University Cyber Security Risk and Mitigation Techniques Report
VerifiedAdded on 2022/11/15
|19
|4079
|163
Report
AI Summary
This report delves into the crucial domain of cyber security, examining various techniques for mitigating risks associated with cyber threats. It begins with an abstract and table of contents, setting the stage for a detailed exploration of the subject. The report provides a comprehensive overview of cyber security, its increasing importance in the digital age, and the need for robust security measures. It outlines the purpose, aims, and research questions, including the techniques to increase system robustness and the cyber security issues mitigated by these techniques. The report defines the paradigm, outlining its components such as ontology, epistemology, and methodology. It describes the methods used for the study, including the use of literary articles and secondary data research, emphasizing the benefits of peer-reviewed journals. The rationale for the study is explained, highlighting the growing need for cyber security in organizational processing. A conceptual framework is presented, illustrating the relationship between institutional and organizational aspects, security measures, and botnet activity. The literature review explores cyber security definitions, the challenges faced, and the techniques employed, such as firewalls, antivirus, and intrusion detection systems. The report concludes by summarizing the key findings and considerations related to cyber security risk mitigation.

Running head: CYBER SECURITY RISK AND MITIGATION TECHNIQUES
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Name of the Student
Name of the University
Author note
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Abstract
This report will discuss about the techniques that are used for mitigating the cyber security
issues. Methodologies that are used for completion of the project is also stated in this report.
Literature review regarding the technologies that are being used for mitigating different cyber
security issues. Variables and relationship in between different variables are also provided. This
report also discusses the issues that are present that leads to the usage of the cyber security
related issues. Summary of considerations are used in the report as well. Detailing regarding data
collection tools are also stated in this report. Secondary data collection process is used in this
report. With the help of the secondary technique the main aspect that is provided includes the
fact that the data that are generated as per the theory and the peer reviewed journals are used in
this process.
Table of Contents
Introduction......................................................................................................................................3
Background......................................................................................................................3
Overview..........................................................................................................................3
Purpose of the study.........................................................................................................4
Summary of research question and purpose....................................................................................4
Research Question...........................................................................................................4
Aim..................................................................................................................................4
Hypothesis.......................................................................................................................4
Definition of Paradigm....................................................................................................5
Method used for the study...............................................................................................6
Rationale for choice.........................................................................................................6
Introduction to conceptual framework.............................................................................7
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Abstract
This report will discuss about the techniques that are used for mitigating the cyber security
issues. Methodologies that are used for completion of the project is also stated in this report.
Literature review regarding the technologies that are being used for mitigating different cyber
security issues. Variables and relationship in between different variables are also provided. This
report also discusses the issues that are present that leads to the usage of the cyber security
related issues. Summary of considerations are used in the report as well. Detailing regarding data
collection tools are also stated in this report. Secondary data collection process is used in this
report. With the help of the secondary technique the main aspect that is provided includes the
fact that the data that are generated as per the theory and the peer reviewed journals are used in
this process.
Table of Contents
Introduction......................................................................................................................................3
Background......................................................................................................................3
Overview..........................................................................................................................3
Purpose of the study.........................................................................................................4
Summary of research question and purpose....................................................................................4
Research Question...........................................................................................................4
Aim..................................................................................................................................4
Hypothesis.......................................................................................................................4
Definition of Paradigm....................................................................................................5
Method used for the study...............................................................................................6
Rationale for choice.........................................................................................................6
Introduction to conceptual framework.............................................................................7

2
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Summary of Relevant Literature.....................................................................................................8
Summary methods, methodology and data collection...................................................................12
Variables used and relation in between variables..........................................................12
Data collection and measurement tools.........................................................................12
Summary of consideration (Safety consideration)........................................................................13
Conclusion.....................................................................................................................................13
References......................................................................................................................................15
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Summary of Relevant Literature.....................................................................................................8
Summary methods, methodology and data collection...................................................................12
Variables used and relation in between variables..........................................................12
Data collection and measurement tools.........................................................................12
Summary of consideration (Safety consideration)........................................................................13
Conclusion.....................................................................................................................................13
References......................................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Introduction
Background
Cyber security has been one of the most dependable technology that provides proper
security services to the devices that are based on the technology of digital platform. Several
techniques are present that are used as cyber security tools for the processing of the security
system of the digital platform. Cyber Security has been one of the major technologies that has
been gaining importance in the regular business commencing process. This increase in the need
of implementation of cyber security is due to the fact that the implementation of digital platform
in regular processing of the management of tasks that have been providing higher benefits in
commencing them and hence there has been higher acceptance of digital technology. With the
implementation of the digital technologies, implementation of cyber security technology is
important. This ensures the fact that proper management of the newly implemented digital
technology will stay protected from cyber-attacks that are performed by the imposters. With
implementation of the cyber security policies these cyber security issues can be mitigated and
hence the efficiency in the functioning of the digital platform will increase. Hence proper
understanding of the terminology of cyber security have been benefitting in staying up to date
with the society.
Overview
This report will provide a proper discussion of the purpose of the study regarding cyber
security techniques and the reasons of their implementation. This report also provides a better
understanding of the research questions. Aims and hypothesis of the study is also stated in the
report. Proper definition of the paradigm is also provided in the report. Methodologies that are
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Introduction
Background
Cyber security has been one of the most dependable technology that provides proper
security services to the devices that are based on the technology of digital platform. Several
techniques are present that are used as cyber security tools for the processing of the security
system of the digital platform. Cyber Security has been one of the major technologies that has
been gaining importance in the regular business commencing process. This increase in the need
of implementation of cyber security is due to the fact that the implementation of digital platform
in regular processing of the management of tasks that have been providing higher benefits in
commencing them and hence there has been higher acceptance of digital technology. With the
implementation of the digital technologies, implementation of cyber security technology is
important. This ensures the fact that proper management of the newly implemented digital
technology will stay protected from cyber-attacks that are performed by the imposters. With
implementation of the cyber security policies these cyber security issues can be mitigated and
hence the efficiency in the functioning of the digital platform will increase. Hence proper
understanding of the terminology of cyber security have been benefitting in staying up to date
with the society.
Overview
This report will provide a proper discussion of the purpose of the study regarding cyber
security techniques and the reasons of their implementation. This report also provides a better
understanding of the research questions. Aims and hypothesis of the study is also stated in the
report. Proper definition of the paradigm is also provided in the report. Methodologies that are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
chosen for the study have been one of the major aspects of the report. Methodologies that are
implemented for completion of the study are also stated in this report. This report also provides a
proper summary of the relevant literatures as per the requirement of the project. the methods that
are important for data collection are also stated in this report. The tools that are used for data
collection are also stated in this report.
Purpose of the study
Purpose of the study is to understand the techniques that can be implemented for
increasing the robustness of the platform. This indicates the fact that better understanding of the
steps that will be required for fighting against the cyber-attacks from the imposters. Different
steps that can be taken by the cyber security department will be stated in the report that will help
in analyzing proper management of security related issues. Aim of the report is to properly
understand the functioning of the different cyber security techniques that will help in mitigating
several risks related to cybercrimes.
Discussion
Summary of research question and purpose
Research Question
Research Question 1: What are the techniques that are used for increasing the robustness of the
system?
Research Question 2: What are the cyber security issues that are mitigated by the Cyber security
techniques?
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
chosen for the study have been one of the major aspects of the report. Methodologies that are
implemented for completion of the study are also stated in this report. This report also provides a
proper summary of the relevant literatures as per the requirement of the project. the methods that
are important for data collection are also stated in this report. The tools that are used for data
collection are also stated in this report.
Purpose of the study
Purpose of the study is to understand the techniques that can be implemented for
increasing the robustness of the platform. This indicates the fact that better understanding of the
steps that will be required for fighting against the cyber-attacks from the imposters. Different
steps that can be taken by the cyber security department will be stated in the report that will help
in analyzing proper management of security related issues. Aim of the report is to properly
understand the functioning of the different cyber security techniques that will help in mitigating
several risks related to cybercrimes.
Discussion
Summary of research question and purpose
Research Question
Research Question 1: What are the techniques that are used for increasing the robustness of the
system?
Research Question 2: What are the cyber security issues that are mitigated by the Cyber security
techniques?

5
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Hypothesis
Hypothesis 1: Implementation of Cyber Security has been ever increasing
Hypothesis 2: There are different cyber security techniques that are implemented for different
cyber-attacks?
Definition of Paradigm
Paradigm is a set of concepts that helps in developing of a pattern that helps in bettering
of the understanding of the concepts. These are the set of assumptions that help in proper
development of the values and as per the viewing of the reality for proper community and
especially as per the intellectual discipline.
The main components that will be sub divided into Ontology, Epistemology and
methodology. As per the ontology, the processing of the Cyber security ontology is also sub
divided in between the General methodology, Specific methodology and Cyber Ontology
architecture. As per the general methodology, the analysis processing that is preformed includes
proper management of the analysis and hence processing of the competency question. Proper
questioning regarding the cyber security is performed. These questions are asked as per the
procedures that helps in understanding the functioning process of the granularity. As per the
Specific methodology, establishing of the possible existing ontologies. Incorporation of the cyber
ontology has been providing proper choosing of the ontologies that are available. Again, as per
the Cyber ontology architecture, the upper ontologies are considered as the high level domain
independent ontologies. These are also considered as the universal ontologies. The mid level
ontologies are concerned with the functional processing of the abstract that enhances the
functioning of the multiple domain ontologies. These provides proper concrete representation of
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Hypothesis
Hypothesis 1: Implementation of Cyber Security has been ever increasing
Hypothesis 2: There are different cyber security techniques that are implemented for different
cyber-attacks?
Definition of Paradigm
Paradigm is a set of concepts that helps in developing of a pattern that helps in bettering
of the understanding of the concepts. These are the set of assumptions that help in proper
development of the values and as per the viewing of the reality for proper community and
especially as per the intellectual discipline.
The main components that will be sub divided into Ontology, Epistemology and
methodology. As per the ontology, the processing of the Cyber security ontology is also sub
divided in between the General methodology, Specific methodology and Cyber Ontology
architecture. As per the general methodology, the analysis processing that is preformed includes
proper management of the analysis and hence processing of the competency question. Proper
questioning regarding the cyber security is performed. These questions are asked as per the
procedures that helps in understanding the functioning process of the granularity. As per the
Specific methodology, establishing of the possible existing ontologies. Incorporation of the cyber
ontology has been providing proper choosing of the ontologies that are available. Again, as per
the Cyber ontology architecture, the upper ontologies are considered as the high level domain
independent ontologies. These are also considered as the universal ontologies. The mid level
ontologies are concerned with the functional processing of the abstract that enhances the
functioning of the multiple domain ontologies. These provides proper concrete representation of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
the demarcation of the points that are related to the processing of the time and location defining
as pee the concept. These ontologies are considered as utility ontologies. The domain ontologies
are processed with the specification of the concepts that are particular for a domain and hence
representation of the same concepts that are imported. These are considered as the extended
versions of the mid level as well as the upper ontologies.
Method used for the study
The method that is used in the commencing of the study includes usage of the literary
articles. This implementation of the literary articles includes the aspect that proper understanding
of the required processing of the cyber security includes secondary data research, with the help
of the secondary data research, peer reviewed journals are taken into consideration. With the help
of the peer reviewed journals the data that are present in the journals are used. This usage of the
data from the peer reviewed journals increases the accuracy of the data that are used in the
processing. This ensures that the data that are provided and gained during the study will be
beneficial. With the help of the peer reviewed journals the main advantages that will be gained
includes the fact that the data are well referenced and hence with the data that are taken for the
completion of the study will be well authenticated and copyright issue will not arise. These are
the reason that the usage of the secondary data collection method is performed for the execution
of the study.
Rationale for choice
Organizational processing has been getting benefitted with the help of the
implementation of the processing of the digital platform. With the benefits, risks are generated.
This generating of risks ensures that proper management of the decision and policy makers will
be having a proper understanding of the risks regarding the data processing. This has been
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
the demarcation of the points that are related to the processing of the time and location defining
as pee the concept. These ontologies are considered as utility ontologies. The domain ontologies
are processed with the specification of the concepts that are particular for a domain and hence
representation of the same concepts that are imported. These are considered as the extended
versions of the mid level as well as the upper ontologies.
Method used for the study
The method that is used in the commencing of the study includes usage of the literary
articles. This implementation of the literary articles includes the aspect that proper understanding
of the required processing of the cyber security includes secondary data research, with the help
of the secondary data research, peer reviewed journals are taken into consideration. With the help
of the peer reviewed journals the data that are present in the journals are used. This usage of the
data from the peer reviewed journals increases the accuracy of the data that are used in the
processing. This ensures that the data that are provided and gained during the study will be
beneficial. With the help of the peer reviewed journals the main advantages that will be gained
includes the fact that the data are well referenced and hence with the data that are taken for the
completion of the study will be well authenticated and copyright issue will not arise. These are
the reason that the usage of the secondary data collection method is performed for the execution
of the study.
Rationale for choice
Organizational processing has been getting benefitted with the help of the
implementation of the processing of the digital platform. With the benefits, risks are generated.
This generating of risks ensures that proper management of the decision and policy makers will
be having a proper understanding of the risks regarding the data processing. This has been
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
increasing the need of implementation of the cyber security. With increase in the number of
issues the techniques that are required for mitigating the issues have also been increasing. With
the increase of cybercrime it has been getting rationale for discuss regarding the functioning of
the cyber security system. This has been a major reason that the functional process has been
getting functional as per the logical basis of the implementation of the cyber security.
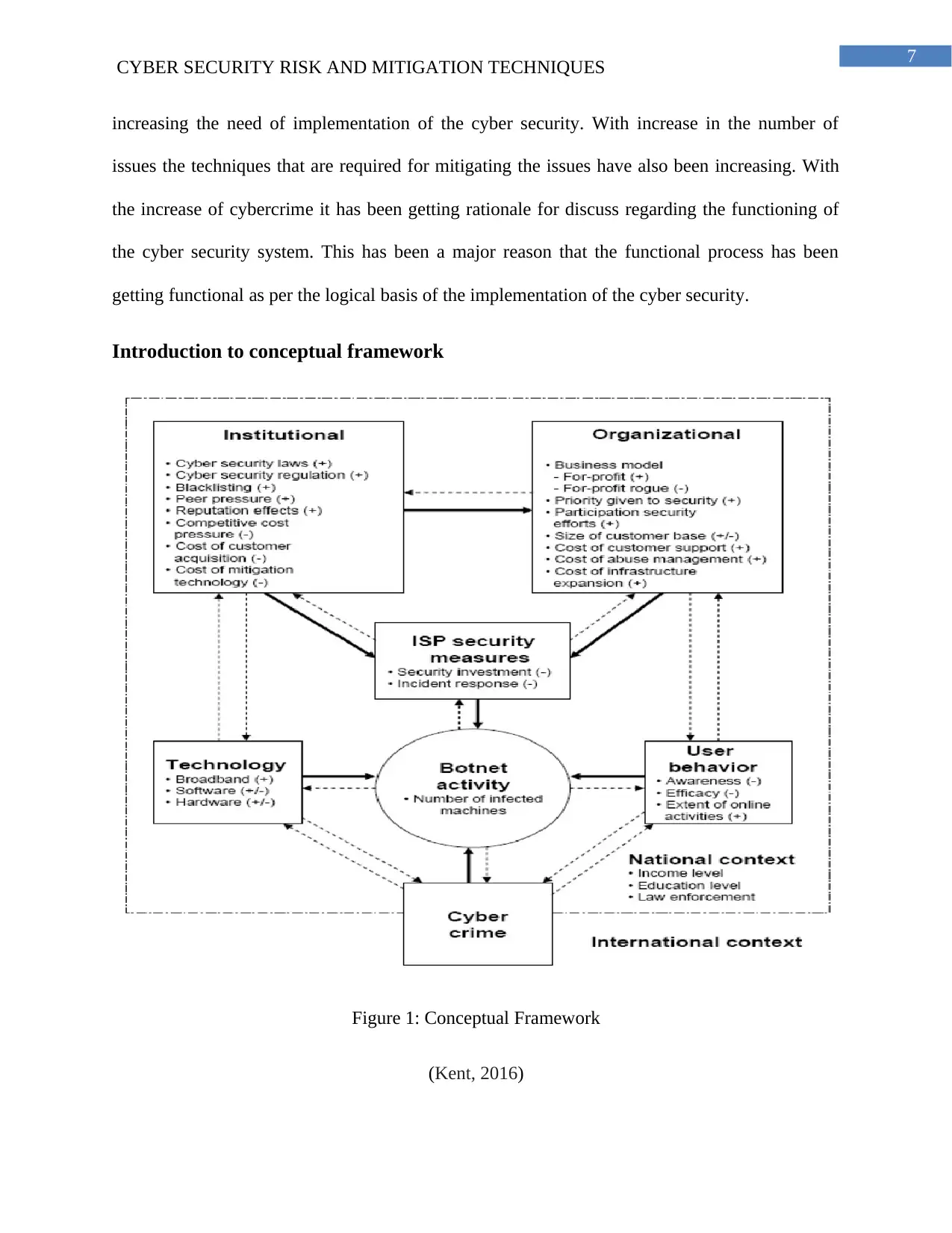
Introduction to conceptual framework
Figure 1: Conceptual Framework
(Kent, 2016)
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
increasing the need of implementation of the cyber security. With increase in the number of
issues the techniques that are required for mitigating the issues have also been increasing. With
the increase of cybercrime it has been getting rationale for discuss regarding the functioning of
the cyber security system. This has been a major reason that the functional process has been
getting functional as per the logical basis of the implementation of the cyber security.
Introduction to conceptual framework
Figure 1: Conceptual Framework
(Kent, 2016)

8
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
As per the above conceptual framework the tasks that imposes cyber-attack risks are
differentiated in 2 halves, namely the Institutional and the organizational. There is an exchange
in between the Institutional and Organization. The output of the respective is sent to the ISP
security measure. These stages perform security investment and incident response. The output of
the ISP security measure is sent to the Bot net activity. This ensures that proper management of
the business organization will get performed as per the technology, user behavior and the cyber
security is the measures that are chosen after performing the entire analysis process. These are
the security related issues that are present and are needed to be mitigated as per the techniques
that benefit the functioning process.
Literature Review
According to Buczak & Guven (2015), Cyber security is a body of technology that
enhances the designing practices that helps in bettering of the network robustness. With the
increase in the processing of the network robustness the main aspect that will be gathered
includes the fact that security of the devices, programs and data from cyber attacks are the main
responsibility of the cyber security system. Information technology security is the main concern
of the cyber security system.
The importance of cyber security has been increasing in the department of the military
government, corporate and financial section. This ensures that the usage of the cyber security has
been increasing as per the global processing of the digital platform. In this case it is considered
that out of the entire data set only a part of the data asset is considered as the important data that
are required for the processing of the business management system. Protecting that part of the
data is the main concern ad the goal of the cyber security system. These data can be treated as the
intellectual property and hence storing of data with higher robustness has always been an issue
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
As per the above conceptual framework the tasks that imposes cyber-attack risks are
differentiated in 2 halves, namely the Institutional and the organizational. There is an exchange
in between the Institutional and Organization. The output of the respective is sent to the ISP
security measure. These stages perform security investment and incident response. The output of
the ISP security measure is sent to the Bot net activity. This ensures that proper management of
the business organization will get performed as per the technology, user behavior and the cyber
security is the measures that are chosen after performing the entire analysis process. These are
the security related issues that are present and are needed to be mitigated as per the techniques
that benefit the functioning process.
Literature Review
According to Buczak & Guven (2015), Cyber security is a body of technology that
enhances the designing practices that helps in bettering of the network robustness. With the
increase in the processing of the network robustness the main aspect that will be gathered
includes the fact that security of the devices, programs and data from cyber attacks are the main
responsibility of the cyber security system. Information technology security is the main concern
of the cyber security system.
The importance of cyber security has been increasing in the department of the military
government, corporate and financial section. This ensures that the usage of the cyber security has
been increasing as per the global processing of the digital platform. In this case it is considered
that out of the entire data set only a part of the data asset is considered as the important data that
are required for the processing of the business management system. Protecting that part of the
data is the main concern ad the goal of the cyber security system. These data can be treated as the
intellectual property and hence storing of data with higher robustness has always been an issue
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
for the following departments. Organizations have been transmitting sensitive data as per the
commencing of the management of the data that are stored in the system. With the increase in
sophistication, growth in the cyber attacks have been noted. Hence need of protecting of data has
been increasing.
According to Carr (2016), The challenges that are faced by the cyber security includes
Network Security, Application security, Endpoint security, data security, Database and
Infrastructure security, cloud security, Mobile security, business continuity planning and end
user planning.
As per the processing of the network security the main step that is taken includes
implementation of the firewall. The main types of network security devices include Active
devices that includes blocking of the surplus traffic. Implementation of the firewalls, content
filtering devices are considered to be the devices that provides security against excess data flow.
Passive devices include implementation of the detection appliances. The main task of the passive
devices is to provide a brief understanding and reporting of the unwanted data and traffic that
have been interfering in the process. Penetrative devices include roper management of the
scanning of the network and hence identifying the issues that are present in the network. These
devices are mainly concerned in performing of the penetration test. This is one of the major
aspects that proper vulnerability assessment is performed with higher scalability and hence the
results that are received are accurate in nature.
The techniques that are used as the cyber security processes includes the functioning of
the Firewalls, Antivirus, Content filtering and Intrusion detection system.
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
for the following departments. Organizations have been transmitting sensitive data as per the
commencing of the management of the data that are stored in the system. With the increase in
sophistication, growth in the cyber attacks have been noted. Hence need of protecting of data has
been increasing.
According to Carr (2016), The challenges that are faced by the cyber security includes
Network Security, Application security, Endpoint security, data security, Database and
Infrastructure security, cloud security, Mobile security, business continuity planning and end
user planning.
As per the processing of the network security the main step that is taken includes
implementation of the firewall. The main types of network security devices include Active
devices that includes blocking of the surplus traffic. Implementation of the firewalls, content
filtering devices are considered to be the devices that provides security against excess data flow.
Passive devices include implementation of the detection appliances. The main task of the passive
devices is to provide a brief understanding and reporting of the unwanted data and traffic that
have been interfering in the process. Penetrative devices include roper management of the
scanning of the network and hence identifying the issues that are present in the network. These
devices are mainly concerned in performing of the penetration test. This is one of the major
aspects that proper vulnerability assessment is performed with higher scalability and hence the
results that are received are accurate in nature.
The techniques that are used as the cyber security processes includes the functioning of
the Firewalls, Antivirus, Content filtering and Intrusion detection system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Firewalls are considered as the network security system that is used for the processing of
the regulation of the network traffic that is based on the functioning of the protocols of the
security measures. With the help of the implementation of the firewall, a barrier in between the
user of the device and the internet is established. This insists that robustness of the system
increases. The main advantage of implementing firewall includes the fact that the processing of
the Firewall exists in a manner that it provides service in both the system software that will
ensure proper management of both the software that runs on the hardware as well as the
hardware that runs on the hardware. Hardware based firewalls are mainly concerned with the
functional processing of the DHCP SERVER of the network. It is noted that there are several
computing devices that firewall is implemented in the computer systems as it increases the
robustness of the computing systems. Another aspect that is needed includes the fact that proper
management of the data that are present in the computing devices. Another aspect that is taken
into consideration is that the router that helps in proper diversification of the data distribution
also has the firewall integrated in the system. This ensures that the data that are transacted via the
router system stays protected from the cyber-attacks. In general, the usage of the firewalls is seen
to be made in the section of the private networks that provides proper robustness to the system.
With the help of the implementation if the Firewall, the main concern that is processed includes
proper checking of the data that are being transacted via the platform. Intranet security have been
a major concern for the processing of the Firewall. This process considers configuration of both
hardware and software system. The minimum requirement of the hardware firewall includes
proper processing of a minimum of 4 network ports. With the help of the 4 network ports prop
protection of the intranet from the threats can be made.
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
Firewalls are considered as the network security system that is used for the processing of
the regulation of the network traffic that is based on the functioning of the protocols of the
security measures. With the help of the implementation of the firewall, a barrier in between the
user of the device and the internet is established. This insists that robustness of the system
increases. The main advantage of implementing firewall includes the fact that the processing of
the Firewall exists in a manner that it provides service in both the system software that will
ensure proper management of both the software that runs on the hardware as well as the
hardware that runs on the hardware. Hardware based firewalls are mainly concerned with the
functional processing of the DHCP SERVER of the network. It is noted that there are several
computing devices that firewall is implemented in the computer systems as it increases the
robustness of the computing systems. Another aspect that is needed includes the fact that proper
management of the data that are present in the computing devices. Another aspect that is taken
into consideration is that the router that helps in proper diversification of the data distribution
also has the firewall integrated in the system. This ensures that the data that are transacted via the
router system stays protected from the cyber-attacks. In general, the usage of the firewalls is seen
to be made in the section of the private networks that provides proper robustness to the system.
With the help of the implementation if the Firewall, the main concern that is processed includes
proper checking of the data that are being transacted via the platform. Intranet security have been
a major concern for the processing of the Firewall. This process considers configuration of both
hardware and software system. The minimum requirement of the hardware firewall includes
proper processing of a minimum of 4 network ports. With the help of the 4 network ports prop
protection of the intranet from the threats can be made.

11
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
According to Ben & Gonzalez (2015), As per the processing of the antivirus, the main
concern is the malicious software. Antivirus are considered as a tool that helps in preventing the
data sets from the malicious software. These tools were initially developed for checking and
testing of virus as well as the removing of the same as per the commencing of the management
of the robustness of the entire system, despite the fact that implementation of the antivirus not
only scanning and mitigation of issues regarding computing devices but these technology also
have been performing in the mitigation of the trojan viruses, adware, spywares, key loggers.
Another aspect of the processing of the business management of the preventing processing of the
spams, phishing attacks. Attacking as per the botnets and the DDOS were attacking the system
was mitigated.
As per the processing of the content filtering, the main aspect that will be taken onto
consideration is mails and web pages that are violent in nature can be prevented from the data
breaching. This phase of cyber security provides the message of access denied when the data that
is to be performed includes the fact the unauthorized data access is blocked. The processes that
are implemented in the process includes Web filtering. Proper screening of the web sites and the
pages that are associated with the processing of the e mail filtering process. Proper screening of
the data management is performed as per the processing of the objectional content. In case of the
presence of the un objectional content are noticed the entire process is paused ad hence issue that
arises gets mitigated.
According to Knowles et al, (2015), As per the processing of the Intrusion detected
system. With the implementation of the Intrusion detection, the applications are properly
monitoring of the entire system. Another aspect that is to be considered is that this system
reduces the processing of the detection and prevention activity attack of the malicious software.
CYBER SECURITY RISK AND MITIGATION TECHNIQUES
According to Ben & Gonzalez (2015), As per the processing of the antivirus, the main
concern is the malicious software. Antivirus are considered as a tool that helps in preventing the
data sets from the malicious software. These tools were initially developed for checking and
testing of virus as well as the removing of the same as per the commencing of the management
of the robustness of the entire system, despite the fact that implementation of the antivirus not
only scanning and mitigation of issues regarding computing devices but these technology also
have been performing in the mitigation of the trojan viruses, adware, spywares, key loggers.
Another aspect of the processing of the business management of the preventing processing of the
spams, phishing attacks. Attacking as per the botnets and the DDOS were attacking the system
was mitigated.
As per the processing of the content filtering, the main aspect that will be taken onto
consideration is mails and web pages that are violent in nature can be prevented from the data
breaching. This phase of cyber security provides the message of access denied when the data that
is to be performed includes the fact the unauthorized data access is blocked. The processes that
are implemented in the process includes Web filtering. Proper screening of the web sites and the
pages that are associated with the processing of the e mail filtering process. Proper screening of
the data management is performed as per the processing of the objectional content. In case of the
presence of the un objectional content are noticed the entire process is paused ad hence issue that
arises gets mitigated.
According to Knowles et al, (2015), As per the processing of the Intrusion detected
system. With the implementation of the Intrusion detection, the applications are properly
monitoring of the entire system. Another aspect that is to be considered is that this system
reduces the processing of the detection and prevention activity attack of the malicious software.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




