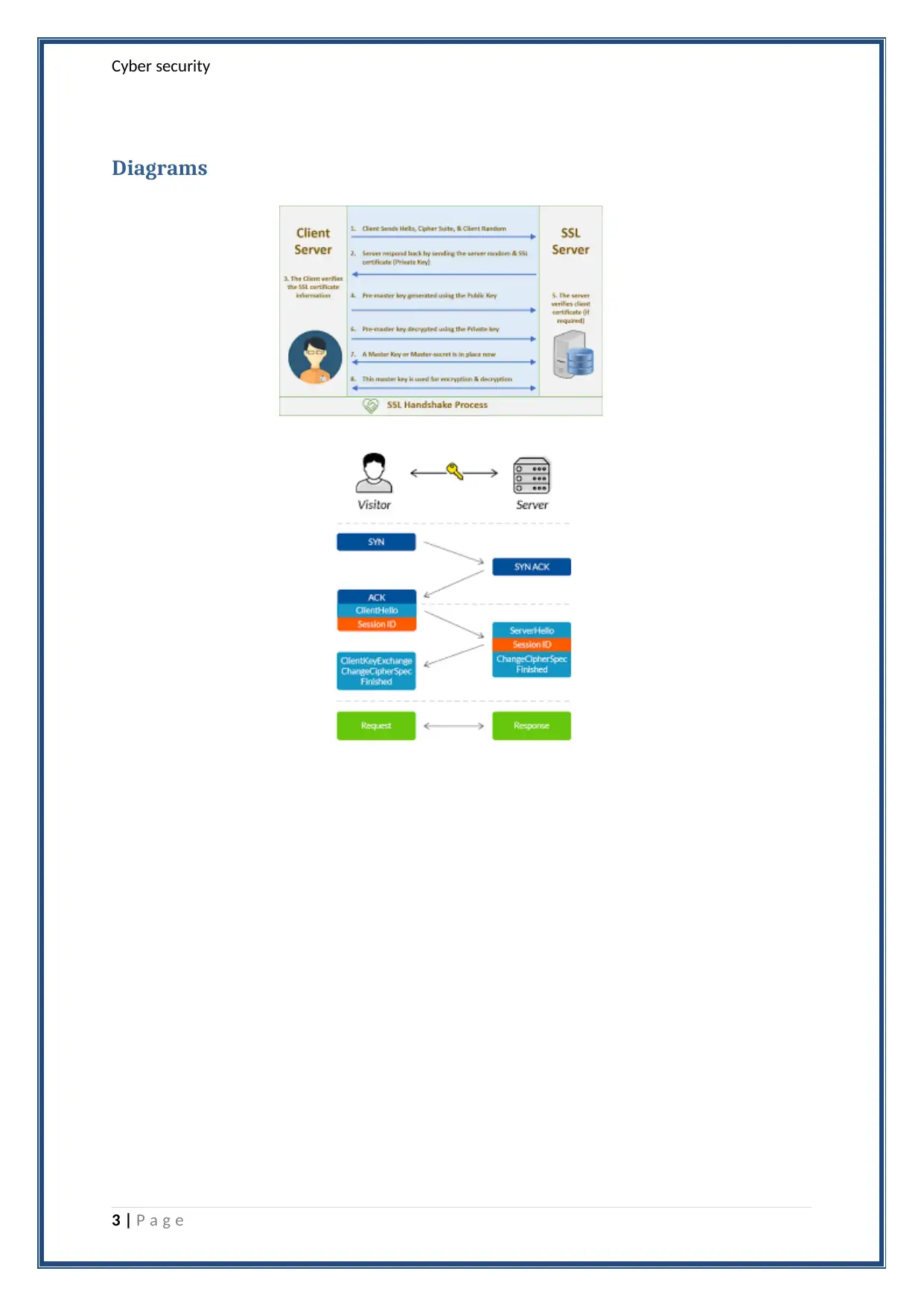
Comprehensive Report: SSL Handshake Protocol in Cybersecurity
VerifiedAdded on 2023/06/07
|5
|774
|344
Report
AI Summary
This report provides a comprehensive analysis of the SSL handshake, a crucial process in cybersecurity for establishing secure communication between a client and a server. The report begins by defining SSL (Secure Sockets Layer) and its role in using public key encryption alongside symmetric keys to ensure secure data transmission. It details the handshake process, which involves authentication, cipher suite negotiation, and secret key generation to create a secure communication path. The report outlines the steps involved, including the client's initial 'hello' message, server certificate exchange, client certificate verification, secret key computation, and data encryption. Diagrams are included to visualize the process. Finally, the report references relevant sources to support the information presented, making it a valuable resource for understanding secure communication protocols in the digital landscape.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)