Cybersecurity Strategies in Training Sessions: Waracle LTD
VerifiedAdded on 2023/06/11
|19
|4721
|296
Project
AI Summary
This research proposal investigates the effectiveness of cybersecurity strategies delivered in training sessions to employees for reducing cybercrimes, focusing on Waracle LTD, UK. It addresses the problem of cybercrime and the need for effective strategies to protect data, maintain customer trust, and enhance business performance. The literature review covers the concept and significance of cybersecurity, specific strategies used in training sessions, and the positive impacts of implementing these strategies on business productivity, customer confidence, and brand reputation. The research aims to determine the strategies' effectiveness, improve academic and professional skills, and provide valuable insights for companies to reduce cybercrimes and improve their cybersecurity posture. The scope includes providing relevant information on the impact and strategies of cybersecurity, highlighting the necessity of adopting these strategies to reduce cybercrimes and eliminate damages.

Research Proposal
(Cybersecurity strategies delivered in training
sessions to employees for reducing rate of
cybercrimes)
(Cybersecurity strategies delivered in training
sessions to employees for reducing rate of
cybercrimes)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
TITLE..............................................................................................................................................3
AIM..................................................................................................................................................3
PROBLEM STATEMENT..............................................................................................................4
BACKGROUND.............................................................................................................................4
Literature review....................................................................................................................4
Relevance of Research...........................................................................................................7
Value of this research.............................................................................................................7
Rationale of this research.......................................................................................................7
SCOPE.............................................................................................................................................8
OBJECTIVES..................................................................................................................................8
METHODOLOGY..........................................................................................................................8
PROJECT PLAN...........................................................................................................................10
Timescale..............................................................................................................................10
KNOWN RISKS............................................................................................................................12
ETHICAL, LEGAL, SOCIAL, SECURITY AND PROFESSIONAL CONCERN.....................13
REFERENCES..............................................................................................................................15
APPENDIX....................................................................................................................................16
INTRODUCTION...........................................................................................................................3
TITLE..............................................................................................................................................3
AIM..................................................................................................................................................3
PROBLEM STATEMENT..............................................................................................................4
BACKGROUND.............................................................................................................................4
Literature review....................................................................................................................4
Relevance of Research...........................................................................................................7
Value of this research.............................................................................................................7
Rationale of this research.......................................................................................................7
SCOPE.............................................................................................................................................8
OBJECTIVES..................................................................................................................................8
METHODOLOGY..........................................................................................................................8
PROJECT PLAN...........................................................................................................................10
Timescale..............................................................................................................................10
KNOWN RISKS............................................................................................................................12
ETHICAL, LEGAL, SOCIAL, SECURITY AND PROFESSIONAL CONCERN.....................13
REFERENCES..............................................................................................................................15
APPENDIX....................................................................................................................................16

INTRODUCTION
Cybersecurity plays an important role within business as it helps in defending against
growing concerns of cyber attack. It helps in protecting the business from threats and damages
due which leads to increase in performance and growth of company. Cybersecurity helps in
preventing data loss, safeguard and organization’s network and data files, install firewalls,
manage vulnerability and also ensure the safety of networks. Company focuses on investing in
cybersecurity as prevent the data from breach and helps in protecting from internal and external
bad actors (Corallo, Lazoi and Lezzi, 2020). Organistaion generally provide training opportunity
to their staff so that they can learn about the impact of cybersecurity on business and how it can
be overcome. The purpose of cybersecurity for business is to maintain security, confidentiality
and integrity. There are different types of cybersecurity training for employees such as
cybersecurity awareness training, specialized cybersecurity programs, compliance security
training and many others. In training session, companies generally make them aware from
different strategies which help in reducing the threats and damages (Ponsard and Grandclaudon,
2019). The implementation of strategy helps in increasing the growth and performance of
business. Organisation gains various benefits through implementing effective cybersecurity
strategies within workplace as it helps in increasing the reputation and productivity of business.
Thus, this project is based on the evaluation of cybersecurity strategies delivered in training
sessions to employees for reducing rate of cybercrimes (Jeyaraj, Zadeh and Sethi, 2021). The
chosen organistaion for this research is Waracle LTD, it is an organisation that believes in
mobile and emerging technologies as a force for good. They collaborate with strategic partners in
order to deliver digital solutions with meaningful real world impact.
TITLE
“To determine the effectiveness of the cybersecurity strategies delivered in training
sessions to employees for reducing rate of cybercrimes”
AIM
“To evaluate the cybersecurity strategies delivered in training sessions to employees for
reducing rate of cybercrimes”. A study on Waracle LTD, UK.
Cybersecurity plays an important role within business as it helps in defending against
growing concerns of cyber attack. It helps in protecting the business from threats and damages
due which leads to increase in performance and growth of company. Cybersecurity helps in
preventing data loss, safeguard and organization’s network and data files, install firewalls,
manage vulnerability and also ensure the safety of networks. Company focuses on investing in
cybersecurity as prevent the data from breach and helps in protecting from internal and external
bad actors (Corallo, Lazoi and Lezzi, 2020). Organistaion generally provide training opportunity
to their staff so that they can learn about the impact of cybersecurity on business and how it can
be overcome. The purpose of cybersecurity for business is to maintain security, confidentiality
and integrity. There are different types of cybersecurity training for employees such as
cybersecurity awareness training, specialized cybersecurity programs, compliance security
training and many others. In training session, companies generally make them aware from
different strategies which help in reducing the threats and damages (Ponsard and Grandclaudon,
2019). The implementation of strategy helps in increasing the growth and performance of
business. Organisation gains various benefits through implementing effective cybersecurity
strategies within workplace as it helps in increasing the reputation and productivity of business.
Thus, this project is based on the evaluation of cybersecurity strategies delivered in training
sessions to employees for reducing rate of cybercrimes (Jeyaraj, Zadeh and Sethi, 2021). The
chosen organistaion for this research is Waracle LTD, it is an organisation that believes in
mobile and emerging technologies as a force for good. They collaborate with strategic partners in
order to deliver digital solutions with meaningful real world impact.
TITLE
“To determine the effectiveness of the cybersecurity strategies delivered in training
sessions to employees for reducing rate of cybercrimes”
AIM
“To evaluate the cybersecurity strategies delivered in training sessions to employees for
reducing rate of cybercrimes”. A study on Waracle LTD, UK.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PROBLEM STATEMENT
The major problem within this research is that it to identify the strategies of reducing
cybercrime. It is important to determine the strategy that helps in increasing the profitability and
productivity of business. Organistaion generally face issues regarding the cybersecurity due to
which they are unable to protect their data and also fails to build trust among customers. Thus,
the current investigation will help the company to implement the effective cybersecurity
strategies that helps in reducing the cybercrimes and improves the reputation of brand.
BACKGROUND
Literature review
What is the concept and significance of Cybersecurity in context to organisation?
According to Brilingaitė, Bukauskas and Juozapavičius (2020), Cybersecurity mainly
includes processes, technologies and controls in order to protect the system, program, devices,
networks and information from cyber attacks. It helps in protecting against the unauthorized
exploitation of technologies, systems and networks and also reduces the risk of cyber attacks.
Cyber security is based on three fundamental concepts such as integrity, confidentiality and
availability. Companies generally use cyber security for protecting all categories of data from
damage and theft. The categories of data cover personal information, sensitive data, intellectual
property data, personally identifiable information, governmental and industry information system
and protected health information. Organisations need protecting against security threats and
cyber attacks due to which it becomes important to invest in cyber security. If company face
issues related to data breaches it can badly affect the business and also it is time consuming and
expensive process (Runciman, 2020). Thus, it is necessary to have a strong infosec as it helps in
reducing the risk of internal and external attacks on information technology system.
Cybersecurity plays an integral role within an organisation as it provides confidence that they
have strong data security which helps in protecting against cyber attack and data breaches issues.
When company have weak cybersecurity it leads to lost or stolen of information, reputational
harm and also creates a poor experience for consumers which leads to lost business (La Torre,
Lucchese and Mancini, 2021). Therefore, it becomes important for firm to have solid infosec as
it helps in reducing the risk of attacks in information technology systems, prevents disruption of
services via cyber attacks, applies security controls to prevent unauthorized access to sensitive
The major problem within this research is that it to identify the strategies of reducing
cybercrime. It is important to determine the strategy that helps in increasing the profitability and
productivity of business. Organistaion generally face issues regarding the cybersecurity due to
which they are unable to protect their data and also fails to build trust among customers. Thus,
the current investigation will help the company to implement the effective cybersecurity
strategies that helps in reducing the cybercrimes and improves the reputation of brand.
BACKGROUND
Literature review
What is the concept and significance of Cybersecurity in context to organisation?
According to Brilingaitė, Bukauskas and Juozapavičius (2020), Cybersecurity mainly
includes processes, technologies and controls in order to protect the system, program, devices,
networks and information from cyber attacks. It helps in protecting against the unauthorized
exploitation of technologies, systems and networks and also reduces the risk of cyber attacks.
Cyber security is based on three fundamental concepts such as integrity, confidentiality and
availability. Companies generally use cyber security for protecting all categories of data from
damage and theft. The categories of data cover personal information, sensitive data, intellectual
property data, personally identifiable information, governmental and industry information system
and protected health information. Organisations need protecting against security threats and
cyber attacks due to which it becomes important to invest in cyber security. If company face
issues related to data breaches it can badly affect the business and also it is time consuming and
expensive process (Runciman, 2020). Thus, it is necessary to have a strong infosec as it helps in
reducing the risk of internal and external attacks on information technology system.
Cybersecurity plays an integral role within an organisation as it provides confidence that they
have strong data security which helps in protecting against cyber attack and data breaches issues.
When company have weak cybersecurity it leads to lost or stolen of information, reputational
harm and also creates a poor experience for consumers which leads to lost business (La Torre,
Lucchese and Mancini, 2021). Therefore, it becomes important for firm to have solid infosec as
it helps in reducing the risk of attacks in information technology systems, prevents disruption of
services via cyber attacks, applies security controls to prevent unauthorized access to sensitive
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

data and many others. There are various cybersecurity threats which can influence the
performance of company they are social engineering, third party exposure, patch management,
malware and overall data vulnerability.
What are the cybersecurity strategies delivered in training sessions to employees for
reducing rate of cybercrimes in Waracle LTD?
As per the perspective of Malatji, Von Solms and Marnewick (2019), there are various
cybersecurity strategies delivered in training sessions to employees for reducing rate of
cybercrimes. Organisation generally provides cybersecurity training to its employees so that they
can know about the potential IT risks and vulnerabilities. The training session helps employees
to identify the security threats that occur while working online and with computer systems. The
few strategies which are delivered by Waracle LTD in training sessions to employees for
reducing rate of cybercrimes are encouraging open standards, strengthening the regulatory
framework, creating mechanism for IT security, protecting critical information system,
protecting information, computers and networks from viruses and spyware, secure wifi networks,
regularly change passwords, limit employee access to data and information and creating a secure
cyber ecosystem. Organistaion train their staff to create secure cyber ecosystem as it helps in
protecting the data from threat. Cyber ecosystem includes wide range of varied entities like
individuals, devices, governments, privation organistaion and many other parties which interact
with each other due to various reasons (De Bruin and Von Solms, 2016). It is one of the cyber
security strategy which helps in exploring the ideas of having robust and string cyber ecosystem
where cyber devices can work with each other effectively in order to prevent cyber attacks and
identify the solutions to recover from cyber attack. A strong cyber ecosystem includes three
structures they are automation, interoperability and authentication (Reeves, Calic and Delfabbro,
2021). The other strategy which is provided by trainer to its trainee for reducing the rate of
cybercrimes in Waracle ltd is encouraging open standards. It becomes important to encourage
open standards as it enhances the efficiency of key processes, enable system incorporation,
organize the approach to arrange new technologies and also interpreting the complex
environment. Strengthening the regulatory framework is also a strategy of cybersecurity which
are delivered to employees in an organistaion during training session. The main motive of this
strategy is to secure cyberspace ecosystem and strengthening the regulatory framework.
What are the impact of implementing cybersecurity strategies on Waracle LTD?
performance of company they are social engineering, third party exposure, patch management,
malware and overall data vulnerability.
What are the cybersecurity strategies delivered in training sessions to employees for
reducing rate of cybercrimes in Waracle LTD?
As per the perspective of Malatji, Von Solms and Marnewick (2019), there are various
cybersecurity strategies delivered in training sessions to employees for reducing rate of
cybercrimes. Organisation generally provides cybersecurity training to its employees so that they
can know about the potential IT risks and vulnerabilities. The training session helps employees
to identify the security threats that occur while working online and with computer systems. The
few strategies which are delivered by Waracle LTD in training sessions to employees for
reducing rate of cybercrimes are encouraging open standards, strengthening the regulatory
framework, creating mechanism for IT security, protecting critical information system,
protecting information, computers and networks from viruses and spyware, secure wifi networks,
regularly change passwords, limit employee access to data and information and creating a secure
cyber ecosystem. Organistaion train their staff to create secure cyber ecosystem as it helps in
protecting the data from threat. Cyber ecosystem includes wide range of varied entities like
individuals, devices, governments, privation organistaion and many other parties which interact
with each other due to various reasons (De Bruin and Von Solms, 2016). It is one of the cyber
security strategy which helps in exploring the ideas of having robust and string cyber ecosystem
where cyber devices can work with each other effectively in order to prevent cyber attacks and
identify the solutions to recover from cyber attack. A strong cyber ecosystem includes three
structures they are automation, interoperability and authentication (Reeves, Calic and Delfabbro,
2021). The other strategy which is provided by trainer to its trainee for reducing the rate of
cybercrimes in Waracle ltd is encouraging open standards. It becomes important to encourage
open standards as it enhances the efficiency of key processes, enable system incorporation,
organize the approach to arrange new technologies and also interpreting the complex
environment. Strengthening the regulatory framework is also a strategy of cybersecurity which
are delivered to employees in an organistaion during training session. The main motive of this
strategy is to secure cyberspace ecosystem and strengthening the regulatory framework.
What are the impact of implementing cybersecurity strategies on Waracle LTD?

As per the viewpoint of Mäses and et. al., (2021), there is a positive impact of
cybersecurity strategies on company as it helps in improving the performance and productivity of
business. The benefits which are gained by company through investing in cybersecurity are
protection for business, increased productivity, inspires customer confidence, protection for
customers and also stops website from going down. These are the few impacts of implementing
cybersecurity strategies on Waracle ltd. By using cybersecurity strategies within an organisation
helps in protecting the business as it provides cyber security solution that ensures that employees
may not face risk from potential threats such as Ransomware and Adware. It also helps in
increasing the productivity of business by eliminating the threat and maximizing the business
potential output. Virus can influence the speed of computer and also make work practically
impossible (Sutherland, 2018). Due to which it is important to focus on investing in cyber
security as it helps in minimizing the risk and also improves the functioning of business. By
implementing the strategies of cybersecurity, company can also protect the information of their
customers in effective and efficient manner. When Waracle ltd ensures that their business is
secure from cyber threats they can protect their customers. The strategy also helps in inspiring
customer confidence by proving that their company is effectively protected against all kinds of
cyber breaches. It helps in building trust among users that their personal data will not be
compromised (da Silva Oliveira and Santos, 2022). The cybersecurity strategies also help in
stopping website from going down. Organisation may face difficulty while hosting their own
website as cyber breach can affect the website which can be disastrous. If the system of company
becomes infected it will force the website to be close due to which they can lose money and also
lost transactions. Effective cybersecurity strategies also help in protecting and maintaining the
business reputation. If Waracle ltd faces data breach it can influence the brand reputation and
also reduce the trust among customers. Therefore, by building secure system and taking all
precautions helps in increasing brand reputation. The cybersecurity technology like network
security and cloud security helps in managing the authentication. Cybersecurity strategies help in
assisting in remote working. Working from home helps employees to work according to their
interest and also it helps in increasing the productivity of staff. It can be relaxing for employees
but it also increases the threat to sensitive organisation information. Thus, cybersecurity
technologies can prevent hackers from snooping or tracking employee data.
cybersecurity strategies on company as it helps in improving the performance and productivity of
business. The benefits which are gained by company through investing in cybersecurity are
protection for business, increased productivity, inspires customer confidence, protection for
customers and also stops website from going down. These are the few impacts of implementing
cybersecurity strategies on Waracle ltd. By using cybersecurity strategies within an organisation
helps in protecting the business as it provides cyber security solution that ensures that employees
may not face risk from potential threats such as Ransomware and Adware. It also helps in
increasing the productivity of business by eliminating the threat and maximizing the business
potential output. Virus can influence the speed of computer and also make work practically
impossible (Sutherland, 2018). Due to which it is important to focus on investing in cyber
security as it helps in minimizing the risk and also improves the functioning of business. By
implementing the strategies of cybersecurity, company can also protect the information of their
customers in effective and efficient manner. When Waracle ltd ensures that their business is
secure from cyber threats they can protect their customers. The strategy also helps in inspiring
customer confidence by proving that their company is effectively protected against all kinds of
cyber breaches. It helps in building trust among users that their personal data will not be
compromised (da Silva Oliveira and Santos, 2022). The cybersecurity strategies also help in
stopping website from going down. Organisation may face difficulty while hosting their own
website as cyber breach can affect the website which can be disastrous. If the system of company
becomes infected it will force the website to be close due to which they can lose money and also
lost transactions. Effective cybersecurity strategies also help in protecting and maintaining the
business reputation. If Waracle ltd faces data breach it can influence the brand reputation and
also reduce the trust among customers. Therefore, by building secure system and taking all
precautions helps in increasing brand reputation. The cybersecurity technology like network
security and cloud security helps in managing the authentication. Cybersecurity strategies help in
assisting in remote working. Working from home helps employees to work according to their
interest and also it helps in increasing the productivity of staff. It can be relaxing for employees
but it also increases the threat to sensitive organisation information. Thus, cybersecurity
technologies can prevent hackers from snooping or tracking employee data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Relevance of Research
This research is quite relevant as it provides brief explanation of the cybersecurity and its
strategies for mitigating the issues related to cybercrimes. It depicts about the different strategies
of cybersecurity which helps in reducing the rate of cybercrimes within an organisation. Thus,
the present study is helpful for the company as it provides valid information of cybersecurity and
its impact on business performance. Through implementing different strategies, company can
reduce the cybercrimes and boost their performance and growth rate. The strategies of
cybersecurity help in protecting customers and employees data in significant manner which leads
to increase in brand reputation.
Value of this research
This investigation holds a great value as it provide in-depth and valid information related
to the cybersecurity strategies delivered in training sessions to employees for reducing rate of
cybercrimes within workplace. The current investigation is useful and helpful for companies,
students and researcher. In respect of student, this research will provide knowledge related to
cybersecurity due to which their academic skills and knowledge gets increased and also they can
implement the strategies of cybersecurity in their professional career. In terms of researcher, the
current study is valuable as it provides all the information related to the impact of cybersecurity
on business which can be used to gain fundamental knowledge and also develop their own
investigation. In respect to organisation, this research will help in gaining information related to
cybersecurity strategy due to which company can implement it in effective and efficient manner
in order to prevent damage and reduce the cybercrimes within workplace.
Rationale of this research
The rationale behind doing this research is that it helps in accumulating the data related to
the cybersecurity strategies delivered in training sessions to employees for reducing rate of
cybercrimes. Current investigation helps in fulfilling personal as well as professional objectives
of the researcher. It helps in increasing the skills and knowledge of the investigator due to which
the personal objective will get fulfilled. The professional objective of the researcher will also get
achieved as it helps to conduct future investigation in systematic and well defined manner.
This research is quite relevant as it provides brief explanation of the cybersecurity and its
strategies for mitigating the issues related to cybercrimes. It depicts about the different strategies
of cybersecurity which helps in reducing the rate of cybercrimes within an organisation. Thus,
the present study is helpful for the company as it provides valid information of cybersecurity and
its impact on business performance. Through implementing different strategies, company can
reduce the cybercrimes and boost their performance and growth rate. The strategies of
cybersecurity help in protecting customers and employees data in significant manner which leads
to increase in brand reputation.
Value of this research
This investigation holds a great value as it provide in-depth and valid information related
to the cybersecurity strategies delivered in training sessions to employees for reducing rate of
cybercrimes within workplace. The current investigation is useful and helpful for companies,
students and researcher. In respect of student, this research will provide knowledge related to
cybersecurity due to which their academic skills and knowledge gets increased and also they can
implement the strategies of cybersecurity in their professional career. In terms of researcher, the
current study is valuable as it provides all the information related to the impact of cybersecurity
on business which can be used to gain fundamental knowledge and also develop their own
investigation. In respect to organisation, this research will help in gaining information related to
cybersecurity strategy due to which company can implement it in effective and efficient manner
in order to prevent damage and reduce the cybercrimes within workplace.
Rationale of this research
The rationale behind doing this research is that it helps in accumulating the data related to
the cybersecurity strategies delivered in training sessions to employees for reducing rate of
cybercrimes. Current investigation helps in fulfilling personal as well as professional objectives
of the researcher. It helps in increasing the skills and knowledge of the investigator due to which
the personal objective will get fulfilled. The professional objective of the researcher will also get
achieved as it helps to conduct future investigation in systematic and well defined manner.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SCOPE
This research is mainly focusing on determining the cybersecurity strategies that will be
helpful for an organistaion in reducing the cybercrimes. The scope of this research is to provide
relevant information to an organisation related to the impact and strategies of cybersecurity. It
can create a great impact on the performance and productivity of business. Thus, it becomes
necessary to adopt cybersecurity strategies in order to reduce cybercrimes and eliminate
damages.
OBJECTIVES
To determine the concept and significance of Cybersecurity in context to organisation.
To examine the cybersecurity strategies delivered in training sessions to employees for
reducing rate of cybercrimes in Waracle LTD.
To analyse the impact of implementing cybersecurity strategies on Waracle LTD.
METHODOLOGY
Research methodology involves different methods of research that aims in accumulating,
analyzing and evaluating the information in systematic manner. It generally helps reader to
evaluate the reliability and validity of the current study.
Research Philosophy:
Research Philosophy is classified into two different kinds such as positivism and
interpretivism philosophy. The current investigation will focuses on choosing positivism
philosophy as it gathers and evaluates numerical piece of information due to which research aims
and objective can be attained in better manner. Researcher will choose positivism philosophy as
it helps in collecting the information related to the subject matter in less time period with low
cost.
Research Approach:
The two different types of research approach are inductive and deductive. Within this
study, the investigator will choose deductive research approach as it is based on quantitative
research and also collects statistical facts and figures (Abbassi and et. al., 2016). The deductive
approach helps in carrying out relevancy and accuracy of numerical information in less time
period as compare to other approach. It also focuses on testing existing theories in respect of
developing new hypothesis. The researcher will test the theory with the help of quantitative data.
This research is mainly focusing on determining the cybersecurity strategies that will be
helpful for an organistaion in reducing the cybercrimes. The scope of this research is to provide
relevant information to an organisation related to the impact and strategies of cybersecurity. It
can create a great impact on the performance and productivity of business. Thus, it becomes
necessary to adopt cybersecurity strategies in order to reduce cybercrimes and eliminate
damages.
OBJECTIVES
To determine the concept and significance of Cybersecurity in context to organisation.
To examine the cybersecurity strategies delivered in training sessions to employees for
reducing rate of cybercrimes in Waracle LTD.
To analyse the impact of implementing cybersecurity strategies on Waracle LTD.
METHODOLOGY
Research methodology involves different methods of research that aims in accumulating,
analyzing and evaluating the information in systematic manner. It generally helps reader to
evaluate the reliability and validity of the current study.
Research Philosophy:
Research Philosophy is classified into two different kinds such as positivism and
interpretivism philosophy. The current investigation will focuses on choosing positivism
philosophy as it gathers and evaluates numerical piece of information due to which research aims
and objective can be attained in better manner. Researcher will choose positivism philosophy as
it helps in collecting the information related to the subject matter in less time period with low
cost.
Research Approach:
The two different types of research approach are inductive and deductive. Within this
study, the investigator will choose deductive research approach as it is based on quantitative
research and also collects statistical facts and figures (Abbassi and et. al., 2016). The deductive
approach helps in carrying out relevancy and accuracy of numerical information in less time
period as compare to other approach. It also focuses on testing existing theories in respect of
developing new hypothesis. The researcher will test the theory with the help of quantitative data.

Research Strategy:
The research strategy helps in gathering information related to the particular topic in
significant way. The different kinds of research strategy are survey, systematic literature review,
action research, experimental, case study and many others. But within this study, the investigator
will lay emphasis on choosing survey strategy as it collects data from wide range of population
which helps in achieving the research aims and objective in effective and efficient manner. It
also collects numerical information related to the chosen topic which helps researcher to
complete the investigation in appropriate way. Through using survey strategy, investigator can
collect primary data from the chosen respondents and also identify their perspective and opinion
related to the cybersecurity.
Research Choice:
Research choice generally determines the types of data which need to be gathered and
analysed by the researcher. It is classified into two different parts such as qualitative and
quantitative research choice. In current investigation, researcher will choose quantitative research
choice as it collects numerical data in systematic manner (Flick, 2020). Through choosing
quantitative resrecah, investigator can evaluate the information in easy and quick manner. With
the help quantitative research choice, investigator can gather data in the forms of numbers and
statistic which will be helpful in completing the investigation in effective way.
Data Collection:
Data collection is also a type of research methodology which collects relevant and
reliable data related to the current investigation. The two different forms of data collection
method are primary data collection method and secondary data collection method. Researcher
will choose both the data collection method in order to accomplish this research. Within this
investigation, questionnaire will be formed by including close ended questions. In order to
accumulate secondary information, researcher will use different sources such as articles,
publication and newspapers (Goertzen, 2017).
Sampling:
Sampling is a process of choosing number of participants to answer the questions related
to the chosen topic. It is classified into two parts such as probability and non-probability
sampling. The investigator will select probability sampling method as it provide equal chance to
each participants to share their perspective and opinion related to the study. 20 employees of
The research strategy helps in gathering information related to the particular topic in
significant way. The different kinds of research strategy are survey, systematic literature review,
action research, experimental, case study and many others. But within this study, the investigator
will lay emphasis on choosing survey strategy as it collects data from wide range of population
which helps in achieving the research aims and objective in effective and efficient manner. It
also collects numerical information related to the chosen topic which helps researcher to
complete the investigation in appropriate way. Through using survey strategy, investigator can
collect primary data from the chosen respondents and also identify their perspective and opinion
related to the cybersecurity.
Research Choice:
Research choice generally determines the types of data which need to be gathered and
analysed by the researcher. It is classified into two different parts such as qualitative and
quantitative research choice. In current investigation, researcher will choose quantitative research
choice as it collects numerical data in systematic manner (Flick, 2020). Through choosing
quantitative resrecah, investigator can evaluate the information in easy and quick manner. With
the help quantitative research choice, investigator can gather data in the forms of numbers and
statistic which will be helpful in completing the investigation in effective way.
Data Collection:
Data collection is also a type of research methodology which collects relevant and
reliable data related to the current investigation. The two different forms of data collection
method are primary data collection method and secondary data collection method. Researcher
will choose both the data collection method in order to accomplish this research. Within this
investigation, questionnaire will be formed by including close ended questions. In order to
accumulate secondary information, researcher will use different sources such as articles,
publication and newspapers (Goertzen, 2017).
Sampling:
Sampling is a process of choosing number of participants to answer the questions related
to the chosen topic. It is classified into two parts such as probability and non-probability
sampling. The investigator will select probability sampling method as it provide equal chance to
each participants to share their perspective and opinion related to the study. 20 employees of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Waracle ltd will be selected on hypothetical basis to answer the questions related to the
cybersecurity strategies delivered in training sessions to employees for reducing rate of
cybercrimes.
Time Horizon:
Time Horizon generally determines about the particular time period required for completing
the task. It is categorized into two different kinds such as cross sectional and longitudinal time
horizon. The researcher will focuses on selecting cross sectional time horizon method as it helps
in achieving the objective of research within real time situation.
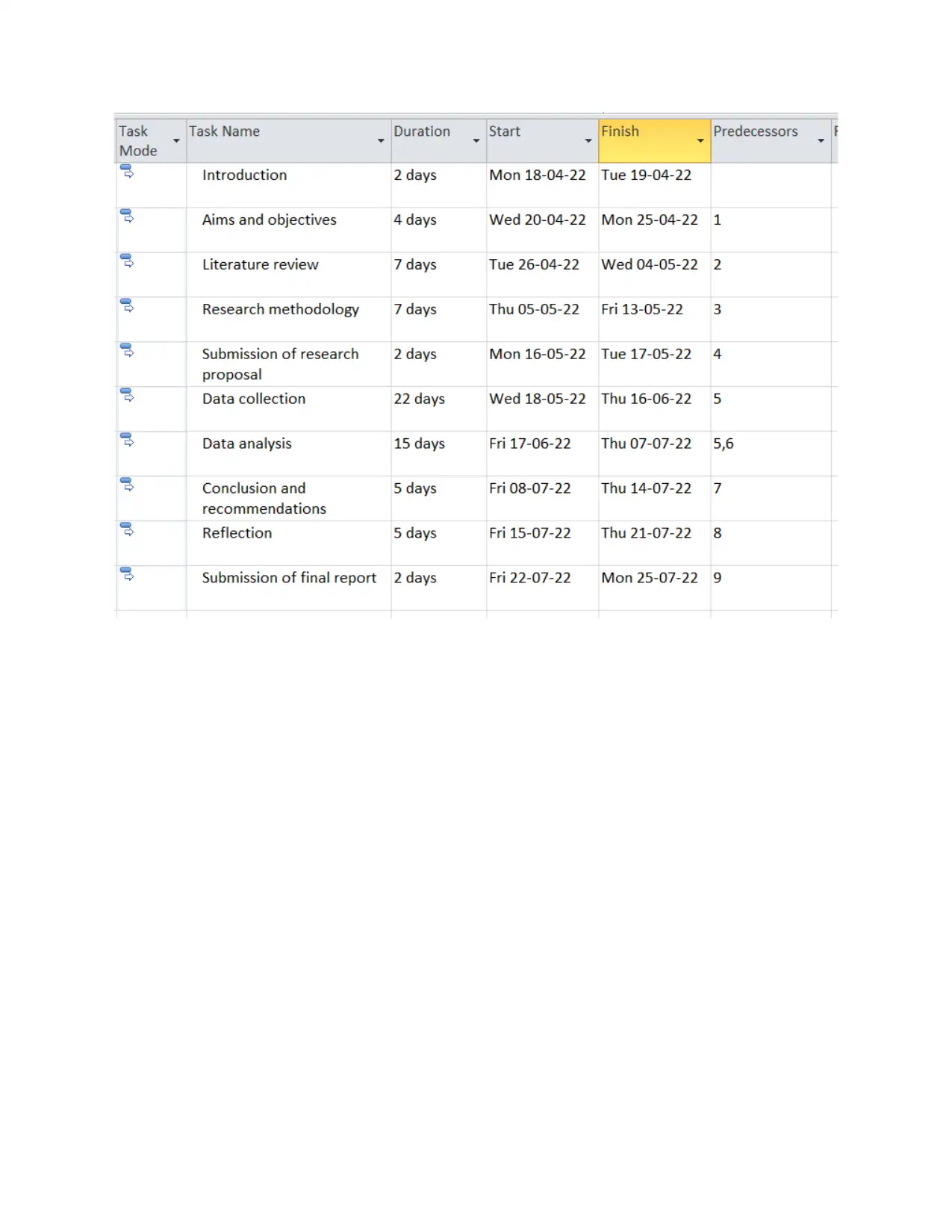
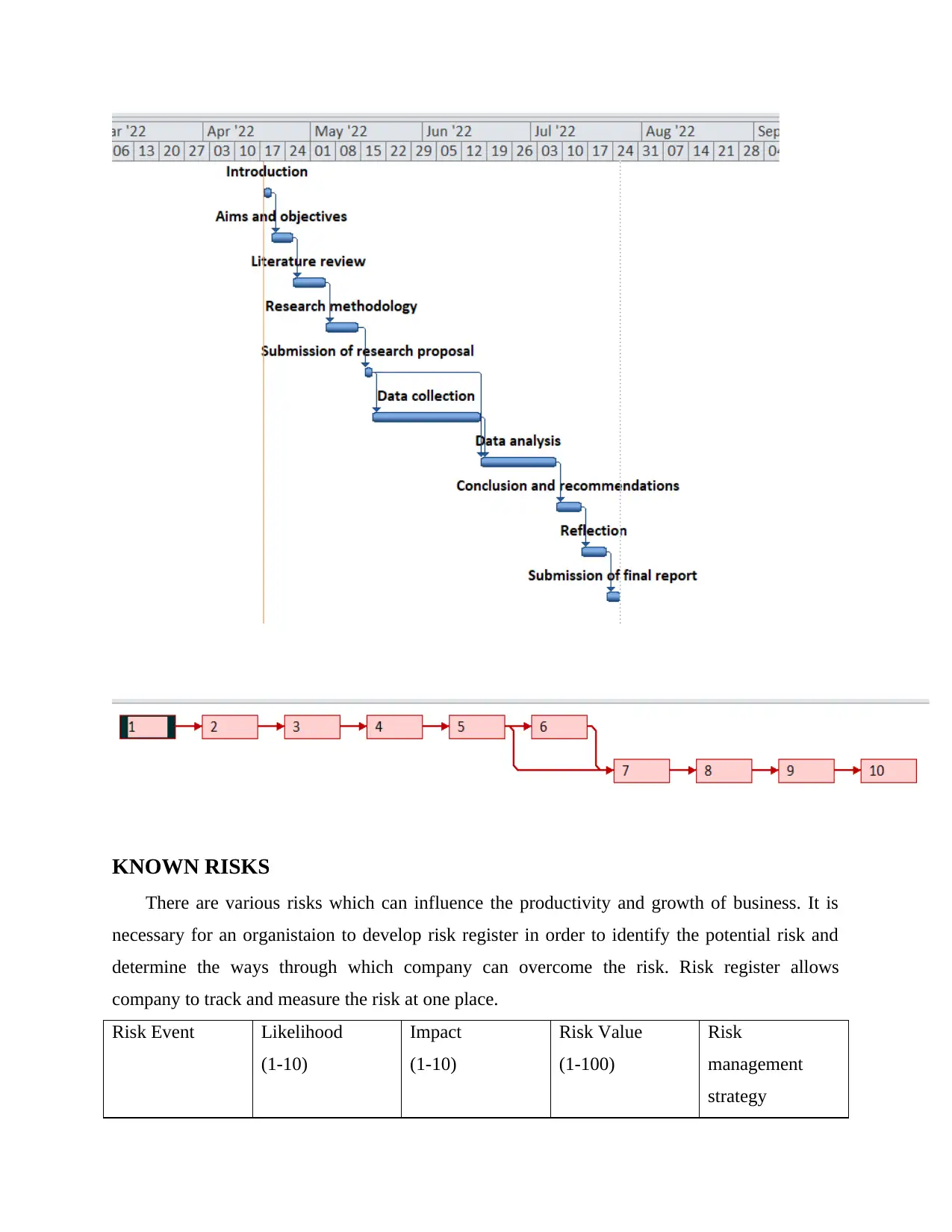
PROJECT PLAN
Timescale
Gantt chart is a tool which divides activities with proper time interval due to which every
activity can be achieved according to set time in systematic manner. It is time scheduling chart
into two sections they are activity to be accomplished and time taken for completing the activity
(Ong, Wang and Zainon, 2016). The activities are presented in bar and the length and position of
bar reflects about the initiation date, end date and duration of activity.
cybersecurity strategies delivered in training sessions to employees for reducing rate of
cybercrimes.
Time Horizon:
Time Horizon generally determines about the particular time period required for completing
the task. It is categorized into two different kinds such as cross sectional and longitudinal time
horizon. The researcher will focuses on selecting cross sectional time horizon method as it helps
in achieving the objective of research within real time situation.
PROJECT PLAN
Timescale
Gantt chart is a tool which divides activities with proper time interval due to which every
activity can be achieved according to set time in systematic manner. It is time scheduling chart
into two sections they are activity to be accomplished and time taken for completing the activity
(Ong, Wang and Zainon, 2016). The activities are presented in bar and the length and position of
bar reflects about the initiation date, end date and duration of activity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
KNOWN RISKS
There are various risks which can influence the productivity and growth of business. It is
necessary for an organistaion to develop risk register in order to identify the potential risk and
determine the ways through which company can overcome the risk. Risk register allows
company to track and measure the risk at one place.
Risk Event Likelihood
(1-10)
Impact
(1-10)
Risk Value
(1-100)
Risk
management
strategy
There are various risks which can influence the productivity and growth of business. It is
necessary for an organistaion to develop risk register in order to identify the potential risk and
determine the ways through which company can overcome the risk. Risk register allows
company to track and measure the risk at one place.
Risk Event Likelihood
(1-10)
Impact
(1-10)
Risk Value
(1-100)
Risk
management
strategy
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





