Cybersecurity Coursework: System Design, Risk Assessment, and Tools
VerifiedAdded on 2022/09/12
|6
|2258
|20
Homework Assignment
AI Summary
This cybersecurity coursework analyzes the network architecture of Brunel Tech Startup, detailing its nodes, networks, and applications, including a main router, sub-routers, Linux servers, and cloud services. The assignment identifies potential risks such as ransomware, database injection, and DoS attacks, and presents a risk model using a recognized cybersecurity risk modeling technique. The solution proposes countermeasures like specific tools to stop ransomware, input validation, anti-DoS hardware and software, and digital signatures. The coursework also describes tools like firewalls, antivirus software, PKI services, MDR, and penetration testing to mitigate these risks, referencing the kill chain. The solution includes a bibliography in Harvard format.
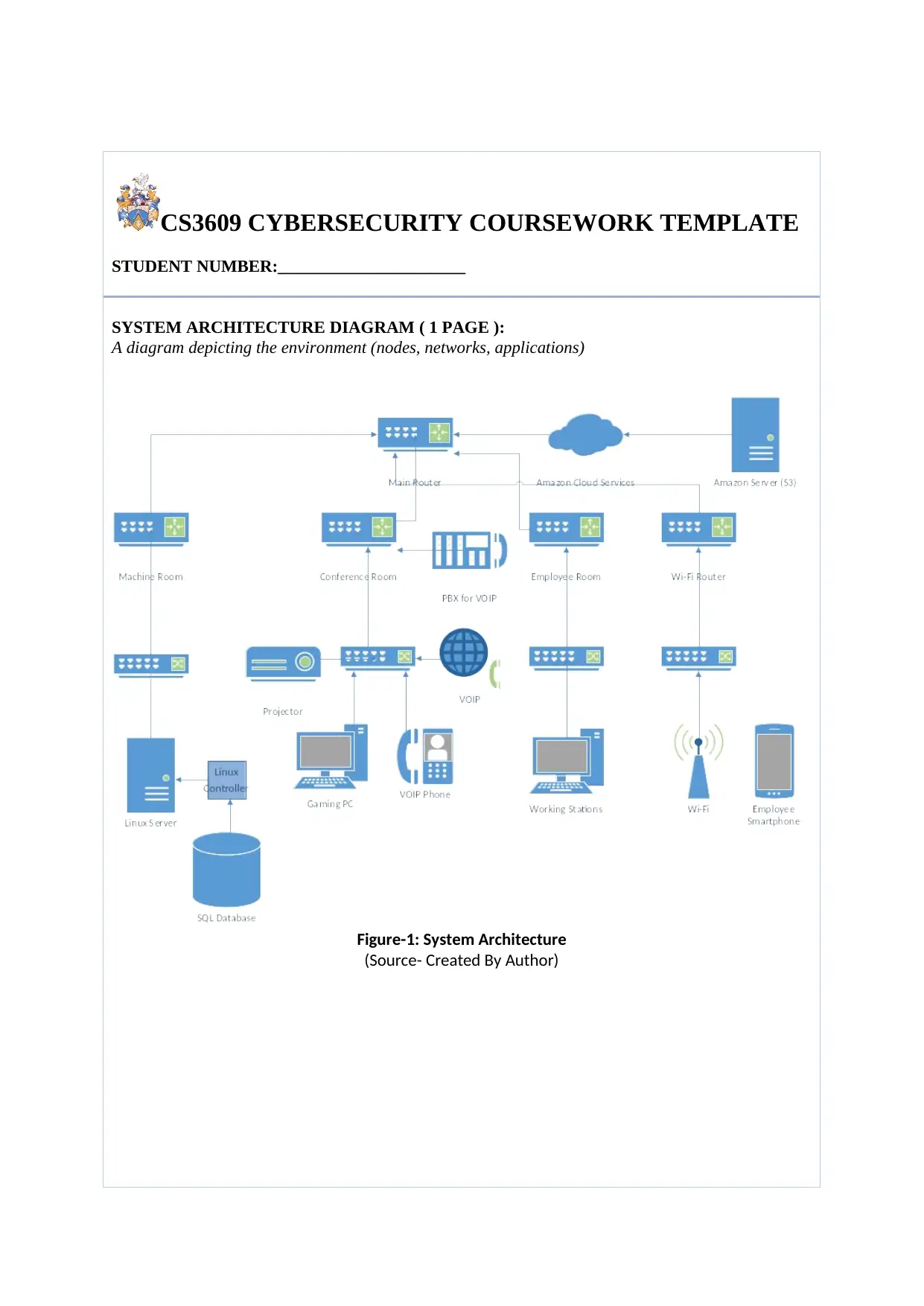
CS3609 CYBERSECURITY COURSEWORK TEMPLATE
STUDENT NUMBER:______________________
SYSTEM ARCHITECTURE DIAGRAM ( 1 PAGE ):
A diagram depicting the environment (nodes, networks, applications)
Figure-1: System Architecture
(Source- Created By Author)
STUDENT NUMBER:______________________
SYSTEM ARCHITECTURE DIAGRAM ( 1 PAGE ):
A diagram depicting the environment (nodes, networks, applications)
Figure-1: System Architecture
(Source- Created By Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SYSTEM ARCHITECTURE DESCRIPTION ( UP TO 2 PAGES ):
A narrative analysis of the environment that covers nodes, networks and applications. This must
include articulation of the elements of the office network, identifying possible risks in the network,
devices and applications (and any assumption made).
Brunel Tech Start-up has set up their new office and is setting up a new network required for the
company to carry out all the business related activities efficiently along with the presence of cloud
service provider for the same.
Firstly, the entire local area network of the company consists of a main router from where all the other
existing sub routers of the network receive the required network connection. Each of the sub router
consist of a switch with the help of which the sub routers controls the equipment attacked to the same.
There are three main sub routers connected to the network.
The first sub router is present within the machine room that consists of a Linux server
belonging to the company that acts as an internal storage for storing all the data along with the
information belonging to the company. To store the information of the company internally, a
SQL database along with a Linux Controller is connected to the Linux Server for storing all the
information locally. In this section of the company, there is the possibility of any employee
taking the advantage of the access to the internal database of the company and make use of the
data towards illegal activities. In addition to this, there is also the shared possibility of database
injection attacks that provisions the attacker with the particular access to the database in an
unauthorized manner.
Next, a sub router has been placed within the conference room to which a switch is connected
for controlling all the devices present inside the conference room. The conference room consists
of a projector meant for the purpose of carrying out meetings inside the room and showing
related information on the projector for the people to get hold of the agendas and other related
information. A gaming PC has been placed within the conference room to carry out all the
activities related to graphics. A device for conference calls to clients, namely VOIP phone has
been placed. To carry out the conference calls without any errors, a PBX has been placed along
with a VOIP network to provision for the same. This VOIP phone is mainly kept for carrying
out all the conversations with the clients and provide the clients with the information related to
their project to keep the client updated with the progress of the project. In case of the routers as
well as the sub routers, there is the possible threat of unauthorized access from external sources,
rerouting, session hijacking, DoS as well as masquerading. Such threats carry the potential
ability to steal the data that belongs to the company and make use of the same for online
existent illegal practices.
For the employees, a separate server meant for the working room has been installed along with
a switch to control all the connected devices present within the working room. Each of the desk
present within the working room will be provisioned with separate working stations for each of
the individual employees. All of the working stations has been connected with a single switch,
with the help of which all of the working stations will be controlled along with turning on and
off. Common risks to the workstations upon which the employees will be working are the likes
of DOS, ransomware as well as malware attacks. All of the risks that have been mentioned
include the possibility of preventing the user from accessing their own data and pay a
ransomware to regain access to the same.
Another sub router has been kept under the main router that has the only purpose of carrying
out the connection of a Wi-Fi. A Wi-Fi device has been installed and connected to a switch,
which connects to the sub router for the Wi-Fi connection. This wireless network has been
installed for the benefits of the employees to download all the documents from the server using
the Wi-Fi connection. The Wi-Fi device can have associated risks such as unauthorized access
from some external source that might get into the communication of the user with the device
A narrative analysis of the environment that covers nodes, networks and applications. This must
include articulation of the elements of the office network, identifying possible risks in the network,
devices and applications (and any assumption made).
Brunel Tech Start-up has set up their new office and is setting up a new network required for the
company to carry out all the business related activities efficiently along with the presence of cloud
service provider for the same.
Firstly, the entire local area network of the company consists of a main router from where all the other
existing sub routers of the network receive the required network connection. Each of the sub router
consist of a switch with the help of which the sub routers controls the equipment attacked to the same.
There are three main sub routers connected to the network.
The first sub router is present within the machine room that consists of a Linux server
belonging to the company that acts as an internal storage for storing all the data along with the
information belonging to the company. To store the information of the company internally, a
SQL database along with a Linux Controller is connected to the Linux Server for storing all the
information locally. In this section of the company, there is the possibility of any employee
taking the advantage of the access to the internal database of the company and make use of the
data towards illegal activities. In addition to this, there is also the shared possibility of database
injection attacks that provisions the attacker with the particular access to the database in an
unauthorized manner.
Next, a sub router has been placed within the conference room to which a switch is connected
for controlling all the devices present inside the conference room. The conference room consists
of a projector meant for the purpose of carrying out meetings inside the room and showing
related information on the projector for the people to get hold of the agendas and other related
information. A gaming PC has been placed within the conference room to carry out all the
activities related to graphics. A device for conference calls to clients, namely VOIP phone has
been placed. To carry out the conference calls without any errors, a PBX has been placed along
with a VOIP network to provision for the same. This VOIP phone is mainly kept for carrying
out all the conversations with the clients and provide the clients with the information related to
their project to keep the client updated with the progress of the project. In case of the routers as
well as the sub routers, there is the possible threat of unauthorized access from external sources,
rerouting, session hijacking, DoS as well as masquerading. Such threats carry the potential
ability to steal the data that belongs to the company and make use of the same for online
existent illegal practices.
For the employees, a separate server meant for the working room has been installed along with
a switch to control all the connected devices present within the working room. Each of the desk
present within the working room will be provisioned with separate working stations for each of
the individual employees. All of the working stations has been connected with a single switch,
with the help of which all of the working stations will be controlled along with turning on and
off. Common risks to the workstations upon which the employees will be working are the likes
of DOS, ransomware as well as malware attacks. All of the risks that have been mentioned
include the possibility of preventing the user from accessing their own data and pay a
ransomware to regain access to the same.
Another sub router has been kept under the main router that has the only purpose of carrying
out the connection of a Wi-Fi. A Wi-Fi device has been installed and connected to a switch,
which connects to the sub router for the Wi-Fi connection. This wireless network has been
installed for the benefits of the employees to download all the documents from the server using
the Wi-Fi connection. The Wi-Fi device can have associated risks such as unauthorized access
from some external source that might get into the communication of the user with the device
and get hold of all the data that is a part of the communication.
Lastly, the company is also using the services of Amazon Cloud for storage of important information
and data belonging to the company for the purpose of backing up all the data to provide support to
situations where data losses can occur. To mitigate such potential happenings, Amazon cloud services
have been installed within the organization. The system architecture consists of an Amazon Server
that is connected to a cloud storage. On the other hand, the main router is connected to the Cloud
storage and gets access to the Amazon Server through the cloud.
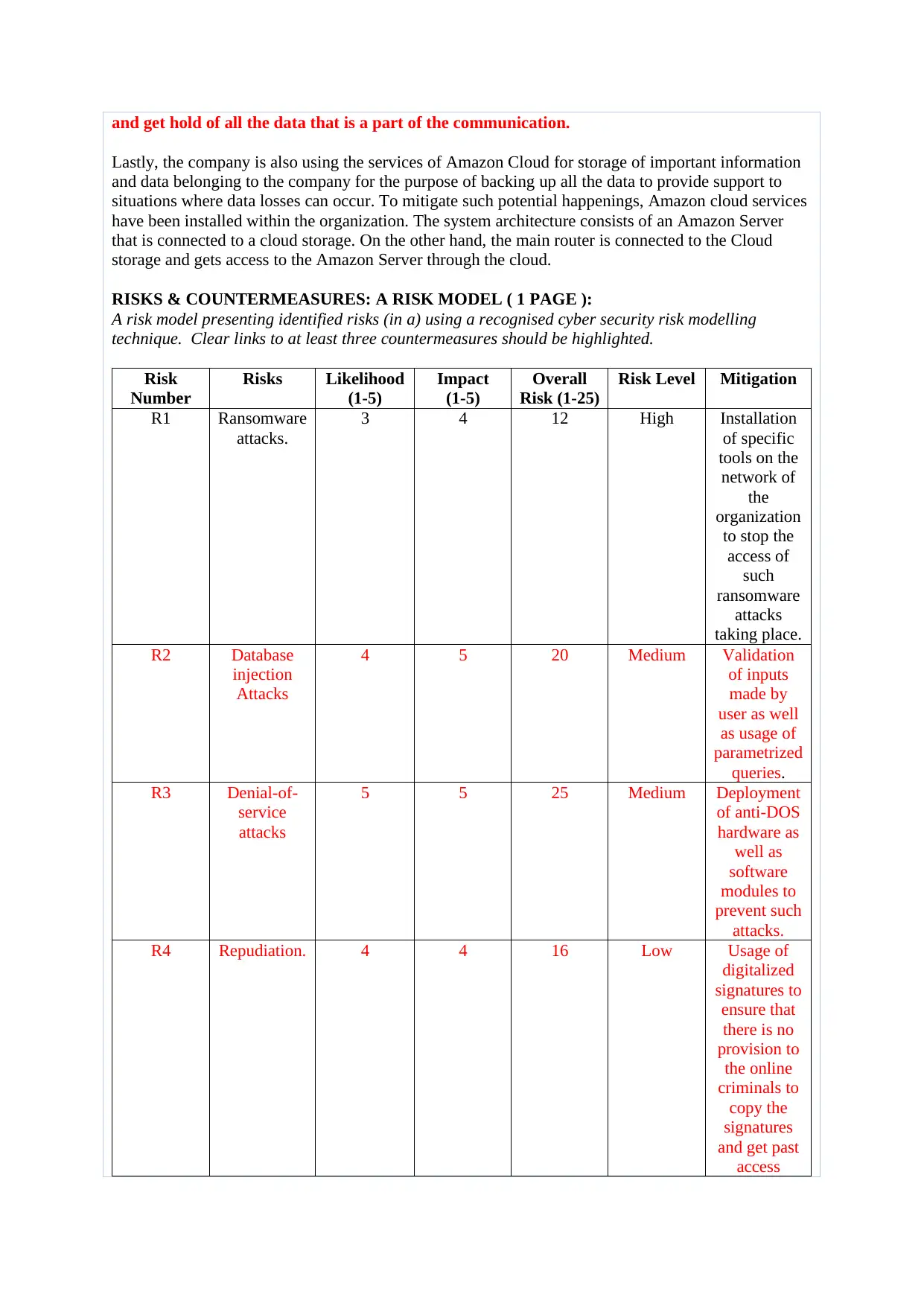
RISKS & COUNTERMEASURES: A RISK MODEL ( 1 PAGE ):
A risk model presenting identified risks (in a) using a recognised cyber security risk modelling
technique. Clear links to at least three countermeasures should be highlighted.
Risk
Number
Risks Likelihood
(1-5)
Impact
(1-5)
Overall
Risk (1-25)
Risk Level Mitigation
R1 Ransomware
attacks.
3 4 12 High Installation
of specific
tools on the
network of
the
organization
to stop the
access of
such
ransomware
attacks
taking place.
R2 Database
injection
Attacks
4 5 20 Medium Validation
of inputs
made by
user as well
as usage of
parametrized
queries.
R3 Denial-of-
service
attacks
5 5 25 Medium Deployment
of anti-DOS
hardware as
well as
software
modules to
prevent such
attacks.
R4 Repudiation. 4 4 16 Low Usage of
digitalized
signatures to
ensure that
there is no
provision to
the online
criminals to
copy the
signatures
and get past
access
Lastly, the company is also using the services of Amazon Cloud for storage of important information
and data belonging to the company for the purpose of backing up all the data to provide support to
situations where data losses can occur. To mitigate such potential happenings, Amazon cloud services
have been installed within the organization. The system architecture consists of an Amazon Server
that is connected to a cloud storage. On the other hand, the main router is connected to the Cloud
storage and gets access to the Amazon Server through the cloud.
RISKS & COUNTERMEASURES: A RISK MODEL ( 1 PAGE ):
A risk model presenting identified risks (in a) using a recognised cyber security risk modelling
technique. Clear links to at least three countermeasures should be highlighted.
Risk
Number
Risks Likelihood
(1-5)
Impact
(1-5)
Overall
Risk (1-25)
Risk Level Mitigation
R1 Ransomware
attacks.
3 4 12 High Installation
of specific
tools on the
network of
the
organization
to stop the
access of
such
ransomware
attacks
taking place.
R2 Database
injection
Attacks
4 5 20 Medium Validation
of inputs
made by
user as well
as usage of
parametrized
queries.
R3 Denial-of-
service
attacks
5 5 25 Medium Deployment
of anti-DOS
hardware as
well as
software
modules to
prevent such
attacks.
R4 Repudiation. 4 4 16 Low Usage of
digitalized
signatures to
ensure that
there is no
provision to
the online
criminals to
copy the
signatures
and get past
access
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

gateways.
TOOLS ( UP TO 1 PAGE ):
A description of at least three tools that could be used as a countermeasure to address risks (with
reference to the kill chain).
Provisioning with protection to the IT environment is considered to be critical. Every single
organization is in need of taking cybersecurity with serious attention. There is the existence of a
number of hacking attacks that might affect the businesses no matter of what size. Hackers, viruses
as well as malware refer to some of the most potential threats existing within the cyber world that
carry the potential capability to cause particular damage to the business activities existing within a
specific organization for business. However, all of these threats can be minimized with the help of
certain tools meant for providing the data with protection. These are,
i) Firewalls- the firewalls refers to a very useful tool but also having certain limitations at
the same time. This tool particularly mitigates or prevents unauthorized access into
the specific network of a business organization. This tools particularly prevents
internet users as well as accessing privately existing networks to enter the network of
any organization without any access. ZoneAlarm is the best firewall tool that exists
within the market and is used by majority of the organizations worldwide.
ii) Antivirus Software- this specifically refers to a design that has been particularly
designed for the purpose of preventing, detecting as well as removing the viruses
along with other existing malware attacks on an individual personal computer, the IT
systems and the Networks. Along with this, it also protects the computers as well as
the networks from all of the variety of different threats and the viruses such as the
likes of Trojan Horses, key loggers, rootkits, spyware and adware. McAfee is
considered to be the best antivirus within the marker that has been protecting the
resources of the business organizations for a long time.
iii) PKI Services- this specific tools provisions with the distribution as well as identification of
all the publicly existing keys for encryption. This enables the users as well as the
computer systems to exchange data in a secure manner over internet along with
verifying the identity of the other existing party. There can also be exchange of data
without the prior presence of PKI, but in such conditions there is no existence of any
assurance of authentication belonging to the other side of transaction.
iv) Managed Detection and Response Service (MDR)- this refers to an advanced form of
security service that provisions with the process of threat hunting, intelligence, analysis
of incident, and response of incident. This is the service arising from the specific needs
aligned to the organizations to stay aware of the risks existing and to improve the
potential ability to detect the same and respond to such threats in a better way. MDE
also makes use of Artificial Intelligence along with the inclusion of machine learning to
specifically carry out the investigation, auto detection of threats as well as to orchestrate
the responses to provision with faster results.
v) Penetration testing- penetration testing refers to an important way of evaluating the
security systems belonging to the businesses as well as the security of the IT
infrastructure by the safe try of exploiting the vulnerabilities. All of these
vulnerabilities exist within the operating systems along with the services as well as the
applications belonging to the computer systems. Within the process of penetration
testing, professionals belonging to the field of cyber security make proper utilization of
similar techniques and procedures that are specifically utilized by the hackers to keep
a check upon the potential threats as well as to define the key areas for weaknesses.
TOOLS ( UP TO 1 PAGE ):
A description of at least three tools that could be used as a countermeasure to address risks (with
reference to the kill chain).
Provisioning with protection to the IT environment is considered to be critical. Every single
organization is in need of taking cybersecurity with serious attention. There is the existence of a
number of hacking attacks that might affect the businesses no matter of what size. Hackers, viruses
as well as malware refer to some of the most potential threats existing within the cyber world that
carry the potential capability to cause particular damage to the business activities existing within a
specific organization for business. However, all of these threats can be minimized with the help of
certain tools meant for providing the data with protection. These are,
i) Firewalls- the firewalls refers to a very useful tool but also having certain limitations at
the same time. This tool particularly mitigates or prevents unauthorized access into
the specific network of a business organization. This tools particularly prevents
internet users as well as accessing privately existing networks to enter the network of
any organization without any access. ZoneAlarm is the best firewall tool that exists
within the market and is used by majority of the organizations worldwide.
ii) Antivirus Software- this specifically refers to a design that has been particularly
designed for the purpose of preventing, detecting as well as removing the viruses
along with other existing malware attacks on an individual personal computer, the IT
systems and the Networks. Along with this, it also protects the computers as well as
the networks from all of the variety of different threats and the viruses such as the
likes of Trojan Horses, key loggers, rootkits, spyware and adware. McAfee is
considered to be the best antivirus within the marker that has been protecting the
resources of the business organizations for a long time.
iii) PKI Services- this specific tools provisions with the distribution as well as identification of
all the publicly existing keys for encryption. This enables the users as well as the
computer systems to exchange data in a secure manner over internet along with
verifying the identity of the other existing party. There can also be exchange of data
without the prior presence of PKI, but in such conditions there is no existence of any
assurance of authentication belonging to the other side of transaction.
iv) Managed Detection and Response Service (MDR)- this refers to an advanced form of
security service that provisions with the process of threat hunting, intelligence, analysis
of incident, and response of incident. This is the service arising from the specific needs
aligned to the organizations to stay aware of the risks existing and to improve the
potential ability to detect the same and respond to such threats in a better way. MDE
also makes use of Artificial Intelligence along with the inclusion of machine learning to
specifically carry out the investigation, auto detection of threats as well as to orchestrate
the responses to provision with faster results.
v) Penetration testing- penetration testing refers to an important way of evaluating the
security systems belonging to the businesses as well as the security of the IT
infrastructure by the safe try of exploiting the vulnerabilities. All of these
vulnerabilities exist within the operating systems along with the services as well as the
applications belonging to the computer systems. Within the process of penetration
testing, professionals belonging to the field of cyber security make proper utilization of
similar techniques and procedures that are specifically utilized by the hackers to keep
a check upon the potential threats as well as to define the key areas for weaknesses.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The best tool for penetration testing that will provision with the best amount of
security against cyber threats is Nmap that carries out the activity of port scanning,
vulnerability scanning, identification of OS as well as tracing the routes.
BIBLIOGRAPHY ( UP TO 1 PAGE ):
Harvard format
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Bada, M., Sasse, A.M. and Nurse, J.R., 2019. Cyber security awareness campaigns: Why do they fail
to change behaviour?. arXiv preprint arXiv:1901.02672.
Buczak, A.L. and Guven, E., 2015. A survey of data mining and machine learning methods for cyber
security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), pp.1153-1176.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016. A
review of cyber security risk assessment methods for SCADA systems. Computers & security, 56,
pp.1-27.
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F., 2016. Decision support
approaches for cyber security investment. Decision Support Systems, 86, pp.13-23.
Graham, J., Olson, R. and Howard, R., 2016. Cyber security essentials. Auerbach Publications.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on modern
cryptographic solutions for computer and cyber security. IGI global.
Hendrix, M., Al-Sherbaz, A. and Bloom, V., 2016. Game based cyber security training: are serious
games suitable for cyber security training?. International Journal of Serious Games, 3(1).
Knowles, W., Prince, D., Hutchison, D., Disso, J.F.P. and Jones, K., 2015. A survey of cyber security
management in industrial control systems. International journal of critical infrastructure
protection, 9, pp.52-80.
Maglaras, L.A., Kim, K.H., Janicke, H., Ferrag, M.A., Rallis, S., Fragkou, P., Maglaras, A. and Cruz,
T.J., 2018. Cyber security of critical infrastructures. Ict Express, 4(1), pp.42-45.
Sun, C.C., Hahn, A. and Liu, C.C., 2018. Cyber security of a power grid: State-of-the-
art. International Journal of Electrical Power & Energy Systems, 99, pp.45-56.
Syed, Z., Padia, A., Finin, T., Mathews, L. and Joshi, A., 2016, March. UCO: A unified cybersecurity
ontology. In Workshops at the Thirtieth AAAI Conference on Artificial Intelligence.
security against cyber threats is Nmap that carries out the activity of port scanning,
vulnerability scanning, identification of OS as well as tracing the routes.
BIBLIOGRAPHY ( UP TO 1 PAGE ):
Harvard format
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Bada, M., Sasse, A.M. and Nurse, J.R., 2019. Cyber security awareness campaigns: Why do they fail
to change behaviour?. arXiv preprint arXiv:1901.02672.
Buczak, A.L. and Guven, E., 2015. A survey of data mining and machine learning methods for cyber
security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), pp.1153-1176.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016. A
review of cyber security risk assessment methods for SCADA systems. Computers & security, 56,
pp.1-27.
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F., 2016. Decision support
approaches for cyber security investment. Decision Support Systems, 86, pp.13-23.
Graham, J., Olson, R. and Howard, R., 2016. Cyber security essentials. Auerbach Publications.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on modern
cryptographic solutions for computer and cyber security. IGI global.
Hendrix, M., Al-Sherbaz, A. and Bloom, V., 2016. Game based cyber security training: are serious
games suitable for cyber security training?. International Journal of Serious Games, 3(1).
Knowles, W., Prince, D., Hutchison, D., Disso, J.F.P. and Jones, K., 2015. A survey of cyber security
management in industrial control systems. International journal of critical infrastructure
protection, 9, pp.52-80.
Maglaras, L.A., Kim, K.H., Janicke, H., Ferrag, M.A., Rallis, S., Fragkou, P., Maglaras, A. and Cruz,
T.J., 2018. Cyber security of critical infrastructures. Ict Express, 4(1), pp.42-45.
Sun, C.C., Hahn, A. and Liu, C.C., 2018. Cyber security of a power grid: State-of-the-
art. International Journal of Electrical Power & Energy Systems, 99, pp.45-56.
Syed, Z., Padia, A., Finin, T., Mathews, L. and Joshi, A., 2016, March. UCO: A unified cybersecurity
ontology. In Workshops at the Thirtieth AAAI Conference on Artificial Intelligence.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





