and be used to prevent any unauthorized users from
accessing the network. IDS/IPS have advanced functional capability to detect and
classify any form of the threat posed into the network. The next tool that Brunel tech
startup security need is anti-malware which would be used to protect data from
damage by viruses and malware. Anti-malware tools are used to identify and remove
malware in devices such as computers and smartphones (Maglaras et al 2018, pp. 1).
It is highly recommended that any device connecting to organizational data have anti-
malware already installed. With the help of anti-malware, IT administrators are able
to adjust security policies to identify malware types and their sources. The
cybersecurity team in the organization should consider using next-generation
firewalls to filter all incoming and outgoing signals. The technology integrated into
this type of firewall is based on stateful data inspection to provide advanced network
protection measures (Shafqat, & Masood 2016, pp. 129). Some of the security
measures provided by the next-generation firewalls include web security scanning
and access controls.
BIBLIOGRAPHY ( UP TO 1 PAGE ):
Harvard format
from occurring. Some of the tools that can be used to secure the network are
Intrusion detection and prevention system (IDS/IPS). These tools help the
cybersecurity team to both identify and protect wireless and WLAN networks
(Conteh, & Schmick 2016, pp. 31). These tools have the capability to monitor the
network from any suspicious traffic flow and alert the administrator. It is a useful
tool because it can both detect and be used to prevent any unauthorized users from
accessing the network. IDS/IPS have advanced functional capability to detect and
classify any form of the threat posed into the network. The next tool that Brunel tech
startup security need is anti-malware which would be used to protect data from
damage by viruses and malware. Anti-malware tools are used to identify and remove
malware in devices such as computers and smartphones (Maglaras et al 2018, pp. 1).
It is highly recommended that any device connecting to organizational data have anti-
malware already installed. With the help of anti-malware, IT administrators are able
to adjust security policies to identify malware types and their sources. The
cybersecurity team in the organization should consider using next-generation
firewalls to filter all incoming and outgoing signals. The technology integrated into
this type of firewall is based on stateful data inspection to provide advanced network
protection measures (Shafqat, & Masood 2016, pp. 129). Some of the security
measures provided by the next-generation firewalls include web security scanning
and access controls.
BIBLIOGRAPHY ( UP TO 1 PAGE ):
Harvard format
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Bays, L.R., Oliveira, R.R., Barcellos, M.P., Gaspary, L.P. and Madeira, E.R.M., 2015.
Virtual network security: threats, countermeasures, and challenges. Journal of
Internet Services and Applications, 6(1), p.1.
Conteh, N.Y. and Schmick, P.J., 2016. Cybersecurity: risks, vulnerabilities, and
countermeasures to prevent social engineering attacks. International Journal of
Advanced Computer Research, 6(23), p.31.
Kornberger, M., 2017. The visible hand and the crowd: Analyzing organization
design in distributed innovation systems. Strategic Organization, 15(2), pp.174-193.
Maglaras, L.A., Ferrag, M.A., Derhab, A., Mukherjee, M., Janicke, H. and Rallis, S.,
2018. Threats, Countermeasures, and Attribution of Cyber Attacks on Critical
Infrastructures. ICST Trans. Security Safety, 5(16), p.1.
Shafqat, N. and Masood, A., 2016. Comparative analysis of various national
cybersecurity strategies. International Journal of Computer Science and Information
Security, 14(1), p.129.
Virtual network security: threats, countermeasures, and challenges. Journal of
Internet Services and Applications, 6(1), p.1.
Conteh, N.Y. and Schmick, P.J., 2016. Cybersecurity: risks, vulnerabilities, and
countermeasures to prevent social engineering attacks. International Journal of
Advanced Computer Research, 6(23), p.31.
Kornberger, M., 2017. The visible hand and the crowd: Analyzing organization
design in distributed innovation systems. Strategic Organization, 15(2), pp.174-193.
Maglaras, L.A., Ferrag, M.A., Derhab, A., Mukherjee, M., Janicke, H. and Rallis, S.,
2018. Threats, Countermeasures, and Attribution of Cyber Attacks on Critical
Infrastructures. ICST Trans. Security Safety, 5(16), p.1.
Shafqat, N. and Masood, A., 2016. Comparative analysis of various national
cybersecurity strategies. International Journal of Computer Science and Information
Security, 14(1), p.129.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





