University Cybersecurity and Cyberwarfare Project Report
VerifiedAdded on 2023/04/23
|59
|946
|121
Project
AI Summary
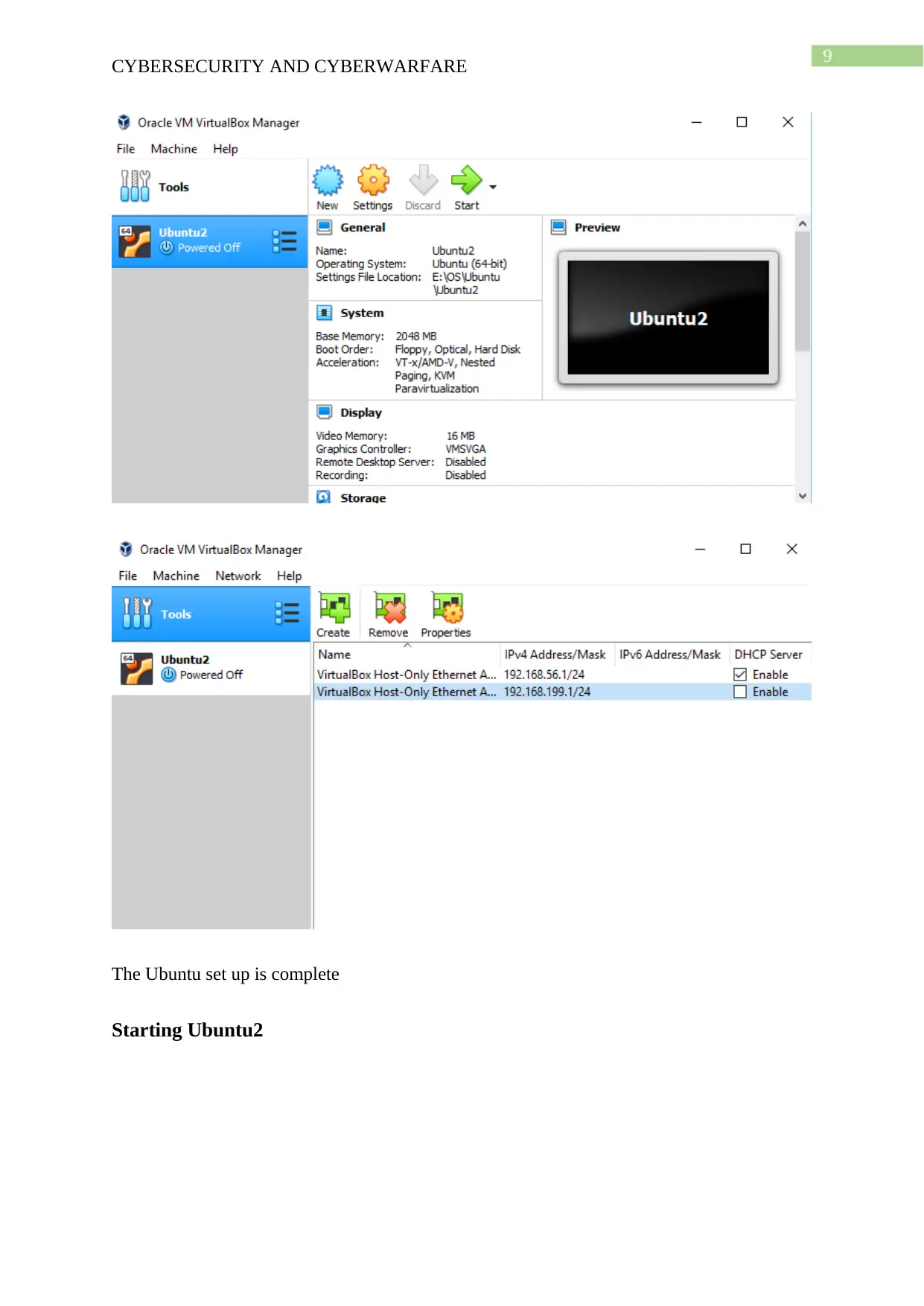
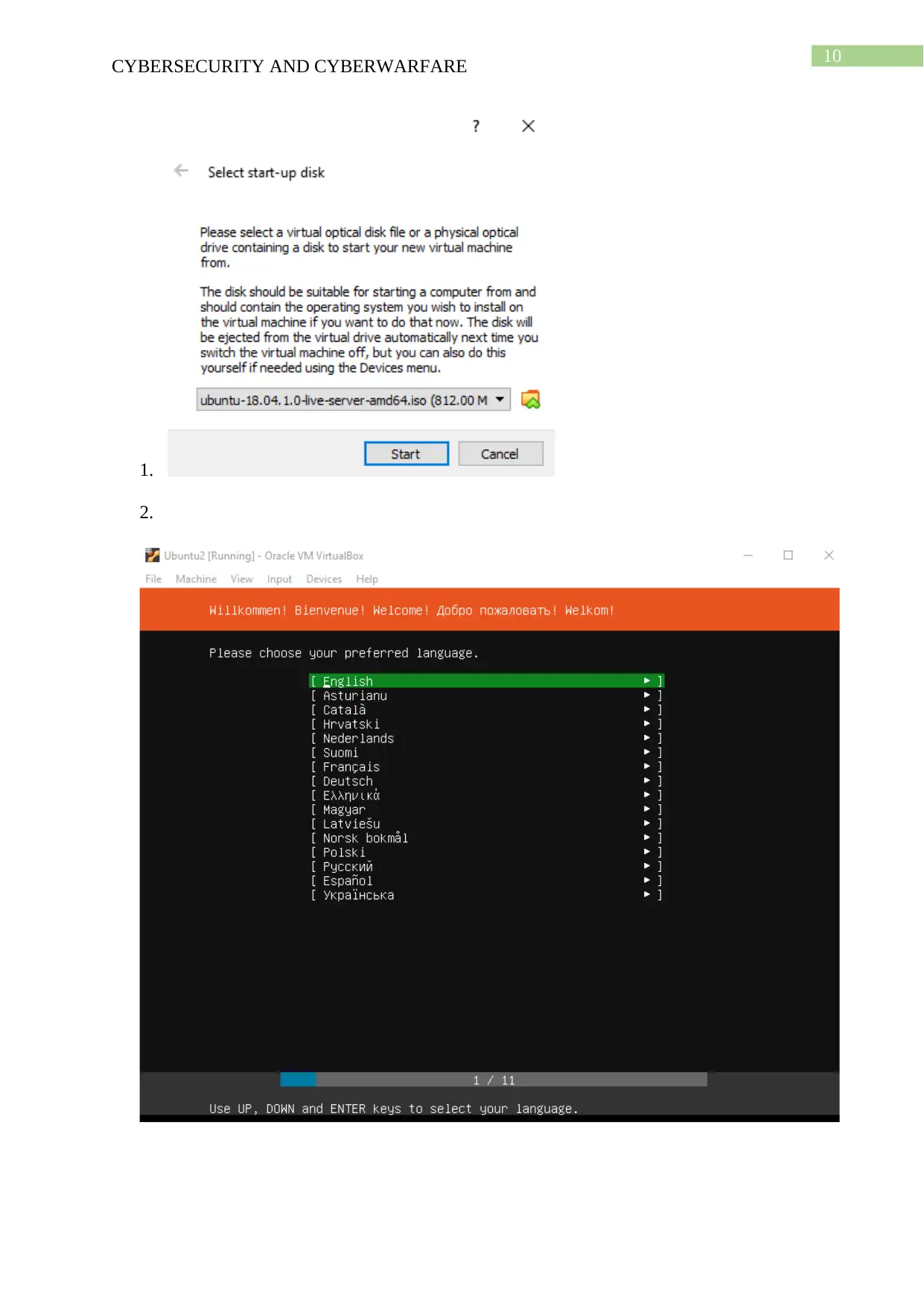
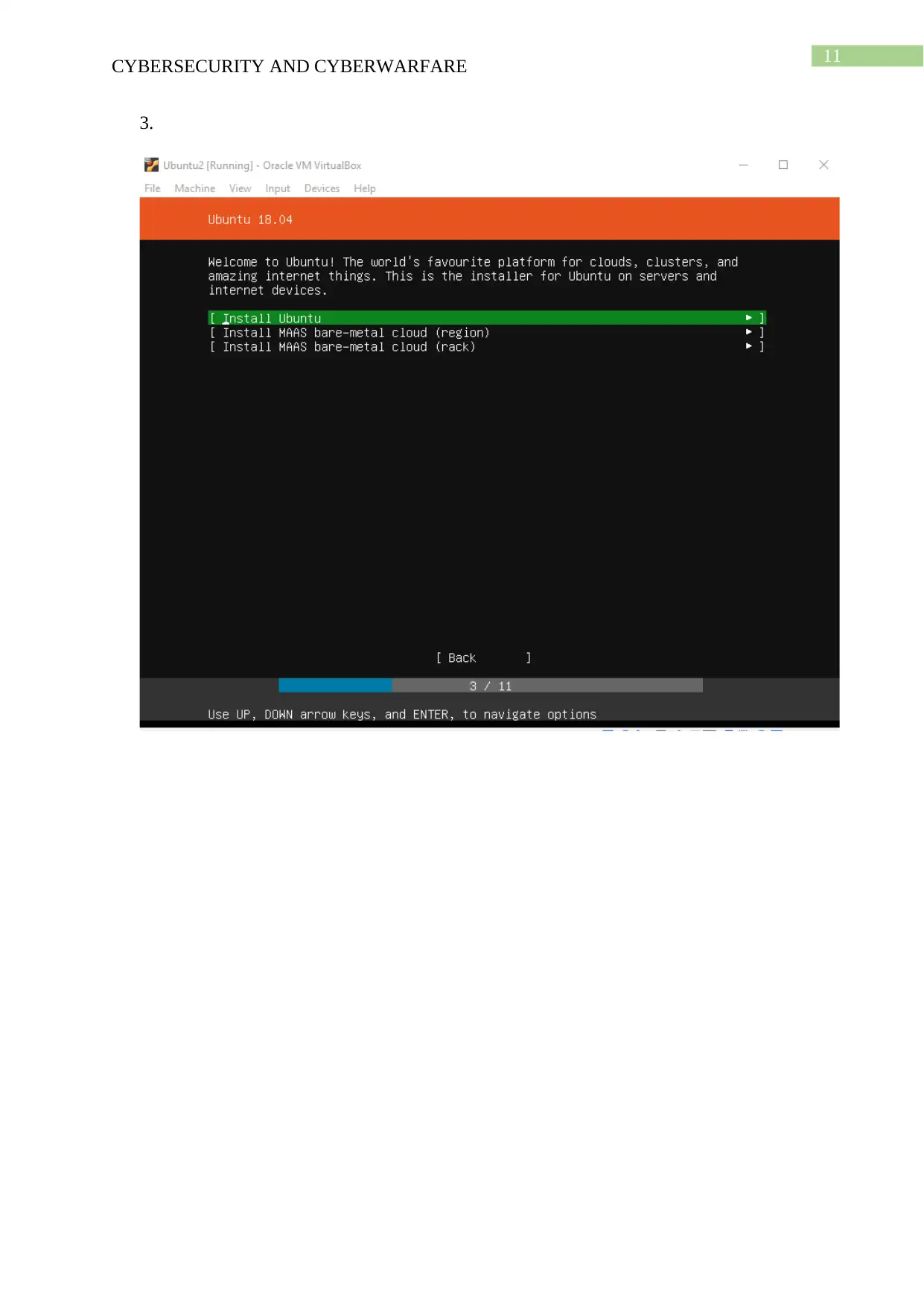
This cybersecurity project report details a hands-on approach to understanding and implementing cybersecurity principles. The project begins with setting up virtual machines, including Ubuntu, Kali Linux, and Metasploitable, using VirtualBox. The report outlines the installation and configuration of each VM. Task 2 focuses on using Metasploit and Armitage within the Kali Linux environment to identify and exploit vulnerabilities on the Metasploitable machine. The report documents the process and outcomes of the exploitation attempts. Task 3 involves installing and configuring Samhain on the Ubuntu VM to create alerts, demonstrating intrusion detection techniques. Task 4 describes the installation of pFSense on the Ubuntu VM and blocking UDP traffic, showcasing network security measures. Finally, Task 5 presents a cybersecurity strategy framework, including stages for identifying, analyzing, validating, and taking action against vulnerabilities, providing a comprehensive approach to securing a project. The report provides a detailed framework for vulnerability management and incident response.
1 out of 59








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)